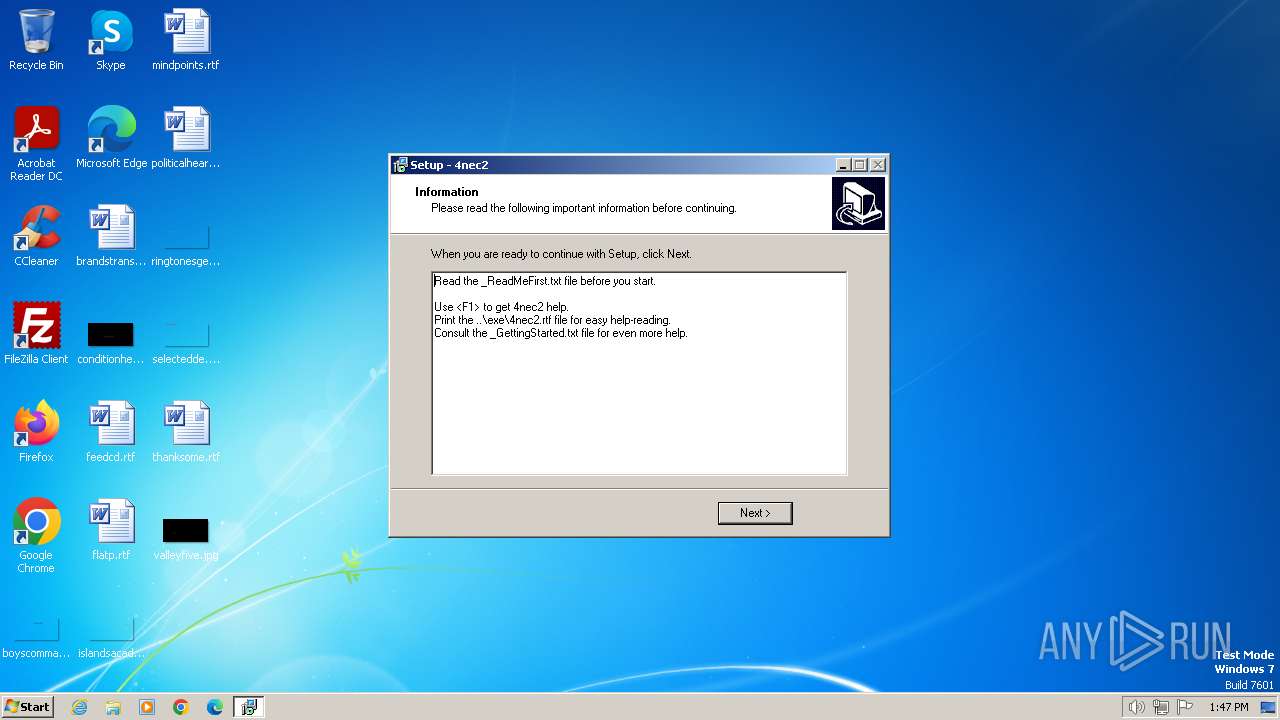
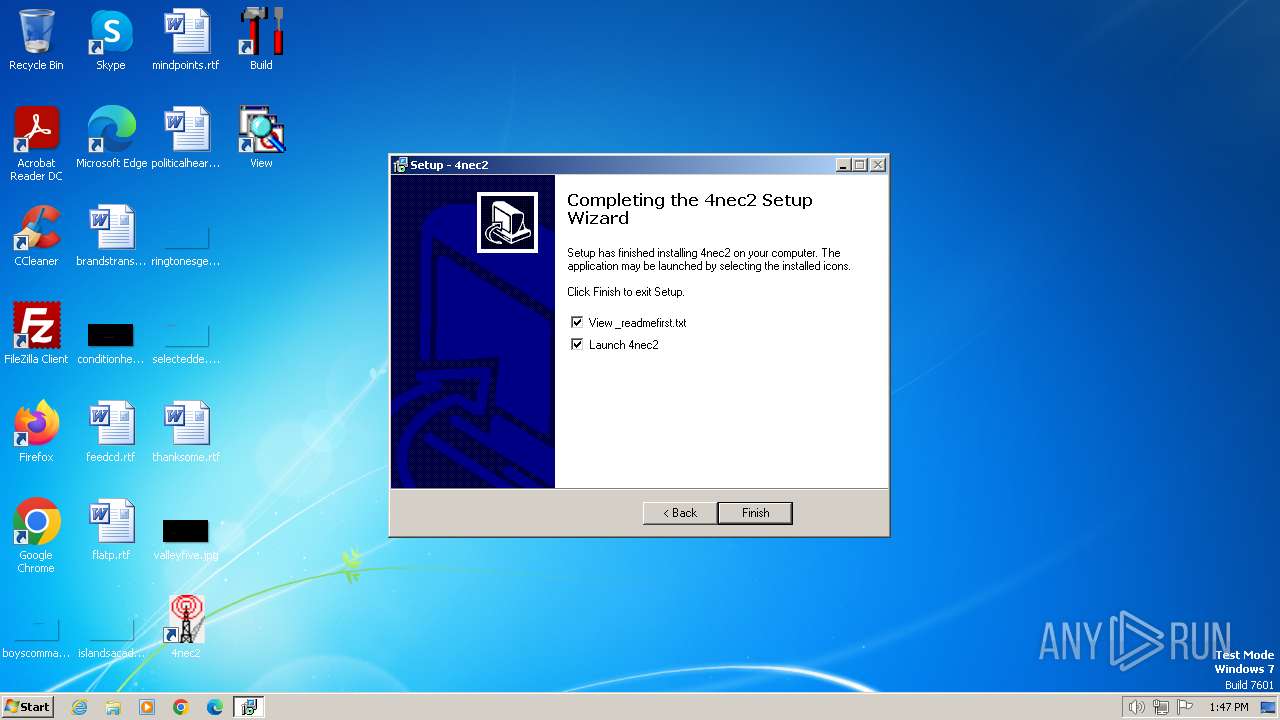
| File name: | Setup_4nec2.exe |
| Full analysis: | https://app.any.run/tasks/92b2534e-f619-4ec0-ad9f-0f3b532e4b42 |
| Verdict: | Malicious activity |
| Analysis date: | January 21, 2024, 13:46:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | D9C1CB4AB1777143F9C81C993C9CD64B |
| SHA1: | 66680AEA502FE6E2F3CD649F5FCC0FED4473DE64 |
| SHA256: | 7DE2860311D0FF1F764F38CC20ED27CBB9F68F7BF2145AFD97736268FA9E5BAD |
| SSDEEP: | 98304:0u0sa7EmVumMpJ1e8nCcE+QI43RVfrYykEtBUYDH2oTAnGlySZaGZf8mLgsKbpIf:w8URYqH |
MALICIOUS
Drops the executable file immediately after the start
- Setup_4nec2.exe (PID: 116)
- Setup_4nec2.exe (PID: 1380)
- Setup_4nec2.tmp (PID: 548)
Creates a writable file in the system directory
- Setup_4nec2.tmp (PID: 548)
Registers / Runs the DLL via REGSVR32.EXE
- Setup_4nec2.tmp (PID: 548)
SUSPICIOUS
Executable content was dropped or overwritten
- Setup_4nec2.exe (PID: 1380)
- Setup_4nec2.exe (PID: 116)
- Setup_4nec2.tmp (PID: 548)
Process drops legitimate windows executable
- Setup_4nec2.tmp (PID: 548)
Reads the Windows owner or organization settings
- Setup_4nec2.tmp (PID: 548)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 1264)
Start notepad (likely ransomware note)
- Setup_4nec2.tmp (PID: 1072)
INFO
Create files in a temporary directory
- Setup_4nec2.exe (PID: 116)
- Setup_4nec2.exe (PID: 1380)
- Setup_4nec2.tmp (PID: 548)
- 4nec2.exe (PID: 848)
Checks supported languages
- Setup_4nec2.exe (PID: 116)
- Setup_4nec2.tmp (PID: 1072)
- Setup_4nec2.exe (PID: 1380)
- Setup_4nec2.tmp (PID: 548)
- 4nec2.exe (PID: 848)
Reads the computer name
- Setup_4nec2.tmp (PID: 1072)
- Setup_4nec2.tmp (PID: 548)
Creates files in the program directory
- Setup_4nec2.tmp (PID: 548)
Manual execution by a user
- chrome.exe (PID: 2344)
Reads the machine GUID from the registry
- 4nec2.exe (PID: 848)
Application launched itself
- chrome.exe (PID: 2344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (77.7) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10) |
| .dll | | | Win32 Dynamic Link Library (generic) (4.6) |
| .exe | | | Win32 Executable (generic) (3.1) |
| .exe | | | Win16/32 Executable Delphi generic (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 37888 |
| InitializedDataSize: | 17920 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9b24 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | 4nec2@gmx.net (Use "4nec2 modeller" as the subject) |
| FileDescription: | 4nec2 Setup |
| FileVersion: | |
| LegalCopyright: | |
| ProductName: | 4nec2 |
| ProductVersion: |
Total processes
65
Monitored processes
29
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Users\admin\AppData\Local\Temp\Setup_4nec2.exe" | C:\Users\admin\AppData\Local\Temp\Setup_4nec2.exe | explorer.exe | ||||||||||||
User: admin Company: 4nec2@gmx.net (Use "4nec2 modeller" as the subject) Integrity Level: MEDIUM Description: 4nec2 Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 548 | "C:\Users\admin\AppData\Local\Temp\is-D2BQ7.tmp\Setup_4nec2.tmp" /SL5="$601B2,4052503,54272,C:\Users\admin\AppData\Local\Temp\Setup_4nec2.exe" /SPAWNWND=$401AE /NOTIFYWND=$301AA | C:\Users\admin\AppData\Local\Temp\is-D2BQ7.tmp\Setup_4nec2.tmp | Setup_4nec2.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.50.0.0 Modules
| |||||||||||||||
| 764 | "C:\Windows\system32\regsvr32.exe" /s "C:\Windows\system32\Tabctl32.ocx" | C:\Windows\System32\regsvr32.exe | — | Setup_4nec2.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 848 | "C:\4nec2\exe\4nec2.exe" | C:\4nec2\exe\4nec2.exe | — | Setup_4nec2.tmp | |||||||||||
User: admin Company: 4nec2@gmx.net Integrity Level: MEDIUM Description: 4nec2 antenna visualizer Exit code: 0 Version: 5.09.0003 Modules
| |||||||||||||||
| 980 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2204 --field-trial-handle=1160,i,9949062933658777860,5986590962253614258,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1072 | "C:\Users\admin\AppData\Local\Temp\is-HN1R6.tmp\Setup_4nec2.tmp" /SL5="$301AA,4052503,54272,C:\Users\admin\AppData\Local\Temp\Setup_4nec2.exe" | C:\Users\admin\AppData\Local\Temp\is-HN1R6.tmp\Setup_4nec2.tmp | — | Setup_4nec2.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.50.0.0 Modules
| |||||||||||||||
| 1220 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=angle --use-angle=swiftshader-webgl --mojo-platform-channel-handle=1420 --field-trial-handle=1160,i,9949062933658777860,5986590962253614258,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1232 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=1620 --field-trial-handle=1160,i,9949062933658777860,5986590962253614258,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1264 | "C:\Windows\system32\regsvr32.exe" /s "C:\Windows\system32\Msvbvm60.dll" | C:\Windows\System32\regsvr32.exe | — | Setup_4nec2.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1380 | "C:\Users\admin\AppData\Local\Temp\Setup_4nec2.exe" /SPAWNWND=$401AE /NOTIFYWND=$301AA | C:\Users\admin\AppData\Local\Temp\Setup_4nec2.exe | Setup_4nec2.tmp | ||||||||||||
User: admin Company: 4nec2@gmx.net (Use "4nec2 modeller" as the subject) Integrity Level: HIGH Description: 4nec2 Setup Exit code: 0 Version: Modules
| |||||||||||||||
Total events
3 573
Read events
3 508
Write events
60
Delete events
5
Modification events
| (PID) Process: | (1840) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{6262D3A0-531B-11CF-91F6-C2863C385E30} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1840) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{6319EEA0-531B-11CF-91F6-C2863C385E30} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1840) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{275DBBA0-805A-11CF-91F7-C2863C385E30} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (1840) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{2334D2B1-713E-11CF-8AE5-00AA00C00905}\TypeLib |
| Operation: | write | Name: | Version |
Value: 2.0 | |||
| (PID) Process: | (1840) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{2334D2B3-713E-11CF-8AE5-00AA00C00905}\TypeLib |
| Operation: | write | Name: | Version |
Value: 2.0 | |||
| (PID) Process: | (764) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{BDC217C5-ED16-11CD-956C-0000C04E4C0A} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (764) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{7DA06D40-54A0-11CF-A521-0080C77A7786} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (764) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{2334D2B1-713E-11CF-8AE5-00AA00C00905}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (764) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{2334D2B3-713E-11CF-8AE5-00AA00C00905}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (1264) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D5DE8D20-5BB8-11D1-A1E3-00A0C90F2731}\InProcServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: Apartment | |||
Executable files
47
Suspicious files
192
Text files
1 188
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 548 | Setup_4nec2.tmp | C:\4nec2\unins000.exe | executable | |
MD5:FBA1DE70F5BB8544A9753957F269F897 | SHA256:87931B032A78E11A4DD491E21A66A9F24DF3FFBBEF61B5672BFE286E3903953B | |||
| 1380 | Setup_4nec2.exe | C:\Users\admin\AppData\Local\Temp\is-D2BQ7.tmp\Setup_4nec2.tmp | executable | |
MD5:ED69E64731547EBA52476A2D2A2F7882 | SHA256:427FA988A8A8C63393693FFEB61DDEC195F000220EE55FD5112EC91682E933B0 | |||
| 548 | Setup_4nec2.tmp | C:\4nec2\is-39MFL.tmp | text | |
MD5:7B261CD7A69AE1202BC8AAAA91ADDCD9 | SHA256:2E89E62367C5F240EACA316002067C1232FF70A3AFE8B7AAFCC20AAD3166D289 | |||
| 548 | Setup_4nec2.tmp | C:\4nec2\_GetStarted.txt | text | |
MD5:24271E8E18AB43467B56986506742112 | SHA256:B894338A61A08A28EC4788A794FAC455BA5C7E115785B1A3ABB205E7DB532981 | |||
| 548 | Setup_4nec2.tmp | C:\4nec2\is-QDA35.tmp | text | |
MD5:24271E8E18AB43467B56986506742112 | SHA256:B894338A61A08A28EC4788A794FAC455BA5C7E115785B1A3ABB205E7DB532981 | |||
| 548 | Setup_4nec2.tmp | C:\4nec2\Nec2.doc | document | |
MD5:C0BAF5358FC6CC4CFDFE1EDE512D68EB | SHA256:CDE6E5890BBD4DB74B2002387B9BF3CAEA23A81D9F91858471CF9437873F781D | |||
| 548 | Setup_4nec2.tmp | C:\4nec2\Cards.rtf | text | |
MD5:208A3AF8352E14DB32306E4A95FB1406 | SHA256:6A756FCFE40677048091098A302C880C24979AAA1A6416233FCC2F69148C00D7 | |||
| 548 | Setup_4nec2.tmp | C:\Users\admin\AppData\Local\Temp\is-AJ01K.tmp\_isetup\_shfoldr.dll | executable | |
MD5:92DC6EF532FBB4A5C3201469A5B5EB63 | SHA256:9884E9D1B4F8A873CCBD81F8AD0AE257776D2348D027D811A56475E028360D87 | |||
| 548 | Setup_4nec2.tmp | C:\4nec2\_Info.txt | text | |
MD5:7B261CD7A69AE1202BC8AAAA91ADDCD9 | SHA256:2E89E62367C5F240EACA316002067C1232FF70A3AFE8B7AAFCC20AAD3166D289 | |||
| 548 | Setup_4nec2.tmp | C:\4nec2\is-K8CH1.tmp | executable | |
MD5:FBA1DE70F5BB8544A9753957F269F897 | SHA256:87931B032A78E11A4DD491E21A66A9F24DF3FFBBEF61B5672BFE286E3903953B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
64
DNS requests
113
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2592 | chrome.exe | 172.217.16.131:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
2344 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2592 | chrome.exe | 173.194.76.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
2592 | chrome.exe | 142.250.186.164:443 | www.google.com | GOOGLE | US | whitelisted |
2592 | chrome.exe | 142.250.185.99:443 | www.gstatic.com | GOOGLE | US | whitelisted |
2592 | chrome.exe | 142.250.185.142:443 | apis.google.com | GOOGLE | US | whitelisted |
2592 | chrome.exe | 142.250.185.227:443 | update.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
encrypted-tbn0.gstatic.com |
| whitelisted |
outlook.com |
| whitelisted |
www.outlook.com |
| whitelisted |
outlook.live.com |
| whitelisted |