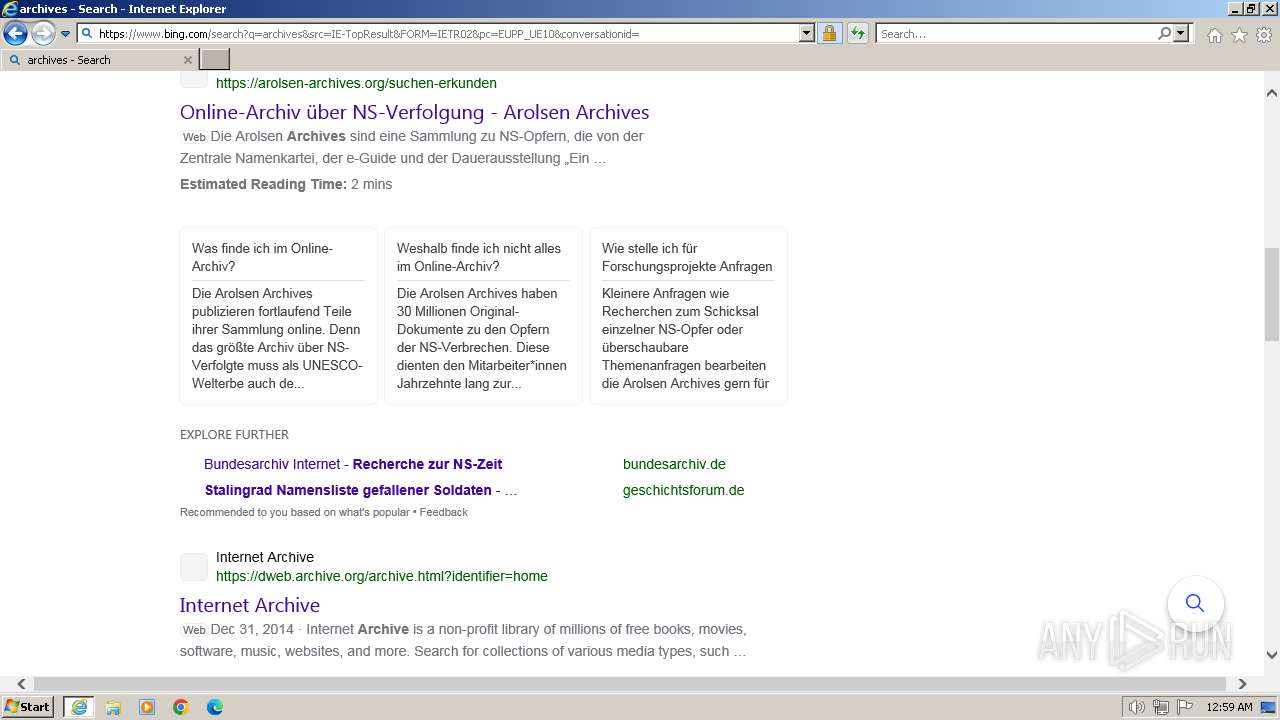
| URL: | http://download-bf3.blogspot.com/2011/01/viruses-2010-05-18-tar-bz2.html |
| Full analysis: | https://app.any.run/tasks/b07504ff-e7e6-4c30-801a-3c4d69c8c047 |
| Verdict: | Malicious activity |
| Analysis date: | February 25, 2024, 00:57:51 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | E03E0A78E8A259DBF07F6EDA0C00229D |
| SHA1: | 1725BABE4E1883366AAE7032B6056F4CDED55AF2 |
| SHA256: | 7E19A32BC4D5E21B3D9E2CEFDB3A899742F4ED5A4B805227AEA920440CD45F7A |
| SSDEEP: | 3:N1KaKEmHUzKMUVdhREkXwJn:CaRzKHoJn |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 3288)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
40
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1432 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3288 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3288 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://download-bf3.blogspot.com/2011/01/viruses-2010-05-18-tar-bz2.html" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
50 021
Read events
49 822
Write events
158
Delete events
41
Modification events
| (PID) Process: | (3288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31090565 | |||
| (PID) Process: | (3288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31090565 | |||
| (PID) Process: | (3288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3288) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
35
Text files
337
Unknown types
25
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1432 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\css[1].css | text | |
MD5:AA5AC0552564CC70FBAF350CC407F8D1 | SHA256:20C4D079C2F90C7DCFAF9D141CD9259B758740DD75E3BF94DA0E47758C15F32C | |||
| 1432 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\maia[1].css | text | |
MD5:9E914FD11C5238C50EBA741A873F0896 | SHA256:8684A32D1A10D050A26FC33192EDF427A5F0C6874C590A68D77AE6E0D186BD8A | |||
| 1432 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:57FF045F34286E5DBAFE38DF8CFC3B63 | SHA256:F76BEDF90B0B33FE7F0B935A98E17D1DA64CFF07F896829741CFBB62A8CF6332 | |||
| 1432 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\memSYaGs126MiZpBA-UvWbX2vVnXBbObj2OVZyOOSr4dVJWUgsiH0B4gaVQ[1].woff | woff | |
MD5:9C845091C3E04D05FABA9FA0A7DD3F87 | SHA256:D4964864E91E640A2B1008F4ECA62CB388DB555A4B1E86FAC028BA01D139DB97 | |||
| 1432 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\F2DDCD2B5F37625B82E81F4976CEE400_91363364208F5CFFAABFD122AF4FD6BD | der | |
MD5:CAD6F6E0069731F61CFE27C0F07165F0 | SHA256:ED23564BA17BBDA58332BB0C06472BF95F6C477100E15D2B97F5EE5D99F44467 | |||
| 1432 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:80EA3F5B5941C89B59BEB9C36114EBA4 | SHA256:FA04554E250C6AED24214B320CFB13534A287F1C954D9362D70DA2D174635781 | |||
| 1432 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:78BC36CDA2F5AF29B101A148C9F46873 | SHA256:76B4D1B118147259CA16600A4DBDA639A212A4CD158350F59A5A918DFBC076F4 | |||
| 1432 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A16C6C16D94F76E0808C087DFC657D99_C62530F37AD5C5022195EB4B959CB082 | der | |
MD5:61A0D3C1230DE600EEF045BD49ED8744 | SHA256:E642A5ADBCFEEA1F001A89130E379CDCB1AEC5C2524E86AB10FE9A7CF892F3C7 | |||
| 1432 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\2223071481-static_pages[1].css | text | |
MD5:ABD7446453CCDC733BA0A08169AFF6C9 | SHA256:BC75B808F349E4FCEC454DE341B7F80FF44FCCD902B0E1109E18D5B3A35B7DE3 | |||
| 1432 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\671481879-analytics_autotrack[1].js | text | |
MD5:1C4256076FAC77893331DB4F22A9A41A | SHA256:57F24A99B10AD3F6431E857B33B26015C29C4CCCCED30375D222A35F0C4F9BB1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
31
TCP/UDP connections
105
DNS requests
42
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1432 | iexplore.exe | GET | — | 142.250.184.225:80 | http://download-bf3.blogspot.com/img/blogger-logotype-color-black-1x.png | unknown | — | — | unknown |
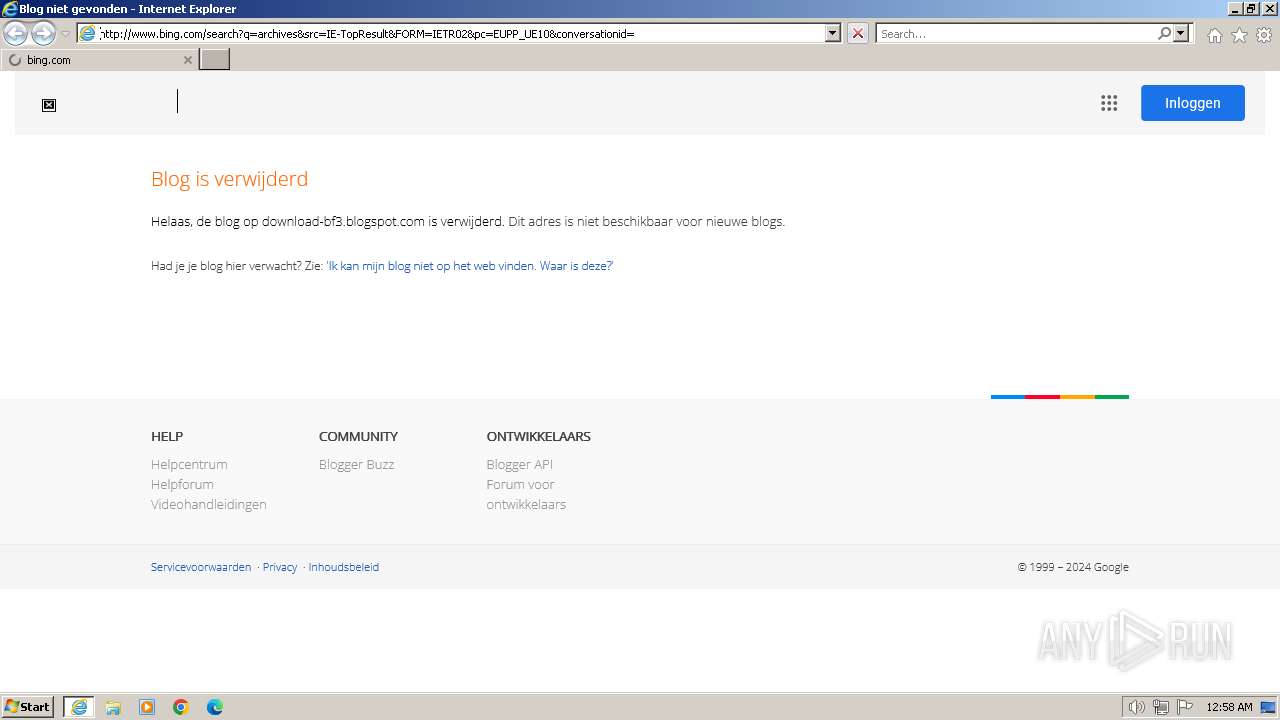
