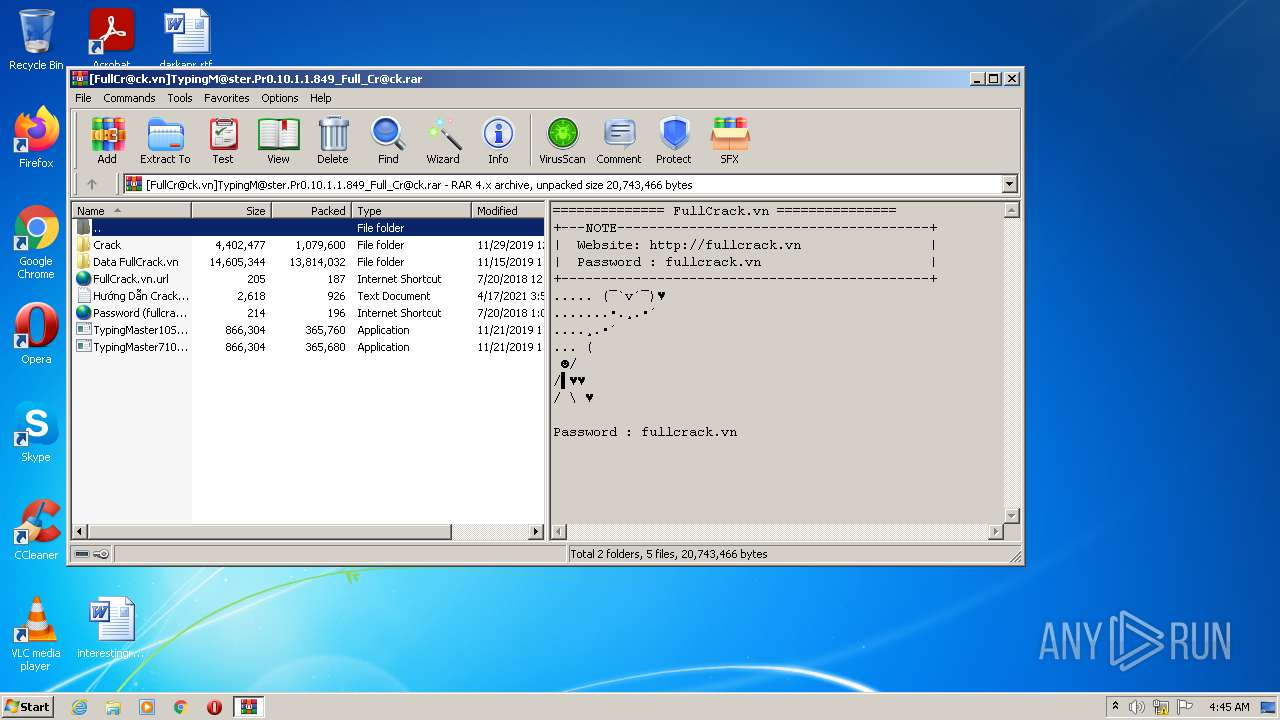
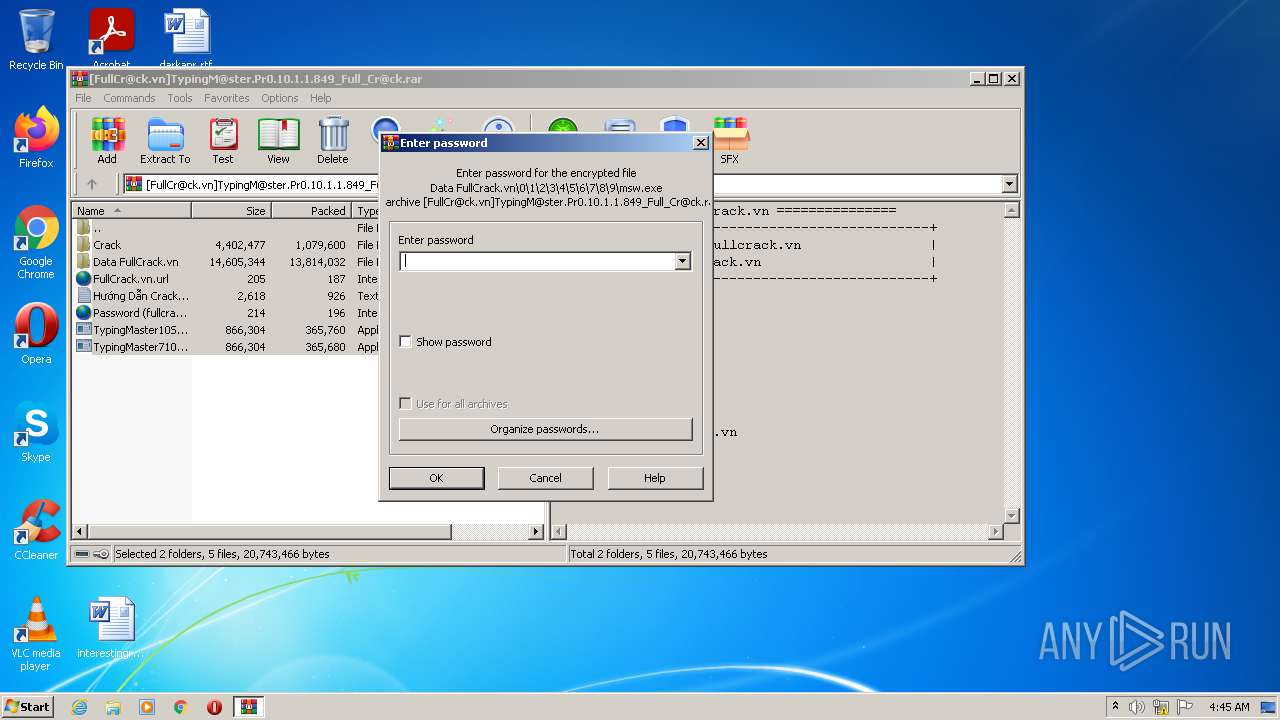
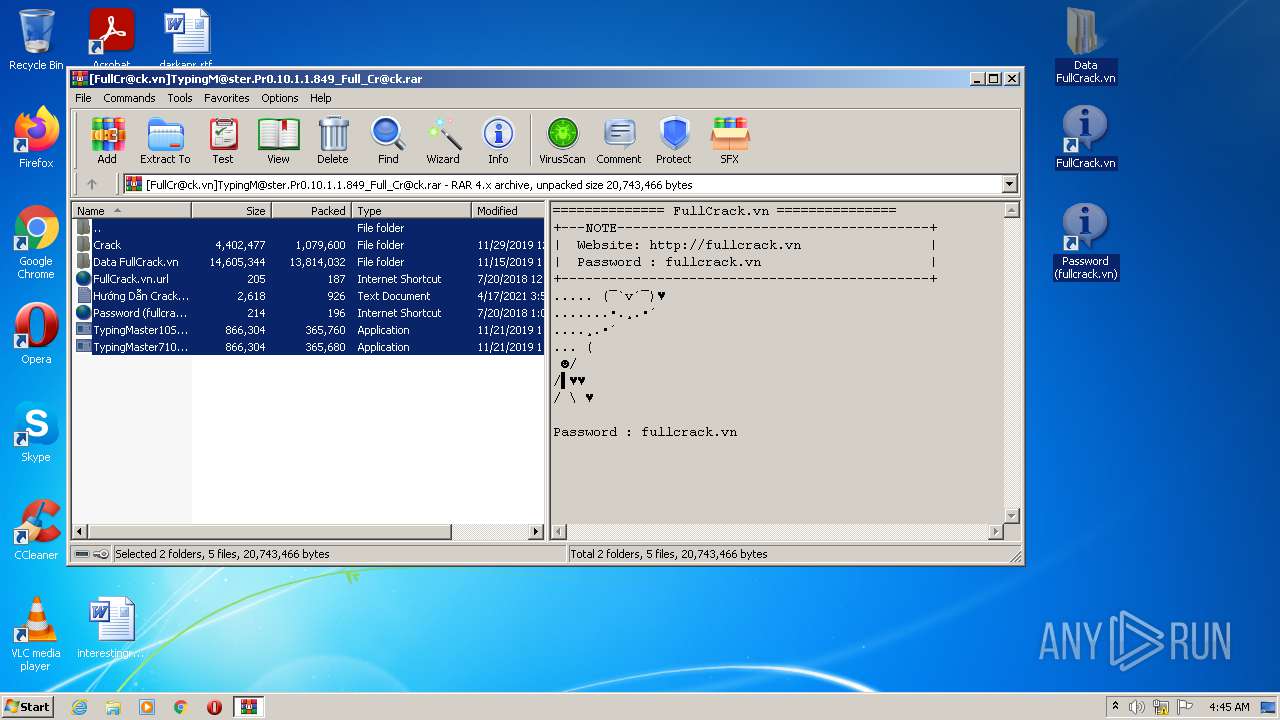
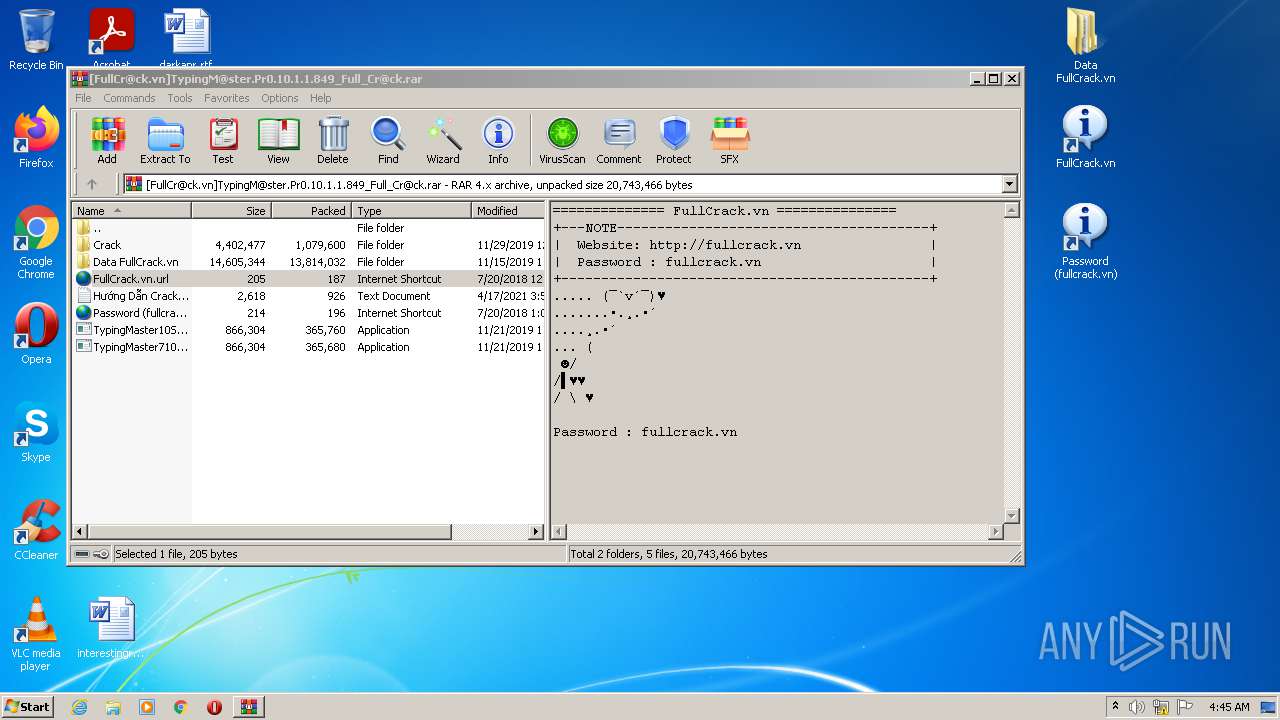
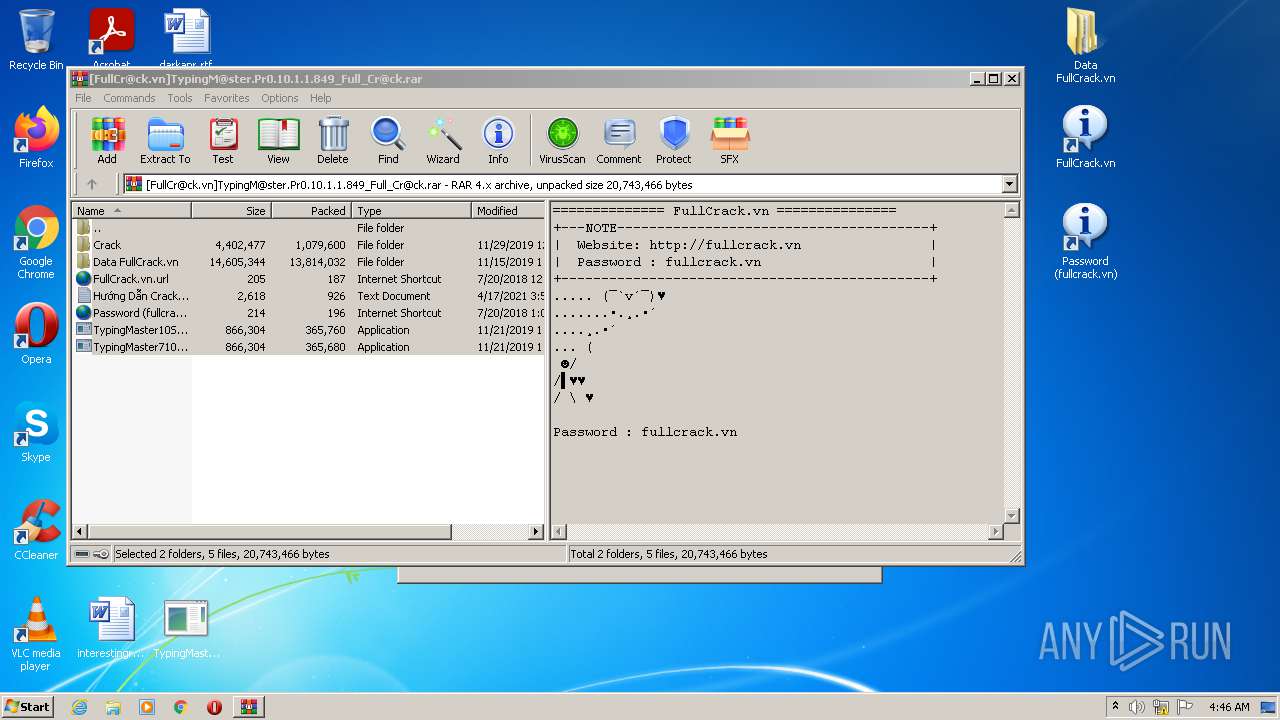
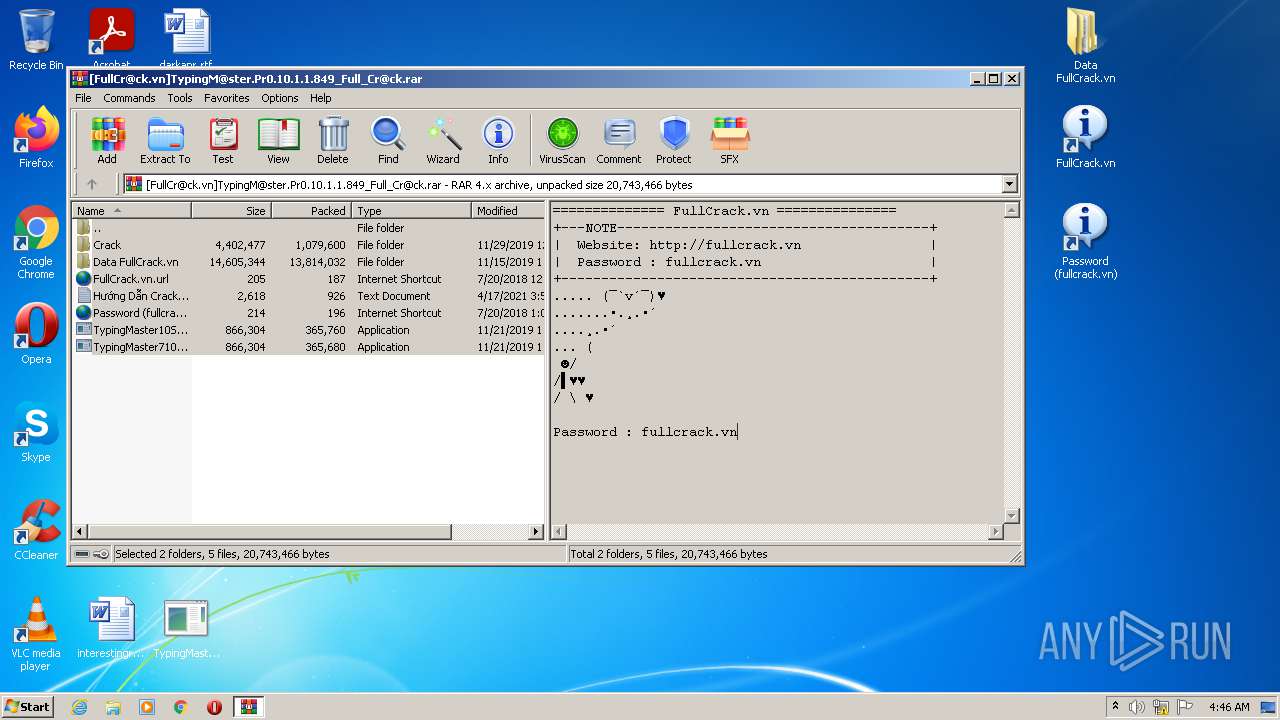
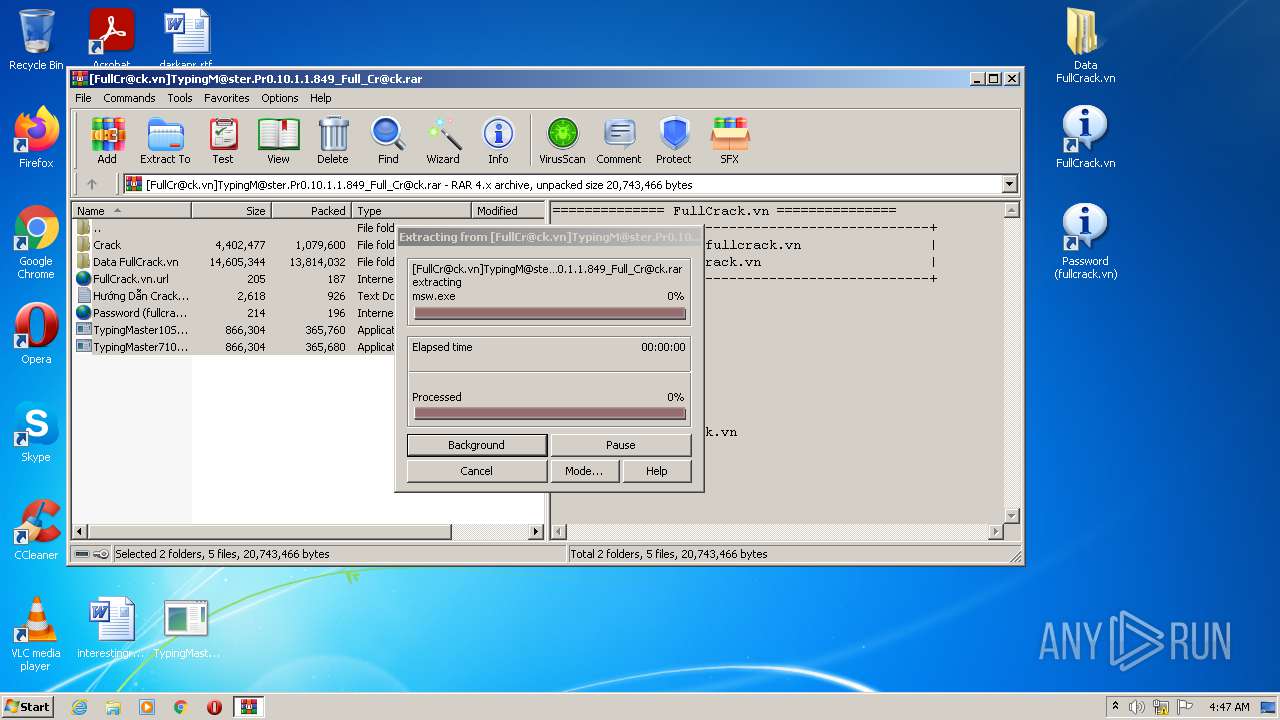
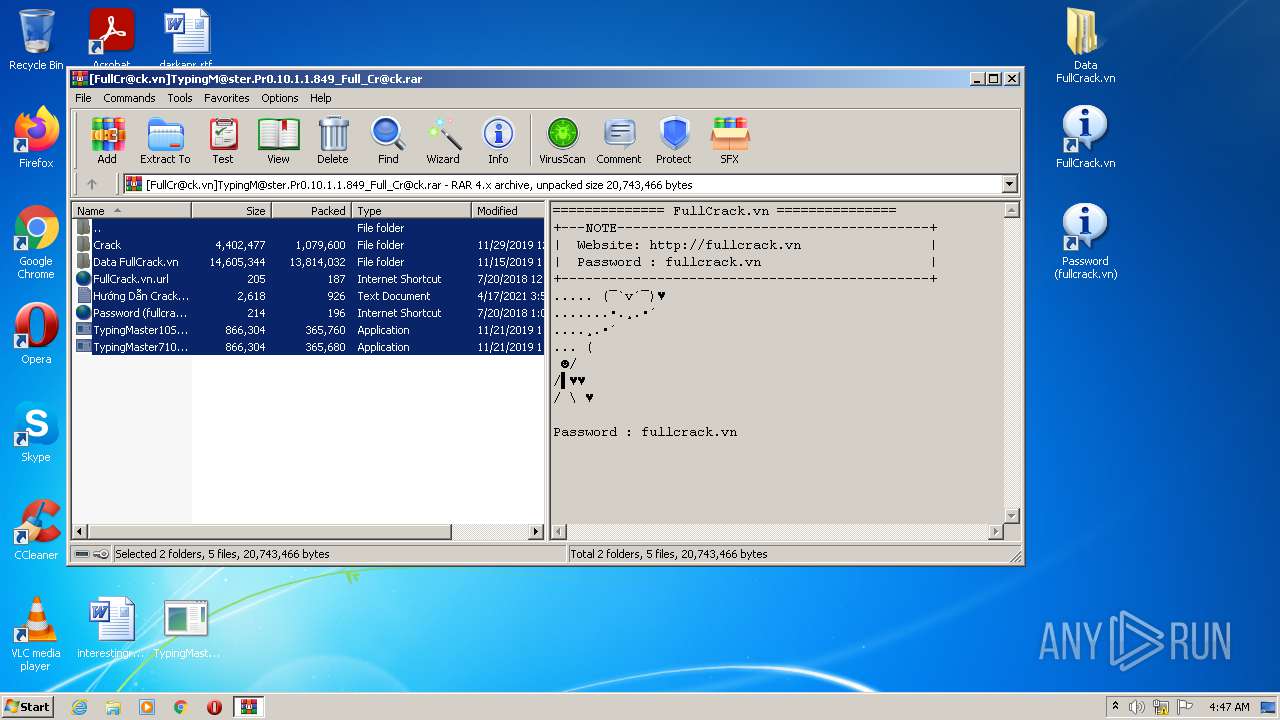
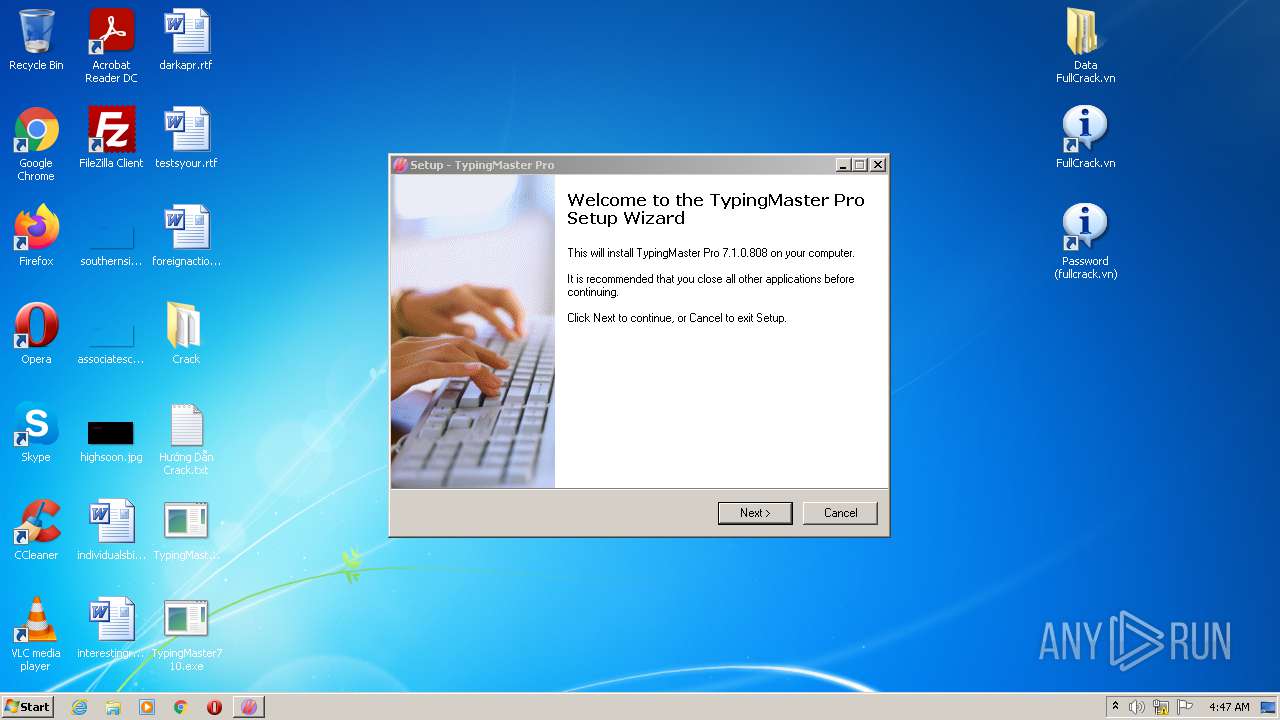
| File name: | [FullCr@ck.vn]TypingM@ster.Pr0.10.1.1.849_Full_Cr@ck.rar |
| Full analysis: | https://app.any.run/tasks/49303f5c-8c97-435d-9ba8-911aed004343 |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2021, 03:44:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 38F1AEAAD892CBA5B86E9D42397A6F36 |
| SHA1: | 73478C3CE4279F9EE6D5B9895BCF069500EB42FF |
| SHA256: | 7DDF9658ED4ADF9F7847A36CDA99BFFD51ED44986FDEC3EC783A921C68894975 |
| SSDEEP: | 393216:TiRDLhf+9lIOyKbdx2mRL5xuX++z6Ur2B5pGm:mVLA9lIOfn26LyXZz6Usn |
MALICIOUS
Application was dropped or rewritten from another process
- TypingMaster710.exe (PID: 2764)
- 2.exe (PID: 668)
- msw.exe (PID: 1580)
- 2.exe (PID: 3424)
- TypingMaster10Setup.exe (PID: 908)
- msw.exe (PID: 3256)
- 1.exe (PID: 3268)
- 1.exe (PID: 1112)
Drops executable file immediately after starts
- 2.exe (PID: 668)
- 2.exe (PID: 3424)
- 1.exe (PID: 3268)
- 1.exe (PID: 1112)
- 1.tmp (PID: 3796)
Actions looks like stealing of personal data
- msw.exe (PID: 1580)
- msw.exe (PID: 3256)
SUSPICIOUS
Executed via COM
- iexplore.exe (PID: 2040)
Checks supported languages
- WinRAR.exe (PID: 3004)
- TypingMaster710.exe (PID: 2764)
- msw.exe (PID: 1580)
- 2.exe (PID: 668)
- 2.tmp (PID: 2400)
- 2.exe (PID: 3424)
- 2.tmp (PID: 3528)
- TypingMaster10Setup.exe (PID: 908)
- 1.exe (PID: 3268)
- msw.exe (PID: 3256)
- 1.tmp (PID: 3864)
- 1.exe (PID: 1112)
- 1.tmp (PID: 3796)
Reads the computer name
- WinRAR.exe (PID: 3004)
- 2.tmp (PID: 2400)
- msw.exe (PID: 1580)
- 2.tmp (PID: 3528)
- 1.tmp (PID: 3864)
- msw.exe (PID: 3256)
- 1.tmp (PID: 3796)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2876)
- iexplore.exe (PID: 3912)
Drops a file with too old compile date
- WinRAR.exe (PID: 3004)
- 2.exe (PID: 668)
- 2.exe (PID: 3424)
- 2.tmp (PID: 3528)
- 1.exe (PID: 3268)
- 1.exe (PID: 1112)
- 1.tmp (PID: 3796)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3004)
- 2.exe (PID: 668)
- 2.exe (PID: 3424)
- 2.tmp (PID: 3528)
- 1.exe (PID: 3268)
- 1.exe (PID: 1112)
- 1.tmp (PID: 3796)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3004)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3004)
- 2.tmp (PID: 3528)
- 1.tmp (PID: 3796)
Reads mouse settings
- msw.exe (PID: 1580)
- TypingMaster710.exe (PID: 2764)
- TypingMaster10Setup.exe (PID: 908)
- msw.exe (PID: 3256)
Reads the Windows organization settings
- 2.tmp (PID: 3528)
- 1.tmp (PID: 3796)
Reads Windows owner or organization settings
- 2.tmp (PID: 3528)
- 1.tmp (PID: 3796)
Creates a directory in Program Files
- 2.tmp (PID: 3528)
Starts Internet Explorer
- 1.tmp (PID: 3796)
INFO
Checks supported languages
- iexplore.exe (PID: 2040)
- iexplore.exe (PID: 2876)
- iexplore.exe (PID: 2504)
- iexplore.exe (PID: 3912)
Application launched itself
- iexplore.exe (PID: 2040)
- iexplore.exe (PID: 2504)
Reads the computer name
- iexplore.exe (PID: 2040)
- iexplore.exe (PID: 2876)
- iexplore.exe (PID: 2504)
- iexplore.exe (PID: 3912)
Changes internet zones settings
- iexplore.exe (PID: 2040)
- iexplore.exe (PID: 2504)
Reads settings of System Certificates
- iexplore.exe (PID: 2876)
- 1.tmp (PID: 3796)
- iexplore.exe (PID: 3912)
Reads the date of Windows installation
- iexplore.exe (PID: 2040)
- iexplore.exe (PID: 2504)
Reads internet explorer settings
- iexplore.exe (PID: 2876)
- iexplore.exe (PID: 3912)
Checks Windows Trust Settings
- iexplore.exe (PID: 2876)
- iexplore.exe (PID: 3912)
Manual execution by user
- TypingMaster710.exe (PID: 2764)
- TypingMaster10Setup.exe (PID: 908)
Application was dropped or rewritten from another process
- 2.tmp (PID: 2400)
- 2.tmp (PID: 3528)
- 1.tmp (PID: 3796)
- 1.tmp (PID: 3864)
Loads dropped or rewritten executable
- 2.tmp (PID: 3528)
- 1.tmp (PID: 3796)
Creates files in the program directory
- 2.tmp (PID: 3528)
Changes settings of System certificates
- iexplore.exe (PID: 3912)
Creates files in the user directory
- iexplore.exe (PID: 3912)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3912)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| ArchivedFileName: | FullCrack.vn.url |
|---|---|
| PackingMethod: | Normal |
| ModifyDate: | 2018:07:20 12:46:16 |
| OperatingSystem: | Win32 |
| UncompressedSize: | 205 |
| CompressedSize: | 229 |
Total processes
63
Monitored processes
17
Malicious processes
6
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 668 | "Data FullCrack.vn\0\1\2\3\4\5\6\7\8\9\2.exe" | C:\Users\admin\Desktop\Data FullCrack.vn\0\1\2\3\4\5\6\7\8\9\2.exe | TypingMaster710.exe | ||||||||||||
User: admin Company: TypingMaster Inc Integrity Level: MEDIUM Description: TypingMaster Pro Exit code: 0 Version: 7.10 Modules
| |||||||||||||||
| 908 | "C:\Users\admin\Desktop\TypingMaster10Setup.exe" | C:\Users\admin\Desktop\TypingMaster10Setup.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1112 | "C:\Users\admin\Desktop\Data FullCrack.vn\0\1\2\3\4\5\6\7\8\9\1.exe" /SPAWNWND=$50184 /NOTIFYWND=$50200 | C:\Users\admin\Desktop\Data FullCrack.vn\0\1\2\3\4\5\6\7\8\9\1.exe | 1.tmp | ||||||||||||
User: admin Company: Typing Innovation Group Ltd Integrity Level: HIGH Description: Typing Master 10 Exit code: 1 Version: 10.00 Modules
| |||||||||||||||
| 1580 | "Data FullCrack.vn\0\1\2\3\4\5\6\7\8\9\msw.exe" | C:\Users\admin\Desktop\Data FullCrack.vn\0\1\2\3\4\5\6\7\8\9\msw.exe | TypingMaster710.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2040 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2400 | "C:\Users\admin\AppData\Local\Temp\is-TECDB.tmp\2.tmp" /SL5="$40160,9009639,72704,C:\Users\admin\Desktop\Data FullCrack.vn\0\1\2\3\4\5\6\7\8\9\2.exe" | C:\Users\admin\AppData\Local\Temp\is-TECDB.tmp\2.tmp | — | 2.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.49.0.0 Modules
| |||||||||||||||
| 2504 | "C:\Program Files\Internet Explorer\iexplore.exe" http://www.typingmaster.com/typing-tutor/10/v2.html | C:\Program Files\Internet Explorer\iexplore.exe | — | 1.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2764 | "C:\Users\admin\Desktop\TypingMaster710.exe" | C:\Users\admin\Desktop\TypingMaster710.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2876 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2040 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3004 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\[FullCr@ck.vn]TypingM@ster.Pr0.10.1.1.849_Full_Cr@ck.rar" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
25 656
Read events
25 456
Write events
198
Delete events
2
Modification events
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\[FullCr@ck.vn]TypingM@ster.Pr0.10.1.1.849_Full_Cr@ck.rar | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3004) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\ieframe.dll,-10046 |
Value: Internet Shortcut | |||
Executable files
33
Suspicious files
17
Text files
660
Unknown types
30
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2876 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\css[1].css | text | |
MD5:— | SHA256:— | |||
| 2876 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\datpass-style[1].css | text | |
MD5:— | SHA256:— | |||
| 2876 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\style[1].css | text | |
MD5:— | SHA256:— | |||
| 2876 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\VNA9DTV1.htm | html | |
MD5:— | SHA256:— | |||
| 2876 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\bwp-external-links[1].css | text | |
MD5:— | SHA256:— | |||
| 2876 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\style[2].css | text | |
MD5:— | SHA256:— | |||
| 2876 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\jquery.validate[1].js | text | |
MD5:9FE5472760A25B494481408BB9A637D6 | SHA256:AD5DA6112553BD7511AEA64DD18D23CEF797432148142D766424C900DD919D0A | |||
| 3004 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3004.9267\FullCrack.vn.url | text | |
MD5:8B6A3EBCBF9F3DCA62B99F976C713CBE | SHA256:309E6926799296271ABBCFE6A8D111653EF9635451A0120A2F933EF00E8D7574 | |||
| 3004 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb3004.9759\FullCrack.vn.url | text | |
MD5:8B6A3EBCBF9F3DCA62B99F976C713CBE | SHA256:309E6926799296271ABBCFE6A8D111653EF9635451A0120A2F933EF00E8D7574 | |||
| 2876 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
73
TCP/UDP connections
48
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2876 | iexplore.exe | GET | 200 | 103.110.84.85:80 | http://fullcrack.vn/wp-content/plugins/bwp-external-links/css/bwp-external-links.css?ver=1.1.3 | unknown | text | 427 b | unknown |
2876 | iexplore.exe | GET | 200 | 103.110.84.85:80 | http://fullcrack.vn/wp-content/themes/executive-pro/style.css?ver=3.0.0 | unknown | text | 8.09 Kb | unknown |
2876 | iexplore.exe | GET | 200 | 103.110.84.85:80 | http://fullcrack.vn/wp-content/plugins/dat-pass/css/datpass-style.css?ver=1.1 | unknown | text | 1022 b | unknown |
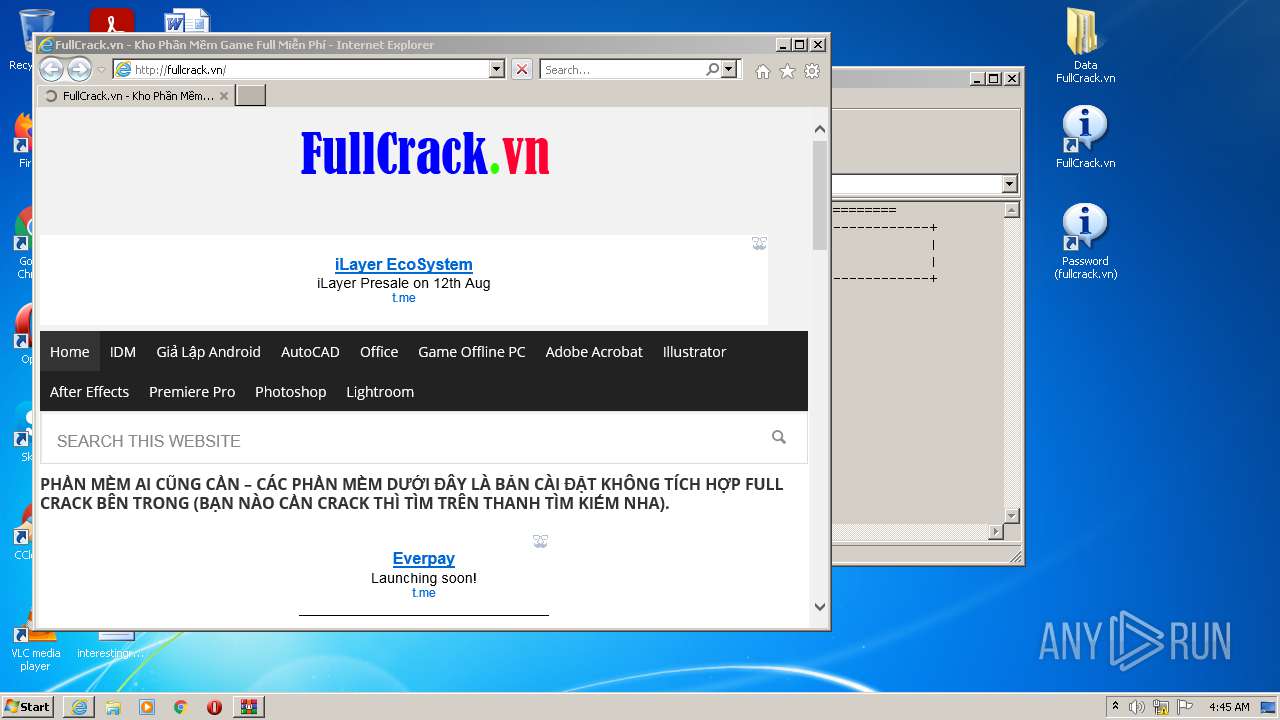
2876 | iexplore.exe | GET | 200 | 103.110.84.85:80 | http://fullcrack.vn/ | unknown | html | 9.81 Kb | unknown |
2876 | iexplore.exe | GET | 200 | 103.110.84.85:80 | http://fullcrack.vn/wp-content/uploads/maxmegamenu/style.css?ver=72caf7 | unknown | text | 5.25 Kb | unknown |
2876 | iexplore.exe | GET | 200 | 103.110.84.85:80 | http://fullcrack.vn/wp-content/plugins/csh-login/assets/css/layout1.css?ver=5.8 | unknown | text | 524 b | unknown |
2876 | iexplore.exe | GET | 200 | 103.110.84.85:80 | http://fullcrack.vn/wp-includes/css/dist/block-library/style.min.css?ver=5.8 | unknown | text | 10.1 Kb | unknown |
2876 | iexplore.exe | GET | 200 | 103.110.84.85:80 | http://fullcrack.vn/wp-content/plugins/csh-login/assets/css/default.css?ver=5.8 | unknown | text | 425 b | unknown |
2876 | iexplore.exe | GET | 200 | 103.110.84.85:80 | http://fullcrack.vn/wp-content/plugins/kk-star-ratings/public/css/kk-star-ratings.css?ver=4.2.0 | unknown | text | 660 b | unknown |
2876 | iexplore.exe | GET | 200 | 103.110.84.85:80 | http://fullcrack.vn/wp-content/uploads/useanyfont/uaf.css?ver=1623293906 | unknown | compressed | 425 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3796 | 1.tmp | 104.26.4.120:80 | www.typingmaster.com | Cloudflare Inc | US | unknown |
3796 | 1.tmp | 104.26.4.120:443 | www.typingmaster.com | Cloudflare Inc | US | unknown |
3912 | iexplore.exe | 104.26.4.120:443 | www.typingmaster.com | Cloudflare Inc | US | unknown |
2876 | iexplore.exe | 103.110.84.85:80 | fullcrack.vn | — | — | unknown |
2876 | iexplore.exe | 152.199.19.160:80 | ajax.aspnetcdn.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2876 | iexplore.exe | 142.250.187.104:443 | www.googletagmanager.com | Google Inc. | US | suspicious |
2876 | iexplore.exe | 142.250.187.164:443 | www.google.com | Google Inc. | US | whitelisted |
2876 | iexplore.exe | 2.16.186.33:80 | ctldl.windowsupdate.com | Akamai International B.V. | — | whitelisted |
2876 | iexplore.exe | 172.217.169.99:80 | fonts.gstatic.com | Google Inc. | US | whitelisted |
3912 | iexplore.exe | 74.125.206.154:443 | stats.g.doubleclick.net | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
fullcrack.vn |
| unknown |
fonts.googleapis.com |
| whitelisted |
ajax.aspnetcdn.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
www.google.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
ad.a-ads.com |
| whitelisted |
static.a-ads.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |