| File name: | WebCruiser Web Vulnerability Scanner Enterprise Edition 3.5.3.rar |
| Full analysis: | https://app.any.run/tasks/5e1864c6-3bb1-4d43-bfb7-935ffff9fc34 |
| Verdict: | Malicious activity |
| Analysis date: | July 11, 2018, 12:49:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 1813FE3568546882CC1FD1AE70CEB92A |
| SHA1: | 3305E2D1386AD3B026FDE060F245309A779A1569 |
| SHA256: | 7DD448E4E8B66F494290170781E61BF02ED1FF69F9DAE44CE09747A2BF93B4B9 |
| SSDEEP: | 24576:Ilv8I9YUduU6dTQ7CR1P/lXh2m3Yljd78pyPpFYWs937fBofexJ+mU:4vzYU1w1P/Nh2m3Ydd7Np+LB4qJBU |
MALICIOUS
Loads dropped or rewritten executable
- WebCruiserWVS.exe (PID: 2500)
- WebCruiserWVS.exe (PID: 2028)
- SearchProtocolHost.exe (PID: 2504)
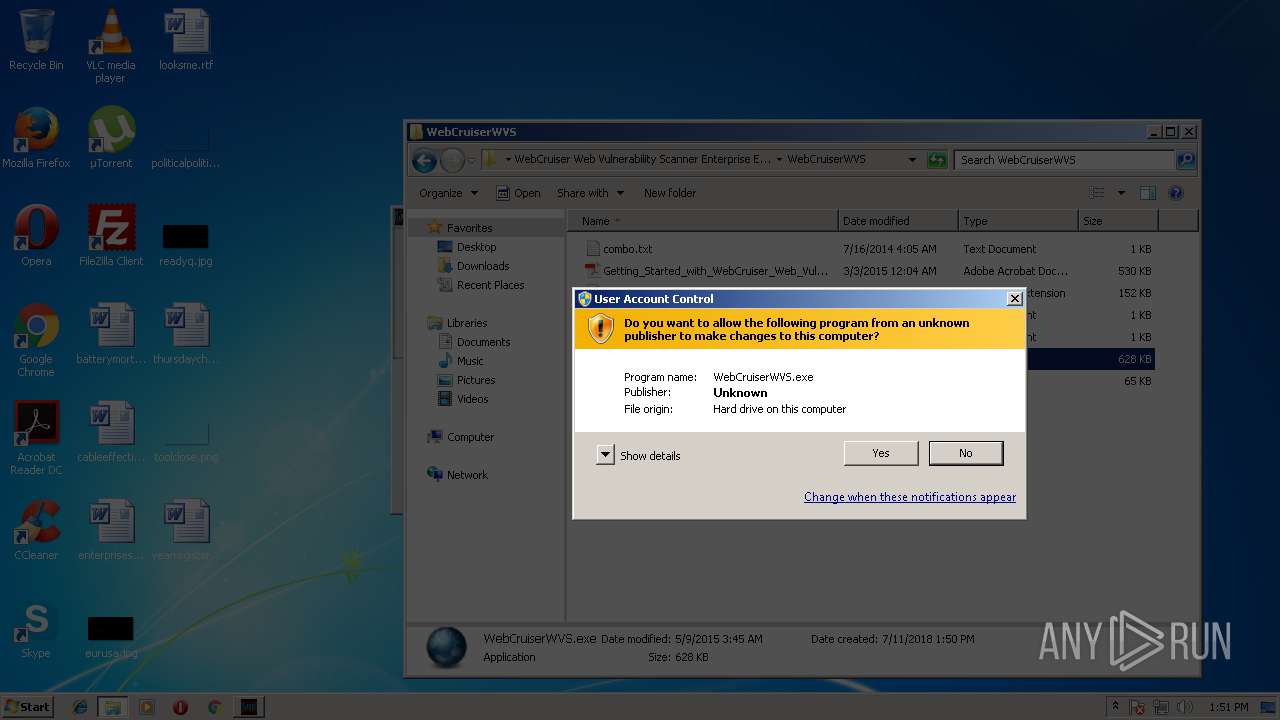
Application was dropped or rewritten from another process
- WebCruiserWVS.exe (PID: 2500)
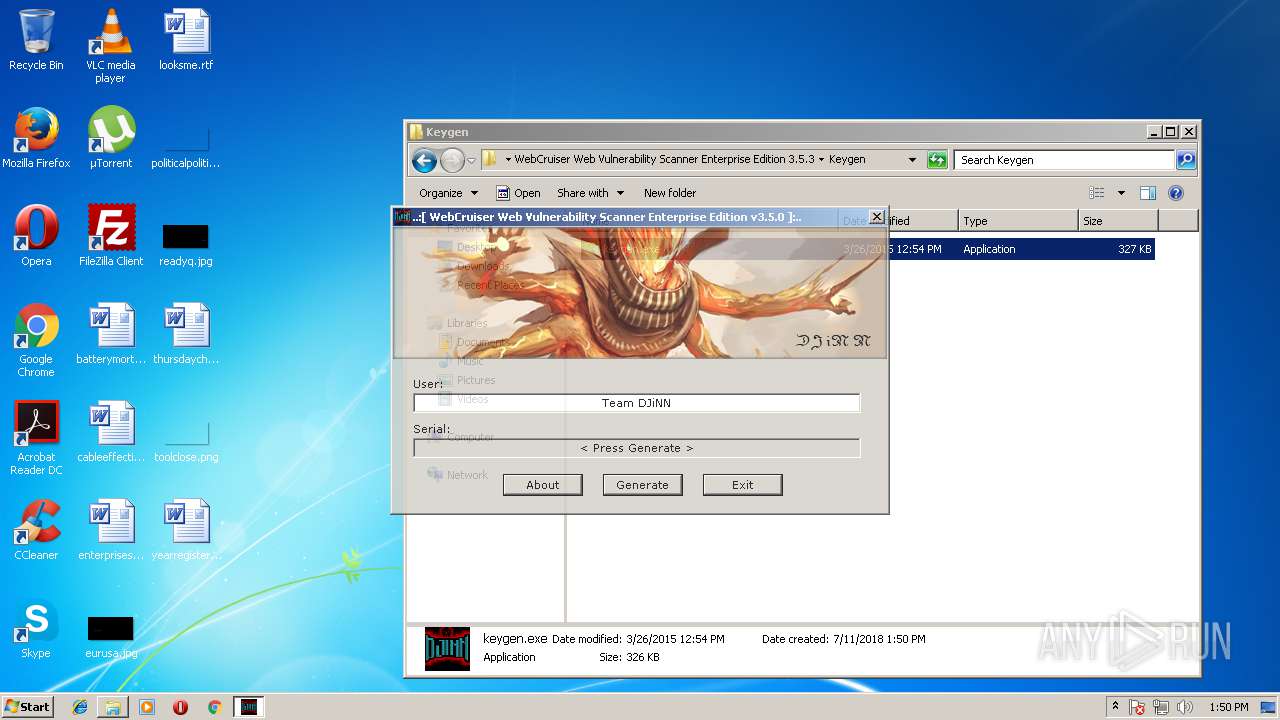
- keygen.exe (PID: 1072)
- WebCruiserWVS.exe (PID: 2028)
SUSPICIOUS
Executable content was dropped or overwritten
- 7zFM.exe (PID: 2216)
Reads internet explorer settings
- WebCruiserWVS.exe (PID: 2500)
- WebCruiserWVS.exe (PID: 2028)
INFO
Dropped object may contain URL's
- 7zFM.exe (PID: 2216)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
40
Monitored processes
5
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
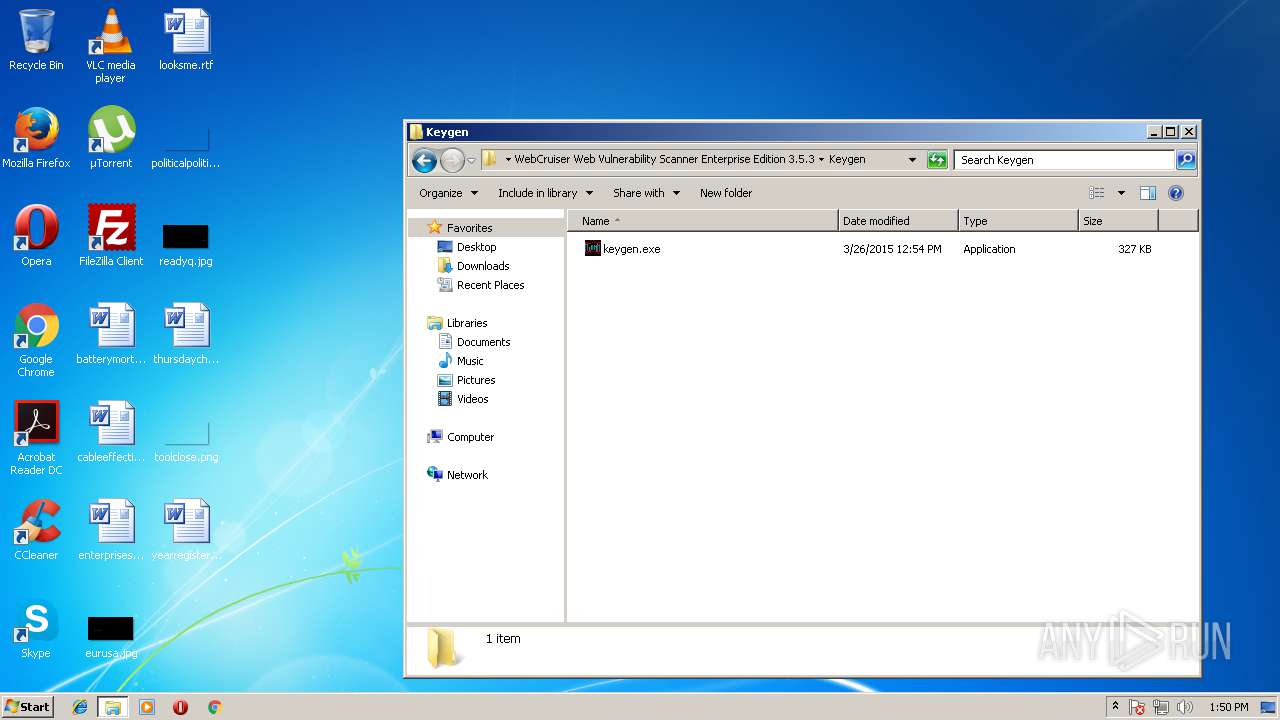
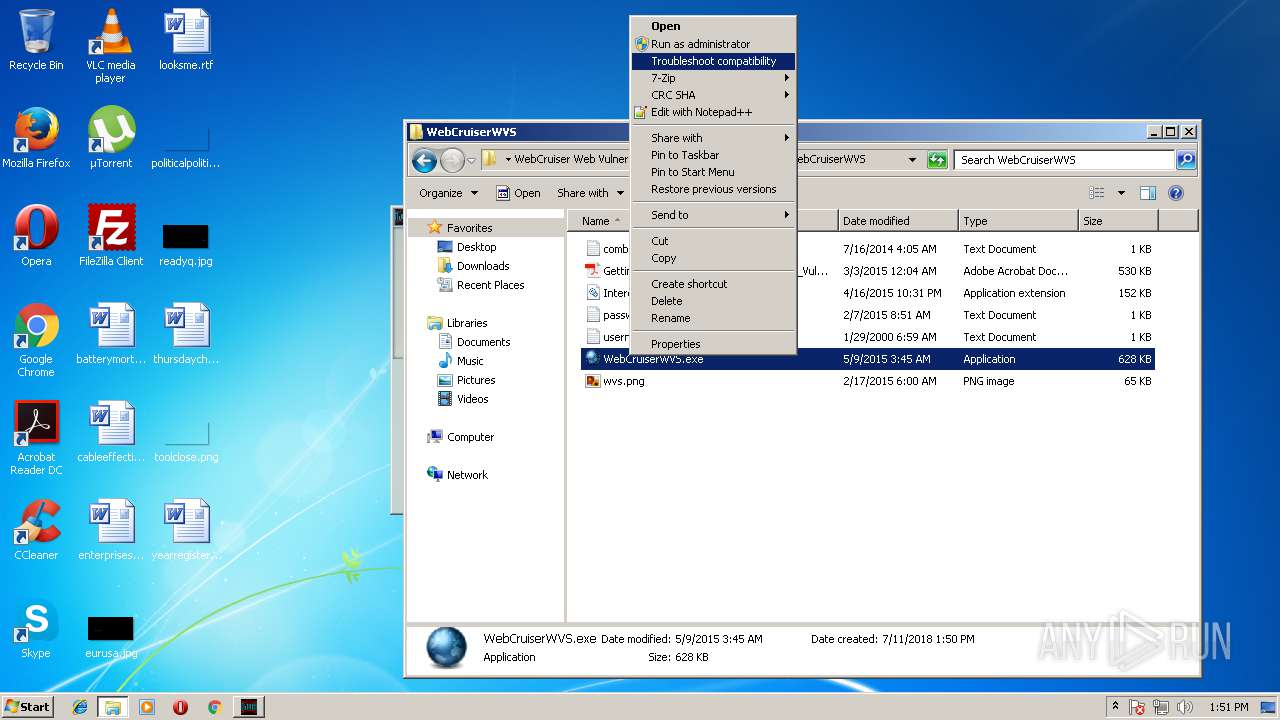
| 1072 | "C:\Users\admin\Desktop\WebCruiser Web Vulnerability Scanner Enterprise Edition 3.5.3\Keygen\keygen.exe" | C:\Users\admin\Desktop\WebCruiser Web Vulnerability Scanner Enterprise Edition 3.5.3\Keygen\keygen.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
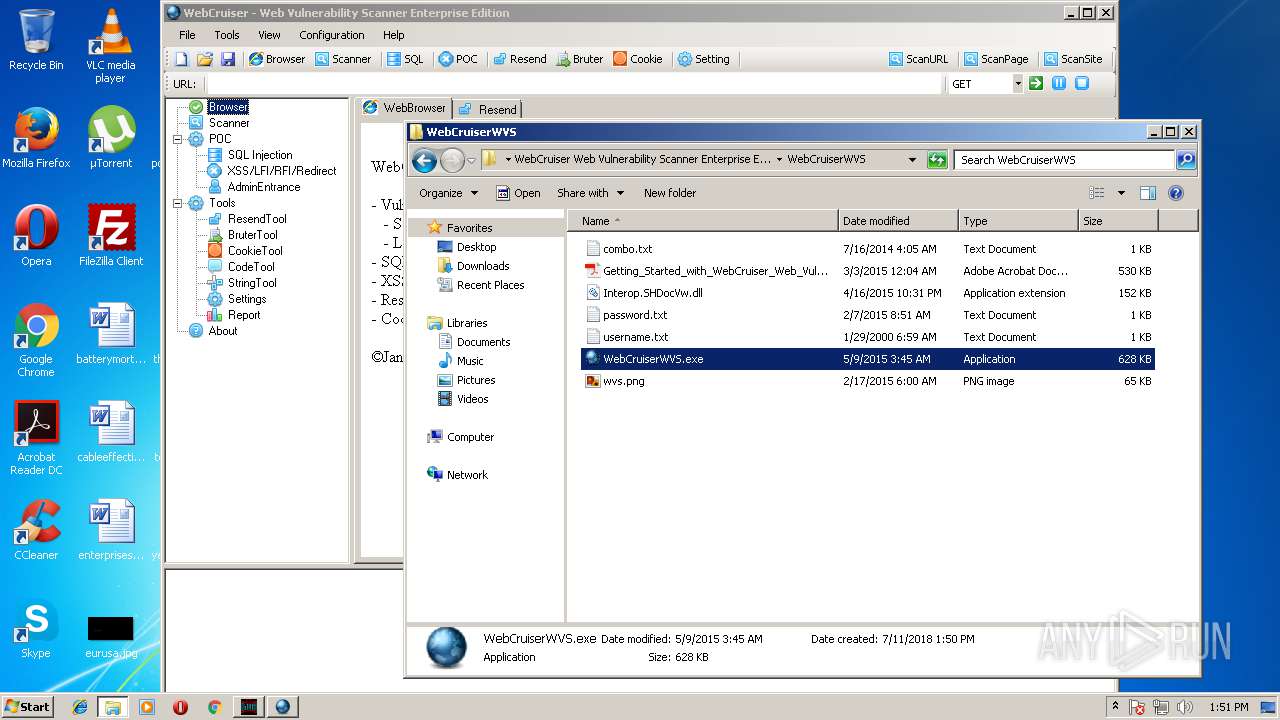
| 2028 | "C:\Users\admin\Desktop\WebCruiser Web Vulnerability Scanner Enterprise Edition 3.5.3\WebCruiserWVS\WebCruiserWVS.exe" | C:\Users\admin\Desktop\WebCruiser Web Vulnerability Scanner Enterprise Edition 3.5.3\WebCruiserWVS\WebCruiserWVS.exe | explorer.exe | ||||||||||||
User: admin Company: Janusec Integrity Level: HIGH Description: WebCruiserWVS Exit code: 0 Version: 3.5.3.0 Modules
| |||||||||||||||
| 2216 | "C:\Program Files\7-Zip\7zFM.exe" "C:\Users\admin\AppData\Local\Temp\WebCruiser Web Vulnerability Scanner Enterprise Edition 3.5.3.rar" | C:\Program Files\7-Zip\7zFM.exe | explorer.exe | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip File Manager Exit code: 0 Version: 16.04 Modules
| |||||||||||||||
| 2500 | "C:\Users\admin\Desktop\WebCruiser Web Vulnerability Scanner Enterprise Edition 3.5.3\WebCruiserWVS\WebCruiserWVS.exe" | C:\Users\admin\Desktop\WebCruiser Web Vulnerability Scanner Enterprise Edition 3.5.3\WebCruiserWVS\WebCruiserWVS.exe | explorer.exe | ||||||||||||
User: admin Company: Janusec Integrity Level: MEDIUM Description: WebCruiserWVS Exit code: 0 Version: 3.5.3.0 Modules
| |||||||||||||||
| 2504 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe3_ Global\UsGthrCtrlFltPipeMssGthrPipe3 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
607
Read events
572
Write events
35
Delete events
0
Modification events
| (PID) Process: | (2216) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FolderShortcuts |
Value: | |||
| (PID) Process: | (2216) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FolderHistory |
Value: 43003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C00570065006200430072007500690073006500720020005700650062002000560075006C006E00650072006100620069006C0069007400790020005300630061006E006E0065007200200045006E00740065007200700072006900730065002000450064006900740069006F006E00200033002E0035002E0033002E007200610072005C000000 | |||
| (PID) Process: | (2216) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | PanelPath0 |
Value: C:\Users\admin\AppData\Local\Temp\ | |||
| (PID) Process: | (2216) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FlatViewArc0 |
Value: 0 | |||
| (PID) Process: | (2216) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | PanelPath1 |
Value: | |||
| (PID) Process: | (2216) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | FlatViewArc1 |
Value: 0 | |||
| (PID) Process: | (2216) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | ListMode |
Value: 771 | |||
| (PID) Process: | (2216) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | Position |
Value: 1600000016000000D60300000B02000000000000 | |||
| (PID) Process: | (2216) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM |
| Operation: | write | Name: | Panels |
Value: 0100000000000000DA010000 | |||
| (PID) Process: | (2216) 7zFM.exe | Key: | HKEY_CURRENT_USER\Software\7-Zip\FM\Columns |
| Operation: | write | Name: | 7-Zip.Rar5 |
Value: 0100000004000000010000000400000001000000A00000000700000001000000640000000800000001000000640000000C00000001000000640000000A00000001000000640000000B00000001000000640000000900000001000000640000003F00000001000000640000000F00000001000000640000000D00000001000000640000001000000001000000640000001100000001000000640000001300000001000000640000001700000001000000640000001600000001000000640000003600000001000000640000005A00000001000000640000005F00000001000000640000001F00000001000000640000002000000001000000640000002E00000001000000640000003E0000000100000064000000 | |||
Executable files
3
Suspicious files
1
Text files
7
Unknown types
0
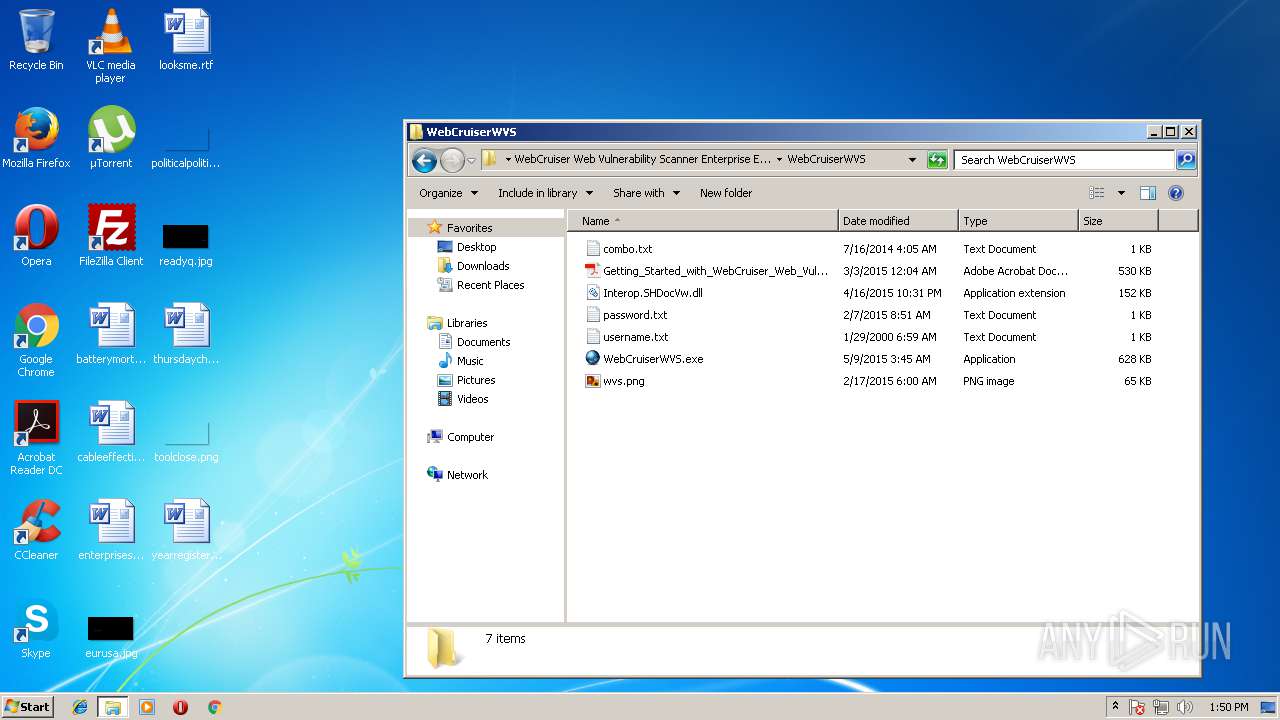
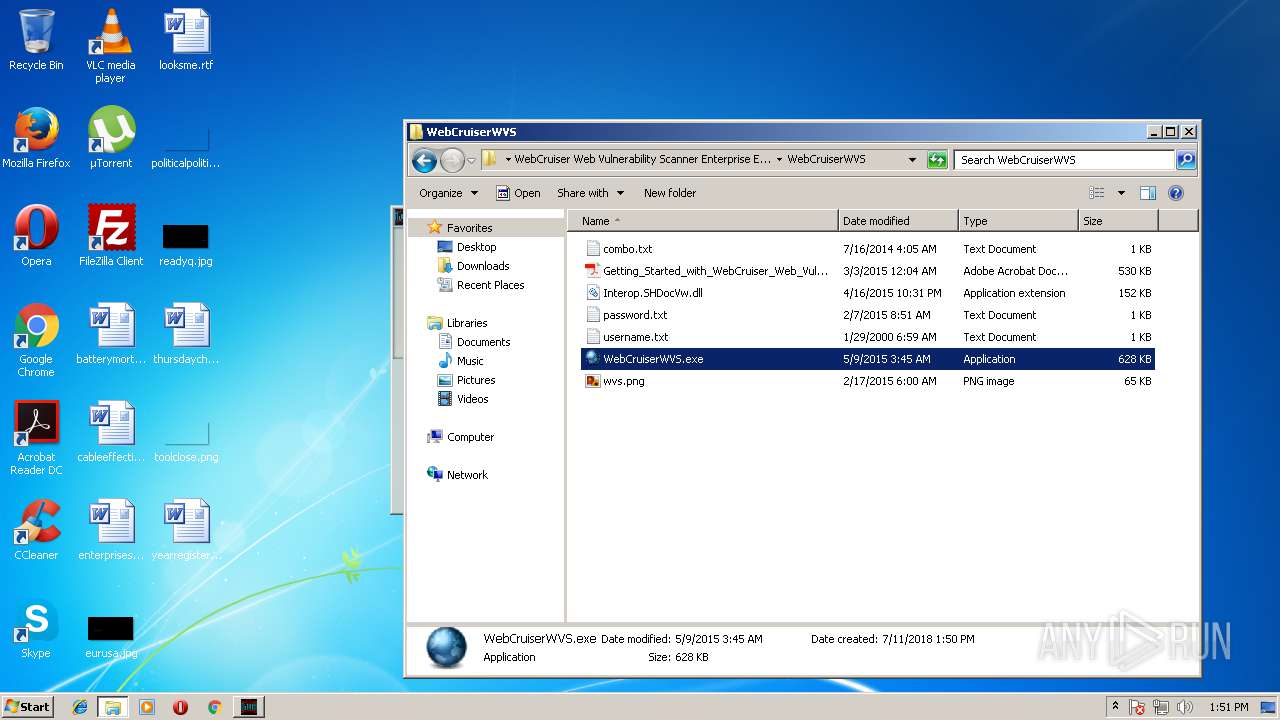
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2216 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE8A8F251B\WebCruiser Web Vulnerability Scanner Enterprise Edition 3.5.3\WebCruiserWVS\combo.txt | text | |
MD5:— | SHA256:— | |||
| 2216 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE8A8F251B\WebCruiser Web Vulnerability Scanner Enterprise Edition 3.5.3\WebCruiserWVS\Getting_Started_with_WebCruiser_Web_Vulnerability_Scanner.pdf | ||
MD5:— | SHA256:— | |||
| 2216 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE8A8F251B\WebCruiser Web Vulnerability Scanner Enterprise Edition 3.5.3\WebCruiserWVS\password.txt | text | |
MD5:— | SHA256:— | |||
| 2216 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE8A8F251B\WebCruiser Web Vulnerability Scanner Enterprise Edition 3.5.3\WebCruiserWVS\Interop.SHDocVw.dll | executable | |
MD5:— | SHA256:— | |||
| 2216 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE8A8F251B\WebCruiser Web Vulnerability Scanner Enterprise Edition 3.5.3\WebCruiserWVS\wvs.png | image | |
MD5:— | SHA256:— | |||
| 2216 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE8A8F251B\WebCruiser Web Vulnerability Scanner Enterprise Edition 3.5.3\Keygen\keygen.exe | executable | |
MD5:— | SHA256:— | |||
| 2216 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE8A8F251B\WebCruiser Web Vulnerability Scanner Enterprise Edition 3.5.3\Novahax.com.URL | text | |
MD5:— | SHA256:— | |||
| 2216 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE8A8F251B\WebCruiser Web Vulnerability Scanner Enterprise Edition 3.5.3\Short-4K.jpg | image | |
MD5:— | SHA256:— | |||
| 2216 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE8A8F251B\WebCruiser Web Vulnerability Scanner Enterprise Edition 3.5.3\Read Me.txt | text | |
MD5:— | SHA256:— | |||
| 2216 | 7zFM.exe | C:\Users\admin\AppData\Local\Temp\7zE8A8F251B\WebCruiser Web Vulnerability Scanner Enterprise Edition 3.5.3\WebCruiserWVS\WebCruiserWVS.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
3
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2028 | WebCruiserWVS.exe | GET | — | 104.238.140.59:80 | http://www.janusec.com/download/version.xml | US | — | — | unknown |
2500 | WebCruiserWVS.exe | GET | 301 | 104.238.140.59:80 | http://www.janusec.com/download/version.xml | US | html | 79 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2500 | WebCruiserWVS.exe | 104.238.140.59:80 | www.janusec.com | Choopa, LLC | US | unknown |
2500 | WebCruiserWVS.exe | 104.238.140.59:443 | www.janusec.com | Choopa, LLC | US | unknown |
2028 | WebCruiserWVS.exe | 104.238.140.59:80 | www.janusec.com | Choopa, LLC | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.janusec.com |
| unknown |