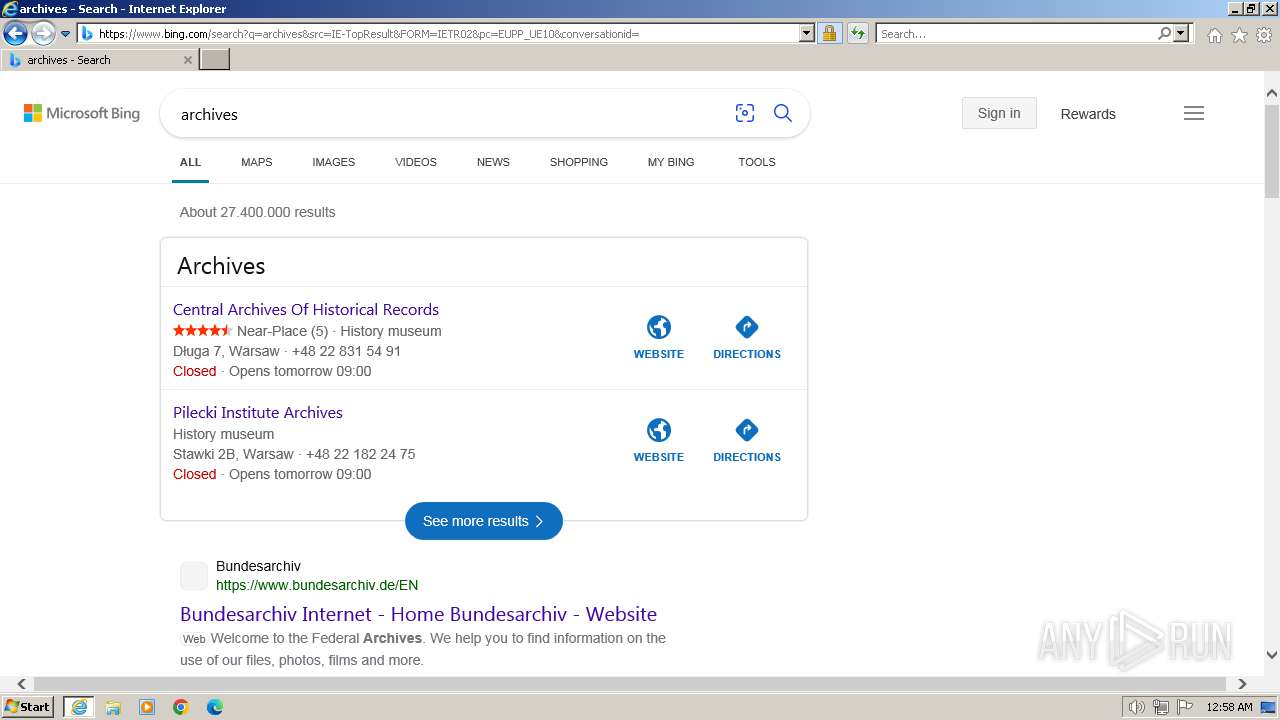
1432 | iexplore.exe | GET | 404 | 142.250.184.225:80 | http://download-bf3.blogspot.com/2011/01/viruses-2010-05-18-tar-bz2.html | unknown | html | 43.3 Kb | unknown |
1432 | iexplore.exe | GET | 200 | 216.58.206.36:80 | http://www.google.com/css/maia.css | unknown | text | 11.9 Kb | unknown |
1432 | iexplore.exe | GET | 200 | 216.58.212.170:80 | http://fonts.googleapis.com/css?family=Open+Sans:300 | unknown | text | 216 b | unknown |
1432 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?21e2d5edb0479497 | unknown | — | — | unknown |
1432 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?31edca662c8b6304 | unknown | — | — | unknown |
1432 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fb542102ae65dd3e | unknown | — | — | unknown |
1432 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?2788e0fe40679967 | unknown | — | — | unknown |
1432 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?4088c777bef75a89 | unknown | — | — | unknown |
1432 | iexplore.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?bf012385ffb92421 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1432 | iexplore.exe | 142.250.184.225:80 | download-bf3.blogspot.com | GOOGLE | US | whitelisted |
1432 | iexplore.exe | 216.58.212.170:80 | fonts.googleapis.com | GOOGLE | US | whitelisted |
1432 | iexplore.exe | 216.58.206.36:80 | www.google.com | GOOGLE | US | whitelisted |
1432 | iexplore.exe | 142.250.184.195:443 | ssl.gstatic.com | GOOGLE | US | whitelisted |
1432 | iexplore.exe | 142.250.186.110:443 | www.google-analytics.com | GOOGLE | US | whitelisted |
1432 | iexplore.exe | 142.250.181.233:443 | www.blogger.com | GOOGLE | US | unknown |
1432 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download-bf3.blogspot.com |
| unknown |
fonts.googleapis.com |
| whitelisted |
www.google.com |
| whitelisted |
www.blogger.com |
| shared |
www.google-analytics.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
www.gstatic.com |
| whitelisted |