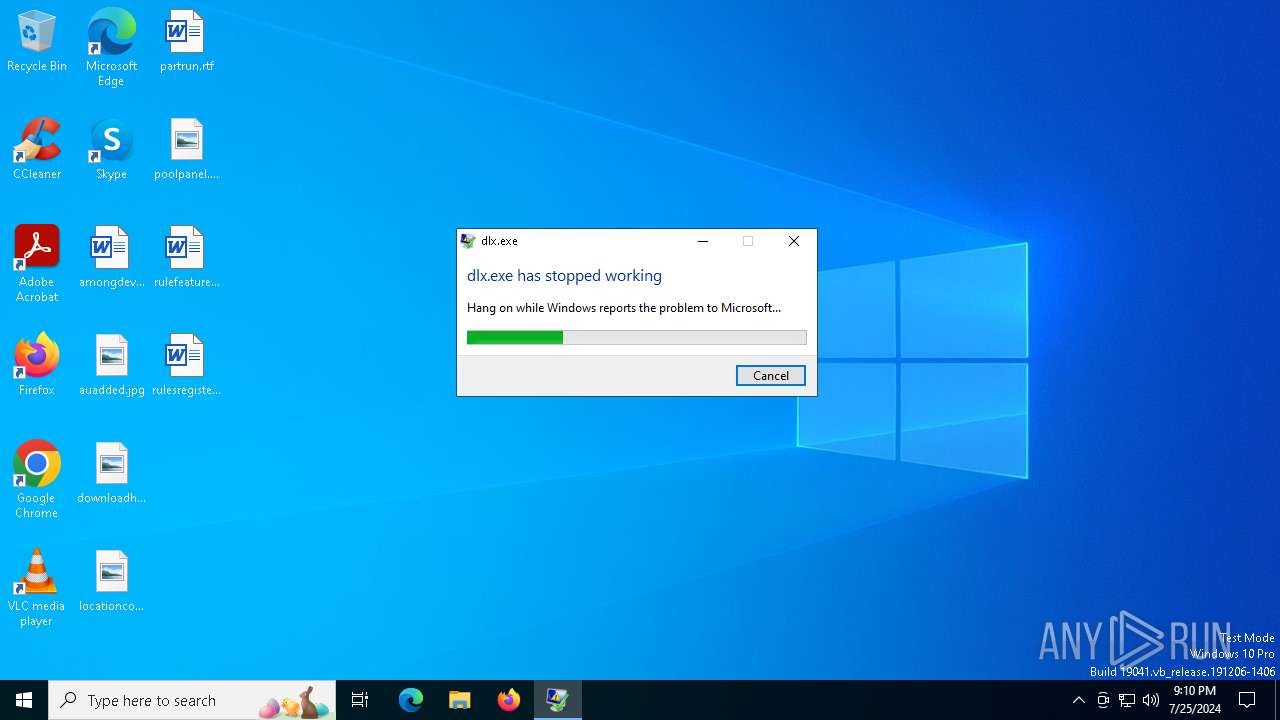
| File name: | dlx.exe |
| Full analysis: | https://app.any.run/tasks/85dddde2-c0a3-43b5-b2fa-6b584deac5ac |
| Verdict: | Malicious activity |
| Analysis date: | July 25, 2024, 21:10:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 597136D76F4706C8F1157B6C0ABAF9FA |
| SHA1: | 1BE4597E07DBEEF4FFFC1BD30D7DC533B06FB359 |
| SHA256: | 7E28687E8E538312503A1647747845A31CA17E2FE1F86AE59FF64E014EFE8871 |
| SSDEEP: | 24576:IYn/GGvn4zZkBqIb2sFXwntbB1d1f0JDa6WeMWsWbzLq/mpbU:7n/GGvnuZkBqIbzFXwntbB1d1f0JDa6X |
MALICIOUS
Drops the executable file immediately after the start
- dlx.exe (PID: 1544)
Scans artifacts that could help determine the target
- dw20.exe (PID: 7044)
SUSPICIOUS
Reads the date of Windows installation
- dw20.exe (PID: 7044)
INFO
Checks supported languages
- dlx.exe (PID: 1544)
- dw20.exe (PID: 7044)
Creates files in the program directory
- dw20.exe (PID: 7044)
Reads Environment values
- dw20.exe (PID: 7044)
Reads the machine GUID from the registry
- dw20.exe (PID: 7044)
Reads the computer name
- dw20.exe (PID: 7044)
Reads product name
- dw20.exe (PID: 7044)
Process checks computer location settings
- dw20.exe (PID: 7044)
Reads CPU info
- dw20.exe (PID: 7044)
Checks proxy server information
- dw20.exe (PID: 7044)
Reads the software policy settings
- dw20.exe (PID: 7044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (55.8) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (21) |
| .scr | | | Windows screen saver (9.9) |
| .dll | | | Win32 Dynamic Link Library (generic) (5) |
| .exe | | | Win32 Executable (generic) (3.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:01:11 18:58:28+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 733184 |
| InitializedDataSize: | 40960 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb4aae |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 9000.1.0.13 |
| ProductVersionNumber: | 9000.1.0.13 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | RedPrairie Corporation |
| FileDescription: | |
| FileVersion: | 9000.1.0.13 |
| InternalName: | Dlx.exe |
| LegalCopyright: | Copyright 2008 |
| OriginalFileName: | Dlx.exe |
| ProductName: | E2e |
| ProductVersion: | 9000.1.0.13 |
| AssemblyVersion: | 9000.1.0.13 |
Total processes
138
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1544 | "C:\Users\admin\AppData\Local\Temp\dlx.exe" | C:\Users\admin\AppData\Local\Temp\dlx.exe | explorer.exe | ||||||||||||
User: admin Company: RedPrairie Corporation Integrity Level: MEDIUM Description: Exit code: 3762507597 Version: 9000.1.0.13 Modules
| |||||||||||||||
| 2368 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7044 | dw20.exe -x -s 844 | C:\Windows\Microsoft.NET\Framework\v2.0.50727\dw20.exe | dlx.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Error Reporting Shim Exit code: 0 Version: 2.0.50727.9149 (WinRelRS6.050727-9100) Modules
| |||||||||||||||
Total events
3 435
Read events
3 433
Write events
2
Delete events
0
Modification events
| (PID) Process: | (7044) dw20.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\IdentityCRL\ClockData |
| Operation: | write | Name: | ClockTimeSeconds |
Value: 44BFA26600000000 | |||
| (PID) Process: | (7044) dw20.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\IdentityCRL\ClockData |
| Operation: | write | Name: | TickCount |
Value: A91F0E0000000000 | |||
Executable files
0
Suspicious files
2
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7044 | dw20.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_dlx.exe_40faa27e2c31430b996bf95707ea918fab0254_00000000_4948e195-ff4a-409c-ad9a-d0abe19b881a\Report.wer | — | |
MD5:— | SHA256:— | |||
| 7044 | dw20.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\37C951188967C8EB88D99893D9D191FE | binary | |
MD5:FB64A9EBEDF48D3895381D5B7D80743D | SHA256:EA21D495930AD76F267A33A0F593DBF0C7EA75E457FCAE49A29DAAD8BD920F42 | |||
| 7044 | dw20.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\21253908F3CB05D51B1C2DA8B681A785 | binary | |
MD5:82C30E45BF5F93A5DB1D5E47F913053B | SHA256:2C6BBFF9207065E8800C4AF0CB2748818ABB3CFFC0D6D518FE17F76A232F8967 | |||
| 7044 | dw20.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER1C8C.tmp.WERInternalMetadata.xml | xml | |
MD5:CD3049C4250DBFC5D8D53CD522DE6DB2 | SHA256:3405449FBC64F9E089921AE48195AD0A19B836B4A361E55EBCAB6E44E89221B8 | |||
| 7044 | dw20.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER1CFA.tmp.xml | xml | |
MD5:34C8C67B7CEDD99F3566846B0CB04354 | SHA256:3B73657E660607FBF65F73722739F1978AFFF118D24B20C845F5DDE092D5FD35 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
44
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5272 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5560 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3996 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3008 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6012 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2628 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4204 | svchost.exe | 4.209.32.67:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
7044 | dw20.exe | 20.189.173.20:443 | watson.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3008 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1952 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |