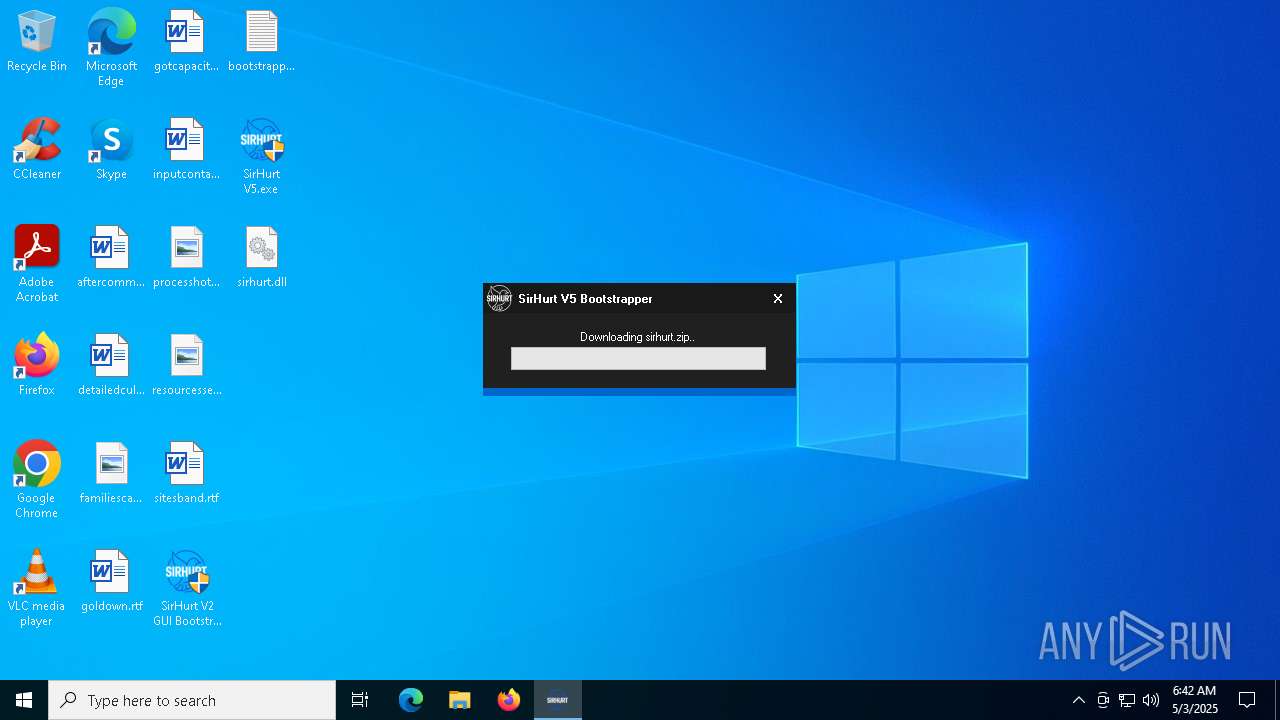
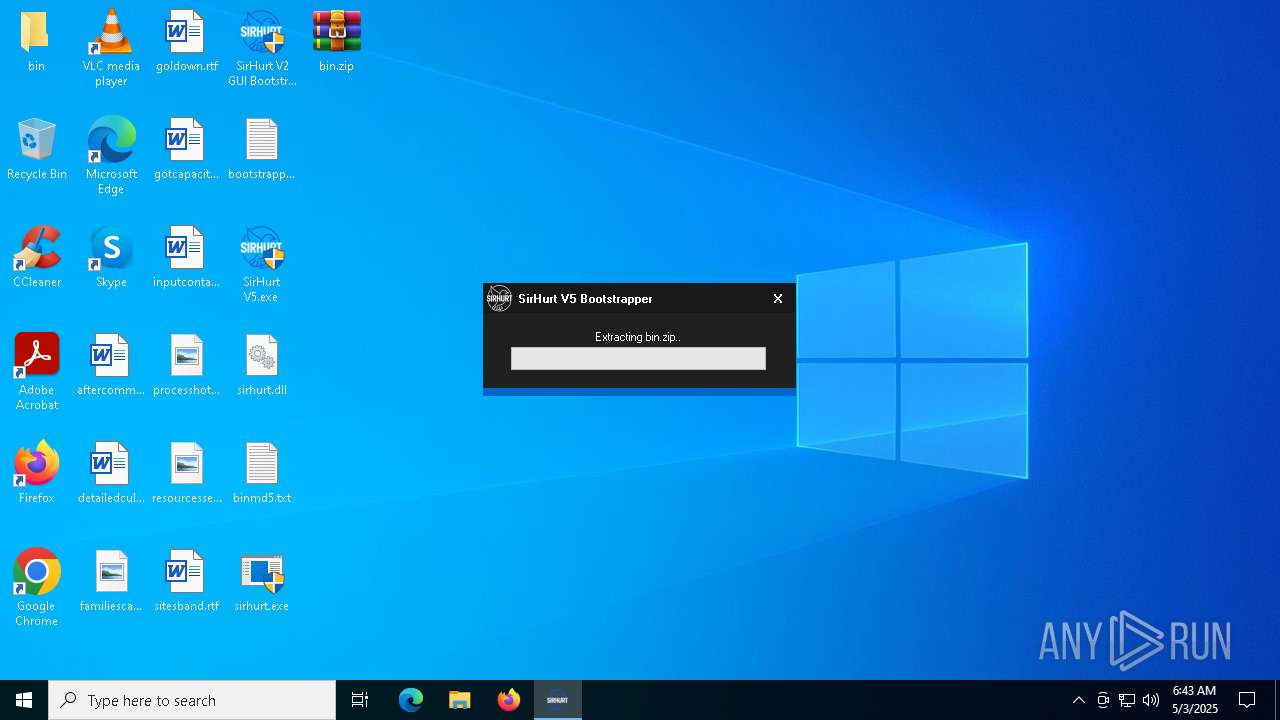
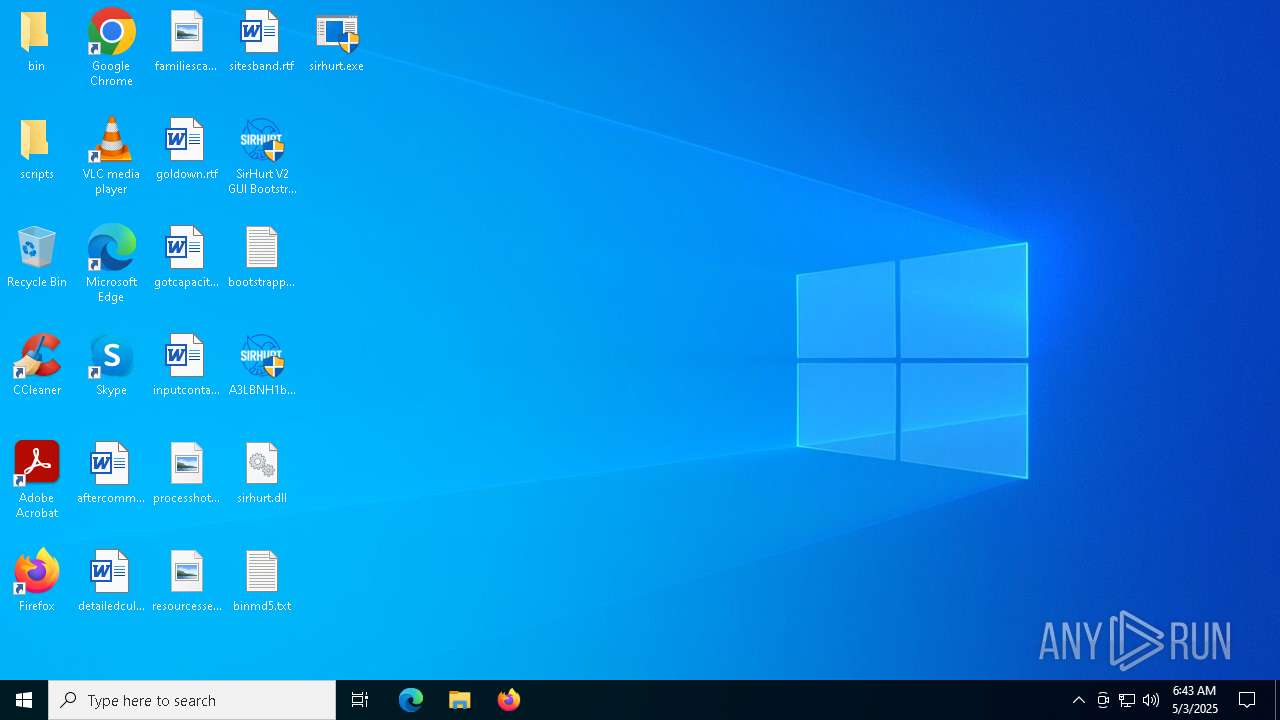
| File name: | SirHurt V2 GUI Bootstrapper.exe |
| Full analysis: | https://app.any.run/tasks/0589fd9b-d12e-476b-af4c-9b1274d1a3b7 |
| Verdict: | Malicious activity |
| Analysis date: | May 03, 2025, 06:42:09 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64 Mono/.Net assembly, for MS Windows, 2 sections |
| MD5: | EB0238C75323D39C4AA3D82A0B480657 |
| SHA1: | 4E37C6515A180CDAA304BC21E45AE10BF73544CB |
| SHA256: | 7E0B74459E898EAB08492209812F9D1B2036055FE97880B1B4386E31F6638505 |
| SSDEEP: | 49152:M/WdvQwnD51SzWiGsfEAy0g/rRfBnJxHocKVK90fSKz1WzKcDxuCU514NXbFzlNl:xdvBnD51S4sfEIg/rXflB2bz14buCU5j |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the date of Windows installation
- SirHurt V2 GUI Bootstrapper.exe (PID: 3884)
Reads security settings of Internet Explorer
- SirHurt V2 GUI Bootstrapper.exe (PID: 3884)
- SirHurt V5.exe (PID: 6676)
- SirHurt V5.exe (PID: 5960)
Process drops legitimate windows executable
- SirHurt V2 GUI Bootstrapper.exe (PID: 3884)
Executable content was dropped or overwritten
- SirHurt V2 GUI Bootstrapper.exe (PID: 3884)
- SirHurt V5.exe (PID: 6676)
- SirHurt V2 GUI Bootstrapper.exe (PID: 3016)
- SirHurt V5.exe (PID: 5960)
Reads the BIOS version
- SirHurt V5.exe (PID: 6676)
- SirHurt V5.exe (PID: 5960)
Executes application which crashes
- SirHurt V5.exe (PID: 6676)
- SirHurt V2 GUI Bootstrapper.exe (PID: 3016)
The process checks if it is being run in the virtual environment
- SirHurt V5.exe (PID: 5960)
INFO
Disables trace logs
- SirHurt V2 GUI Bootstrapper.exe (PID: 3884)
- SirHurt V5.exe (PID: 6676)
- SirHurt V2 GUI Bootstrapper.exe (PID: 3016)
- SirHurt V5.exe (PID: 5960)
Checks supported languages
- SirHurt V2 GUI Bootstrapper.exe (PID: 3884)
- SirHurt V5.exe (PID: 6676)
- CefSharp.BrowserSubprocess.exe (PID: 1168)
- CefSharp.BrowserSubprocess.exe (PID: 7156)
- CefSharp.BrowserSubprocess.exe (PID: 6828)
- CefSharp.BrowserSubprocess.exe (PID: 3124)
- CefSharp.BrowserSubprocess.exe (PID: 6960)
- SirHurt V2 GUI Bootstrapper.exe (PID: 3016)
- SirHurt V5.exe (PID: 5960)
- CefSharp.BrowserSubprocess.exe (PID: 6244)
- CefSharp.BrowserSubprocess.exe (PID: 1348)
- CefSharp.BrowserSubprocess.exe (PID: 4528)
- CefSharp.BrowserSubprocess.exe (PID: 672)
- CefSharp.BrowserSubprocess.exe (PID: 6372)
- CefSharp.BrowserSubprocess.exe (PID: 2568)
The sample compiled with english language support
- SirHurt V2 GUI Bootstrapper.exe (PID: 3884)
Reads the computer name
- SirHurt V2 GUI Bootstrapper.exe (PID: 3884)
- SirHurt V5.exe (PID: 6676)
- CefSharp.BrowserSubprocess.exe (PID: 1168)
- CefSharp.BrowserSubprocess.exe (PID: 7156)
- CefSharp.BrowserSubprocess.exe (PID: 6828)
- CefSharp.BrowserSubprocess.exe (PID: 3124)
- SirHurt V2 GUI Bootstrapper.exe (PID: 3016)
- CefSharp.BrowserSubprocess.exe (PID: 6960)
- SirHurt V5.exe (PID: 5960)
- CefSharp.BrowserSubprocess.exe (PID: 6244)
- CefSharp.BrowserSubprocess.exe (PID: 1348)
- CefSharp.BrowserSubprocess.exe (PID: 4528)
- CefSharp.BrowserSubprocess.exe (PID: 672)
- CefSharp.BrowserSubprocess.exe (PID: 6372)
- CefSharp.BrowserSubprocess.exe (PID: 2568)
Reads Environment values
- SirHurt V2 GUI Bootstrapper.exe (PID: 3884)
- SirHurt V2 GUI Bootstrapper.exe (PID: 3016)
Reads the machine GUID from the registry
- SirHurt V2 GUI Bootstrapper.exe (PID: 3884)
- SirHurt V5.exe (PID: 6676)
- CefSharp.BrowserSubprocess.exe (PID: 7156)
- CefSharp.BrowserSubprocess.exe (PID: 1168)
- CefSharp.BrowserSubprocess.exe (PID: 6828)
- CefSharp.BrowserSubprocess.exe (PID: 3124)
- SirHurt V2 GUI Bootstrapper.exe (PID: 3016)
- CefSharp.BrowserSubprocess.exe (PID: 6960)
- SirHurt V5.exe (PID: 5960)
- CefSharp.BrowserSubprocess.exe (PID: 4528)
- CefSharp.BrowserSubprocess.exe (PID: 6244)
- CefSharp.BrowserSubprocess.exe (PID: 1348)
- CefSharp.BrowserSubprocess.exe (PID: 672)
- CefSharp.BrowserSubprocess.exe (PID: 6372)
- CefSharp.BrowserSubprocess.exe (PID: 2568)
Reads the software policy settings
- SirHurt V2 GUI Bootstrapper.exe (PID: 3884)
- slui.exe (PID: 900)
- SirHurt V5.exe (PID: 6676)
- SirHurt V2 GUI Bootstrapper.exe (PID: 3016)
- SirHurt V5.exe (PID: 5960)
Checks proxy server information
- SirHurt V2 GUI Bootstrapper.exe (PID: 3884)
- SirHurt V5.exe (PID: 6676)
- SirHurt V2 GUI Bootstrapper.exe (PID: 3016)
- SirHurt V5.exe (PID: 5960)
- slui.exe (PID: 5756)
Process checks computer location settings
- SirHurt V2 GUI Bootstrapper.exe (PID: 3884)
- SirHurt V5.exe (PID: 6676)
- CefSharp.BrowserSubprocess.exe (PID: 6828)
- CefSharp.BrowserSubprocess.exe (PID: 6960)
- CefSharp.BrowserSubprocess.exe (PID: 3124)
- SirHurt V5.exe (PID: 5960)
- CefSharp.BrowserSubprocess.exe (PID: 1348)
- CefSharp.BrowserSubprocess.exe (PID: 672)
- CefSharp.BrowserSubprocess.exe (PID: 6372)
Process checks whether UAC notifications are on
- SirHurt V5.exe (PID: 6676)
- SirHurt V5.exe (PID: 5960)
Creates files or folders in the user directory
- SirHurt V5.exe (PID: 6676)
- WerFault.exe (PID: 5956)
- WerFault.exe (PID: 3124)
Create files in a temporary directory
- SirHurt V5.exe (PID: 6676)
- SirHurt V5.exe (PID: 5960)
Themida protector has been detected
- SirHurt V5.exe (PID: 6676)
Manual execution by a user
- SirHurt V2 GUI Bootstrapper.exe (PID: 3016)
- SirHurt V2 GUI Bootstrapper.exe (PID: 6468)
- SirHurt V5.exe (PID: 2140)
- SirHurt V5.exe (PID: 5960)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2051:01:04 13:14:33+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 48 |
| CodeSize: | 1378614 |
| InitializedDataSize: | 138536 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x0000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | HP Inc. |
| FileDescription: | SirHurt V2 GUI Bootstrapper |
| FileVersion: | 1.0.0.0 |
| InternalName: | SirHurt V2 GUI Bootstrapper.exe |
| LegalCopyright: | Copyright © HP Inc. 2019 |
| LegalTrademarks: | - |
| OriginalFileName: | SirHurt V2 GUI Bootstrapper.exe |
| ProductName: | SirHurt V2 GUI Bootstrapper |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
160
Monitored processes
23
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | "C:\Users\admin\Desktop\bin\CefSharp.BrowserSubprocess.exe" --type=renderer --string-annotations=is-enterprise-managed=no --user-data-dir="C:\Users\admin\Desktop\bin\Cache" --log-severity=disable --cefsharpexitsub --no-sandbox --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --field-trial-handle=5548,i,15151917207502772469,13554840782160410628,262144 --disable-features=EnableHangWatcher --variations-seed-version --enable-logging=handle --log-file=5784 --mojo-platform-channel-handle=5780 --host-process-id=5960 /prefetch:1 | C:\Users\admin\Desktop\bin\CefSharp.BrowserSubprocess.exe | — | SirHurt V5.exe | |||||||||||
User: admin Company: The CefSharp Authors Integrity Level: HIGH Description: CefSharp.BrowserSubprocess Version: 131.2.70.0 Modules
| |||||||||||||||
| 900 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1116 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1168 | "C:\Users\admin\Desktop\bin\CefSharp.BrowserSubprocess.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-sandbox --string-annotations=is-enterprise-managed=no --user-data-dir="C:\Users\admin\Desktop\bin\Cache" --log-severity=disable --cefsharpexitsub --field-trial-handle=3840,i,11810534750371135411,16218582958853143724,262144 --disable-features=EnableHangWatcher --variations-seed-version --enable-logging=handle --log-file=3860 --mojo-platform-channel-handle=3852 /prefetch:3 --host-process-id=6676 | C:\Users\admin\Desktop\bin\CefSharp.BrowserSubprocess.exe | SirHurt V5.exe | ||||||||||||
User: admin Company: The CefSharp Authors Integrity Level: HIGH Description: CefSharp.BrowserSubprocess Exit code: 0 Version: 131.2.70.0 Modules
| |||||||||||||||
| 1348 | "C:\Users\admin\Desktop\bin\CefSharp.BrowserSubprocess.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-sandbox --string-annotations=is-enterprise-managed=no --user-data-dir="C:\Users\admin\Desktop\bin\Cache" --log-severity=disable --cefsharpexitsub --field-trial-handle=4844,i,15151917207502772469,13554840782160410628,262144 --disable-features=EnableHangWatcher --variations-seed-version --enable-logging=handle --log-file=4848 --mojo-platform-channel-handle=4828 /prefetch:8 --host-process-id=5960 | C:\Users\admin\Desktop\bin\CefSharp.BrowserSubprocess.exe | — | SirHurt V5.exe | |||||||||||
User: admin Company: The CefSharp Authors Integrity Level: HIGH Description: CefSharp.BrowserSubprocess Version: 131.2.70.0 Modules
| |||||||||||||||
| 2140 | "C:\Users\admin\Desktop\SirHurt V5.exe" | C:\Users\admin\Desktop\SirHurt V5.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: SirHurtUI Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2568 | "C:\Users\admin\Desktop\bin\CefSharp.BrowserSubprocess.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --no-sandbox --string-annotations=is-enterprise-managed=no --user-data-dir="C:\Users\admin\Desktop\bin\Cache" --log-severity=disable --cefsharpexitsub --field-trial-handle=6104,i,15151917207502772469,13554840782160410628,262144 --disable-features=EnableHangWatcher --variations-seed-version --enable-logging=handle --log-file=6124 --mojo-platform-channel-handle=6120 /prefetch:8 --host-process-id=5960 | C:\Users\admin\Desktop\bin\CefSharp.BrowserSubprocess.exe | — | SirHurt V5.exe | |||||||||||
User: admin Company: The CefSharp Authors Integrity Level: HIGH Description: CefSharp.BrowserSubprocess Exit code: 0 Version: 131.2.70.0 Modules
| |||||||||||||||
| 3016 | "C:\Users\admin\Desktop\SirHurt V2 GUI Bootstrapper.exe" | C:\Users\admin\Desktop\SirHurt V2 GUI Bootstrapper.exe | explorer.exe | ||||||||||||
User: admin Company: HP Inc. Integrity Level: HIGH Description: SirHurt V2 GUI Bootstrapper Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3124 | "C:\Users\admin\Desktop\bin\CefSharp.BrowserSubprocess.exe" --type=renderer --string-annotations=is-enterprise-managed=no --user-data-dir="C:\Users\admin\Desktop\bin\Cache" --log-severity=disable --cefsharpexitsub --no-sandbox --video-capture-use-gpu-memory-buffer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --field-trial-handle=5724,i,11810534750371135411,16218582958853143724,262144 --disable-features=EnableHangWatcher --variations-seed-version --enable-logging=handle --log-file=5576 --mojo-platform-channel-handle=5580 --host-process-id=6676 /prefetch:1 | C:\Users\admin\Desktop\bin\CefSharp.BrowserSubprocess.exe | — | SirHurt V5.exe | |||||||||||
User: admin Company: The CefSharp Authors Integrity Level: HIGH Description: CefSharp.BrowserSubprocess Exit code: 0 Version: 131.2.70.0 Modules
| |||||||||||||||
| 3124 | C:\WINDOWS\system32\WerFault.exe -u -p 3016 -s 2224 | C:\Windows\System32\WerFault.exe | — | SirHurt V2 GUI Bootstrapper.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 574
Read events
13 480
Write events
88
Delete events
6
Modification events
| (PID) Process: | (3884) SirHurt V2 GUI Bootstrapper.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Attachments |
| Operation: | write | Name: | SaveZoneInformation |
Value: 1 | |||
| (PID) Process: | (3884) SirHurt V2 GUI Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Attachments |
| Operation: | write | Name: | SaveZoneInformation |
Value: 1 | |||
| (PID) Process: | (3884) SirHurt V2 GUI Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SirHurt V2 GUI Bootstrapper_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3884) SirHurt V2 GUI Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SirHurt V2 GUI Bootstrapper_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (3884) SirHurt V2 GUI Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SirHurt V2 GUI Bootstrapper_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3884) SirHurt V2 GUI Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SirHurt V2 GUI Bootstrapper_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (3884) SirHurt V2 GUI Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SirHurt V2 GUI Bootstrapper_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (3884) SirHurt V2 GUI Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SirHurt V2 GUI Bootstrapper_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3884) SirHurt V2 GUI Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SirHurt V2 GUI Bootstrapper_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3884) SirHurt V2 GUI Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\SirHurt V2 GUI Bootstrapper_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
30
Suspicious files
425
Text files
53
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3884 | SirHurt V2 GUI Bootstrapper.exe | C:\Users\admin\Desktop\bin.zip | — | |
MD5:— | SHA256:— | |||
| 3884 | SirHurt V2 GUI Bootstrapper.exe | C:\Users\admin\Desktop\sirhurt.exe | executable | |
MD5:B4BFA67D1897B2341078F47042D09421 | SHA256:2F474C0594F7B18068F6457CF7F20592CB7005AE72BB397D98E11061CC5D7AEC | |||
| 3884 | SirHurt V2 GUI Bootstrapper.exe | C:\Users\admin\Desktop\bin\ace\ace\ext-beautify.js | binary | |
MD5:AD7F90D7BDCD39232E4743C5F73EBD9C | SHA256:315E22AD02969C76033CB8326D69BBAC69A8246D58556AC00FFC9075D43011AA | |||
| 3884 | SirHurt V2 GUI Bootstrapper.exe | C:\Users\admin\Desktop\sirhurt.zip | compressed | |
MD5:BFA59E61EFC71CE72E30CD9D37F770D1 | SHA256:9A7F6447D4B069AC730A90A3CD2F1E2458F2707A530CF69E4C22A9A51578D985 | |||
| 3884 | SirHurt V2 GUI Bootstrapper.exe | C:\Users\admin\Desktop\sirhurt.dll | executable | |
MD5:B0ADF3DCAA727E8765C14F0ED7F7A99C | SHA256:835F36D66092C08E0F2AF94C7F2A62C673DDE84333E1FE9763C1CCE0833430CD | |||
| 3884 | SirHurt V2 GUI Bootstrapper.exe | C:\Users\admin\Desktop\SirHurt V5.exe | executable | |
MD5:E2AE49FF7B94A6F4CA78ADBA1468B1CB | SHA256:4AA68FCA82F6D2407F2AADD1ABFA575E15ABF8E3563306C04107F685F19F6A4E | |||
| 3884 | SirHurt V2 GUI Bootstrapper.exe | C:\Users\admin\Desktop\binmd5.txt | text | |
MD5:07FBC176616AF93AF4A10A8AEA1F742A | SHA256:16583661C0FE97149182686046AE5654B9256EDB51B5D30DDB3C151B22BED020 | |||
| 3884 | SirHurt V2 GUI Bootstrapper.exe | C:\Users\admin\Desktop\bin\ace\ace\ace.js | binary | |
MD5:6A1ACA1328B0A6BB78E7053A33D3FCA3 | SHA256:C635ED59BB141B5B1B819B448AEECF874E06B4328CA3BA4E404B53F2D83509B9 | |||
| 3884 | SirHurt V2 GUI Bootstrapper.exe | C:\Users\admin\Desktop\bootstrapper_debug.txt | text | |
MD5:B420FBC40EFE09538B621D5727877FB8 | SHA256:7D8CDB68CB046B7A809931AD99242C87EF0F58DE6D5730E66BF2A1AA08392E23 | |||
| 3884 | SirHurt V2 GUI Bootstrapper.exe | C:\Users\admin\Desktop\SirHurt UI.zip | compressed | |
MD5:E0F57D6BB2908144221F4C7E006DEBAF | SHA256:17F93CA8F6B64322C84615A56BA89B31AFFA19B9F668F1FA7E747B5F866EA644 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
37
DNS requests
24
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2236 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2236 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3884 | SirHurt V2 GUI Bootstrapper.exe | 104.21.95.242:443 | sirhurt.net | CLOUDFLARENET | — | unknown |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
3884 | SirHurt V2 GUI Bootstrapper.exe | 172.67.149.166:443 | sirhurt.net | CLOUDFLARENET | US | unknown |
6544 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
sirhurt.net |
| unknown |
client.wns.windows.com |
| whitelisted |
www.sirhurt.net |
| unknown |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
6676 | SirHurt V5.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
6676 | SirHurt V5.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
5960 | SirHurt V5.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
5960 | SirHurt V5.exe | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
4528 | CefSharp.BrowserSubprocess.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
4528 | CefSharp.BrowserSubprocess.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
4528 | CefSharp.BrowserSubprocess.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
4528 | CefSharp.BrowserSubprocess.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
4528 | CefSharp.BrowserSubprocess.exe | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |