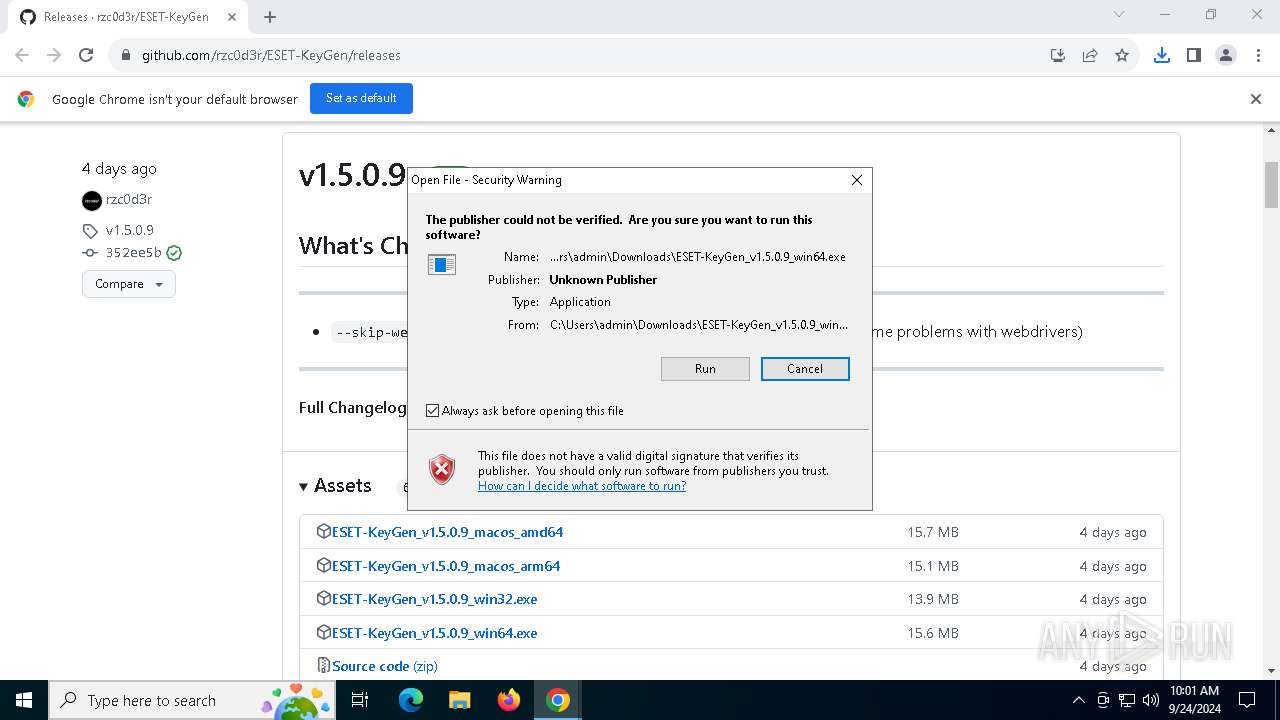
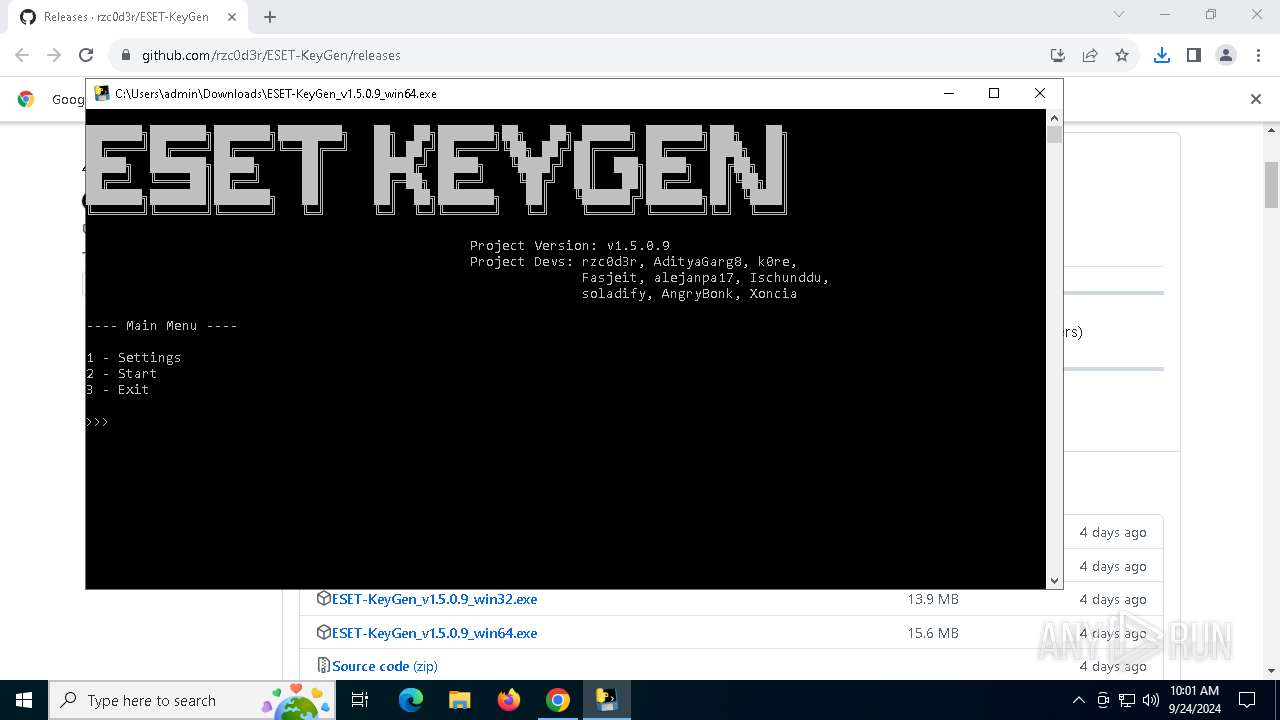
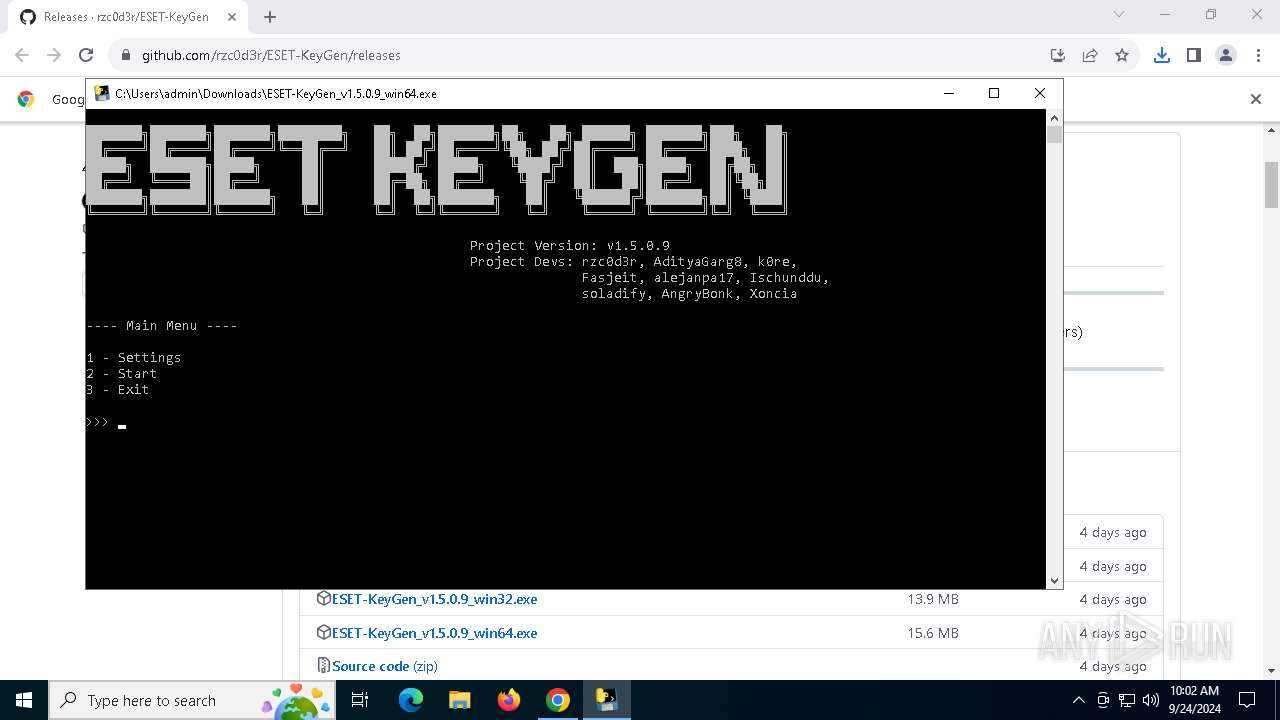
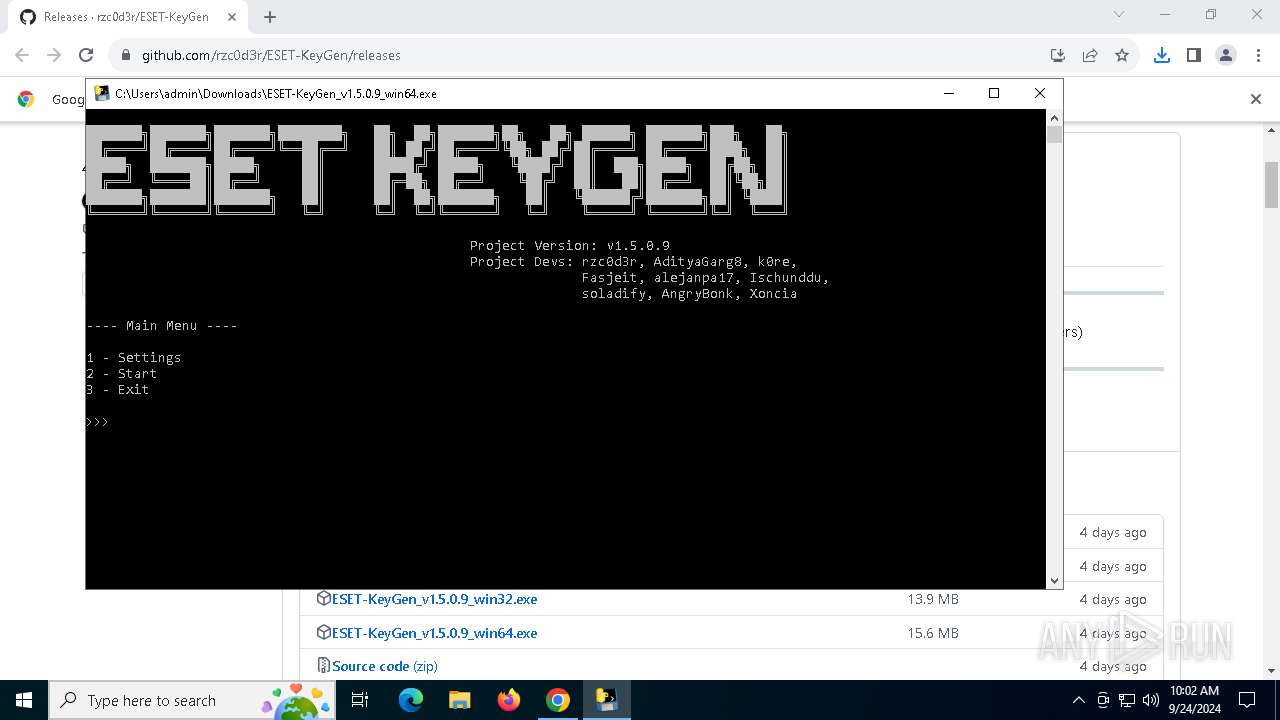
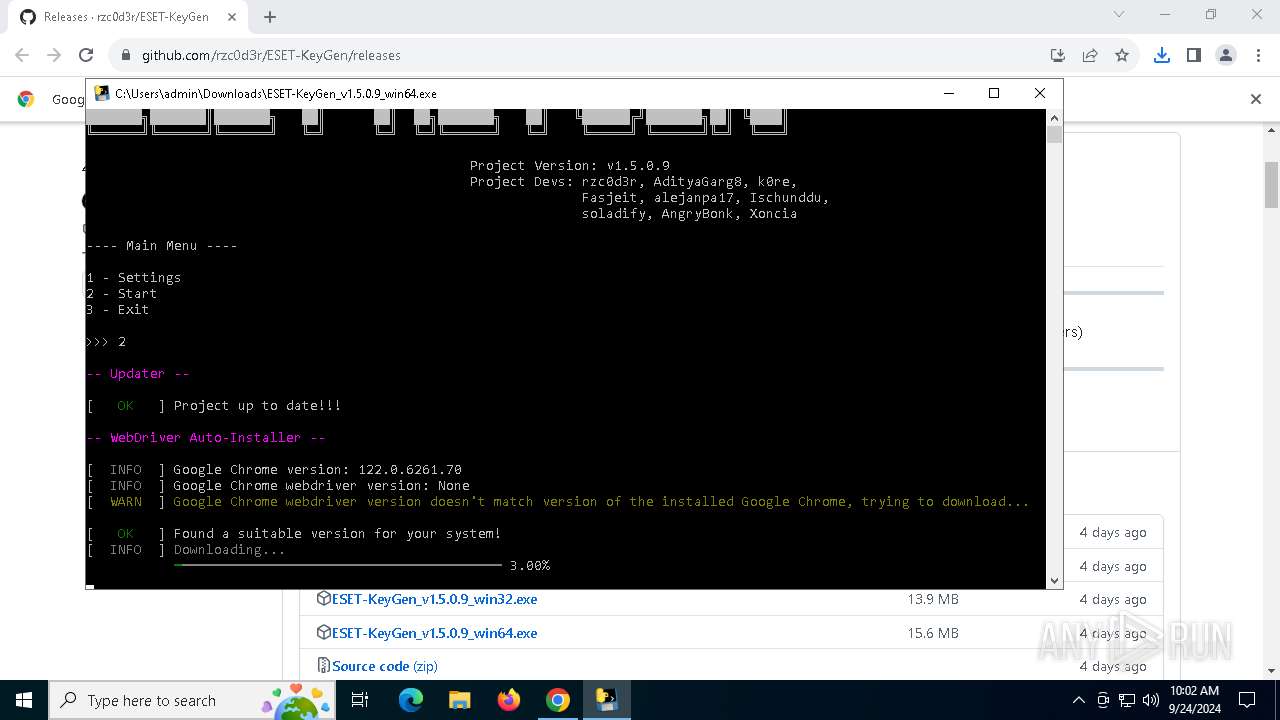
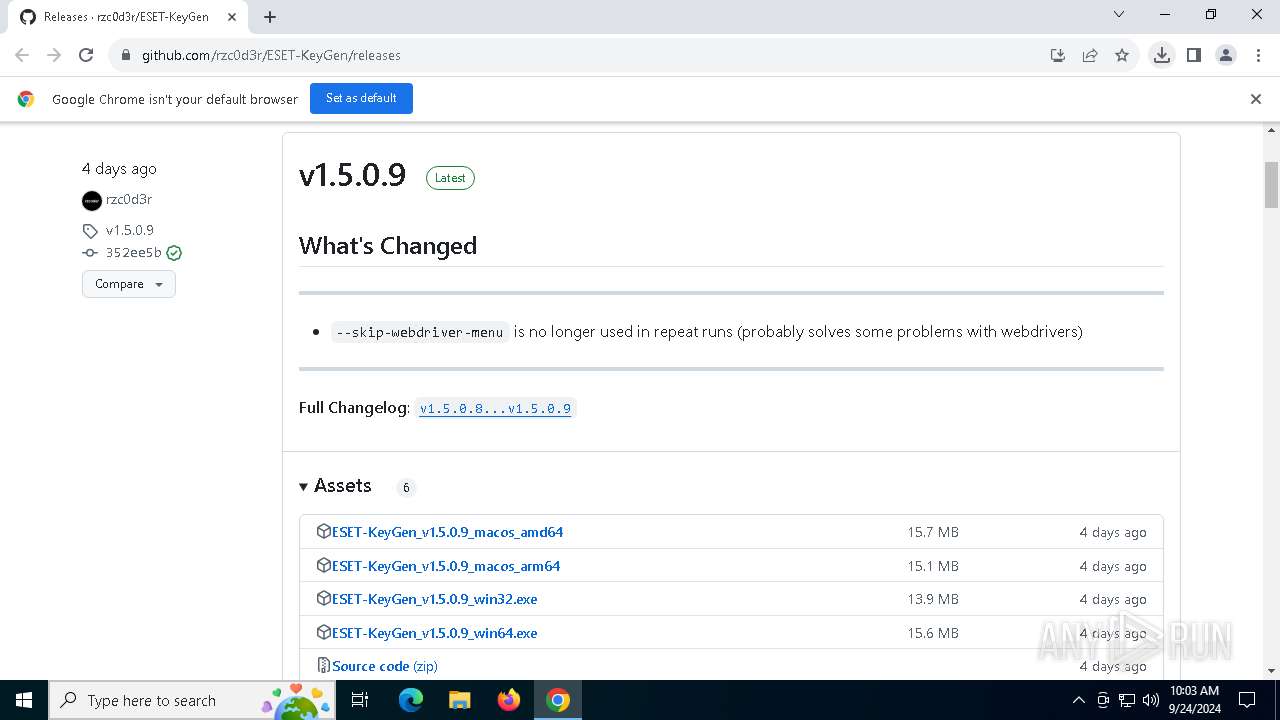
| URL: | https://github.com/rzc0d3r/ESET-KeyGen/releases |
| Full analysis: | https://app.any.run/tasks/697a4d76-3a70-4c16-9e69-f25b5dfcf545 |
| Verdict: | Malicious activity |
| Analysis date: | September 24, 2024, 10:01:10 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 4E1902BB0751FB58DD60CC8F04E79457 |
| SHA1: | 4D7740875A7AF88371BE2C7D6CB0BBEEEFBFACC8 |
| SHA256: | 7DF8080B7CE6F7DDA4F54DB07C4867FA5617FB9F6E4D9FCCE126D4E7E29D97FA |
| SSDEEP: | 3:N8tEdnurQKqjLBJMn:2u4rQX/Mn |
MALICIOUS
No malicious indicators.SUSPICIOUS
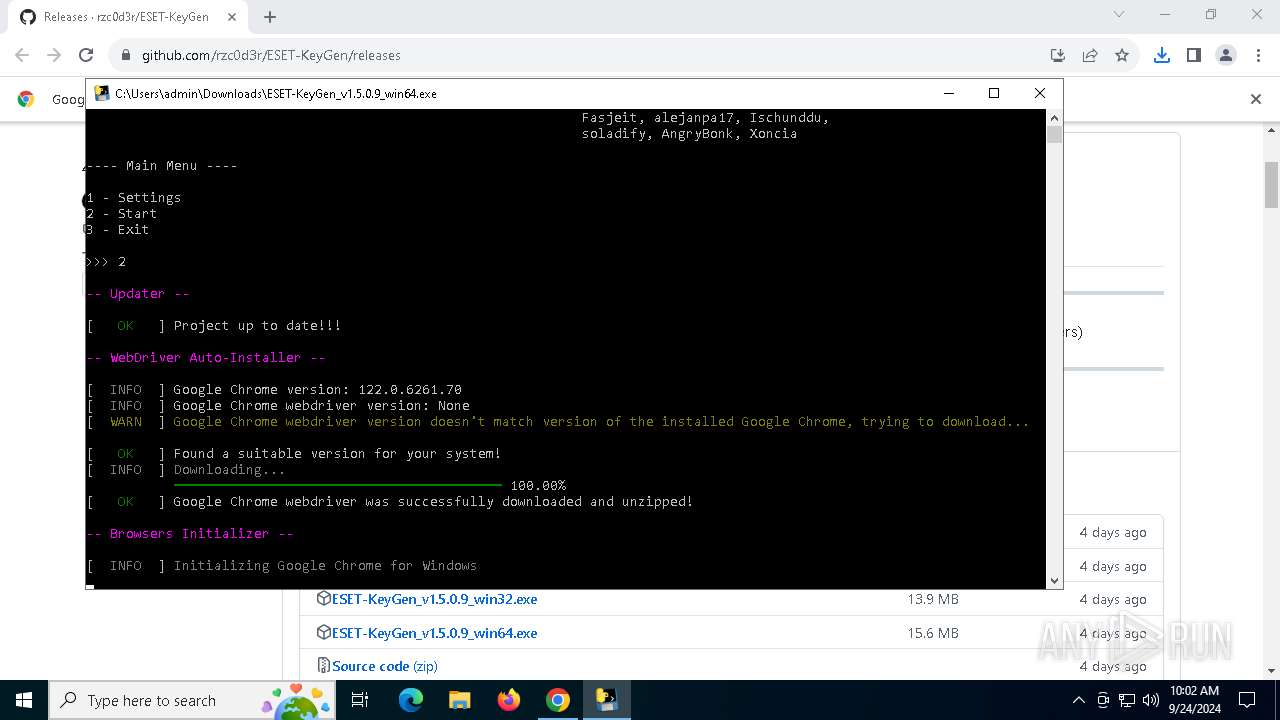
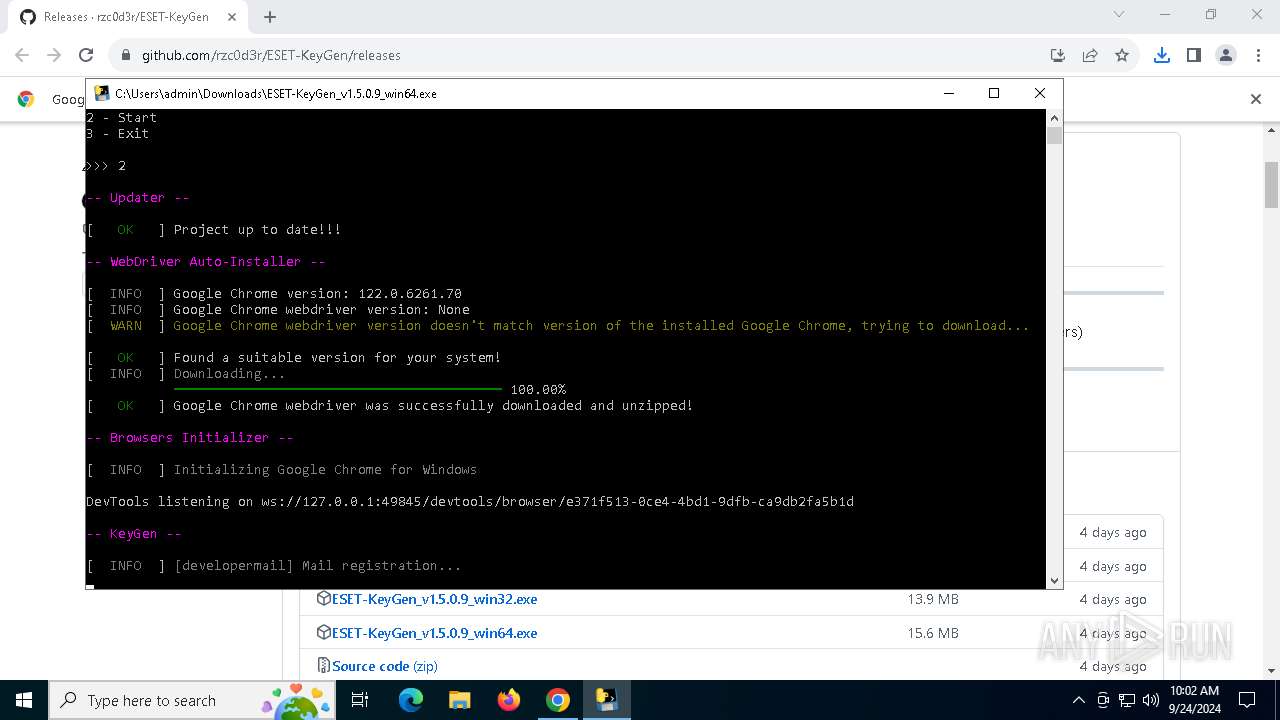
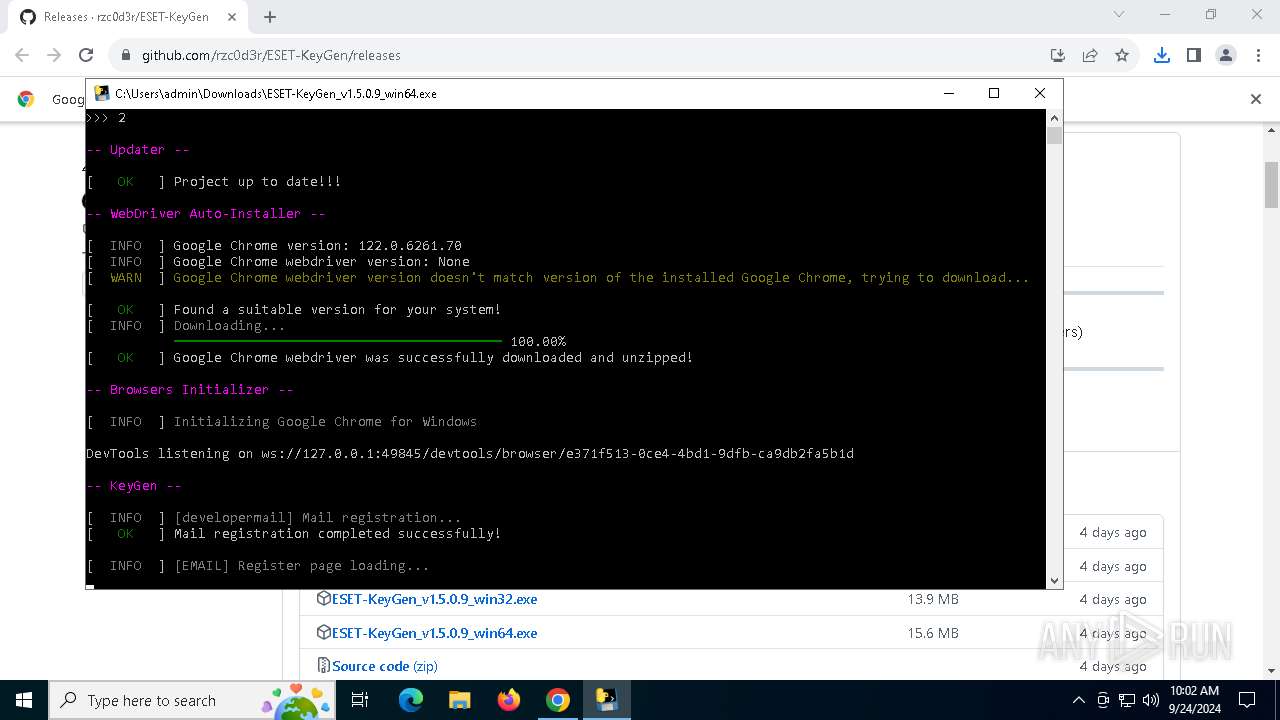
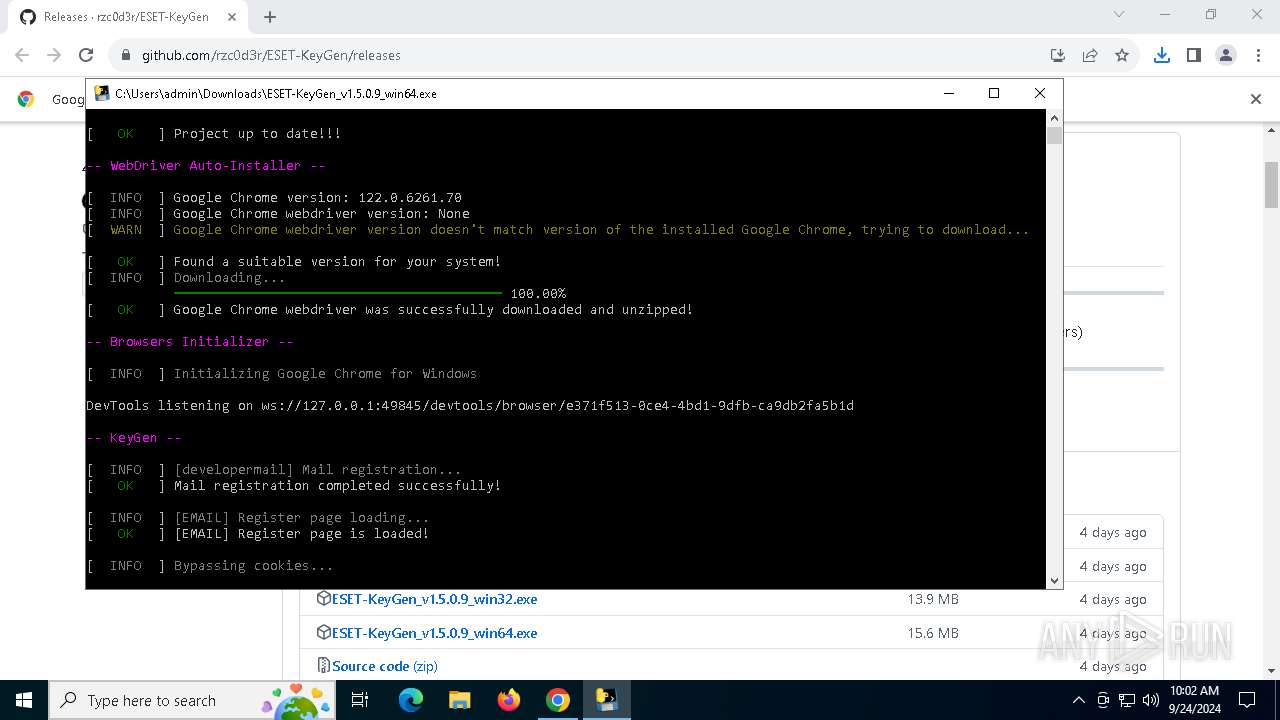
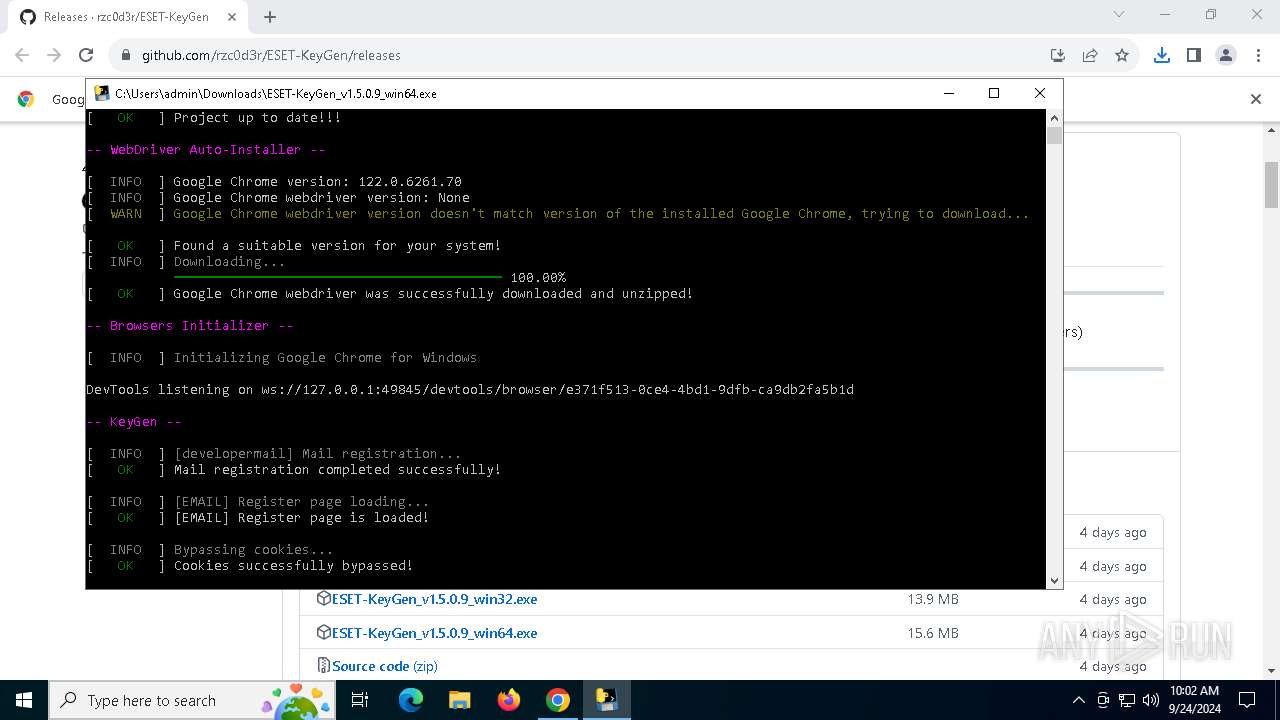
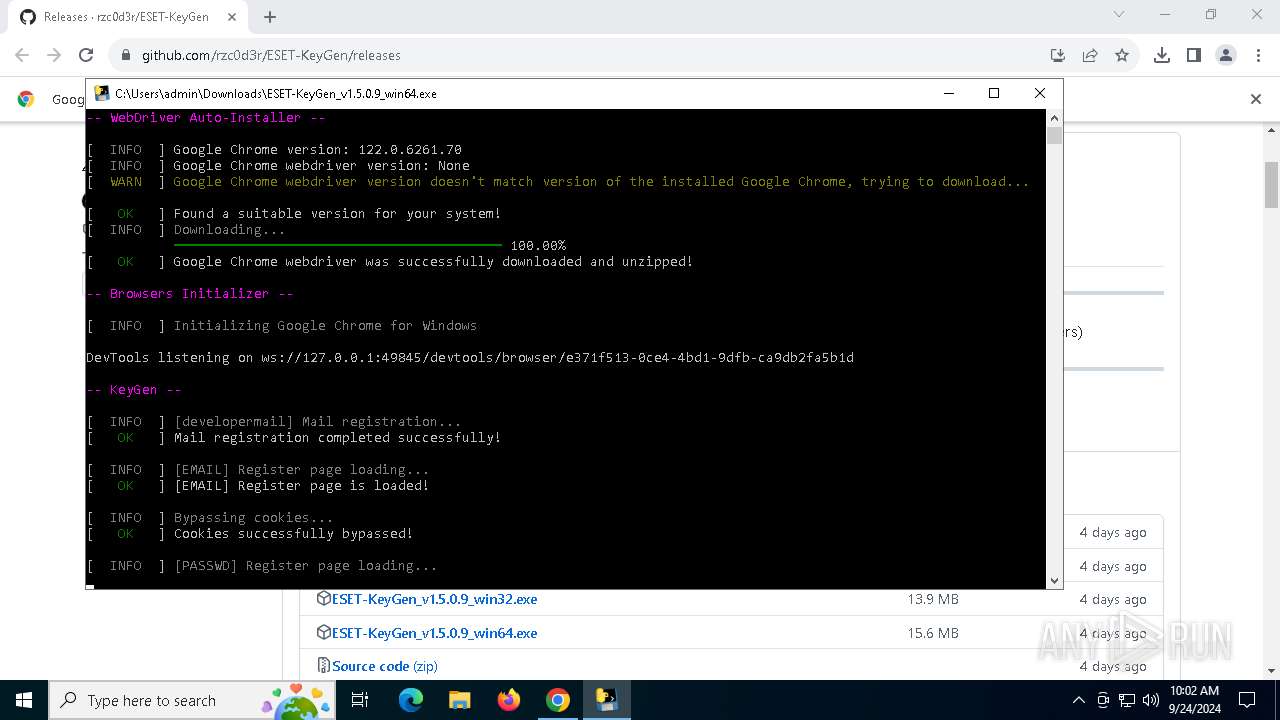
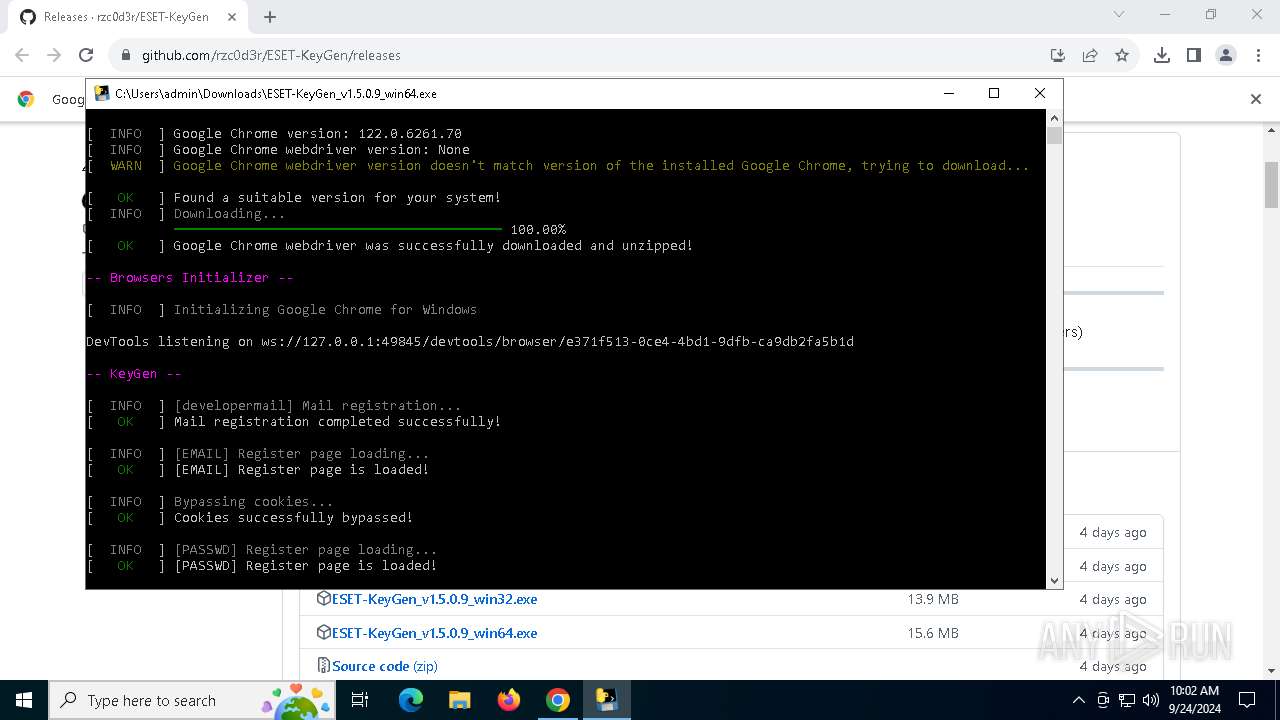
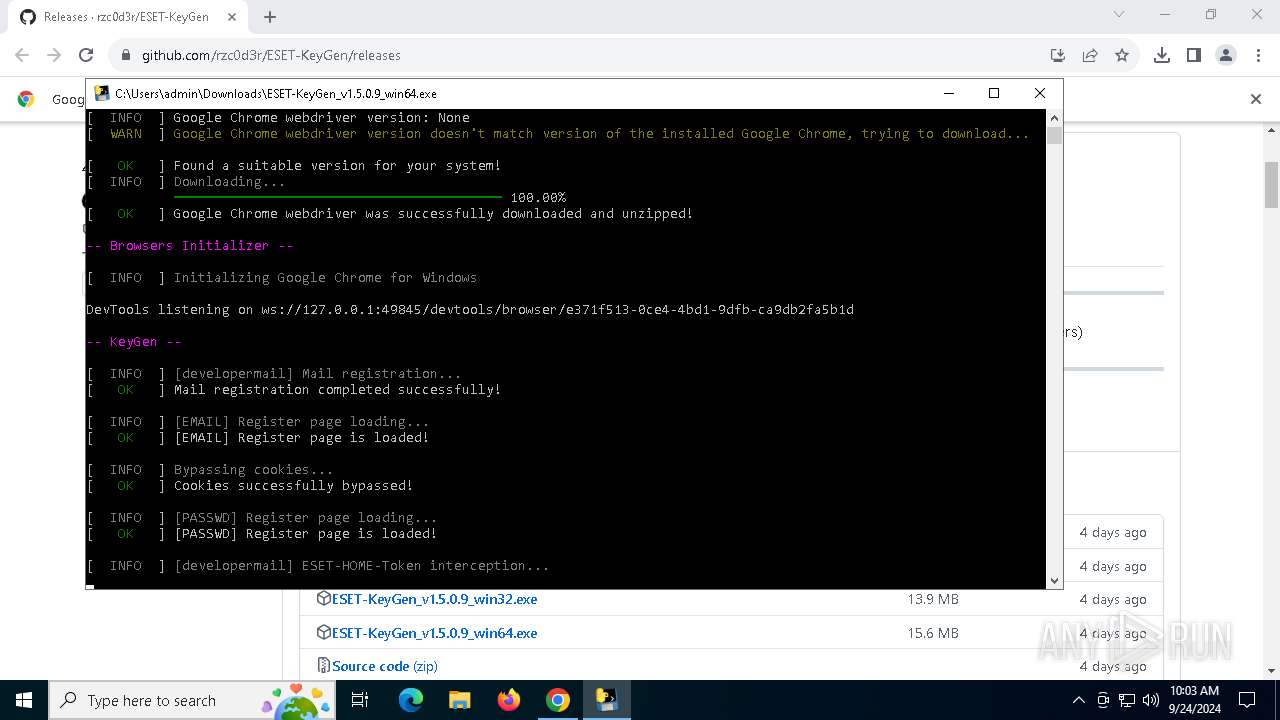
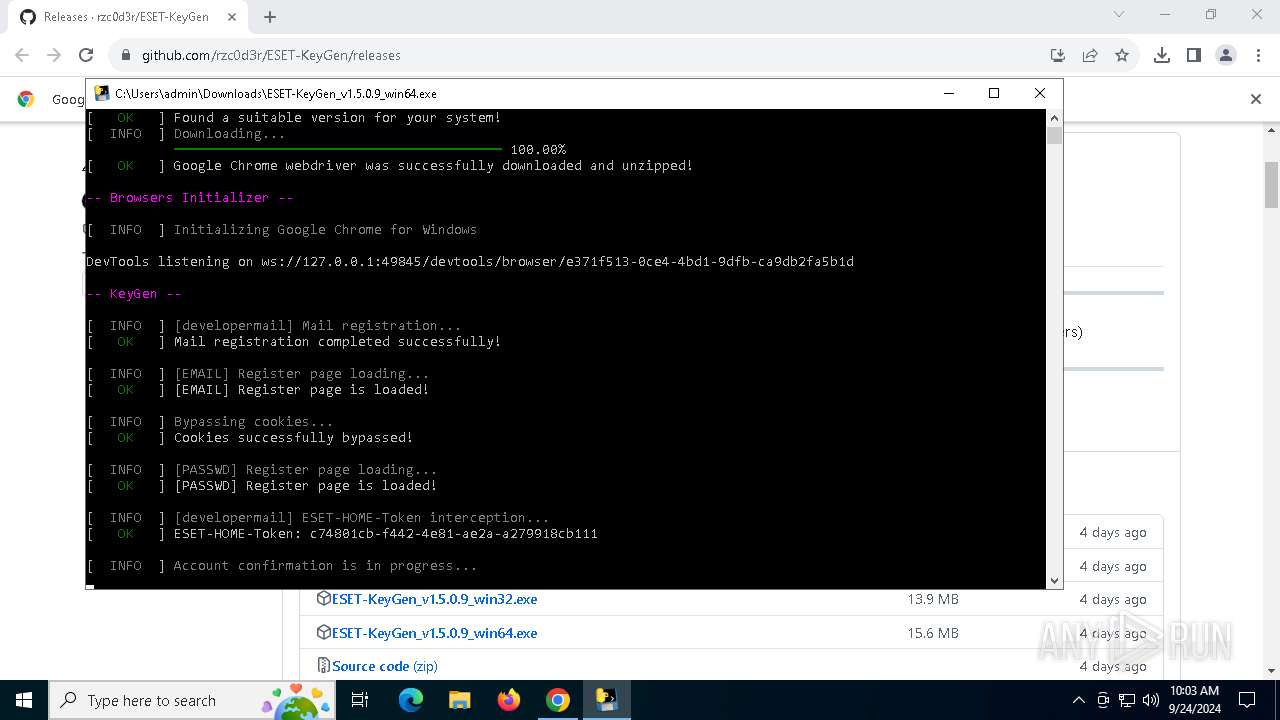
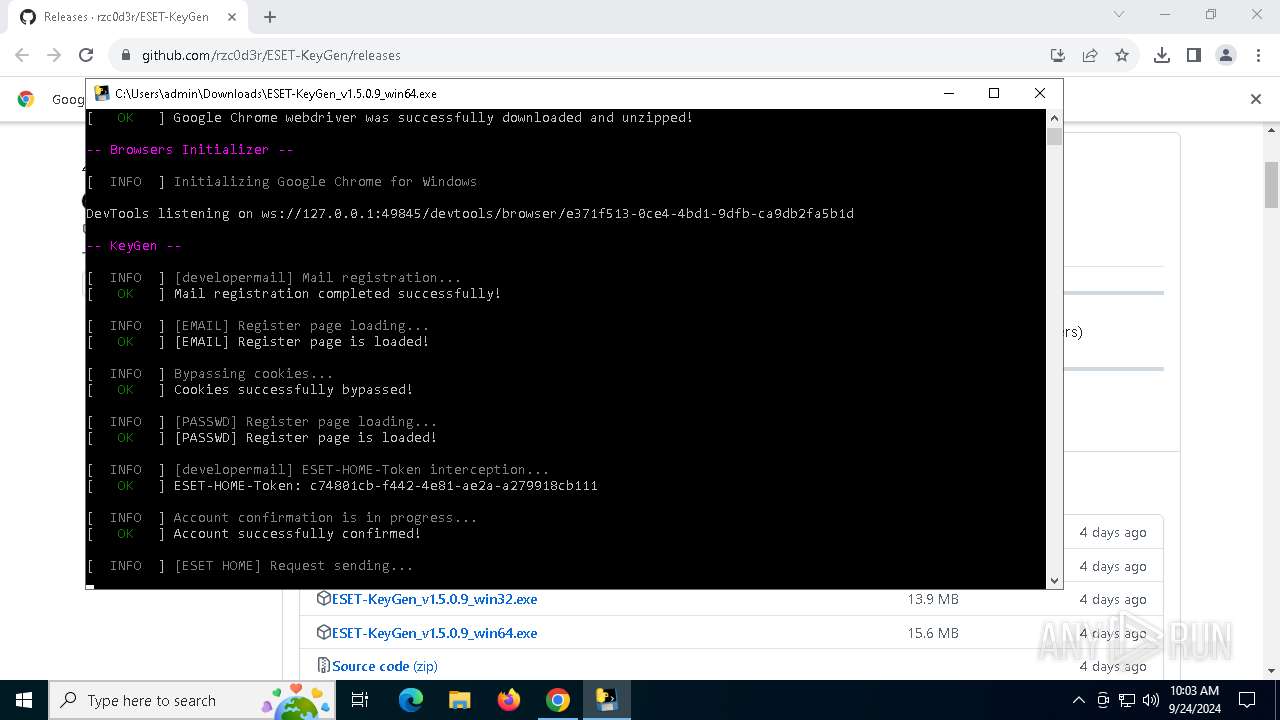
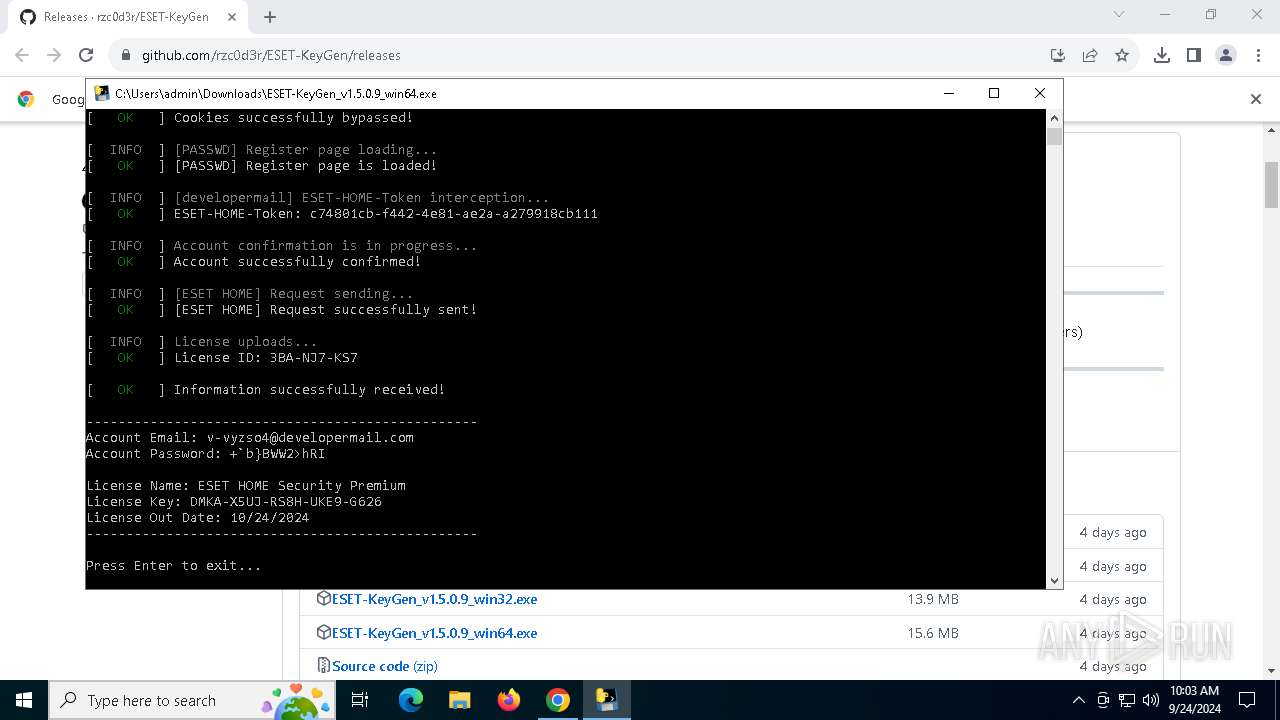
Starts CMD.EXE for commands execution
- ESET-KeyGen_v1.5.0.9_win64.exe (PID: 2960)
Application launched itself
- ESET-KeyGen_v1.5.0.9_win64.exe (PID: 3464)
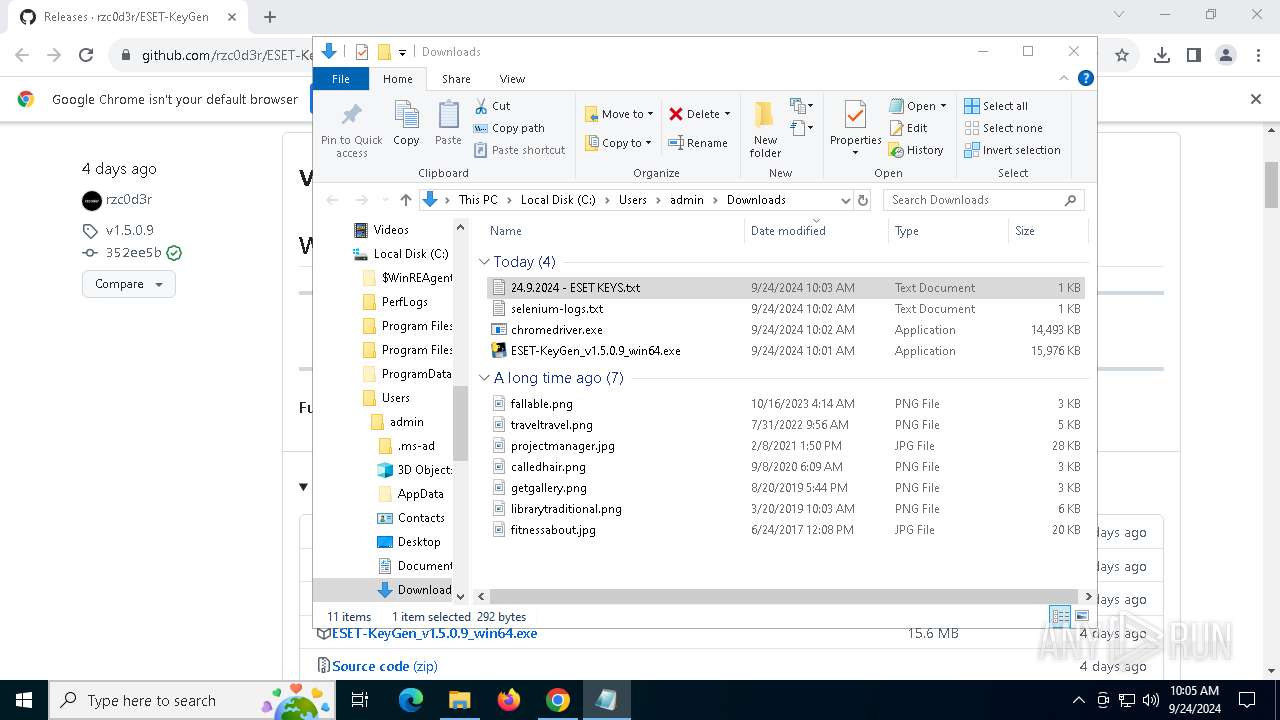
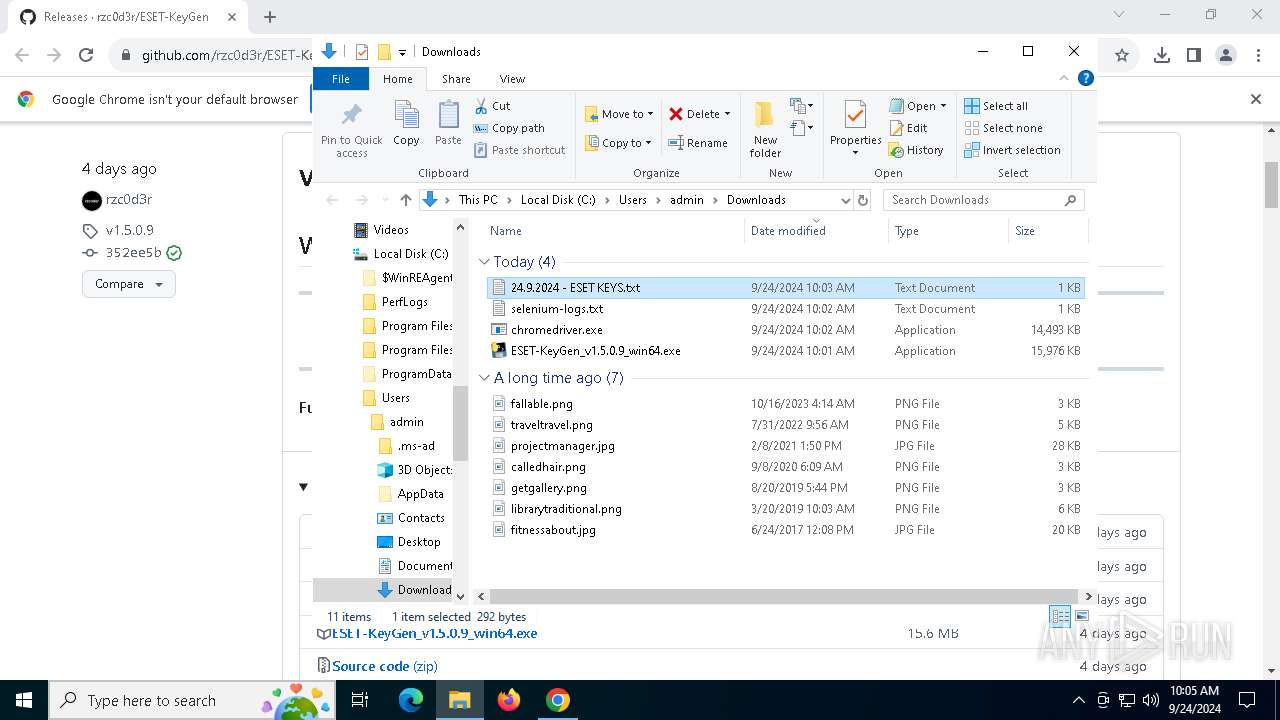
Executable content was dropped or overwritten
- ESET-KeyGen_v1.5.0.9_win64.exe (PID: 3464)
- ESET-KeyGen_v1.5.0.9_win64.exe (PID: 2960)
Process drops legitimate windows executable
- ESET-KeyGen_v1.5.0.9_win64.exe (PID: 3464)
The process drops C-runtime libraries
- ESET-KeyGen_v1.5.0.9_win64.exe (PID: 3464)
Process drops python dynamic module
- ESET-KeyGen_v1.5.0.9_win64.exe (PID: 3464)
INFO
Application launched itself
- chrome.exe (PID: 7092)
- chrome.exe (PID: 6996)
PyInstaller has been detected (YARA)
- ESET-KeyGen_v1.5.0.9_win64.exe (PID: 2960)
- ESET-KeyGen_v1.5.0.9_win64.exe (PID: 3464)
Checks operating system version
- ESET-KeyGen_v1.5.0.9_win64.exe (PID: 2960)
Manual execution by a user
- notepad.exe (PID: 2144)
- mspaint.exe (PID: 5996)
Executable content was dropped or overwritten
- chrome.exe (PID: 7092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
182
Monitored processes
44
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 32 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 360 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | ESET-KeyGen_v1.5.0.9_win64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 740 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoABAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=5232 --field-trial-handle=1904,i,6720055063144530367,9118833272710913558,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1128 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | ESET-KeyGen_v1.5.0.9_win64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1748 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=2124 --field-trial-handle=1904,i,6720055063144530367,9118833272710913558,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:3 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1964 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4884 --field-trial-handle=1904,i,6720055063144530367,9118833272710913558,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2132 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | ESET-KeyGen_v1.5.0.9_win64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
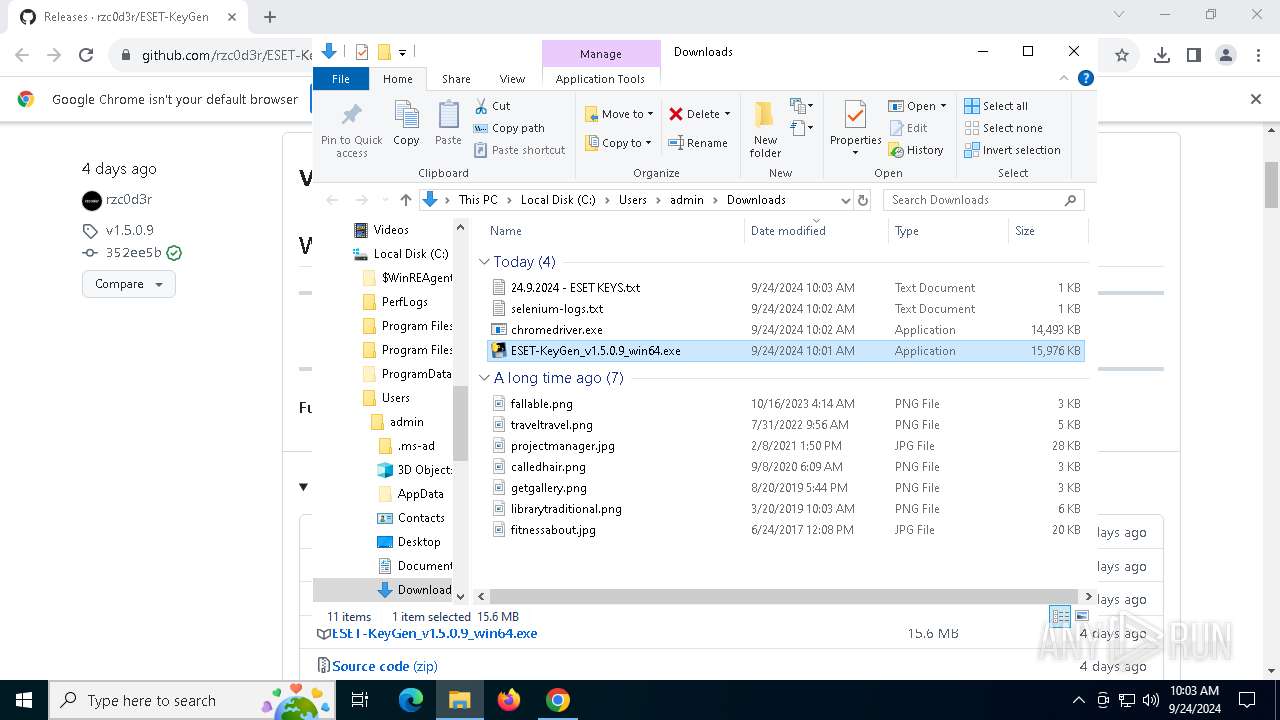
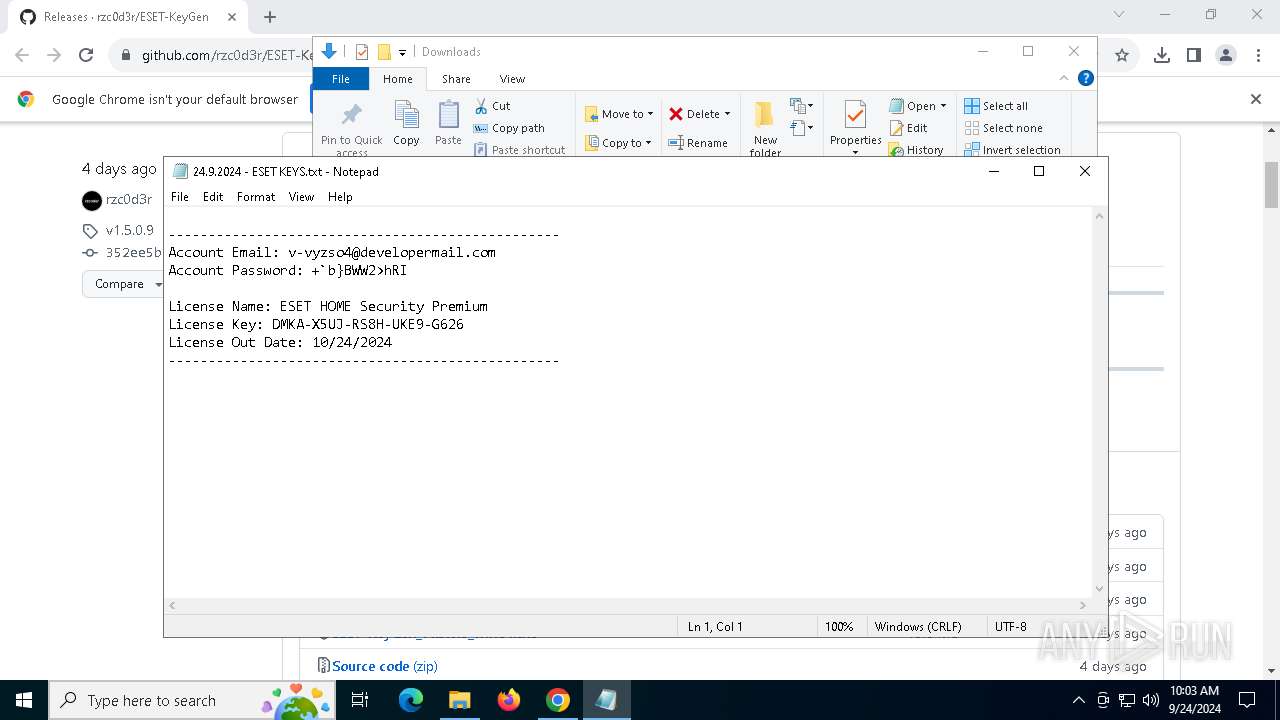
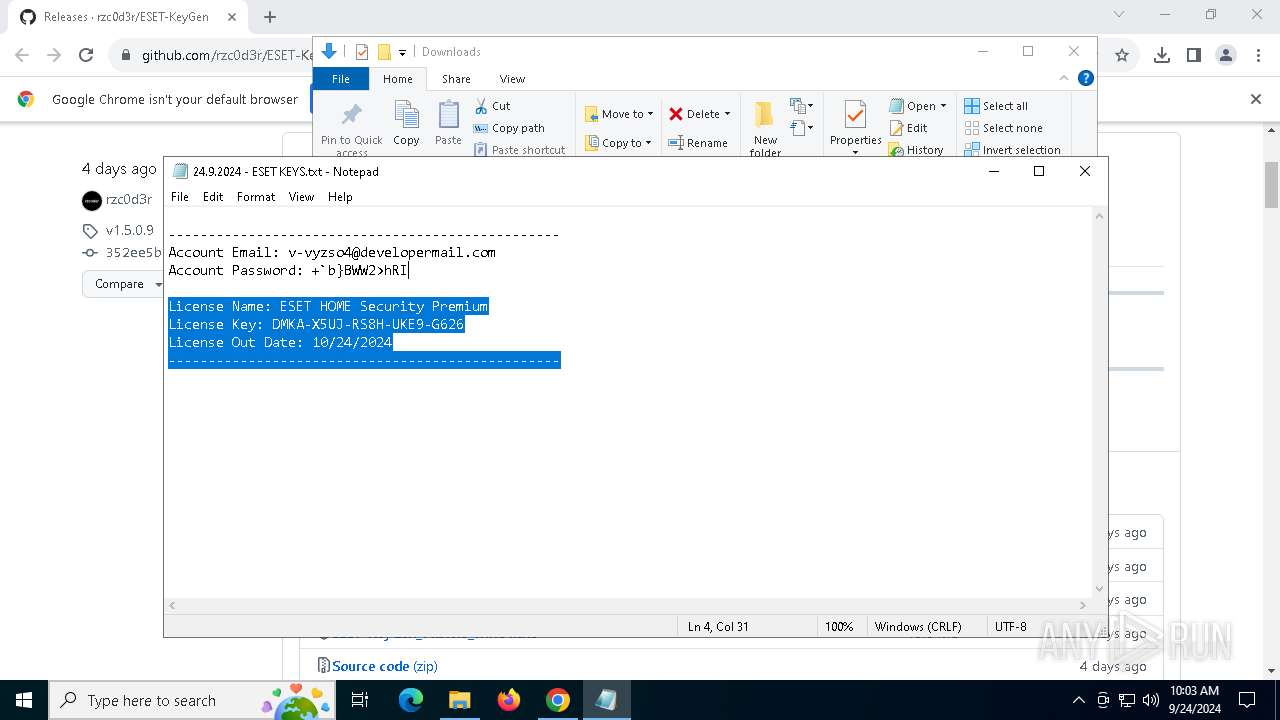
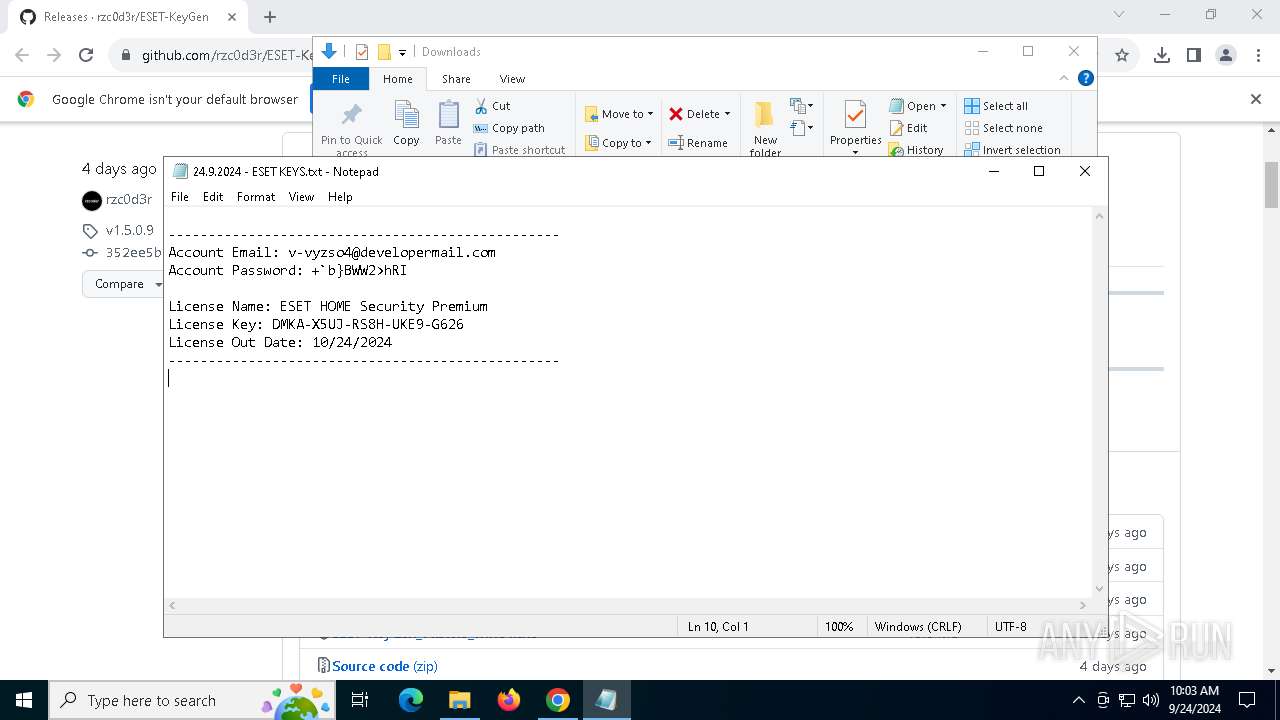
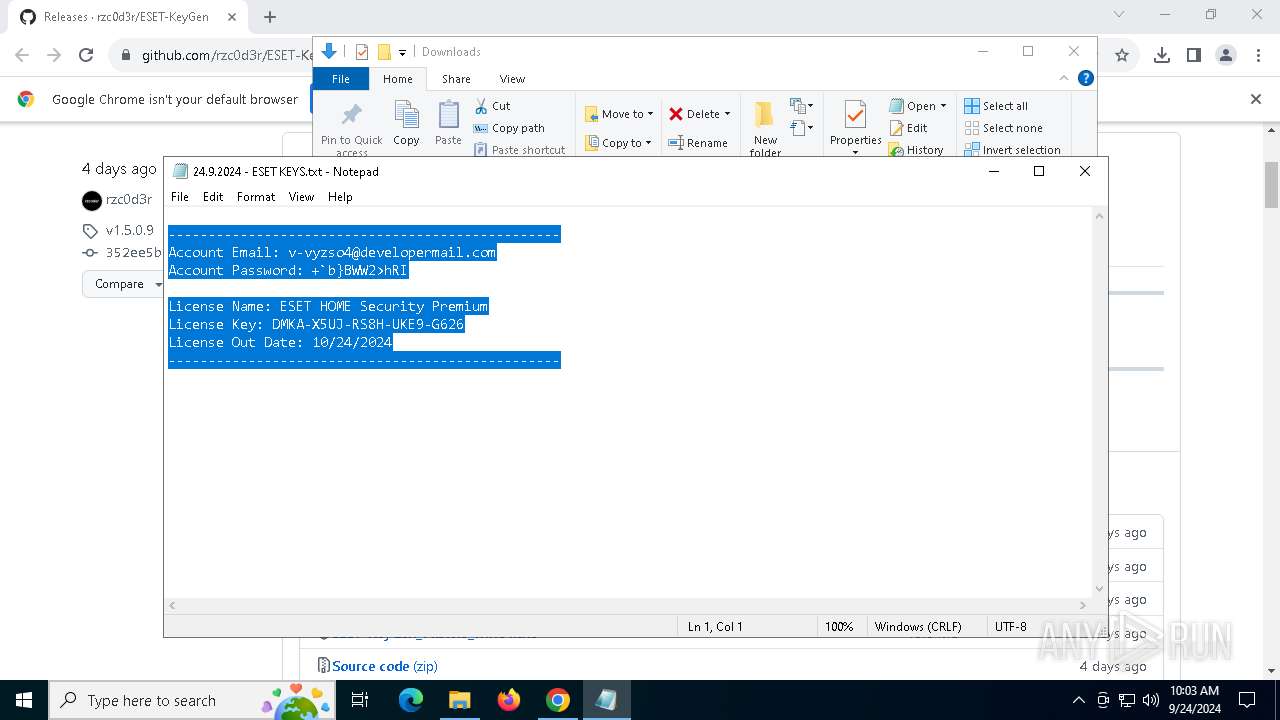
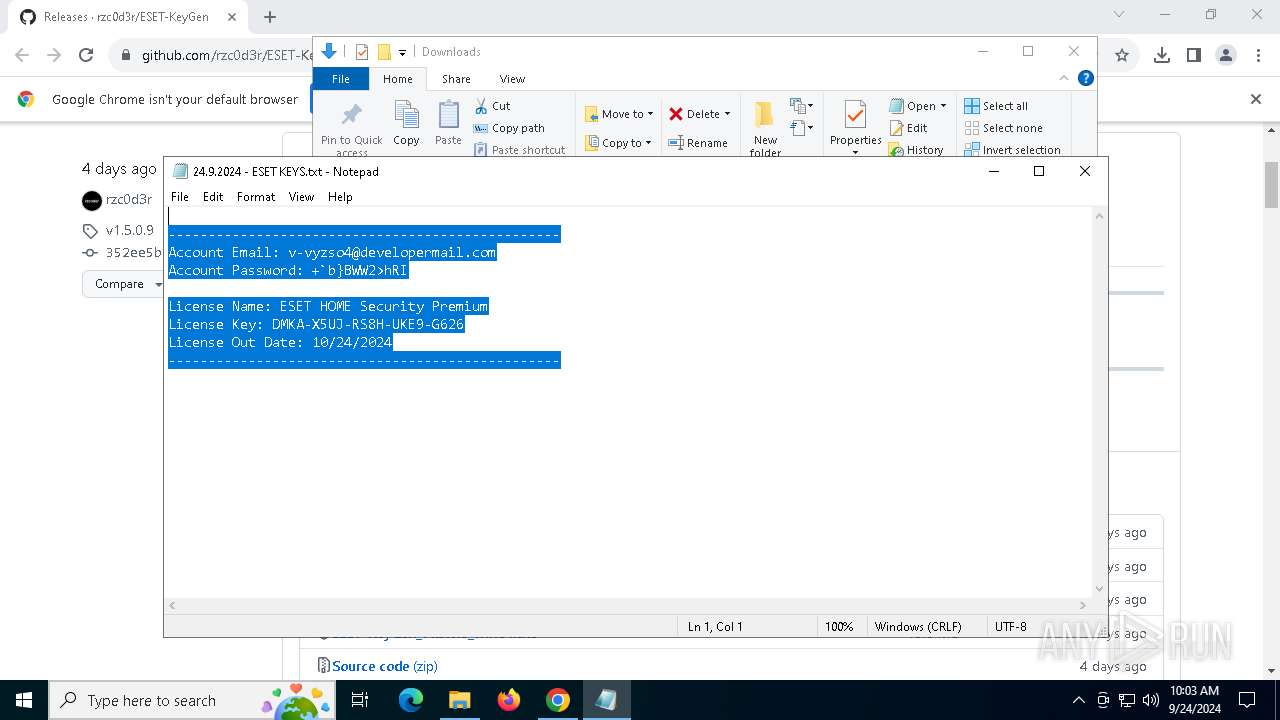
| 2144 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Downloads\24.9.2024 - ESET KEYS.txt | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2376 | C:\WINDOWS\system32\cmd.exe /c cls | C:\Windows\System32\cmd.exe | — | ESET-KeyGen_v1.5.0.9_win64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2384 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 151
Read events
11 092
Write events
51
Delete events
8
Modification events
| (PID) Process: | (7092) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7092) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7092) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7092) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (7092) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (4076) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 010000000000000049C471C6680EDB01 | |||
| (PID) Process: | (6996) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6996) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6996) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7092) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1I |
Value: 1 | |||
Executable files
66
Suspicious files
191
Text files
55
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7092 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7092 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1fd8c5.TMP | — | |
MD5:— | SHA256:— | |||
| 7092 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7092 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7092 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7092 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF1fd8e4.TMP | — | |
MD5:— | SHA256:— | |||
| 7092 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7092 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7092 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 7092 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:FC81892AC822DCBB09441D3B58B47125 | SHA256:FB077C966296D02D50CCBF7F761D2A3311A206A784A7496F331C2B0D6AD205C8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
105
DNS requests
72
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7072 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4604 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
4824 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4824 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5172 | svchost.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4604 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
4604 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
2488 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5172 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5796 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.23.209.153:443 | — | Akamai International B.V. | GB | unknown |
— | — | 20.42.65.91:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7092 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1748 | chrome.exe | 140.82.121.3:443 | github.com | GITHUB | US | shared |
1748 | chrome.exe | 142.251.31.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
github.com |
| shared |
accounts.google.com |
| whitelisted |
github.githubassets.com |
| whitelisted |
avatars.githubusercontent.com |
| whitelisted |
github-cloud.s3.amazonaws.com |
| shared |
user-images.githubusercontent.com |
| whitelisted |
content-autofill.googleapis.com |
| whitelisted |
collector.github.com |
| whitelisted |
Threats
Process | Message |
|---|---|
chrome.exe | RecursiveDirectoryCreate( C:\Users\admin\AppData\Local\Temp\scoped_dir4232_812681896 directory exists )
|