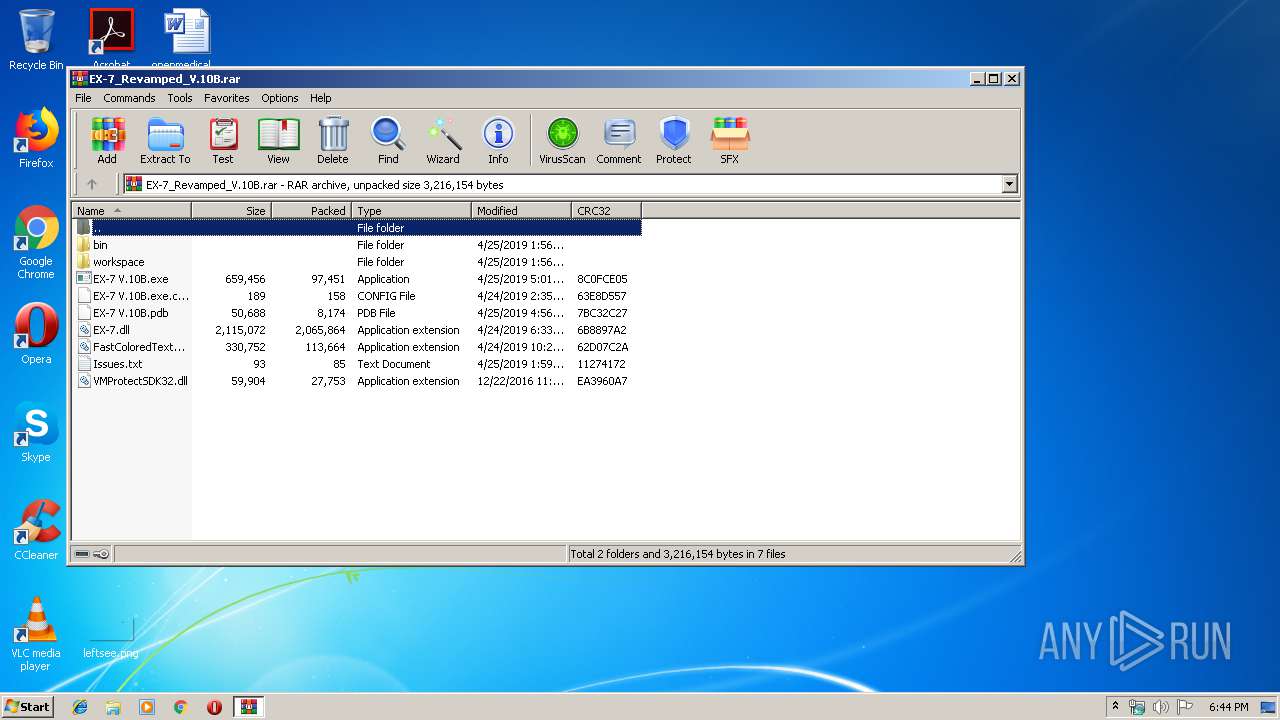
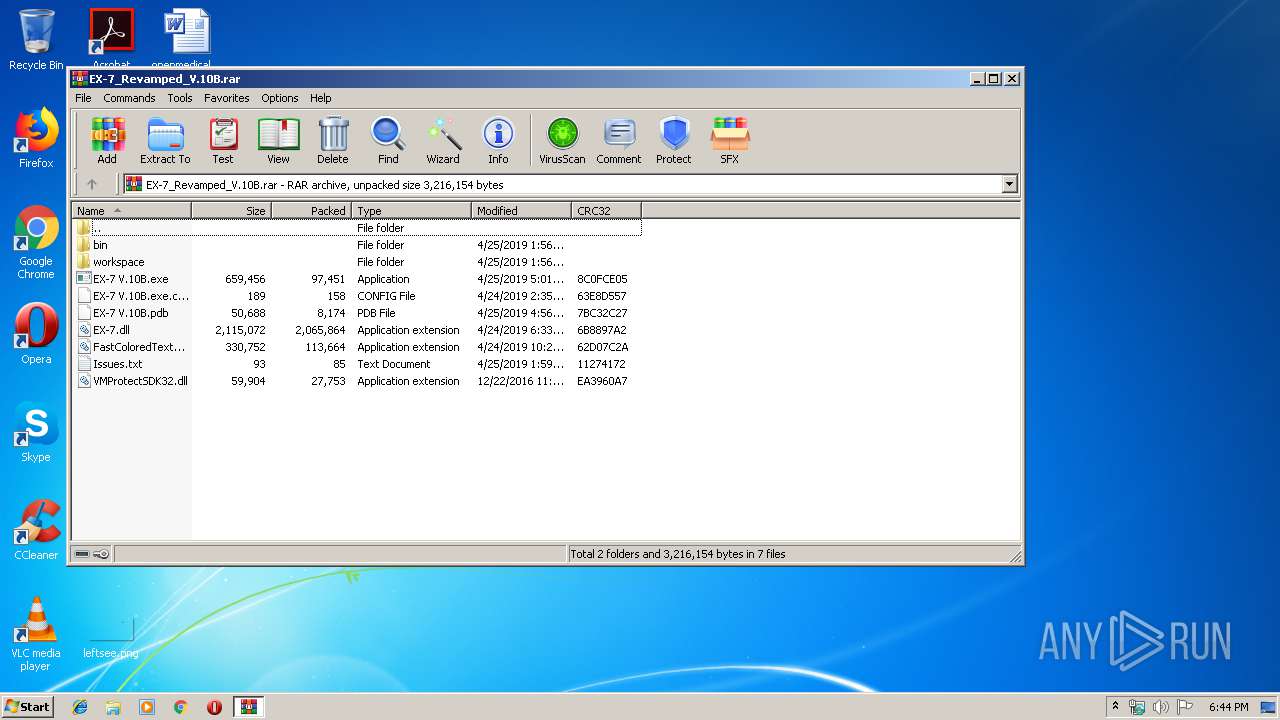
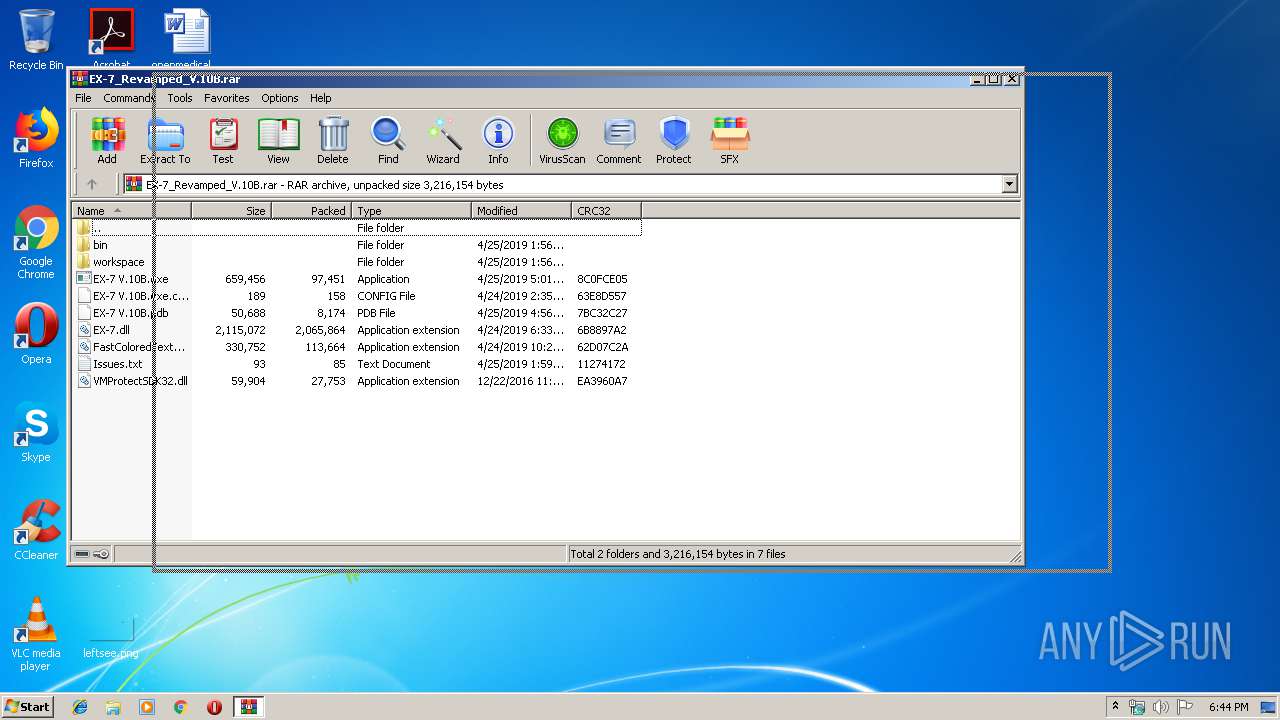
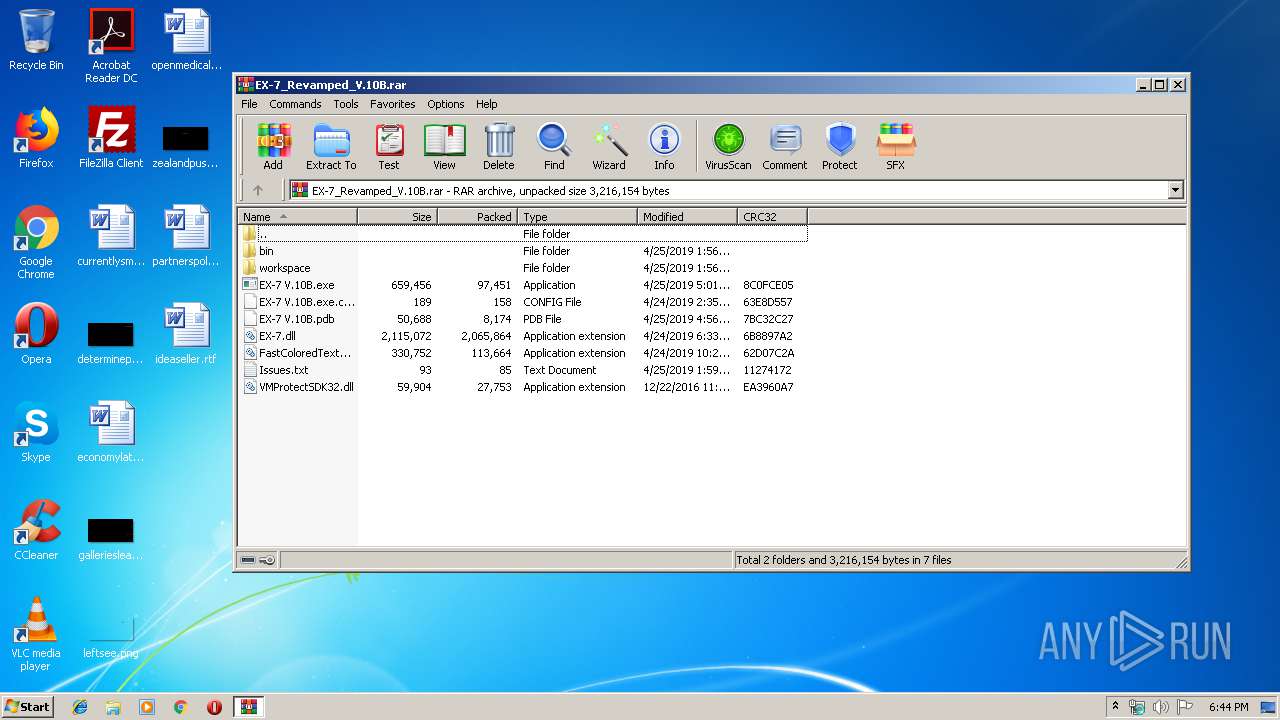
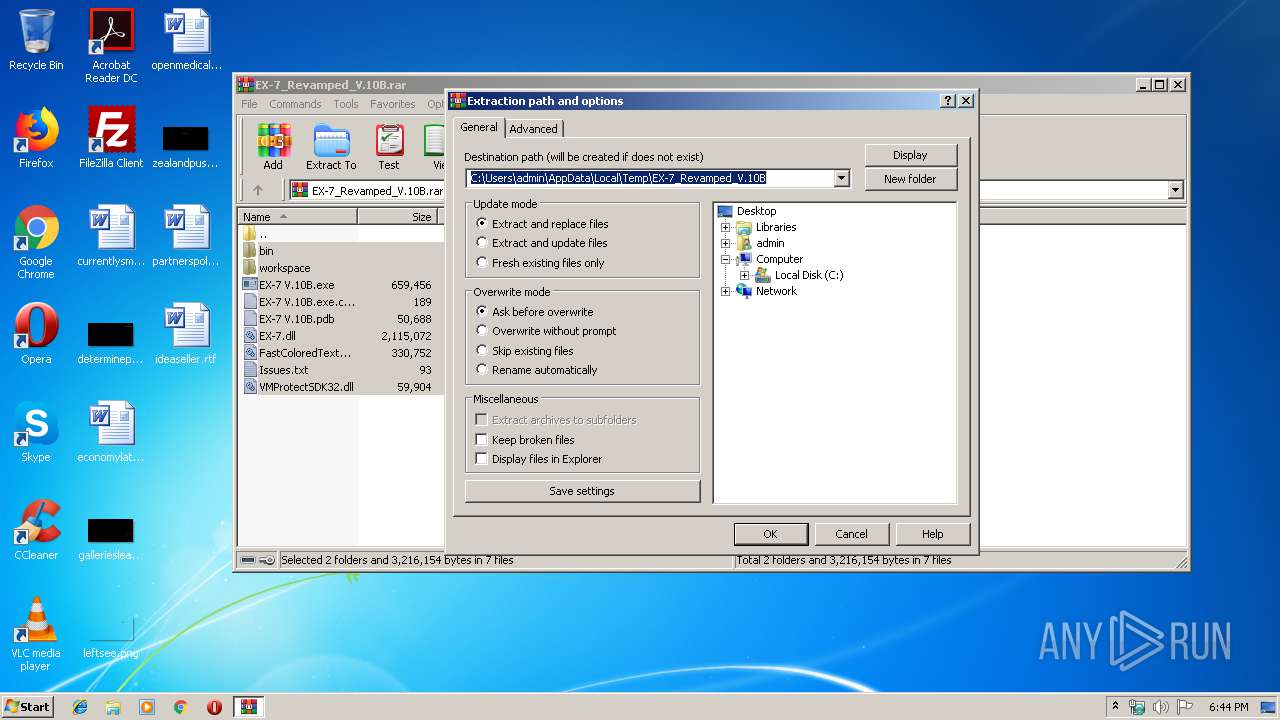
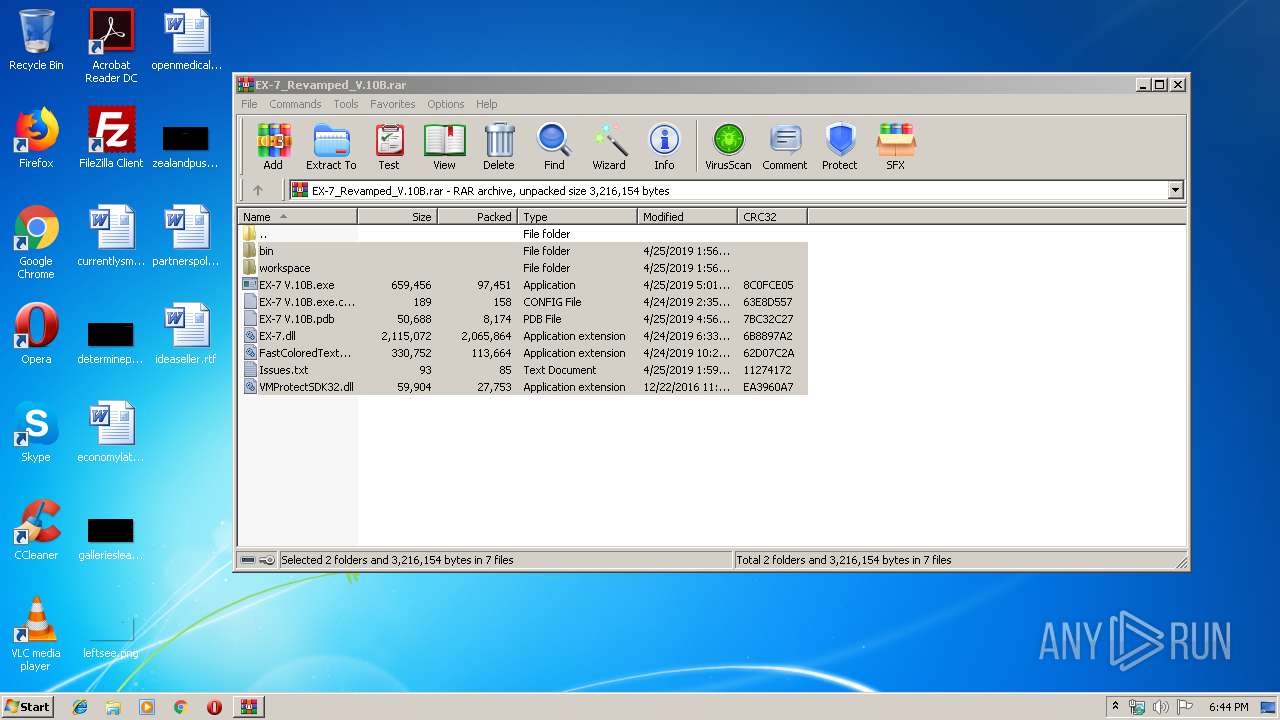
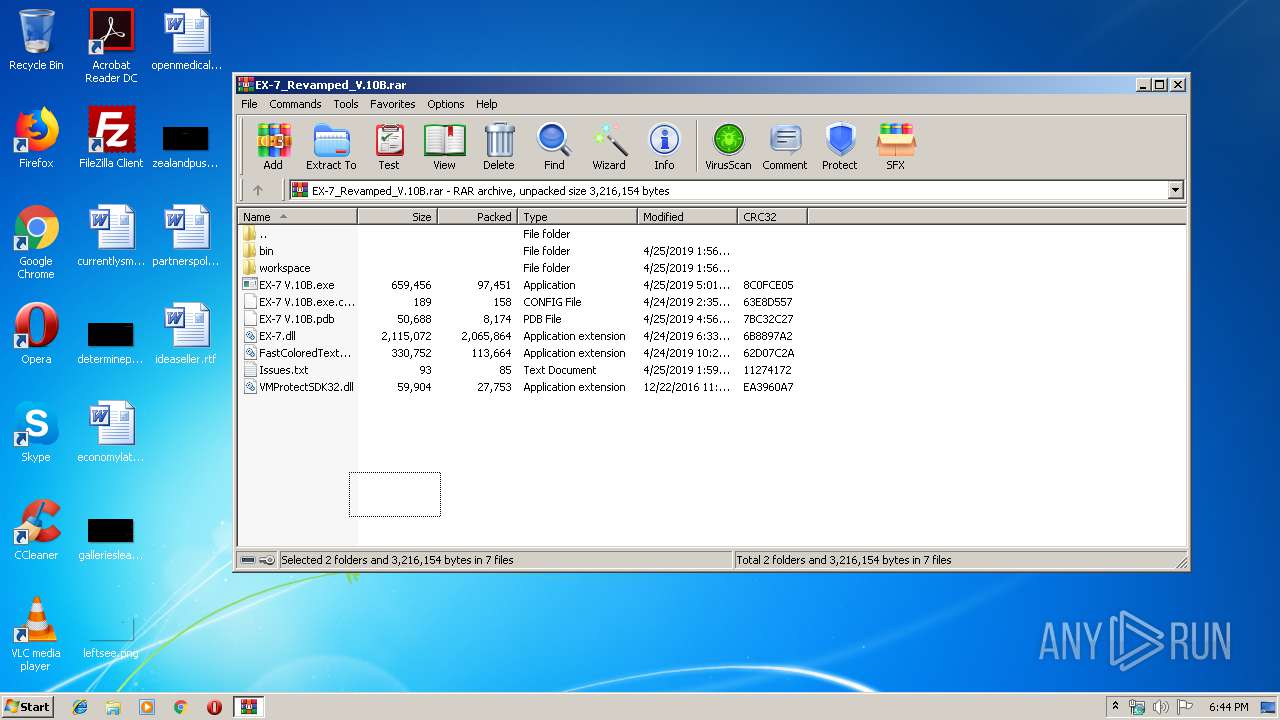
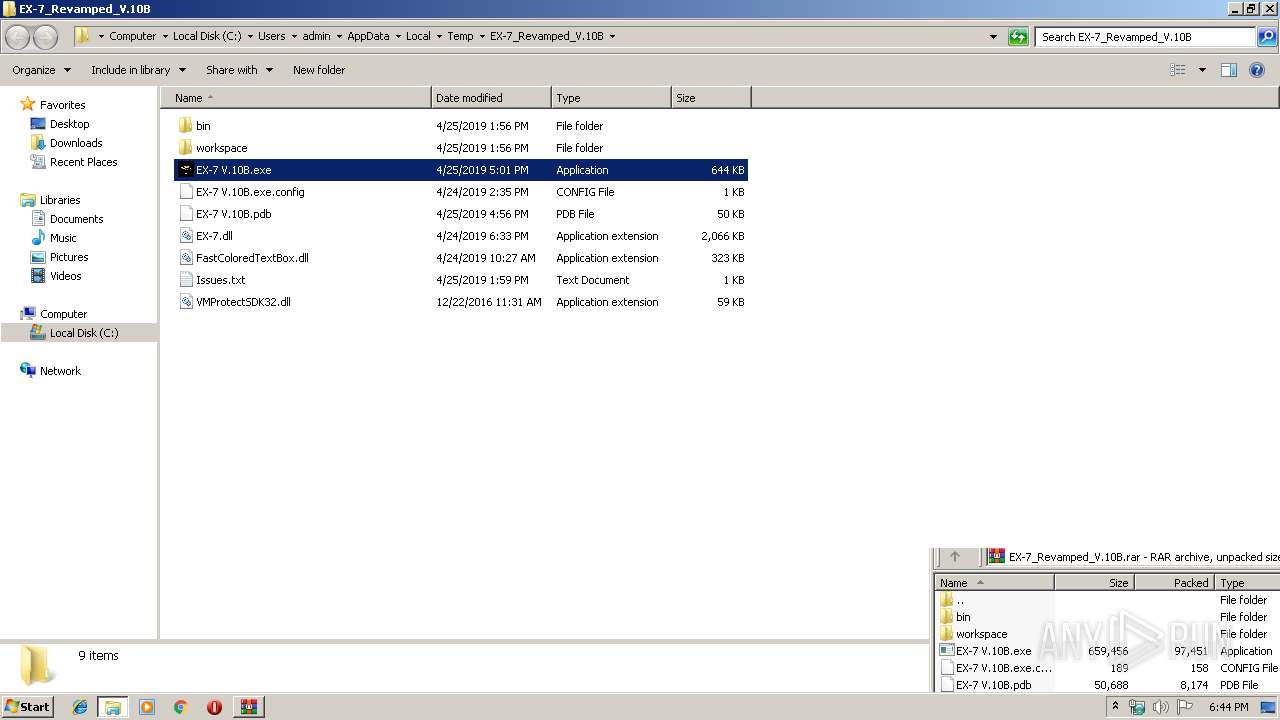
| File name: | EX-7_Revamped_V.10B.rar |
| Full analysis: | https://app.any.run/tasks/2eb09333-6278-4dca-9084-ee3dc021b4ec |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2019, 17:43:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 97FF096FF3732AFF6247E488DFE17744 |
| SHA1: | F21DBC79FC57D2CAA6A9AB09BE0C12233952425F |
| SHA256: | 7DF10299B4F2AA0765FBCEF4BB90CC85BF9175C574F16039A128756C2111076F |
| SSDEEP: | 49152:4KWf1F7JP5dPkhdQyw2tq66rD/JbM3lmqmok+Tf630:4K+1nMhdFrJ6rD/WmG/rQ0 |
MALICIOUS
Application was dropped or rewritten from another process
- EX-7 V.10B.exe (PID: 3588)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2840)
- msdt.exe (PID: 3164)
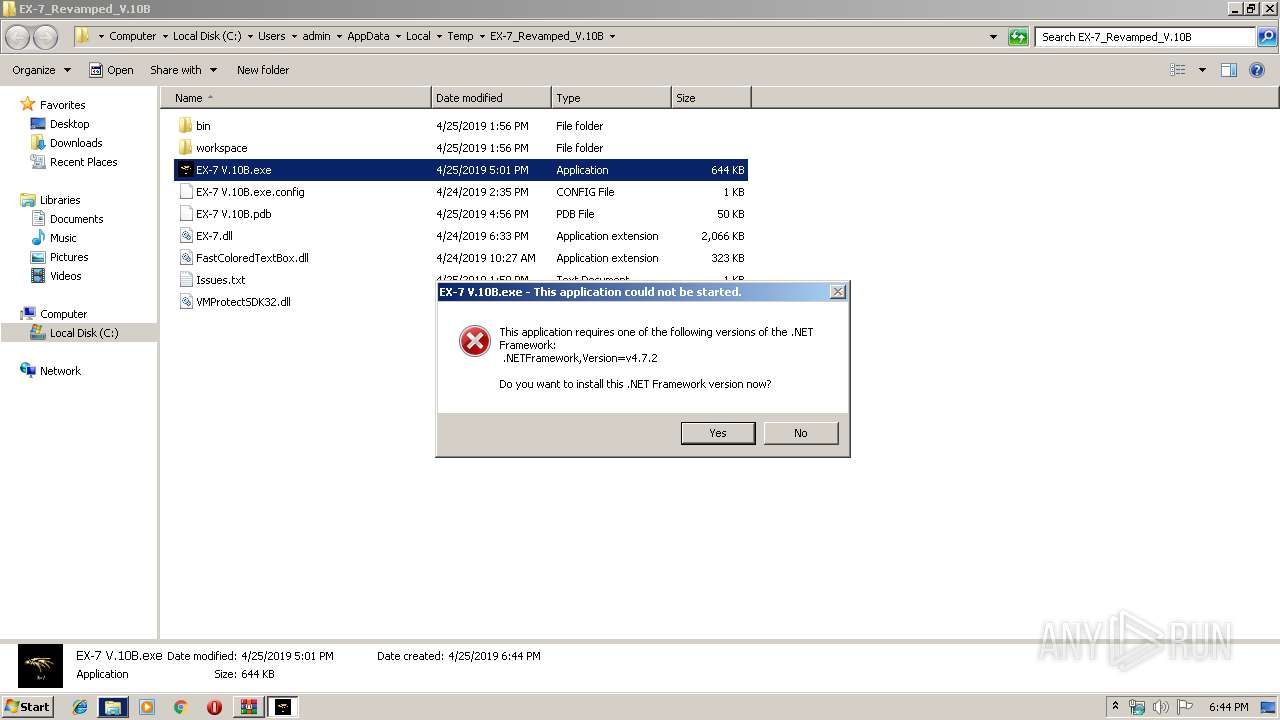
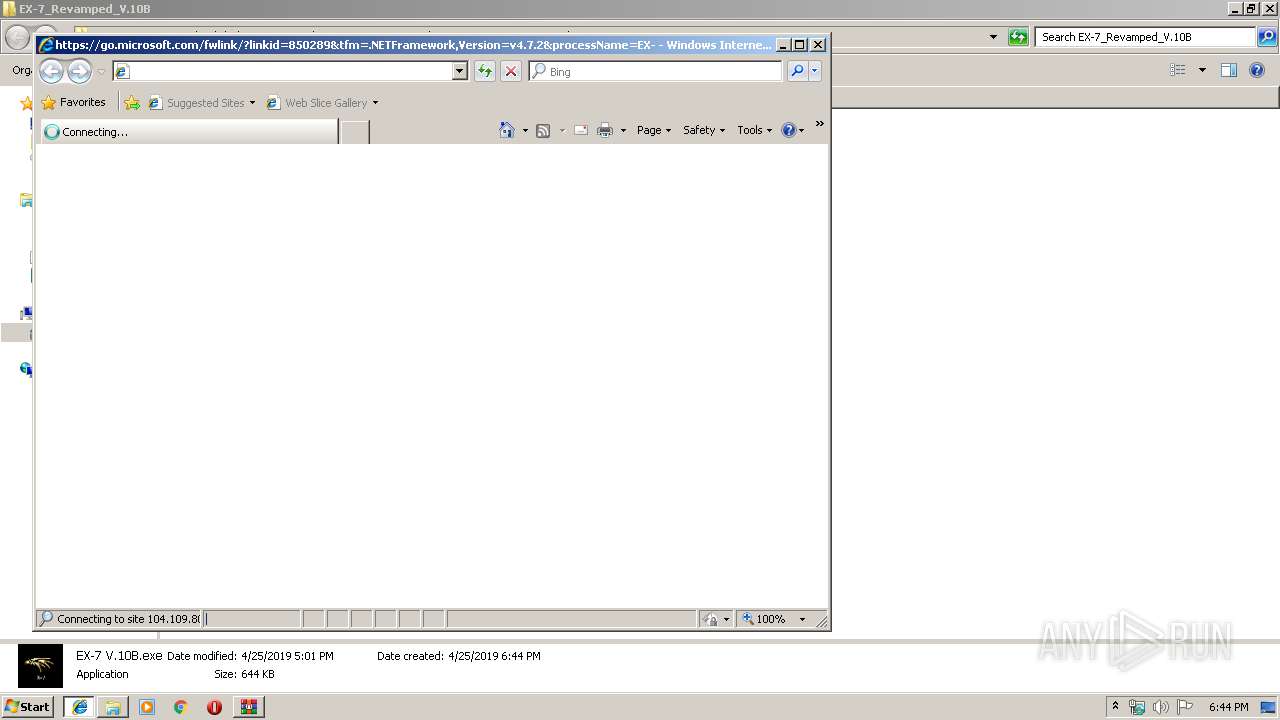
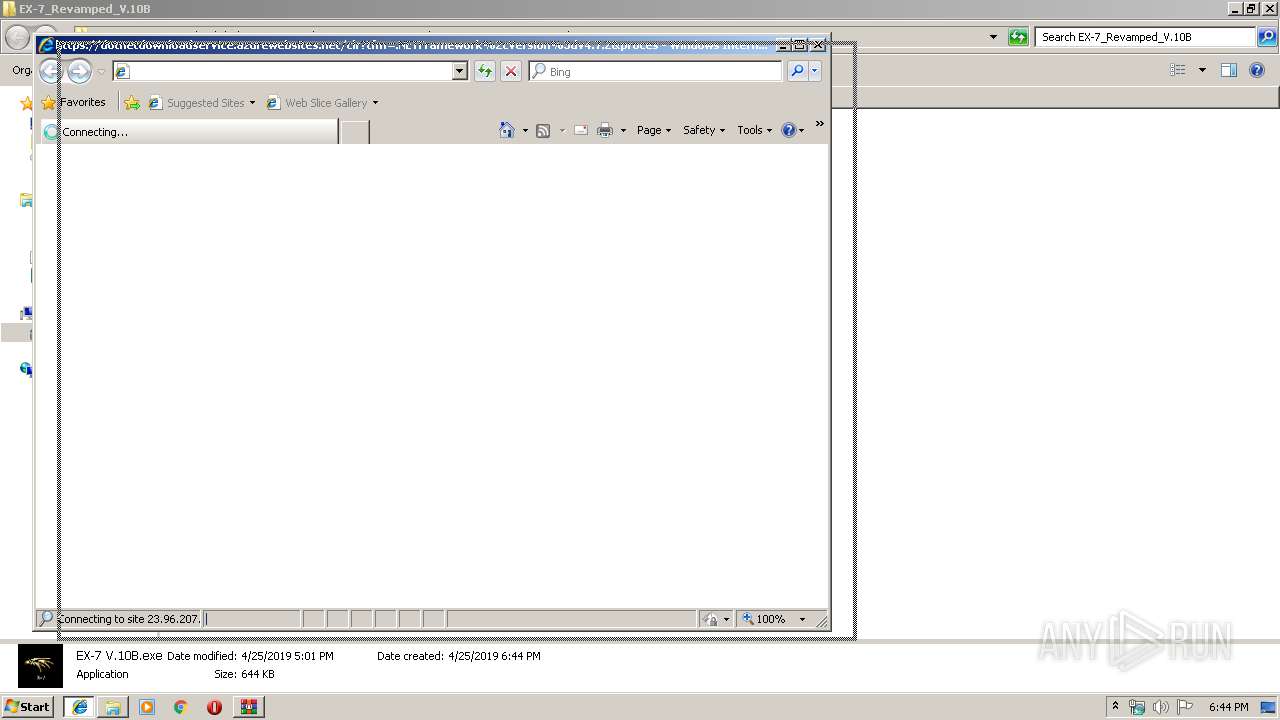
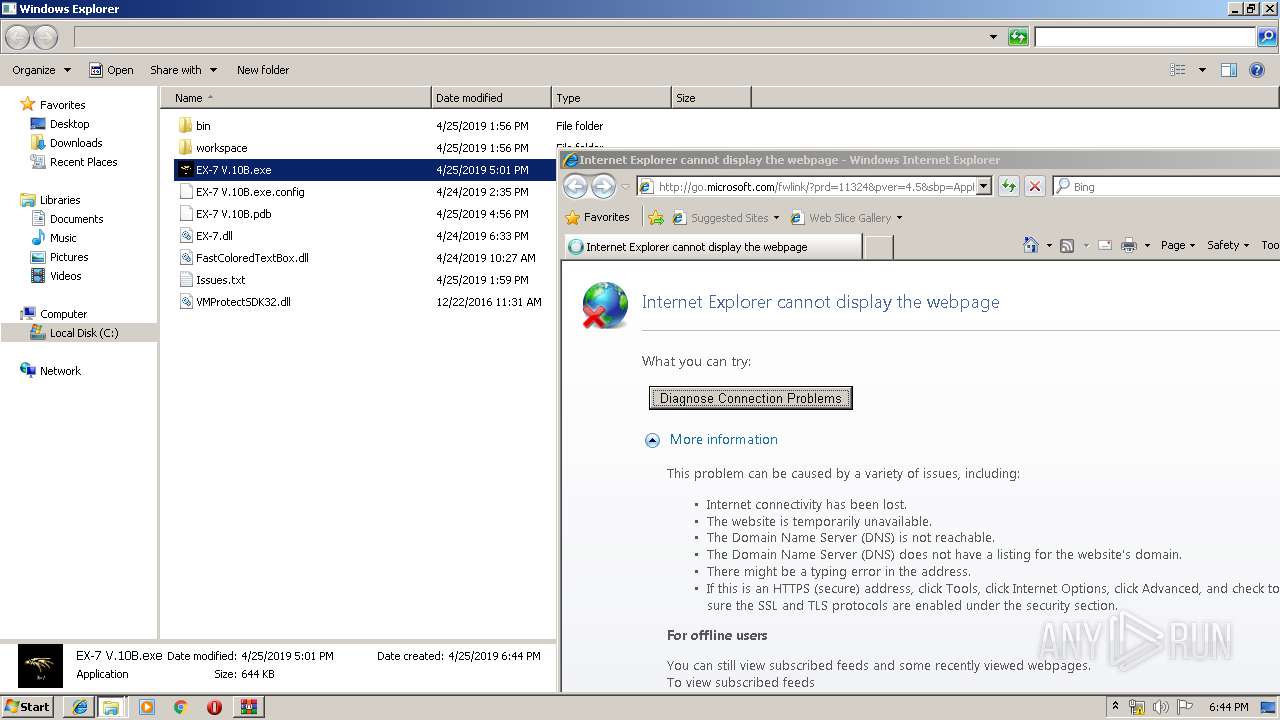
Starts Internet Explorer
- EX-7 V.10B.exe (PID: 3588)
Uses IPCONFIG.EXE to discover IP address
- sdiagnhost.exe (PID: 3388)
INFO
Creates files in the user directory
- iexplore.exe (PID: 992)
Reads Internet Cache Settings
- iexplore.exe (PID: 992)
Changes internet zones settings
- iexplore.exe (PID: 3016)
Reads internet explorer settings
- iexplore.exe (PID: 992)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
45
Monitored processes
12
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 992 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3016 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2416 | "C:\Windows\System32\rundll32.exe" werconcpl.dll, LaunchErcApp -queuereporting | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2836 | "C:\Windows\system32\makecab.exe" /f NetworkConfiguration.ddf | C:\Windows\system32\makecab.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Cabinet Maker Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2840 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\EX-7_Revamped_V.10B.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2904 | "C:\Windows\system32\ipconfig.exe" /all | C:\Windows\system32\ipconfig.exe | — | sdiagnhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3016 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | EX-7 V.10B.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3072 | "C:\Windows\System32\control.exe" /name Microsoft.Troubleshooting /page "resultPage?keywords=+;NetworkDiagnostics" | C:\Windows\System32\control.exe | — | msdt.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Control Panel Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3164 | -modal 131544 -skip TRUE -path C:\Windows\diagnostics\system\networking -af C:\Users\admin\AppData\Local\Temp\NDFC2B7.tmp -ep NetworkDiagnosticsWeb | C:\Windows\system32\msdt.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Diagnostics Troubleshooting Wizard Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3200 | "C:\Windows\system32\verclsid.exe" /S /C {0B2C9183-C9FA-4C53-AE21-C900B0C39965} /I {0C733A8A-2A1C-11CE-ADE5-00AA0044773D} /X 0x401 | C:\Windows\system32\verclsid.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Extension CLSID Verification Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3388 | C:\Windows\System32\sdiagnhost.exe -Embedding | C:\Windows\System32\sdiagnhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Scripted Diagnostics Native Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 103
Read events
1 020
Write events
83
Delete events
0
Modification events
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\EX-7_Revamped_V.10B.rar | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
| (PID) Process: | (2840) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\EX-7_Revamped_V.10B | |||
Executable files
6
Suspicious files
9
Text files
58
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3016 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3016 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2840 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\EX-7_Revamped_V.10B\VMProtectSDK32.dll | executable | |
MD5:— | SHA256:— | |||
| 992 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 992 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2840 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\EX-7_Revamped_V.10B\Issues.txt | text | |
MD5:— | SHA256:— | |||
| 2840 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\EX-7_Revamped_V.10B\EX-7.dll | executable | |
MD5:— | SHA256:— | |||
| 2840 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\EX-7_Revamped_V.10B\EX-7 V.10B.pdb | pdb | |
MD5:— | SHA256:— | |||
| 2840 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\EX-7_Revamped_V.10B\EX-7 V.10B.exe | executable | |
MD5:— | SHA256:— | |||
| 992 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\SBE1OA30\desktop.ini | ini | |
MD5:4A3DEB274BB5F0212C2419D3D8D08612 | SHA256:2842973D15A14323E08598BE1DFB87E54BF88A76BE8C7BC94C56B079446EDF38 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
13
DNS requests
4
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
976 | svchost.exe | GET | 302 | 104.109.80.115:80 | http://go.microsoft.com/ | NL | — | — | whitelisted |
992 | iexplore.exe | GET | 302 | 104.109.80.115:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=4.5&sbp=AppLaunch&plcid=0x409&o1=.NETFramework,Version=v4.7.2&processName=EX-7%20V.10B.exe&platform=0000&osver=5&isServer=0&shimver=4.0.30319.0 | NL | — | — | whitelisted |
992 | iexplore.exe | GET | 302 | 104.109.80.115:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=4.5&sbp=AppLaunch&plcid=0x409&o1=.NETFramework,Version=v4.7.2&processName=EX-7%20V.10B.exe&platform=0000&osver=5&isServer=0&shimver=4.0.30319.0 | NL | — | — | whitelisted |
3016 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
976 | svchost.exe | GET | 200 | 2.23.106.83:80 | http://www.microsoft.com/ | unknown | html | 1020 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3016 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
992 | iexplore.exe | 104.109.80.115:80 | go.microsoft.com | Akamai International B.V. | NL | whitelisted |
992 | iexplore.exe | 104.109.80.115:443 | go.microsoft.com | Akamai International B.V. | NL | whitelisted |
992 | iexplore.exe | 23.96.207.177:443 | dotnetdownloadservice.azurewebsites.net | Microsoft Corporation | US | whitelisted |
976 | svchost.exe | 104.109.80.115:80 | go.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 23.96.207.177:443 | dotnetdownloadservice.azurewebsites.net | Microsoft Corporation | US | whitelisted |
976 | svchost.exe | 2.23.106.83:80 | www.microsoft.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
dotnetdownloadservice.azurewebsites.net |
| unknown |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
976 | svchost.exe | A Network Trojan was detected | ET POLICY Microsoft user-agent automated process response to automated request |