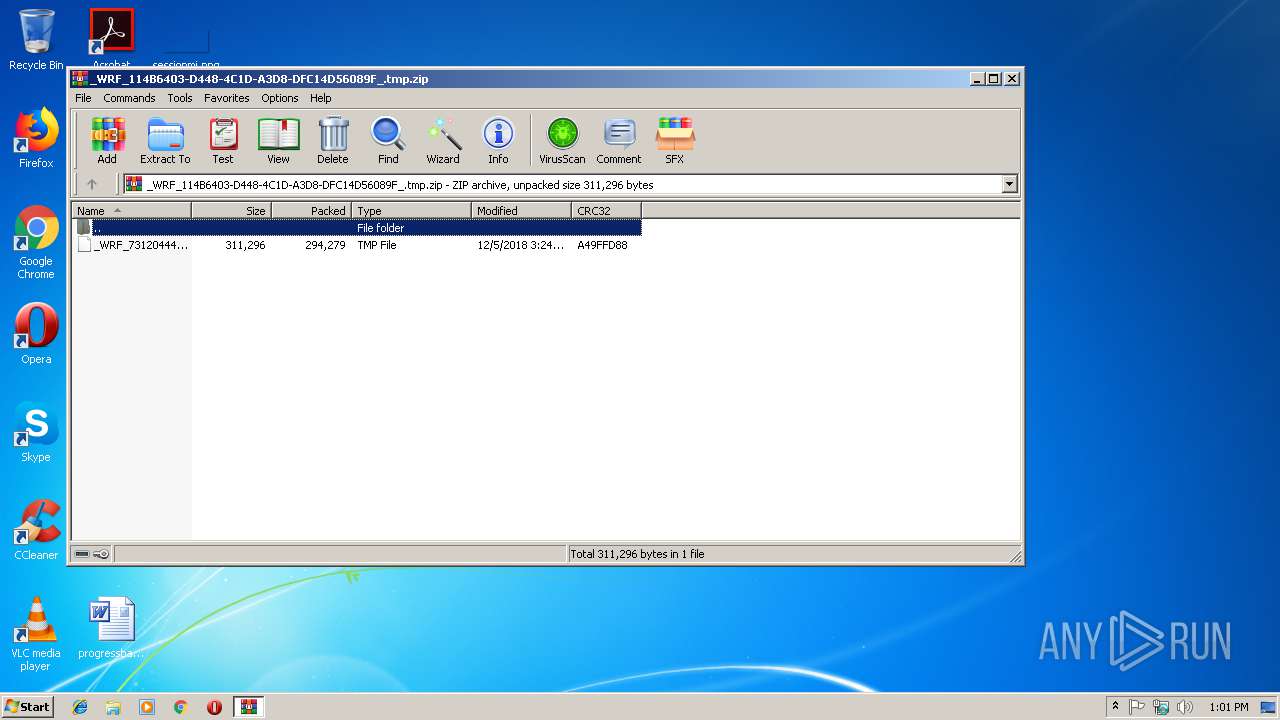
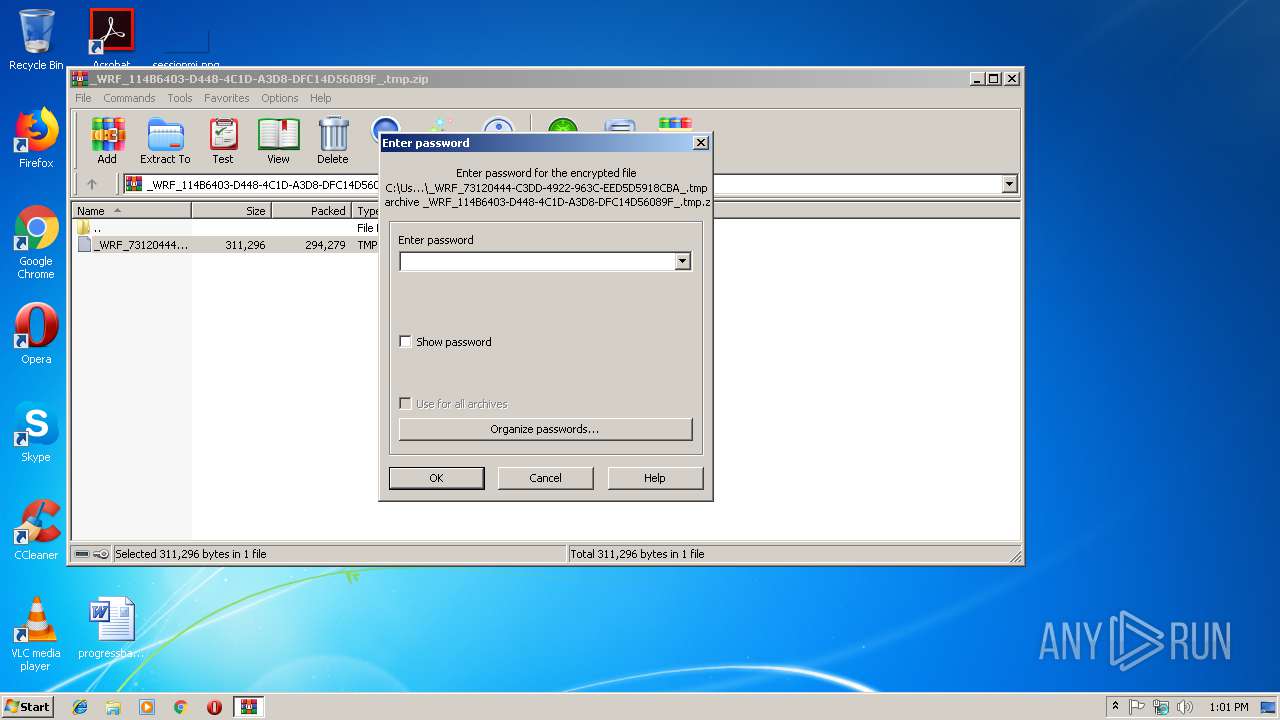
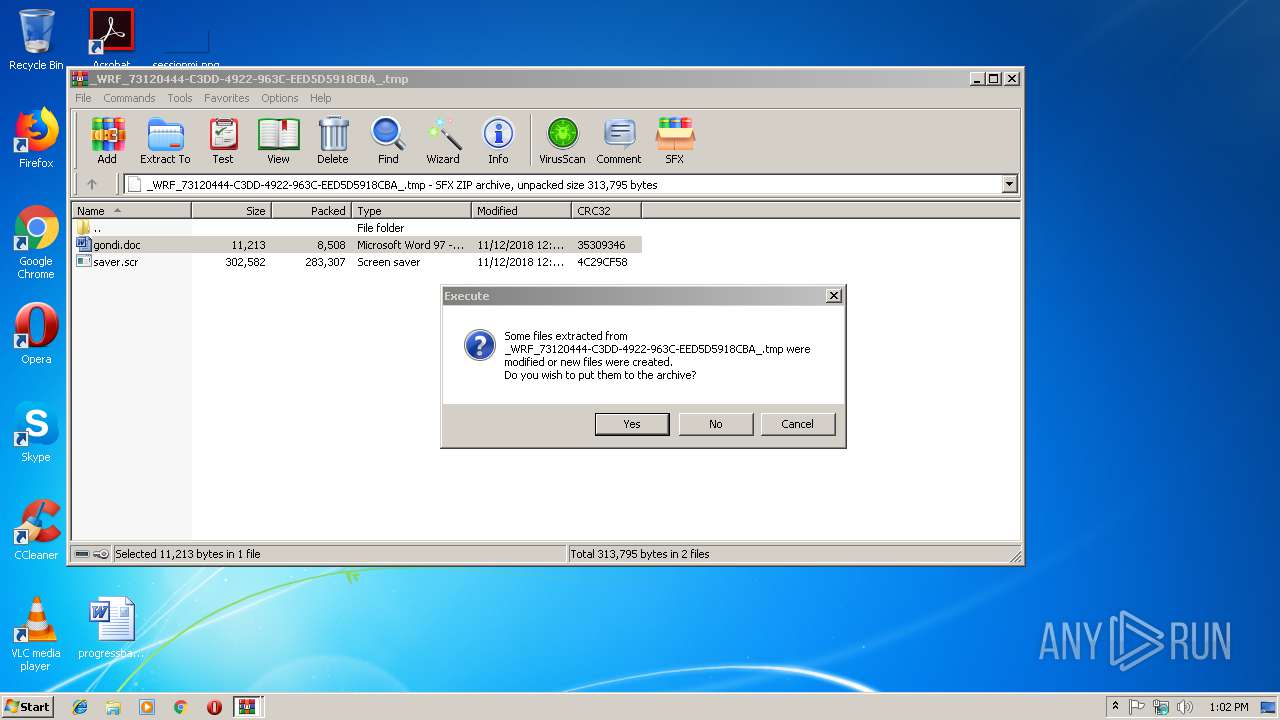
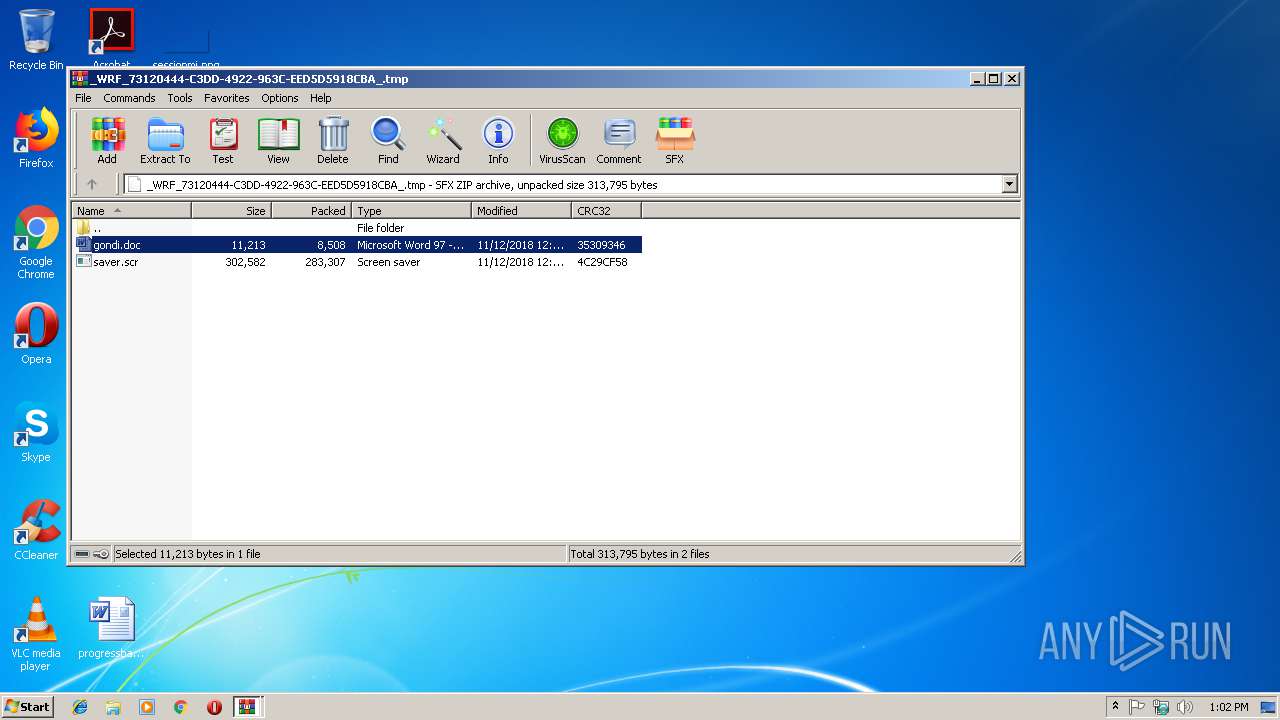
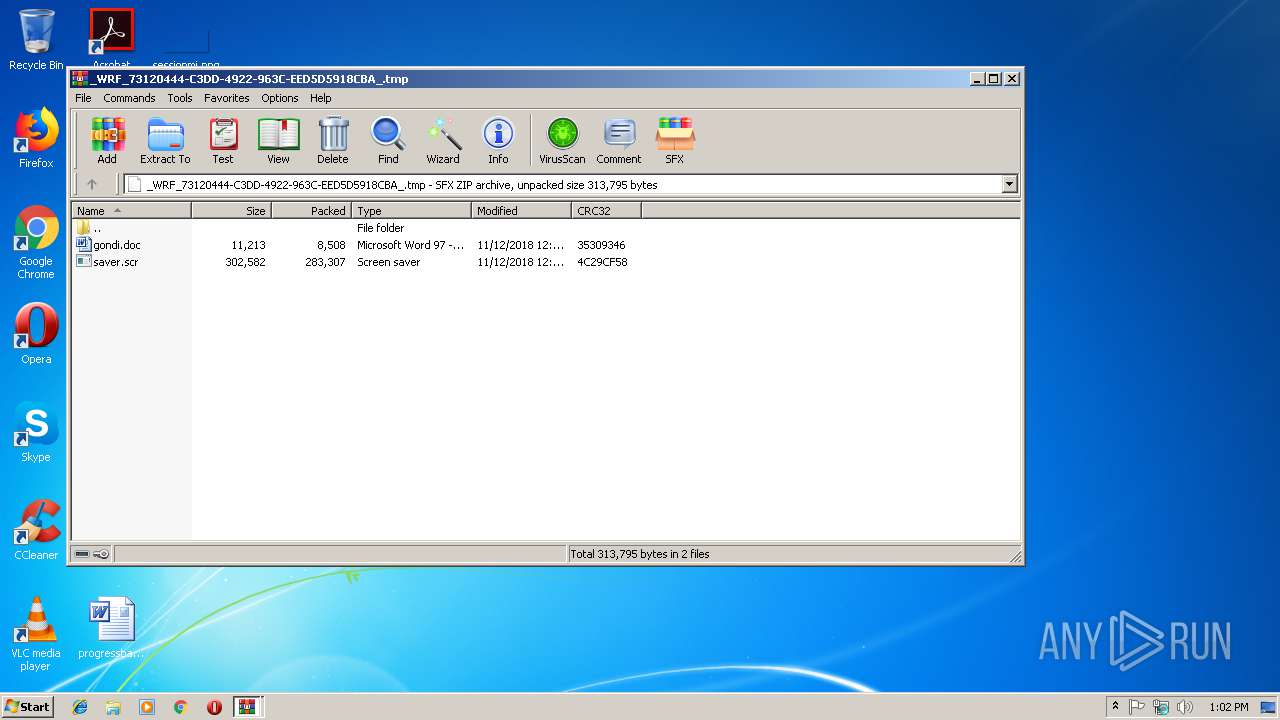
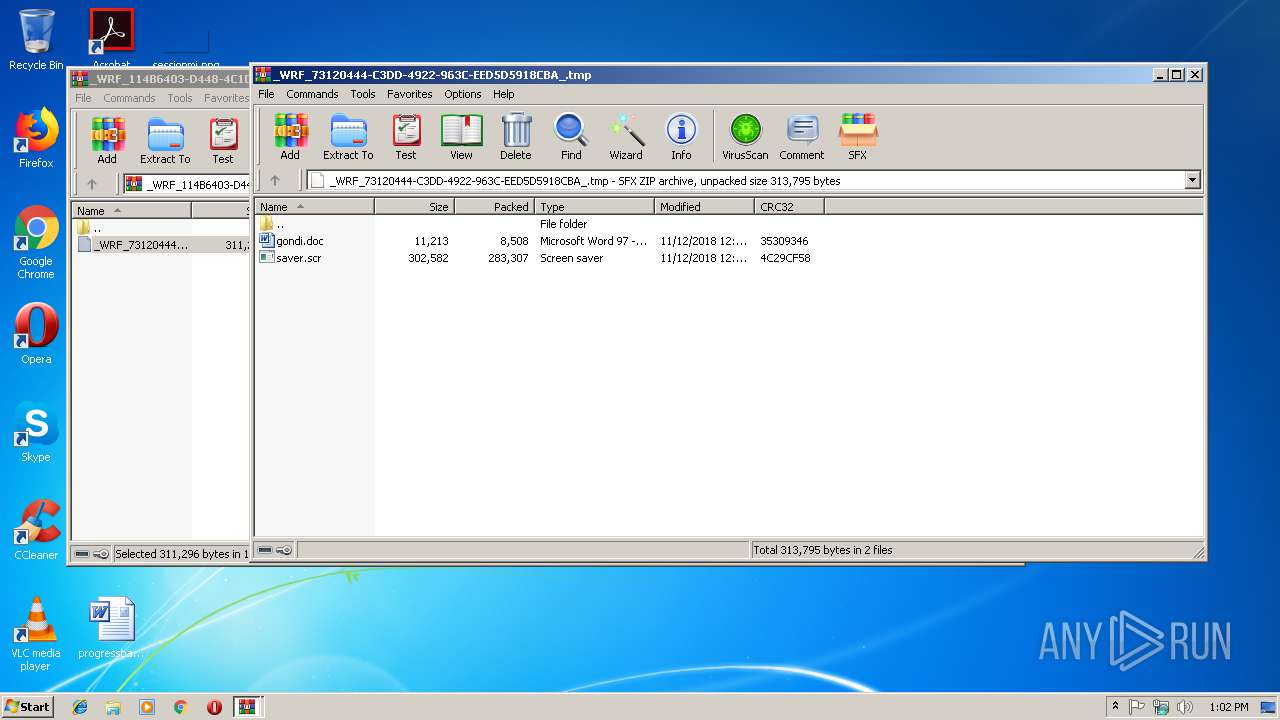
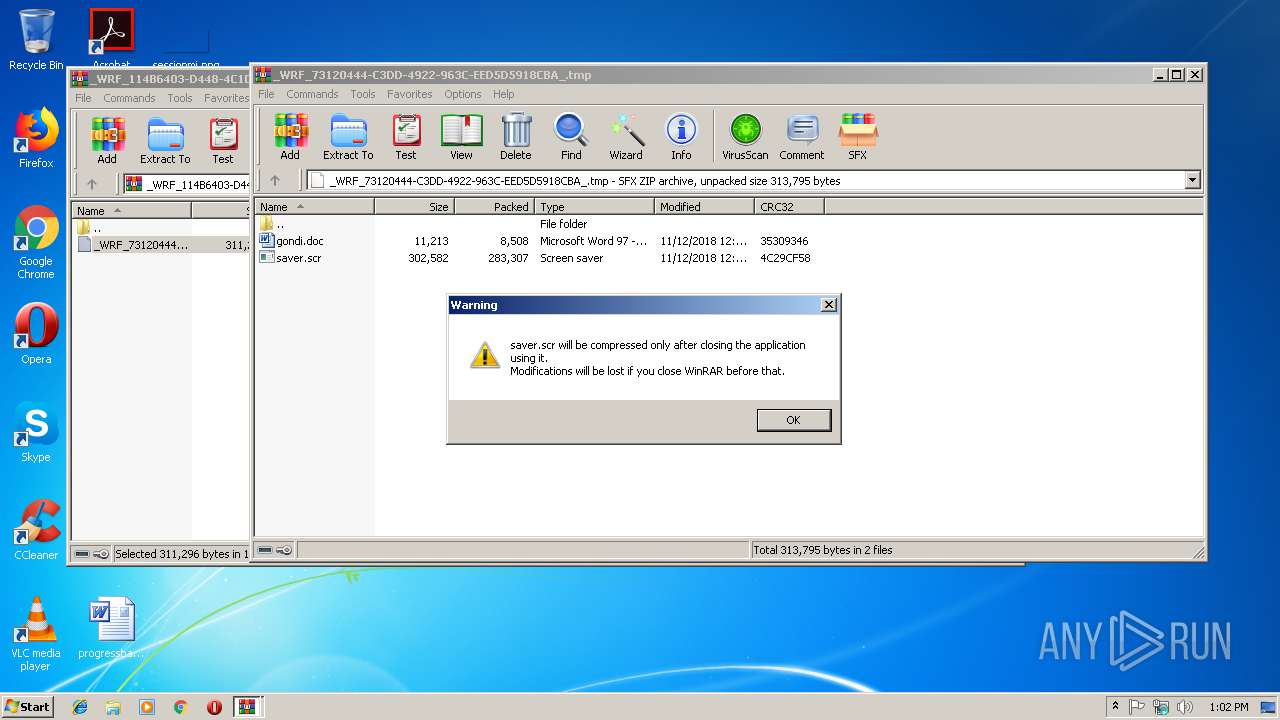
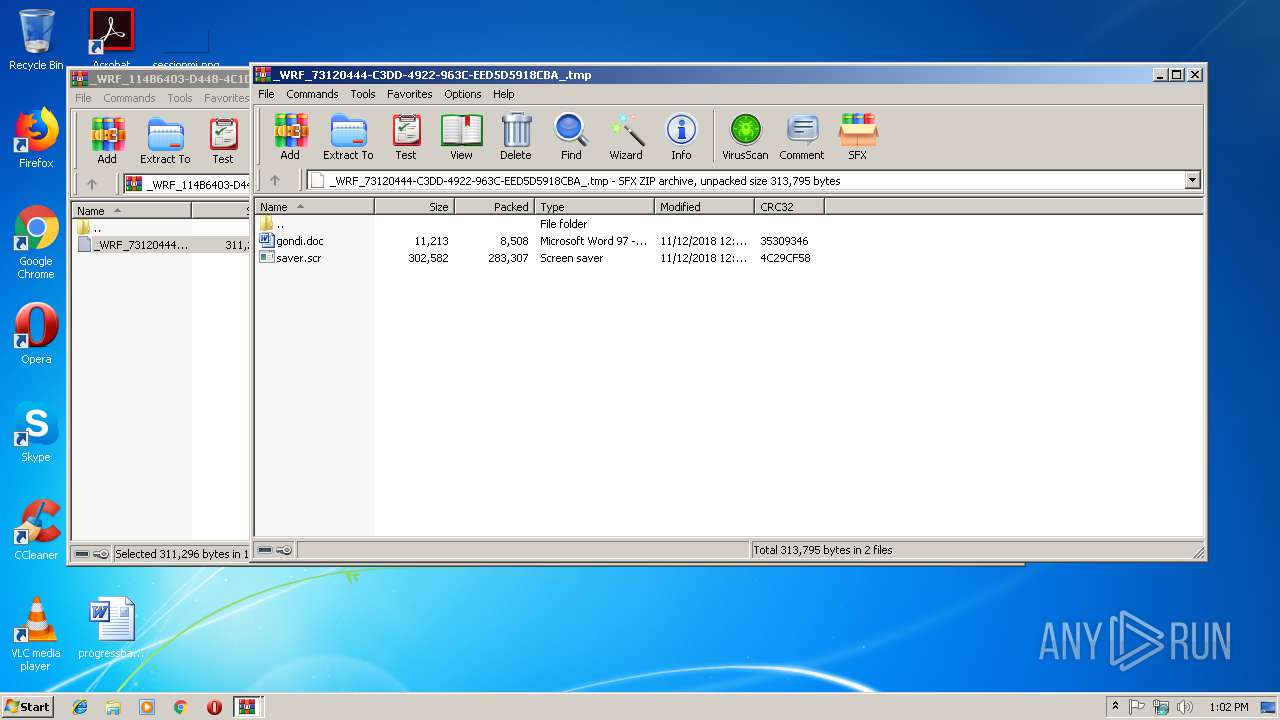
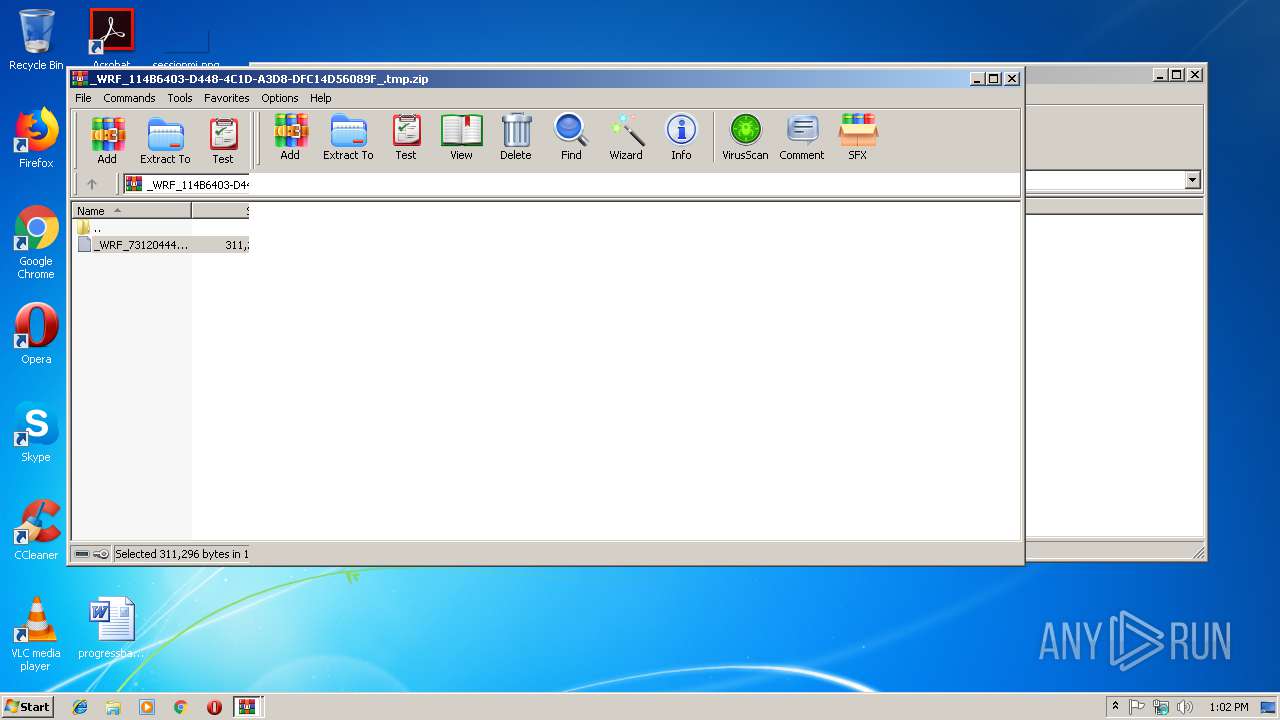
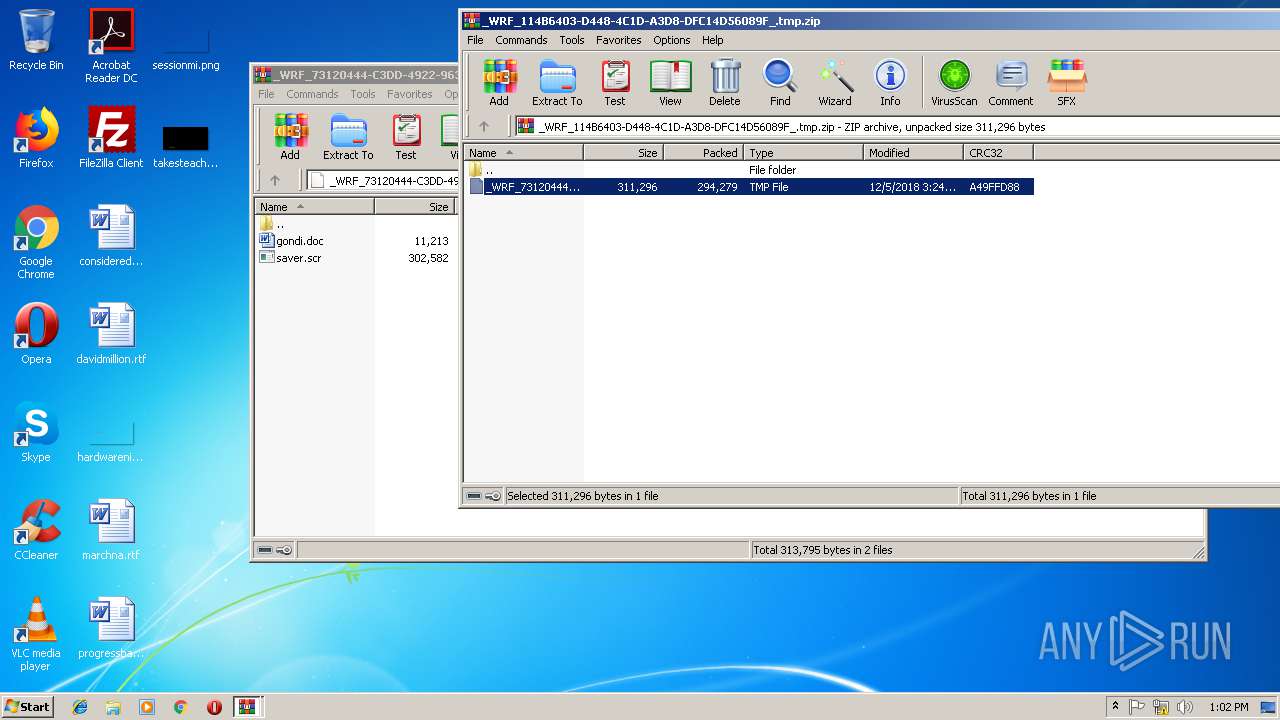
| File name: | _WRF_114B6403-D448-4C1D-A3D8-DFC14D56089F_.tmp.zip |
| Full analysis: | https://app.any.run/tasks/5a91c36d-5f6e-4c65-be56-bf01938b6313 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2018, 13:01:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | FBC8544BABE46997B051B963F8909746 |
| SHA1: | BDB6BDD407209278DE4118E91FB6EAFCB0265C36 |
| SHA256: | 7E00E15B01BE2634E78A10C1AA1462AA4463A1811B9996E673E9536A1E933CA4 |
| SSDEEP: | 6144:bgBFQyym4VsDIc+Kau2RIiyIDJJJEJGCW6Js:bEnUG+u2RIkDJbEYC7Js |
MALICIOUS
Application was dropped or rewritten from another process
- saver.scr (PID: 3248)
SUSPICIOUS
Application launched itself
- WinRAR.exe (PID: 2920)
Starts application with an unusual extension
- WinRAR.exe (PID: 2776)
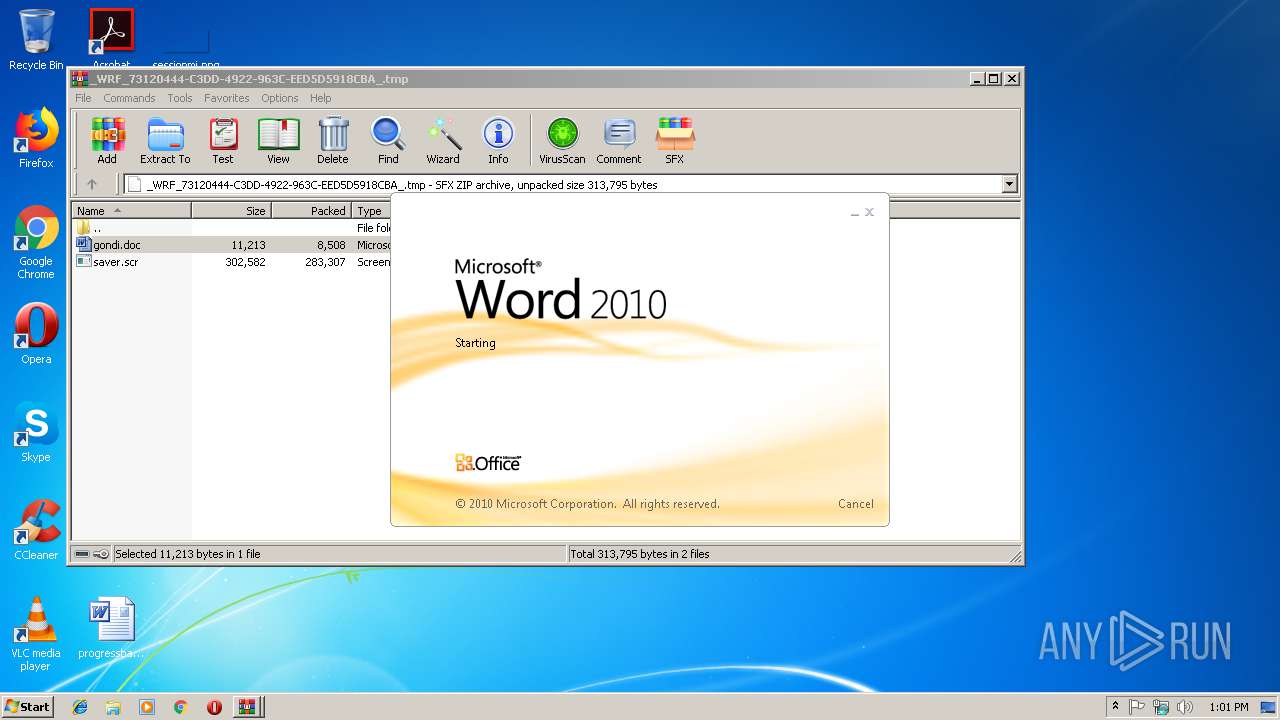
Starts Microsoft Office Application
- WinRAR.exe (PID: 2776)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2776)
- saver.scr (PID: 3248)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 1360)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 1360)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:12:05 16:24:17 |
| ZipCRC: | 0xa49ffd88 |
| ZipCompressedSize: | 294279 |
| ZipUncompressedSize: | 311296 |
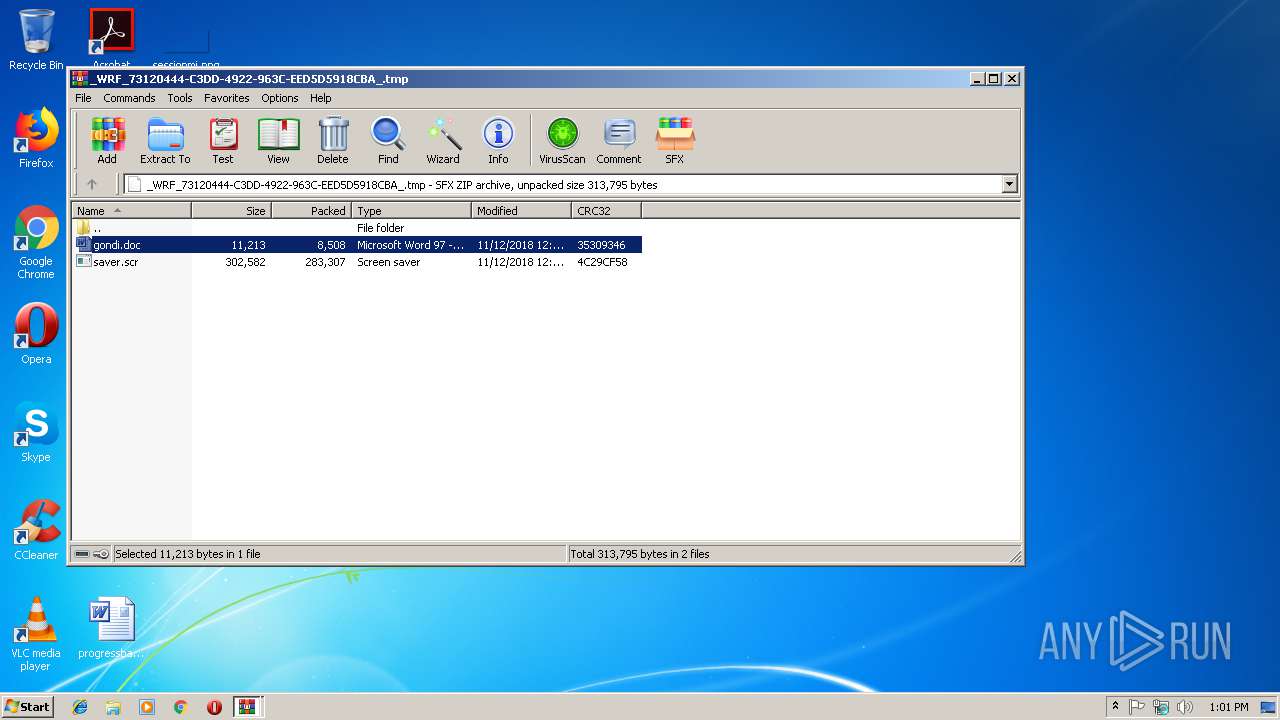
| ZipFileName: | _WRF_73120444-C3DD-4922-963C-EED5D5918CBA_.tmp |
Total processes
34
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1360 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Rar$DIa2776.31040\gondi.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
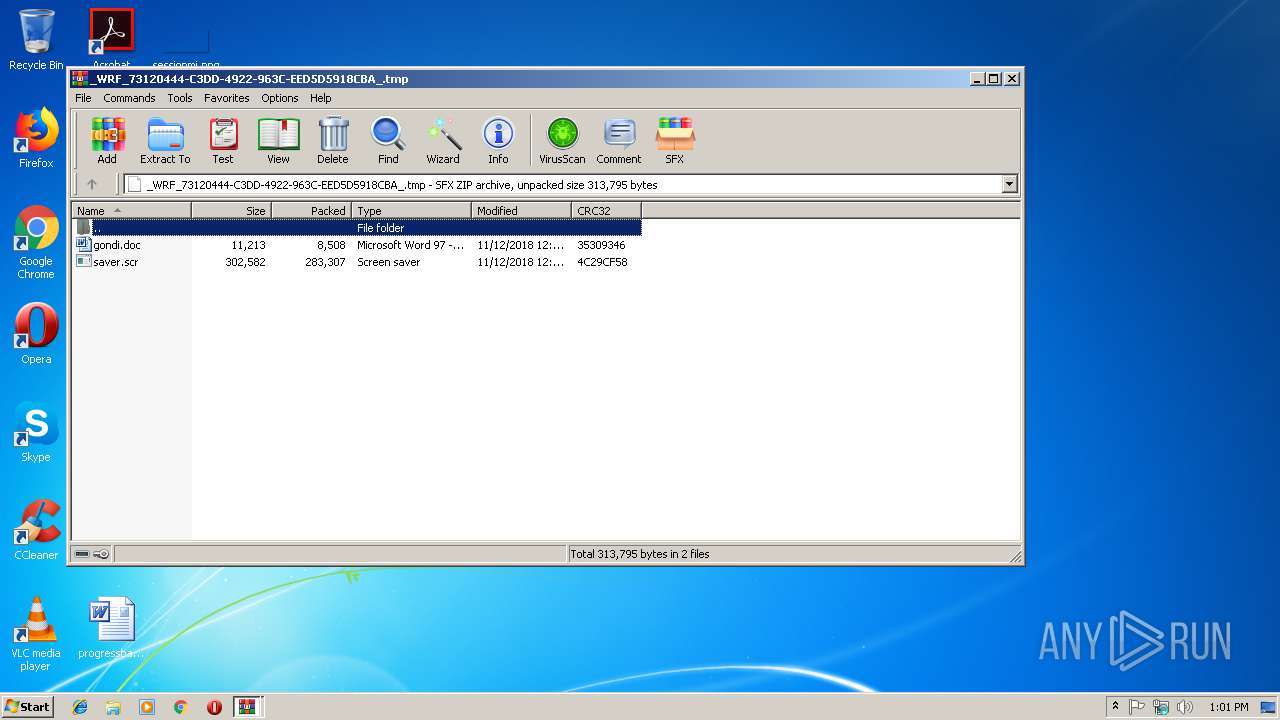
| 2776 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIb2920.30376\_WRF_73120444-C3DD-4922-963C-EED5D5918CBA_.tmp | C:\Program Files\WinRAR\WinRAR.exe | WinRAR.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2920 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\_WRF_114B6403-D448-4C1D-A3D8-DFC14D56089F_.tmp.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3248 | "C:\Users\admin\AppData\Local\Temp\Rar$DIa2776.32387\saver.scr" /S | C:\Users\admin\AppData\Local\Temp\Rar$DIa2776.32387\saver.scr | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
2 370
Read events
2 009
Write events
352
Delete events
9
Modification events
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\_WRF_114B6403-D448-4C1D-A3D8-DFC14D56089F_.tmp.zip | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2920) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2776) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2776) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
Executable files
3
Suspicious files
3
Text files
1
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1360 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRF05E.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1360 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{922FDF09-48F5-480B-B347-2E4B60E8B9B4}.tmp | — | |
MD5:— | SHA256:— | |||
| 1360 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{9538CCCE-87EA-4424-B8A7-7E1087C83CD9}.tmp | — | |
MD5:— | SHA256:— | |||
| 1360 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Rar$DIa2776.31040\~$gondi.doc | pgc | |
MD5:— | SHA256:— | |||
| 1360 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2920 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb2920.30376\_WRF_73120444-C3DD-4922-963C-EED5D5918CBA_.tmp | binary | |
MD5:— | SHA256:— | |||
| 2776 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2776.31040\gondi.doc | document | |
MD5:— | SHA256:— | |||
| 3248 | saver.scr | C:\Users\admin\AppData\Local\Temp\Marabou | binary | |
MD5:— | SHA256:— | |||
| 3248 | saver.scr | C:\Users\admin\AppData\Local\Temp\penalisation.dll | executable | |
MD5:— | SHA256:— | |||
| 2776 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2776.32387\saver.scr | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | — | 91.243.80.52:80 | http://radburgsoft.com/bet/nite/logout.php?page=70 | NL | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 134.170.58.221:80 | update.microsoft.com | Microsoft Corporation | US | whitelisted |
— | — | 91.243.80.52:80 | radburgsoft.com | Sinarohost LTD | NL | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
update.microsoft.com |
| whitelisted |
radburgsoft.com |
| malicious |