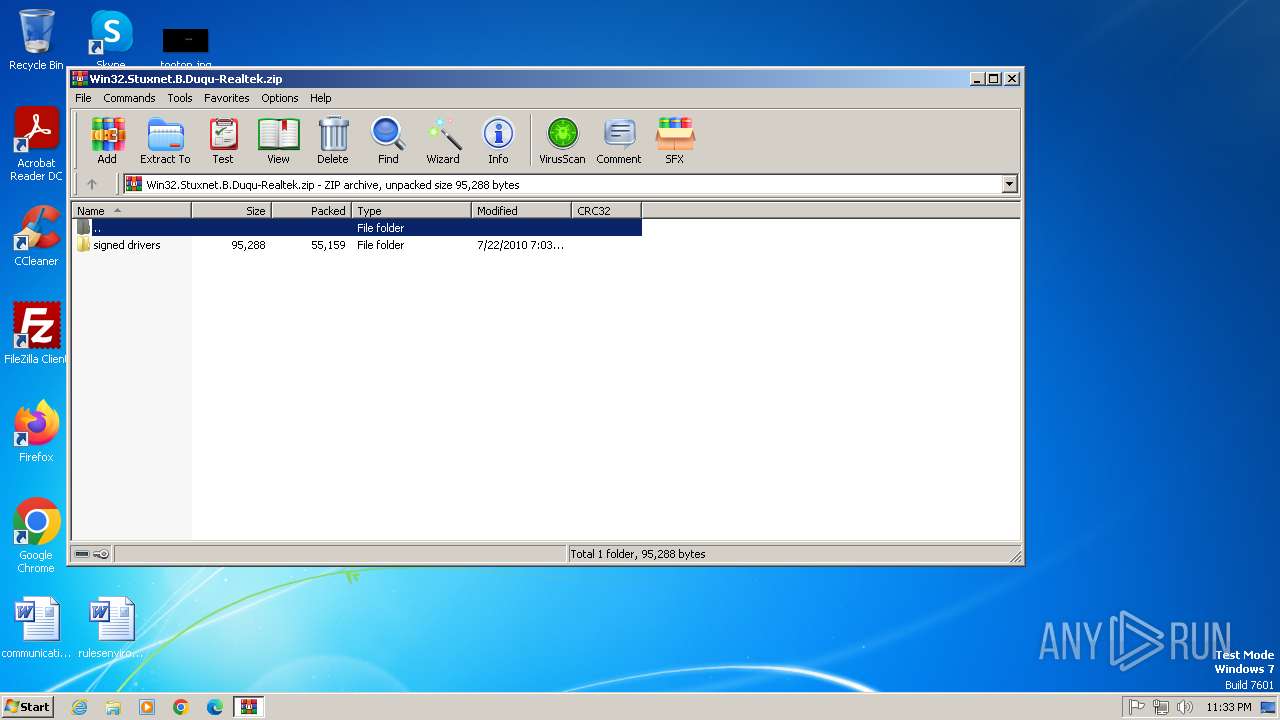
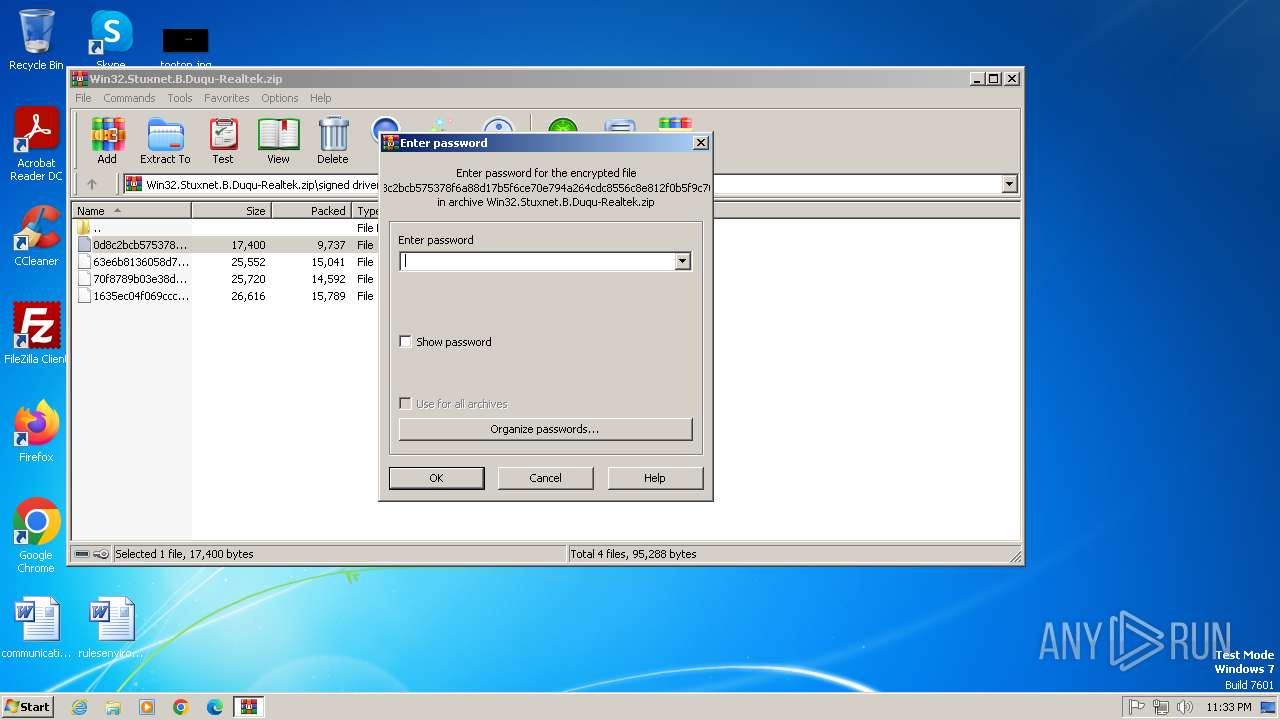
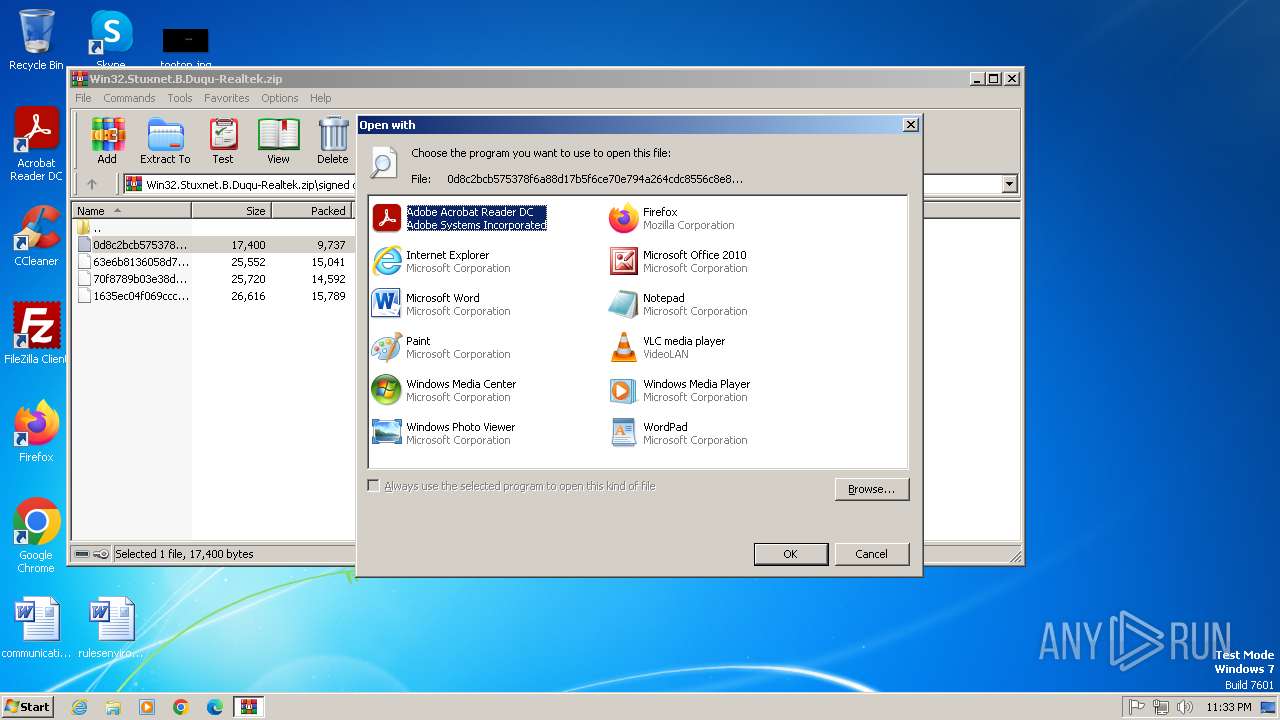
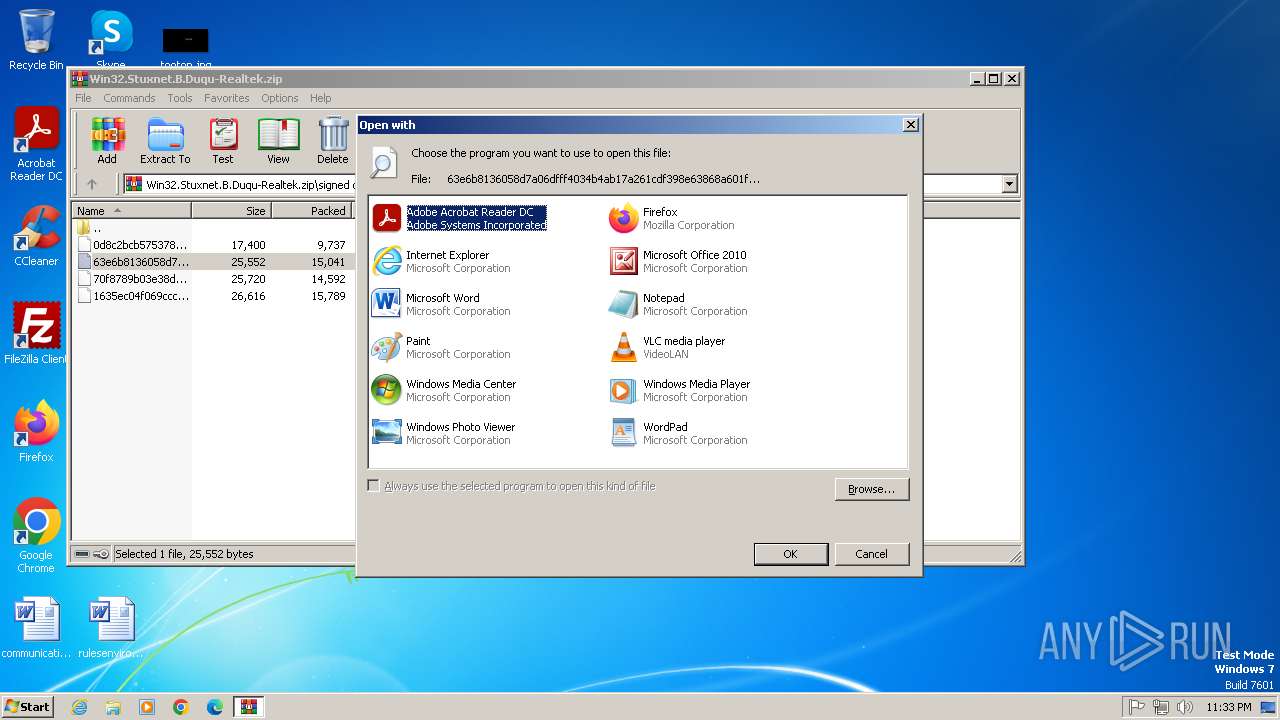
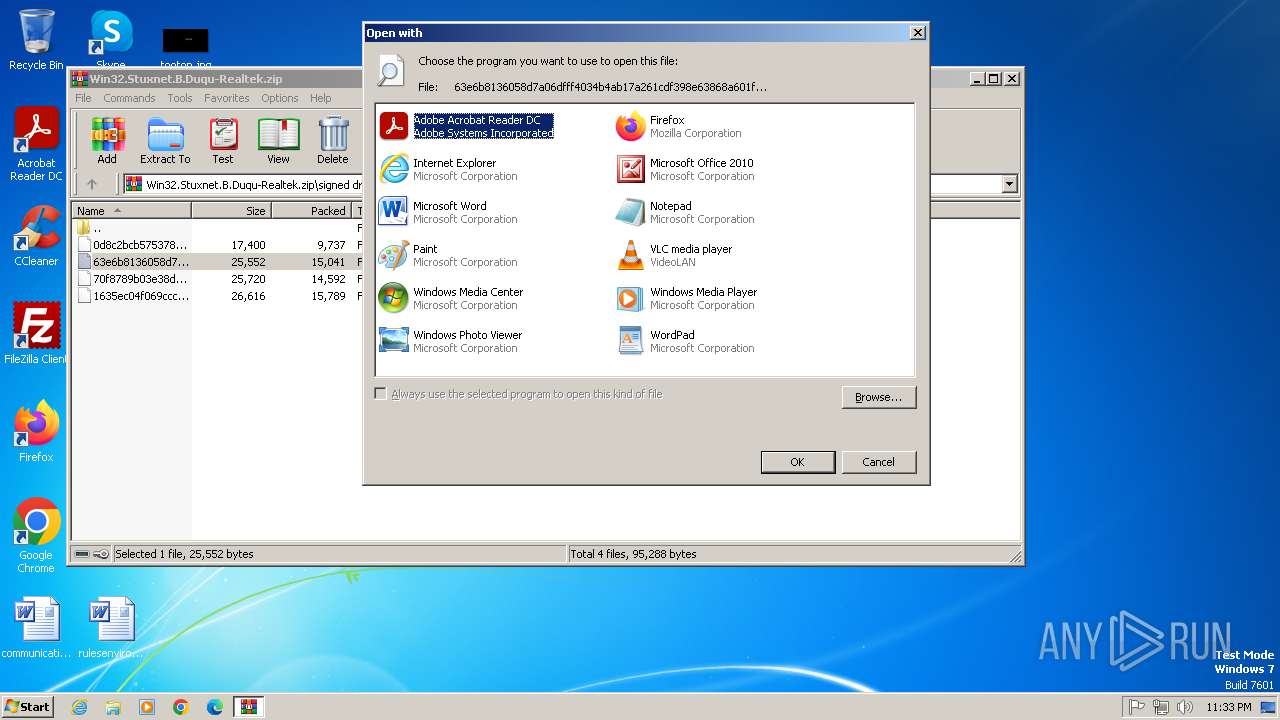
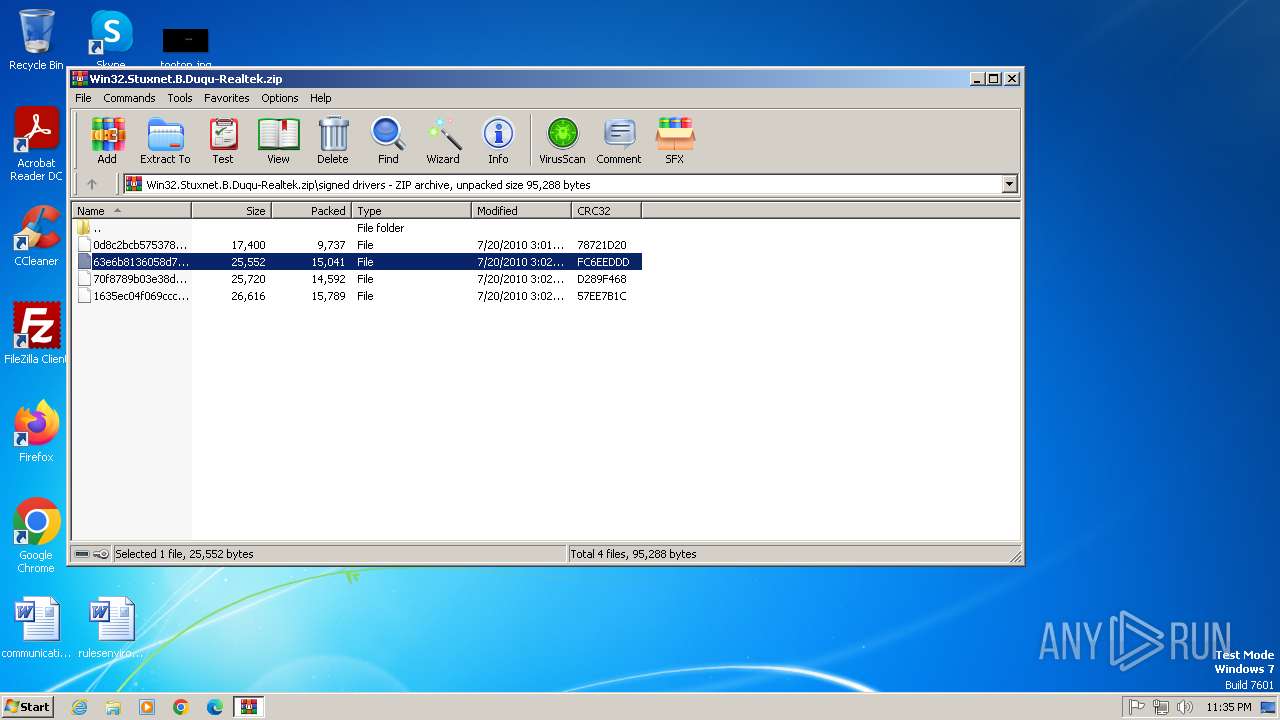
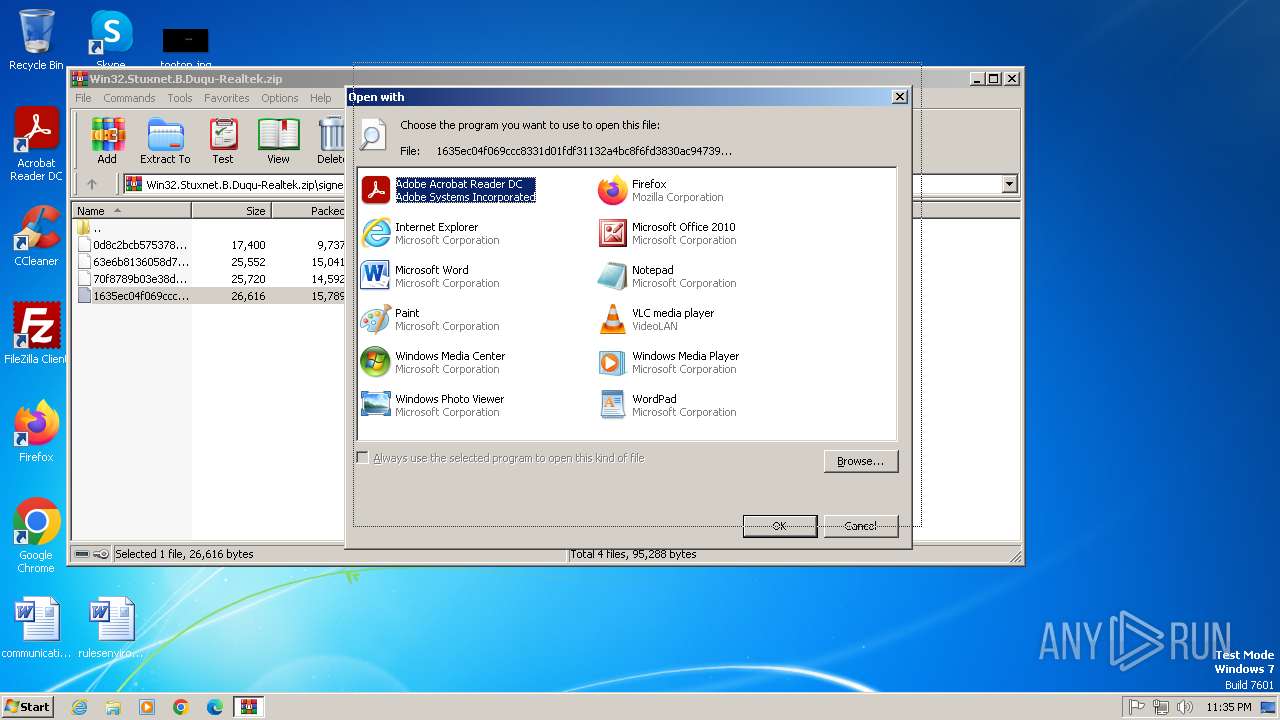
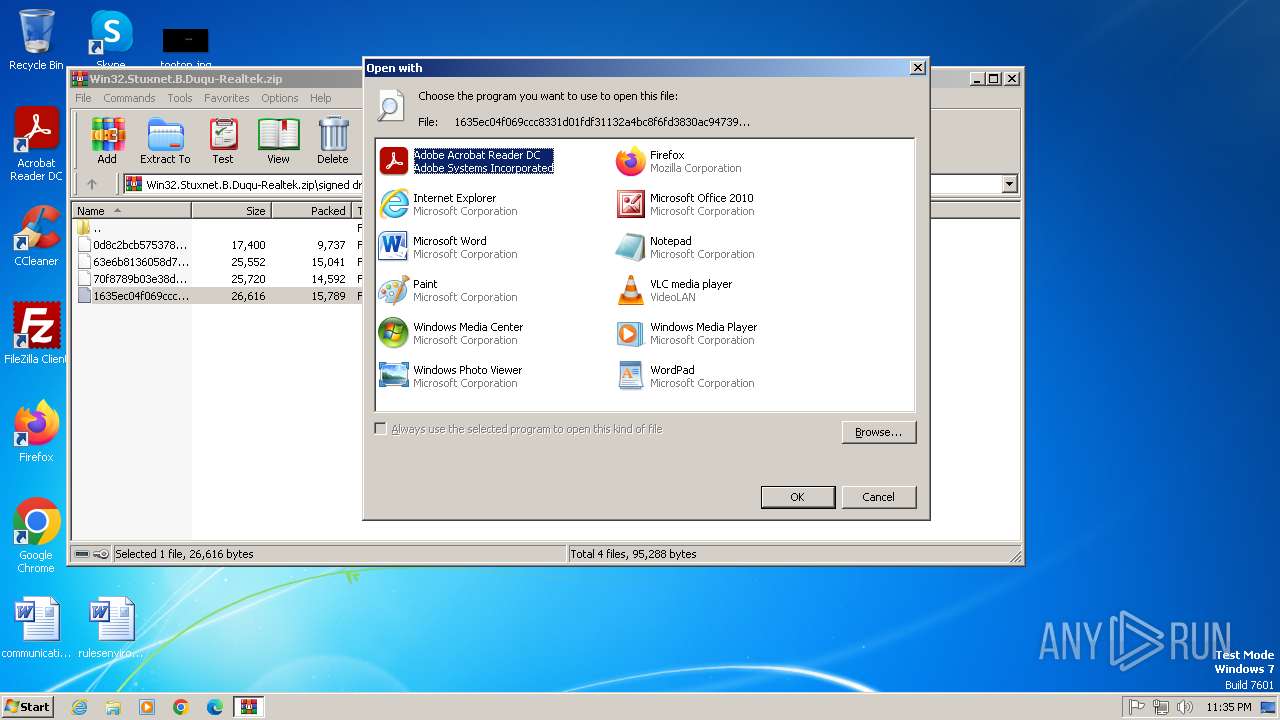
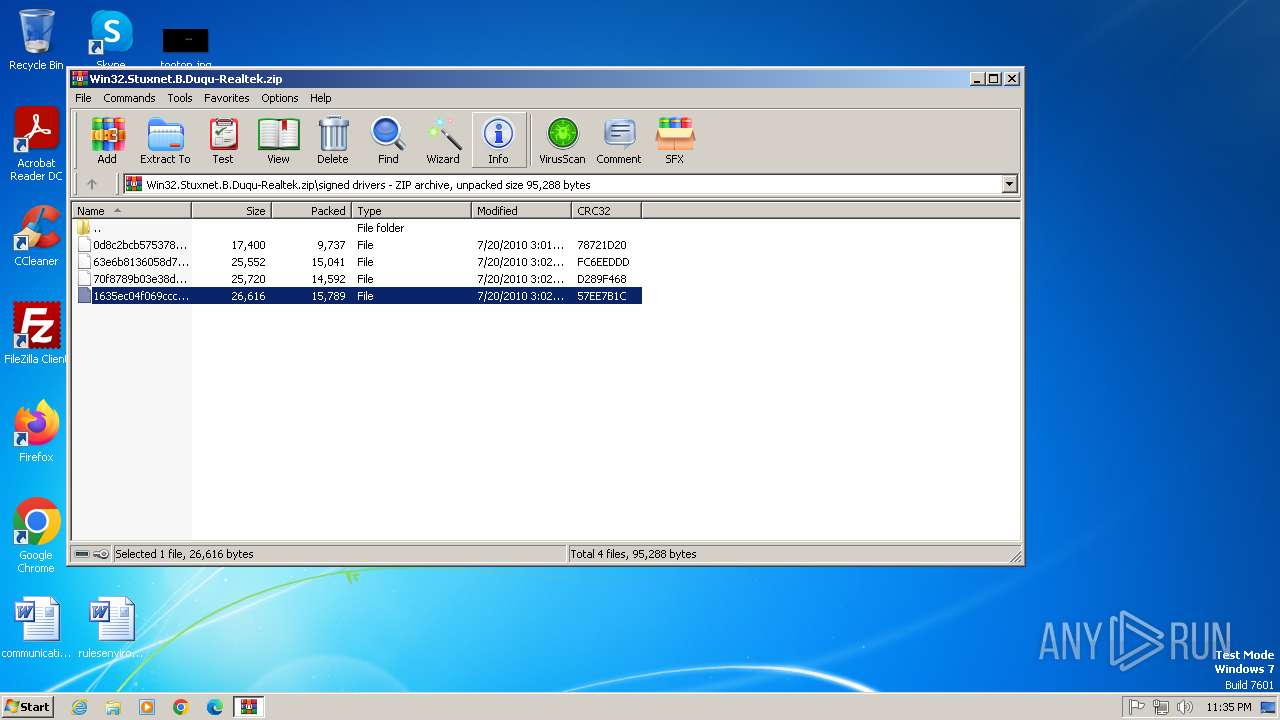
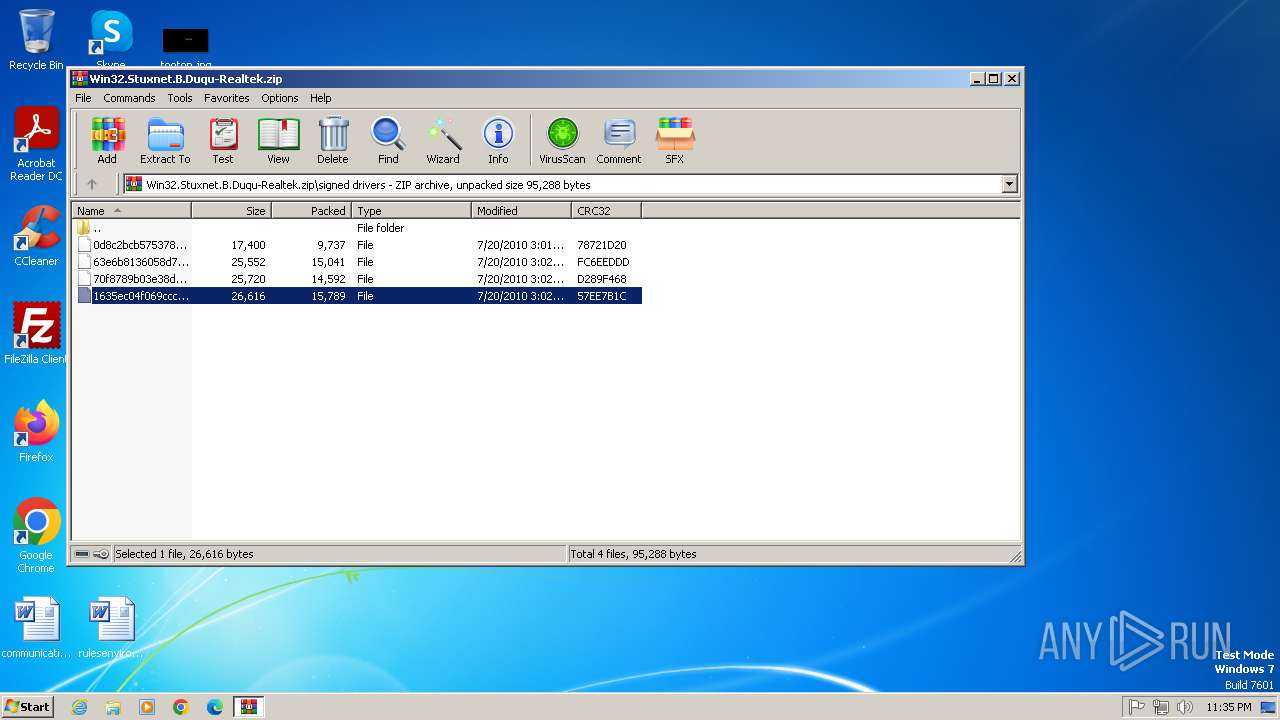
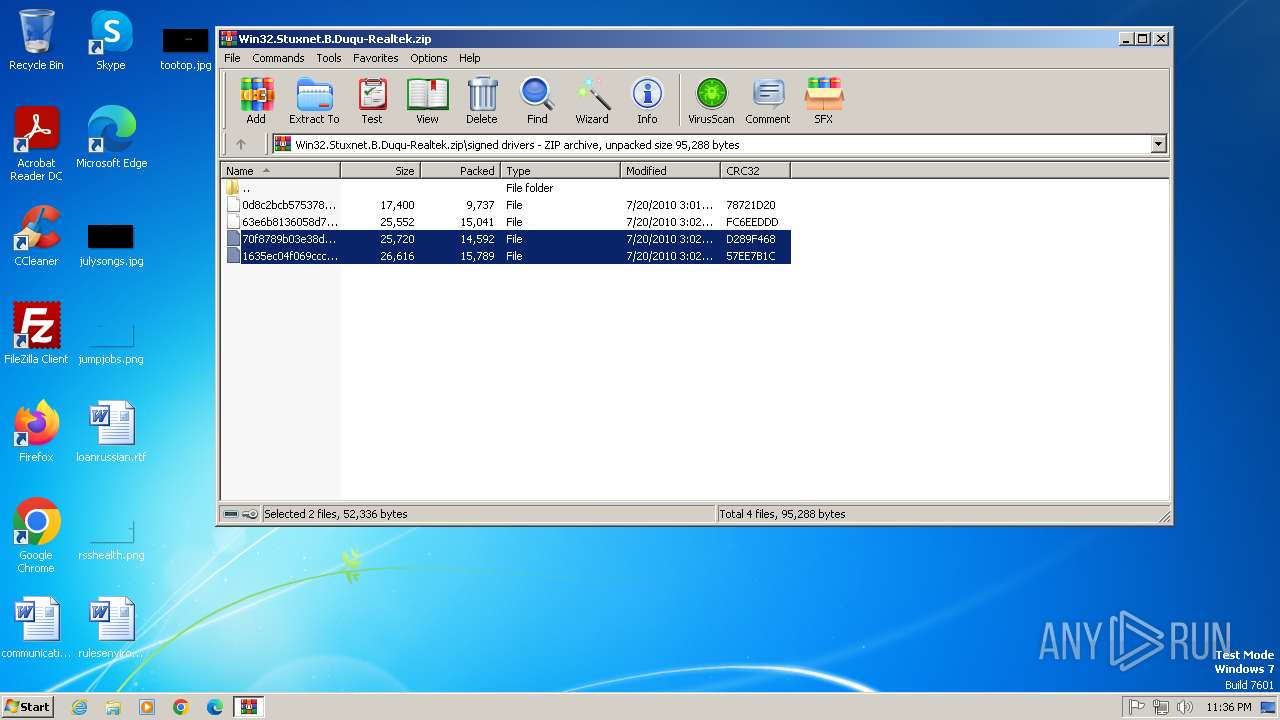
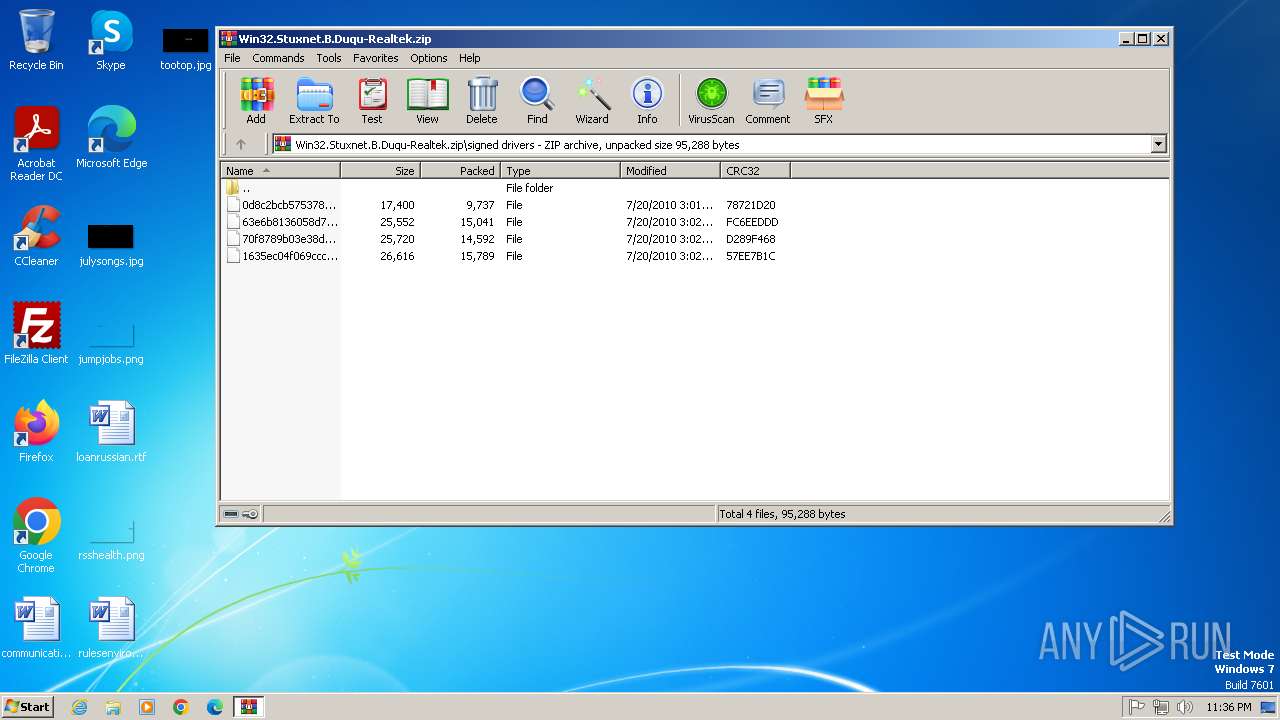
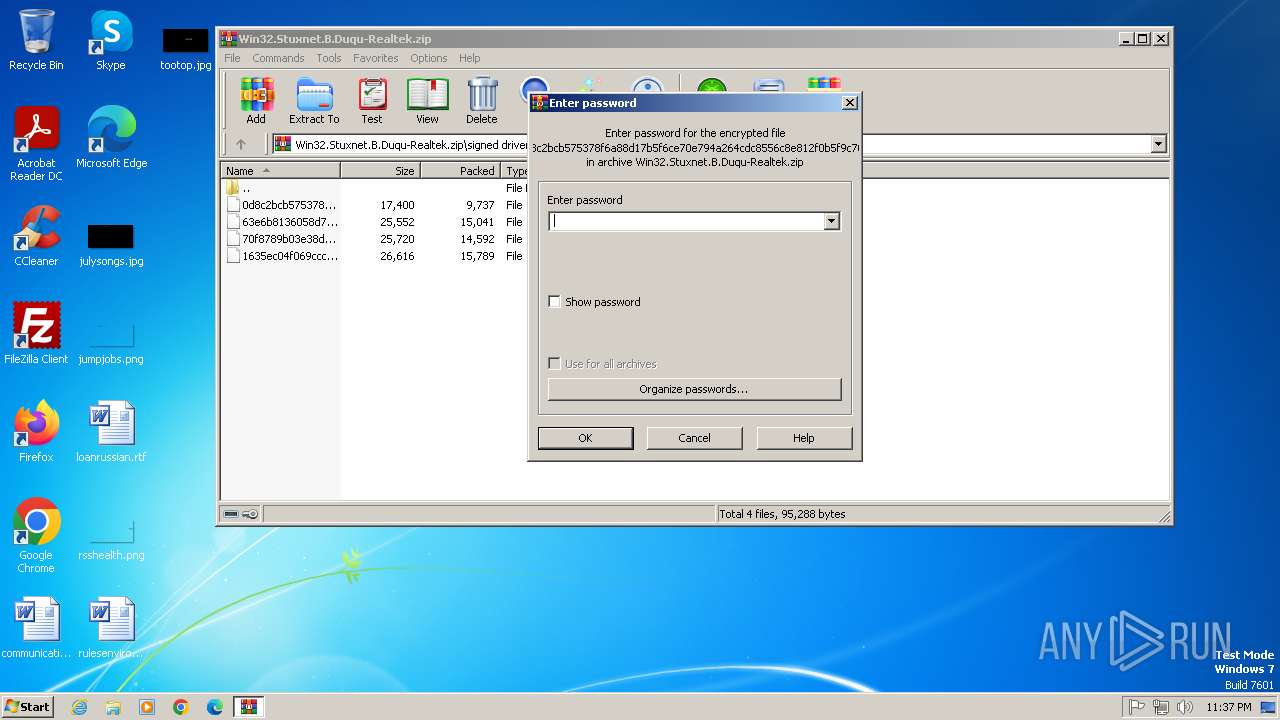
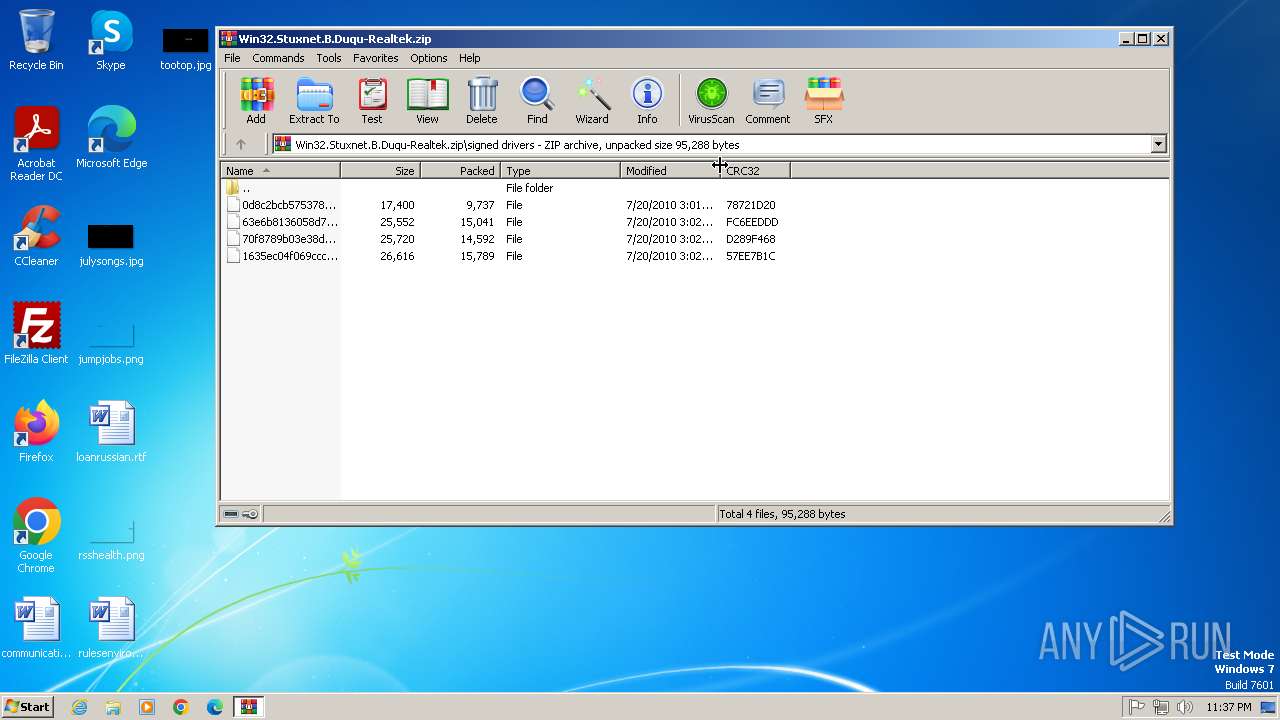
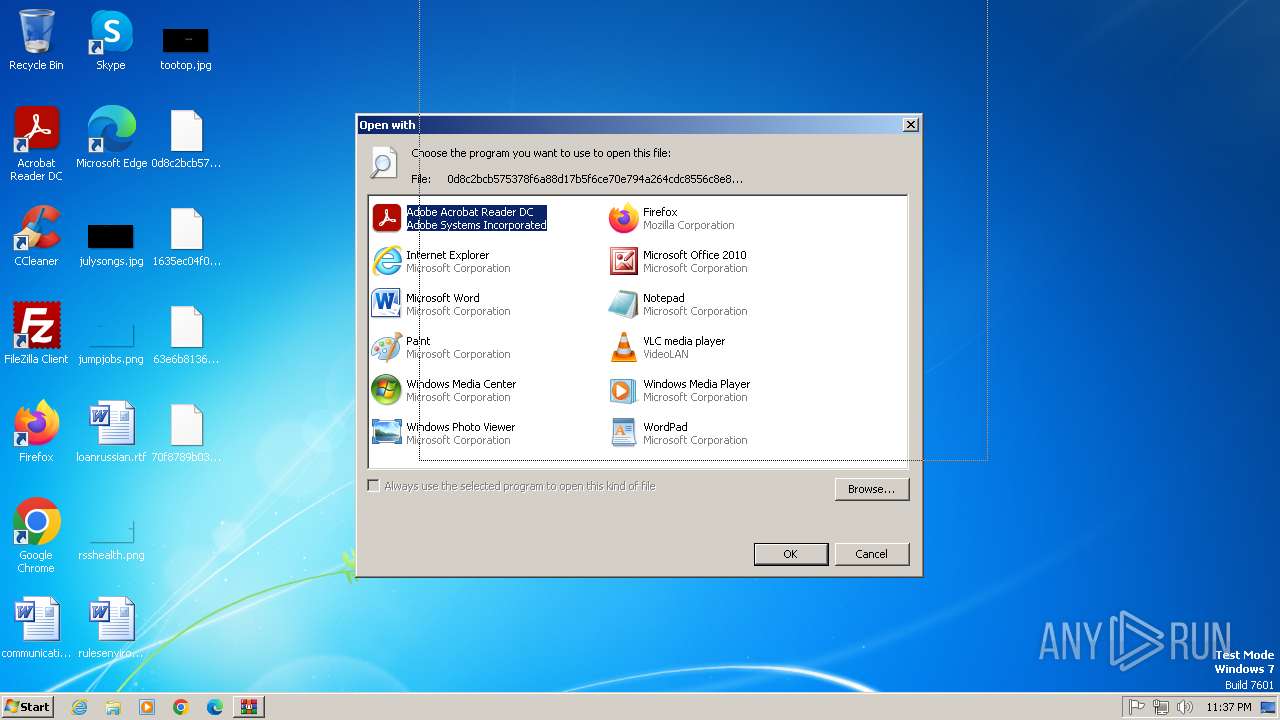
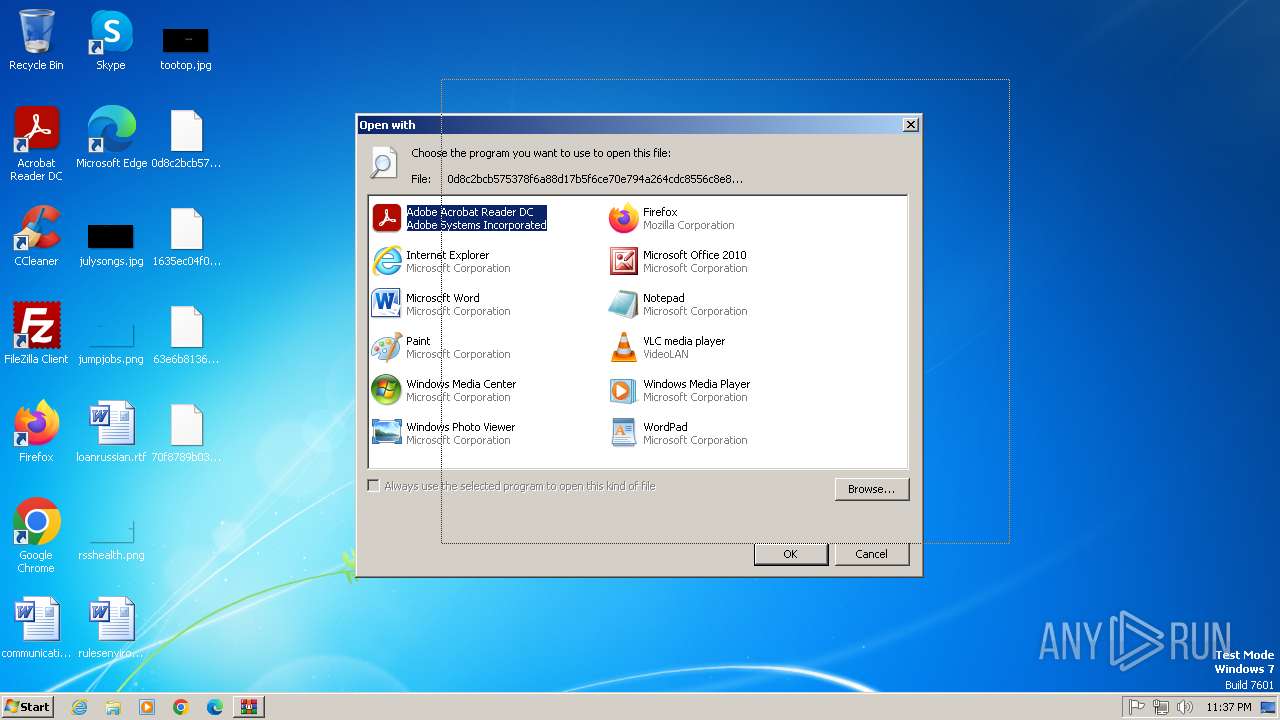
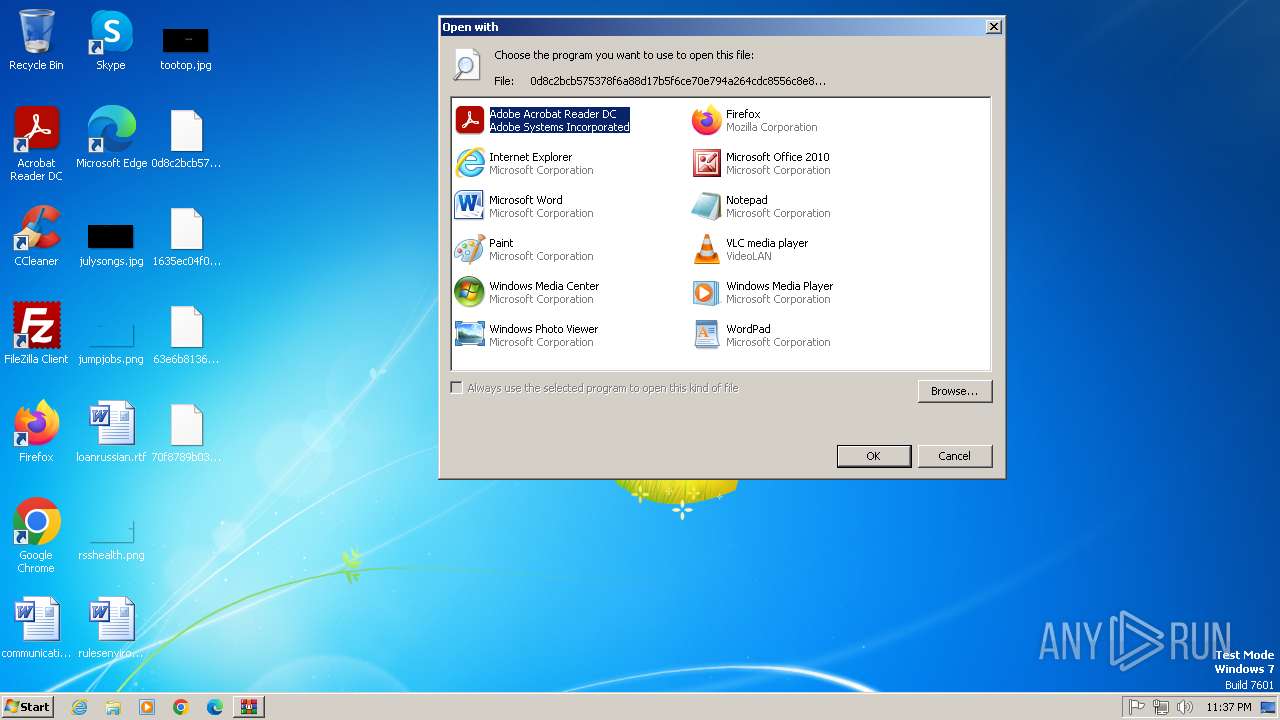
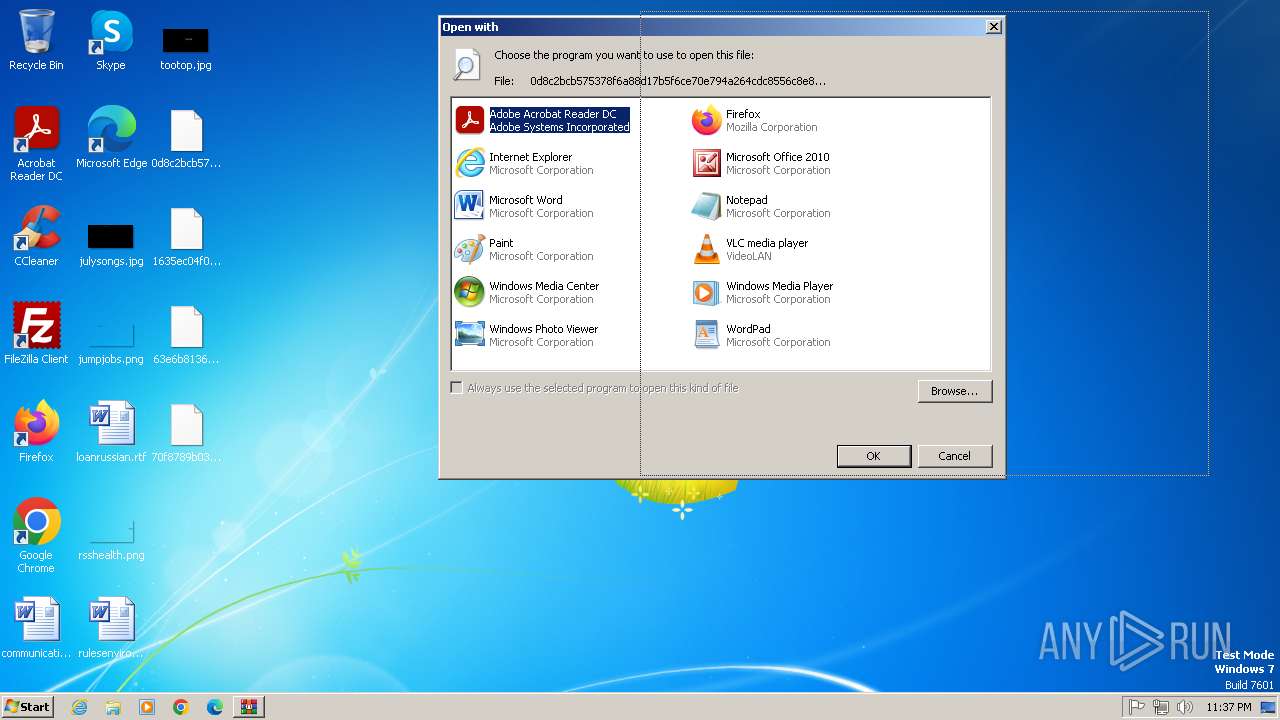
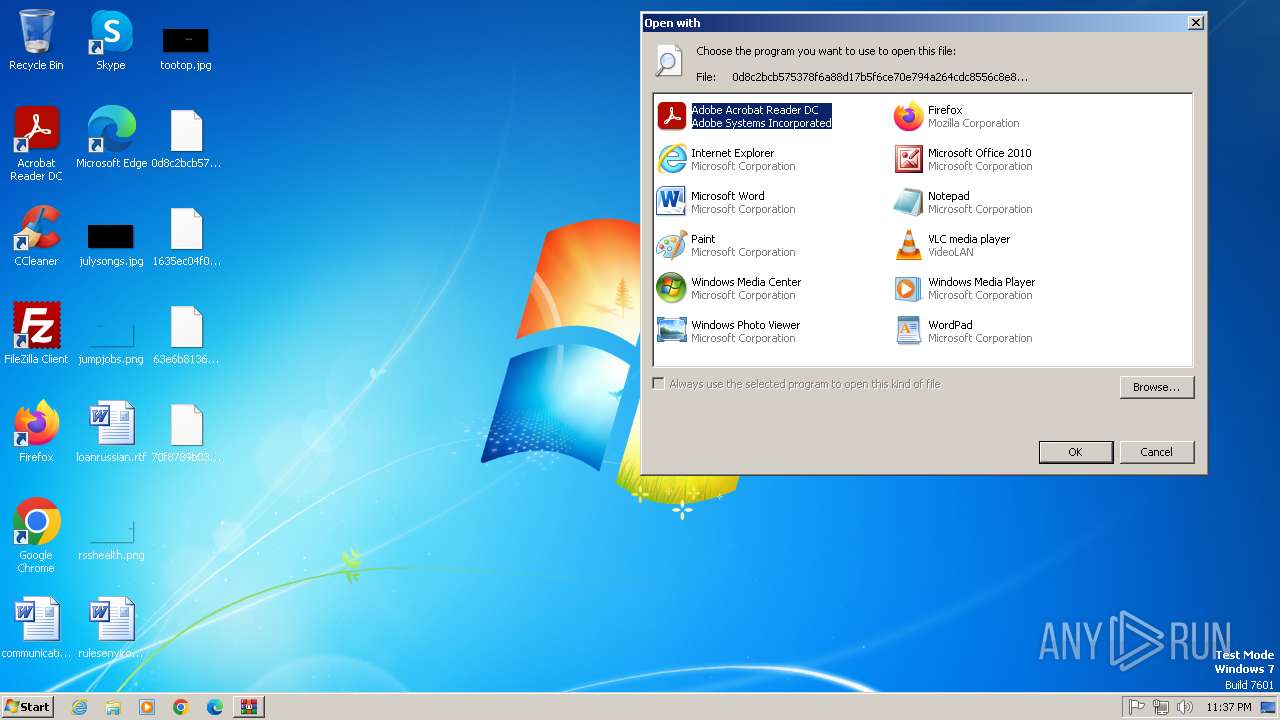
| File name: | Win32.Stuxnet.B.Duqu-Realtek.zip |
| Full analysis: | https://app.any.run/tasks/9a41a17d-0a9b-4188-8c86-4bb7fe331e32 |
| Verdict: | Malicious activity |
| Analysis date: | April 13, 2025, 22:33:15 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | C5D82342430CFD542BC287B178025E5F |
| SHA1: | D7DDDCC72F69CB9B11E7034A32D5308B27B09ADD |
| SHA256: | 7DAFE09A44E72C7B6522319E40C3FADCBAD7A0B42D584988A1BE8DE818689896 |
| SSDEEP: | 1536:TArN3d/cPIx4UECs/Bi2maE7aIRbBvylZGI:krNhcPo0vF6La3 |
MALICIOUS
GENERIC has been found (auto)
- WinRAR.exe (PID: 1224)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1224)
Reads the Internet Settings
- rundll32.exe (PID: 1572)
- rundll32.exe (PID: 2464)
- rundll32.exe (PID: 3280)
- rundll32.exe (PID: 2960)
- rundll32.exe (PID: 2332)
- rundll32.exe (PID: 3164)
Process drops legitimate windows executable
- WinRAR.exe (PID: 1224)
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 1224)
- iexplore.exe (PID: 1336)
There is functionality for taking screenshot (YARA)
- AcroRd32.exe (PID: 3752)
Creates file in the systems drive root
- AcroRd32.exe (PID: 3752)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 1224)
- iexplore.exe (PID: 1336)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 1572)
- rundll32.exe (PID: 2332)
- rundll32.exe (PID: 2960)
- rundll32.exe (PID: 2464)
- rundll32.exe (PID: 3280)
- rundll32.exe (PID: 3164)
Application launched itself
- iexplore.exe (PID: 1336)
- AcroRd32.exe (PID: 948)
- RdrCEF.exe (PID: 3180)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1224)
- iexplore.exe (PID: 1336)
Manual execution by a user
- rundll32.exe (PID: 3980)
Modifies the phishing filter of IE
- iexplore.exe (PID: 1336)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2010:07:22 09:03:34 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
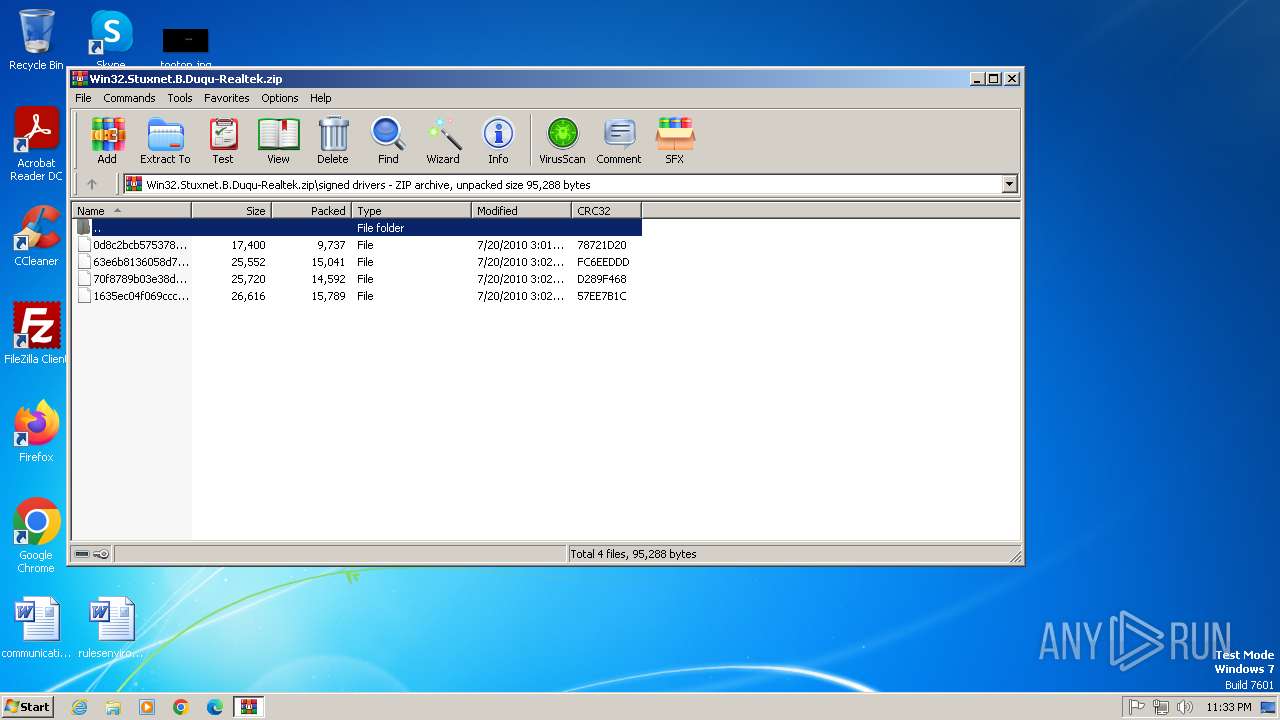
| ZipFileName: | signed drivers/ |
Total processes
59
Monitored processes
22
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 848 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1180,7728931647596550113,15742208958910796196,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=8213153883690146343 --mojo-platform-channel-handle=1452 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 948 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Temp\Rar$DIb1224.1472\1635ec04f069ccc8331d01fdf31132a4bc8f6fd3830ac94739df95ee093c555c" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | rundll32.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1224 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Win32.Stuxnet.B.Duqu-Realtek.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1336 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIb1224.43992\63e6b8136058d7a06dfff4034b4ab17a261cdf398e63868a601f77ddd1b32802 | C:\Program Files\Internet Explorer\iexplore.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1572 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIb1224.41641\0d8c2bcb575378f6a88d17b5f6ce70e794a264cdc8556c8e812f0b5f9c709198 | C:\Windows\System32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1784 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1336 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2276 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIb1224.41641\0d8c2bcb575378f6a88d17b5f6ce70e794a264cdc8556c8e812f0b5f9c709198 | C:\Windows\System32\notepad.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2332 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIb1224.43992\63e6b8136058d7a06dfff4034b4ab17a261cdf398e63868a601f77ddd1b32802 | C:\Windows\System32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2416 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\Rar$DIb1224.43992\63e6b8136058d7a06dfff4034b4ab17a261cdf398e63868a601f77ddd1b32802 | C:\Program Files\Internet Explorer\iexplore.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2464 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIb1224.48086\63e6b8136058d7a06dfff4034b4ab17a261cdf398e63868a601f77ddd1b32802 | C:\Windows\System32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
26 860
Read events
26 210
Write events
580
Delete events
70
Modification events
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Win32.Stuxnet.B.Duqu-Realtek.zip | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1224) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
15
Suspicious files
76
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3180 | RdrCEF.exe | — | ||
MD5:— | SHA256:— | |||
| 1336 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF192B89998CD98466.TMP | binary | |
MD5:71B6395E02D172D266C6684B886D7187 | SHA256:81A33C68A71667C95AA5668F8F1D77585329AB457DDB428EF7E971F7D1643AA0 | |||
| 1336 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{71025D2D-18B7-11F0-B32B-12A9866C77DE}.dat | binary | |
MD5:4FBA5725712E432F21BDE3A7672A8770 | SHA256:D22F2C7CE4E18ECC80DF41052789AAFE30D9DF44AE90456A083A011B65080548 | |||
| 1336 | iexplore.exe | C:\Users\admin\Downloads\63e6b8136058d7a06dfff4034b4ab17a261cdf398e63868a601f77ddd1b32802.ydrnloi.partial | executable | |
MD5:1E17D81979271CFA44D471430FE123A5 | SHA256:63E6B8136058D7A06DFFF4034B4AB17A261CDF398E63868A601F77DDD1B32802 | |||
| 1224 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb1224.48086\63e6b8136058d7a06dfff4034b4ab17a261cdf398e63868a601f77ddd1b32802 | executable | |
MD5:1E17D81979271CFA44D471430FE123A5 | SHA256:63E6B8136058D7A06DFFF4034B4AB17A261CDF398E63868A601F77DDD1B32802 | |||
| 3752 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Reader\Files\TESTING | binary | |
MD5:DC84B0D741E5BEAE8070013ADDCC8C28 | SHA256:81FF65EFC4487853BDB4625559E69AB44F19E0F5EFBD6D5B2AF5E3AB267C8E06 | |||
| 1224 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb1224.1472\1635ec04f069ccc8331d01fdf31132a4bc8f6fd3830ac94739df95ee093c555c | executable | |
MD5:F8153747BAE8B4AE48837EE17172151E | SHA256:1635EC04F069CCC8331D01FDF31132A4BC8F6FD3830AC94739DF95EE093C555C | |||
| 3752 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Reader\SOPHIA.json | binary | |
MD5:01F233C92A89C705229A0D63D09F846A | SHA256:62137C4381ACC2DE8BCA158AD9D9CE730BD7A96A39A2FB64CE7CFA5C861CF7B4 | |||
| 1336 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF4D62260D1AEFD647.TMP | binary | |
MD5:B9712D81A45DD853ED58D34D517D1033 | SHA256:9BA6264966B841876F27BF9670EBF9D0CDFE1C7BDE36815ED56CDC2EC1A7AEA1 | |||
| 1336 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{670421F3-18B7-11F0-B32B-12A9866C77DE}.dat | binary | |
MD5:EDFAFD1EA458C7196165ABC0AD308FDB | SHA256:501726F685F8A6C13065F06A66E0FFC44737DCD78B2A51D43108031C65618732 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
17
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1336 | iexplore.exe | GET | 404 | 23.50.131.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?a3d6dbbb9db9bca8 | unknown | — | — | whitelisted |
948 | AcroRd32.exe | GET | 404 | 23.50.131.216:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?11521a1b9aa410d0 | unknown | — | — | whitelisted |
948 | AcroRd32.exe | GET | 404 | 23.53.40.8:80 | http://acroipm2.adobe.com/20/rdr/ENU/win/nooem/none/consumer/279_20_13_20064.zip | unknown | — | — | whitelisted |
1080 | svchost.exe | GET | 404 | 208.89.74.31:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?c4805327f819afbf | unknown | — | — | whitelisted |
948 | AcroRd32.exe | GET | 404 | 23.53.40.8:80 | http://acroipm2.adobe.com/20/rdr/ENU/win/nooem/none/consumer/277_20_13_20064.zip | unknown | — | — | whitelisted |
948 | AcroRd32.exe | GET | 404 | 23.53.40.8:80 | http://acroipm2.adobe.com/20/rdr/ENU/win/nooem/none/consumer/281_20_13_20064.zip | unknown | — | — | whitelisted |
948 | AcroRd32.exe | GET | 404 | 23.53.40.8:80 | http://acroipm2.adobe.com/20/rdr/ENU/win/nooem/none/consumer/280_20_13_20064.zip | unknown | — | — | whitelisted |
1080 | svchost.exe | GET | 404 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?178b5f18270f7221 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1336 | iexplore.exe | 23.50.131.200:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | whitelisted |
3180 | RdrCEF.exe | 184.30.16.204:443 | geo2.adobe.com | AKAMAI-AS | DE | whitelisted |
3180 | RdrCEF.exe | 184.30.20.134:443 | armmf.adobe.com | AKAMAI-AS | DE | whitelisted |
948 | AcroRd32.exe | 23.53.40.8:443 | acroipm2.adobe.com | Akamai International B.V. | DE | whitelisted |
3180 | RdrCEF.exe | 52.22.41.97:443 | p13n.adobe.io | AMAZON-AES | US | whitelisted |
948 | AcroRd32.exe | 23.50.131.216:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |