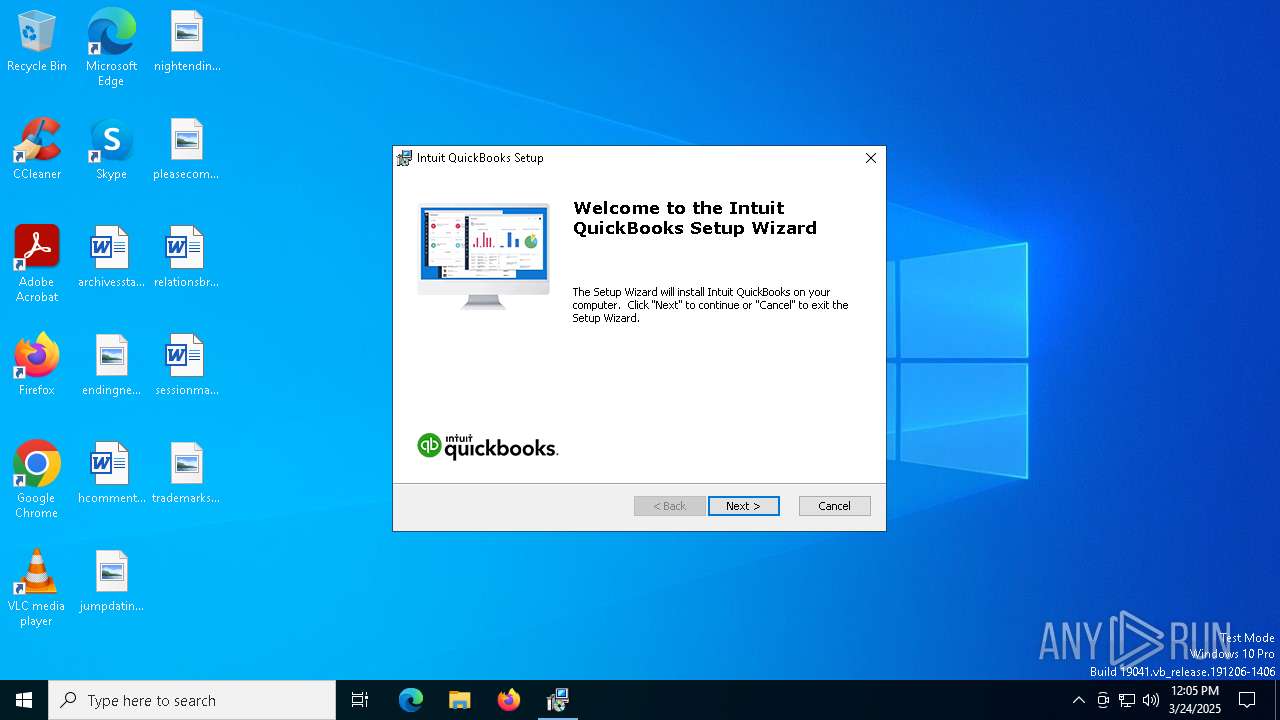
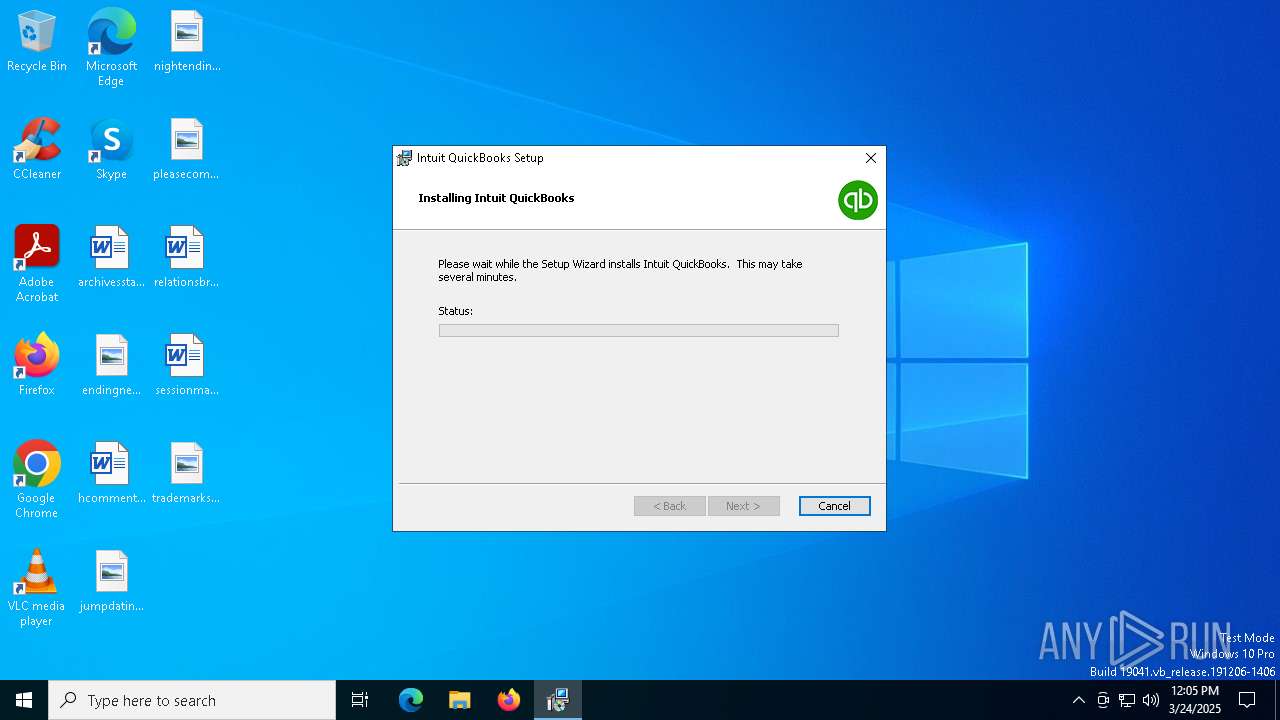
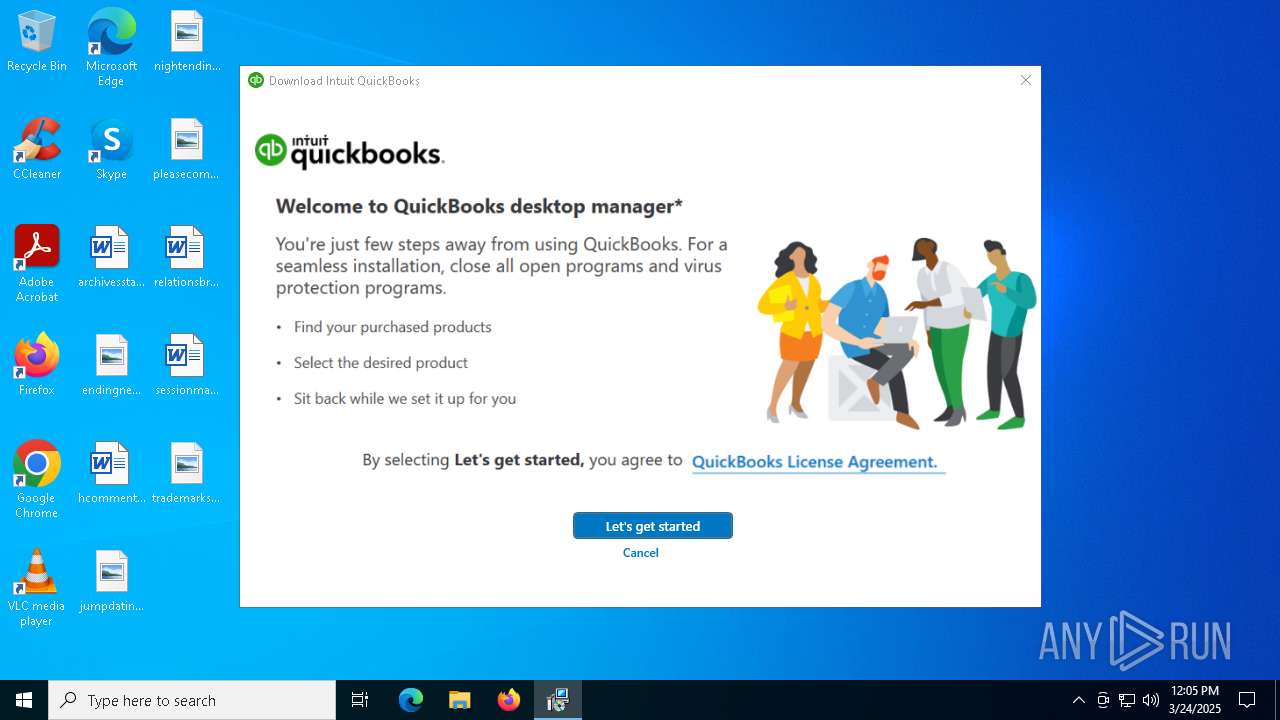
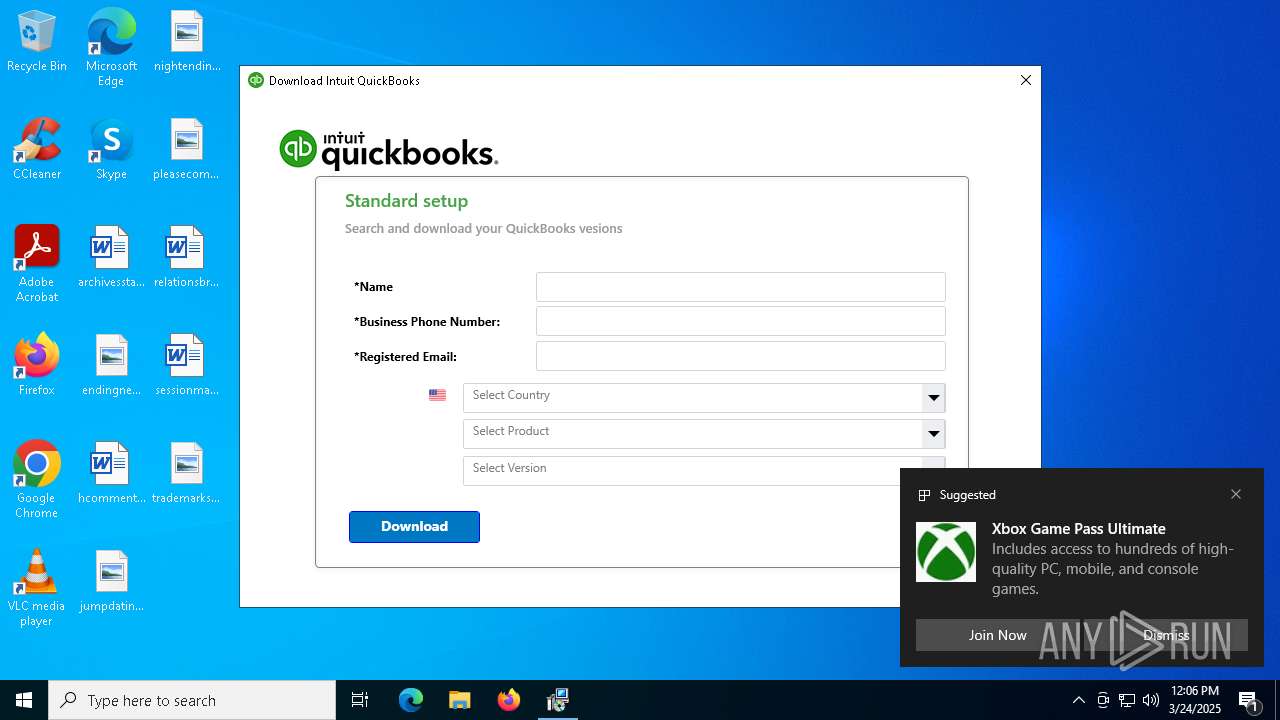
| File name: | 80439D9D6CF0D6C2620C8D0B66E509F07D0DFCAF.msi |
| Full analysis: | https://app.any.run/tasks/8201cc8b-3f81-4872-a803-f6732c44acc0 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 12:05:06 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Last Printed: Fri Dec 11 11:47:44 2009, Create Time/Date: Fri Dec 11 11:47:44 2009, Last Saved Time/Date: Fri Sep 18 14:06:51 2020, Security: 0, Code page: 1252, Revision Number: {1627FCDA-305F-412F-8D6E-88FFAD73B73A}, Number of Words: 2, Subject: Intuit QuickBooks, Author: Intuit Inc., Name of Creating Application: Intuit QuickBooks, Template: ;1033, Comments: This installer database contains the logic and data required to install Intuit QuickBooks., Title: Installation Database, Keywords: Installer, MSI, Database, Number of Pages: 200 |
| MD5: | B64339E95F7C15DD2D96EA11279BD5F0 |
| SHA1: | 1EE15A3522C78116FC87BFA7F5ECD9B6DC7FA5A8 |
| SHA256: | 7E13B603FED156B652D8AE2C19688CF1259C7E547F022708C2B74492EAF7D4A8 |
| SSDEEP: | 98304:AXoQ4svwET/p2zYPRDXtjVq/owoCtdenRg0OcyQfTi3KTl5sGjOX9nb1D1kBpXGF:32 |
MALICIOUS
Creates a new scheduled task via Registry
- msiexec.exe (PID: 7920)
Create files in the Startup directory
- msiexec.exe (PID: 5176)
SUSPICIOUS
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6988)
- MSI22A4.tmp (PID: 8080)
- QuickBooksDownloder.exe (PID: 7208)
Adds/modifies Windows certificates
- msiexec.exe (PID: 2236)
Executes as Windows Service
- VSSVC.exe (PID: 7504)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 5176)
Detects AdvancedInstaller (YARA)
- msiexec.exe (PID: 5176)
Creates FileSystem object to access computer's file system (SCRIPT)
- msiexec.exe (PID: 7920)
Likely accesses (executes) a file from the Public directory
- MSI22A4.tmp (PID: 8080)
- QuickBooksDownloder.exe (PID: 7208)
INFO
Reads security settings of Internet Explorer
- msiexec.exe (PID: 4448)
- msiexec.exe (PID: 2236)
- BackgroundTransferHost.exe (PID: 7924)
- BackgroundTransferHost.exe (PID: 7716)
- BackgroundTransferHost.exe (PID: 8092)
- BackgroundTransferHost.exe (PID: 5576)
- BackgroundTransferHost.exe (PID: 4024)
Reads the software policy settings
- msiexec.exe (PID: 4448)
- msiexec.exe (PID: 2236)
- msiexec.exe (PID: 5176)
Creates files or folders in the user directory
- msiexec.exe (PID: 4448)
- BackgroundTransferHost.exe (PID: 7924)
Checks supported languages
- msiexec.exe (PID: 5176)
- msiexec.exe (PID: 6988)
- msiexec.exe (PID: 4180)
- msiexec.exe (PID: 7920)
- MSI22A4.tmp (PID: 8080)
- QuickBooksDownloder.exe (PID: 7208)
- ShellExperienceHost.exe (PID: 8008)
Reads the computer name
- msiexec.exe (PID: 5176)
- msiexec.exe (PID: 6988)
- msiexec.exe (PID: 4180)
- MSI22A4.tmp (PID: 8080)
Executable content was dropped or overwritten
- msiexec.exe (PID: 4448)
- msiexec.exe (PID: 2236)
- msiexec.exe (PID: 5176)
The sample compiled with english language support
- msiexec.exe (PID: 4448)
- msiexec.exe (PID: 2236)
- msiexec.exe (PID: 5176)
Reads Environment values
- msiexec.exe (PID: 6988)
- msiexec.exe (PID: 4180)
Application launched itself
- msiexec.exe (PID: 6988)
Process checks computer location settings
- msiexec.exe (PID: 6988)
- MSI22A4.tmp (PID: 8080)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 7924)
- QuickBooksDownloder.exe (PID: 7208)
Manages system restore points
- SrTasks.exe (PID: 7732)
Reads the machine GUID from the registry
- msiexec.exe (PID: 5176)
- msiexec.exe (PID: 7920)
- QuickBooksDownloder.exe (PID: 7208)
Starts application with an unusual extension
- msiexec.exe (PID: 5176)
Disables trace logs
- QuickBooksDownloder.exe (PID: 7208)
Autorun file from Startup directory
- msiexec.exe (PID: 5176)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (78.4) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (8.8) |
| .msp | | | Windows Installer Patch (7.3) |
| .xls | | | Microsoft Excel sheet (4.2) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| LastPrinted: | 2009:12:11 11:47:44 |
|---|---|
| CreateDate: | 2009:12:11 11:47:44 |
| ModifyDate: | 2020:09:18 14:06:51 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {1627FCDA-305F-412F-8D6E-88FFAD73B73A} |
| Words: | 2 |
| Subject: | Intuit QuickBooks |
| Author: | Intuit Inc. |
| LastModifiedBy: | - |
| Software: | Intuit QuickBooks |
| Template: | ;1033 |
| Comments: | This installer database contains the logic and data required to install Intuit QuickBooks. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| Pages: | 200 |
Total processes
159
Monitored processes
21
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2236 | "C:\WINDOWS\SysWOW64\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\80439D9D6CF0D6C2620C8D0B66E509F07D0DFCAF.msi" | C:\Windows\SysWOW64\msiexec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4024 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4180 | C:\Windows\syswow64\MsiExec.exe -Embedding FCDC7CD69C48C6D4CF58F82B640DFDA1 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4448 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\80439D9D6CF0D6C2620C8D0B66E509F07D0DFCAF.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 1602 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5124 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5176 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5576 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6272 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6988 | C:\Windows\syswow64\MsiExec.exe -Embedding DFBB4CCF02B47011C02AA28848B30367 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7208 | "C:\Users\Public\Documents\Windows\QuickBooksDownloder.exe" | C:\Users\Public\Documents\Windows\QuickBooksDownloder.exe | MSI22A4.tmp | ||||||||||||
User: admin Integrity Level: HIGH Description: QuickBooksDownloder Version: 31.0.4006.3103 Modules
| |||||||||||||||
Total events
20 087
Read events
19 831
Write events
239
Delete events
17
Modification events
| (PID) Process: | (2236) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{618736E0-3C3D-11CF-810C-00AA00389B71}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (2236) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{618736E0-3C3D-11CF-810C-00AA00389B71}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (2236) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Volatile\00\MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{03022430-ABC4-11D0-BDE2-00AA001A1953}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (2236) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Volatile\00\MACHINE\SOFTWARE\Classes\Interface\{03022430-ABC4-11D0-BDE2-00AA001A1953}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (2236) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | B7AB3308D1EA4477BA1480125A6FBDA936490CBB |
Value: | |||
| (PID) Process: | (2236) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\B7AB3308D1EA4477BA1480125A6FBDA936490CBB |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000866912C070F1ECACACC2D5BCA55BA129140000000100000014000000DD040907A2F57A7D5253129295EE3880250DA65909000000010000004C000000304A06082B0601050507030206082B06010505070303060A2B0601040182370A030C060A2B0601040182370A030406082B0601050507030406082B0601050507030106082B06010505070308190000000100000010000000787D09F953C59978ECD8D6E44B38E24F030000000100000014000000B7AB3308D1EA4477BA1480125A6FBDA936490CBB0F0000000100000020000000489FF6233F3D3C5DA77604BE230745657FE488CB05257DA551BFD64C1F179E720B0000000100000052000000530053004C002E0063006F006D00200052006F006F0074002000430065007200740069006600690063006100740069006F006E00200041007500740068006F0072006900740079002000520053004100000062000000010000002000000085666A562EE0BE5CE925C1D8890A6F76A87EC16D4D7D5F29EA7419CF20123B691D00000001000000100000000D48EE33D7F1AF8F4B002527F82A344A2000000001000000E1050000308205DD308203C5A00302010202087B2C9BD316803299300D06092A864886F70D01010B0500307C310B3009060355040613025553310E300C06035504080C0554657861733110300E06035504070C07486F7573746F6E31183016060355040A0C0F53534C20436F72706F726174696F6E3131302F06035504030C2853534C2E636F6D20526F6F742043657274696669636174696F6E20417574686F7269747920525341301E170D3136303231323137333933395A170D3431303231323137333933395A307C310B3009060355040613025553310E300C06035504080C0554657861733110300E06035504070C07486F7573746F6E31183016060355040A0C0F53534C20436F72706F726174696F6E3131302F06035504030C2853534C2E636F6D20526F6F742043657274696669636174696F6E20417574686F726974792052534130820222300D06092A864886F70D01010105000382020F003082020A0282020100F90FDDA32B7DCBD02AFEEC6785A6E72E1BBA77E1E3F5AFA4ECFA4A5D91C457476B18776B76F2FD93E43D0FC2169E0B66C356949E178385CE56EFF216FD0062F5220954E865174E41B9E04F4697AA1BC8B86E625E69B15FDB2A027EFC6CCAF341D8EDD0E8FC3F6148EDB003141D100E4B19E0BB4EEC8665FF36F35E67020B9D865561FD7A38EDFEE21900B76FA1506275743CA0FAC82592B46E7A22C7F81EA1E3B2DD9131AB2B1D04FFA54A0437E985A4332BFDE2D655347C19A44A68C7B2A8D3B7CAA19388EBC197BC8CF91DD922842474C7043D6AA92993CCEBB85BE1FE5F25AA3458C8C123549D1B9811C3389C7E3D866CA50F40867C02F45C024F28CBAE719F0F3AC833FE112535EAFCBAC5603DD97C18D5B2A9D37578037222CA3AC31FEF2CE52EA9FA9E2CB65146FDAF03D6EA6068EA8516366B85E91EC0B3DDC424DC802A81416D943EC8E0C98141009E5EBF7FC50898A2182C4240B3F96F38274B4E80F43D8147E0887CEA1CCEB5755C512E1C2B7F1A7228E700B5D174C6D7E49FAD0793B6533535FC37E4C3F65D16BE2173DE920AF8A0636ABC96926A3EF8BC65559BDEF50D892604FC251AA62569CBC26DCA7CE2595F97ACEBEF2EC8BCD71B593C2BCCF219C8936B276319CFFCE926F8CA719B7F93FE3467844E99EBFCB378093370BA66A676ED1B73EB1AA50DC422132094560A4E2C6C4EB1FDCF9C09BAA233ED870203010001A3633061301D0603551D0E04160414DD040907A2F57A7D5253129295EE3880250DA659300F0603551D130101FF040530030101FF301F0603551D23041830168014DD040907A2F57A7D5253129295EE3880250DA659300E0603551D0F0101FF040403020186300D06092A864886F70D01010B050003820201002018119429FB269D1C1E1E7061F19572937124AD6893588E32AF1BB37003FC252B7485903D786AF4B98BA5973BB51891BB1EA7F9405B91F95599AF1E11D05C1DA766E3B194070C3239A6EA1BB079D81D9C7044E38ADDC4F9951F8A38433F0185A547A73D46B2BCE52268F77B9CD82C3E0A21C82D33ACBFC581993174C17571C5BEB1F02345F49D6BFC19639DA3BC04C6180B25BB53890FB38050DE45EE447FAB94786498D3F628DD87D8706574FB0EB913EBA70F61A93296CCDEBBED634C18BBA940F7A0546E2088717518EA7AB43472E02327775CB690EA862540ABEF330FCB9F82BEA220FBF6B52D1AE6C285B1740FFBC86502A4520147DD4922C1BFD8EB6BAC7EDEEC633315B723088FC60F8D415ADD8EC5B98FE5453F78DBBAD21B40B1FE714D3FE081A2BA5EB4EC15E093DD081F7EE155990B21DE939E0AFBE6A349BD3630FEE777B2A07597B52D8188176520F7DA90009FC952CC32CA357CF53D0FD82BD7F5266CC906349616EA70591A3279790BB6887F0F52483DBF6CD8A2442ED14EB77258D3891395FE44ABF8D78B1B6E9CBC2CA05BD56A00AF5F37E1D5FA100B989C86E7268FCEF0EC6E8A570B80E34EB2C0A0636190BA556837746AB692DB9FA18622B665270EECB69F4260E467C2B5DA410BC4D38B611BBCFA1F912BD744075EBA29ACD9C5E9EF53485AEB80F1285821CDB00655FB273F539070A9041E5727B9 | |||
| (PID) Process: | (2236) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\B7AB3308D1EA4477BA1480125A6FBDA936490CBB |
| Operation: | write | Name: | Blob |
Value: 5C0000000100000004000000001000001D00000001000000100000000D48EE33D7F1AF8F4B002527F82A344A62000000010000002000000085666A562EE0BE5CE925C1D8890A6F76A87EC16D4D7D5F29EA7419CF20123B690B0000000100000052000000530053004C002E0063006F006D00200052006F006F0074002000430065007200740069006600690063006100740069006F006E00200041007500740068006F007200690074007900200052005300410000000F0000000100000020000000489FF6233F3D3C5DA77604BE230745657FE488CB05257DA551BFD64C1F179E72030000000100000014000000B7AB3308D1EA4477BA1480125A6FBDA936490CBB190000000100000010000000787D09F953C59978ECD8D6E44B38E24F09000000010000004C000000304A06082B0601050507030206082B06010505070303060A2B0601040182370A030C060A2B0601040182370A030406082B0601050507030406082B0601050507030106082B06010505070308140000000100000014000000DD040907A2F57A7D5253129295EE3880250DA659040000000100000010000000866912C070F1ECACACC2D5BCA55BA1292000000001000000E1050000308205DD308203C5A00302010202087B2C9BD316803299300D06092A864886F70D01010B0500307C310B3009060355040613025553310E300C06035504080C0554657861733110300E06035504070C07486F7573746F6E31183016060355040A0C0F53534C20436F72706F726174696F6E3131302F06035504030C2853534C2E636F6D20526F6F742043657274696669636174696F6E20417574686F7269747920525341301E170D3136303231323137333933395A170D3431303231323137333933395A307C310B3009060355040613025553310E300C06035504080C0554657861733110300E06035504070C07486F7573746F6E31183016060355040A0C0F53534C20436F72706F726174696F6E3131302F06035504030C2853534C2E636F6D20526F6F742043657274696669636174696F6E20417574686F726974792052534130820222300D06092A864886F70D01010105000382020F003082020A0282020100F90FDDA32B7DCBD02AFEEC6785A6E72E1BBA77E1E3F5AFA4ECFA4A5D91C457476B18776B76F2FD93E43D0FC2169E0B66C356949E178385CE56EFF216FD0062F5220954E865174E41B9E04F4697AA1BC8B86E625E69B15FDB2A027EFC6CCAF341D8EDD0E8FC3F6148EDB003141D100E4B19E0BB4EEC8665FF36F35E67020B9D865561FD7A38EDFEE21900B76FA1506275743CA0FAC82592B46E7A22C7F81EA1E3B2DD9131AB2B1D04FFA54A0437E985A4332BFDE2D655347C19A44A68C7B2A8D3B7CAA19388EBC197BC8CF91DD922842474C7043D6AA92993CCEBB85BE1FE5F25AA3458C8C123549D1B9811C3389C7E3D866CA50F40867C02F45C024F28CBAE719F0F3AC833FE112535EAFCBAC5603DD97C18D5B2A9D37578037222CA3AC31FEF2CE52EA9FA9E2CB65146FDAF03D6EA6068EA8516366B85E91EC0B3DDC424DC802A81416D943EC8E0C98141009E5EBF7FC50898A2182C4240B3F96F38274B4E80F43D8147E0887CEA1CCEB5755C512E1C2B7F1A7228E700B5D174C6D7E49FAD0793B6533535FC37E4C3F65D16BE2173DE920AF8A0636ABC96926A3EF8BC65559BDEF50D892604FC251AA62569CBC26DCA7CE2595F97ACEBEF2EC8BCD71B593C2BCCF219C8936B276319CFFCE926F8CA719B7F93FE3467844E99EBFCB378093370BA66A676ED1B73EB1AA50DC422132094560A4E2C6C4EB1FDCF9C09BAA233ED870203010001A3633061301D0603551D0E04160414DD040907A2F57A7D5253129295EE3880250DA659300F0603551D130101FF040530030101FF301F0603551D23041830168014DD040907A2F57A7D5253129295EE3880250DA659300E0603551D0F0101FF040403020186300D06092A864886F70D01010B050003820201002018119429FB269D1C1E1E7061F19572937124AD6893588E32AF1BB37003FC252B7485903D786AF4B98BA5973BB51891BB1EA7F9405B91F95599AF1E11D05C1DA766E3B194070C3239A6EA1BB079D81D9C7044E38ADDC4F9951F8A38433F0185A547A73D46B2BCE52268F77B9CD82C3E0A21C82D33ACBFC581993174C17571C5BEB1F02345F49D6BFC19639DA3BC04C6180B25BB53890FB38050DE45EE447FAB94786498D3F628DD87D8706574FB0EB913EBA70F61A93296CCDEBBED634C18BBA940F7A0546E2088717518EA7AB43472E02327775CB690EA862540ABEF330FCB9F82BEA220FBF6B52D1AE6C285B1740FFBC86502A4520147DD4922C1BFD8EB6BAC7EDEEC633315B723088FC60F8D415ADD8EC5B98FE5453F78DBBAD21B40B1FE714D3FE081A2BA5EB4EC15E093DD081F7EE155990B21DE939E0AFBE6A349BD3630FEE777B2A07597B52D8188176520F7DA90009FC952CC32CA357CF53D0FD82BD7F5266CC906349616EA70591A3279790BB6887F0F52483DBF6CD8A2442ED14EB77258D3891395FE44ABF8D78B1B6E9CBC2CA05BD56A00AF5F37E1D5FA100B989C86E7268FCEF0EC6E8A570B80E34EB2C0A0636190BA556837746AB692DB9FA18622B665270EECB69F4260E467C2B5DA410BC4D38B611BBCFA1F912BD744075EBA29ACD9C5E9EF53485AEB80F1285821CDB00655FB273F539070A9041E5727B9 | |||
| (PID) Process: | (2236) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | 07E032E020B72C3F192F0628A2593A19A70F069E |
Value: | |||
| (PID) Process: | (2236) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\07E032E020B72C3F192F0628A2593A19A70F069E |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000D5E98140C51869FC462C8975620FAA781400000001000000140000000876CDCB07FF24F6C5CDEDBB90BCE284374675F70B0000000100000034000000430065007200740075006D002000540072007500730074006500640020004E006500740077006F0072006B00200043004100000053000000010000006500000030633021060B2A84680186F6770205010130123010060A2B0601040182373C0101030200C03021060B2A84680186F6770205010730123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C00F0000000100000014000000A8569CCD21EF9CC5737C7A12DF608C2CBC545DF103000000010000001400000007E032E020B72C3F192F0628A2593A19A70F069E1900000001000000100000001F7E750B566B128AC0B8D6576D2A70A5090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703086200000001000000200000005C58468D55F58E497E743982D2B50010B6D165374ACF83A7D4A32DB768C4408E1D0000000100000010000000E3F9AF952C6DF2AAA41706A77A44C2032000000001000000BF030000308203BB308202A3A00302010202030444C0300D06092A864886F70D0101050500307E310B300906035504061302504C31223020060355040A1319556E697A65746F20546563686E6F6C6F6769657320532E412E31273025060355040B131E43657274756D2043657274696669636174696F6E20417574686F72697479312230200603550403131943657274756D2054727573746564204E6574776F726B204341301E170D3038313032323132303733375A170D3239313233313132303733375A307E310B300906035504061302504C31223020060355040A1319556E697A65746F20546563686E6F6C6F6769657320532E412E31273025060355040B131E43657274756D2043657274696669636174696F6E20417574686F72697479312230200603550403131943657274756D2054727573746564204E6574776F726B20434130820122300D06092A864886F70D01010105000382010F003082010A0282010100E3FB7DA372BAC2F0C91487F56B014EE16E4007BA6D275D7FF75B2DB35AC7515FABA432A66187B66E0F86D2300297F8D76957A118395D6A6479C60159AC3C314A387CD204D24B28E8205F3B07A2CC4D73DBF3AE4FC756D55AA79689FAF3AB68D423865927CF0927BCAC6E72831C3072DFE0A2E9D2E1747519BD2A9E7B1554041BD74339AD5528C5E21ABBF4C0E4AE384933CC76859F3945D2A49EF2128C51F87CE42D7FF5AC5FEB169FB12DD1BACC9142774C25C990386FDBF0CCFB8E1E97593ED5604EE60528ED4979134BBA48DB2FF972D339CAFE1FD83472F5B440CF3101C3ECDE112D175D1FB850D15E19A769DE073328CA5095F9A754CB54865045A9F9490203010001A3423040300F0603551D130101FF040530030101FF301D0603551D0E041604140876CDCB07FF24F6C5CDEDBB90BCE284374675F7300E0603551D0F0101FF040403020106300D06092A864886F70D01010505000382010100A6A8AD22CE013DA6A3FF62D0489D8B5E72B07844E3DC1CAF09FD2348FABD2AC4B95504B510A38D27DE0B8263D0EEDE0C3779415B22B2B09A415CA670E0D4D077CB23D300E06C562FE1690D0DD9AABF218150D906A5A8FF9537D0AAFEE2B3F5992D45848AE54209D774022FF789D899E9BC27D4478DBA0D461C77CF14A41CB9A431C49C28740334FF331926A5E90D74B73E97C676E82796A366DDE1AEF2415BCA9856837370E4861AD23141BA2FBE2D135A766F4EE84E810E3F5B0322A012BE6658114ACB03C4B42A2A2D9617E03954BC48D376279D9A2D06A6C9EC39D2ABDB9F9A0B27023529B14095E7F9E89C55881946D6B734F57ECE399AD938F151F74F2C | |||
| (PID) Process: | (2236) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\07E032E020B72C3F192F0628A2593A19A70F069E |
| Operation: | write | Name: | Blob |
Value: 5C0000000100000004000000000800001D0000000100000010000000E3F9AF952C6DF2AAA41706A77A44C2036200000001000000200000005C58468D55F58E497E743982D2B50010B6D165374ACF83A7D4A32DB768C4408E090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703081900000001000000100000001F7E750B566B128AC0B8D6576D2A70A503000000010000001400000007E032E020B72C3F192F0628A2593A19A70F069E0F0000000100000014000000A8569CCD21EF9CC5737C7A12DF608C2CBC545DF153000000010000006500000030633021060B2A84680186F6770205010130123010060A2B0601040182373C0101030200C03021060B2A84680186F6770205010730123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C00B0000000100000034000000430065007200740075006D002000540072007500730074006500640020004E006500740077006F0072006B0020004300410000001400000001000000140000000876CDCB07FF24F6C5CDEDBB90BCE284374675F7040000000100000010000000D5E98140C51869FC462C8975620FAA782000000001000000BF030000308203BB308202A3A00302010202030444C0300D06092A864886F70D0101050500307E310B300906035504061302504C31223020060355040A1319556E697A65746F20546563686E6F6C6F6769657320532E412E31273025060355040B131E43657274756D2043657274696669636174696F6E20417574686F72697479312230200603550403131943657274756D2054727573746564204E6574776F726B204341301E170D3038313032323132303733375A170D3239313233313132303733375A307E310B300906035504061302504C31223020060355040A1319556E697A65746F20546563686E6F6C6F6769657320532E412E31273025060355040B131E43657274756D2043657274696669636174696F6E20417574686F72697479312230200603550403131943657274756D2054727573746564204E6574776F726B20434130820122300D06092A864886F70D01010105000382010F003082010A0282010100E3FB7DA372BAC2F0C91487F56B014EE16E4007BA6D275D7FF75B2DB35AC7515FABA432A66187B66E0F86D2300297F8D76957A118395D6A6479C60159AC3C314A387CD204D24B28E8205F3B07A2CC4D73DBF3AE4FC756D55AA79689FAF3AB68D423865927CF0927BCAC6E72831C3072DFE0A2E9D2E1747519BD2A9E7B1554041BD74339AD5528C5E21ABBF4C0E4AE384933CC76859F3945D2A49EF2128C51F87CE42D7FF5AC5FEB169FB12DD1BACC9142774C25C990386FDBF0CCFB8E1E97593ED5604EE60528ED4979134BBA48DB2FF972D339CAFE1FD83472F5B440CF3101C3ECDE112D175D1FB850D15E19A769DE073328CA5095F9A754CB54865045A9F9490203010001A3423040300F0603551D130101FF040530030101FF301D0603551D0E041604140876CDCB07FF24F6C5CDEDBB90BCE284374675F7300E0603551D0F0101FF040403020106300D06092A864886F70D01010505000382010100A6A8AD22CE013DA6A3FF62D0489D8B5E72B07844E3DC1CAF09FD2348FABD2AC4B95504B510A38D27DE0B8263D0EEDE0C3779415B22B2B09A415CA670E0D4D077CB23D300E06C562FE1690D0DD9AABF218150D906A5A8FF9537D0AAFEE2B3F5992D45848AE54209D774022FF789D899E9BC27D4478DBA0D461C77CF14A41CB9A431C49C28740334FF331926A5E90D74B73E97C676E82796A366DDE1AEF2415BCA9856837370E4861AD23141BA2FBE2D135A766F4EE84E810E3F5B0322A012BE6658114ACB03C4B42A2A2D9617E03954BC48D376279D9A2D06A6C9EC39D2ABDB9F9A0B27023529B14095E7F9E89C55881946D6B734F57ECE399AD938F151F74F2C | |||
Executable files
26
Suspicious files
25
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7924 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\61fa03a2-317b-48bc-8121-44feb8051d7c.down_data | — | |
MD5:— | SHA256:— | |||
| 4448 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\54C62B182F5BF07FA8427C07B0A3AAF8_4DBBCB40FA282C06F1543D887F4F4DCC | binary | |
MD5:38BCB3A0EC43CF70F4F2CB79102EF18C | SHA256:A3B7C4EBADC41994961D422C6637842F4663ED0200A0C703A82347180C3F2217 | |||
| 4448 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D682FDDA10064185EC8111DC39DBA8EC | binary | |
MD5:ED3D91B7077CB63CC4A47D4F6795C06D | SHA256:942EB906D8D76B6115A36C688870AB7E59A9252E04AFB599BBA38108DEBBED44 | |||
| 4448 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\94D451DDCFFF94F1A6B8406468FA3558_E4A7C6A10F816F002B00DE3B58B7E44E | binary | |
MD5:FA6628EC08DD84FB62A6820F228F5434 | SHA256:58C2B75D887DBA6D507EB689A9DA26A3999D86B760922474BAF23F6A02B76F35 | |||
| 4448 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIB902.tmp | executable | |
MD5:CFAB78AC0D042A1D8AD7085A94328EF6 | SHA256:17B10DF05B4B92735B673914FE2BF0C0D7BBDA5B4A8F9A7FC81A0EFAA4380168 | |||
| 4448 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\971E98FB192CF25D1FBA2923458B97CB | binary | |
MD5:9A83B71E004DE6D98B7B9D36F72A9599 | SHA256:7A2FF419B4F5B8CE2658B381830AABBB98CEC9A352C94F7F1BA716ECFE25FA8A | |||
| 5176 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 4448 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D682FDDA10064185EC8111DC39DBA8EC | binary | |
MD5:443F89CF09D2BBDB3B5934FAE26222CB | SHA256:F741A35A49AB418F78441DDDB9FC150D394071D24A3E26446A05730980D5498C | |||
| 4448 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\94D451DDCFFF94F1A6B8406468FA3558_E4A7C6A10F816F002B00DE3B58B7E44E | binary | |
MD5:A9B83AF7A2676C328B90292570EBE4F7 | SHA256:2F5D9ACA00F37E44C75DD18182F5BFA54B20D25CDE7E2685932A109B300E7771 | |||
| 4448 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIB855.tmp | executable | |
MD5:CFAB78AC0D042A1D8AD7085A94328EF6 | SHA256:17B10DF05B4B92735B673914FE2BF0C0D7BBDA5B4A8F9A7FC81A0EFAA4380168 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
36
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4448 | msiexec.exe | GET | 200 | 18.66.147.75:80 | http://ocsps.ssl.com/MEkwRzBFMEMwQTAJBgUrDgMCGgUABBQMDtATfnJO6JAXDQoHl8pAaJdhTQQU3QQJB6L1en1SUxKSle44gCUNplkCCGQzUdPHOJ8I | unknown | — | — | whitelisted |
4448 | msiexec.exe | GET | 200 | 23.50.131.150:80 | http://sslcom.ocsp-certum.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTYOkzrrCGQj08njZXbUQQpkoUmuQQUCHbNywf%2FJPbFze27kLzihDdGdfcCEQDkJwSV9oyR1tDse0lOpN8c | unknown | — | — | whitelisted |
4448 | msiexec.exe | GET | 200 | 18.66.147.75:80 | http://ocsps.ssl.com/MEkwRzBFMEMwQTAJBgUrDgMCGgUABBQMDtATfnJO6JAXDQoHl8pAaJdhTQQU3QQJB6L1en1SUxKSle44gCUNplkCCGQzUdPHOJ8I | unknown | — | — | whitelisted |
4448 | msiexec.exe | GET | 200 | 18.244.18.60:80 | http://crls.ssl.com/ssl.com-rsa-RootCA.crl | unknown | — | — | whitelisted |
4448 | msiexec.exe | GET | 200 | 18.244.18.60:80 | http://crls.ssl.com/SSLcom-SubCA-CodeSigning-RSA-4096-R1.crl | unknown | — | — | whitelisted |
2136 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7924 | BackgroundTransferHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4448 | msiexec.exe | 23.50.131.150:80 | sslcom.ocsp-certum.com | Akamai International B.V. | DE | whitelisted |
4448 | msiexec.exe | 18.66.147.75:80 | ocsps.ssl.com | AMAZON-02 | US | whitelisted |
4448 | msiexec.exe | 18.244.18.60:80 | crls.ssl.com | — | US | whitelisted |
3216 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.22:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
sslcom.ocsp-certum.com |
| whitelisted |
ocsps.ssl.com |
| whitelisted |
crls.ssl.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |