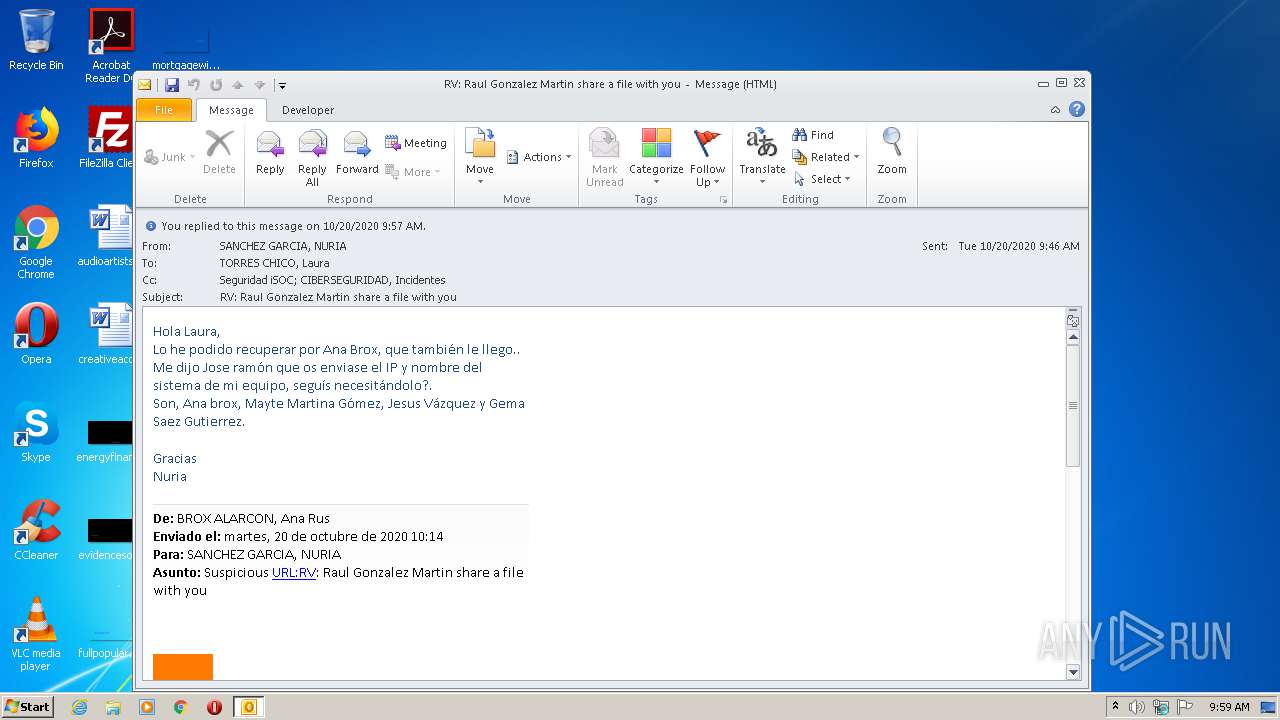
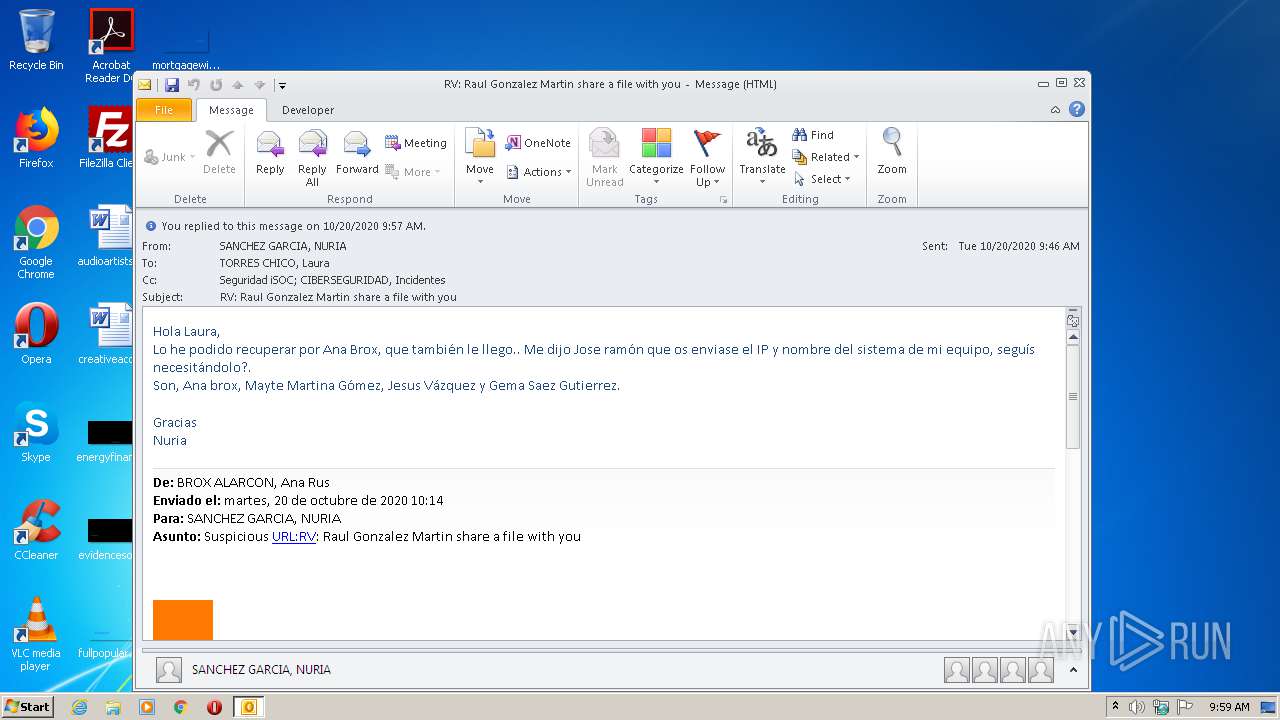
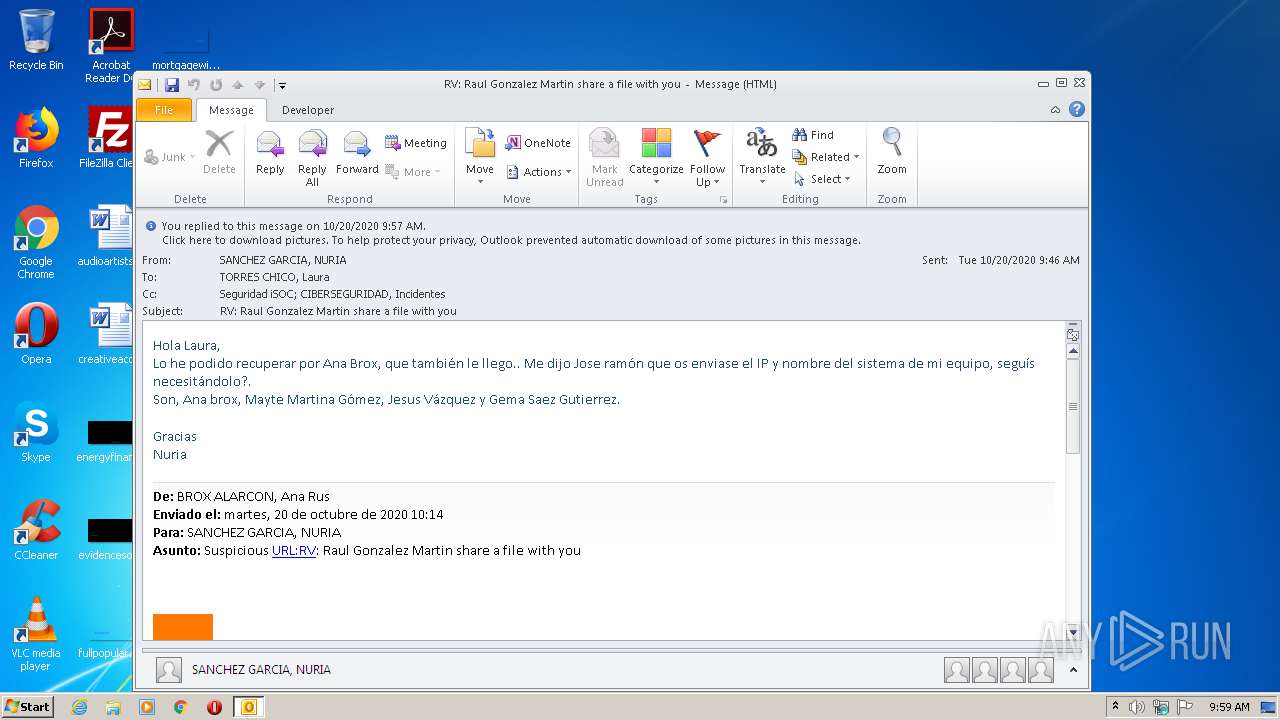
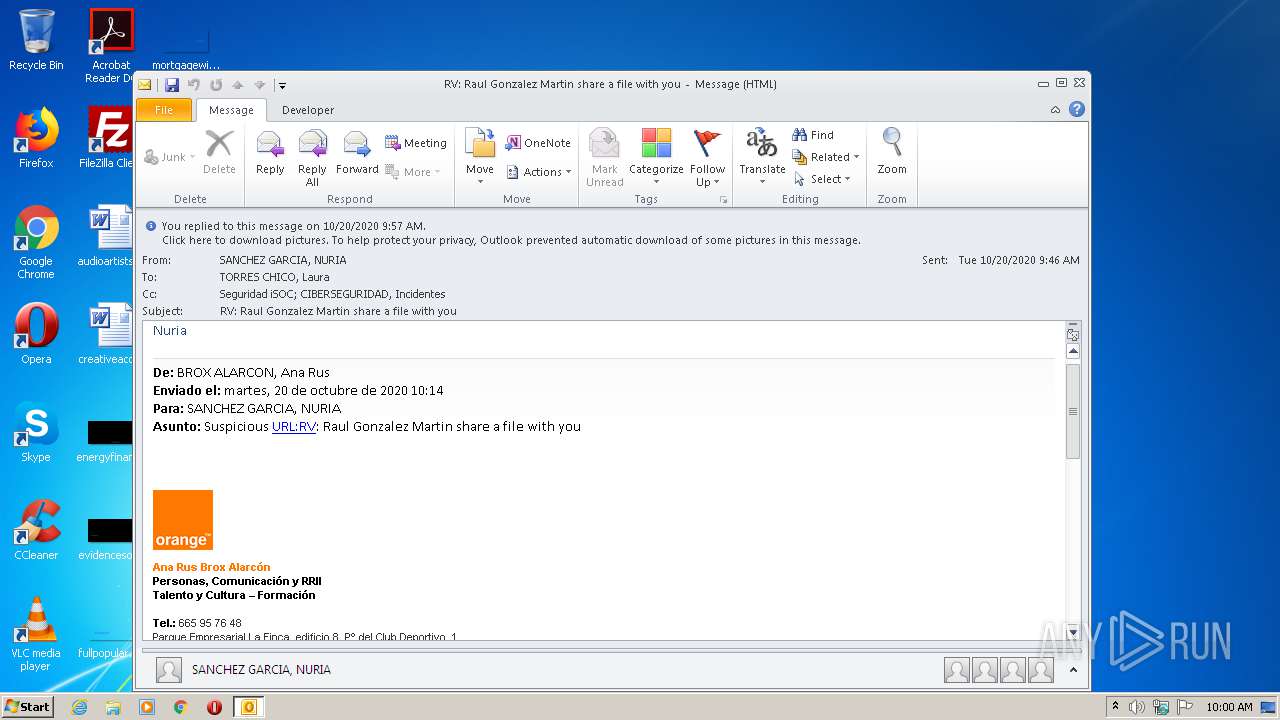
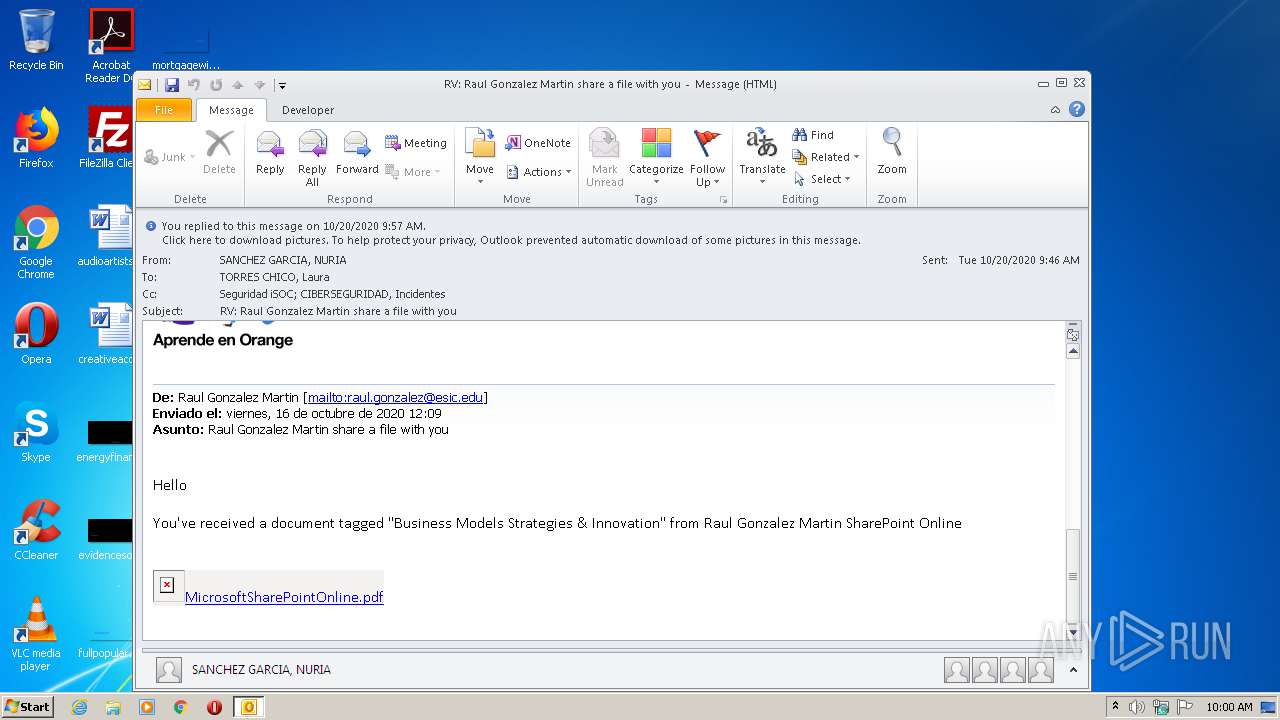
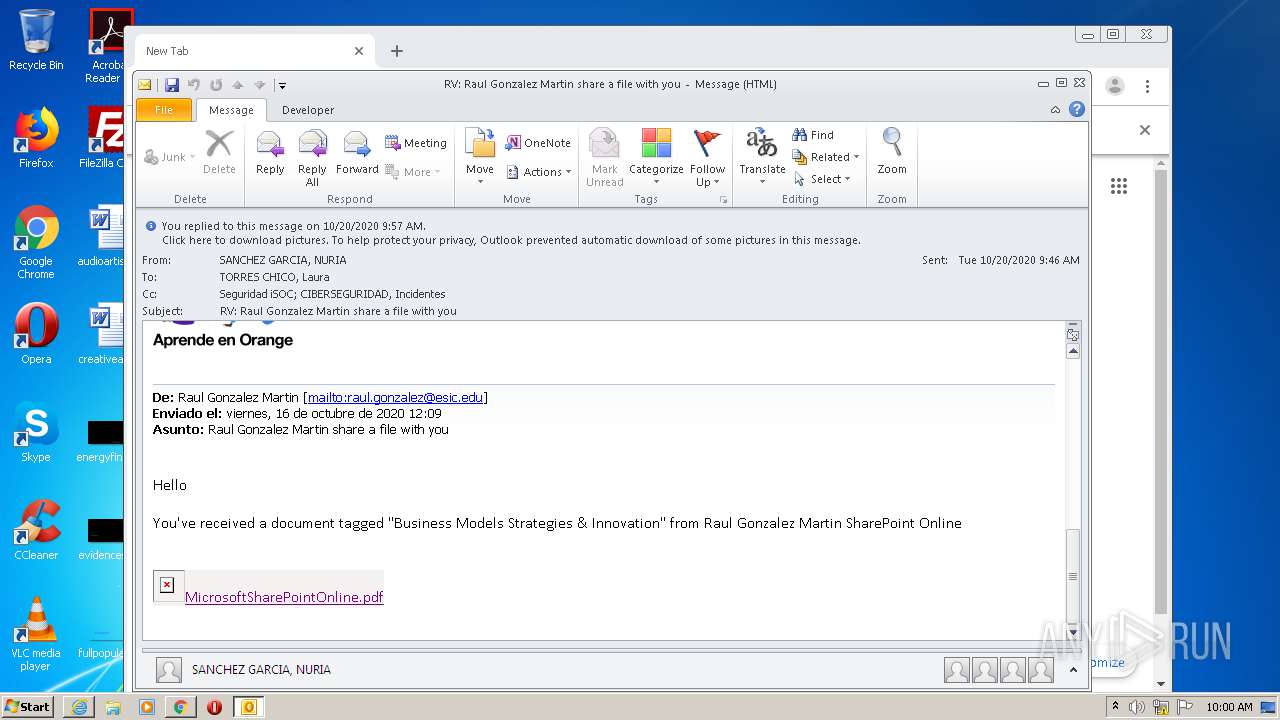
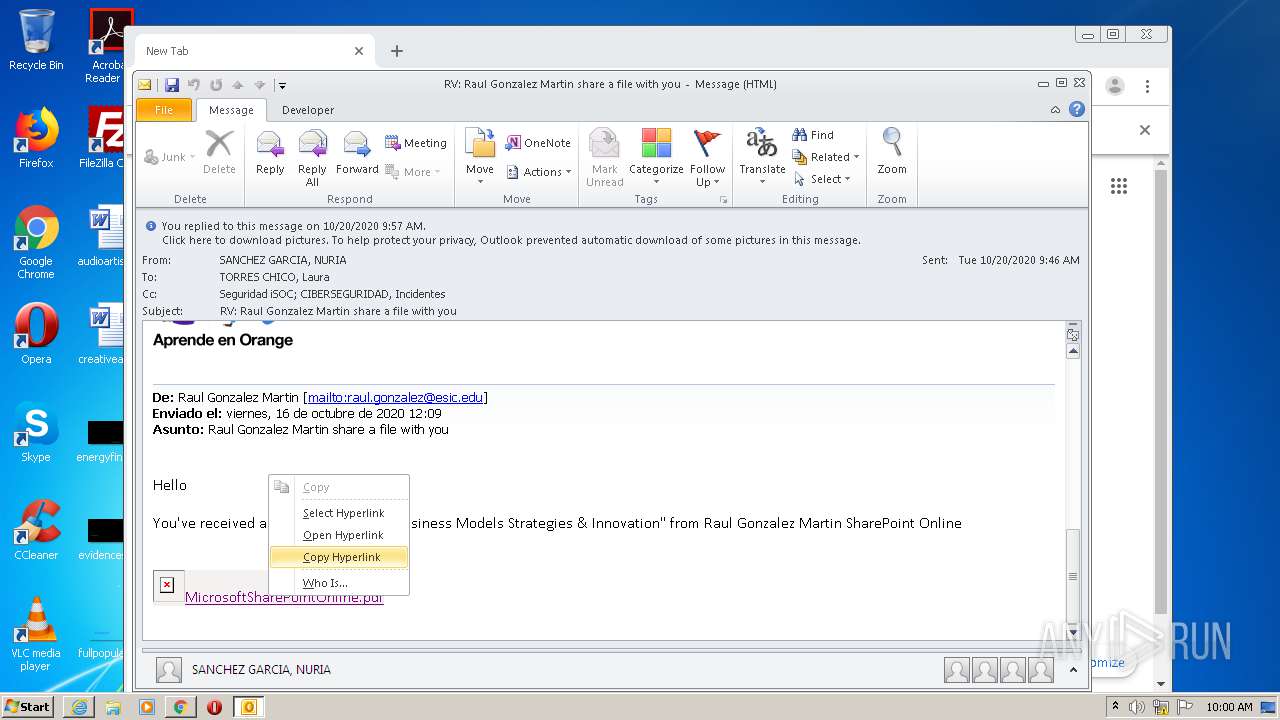
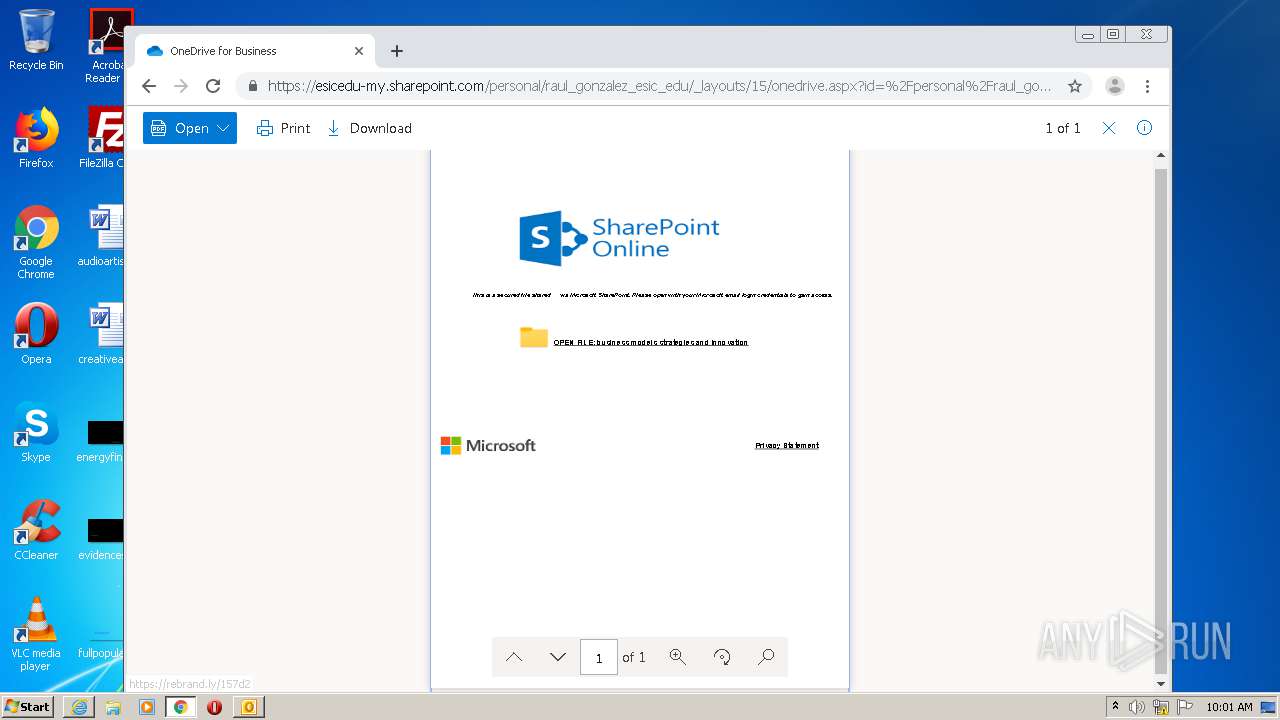
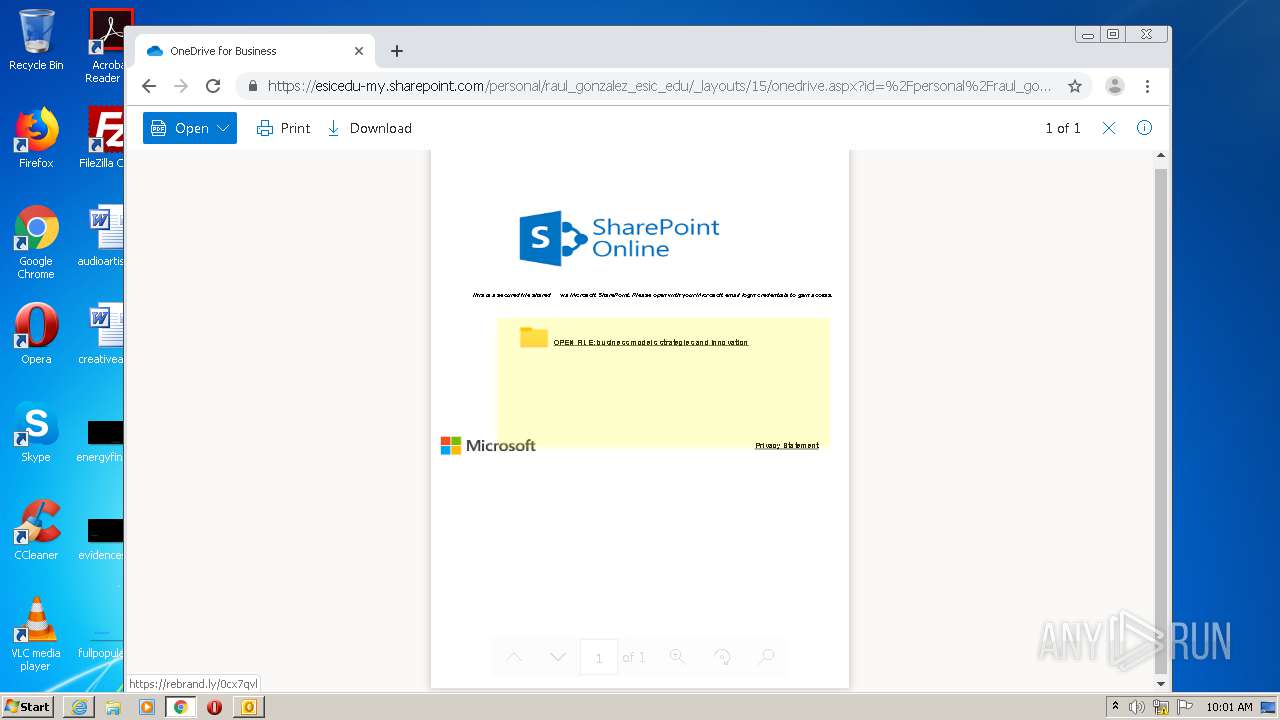
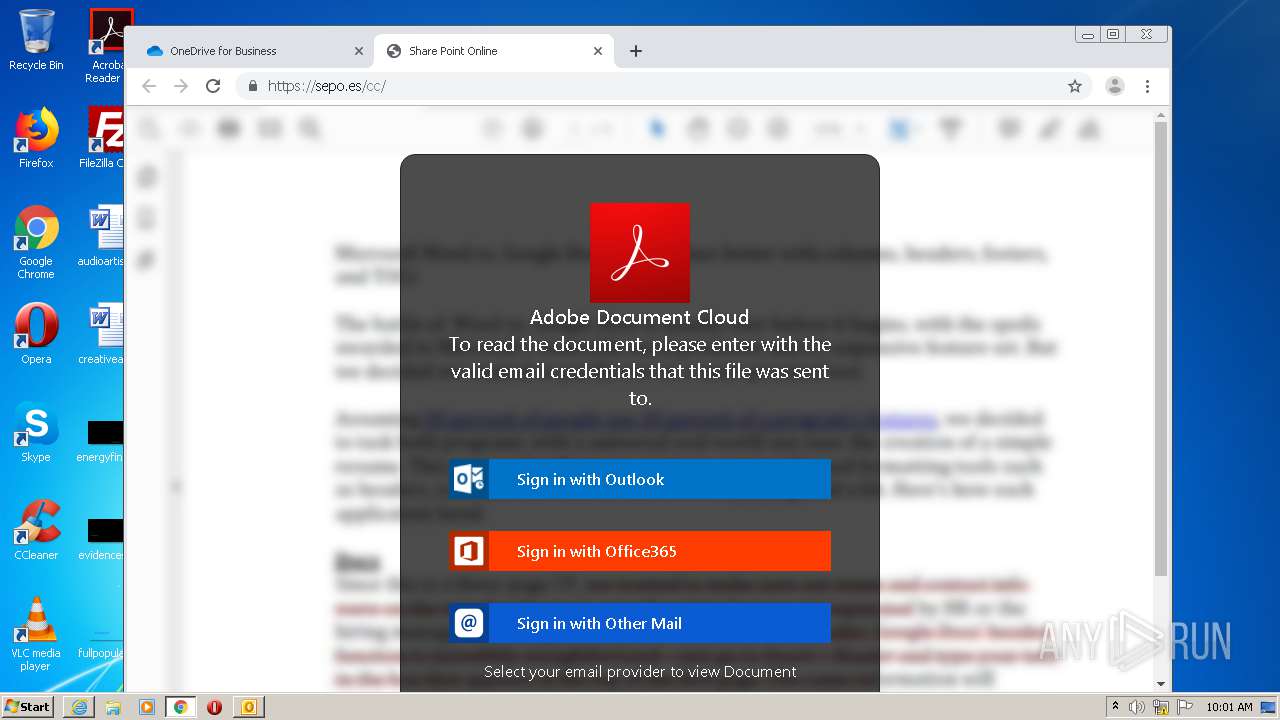
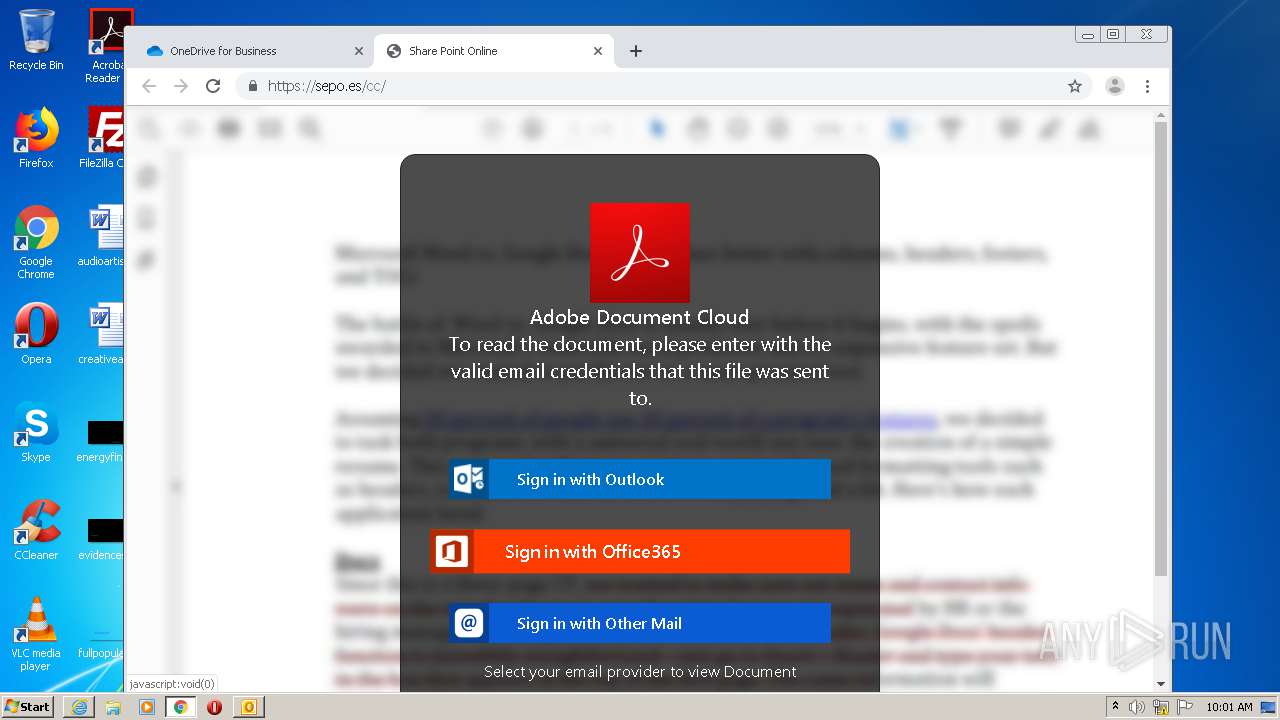
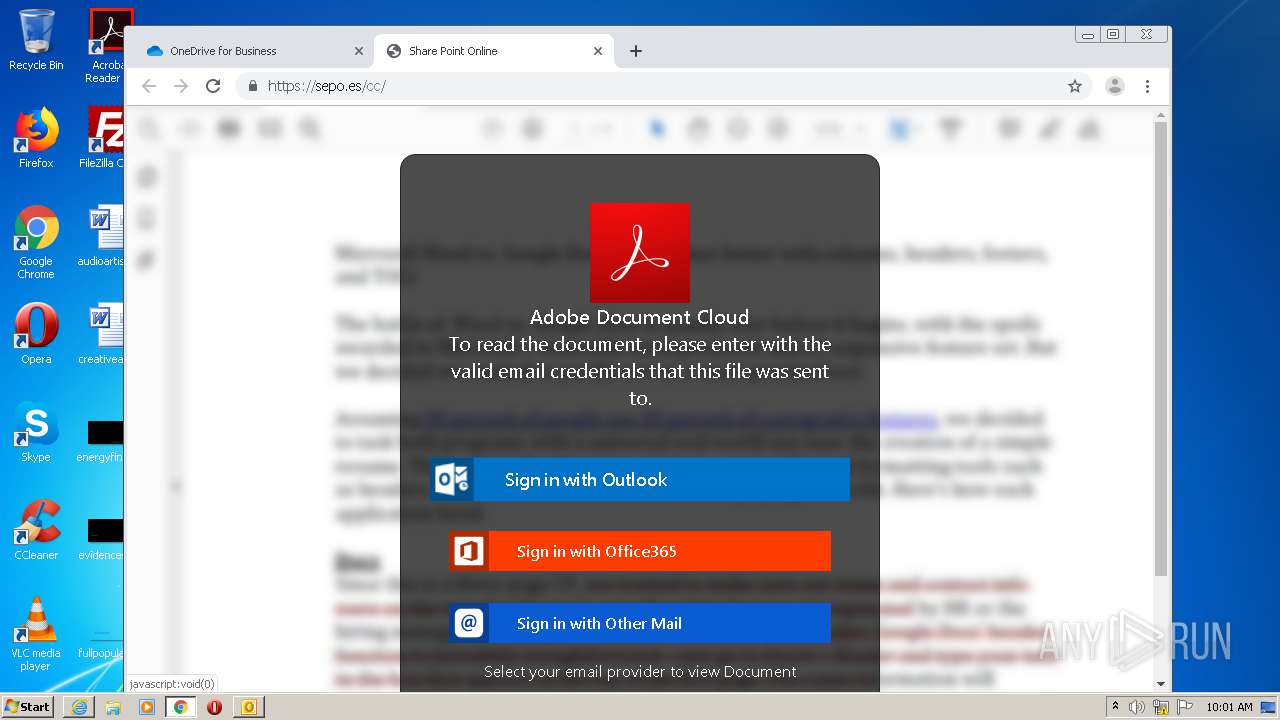
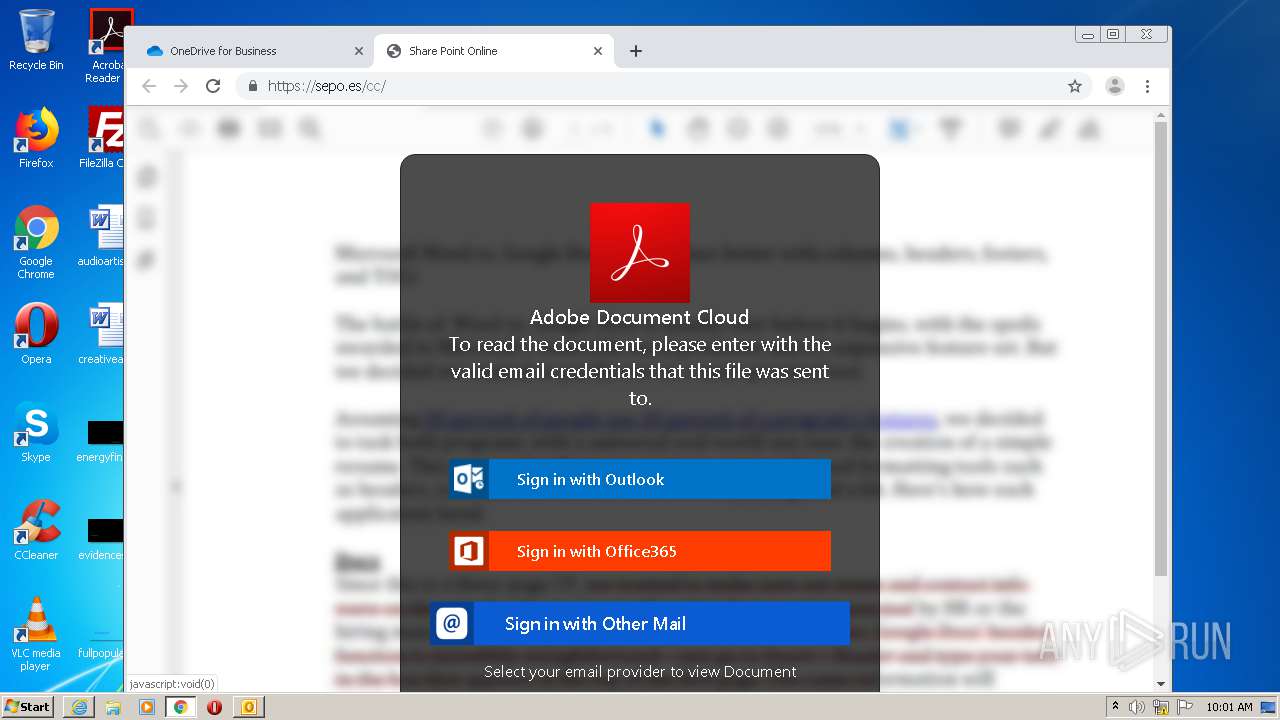
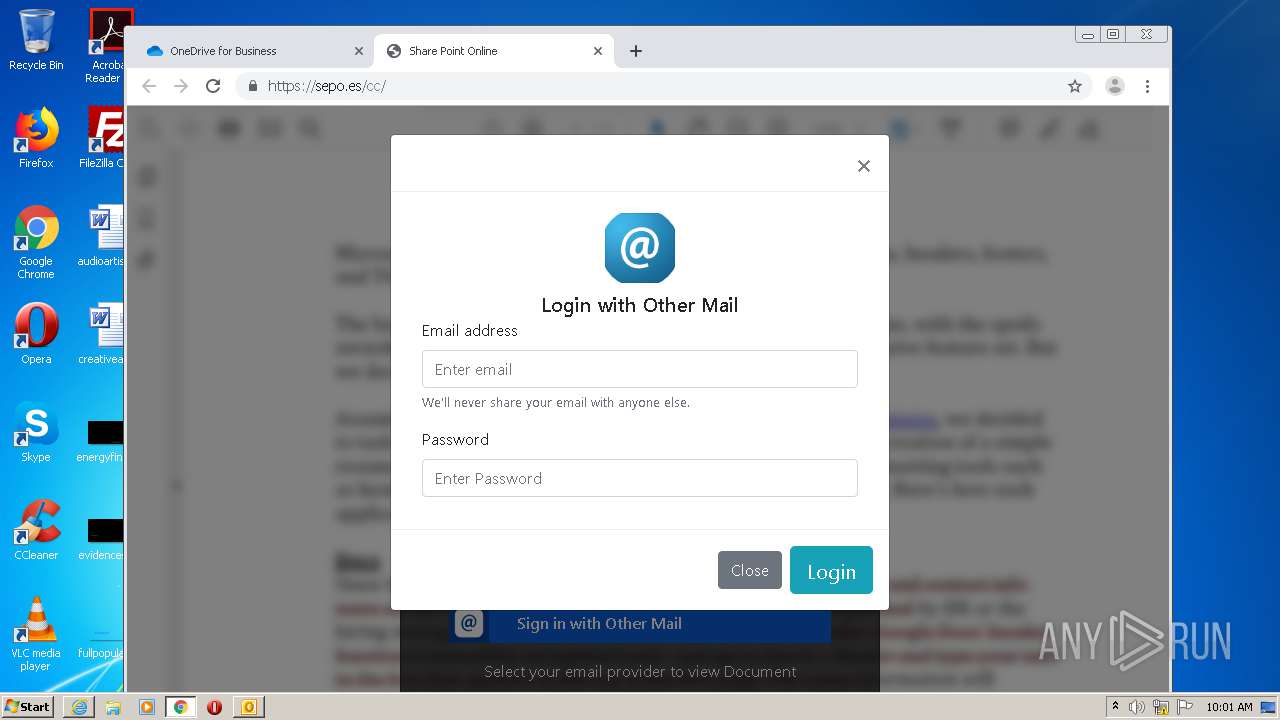
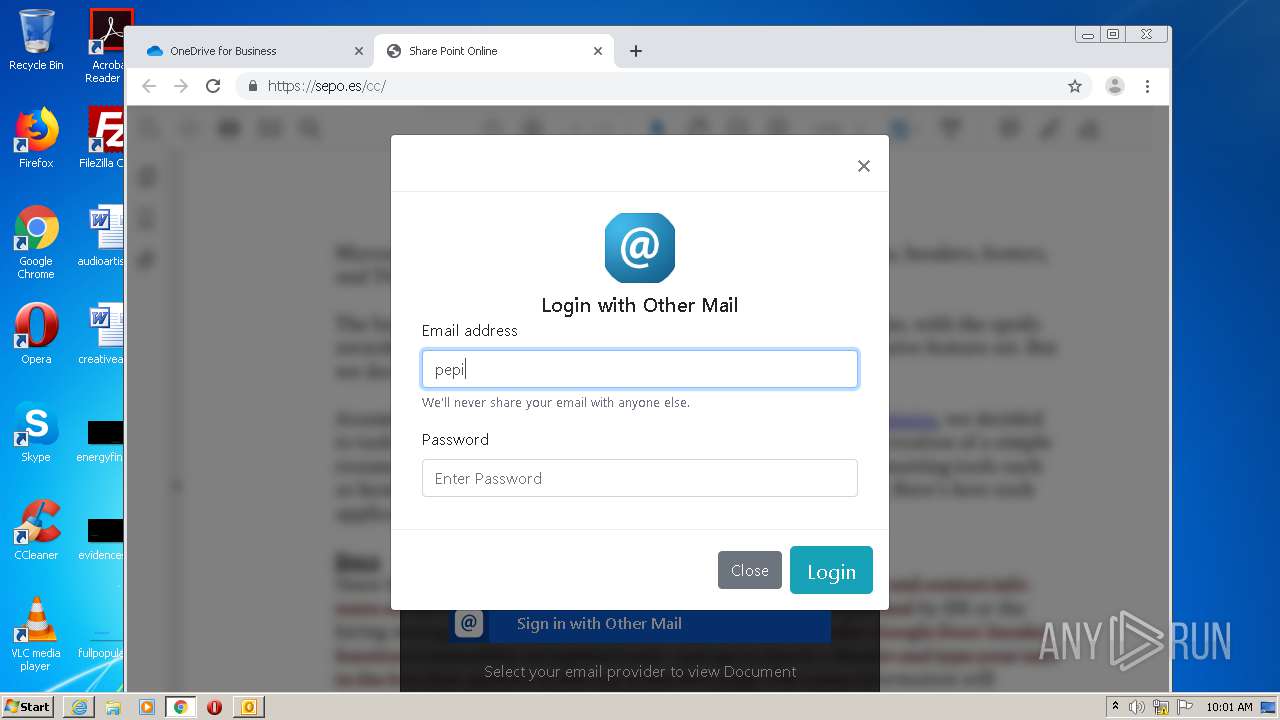
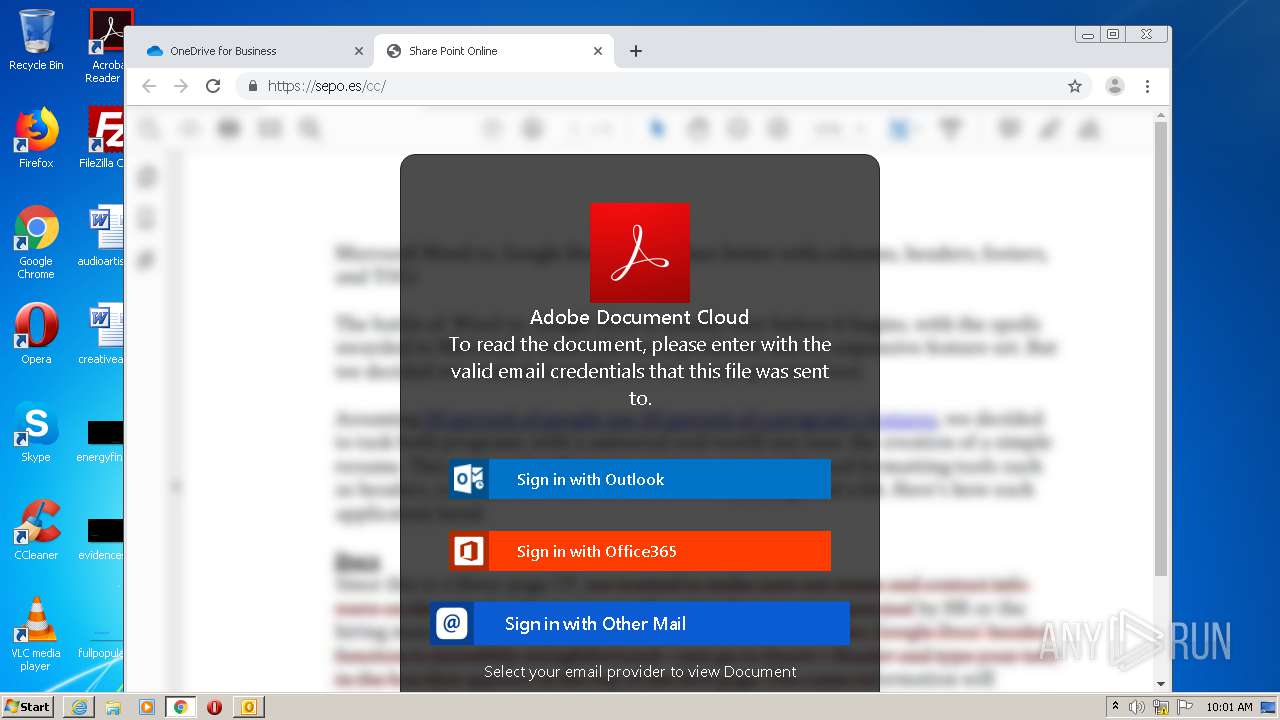
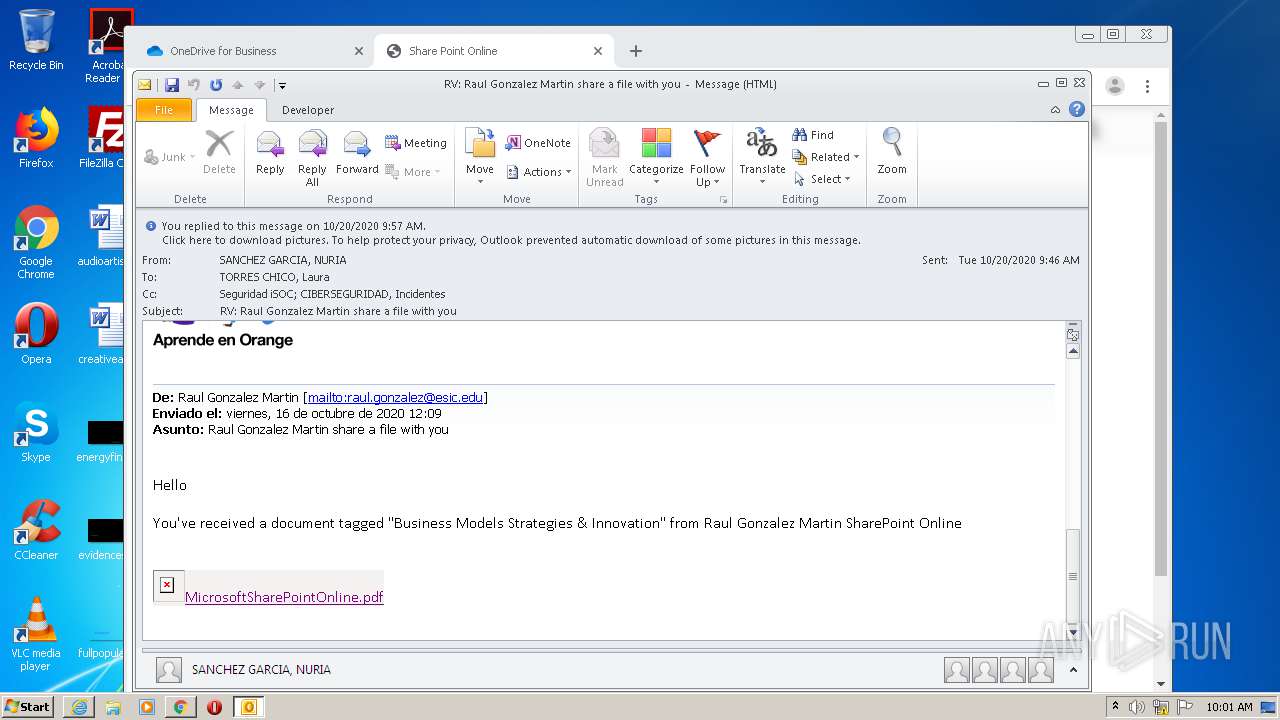
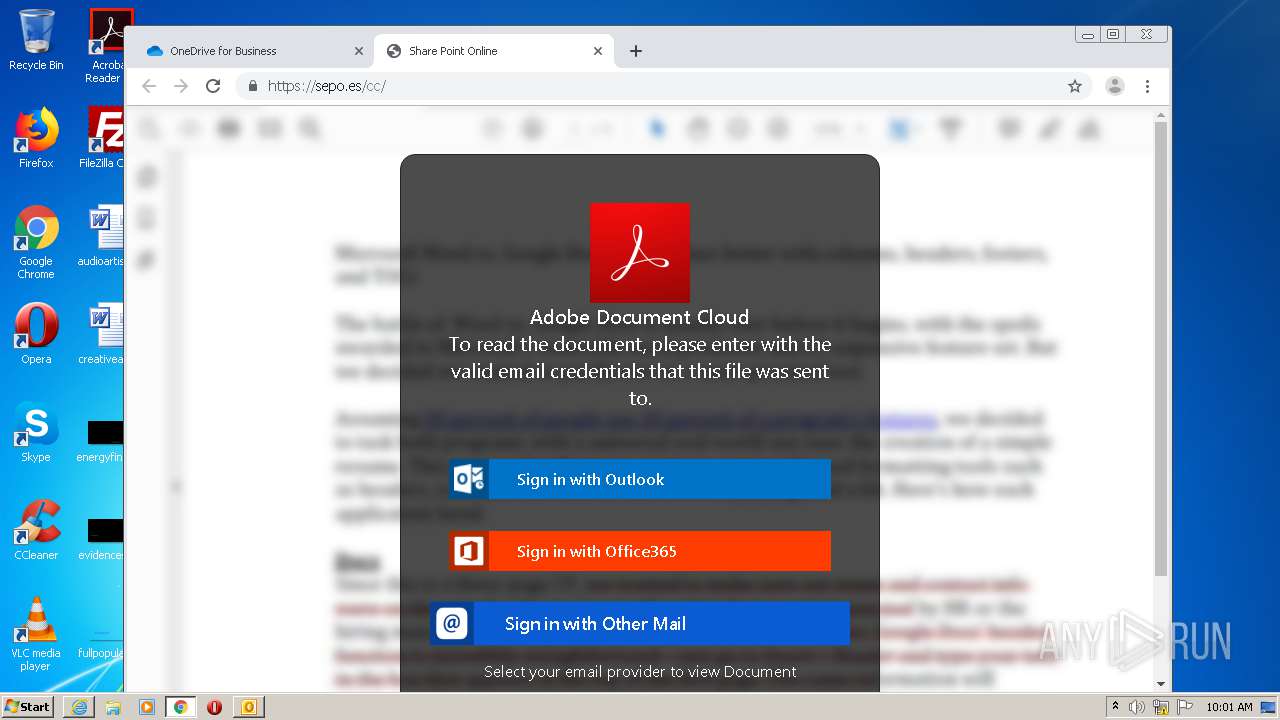
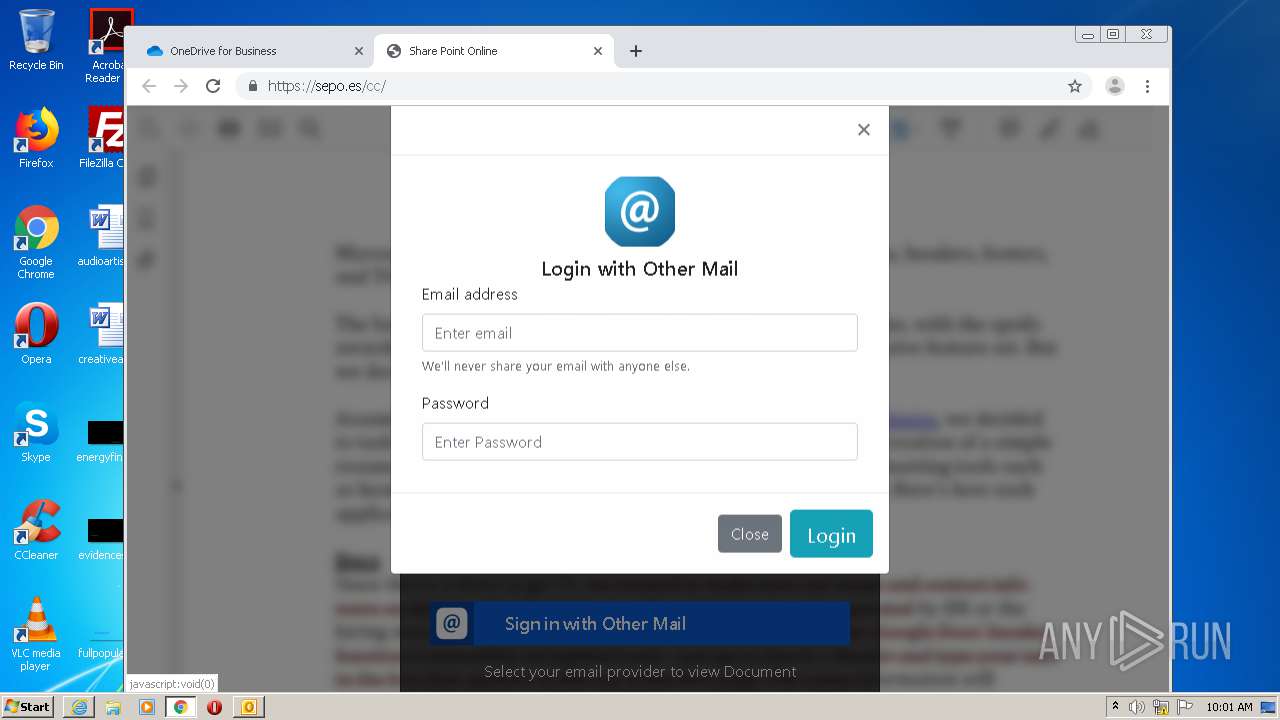
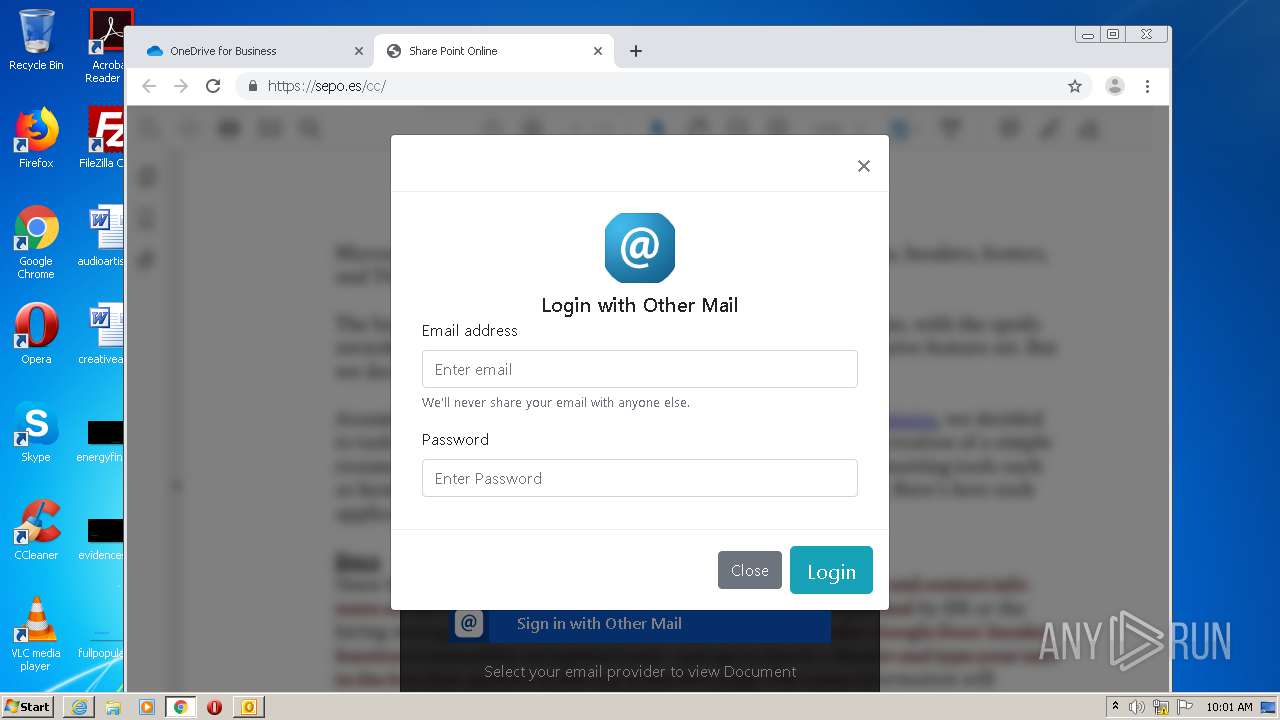
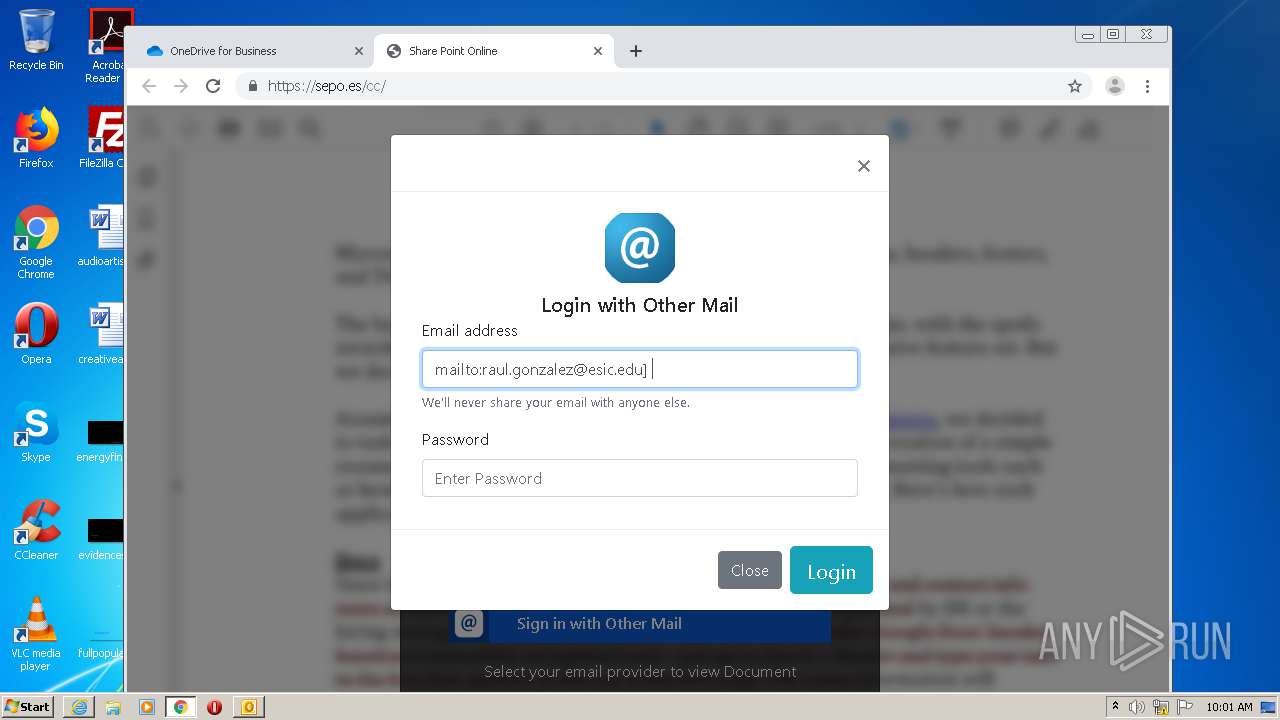
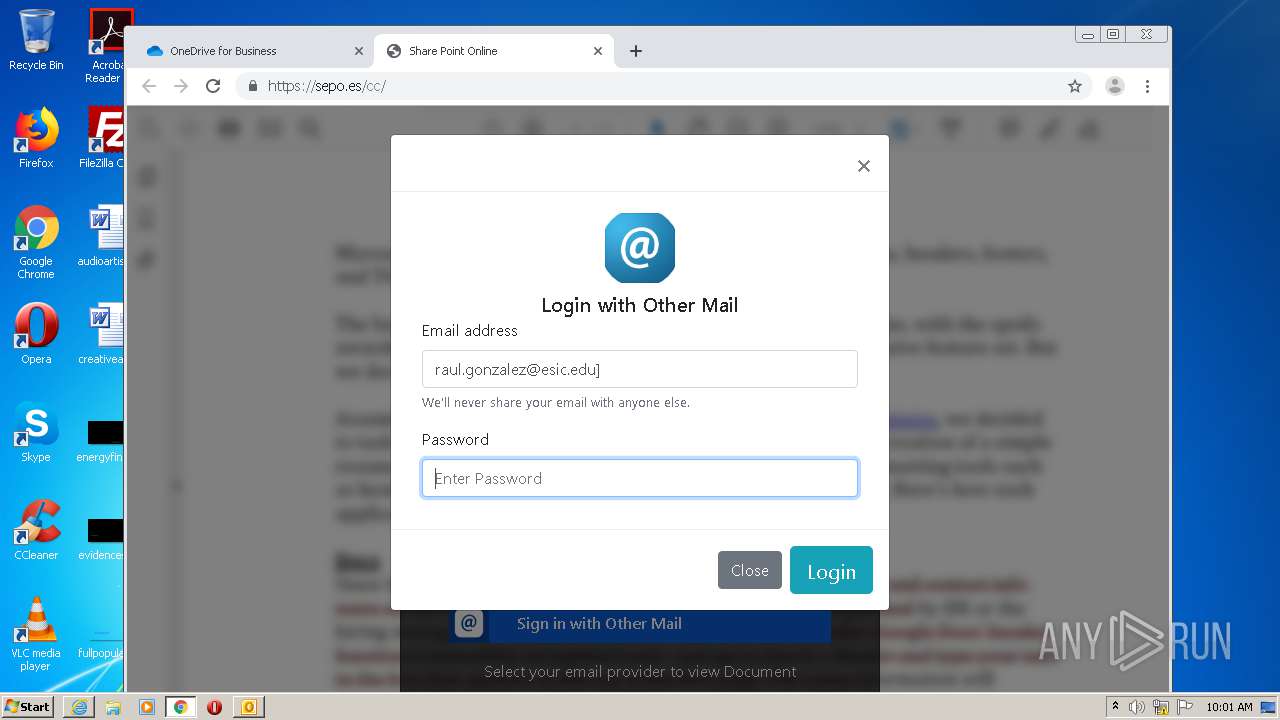
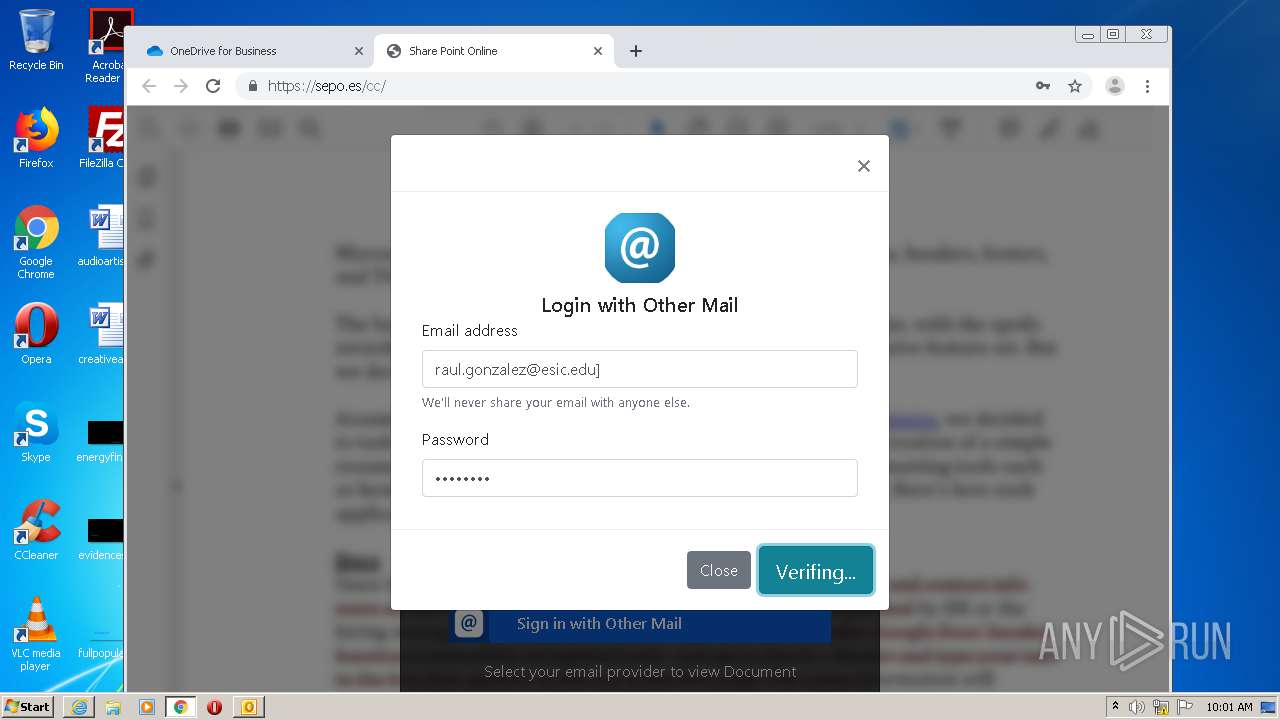
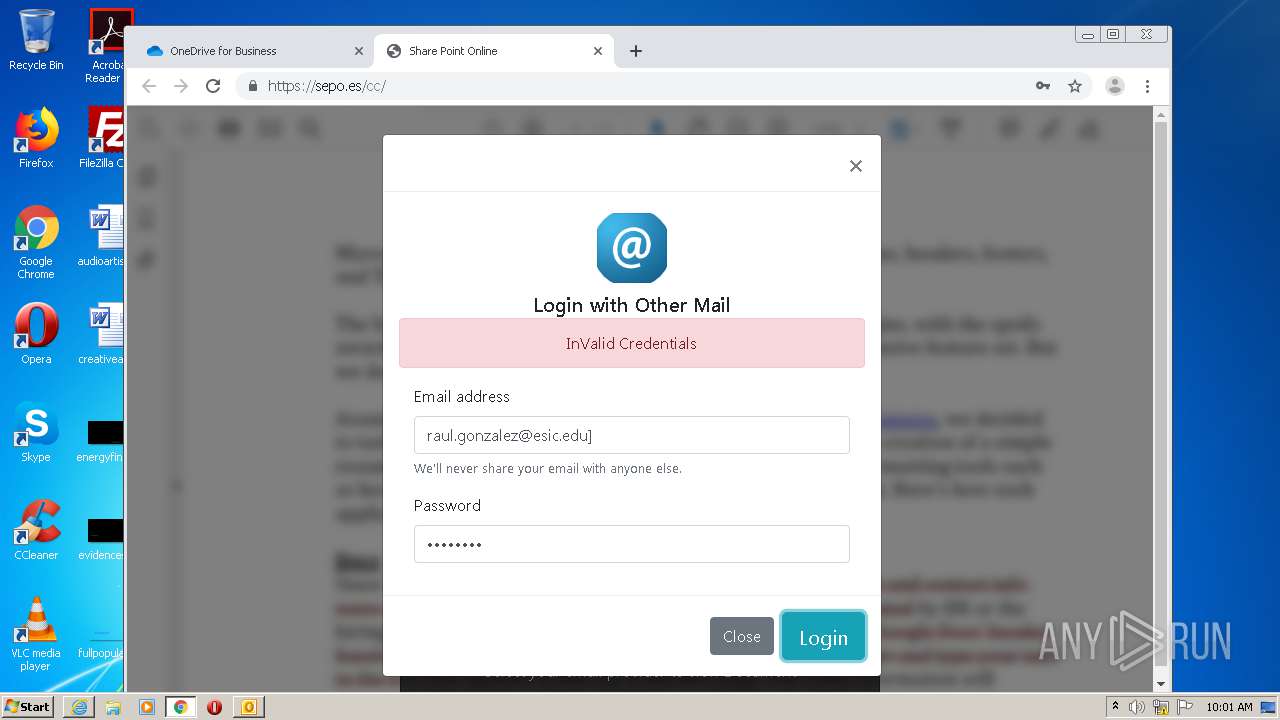
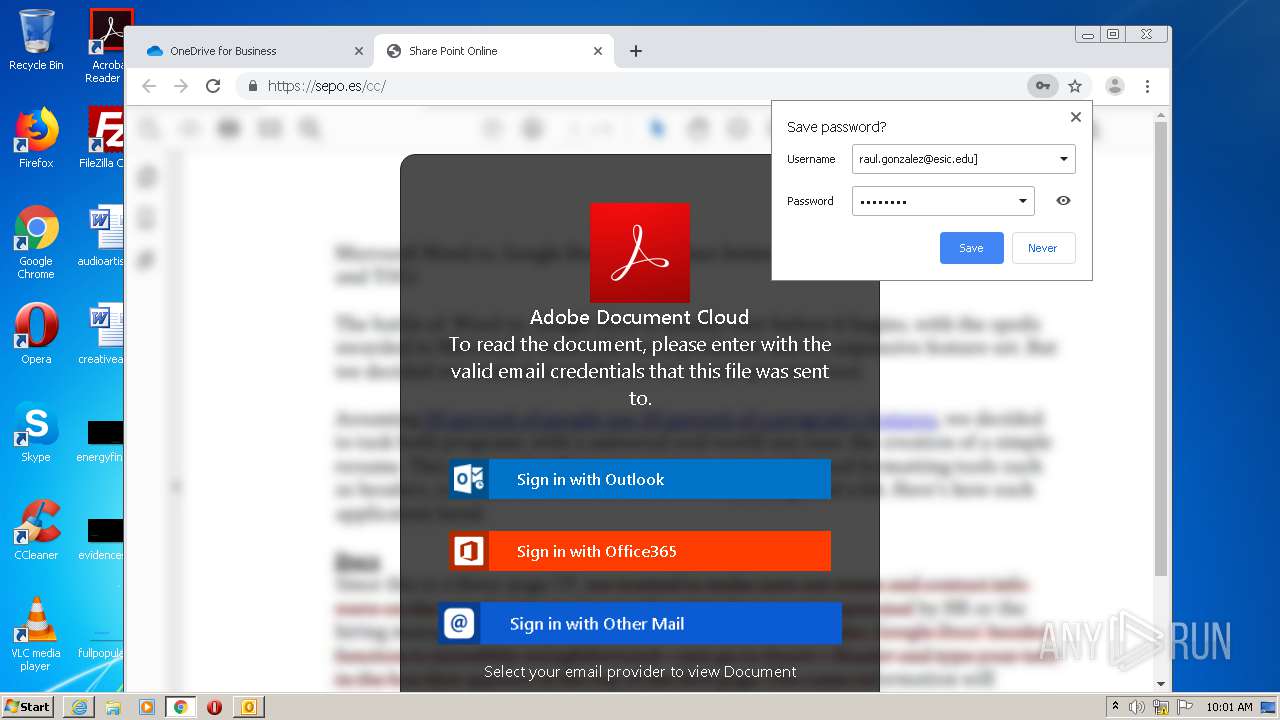
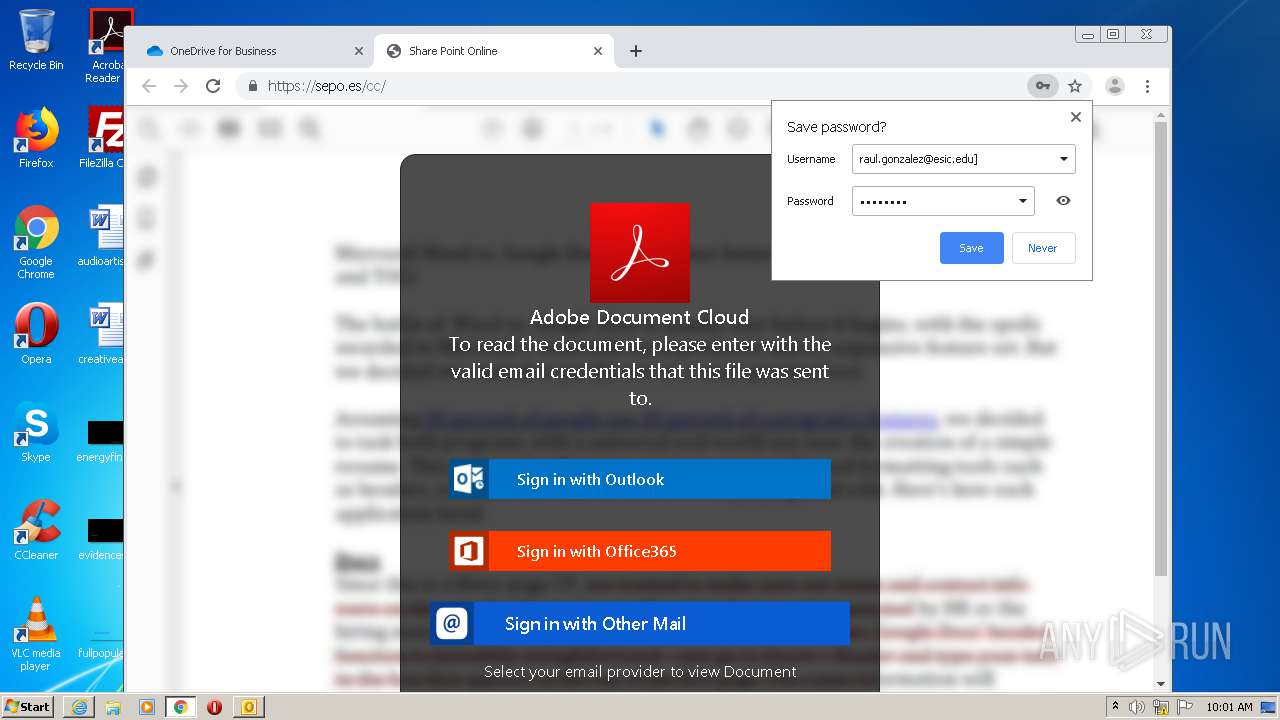
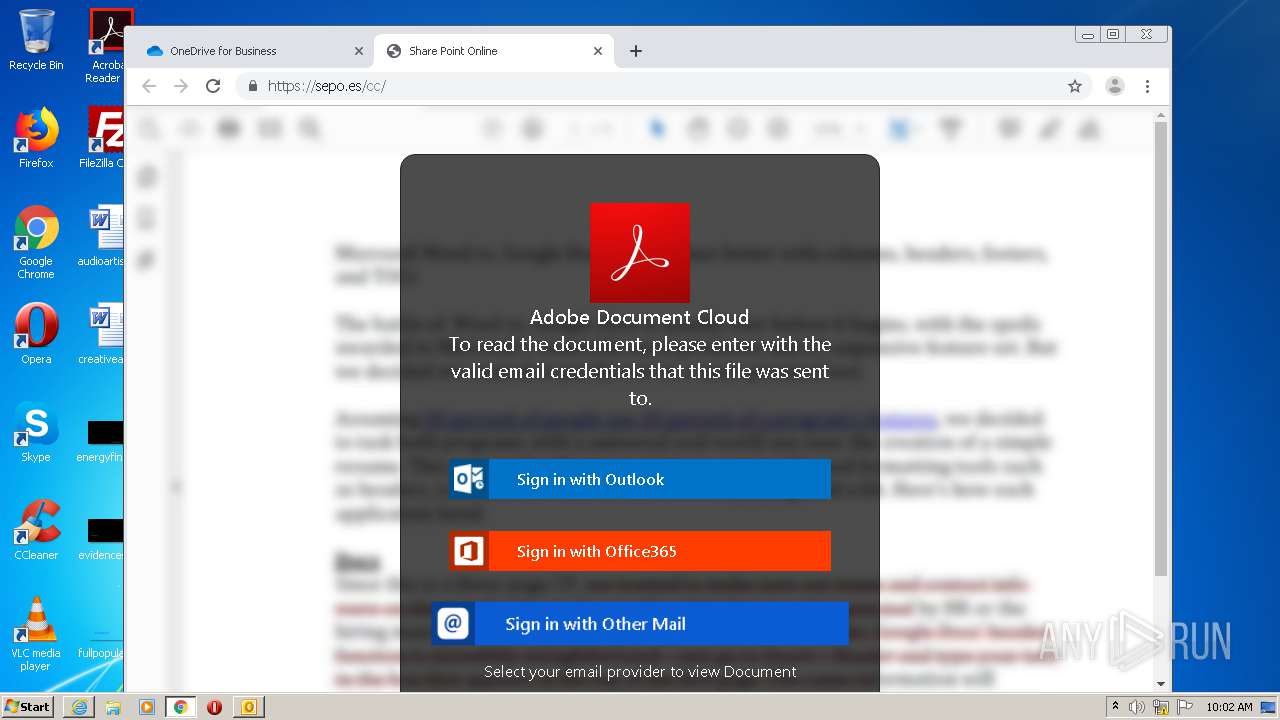
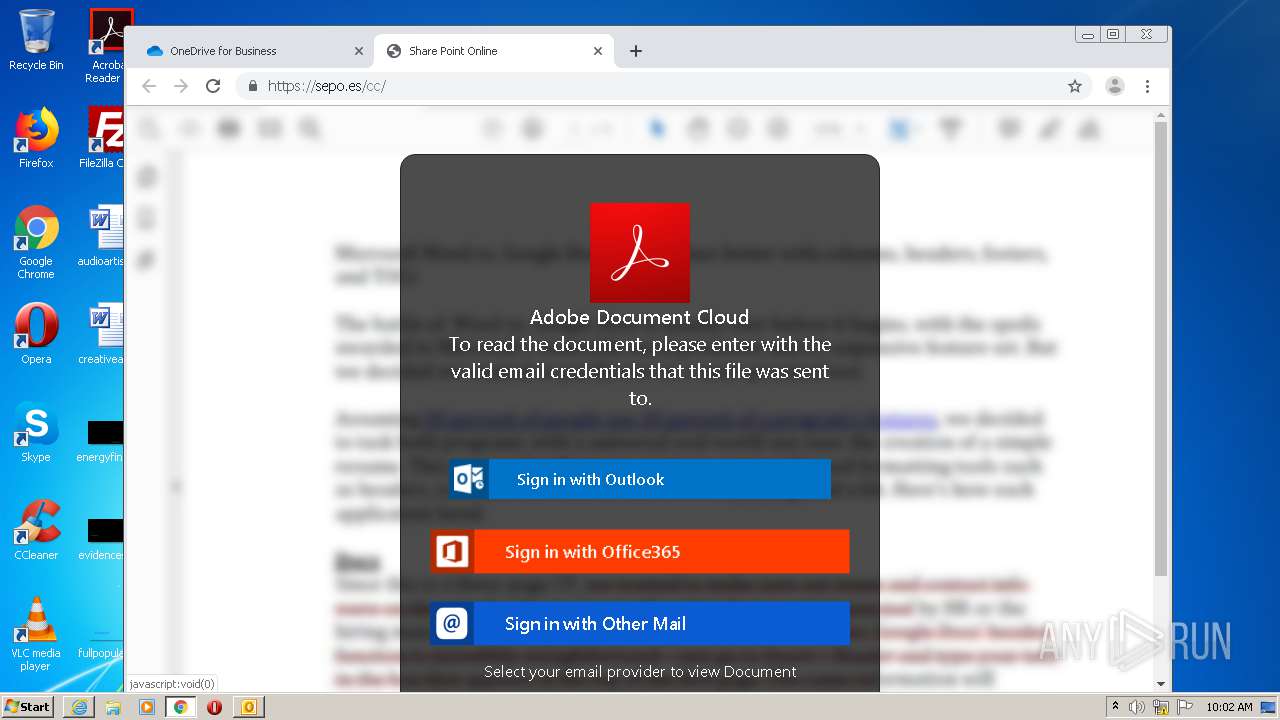
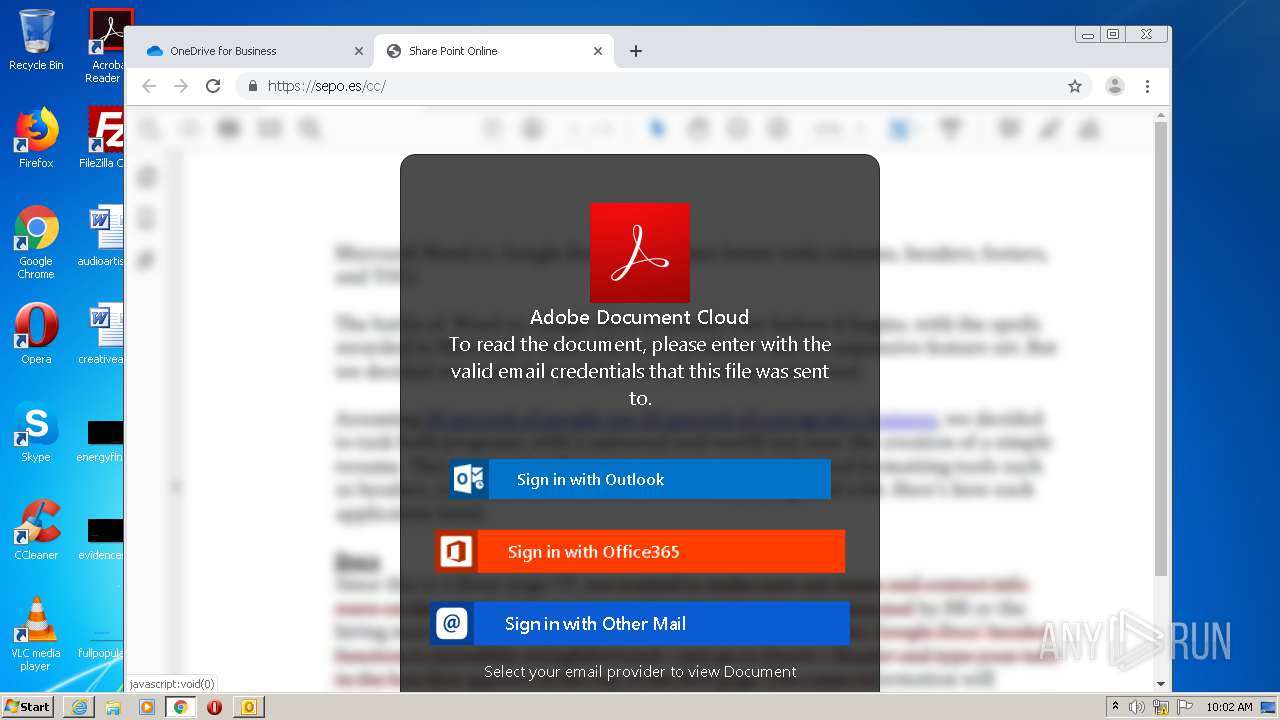
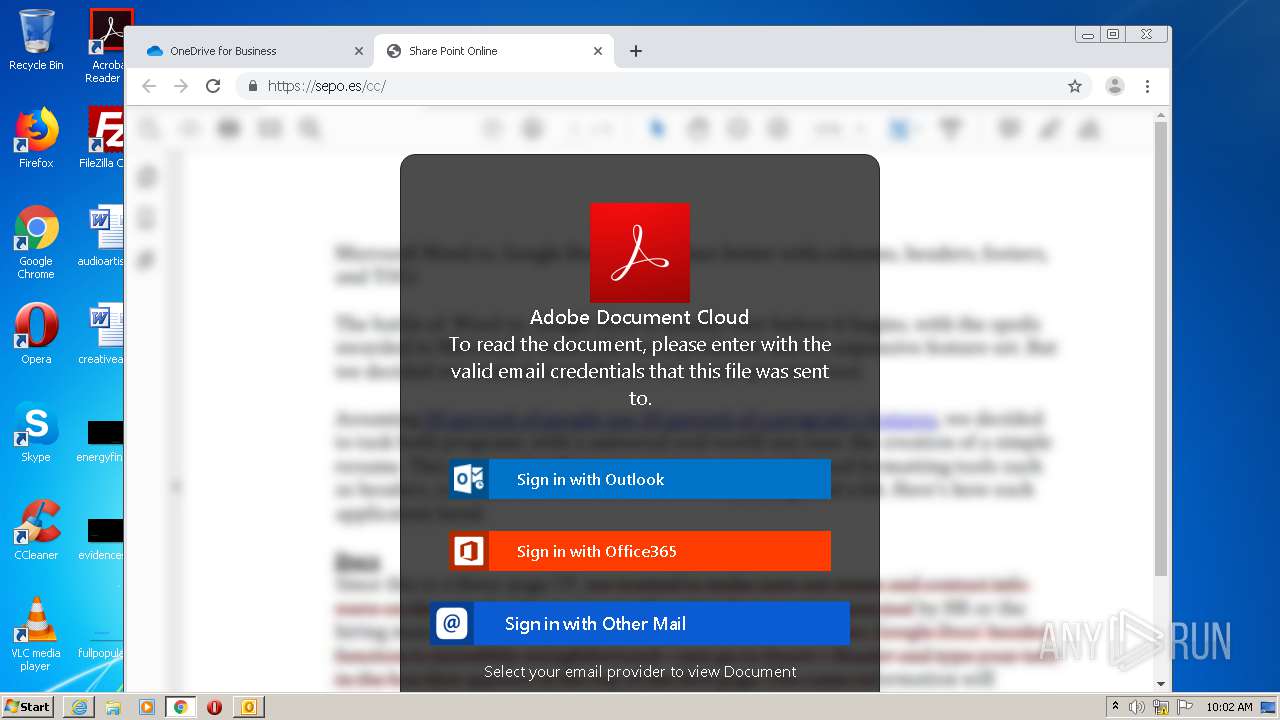
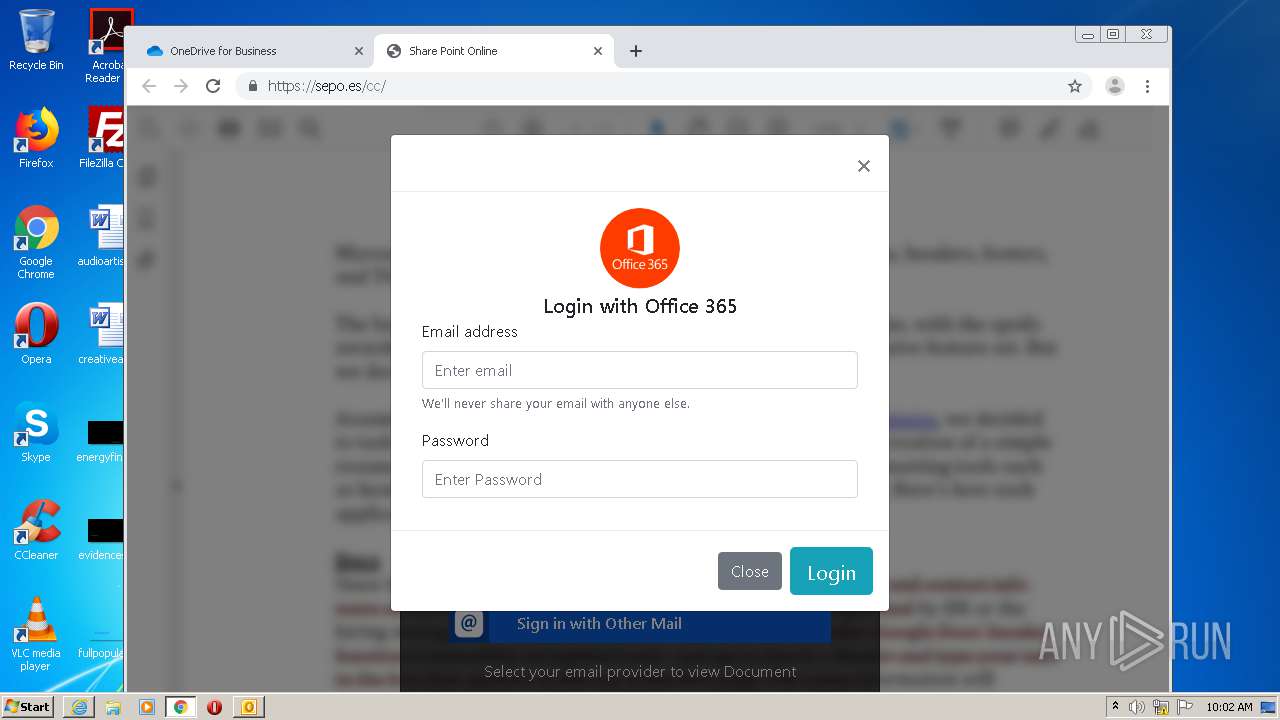
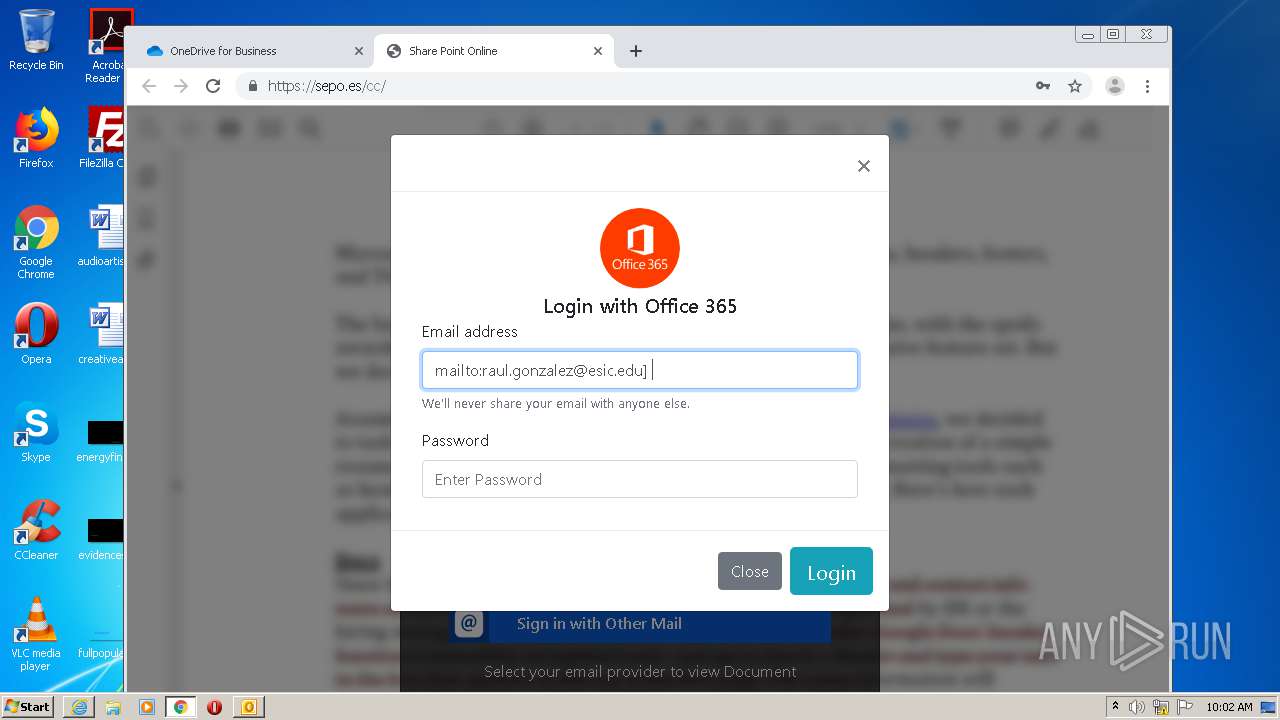
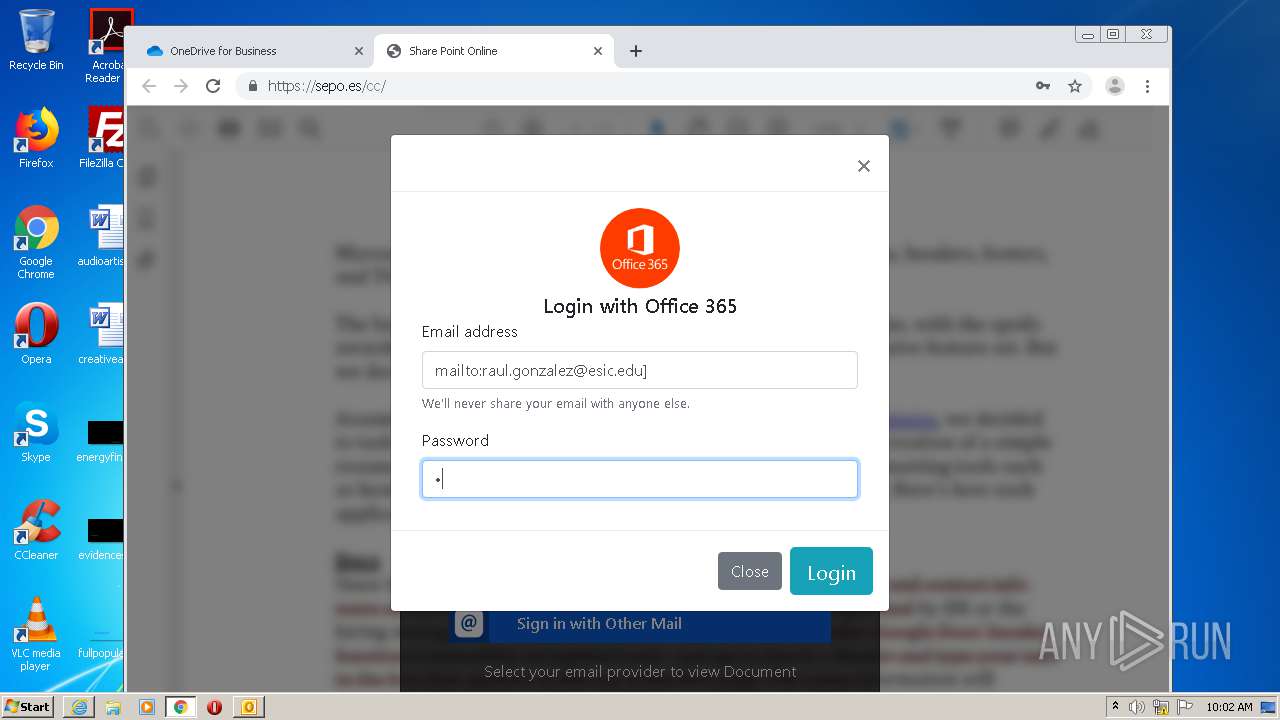
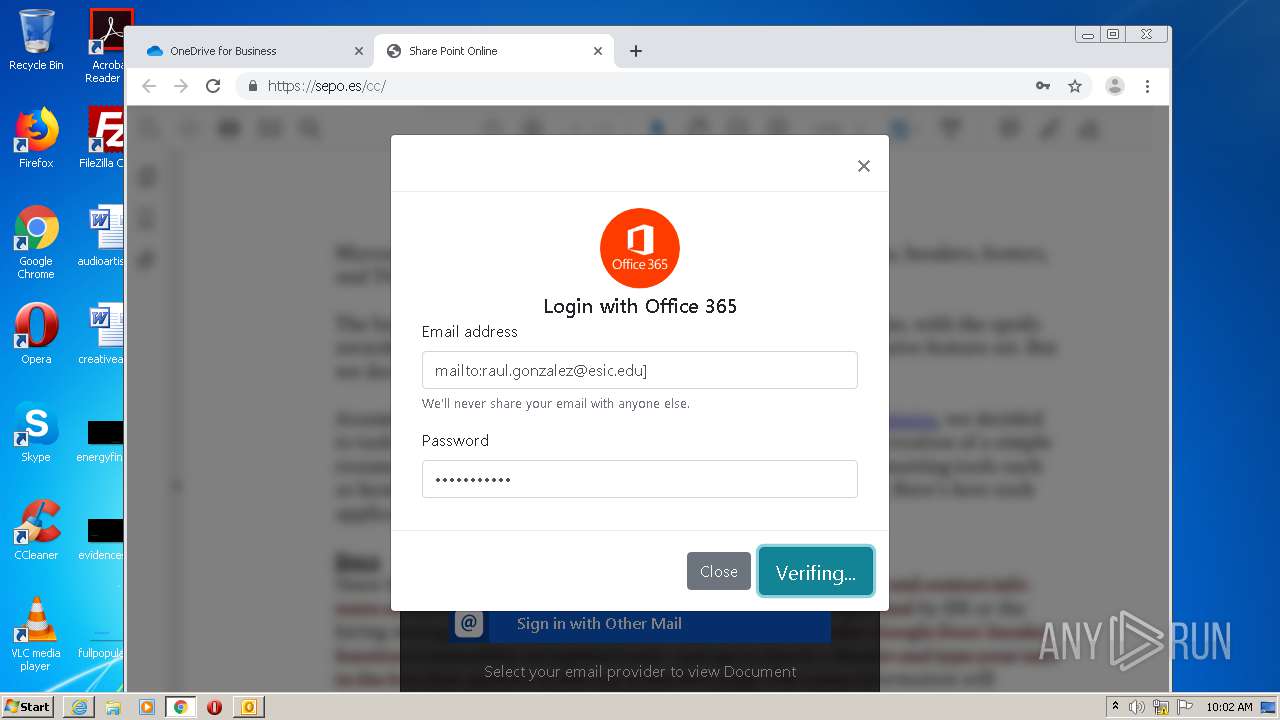
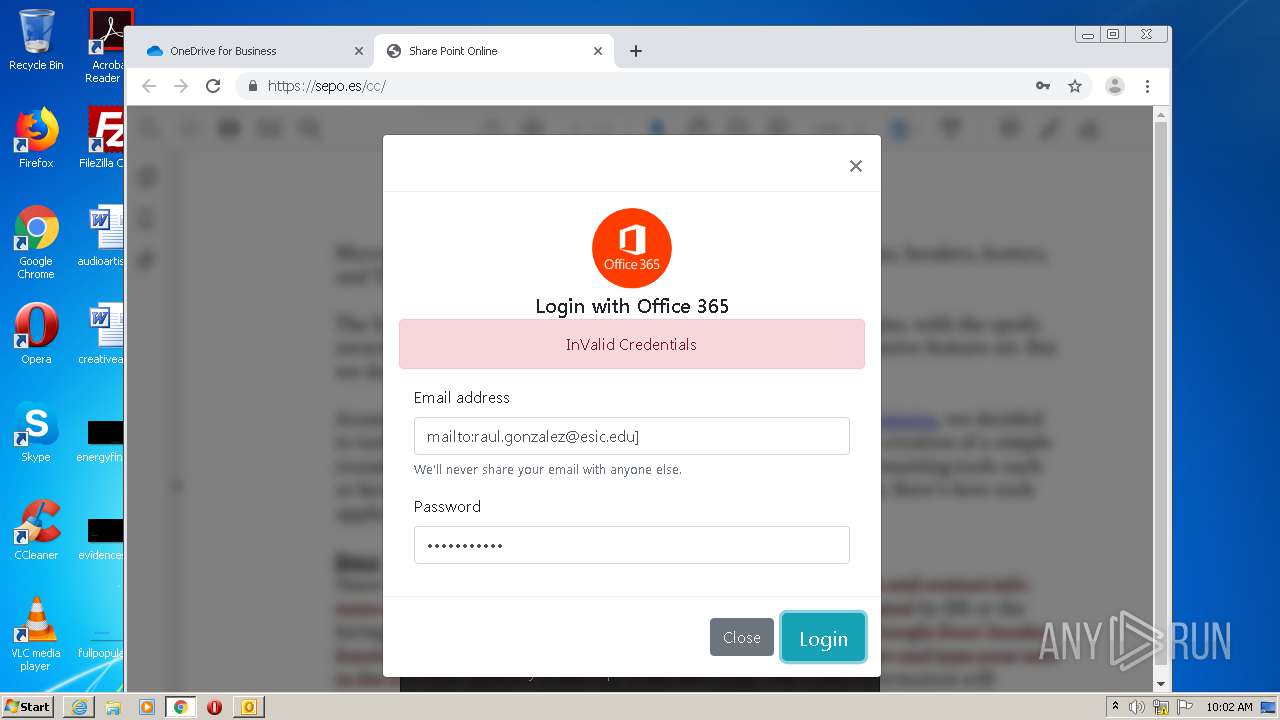
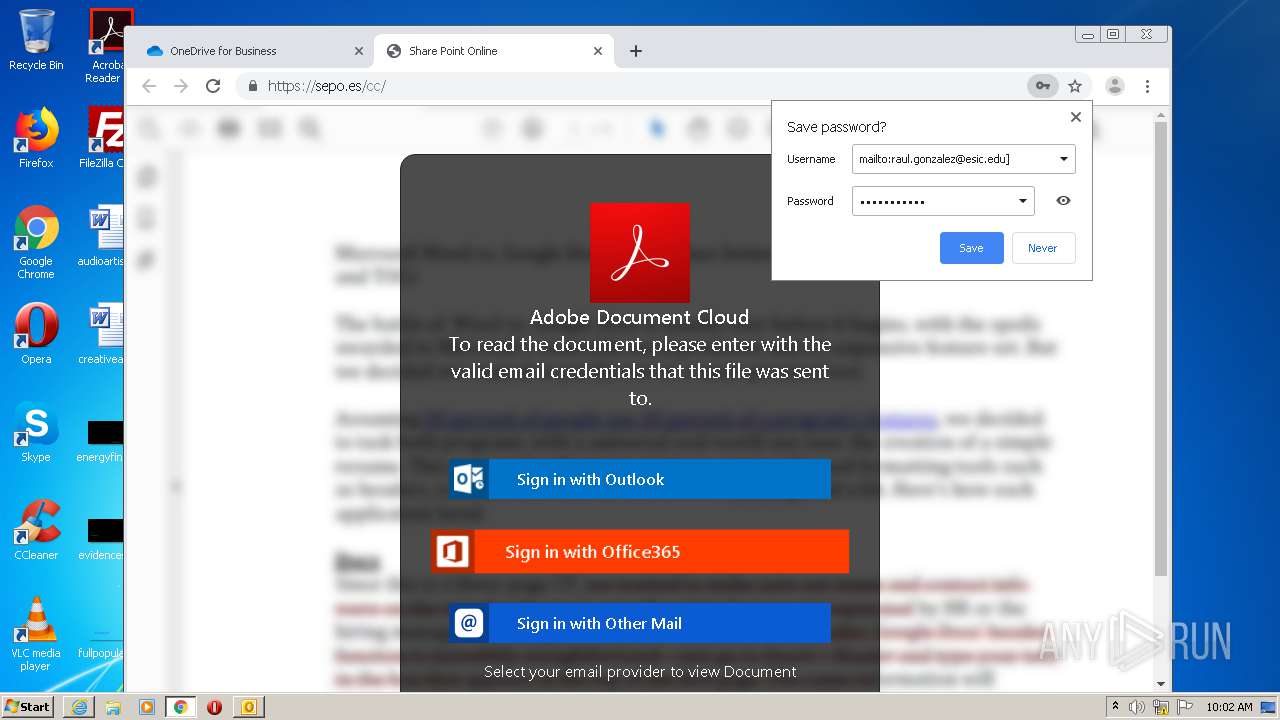
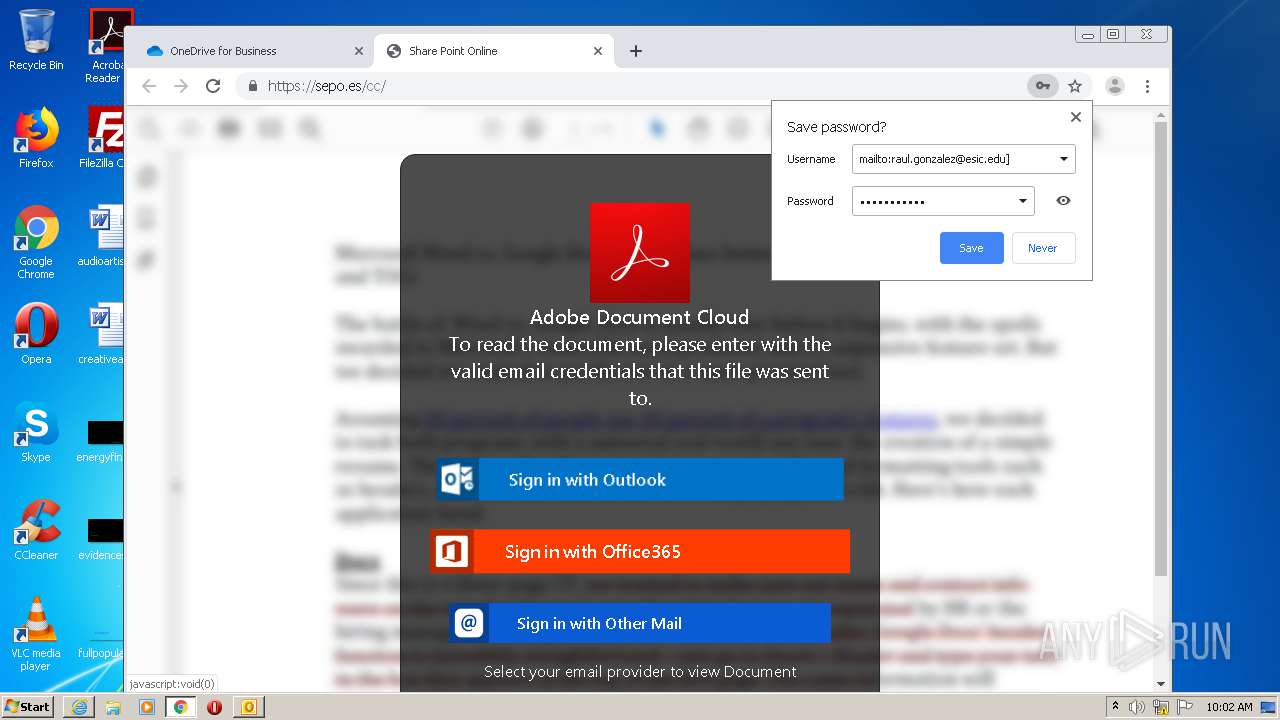
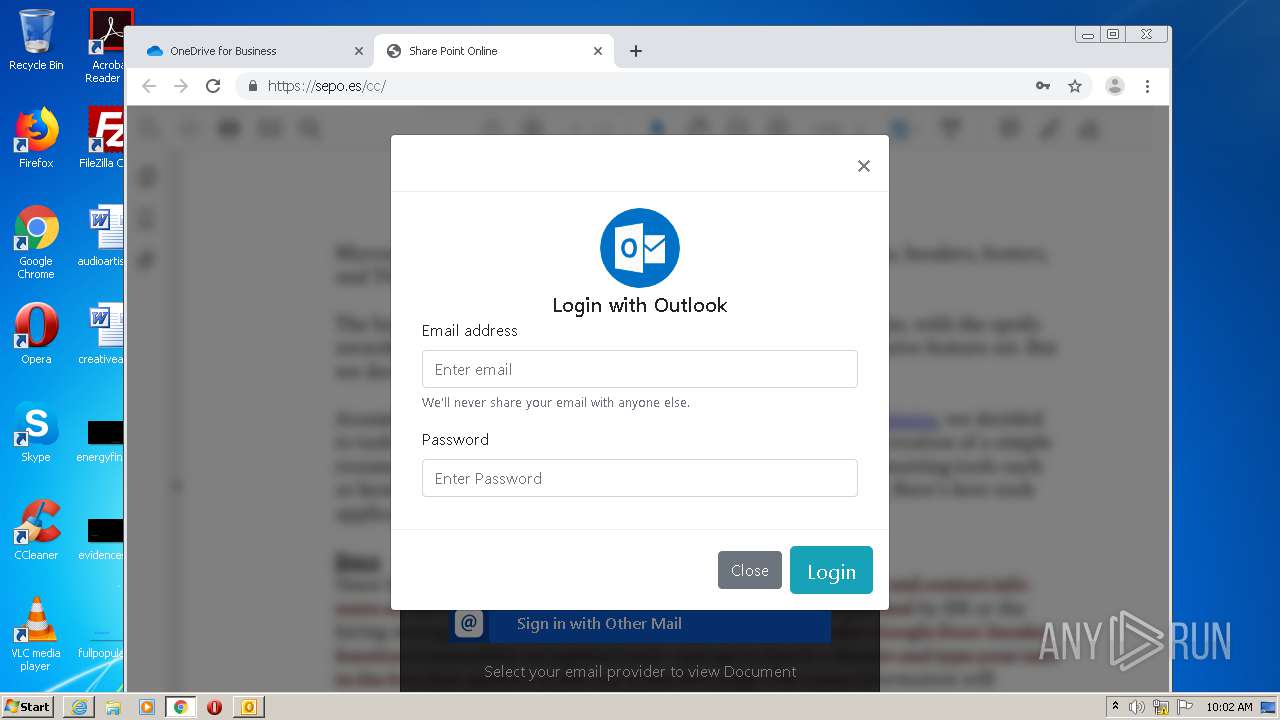
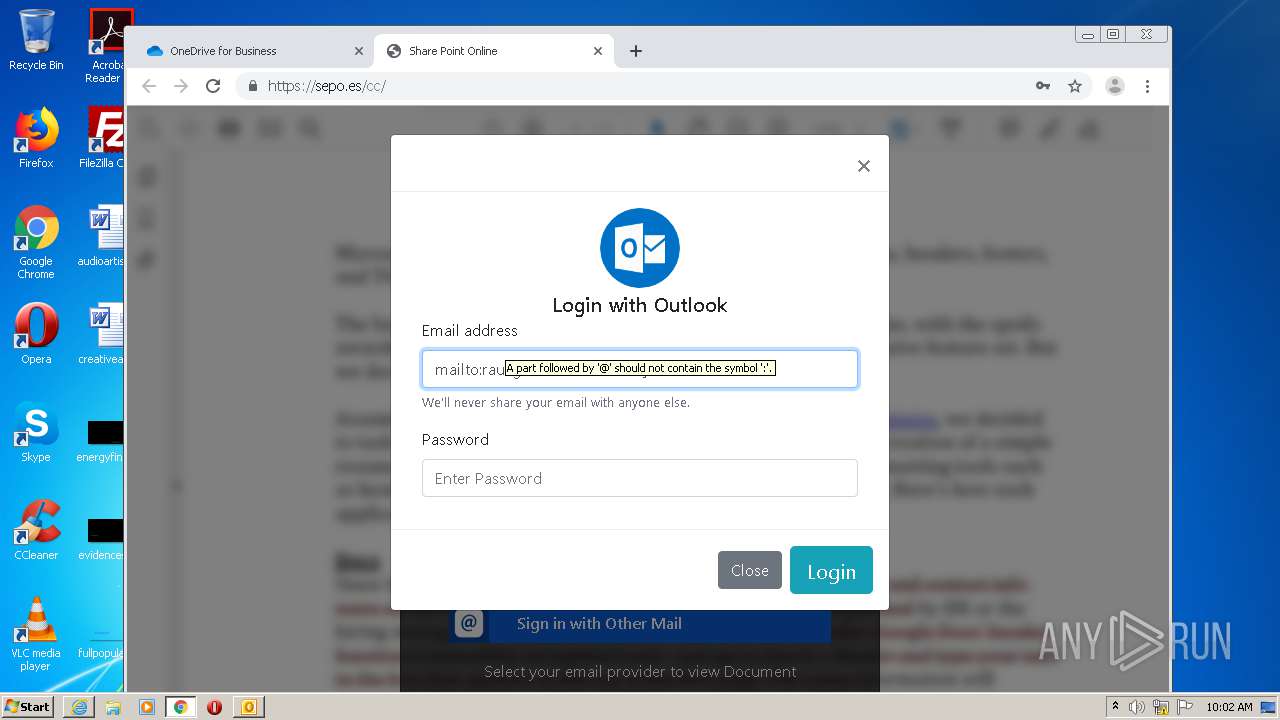
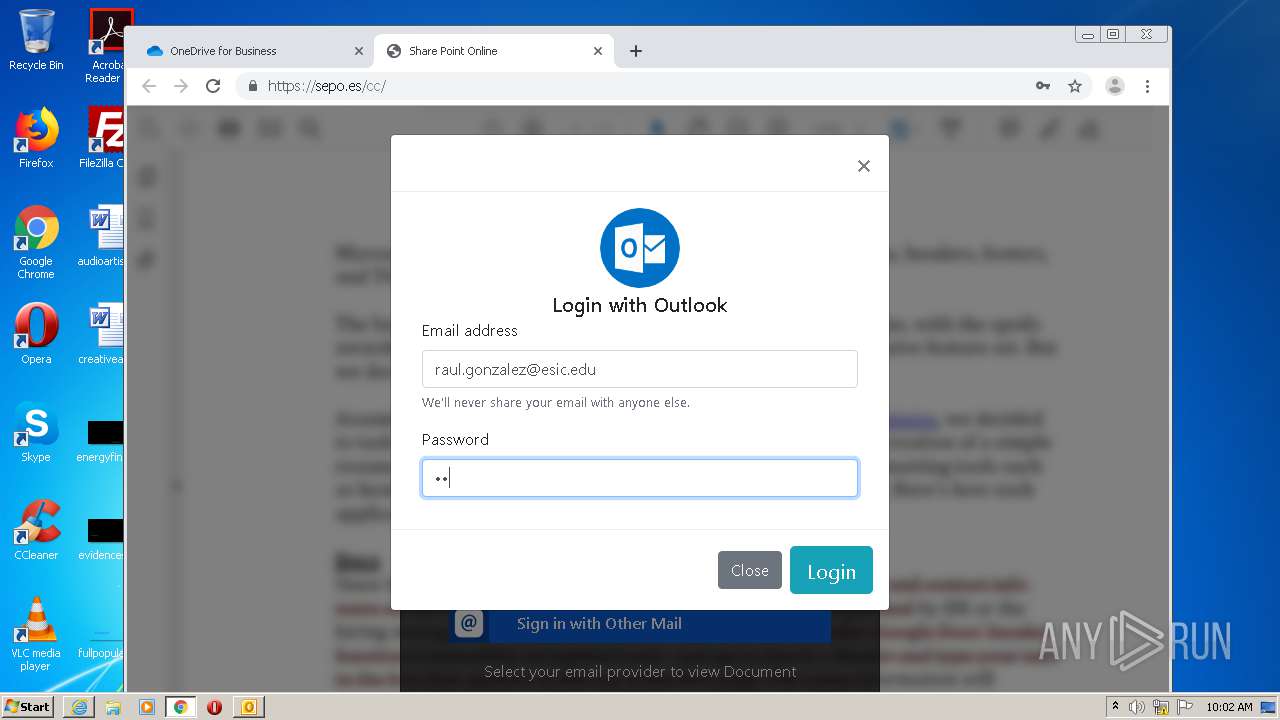
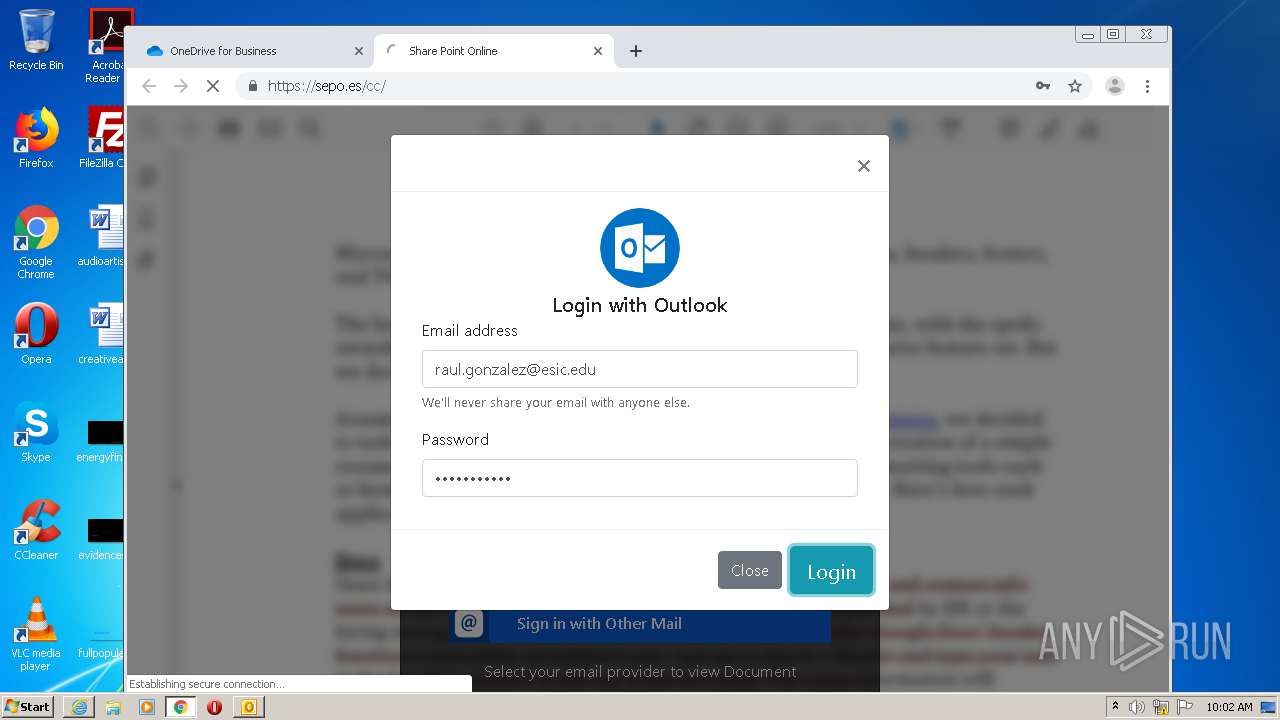
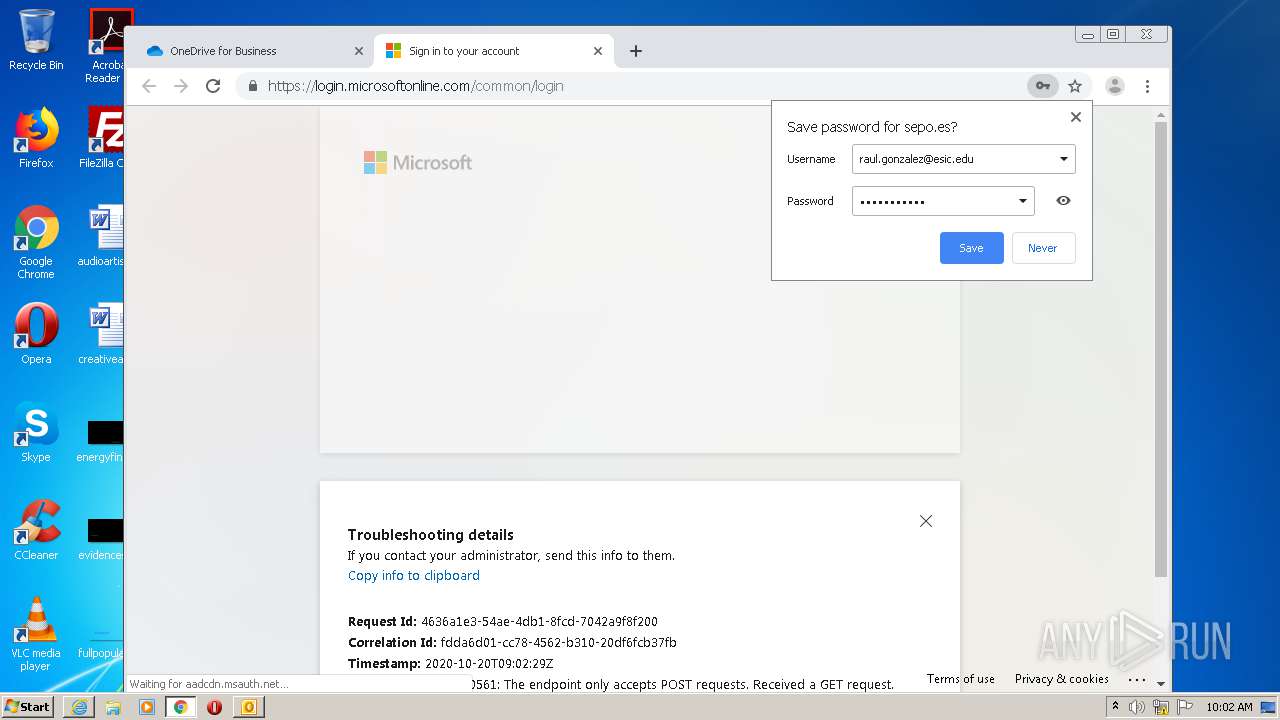
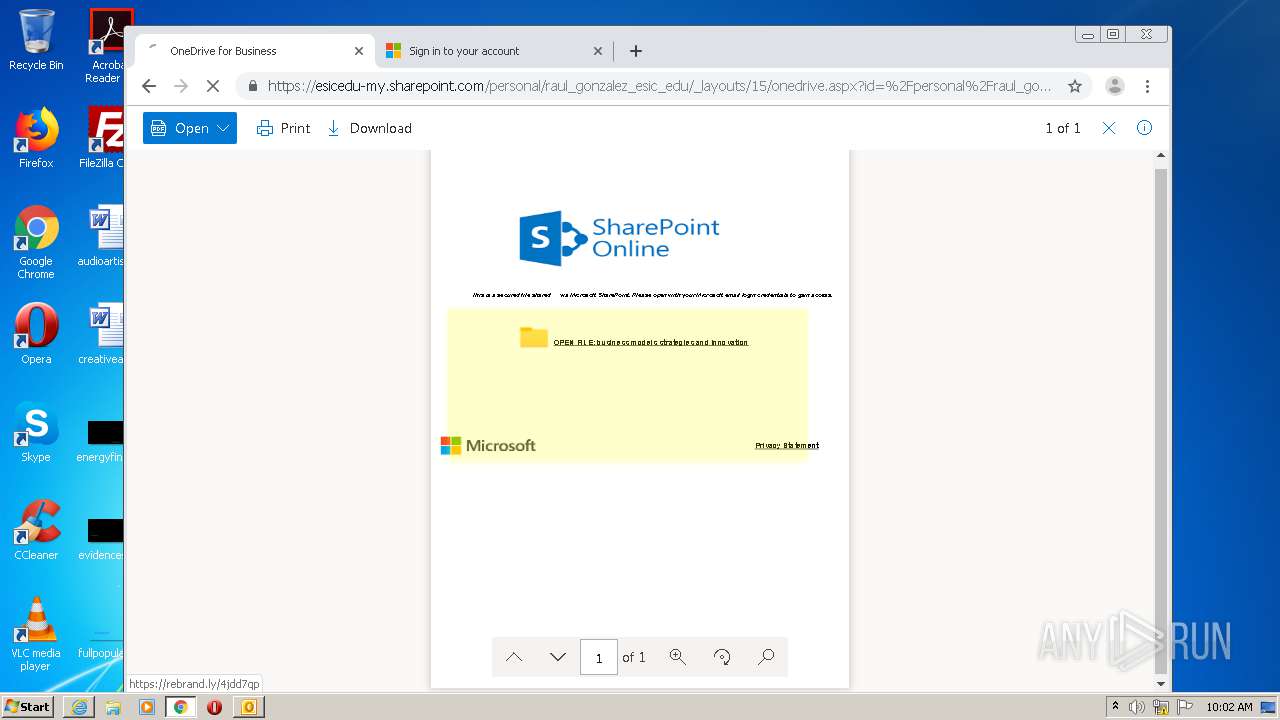
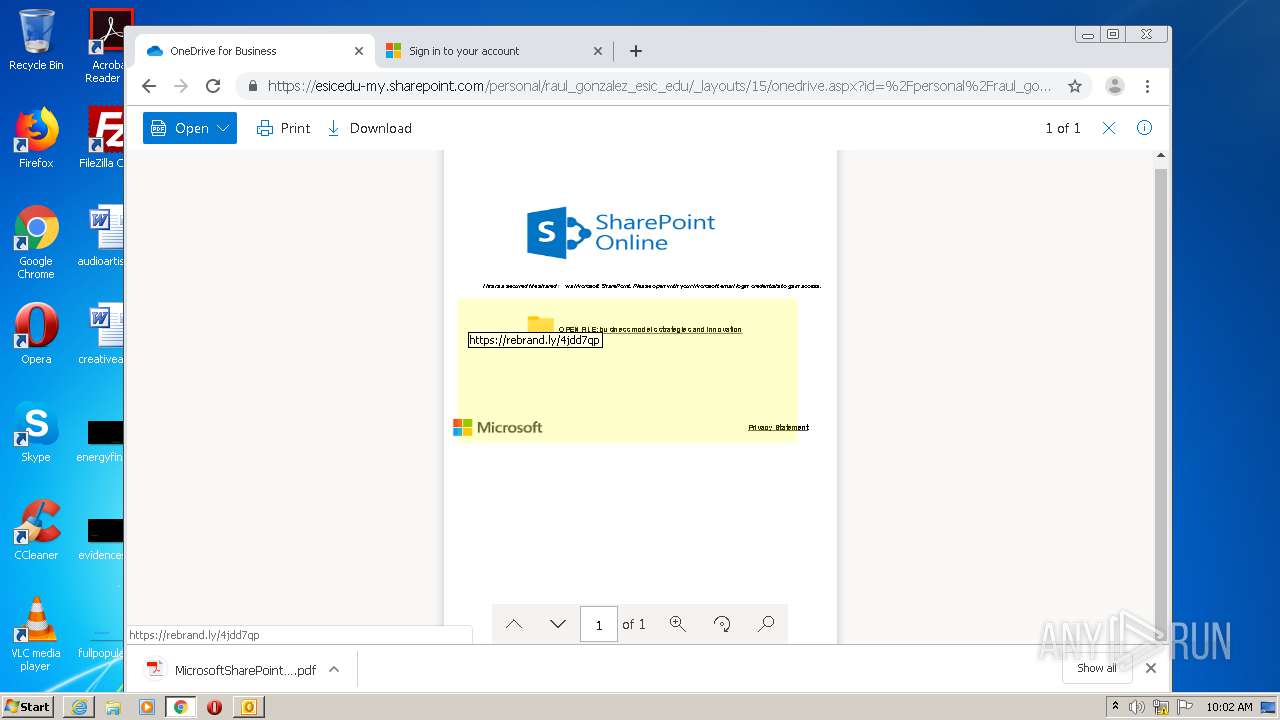
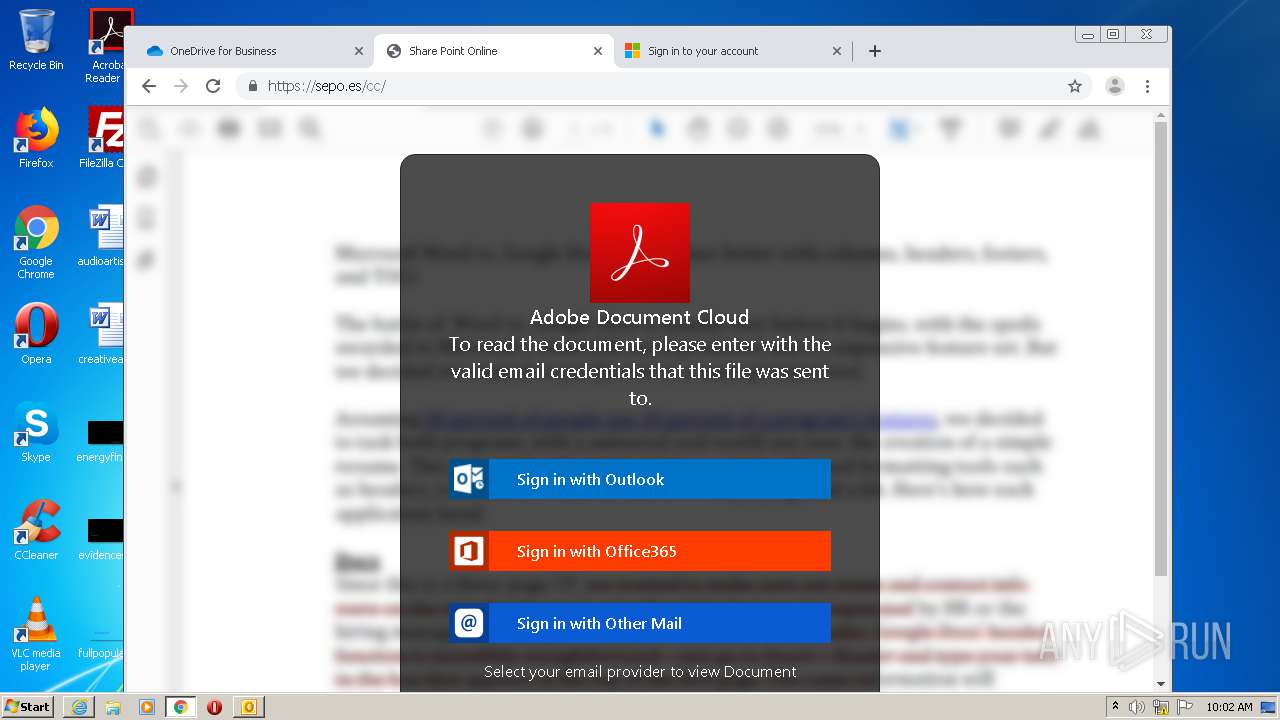
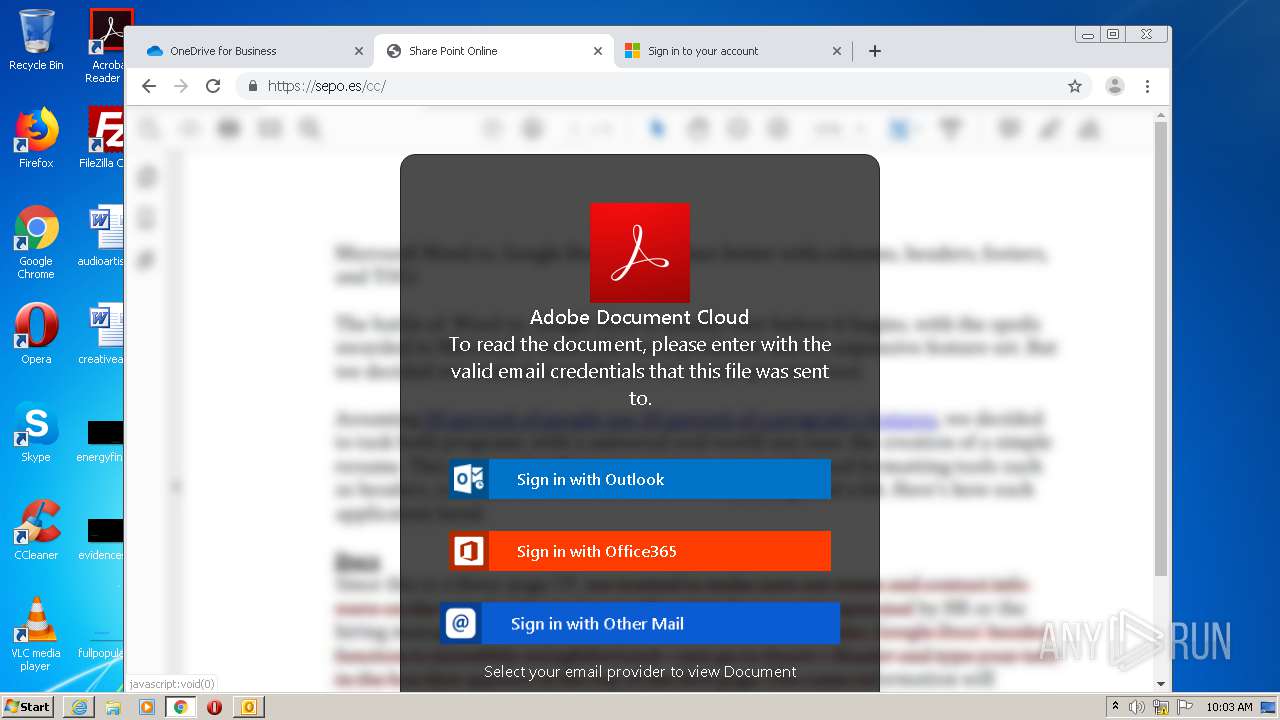
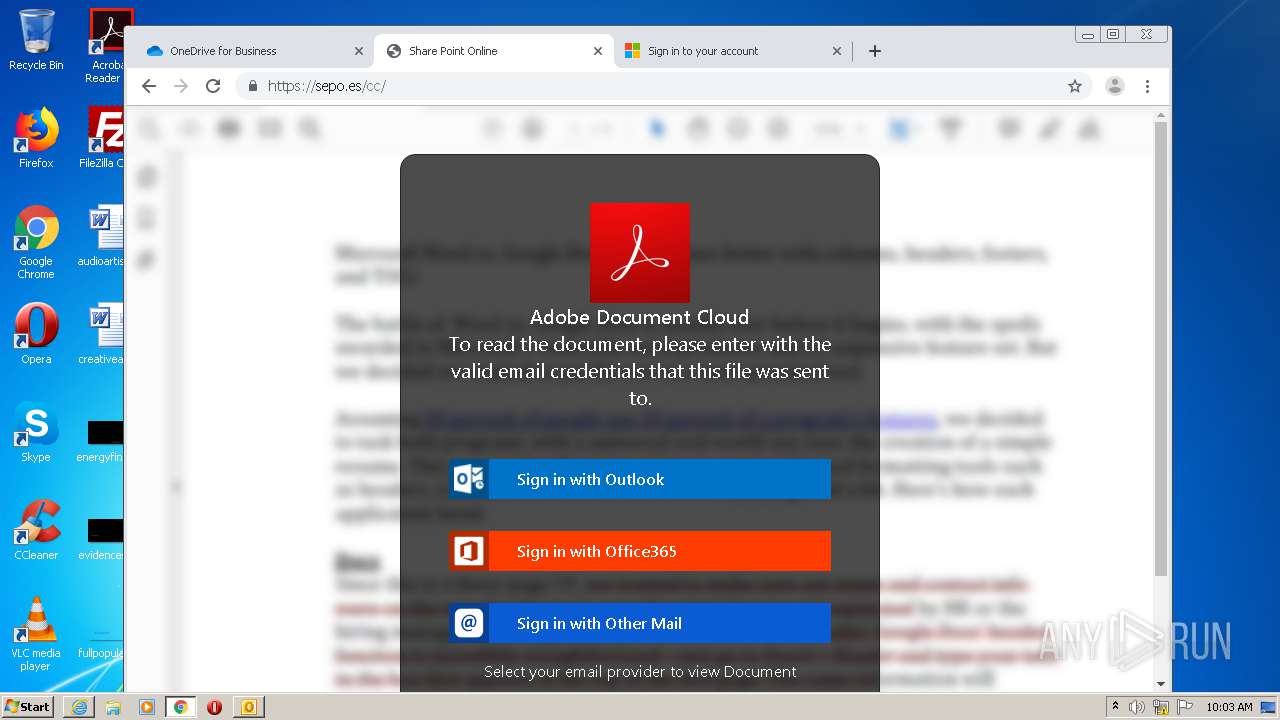
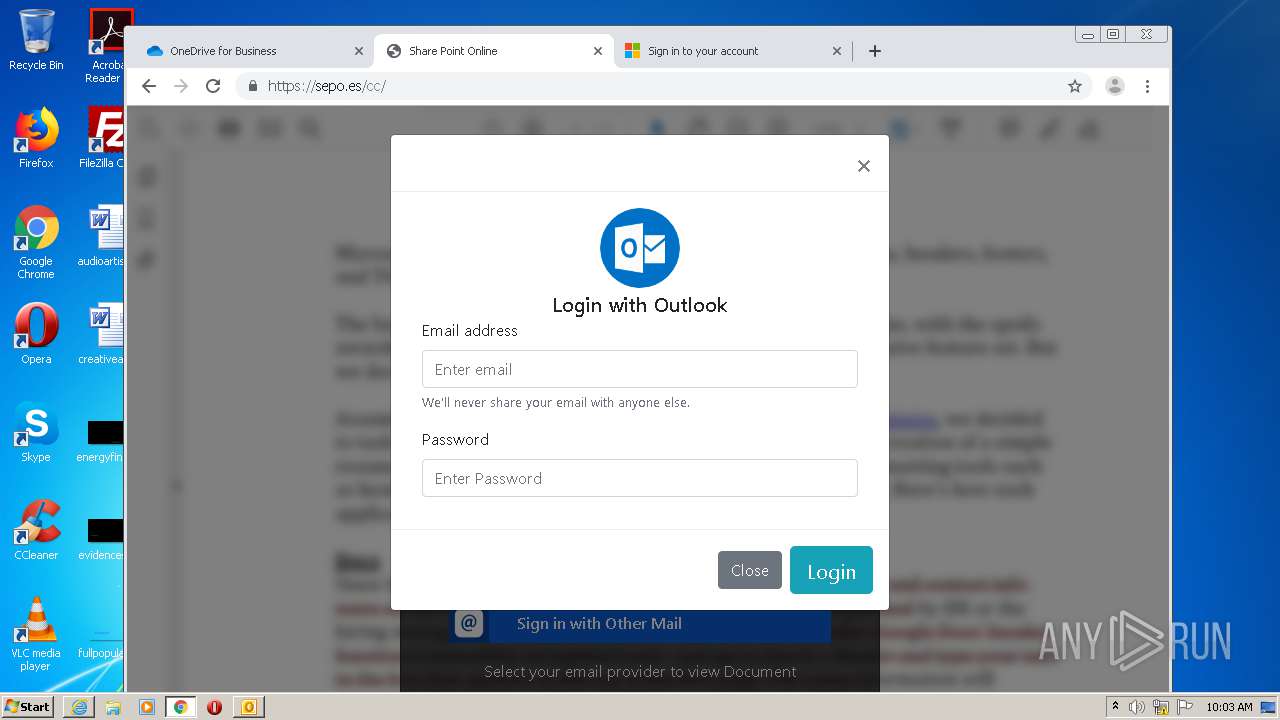
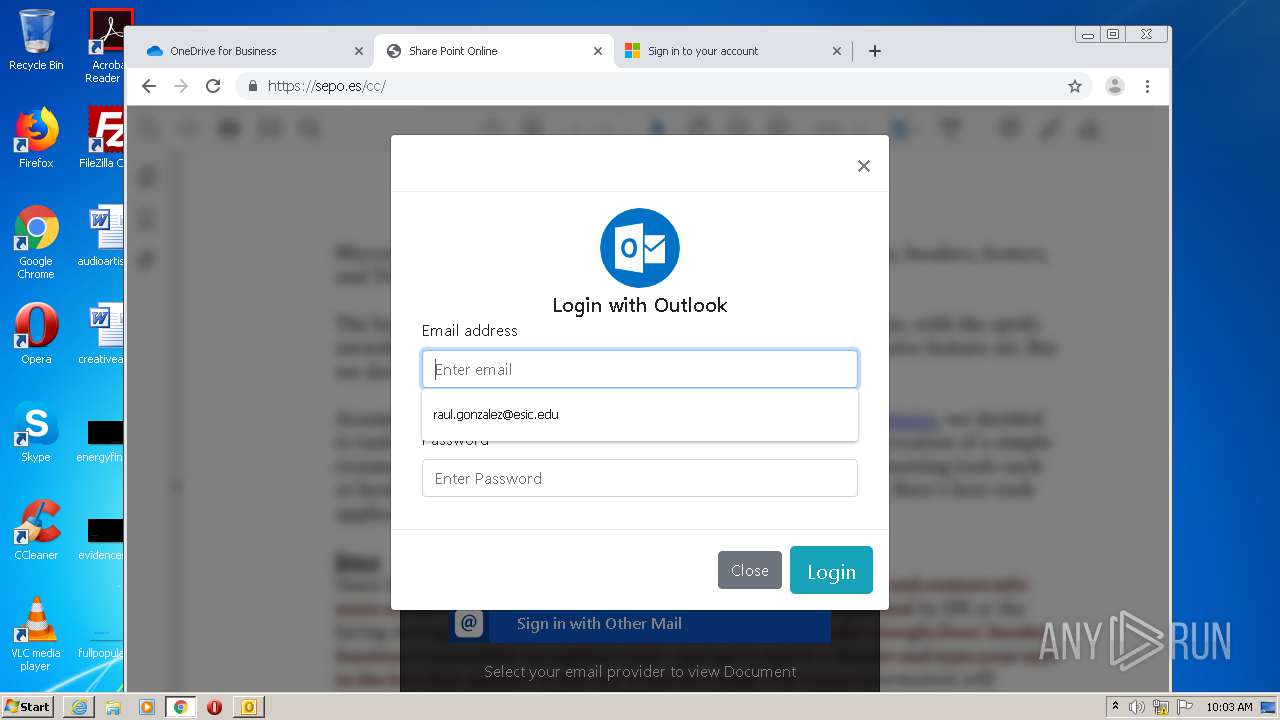
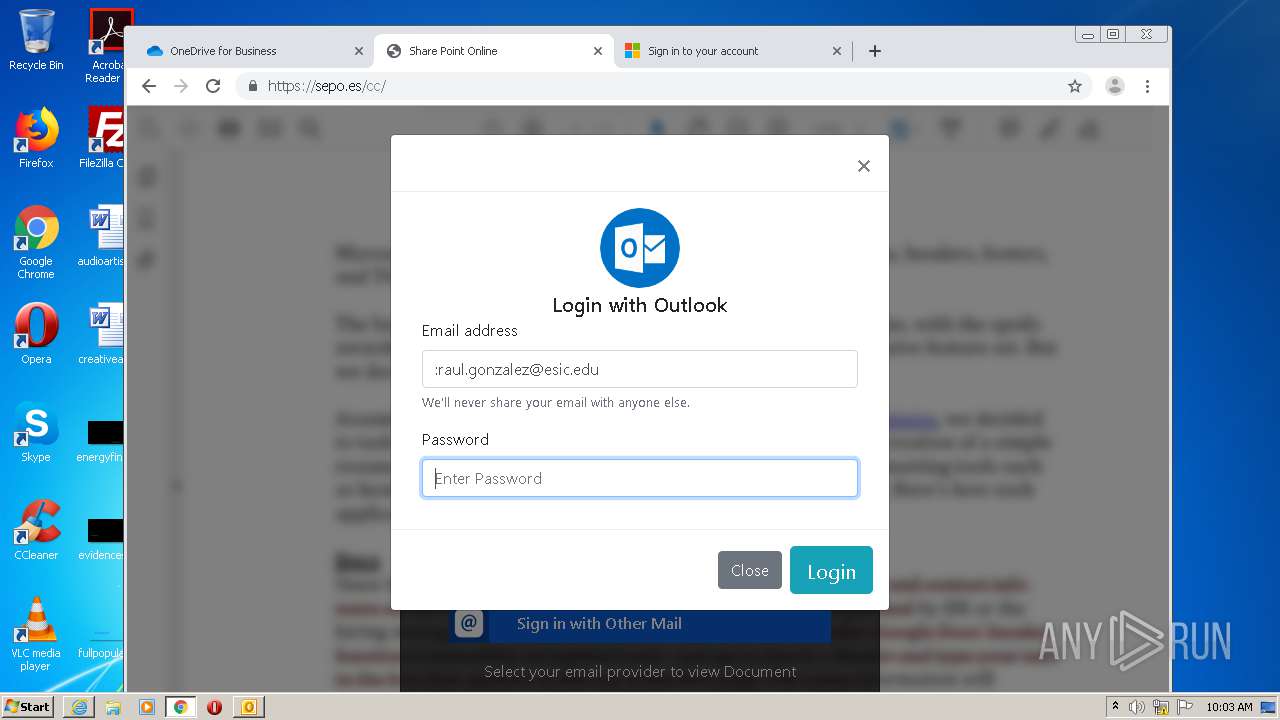
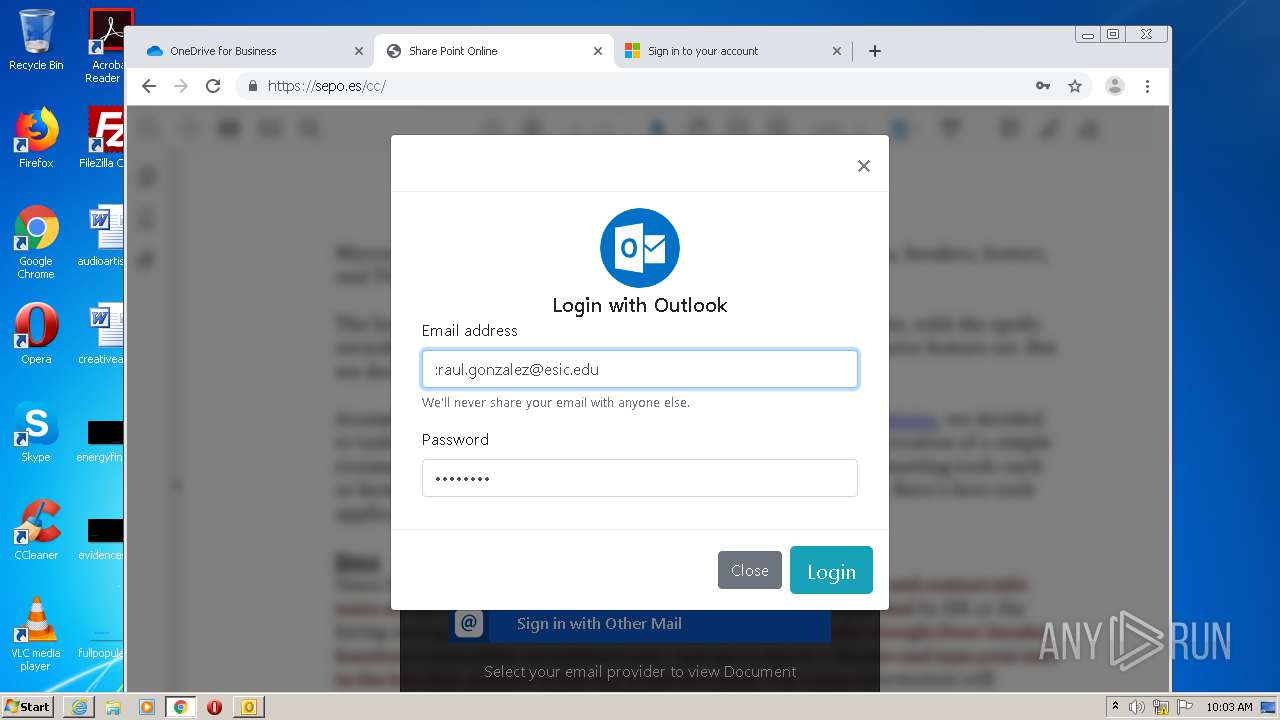
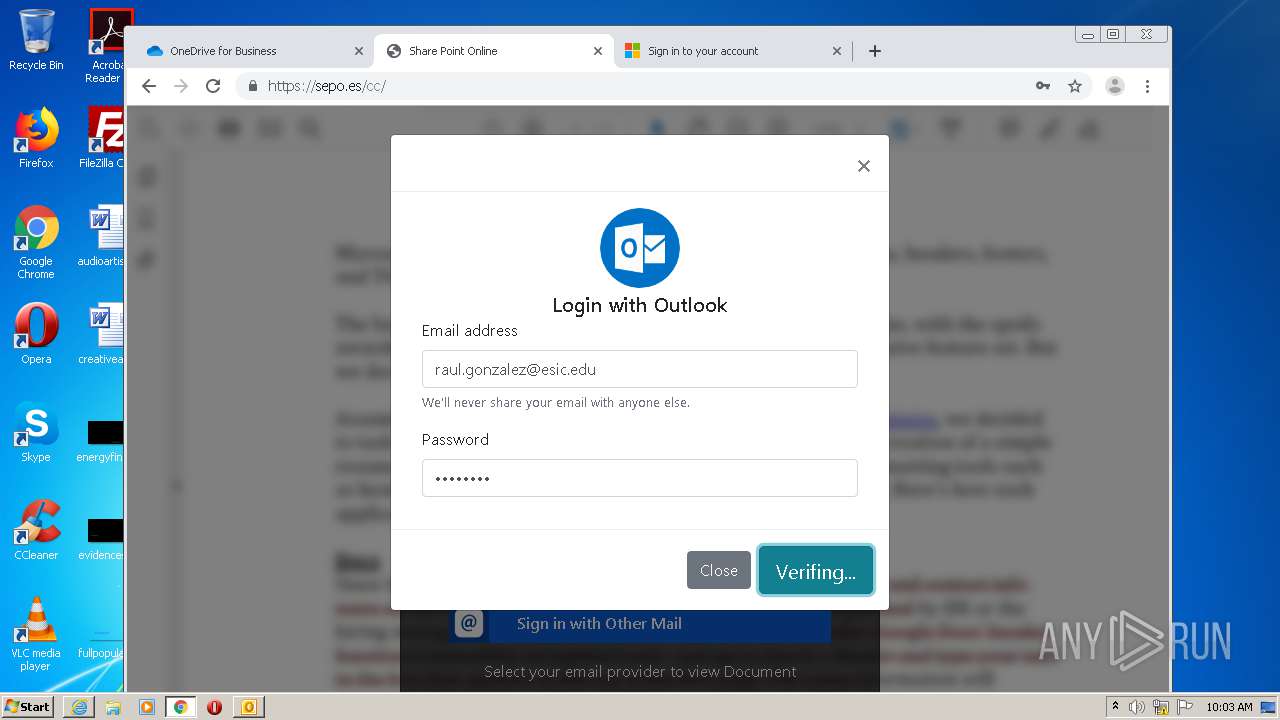
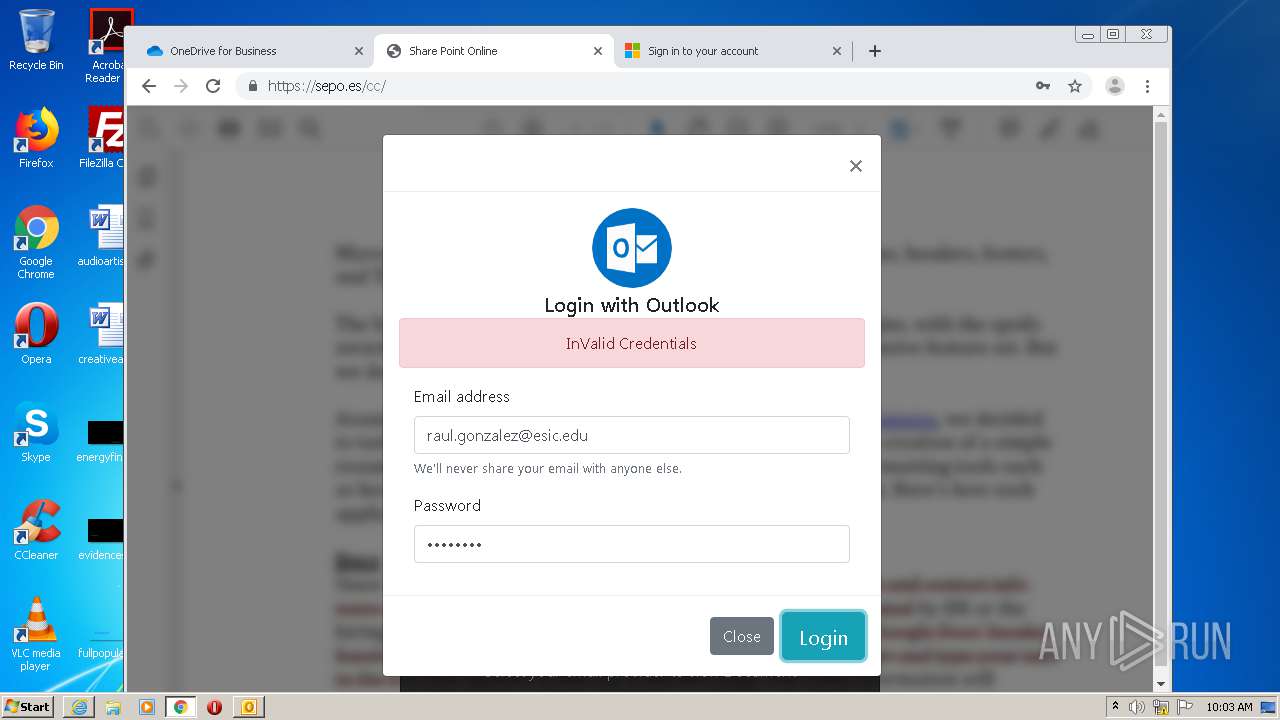
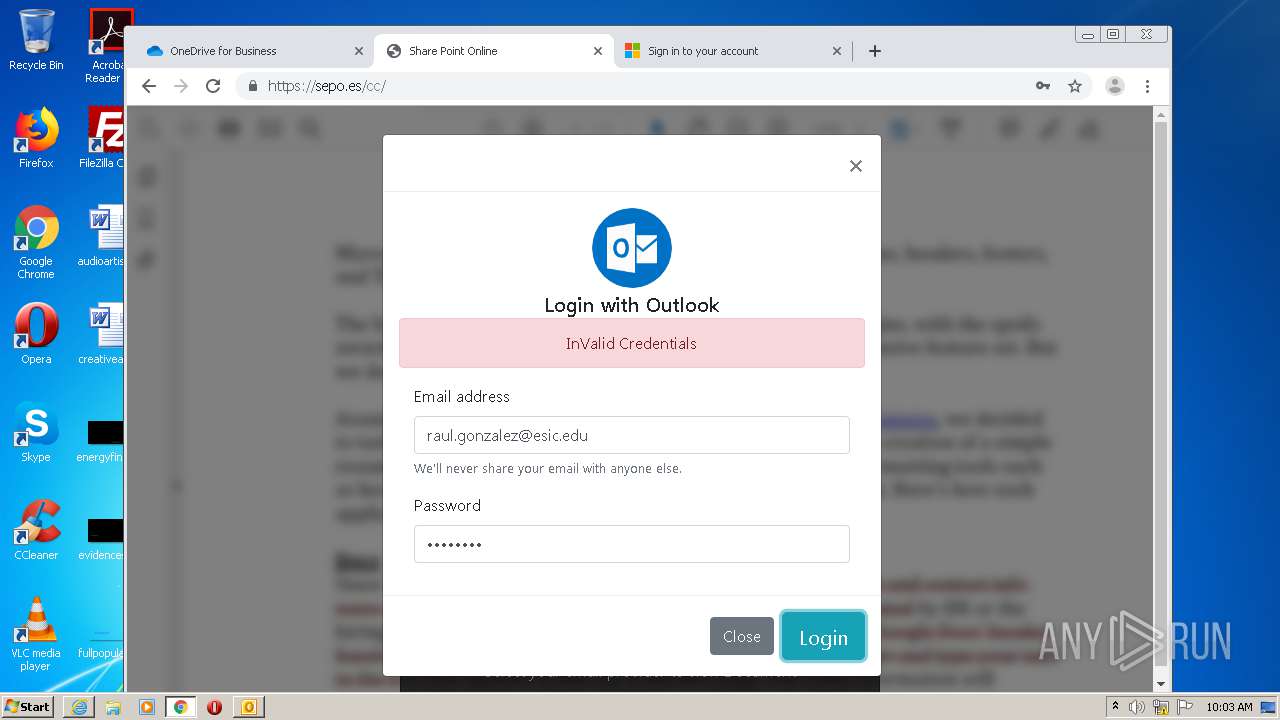
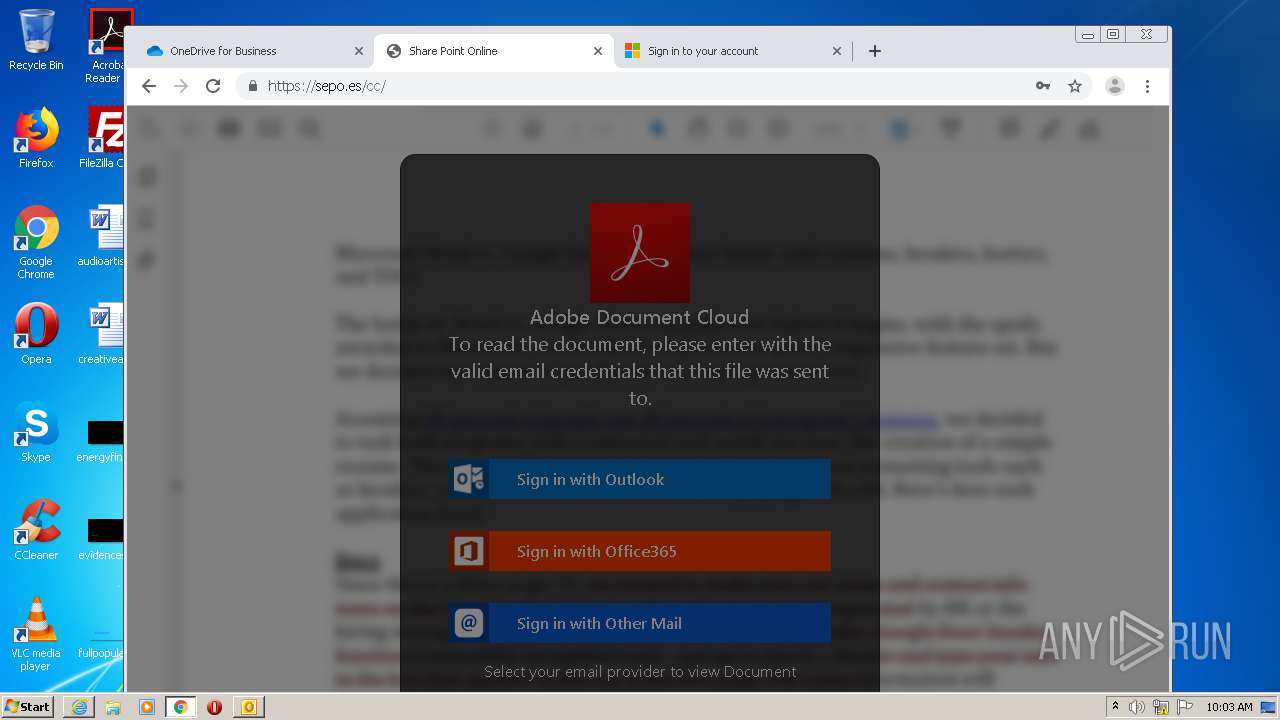
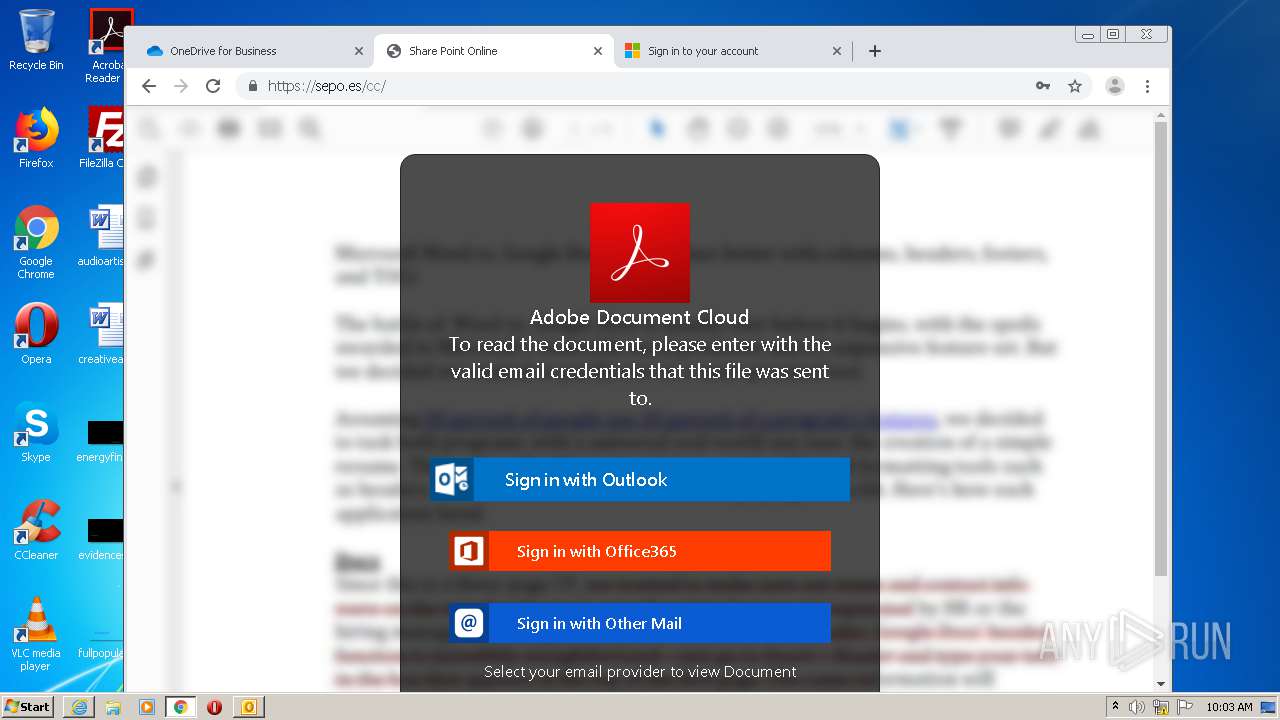
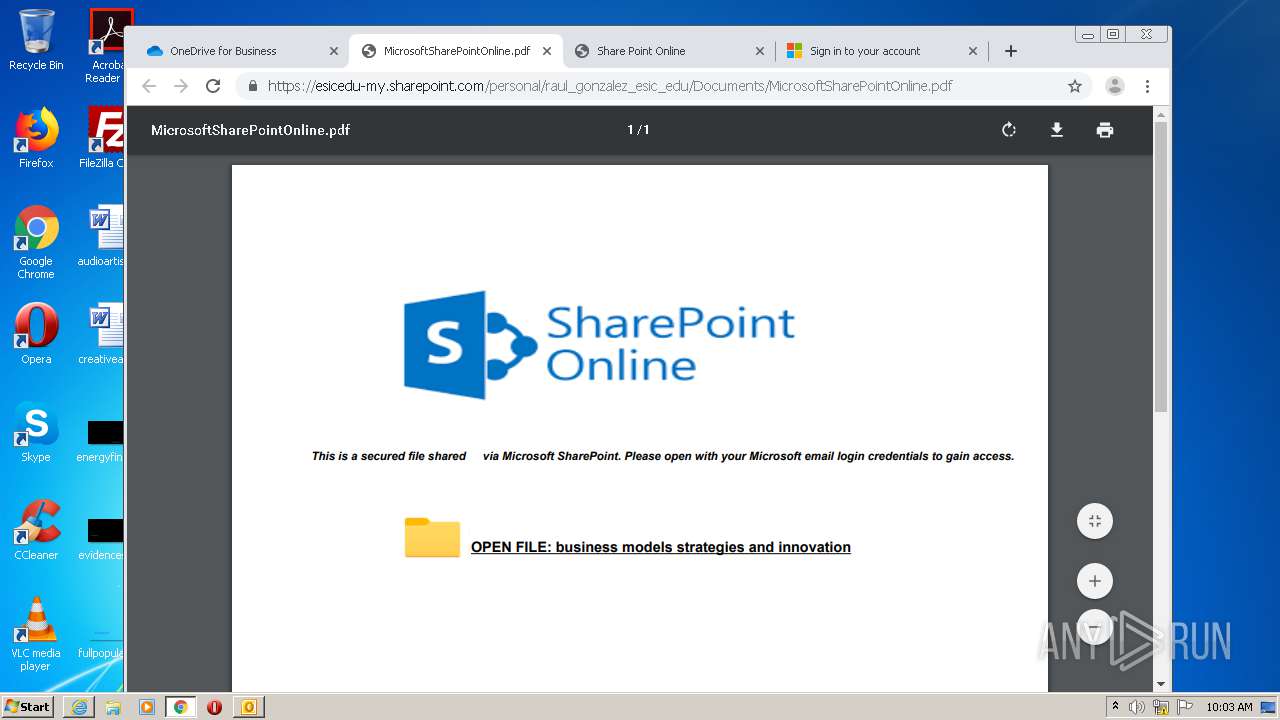
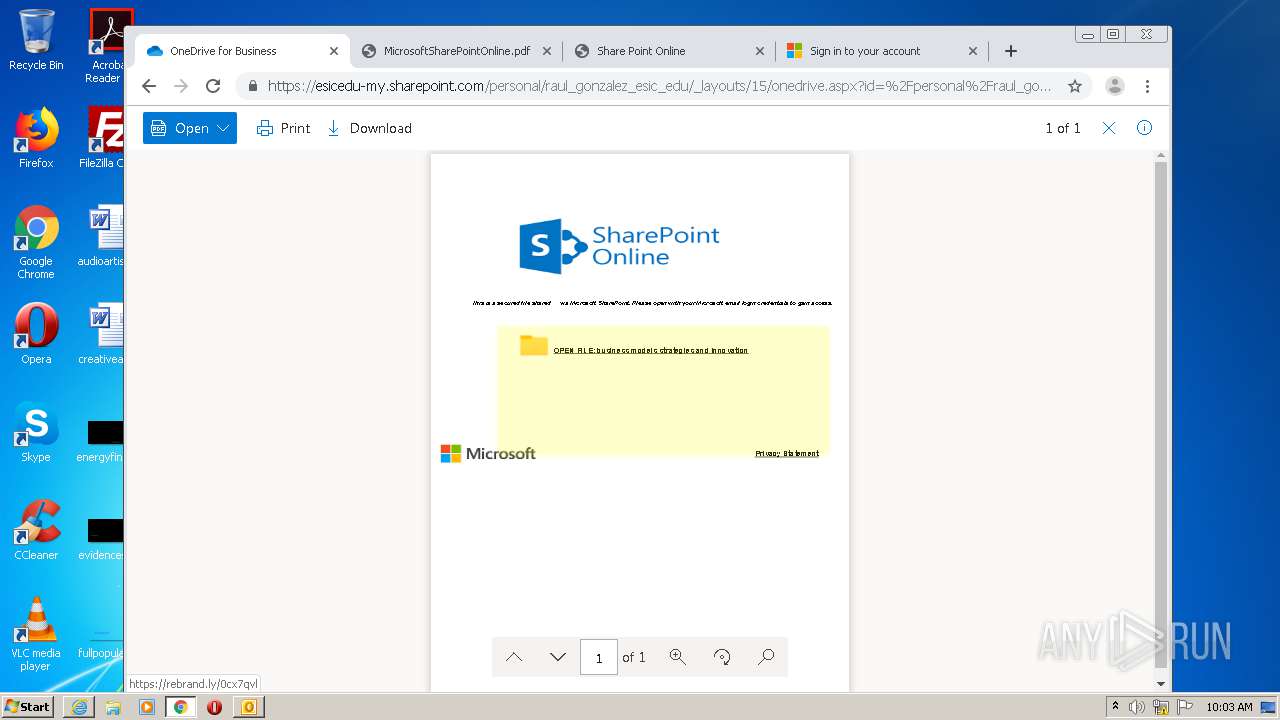
| File name: | RV Raul Gonzalez Martin share a file with you.msg |
| Full analysis: | https://app.any.run/tasks/0e36e375-4e4d-4ce5-b3b1-d2680b3e626e |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2020, 08:59:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 16B6B1C49895C15DE61635FD753826BB |
| SHA1: | 8D9B1B60F344109836BE18D5AD996F7167FA1756 |
| SHA256: | 7DADF14646FD93BBCE05F2530A05F553C7B3AA54C388E092C0D7BB5CC0DCBCC8 |
| SSDEEP: | 1536:gjNmK5lxxzIeUXR+dlRbT/W9OkTYKmxSbQD:gjNX5RUAmLvmxF |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 2944)
SUSPICIOUS
Starts Internet Explorer
- OUTLOOK.EXE (PID: 2944)
INFO
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 2944)
- iexplore.exe (PID: 3988)
- iexplore.exe (PID: 3616)
- chrome.exe (PID: 3176)
Changes internet zones settings
- iexplore.exe (PID: 3988)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2944)
Changes settings of System certificates
- iexplore.exe (PID: 3988)
Creates files in the user directory
- OUTLOOK.EXE (PID: 2944)
- iexplore.exe (PID: 3988)
Reads the hosts file
- chrome.exe (PID: 3176)
- chrome.exe (PID: 3516)
Reads internet explorer settings
- iexplore.exe (PID: 3616)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3988)
Reads settings of System Certificates
- chrome.exe (PID: 3516)
- iexplore.exe (PID: 3616)
- iexplore.exe (PID: 3988)
Application launched itself
- iexplore.exe (PID: 3988)
- chrome.exe (PID: 3176)
Manual execution by user
- chrome.exe (PID: 3176)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (50.8) |
|---|---|---|
| .oft | | | Outlook Form Template (29.7) |
| .doc | | | Microsoft Word document (old ver.) (13.6) |
Total processes
80
Monitored processes
39
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 792 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,14767203780690689224,12360827305972315815,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=8027358975054619035 --renderer-client-id=25 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4036 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 952 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,14767203780690689224,12360827305972315815,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16054743733030068368 --renderer-client-id=14 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3624 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1548 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,14767203780690689224,12360827305972315815,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=2091644702425575484 --renderer-client-id=29 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4580 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1924 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1012,14767203780690689224,12360827305972315815,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=4748808194543038743 --mojo-platform-channel-handle=3608 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2056 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,14767203780690689224,12360827305972315815,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3888610606931510491 --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3008 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2096 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=75.0.3770.100 --initial-client-data=0x7c,0x80,0x84,0x78,0x88,0x6030a9d0,0x6030a9e0,0x6030a9ec | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2116 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,14767203780690689224,12360827305972315815,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9571284390636042814 --renderer-client-id=32 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4476 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2216 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,14767203780690689224,12360827305972315815,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=14735442709157534762 --renderer-client-id=16 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3204 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2276 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,14767203780690689224,12360827305972315815,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=16403692789581784098 --renderer-client-id=33 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4568 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2472 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1012,14767203780690689224,12360827305972315815,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3583779530501557482 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2236 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
3 379
Read events
2 244
Write events
1 110
Delete events
25
Modification events
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (2944) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
130
Text files
197
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2944 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR5161.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3616 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabD6BD.tmp | — | |
MD5:— | SHA256:— | |||
| 3616 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarD6BE.tmp | — | |
MD5:— | SHA256:— | |||
| 2944 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 3988 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\CabE014.tmp | — | |
MD5:— | SHA256:— | |||
| 3988 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\TarE015.tmp | — | |
MD5:— | SHA256:— | |||
| 2944 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2944 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\StructuredQuery.log | text | |
MD5:— | SHA256:— | |||
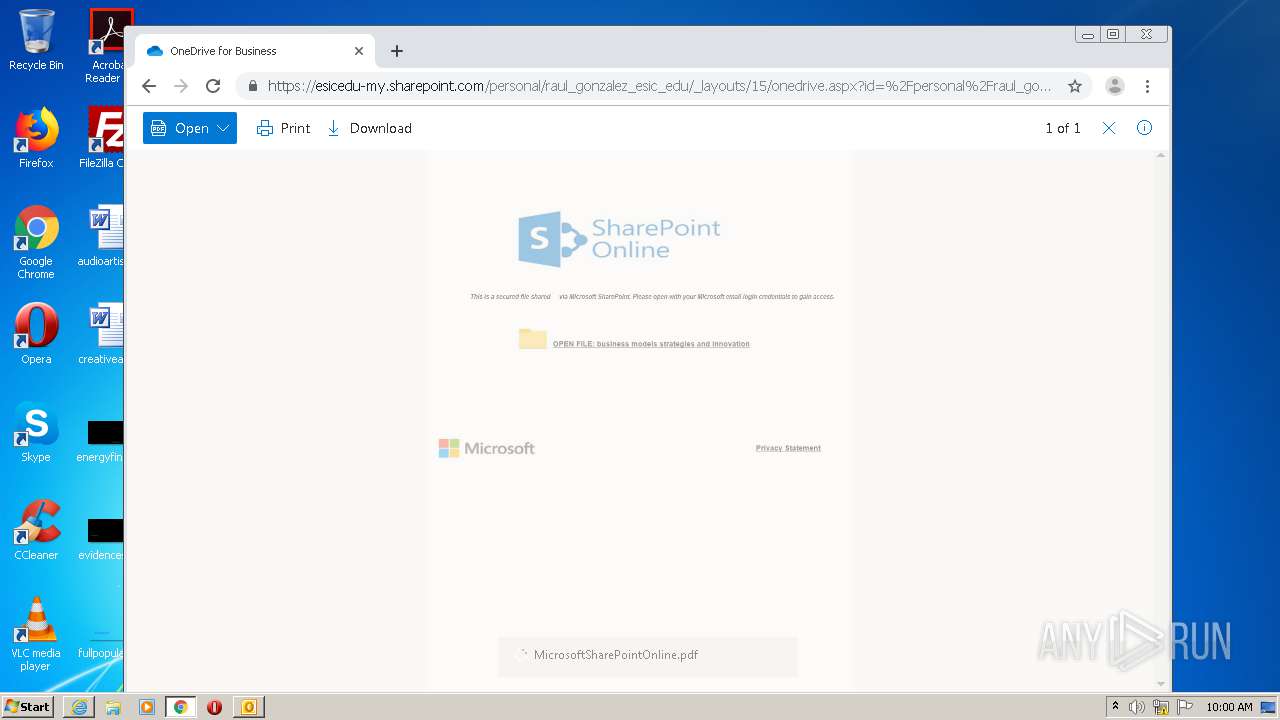
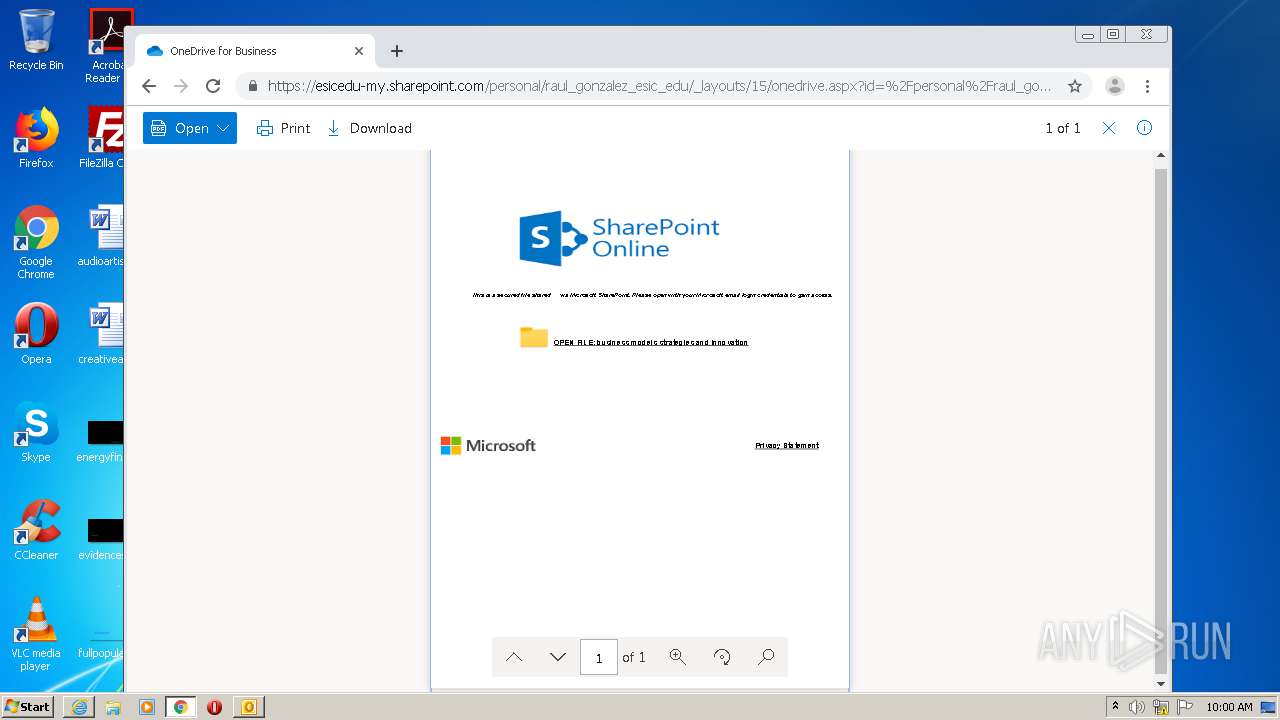
| 3616 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\onedrive[1].htm | html | |
MD5:— | SHA256:— | |||
| 3988 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
124
DNS requests
58
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2944 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
3616 | iexplore.exe | GET | 304 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAtb9ltrp%2FvQiykNkEU33uA%3D | US | — | — | whitelisted |
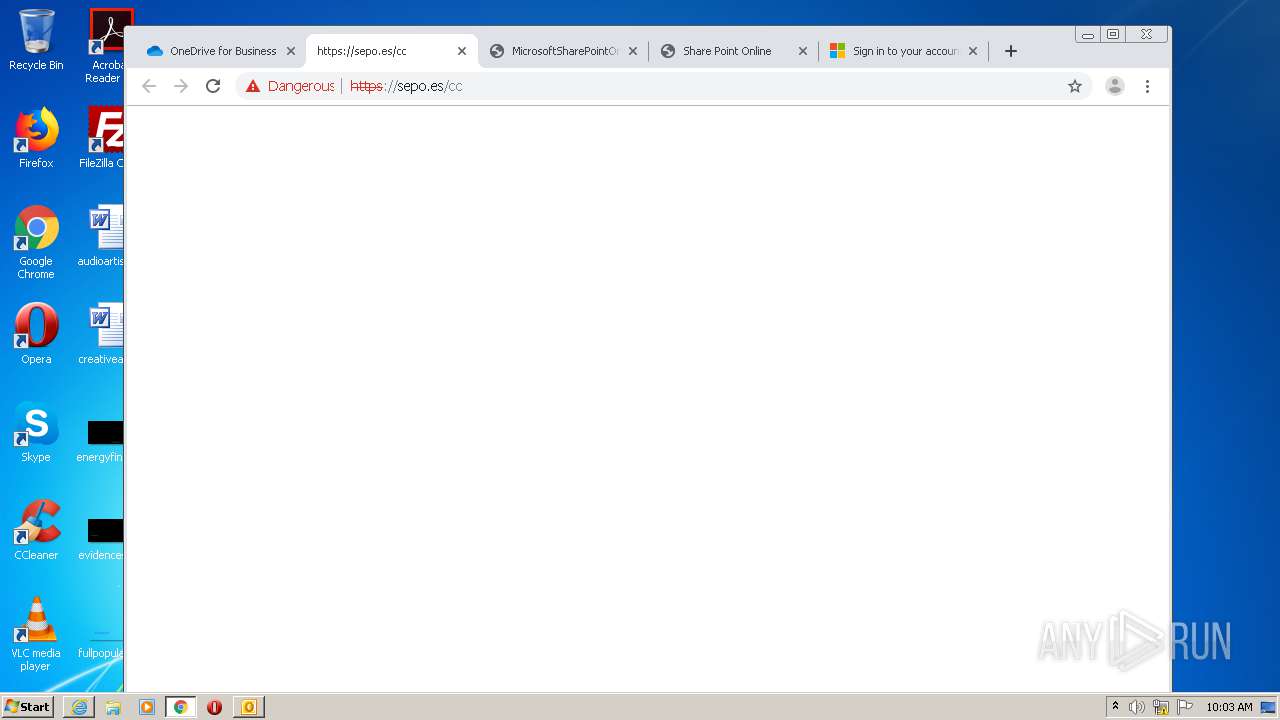
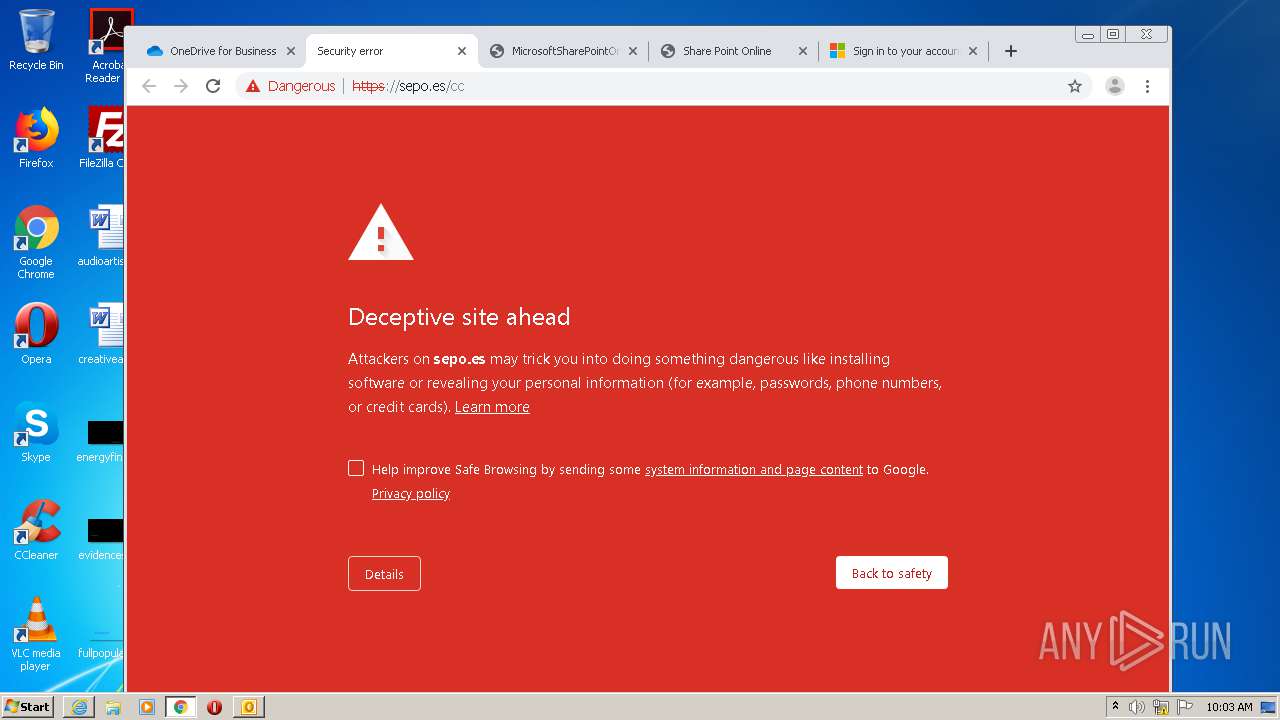
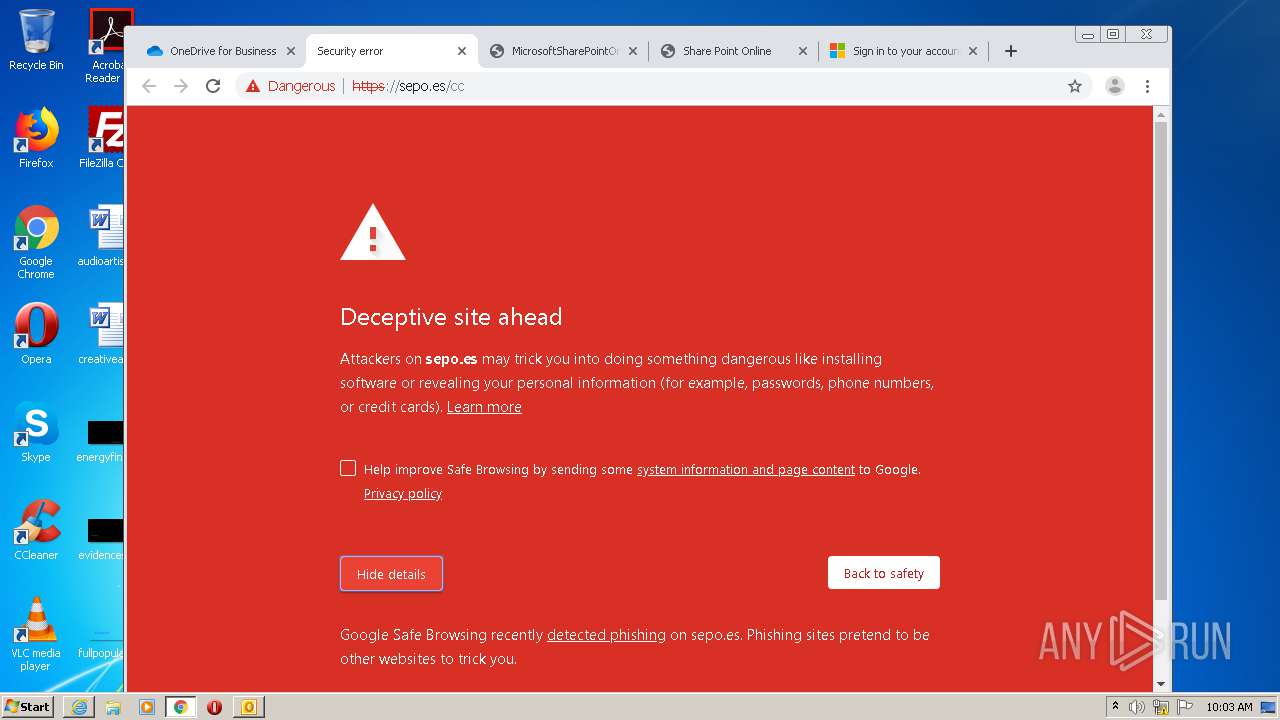
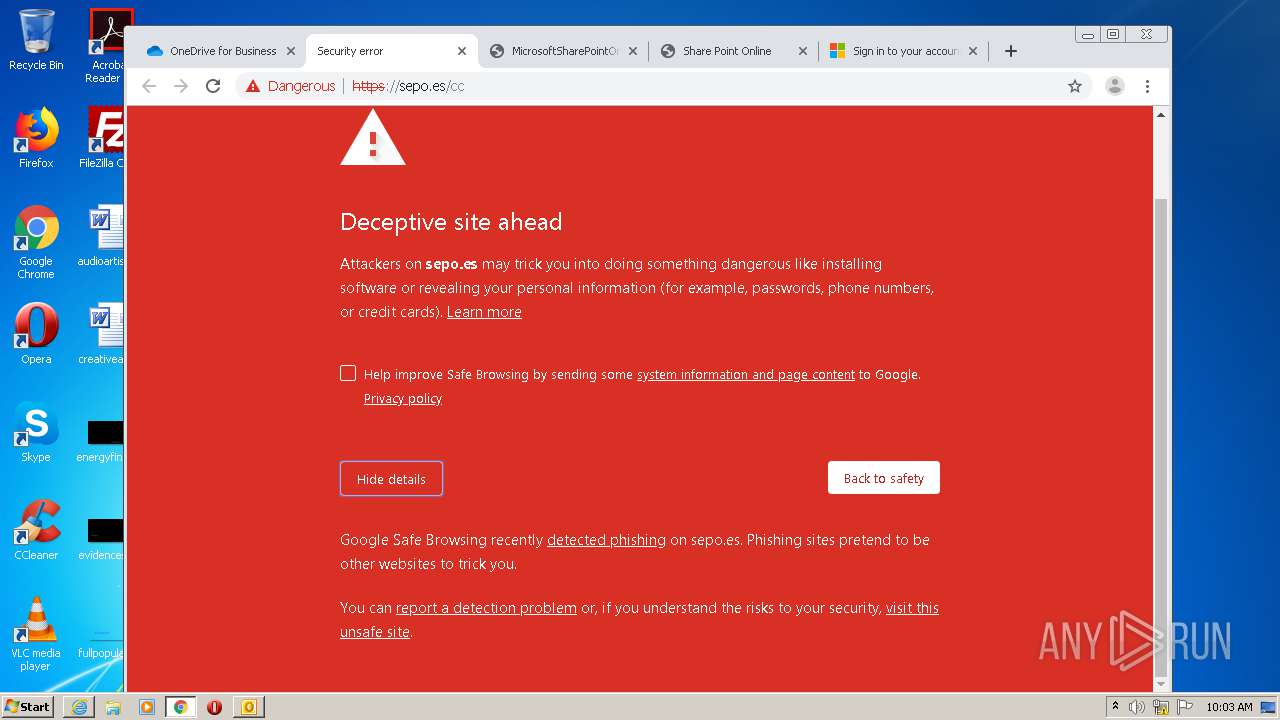
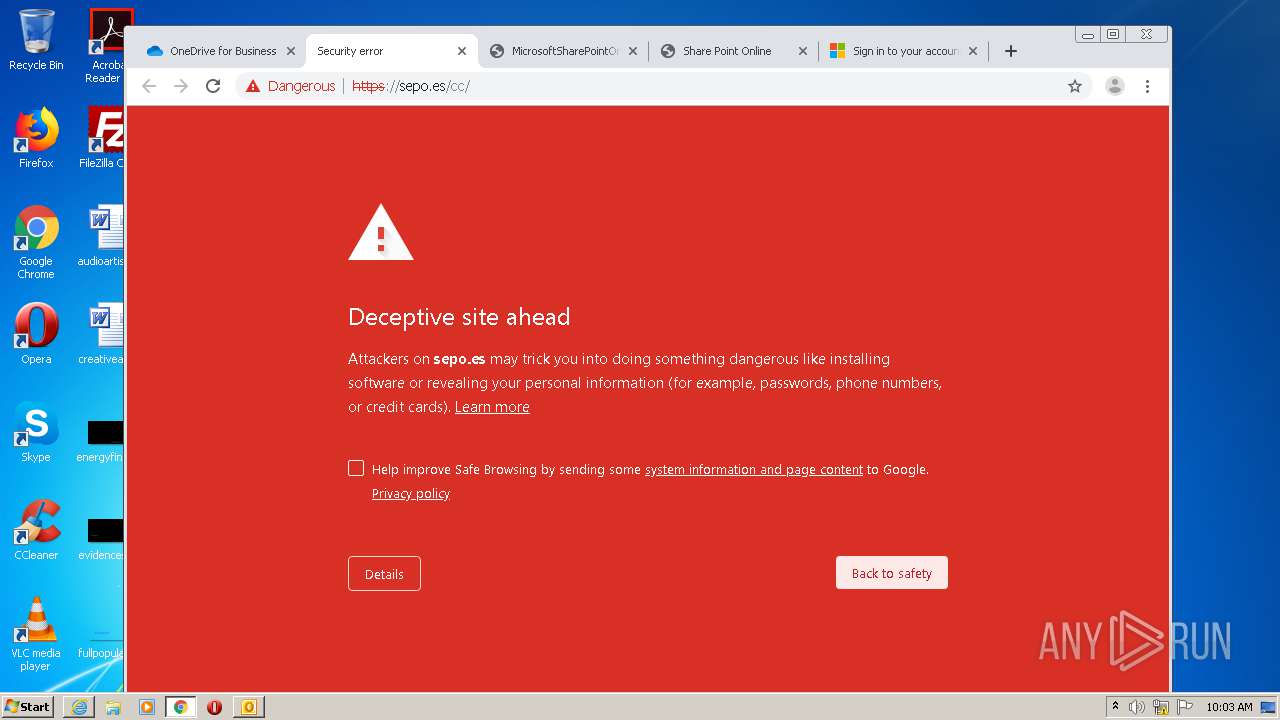
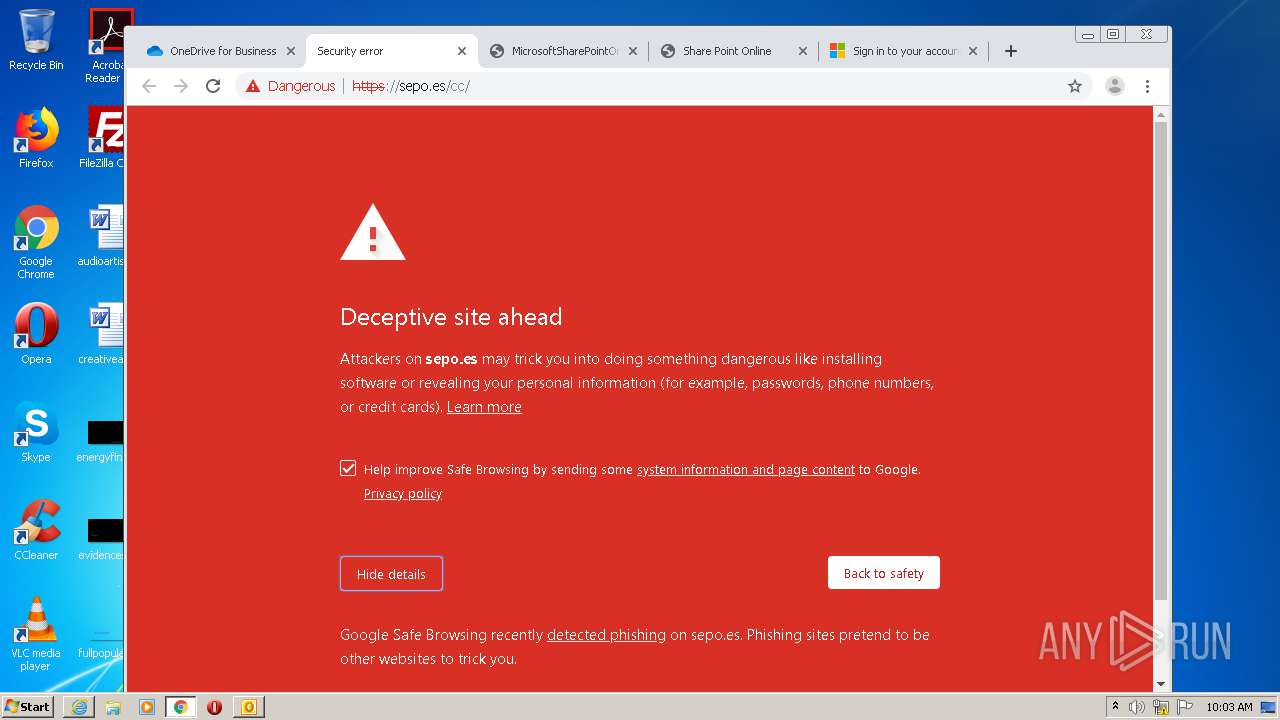
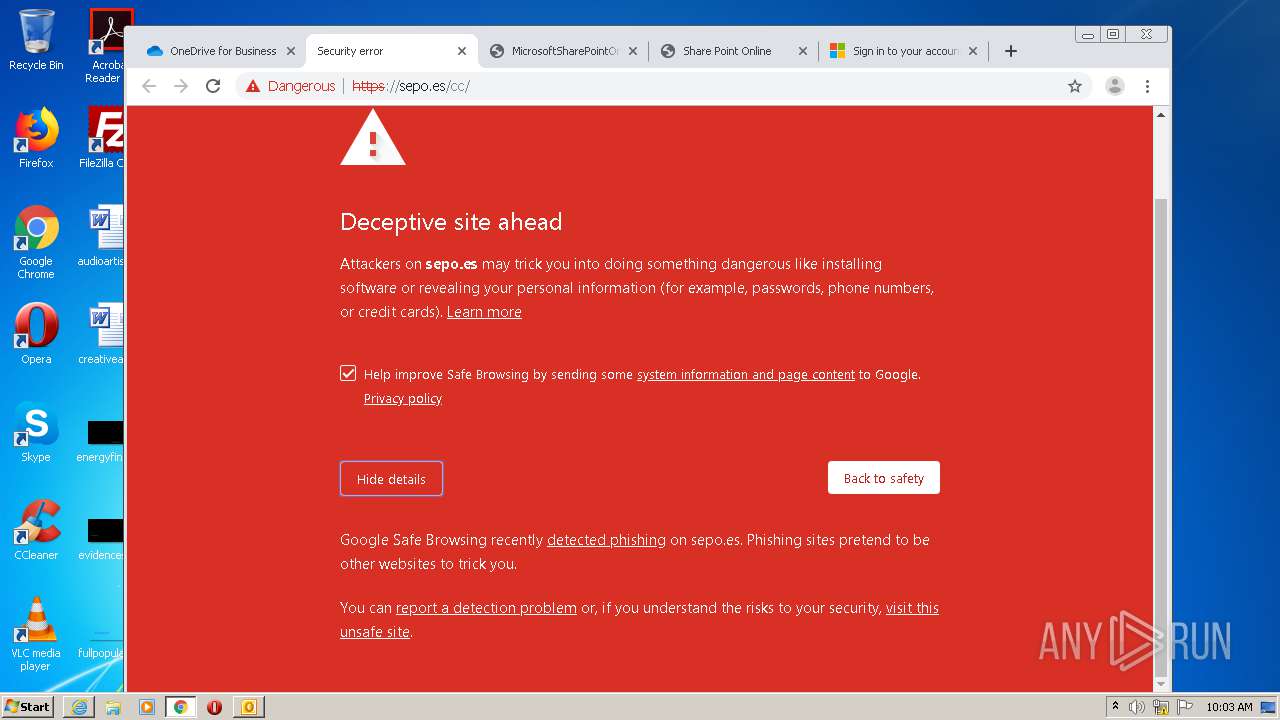
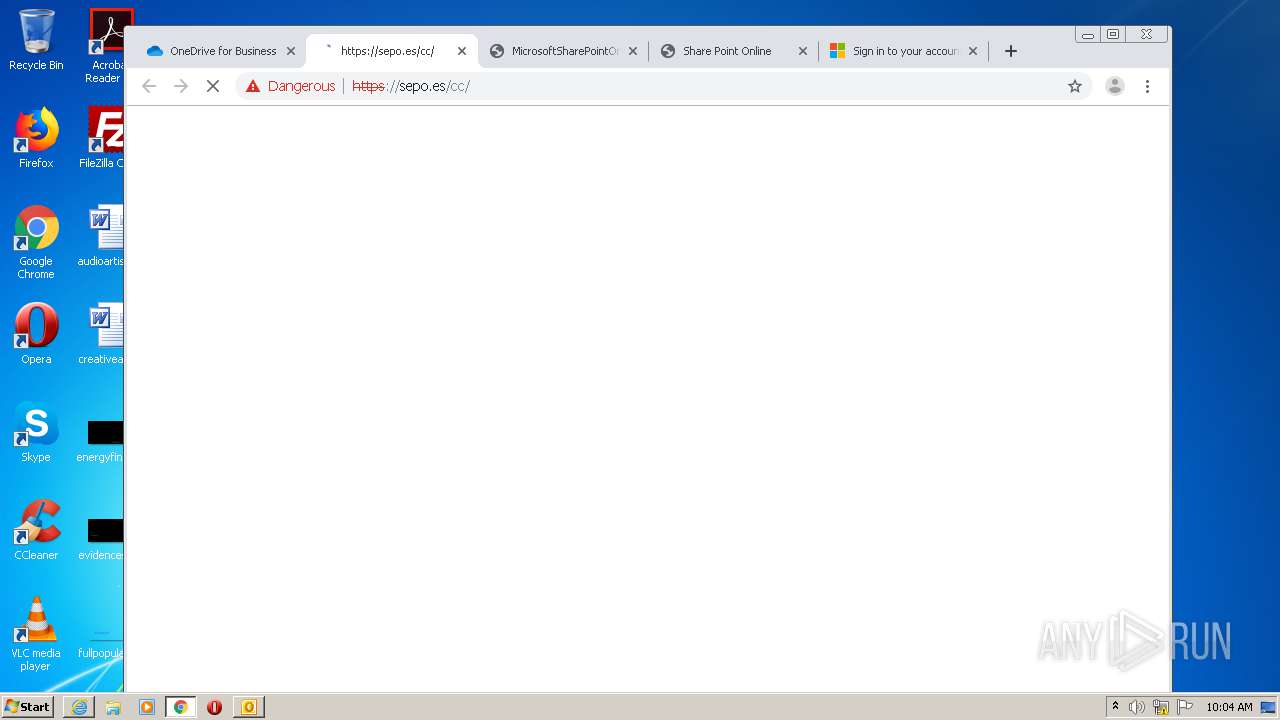
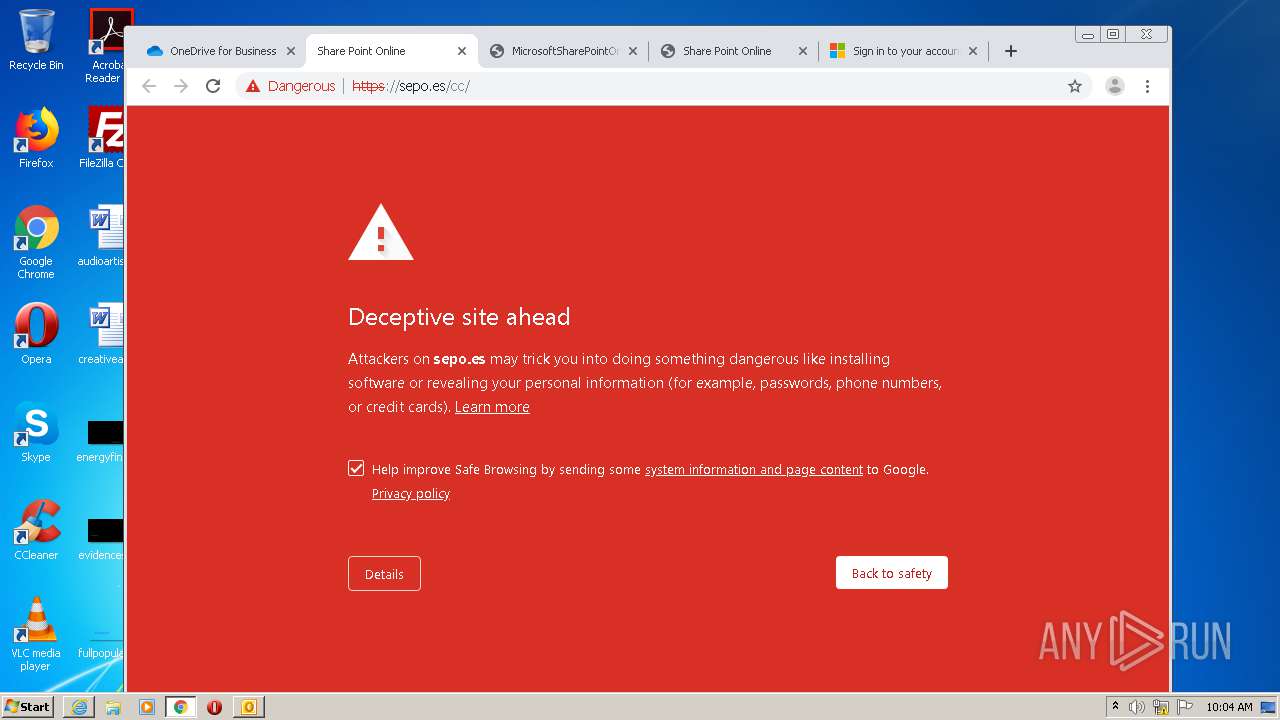
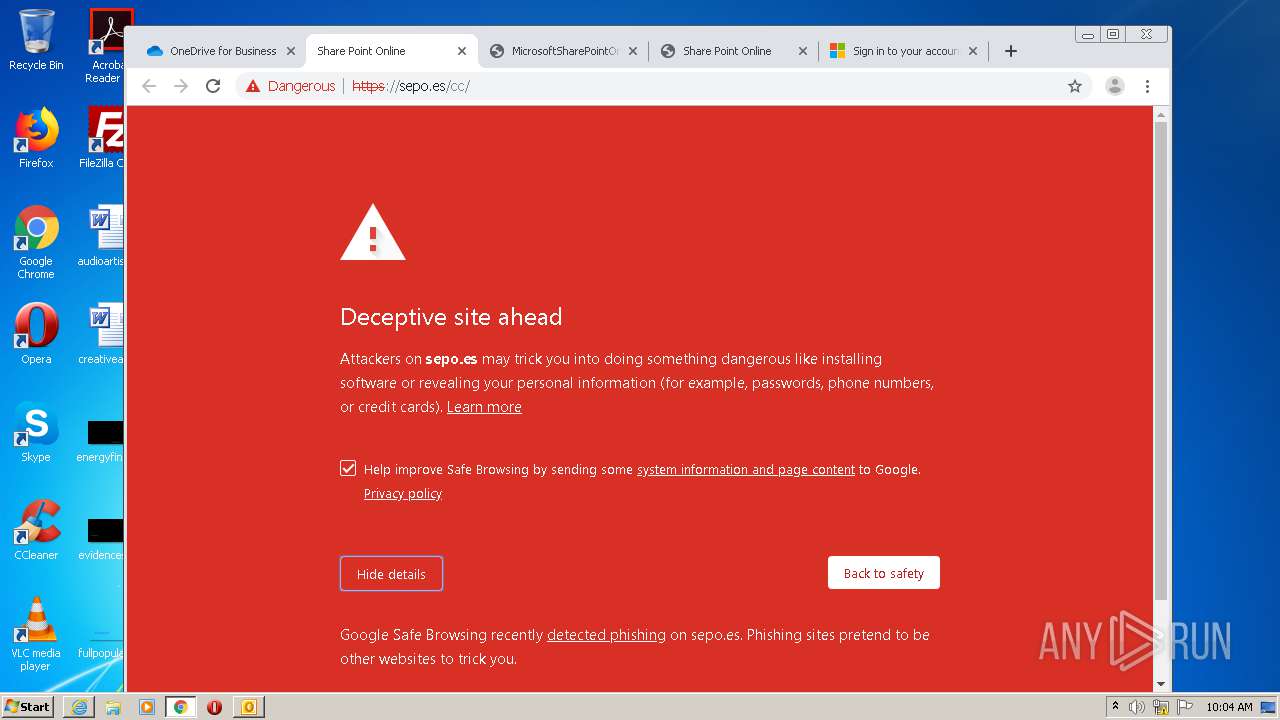
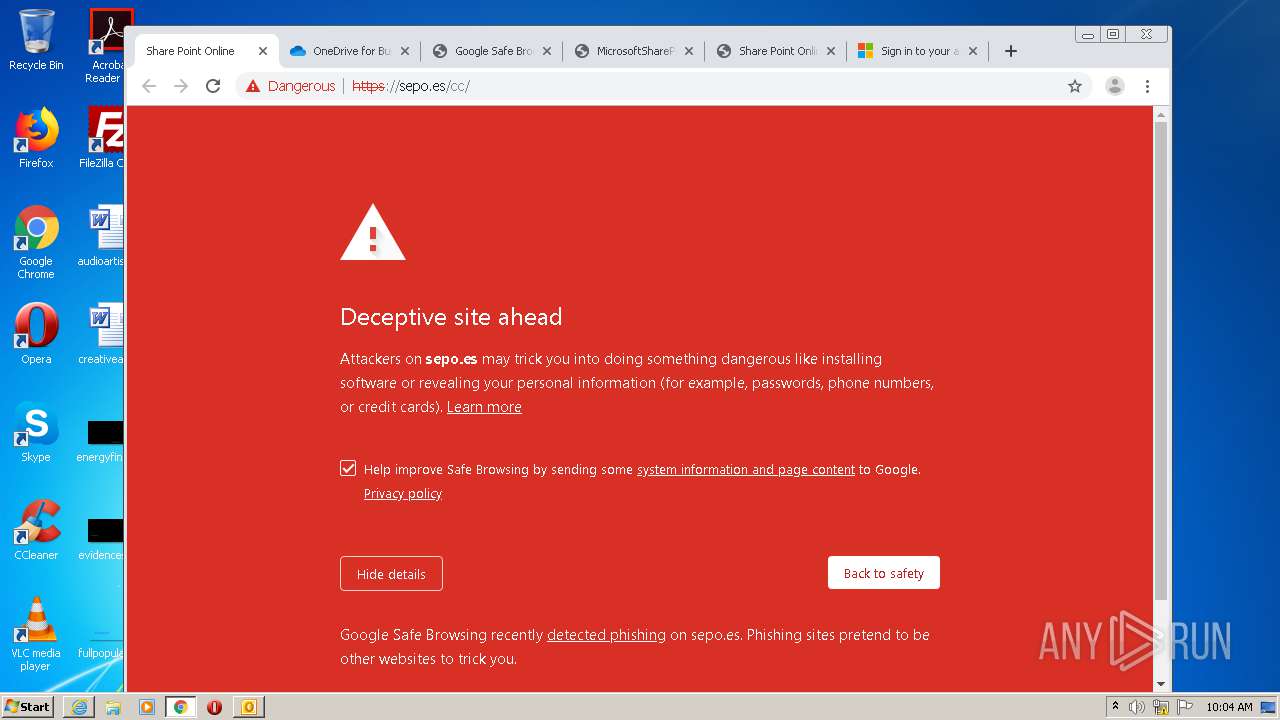
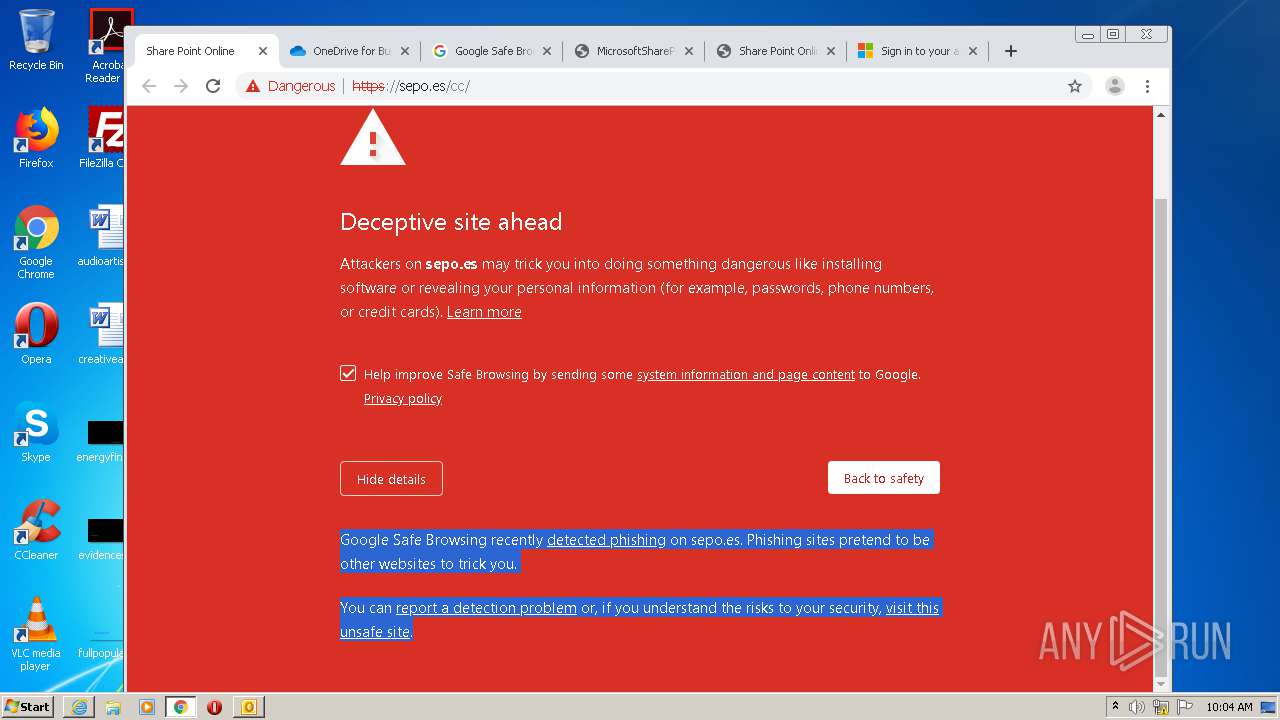
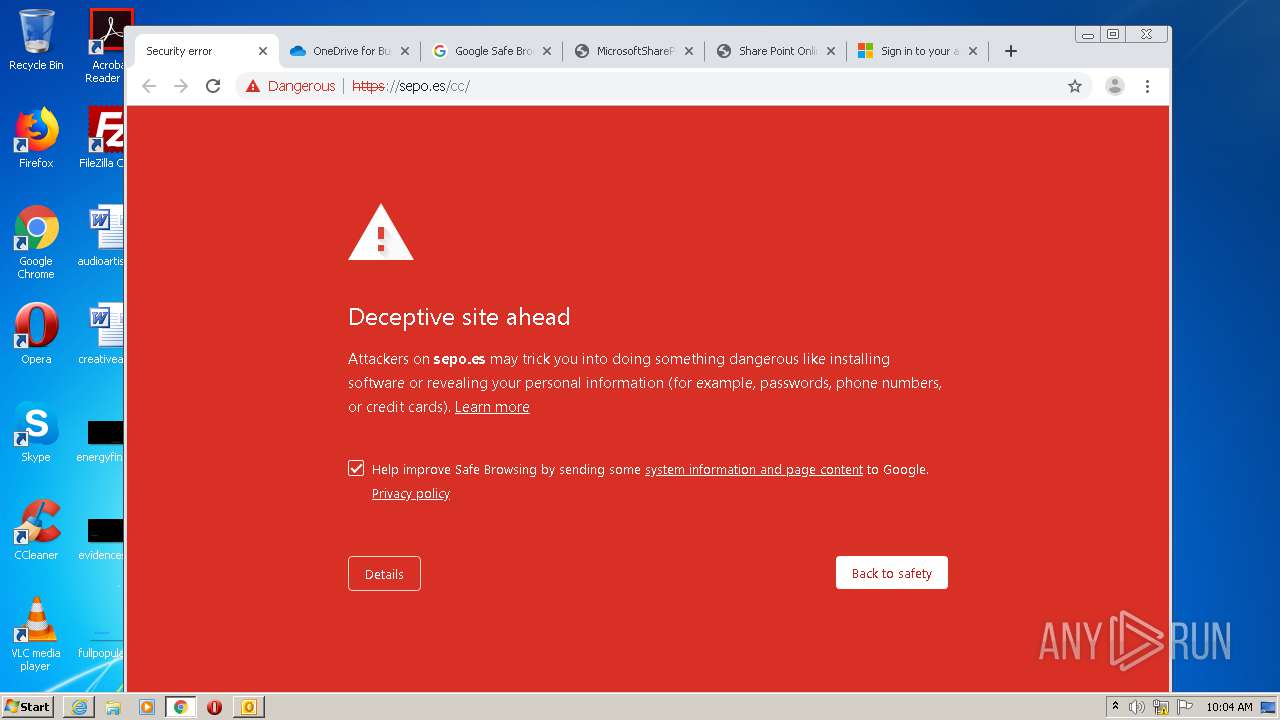
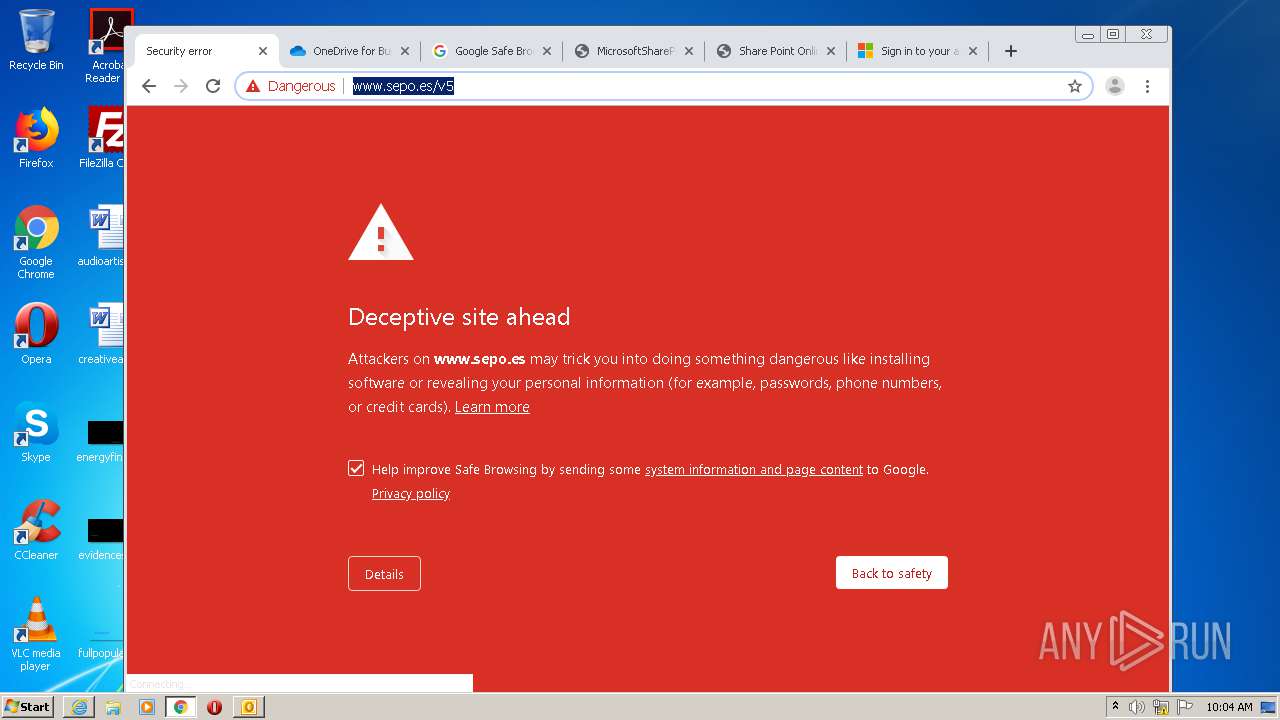
3516 | chrome.exe | GET | — | 46.105.171.173:80 | http://sepo.es/v5/ | FR | — | — | unknown |
3616 | iexplore.exe | GET | 304 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAtb9ltrp%2FvQiykNkEU33uA%3D | US | — | — | whitelisted |
3616 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
3616 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
3616 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAtb9ltrp%2FvQiykNkEU33uA%3D | US | der | 471 b | whitelisted |
3616 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAiIzVJfGSRETRSlgpHeuVI%3D | US | der | 1.47 Kb | whitelisted |
3616 | iexplore.exe | GET | 304 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAtb9ltrp%2FvQiykNkEU33uA%3D | US | der | 1.47 Kb | whitelisted |
3516 | chrome.exe | GET | 301 | 46.105.171.173:80 | http://www.sepo.es/v5/ | FR | html | 230 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3516 | chrome.exe | 172.217.18.174:443 | clients2.google.com | Google Inc. | US | whitelisted |
3516 | chrome.exe | 216.58.205.227:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3516 | chrome.exe | 216.58.207.42:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3516 | chrome.exe | 172.217.23.163:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
3516 | chrome.exe | 172.217.22.110:443 | apis.google.com | Google Inc. | US | whitelisted |
3516 | chrome.exe | 172.217.22.78:443 | ogs.google.com | Google Inc. | US | whitelisted |
3988 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3516 | chrome.exe | 172.217.23.99:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
2944 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
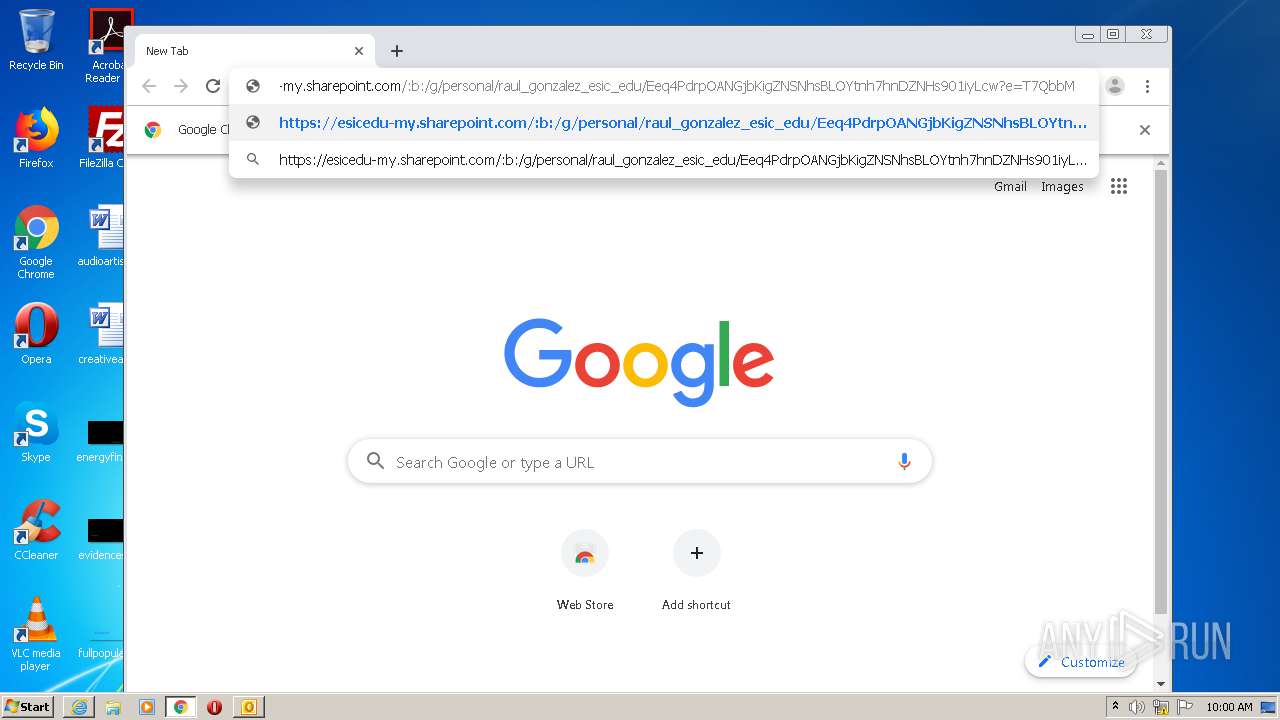
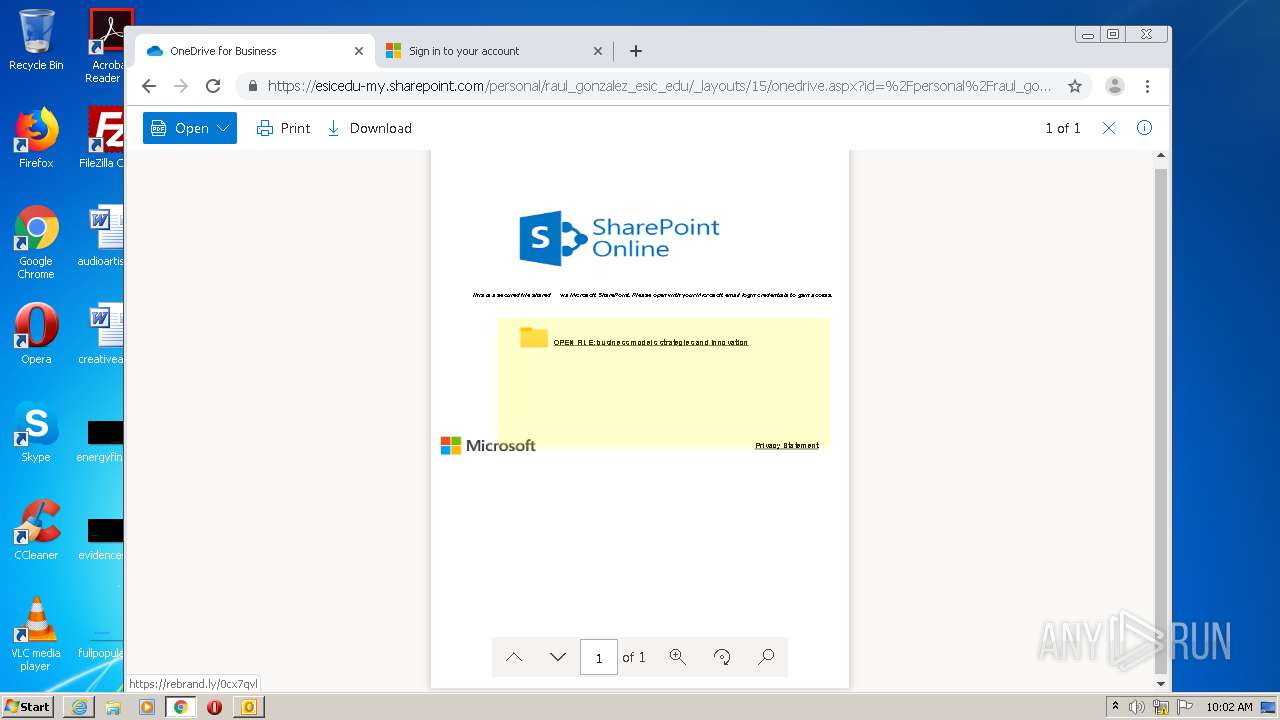
3616 | iexplore.exe | 104.146.250.33:443 | esicedu-my.sharepoint.com | Microsoft Corporation | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
esicedu-my.sharepoint.com |
| suspicious |
ocsp.digicert.com |
| whitelisted |
shell.cdn.office.net |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
clients2.google.com |
| whitelisted |