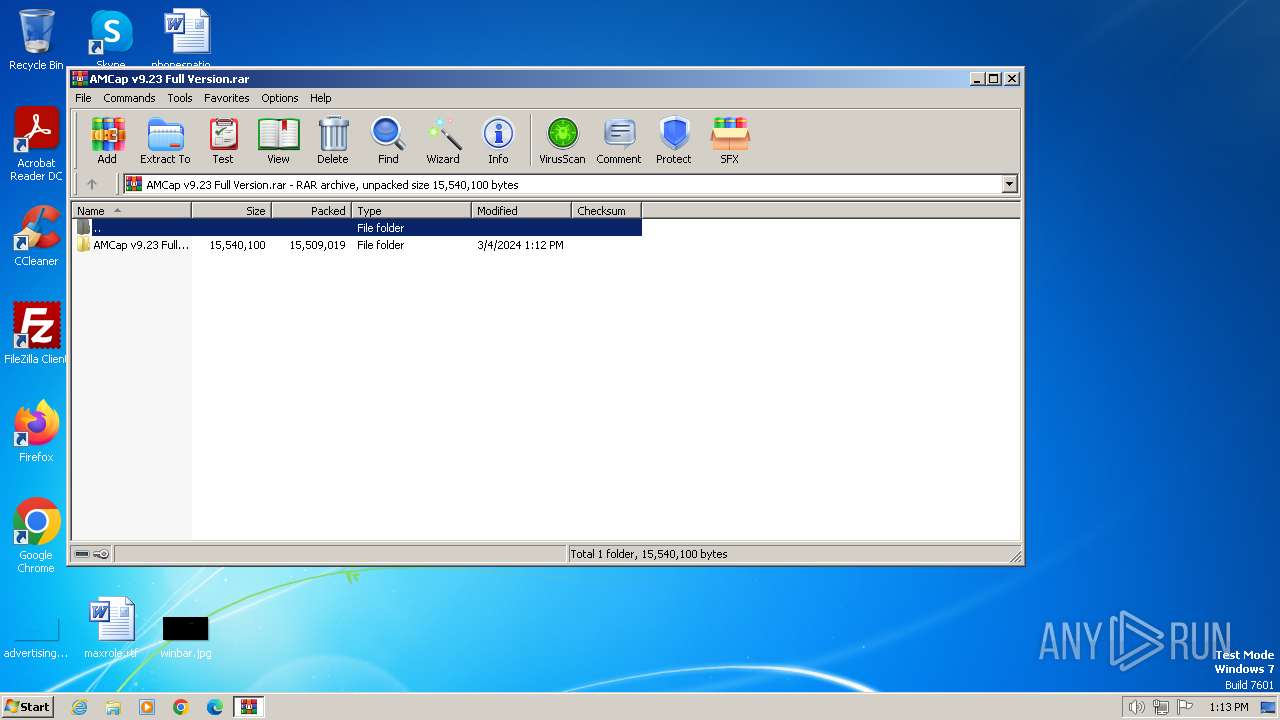
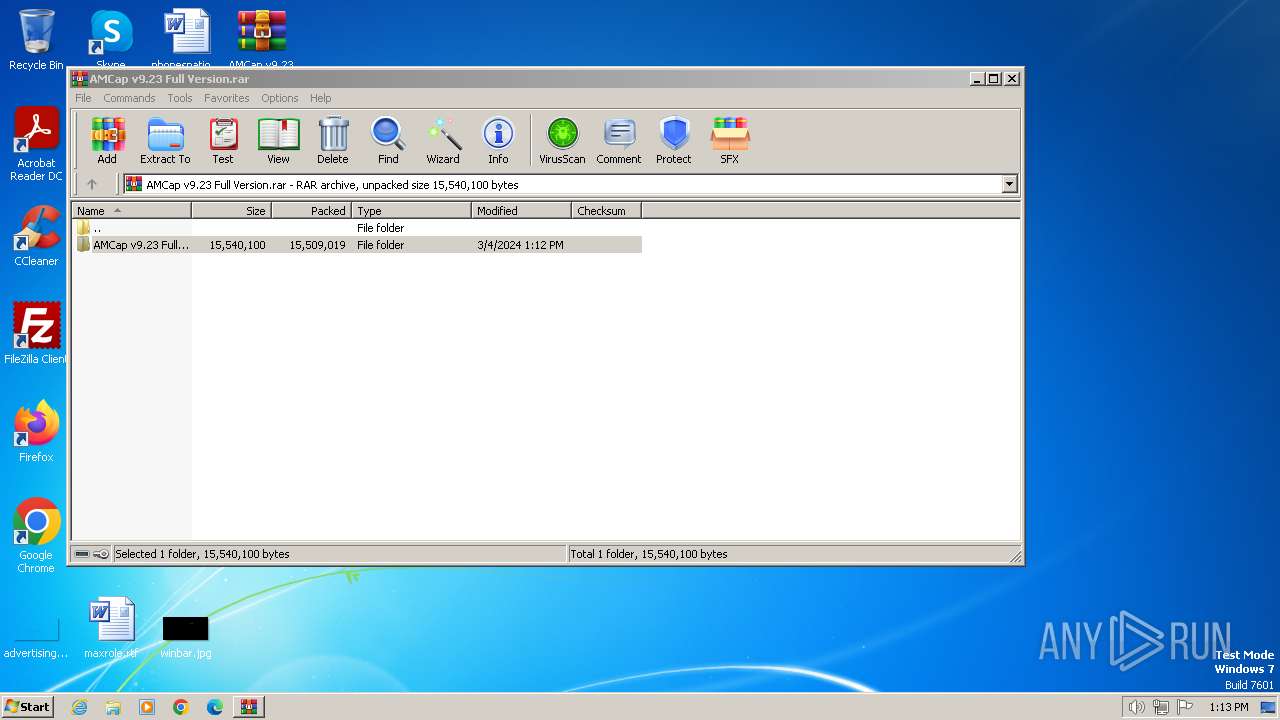
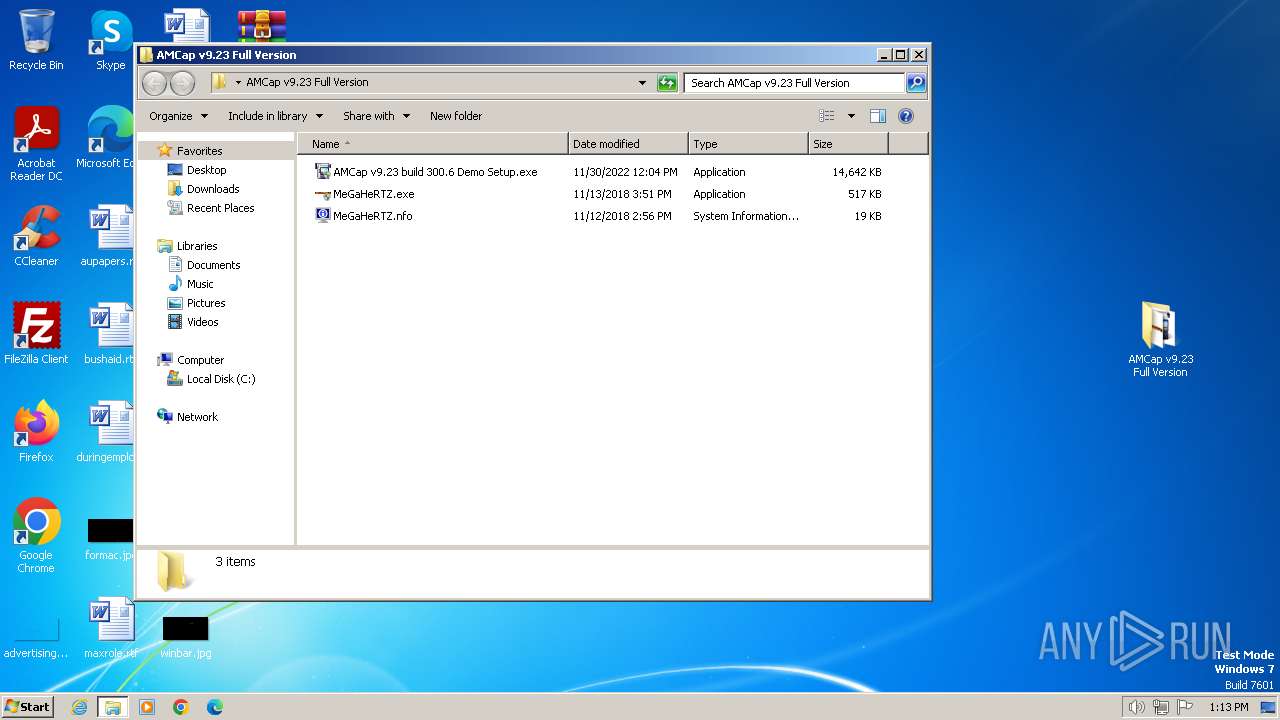
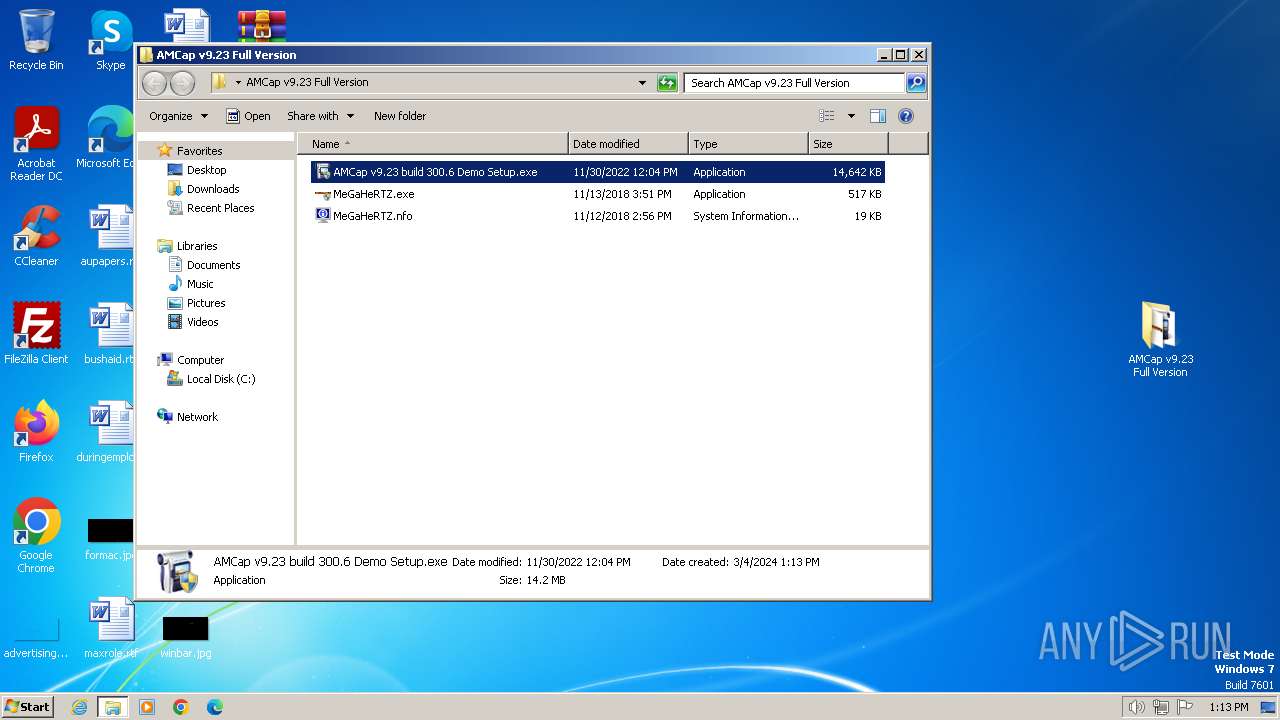
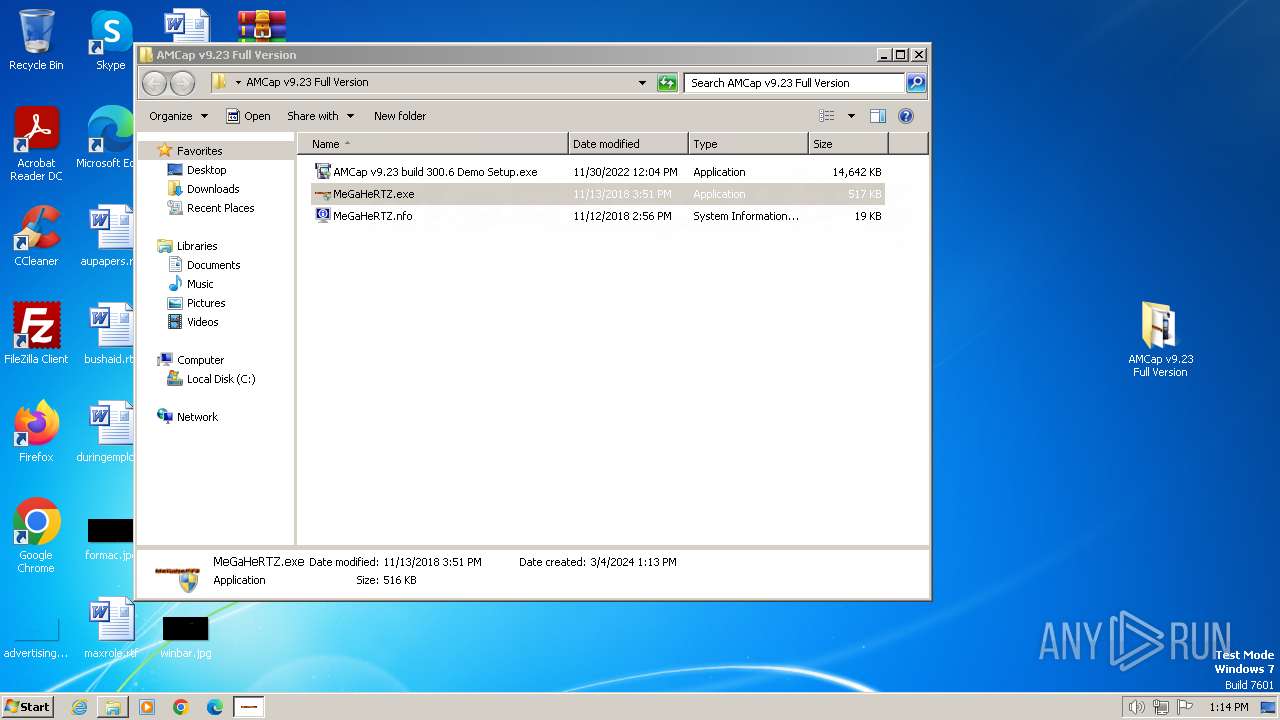
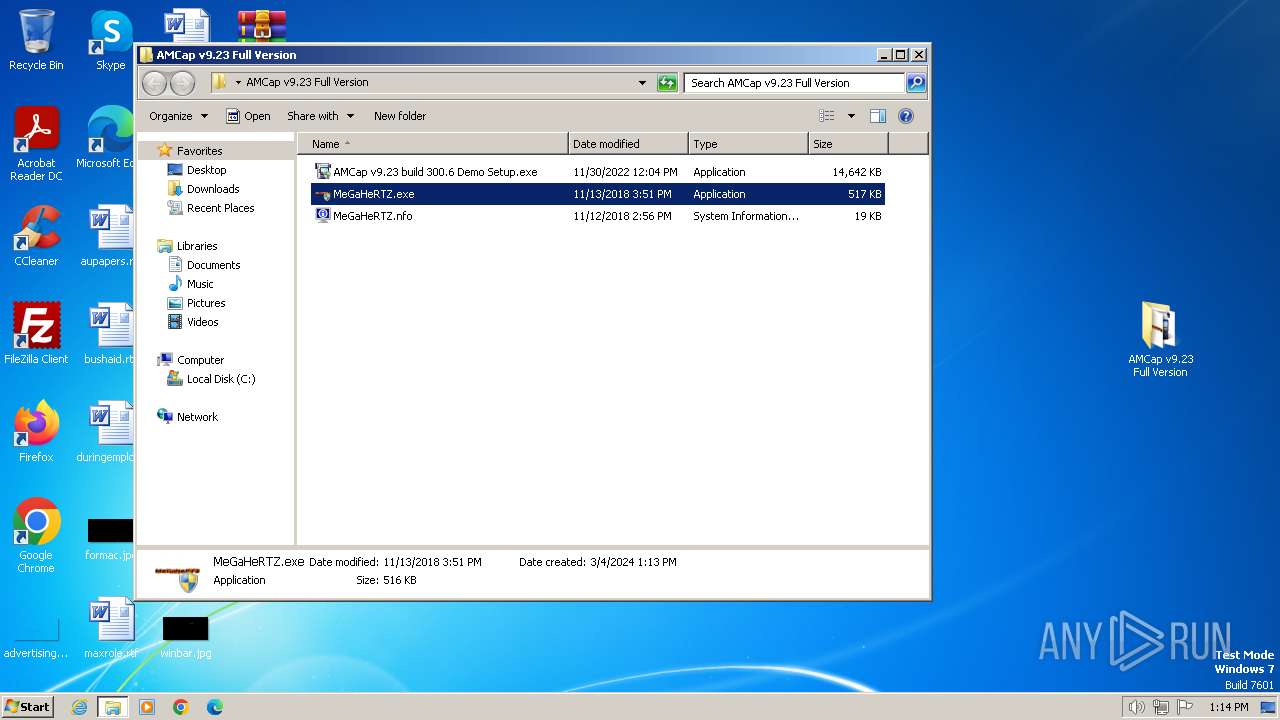
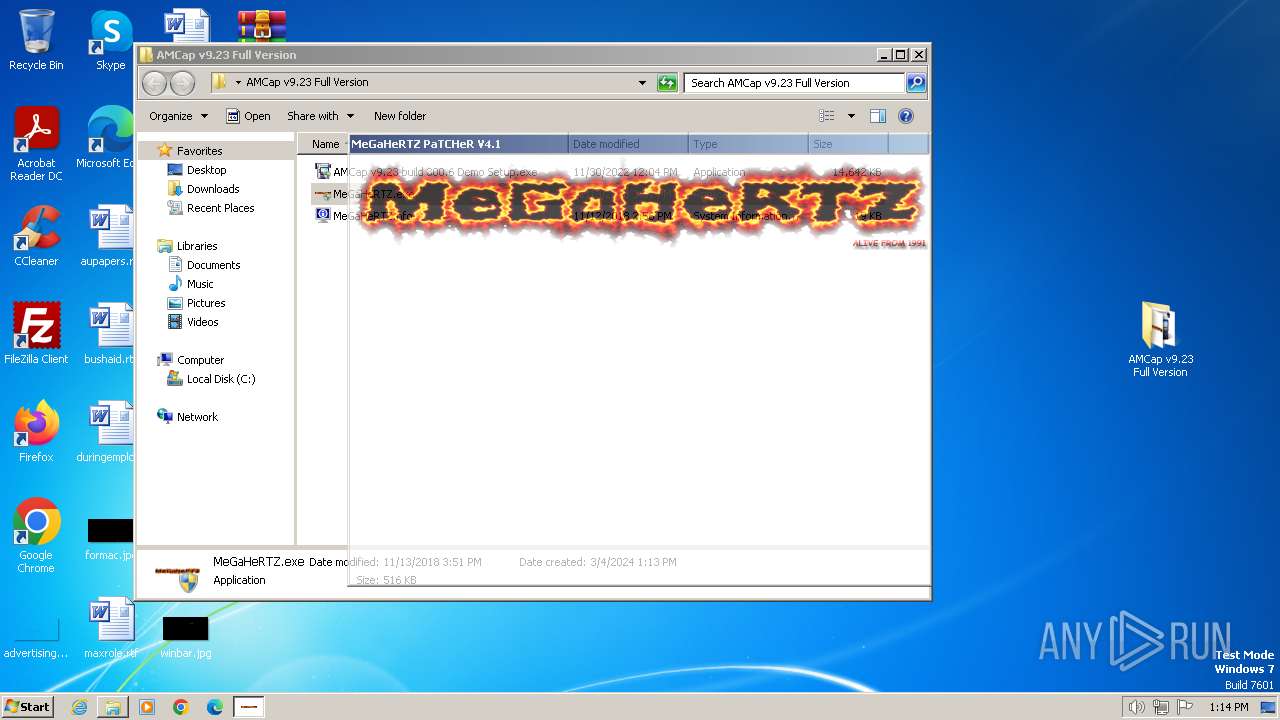
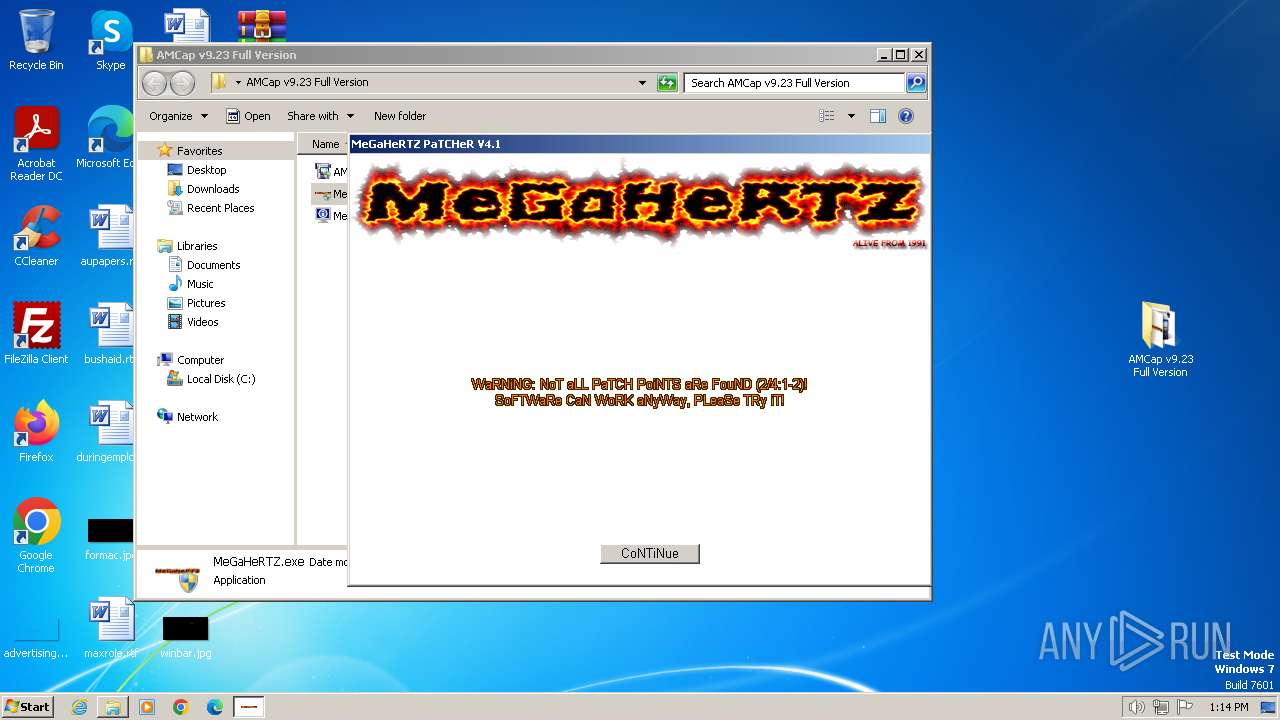
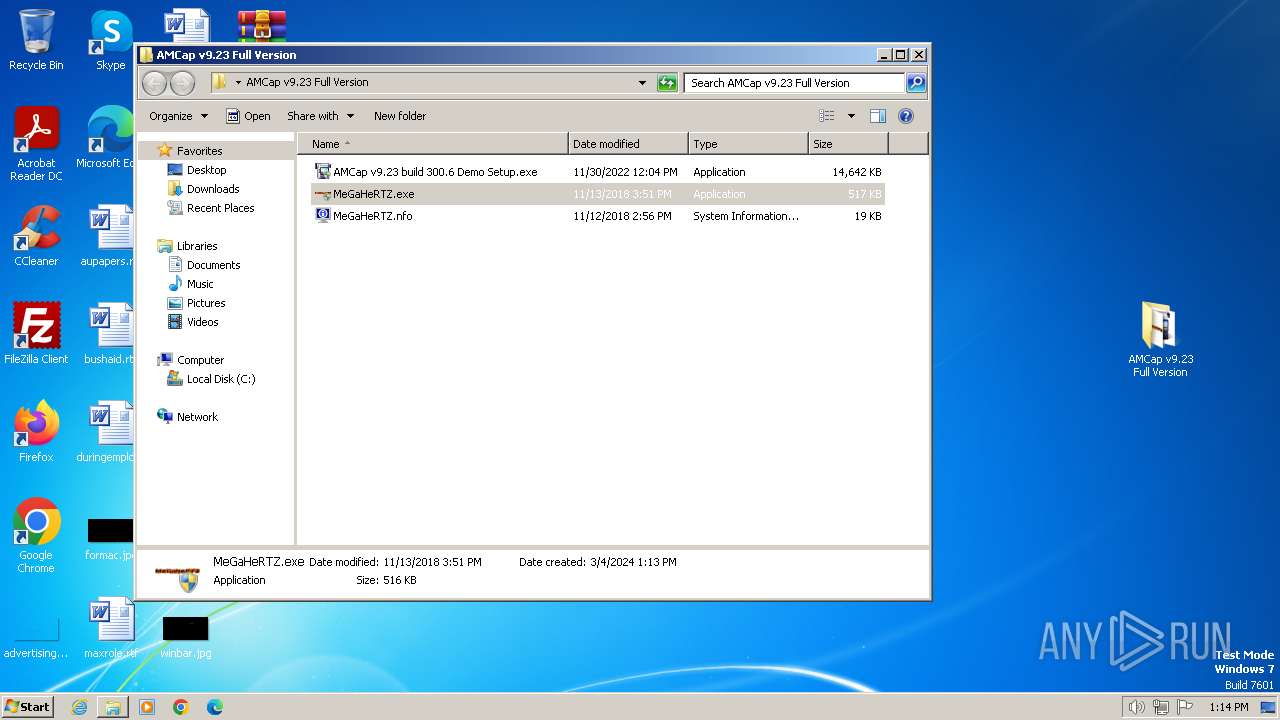
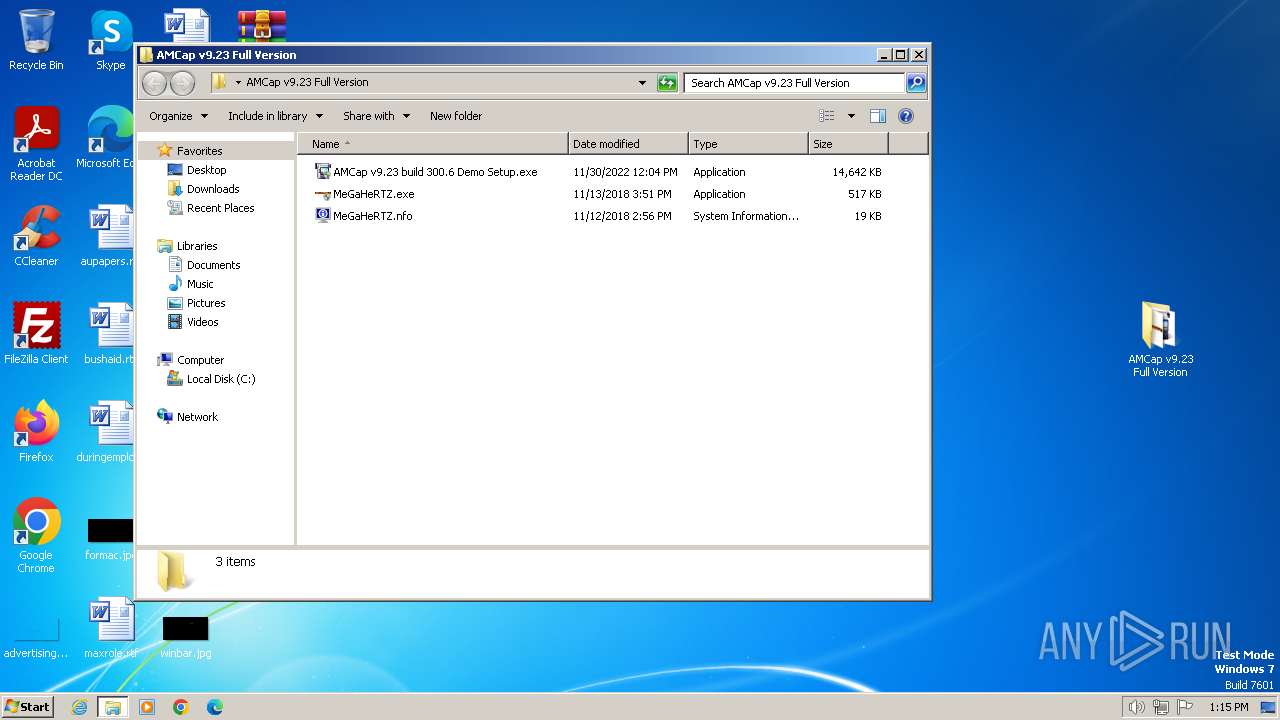
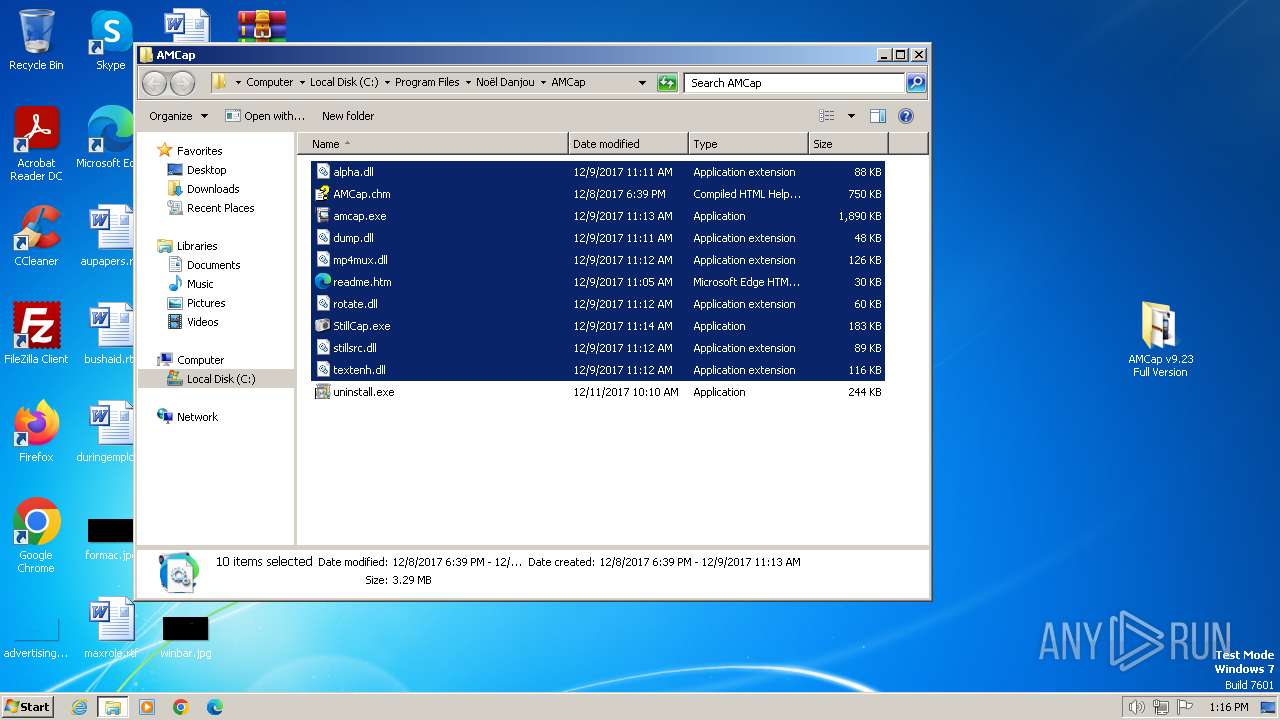
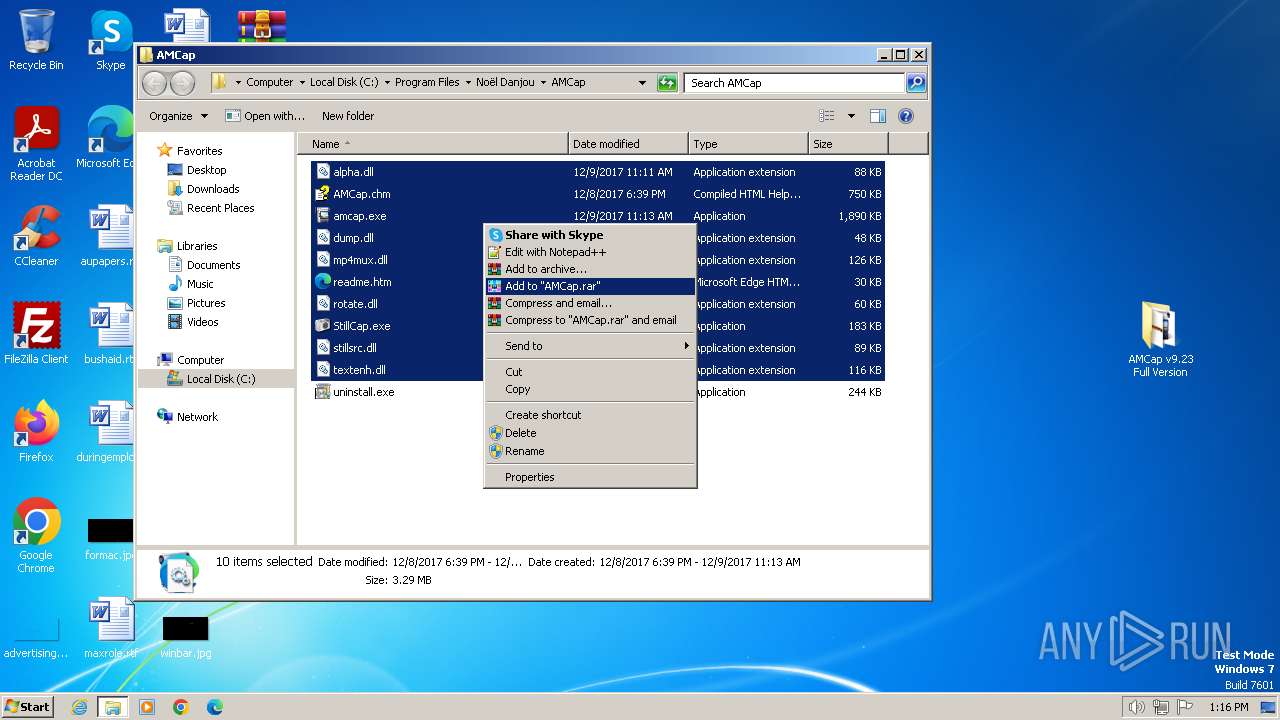
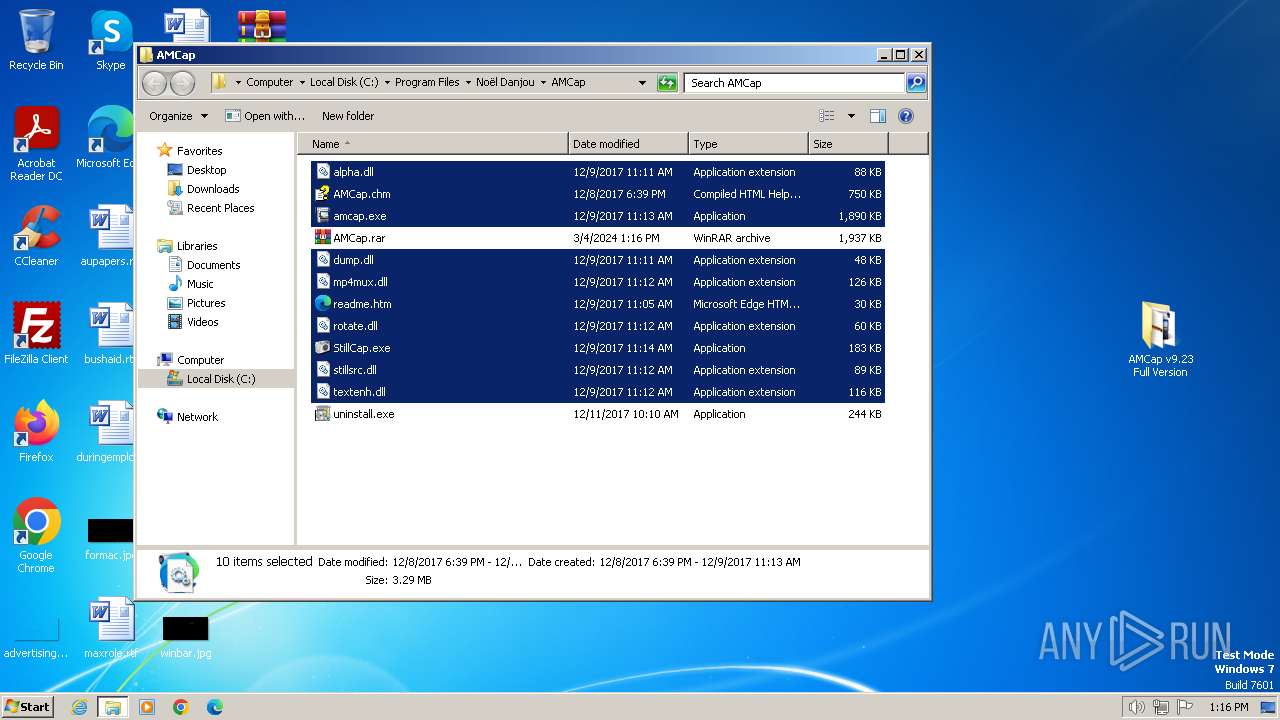
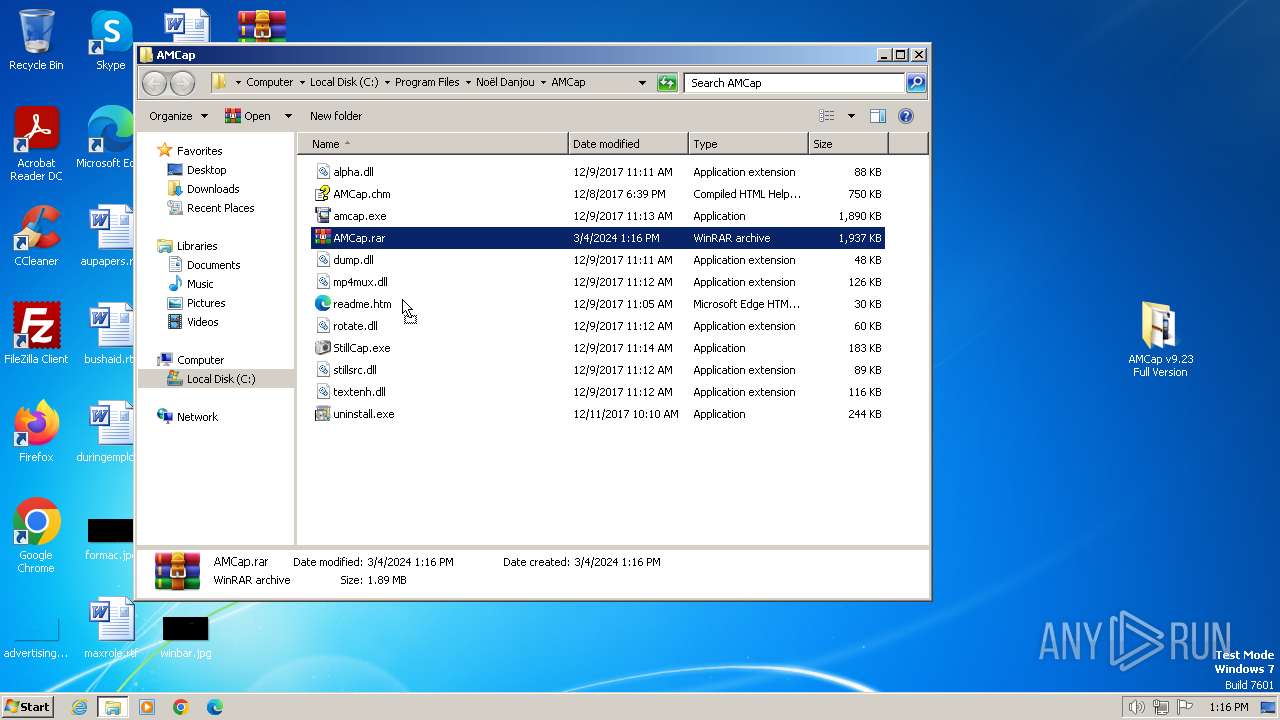
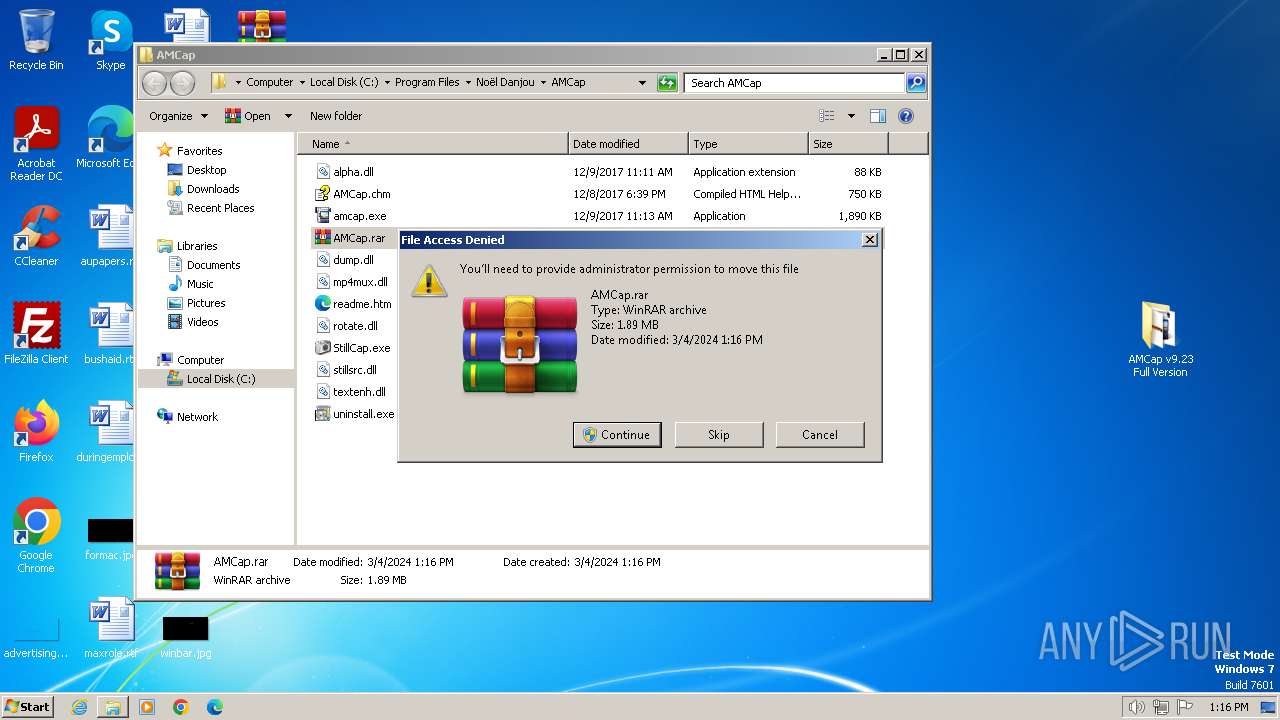
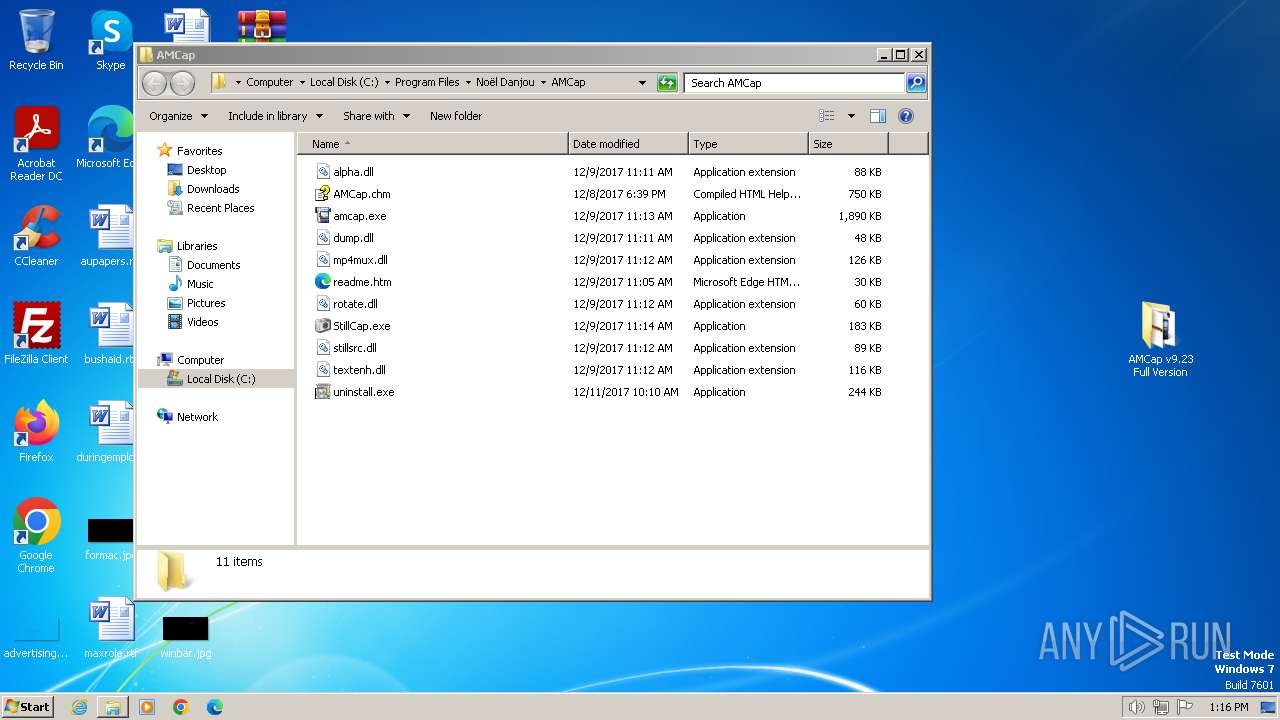
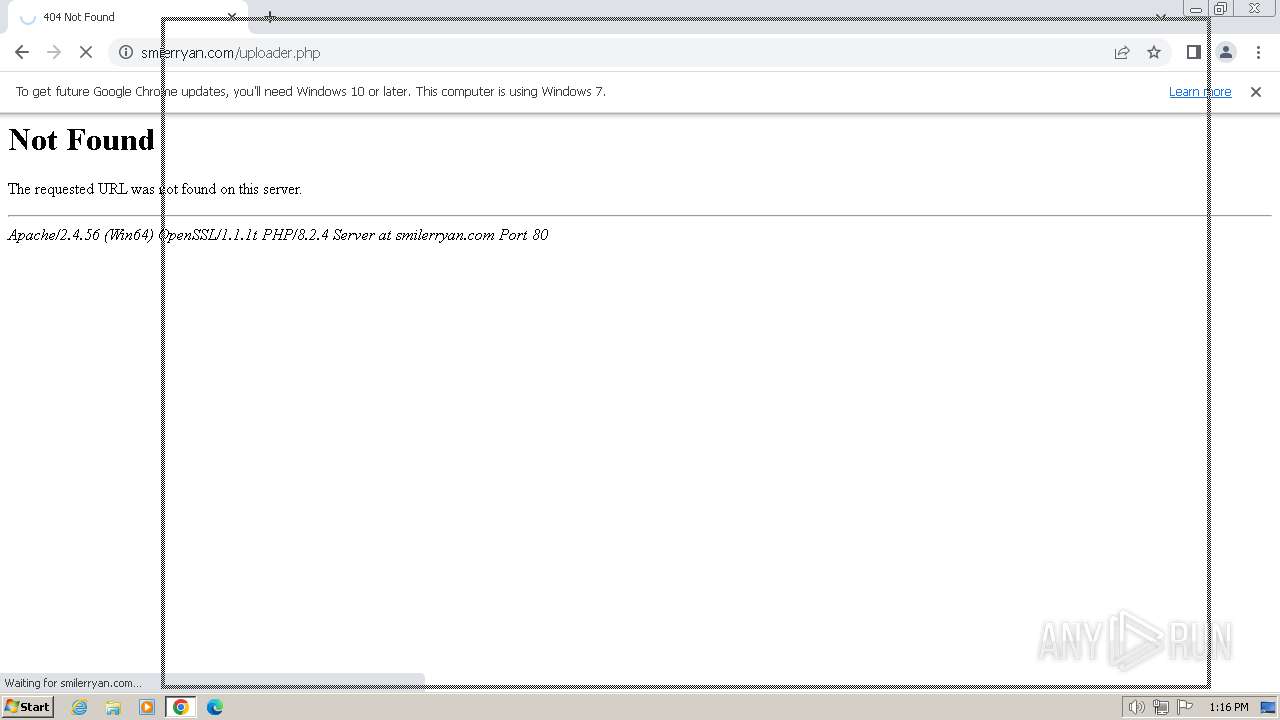
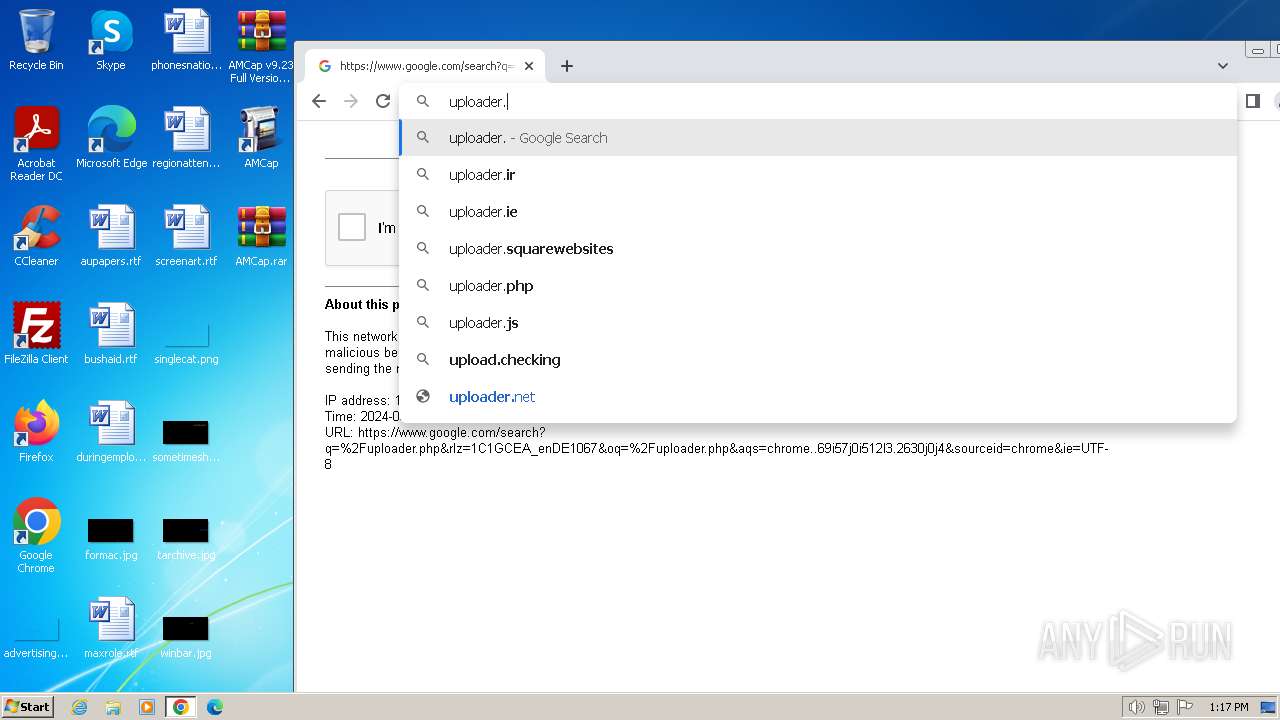
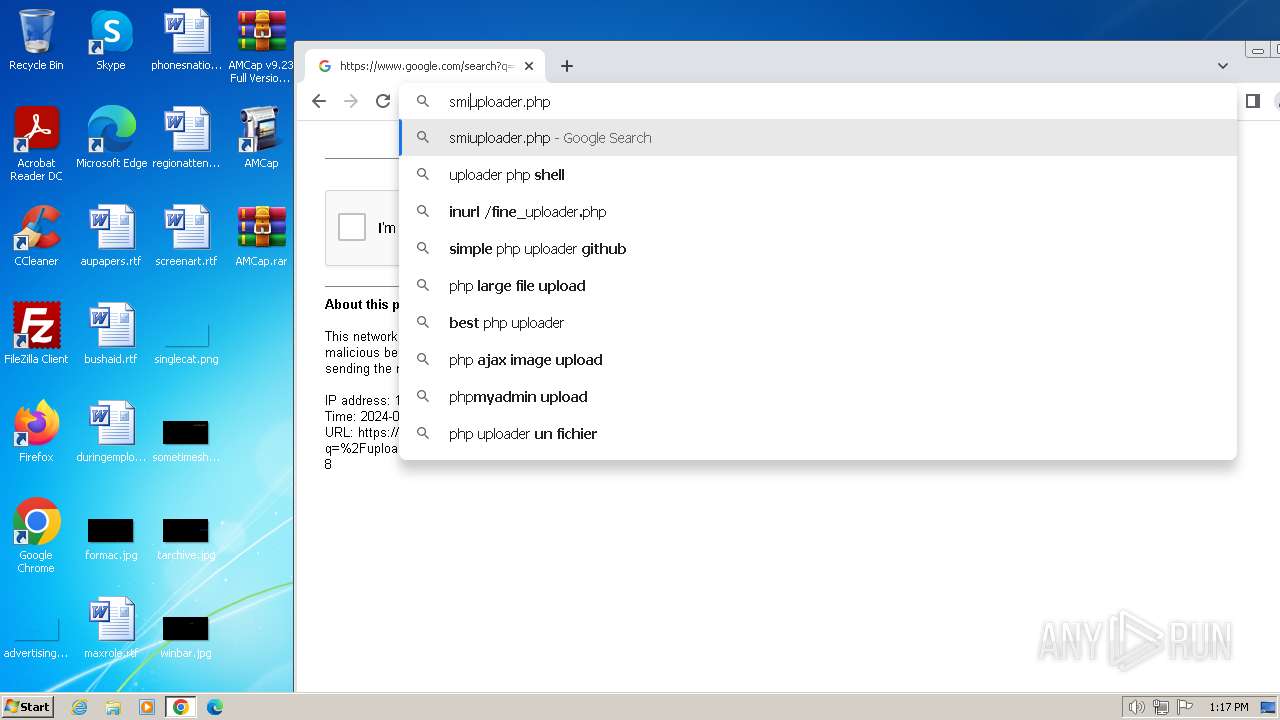
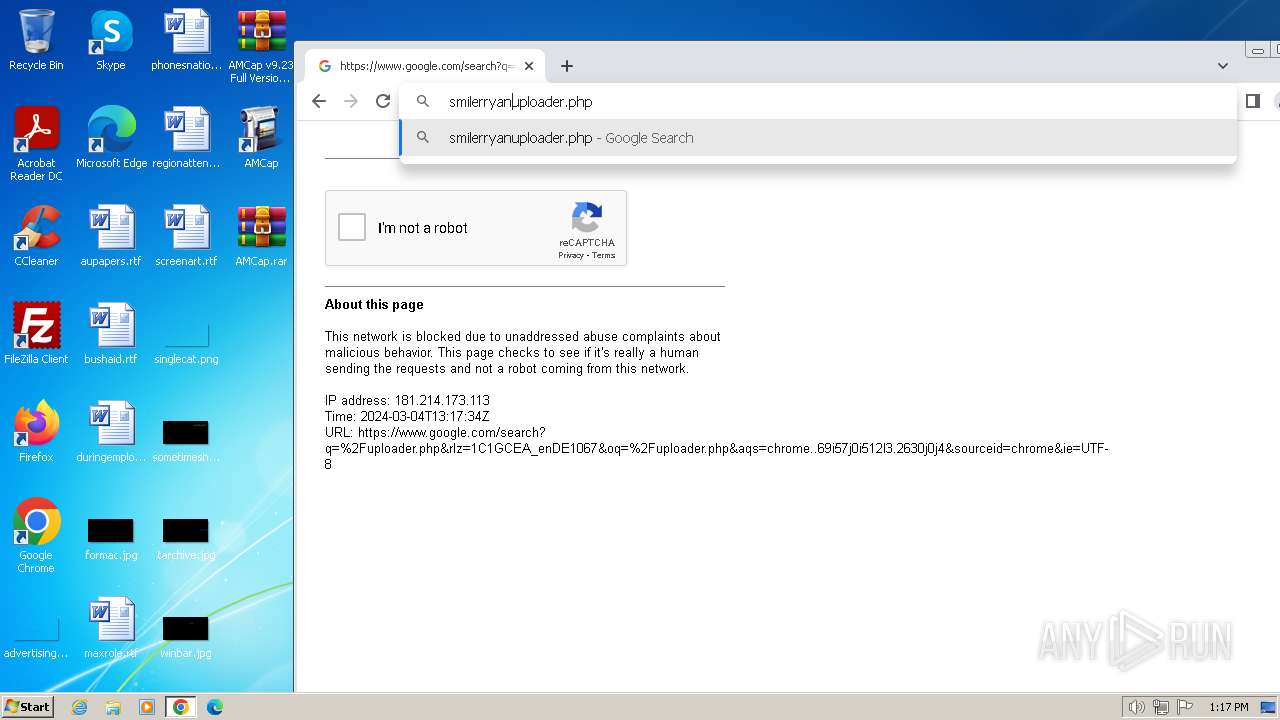
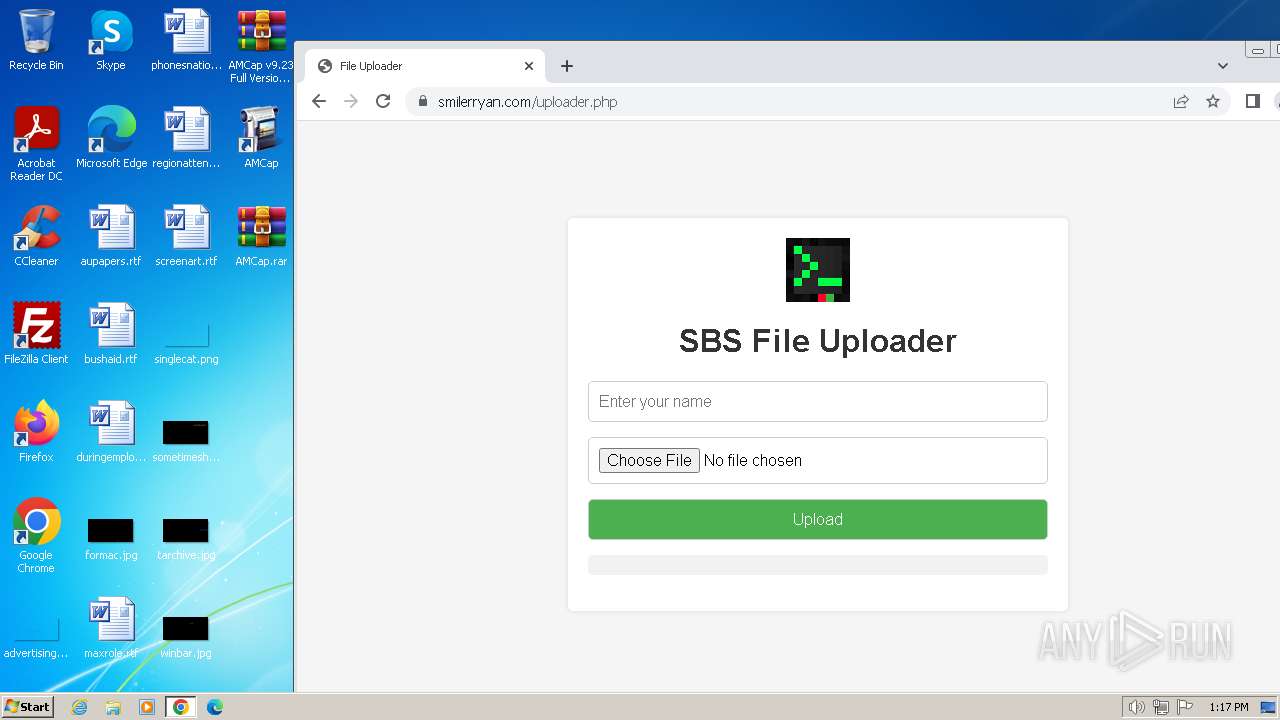
| File name: | AMCap v9.23 Full Version.rar |
| Full analysis: | https://app.any.run/tasks/a48c2fb3-28a9-43c6-858f-976838aa1e53 |
| Verdict: | Malicious activity |
| Analysis date: | March 04, 2024, 13:12:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | D20FD4CEA31FB188678BB04C0565EBA2 |
| SHA1: | A4A8A3071E910D5555DF9BA62CC48C9F208062DA |
| SHA256: | 7D8F222495E087F4EE999DA971A4D353BC8461EC9DE1B12FF7D07CBBAA330311 |
| SSDEEP: | 196608:oPvfohb0nyhBkb0laroCantEaFTPiPxrq:o3foJ0nZb0lAoCatEQTPiJrq |
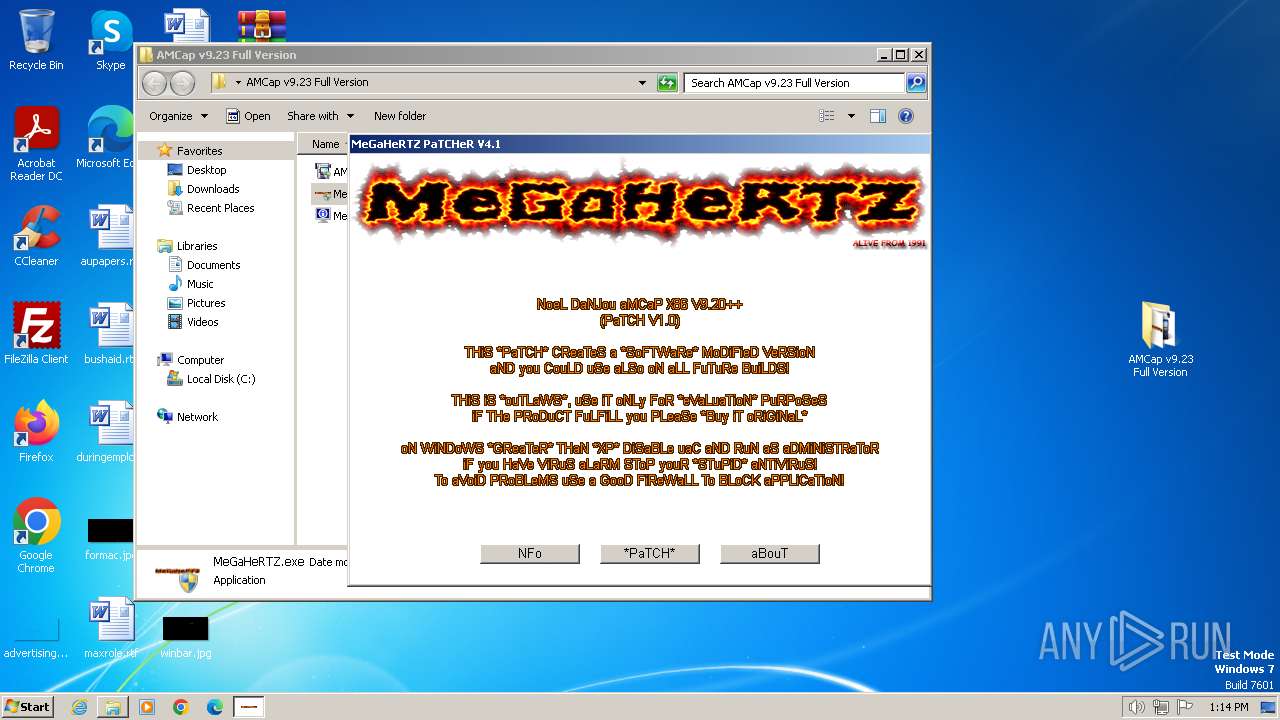
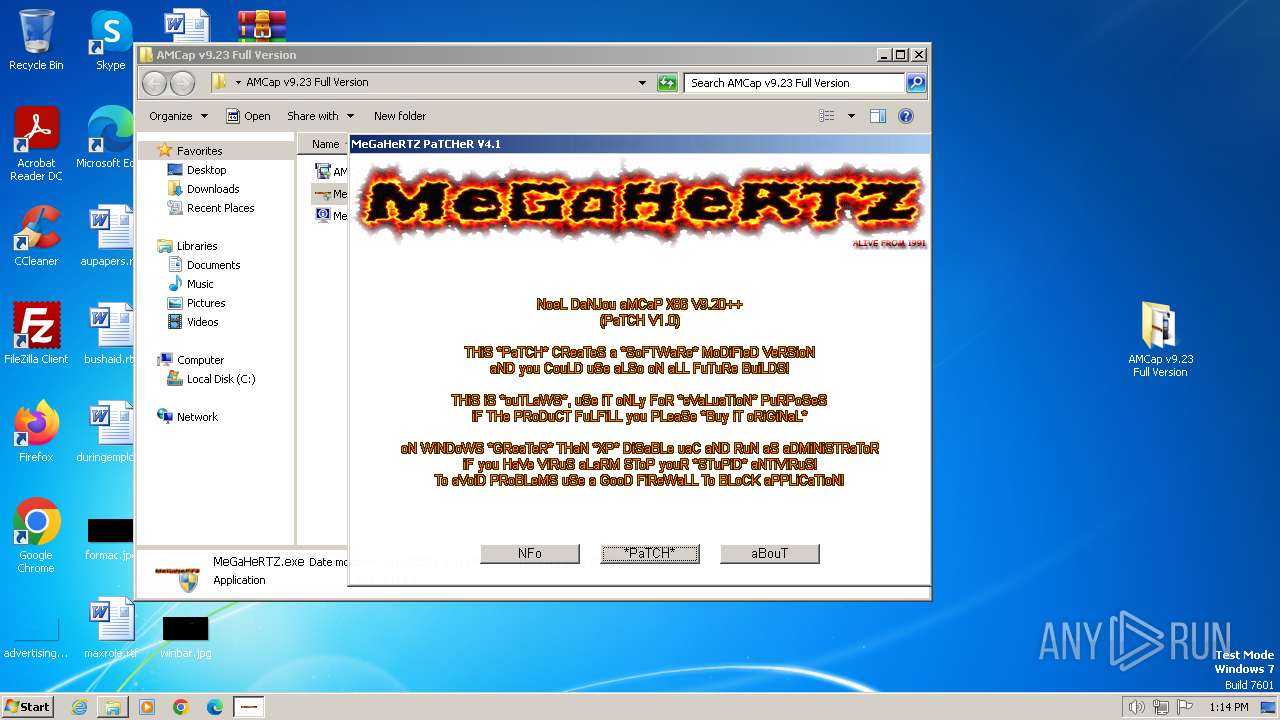
MALICIOUS
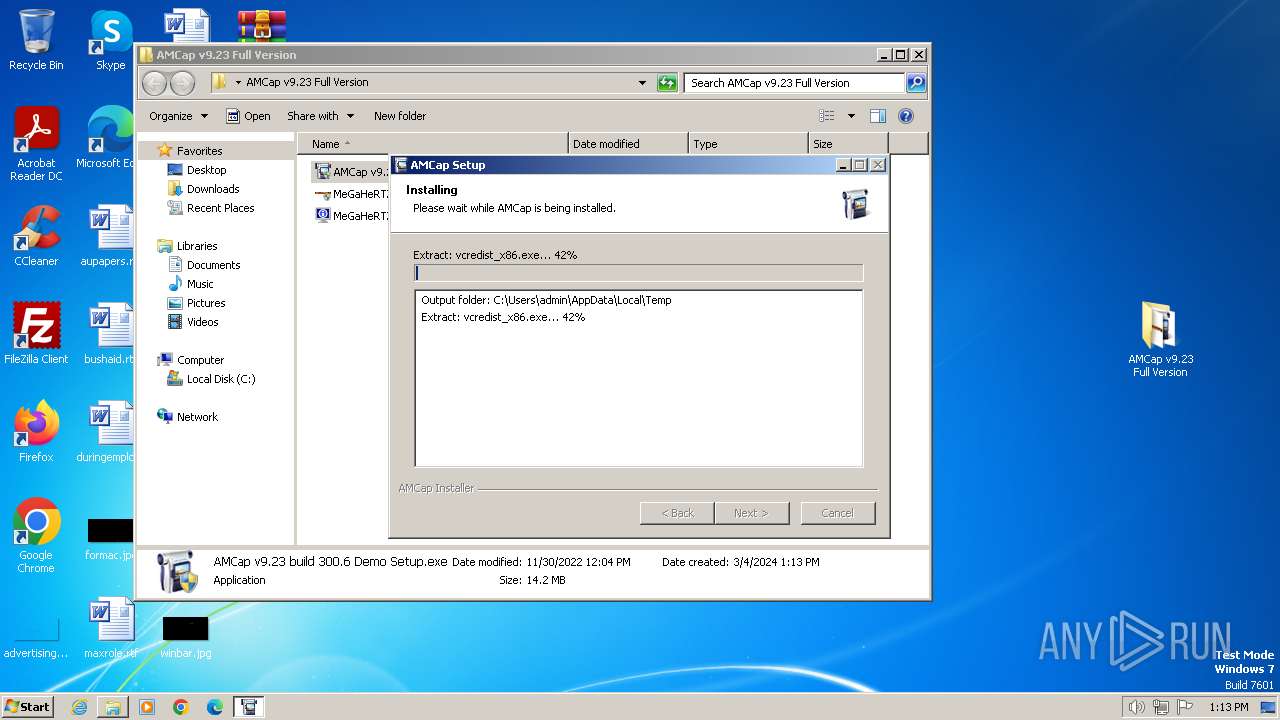
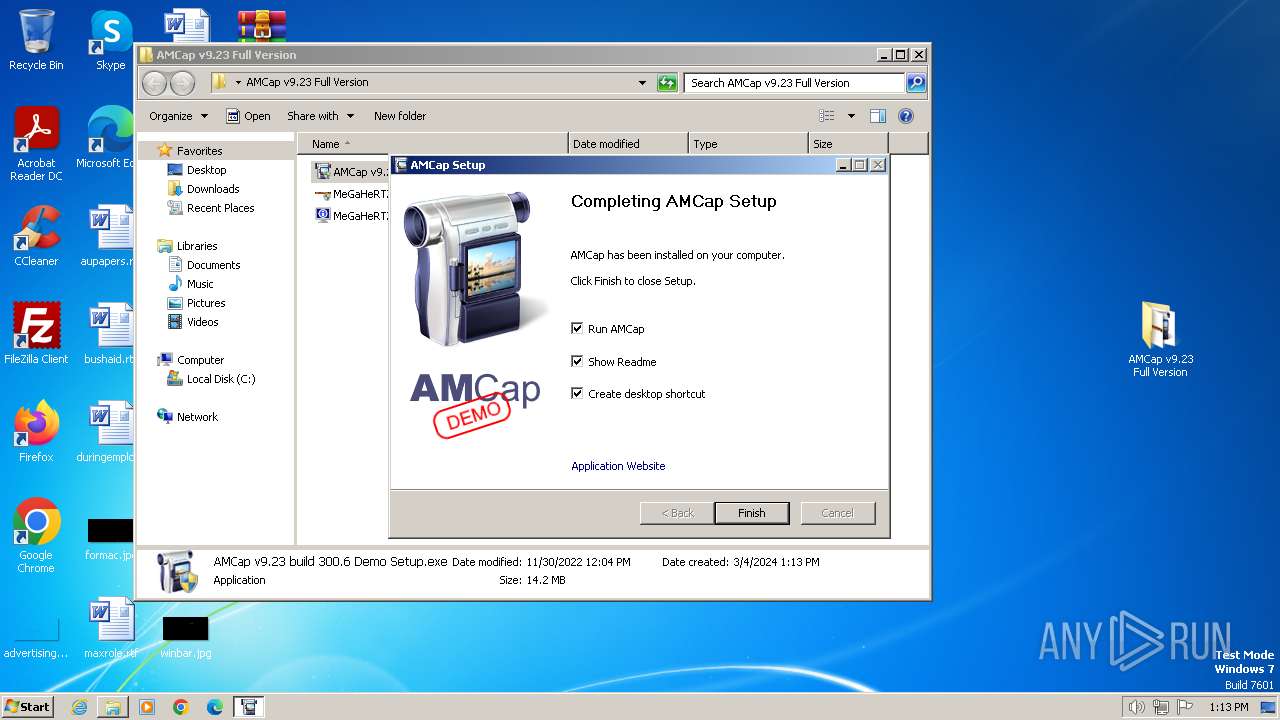
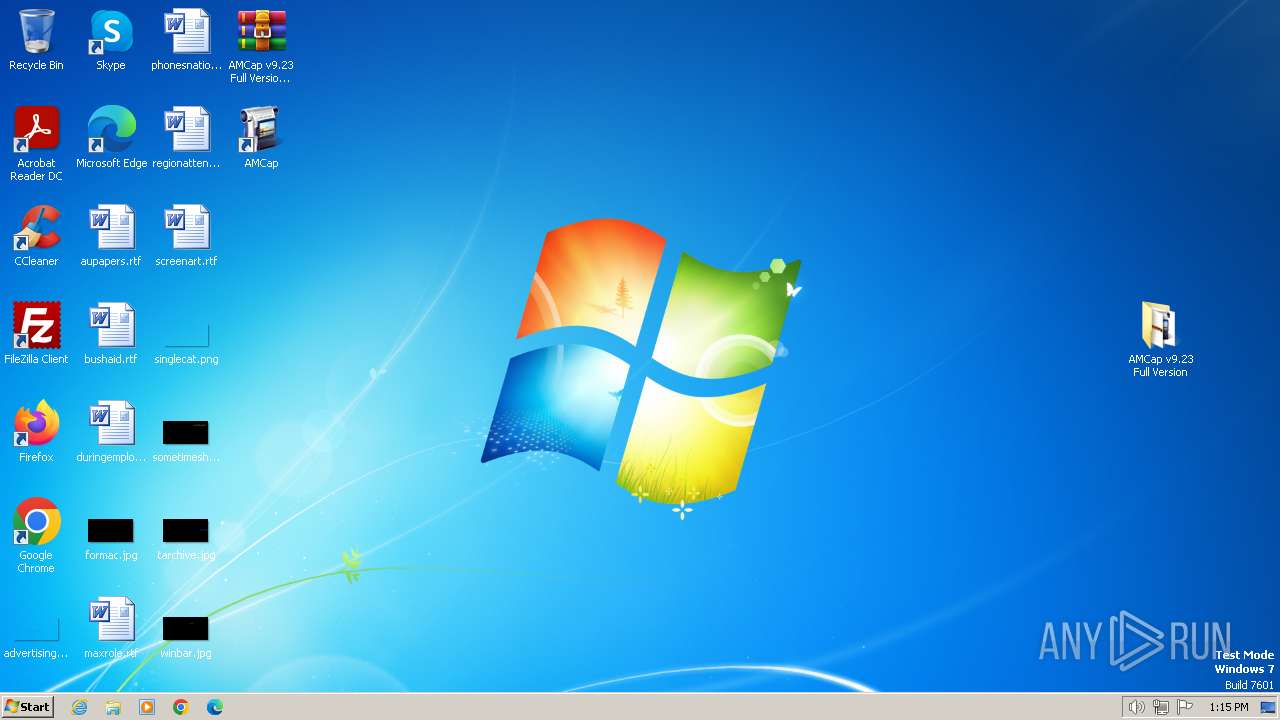
Drops the executable file immediately after the start
- WinRAR.exe (PID: 4052)
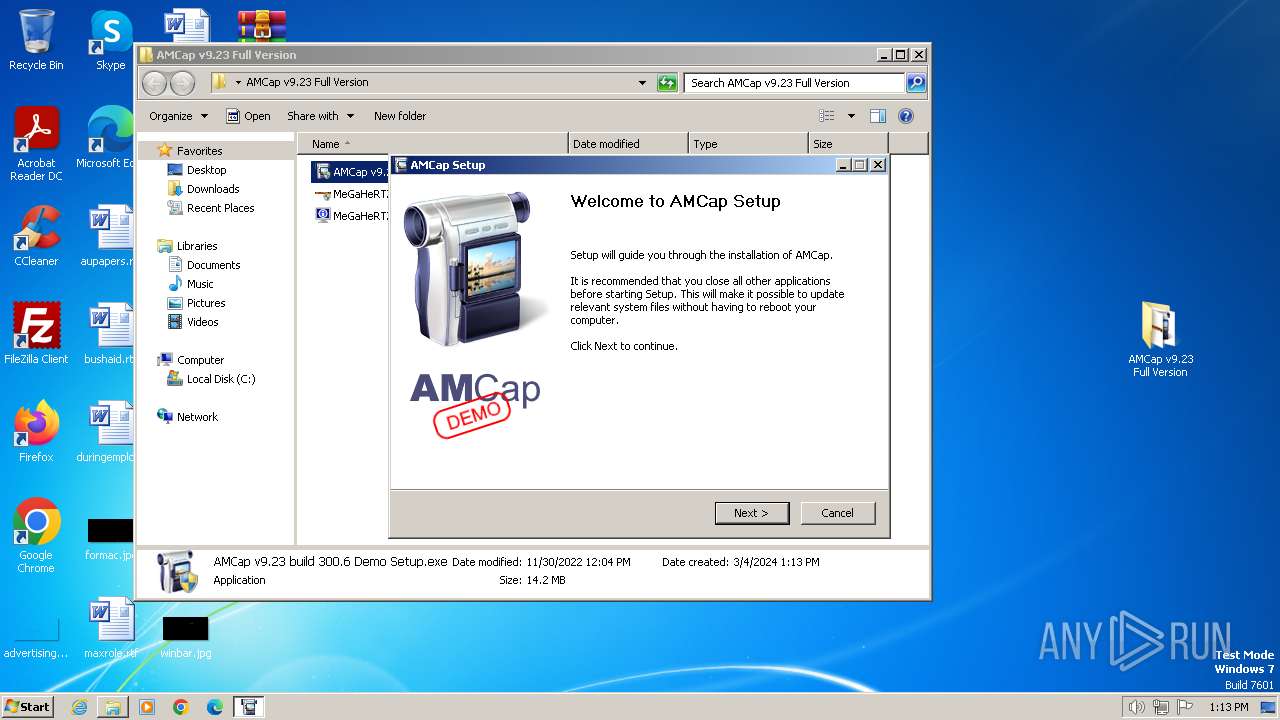
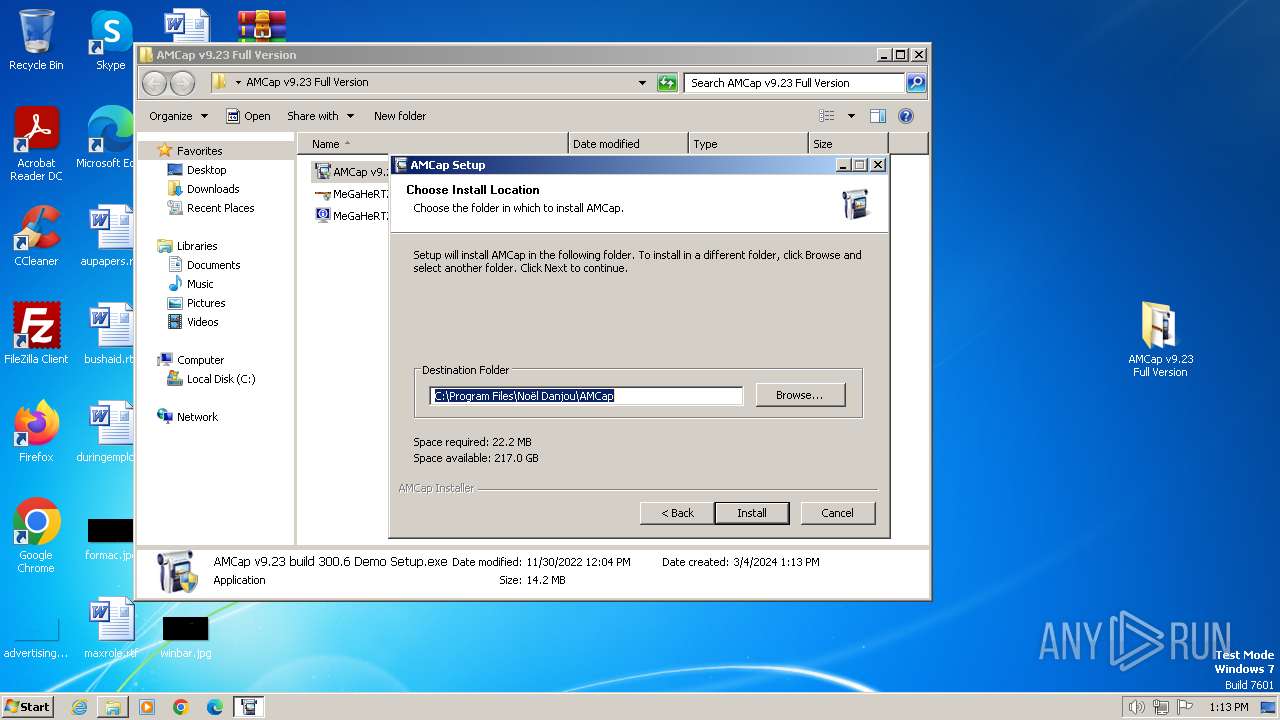
- AMCap v9.23 build 300.6 Demo Setup.exe (PID: 2232)
- vcredist_x86.exe (PID: 2408)
SUSPICIOUS
Executable content was dropped or overwritten
- AMCap v9.23 build 300.6 Demo Setup.exe (PID: 2232)
- vcredist_x86.exe (PID: 2408)
The process creates files with name similar to system file names
- AMCap v9.23 build 300.6 Demo Setup.exe (PID: 2232)
Process drops legitimate windows executable
- AMCap v9.23 build 300.6 Demo Setup.exe (PID: 2232)
- vcredist_x86.exe (PID: 2408)
Malware-specific behavior (creating "System.dll" in Temp)
- AMCap v9.23 build 300.6 Demo Setup.exe (PID: 2232)
Starts a Microsoft application from unusual location
- vcredist_x86.exe (PID: 3996)
- vcredist_x86.exe (PID: 2408)
Application launched itself
- vcredist_x86.exe (PID: 3996)
- WinRAR.exe (PID: 3396)
Searches for installed software
- vcredist_x86.exe (PID: 2408)
- AMCap v9.23 build 300.6 Demo Setup.exe (PID: 2232)
Executes as Windows Service
- VSSVC.exe (PID: 2792)
Creates/Modifies COM task schedule object
- AMCap v9.23 build 300.6 Demo Setup.exe (PID: 2232)
Creates a software uninstall entry
- AMCap v9.23 build 300.6 Demo Setup.exe (PID: 2232)
Reads the Internet Settings
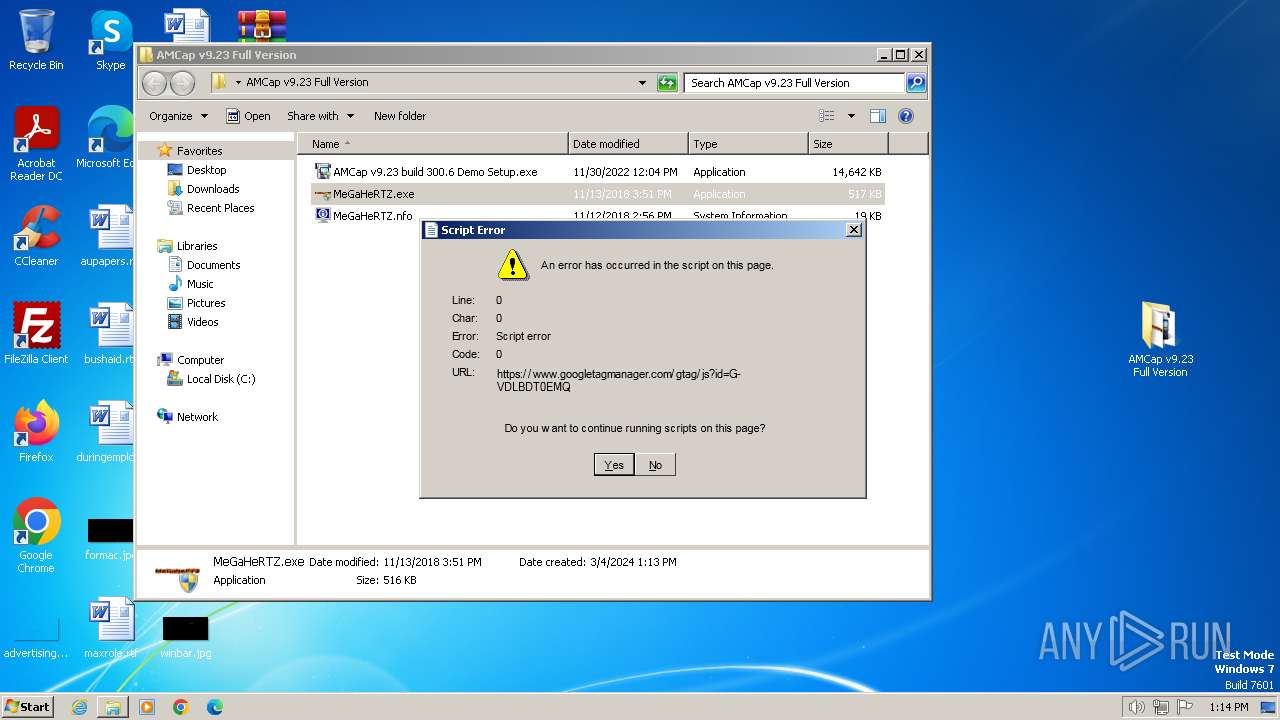
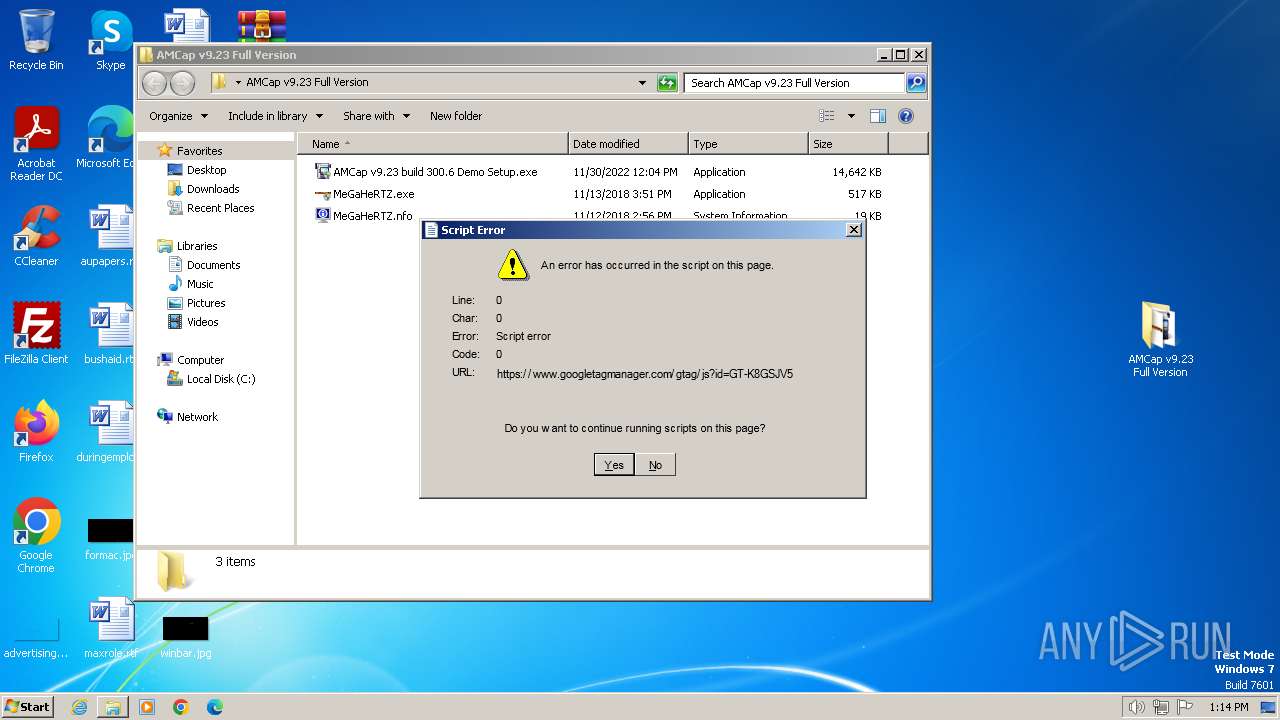
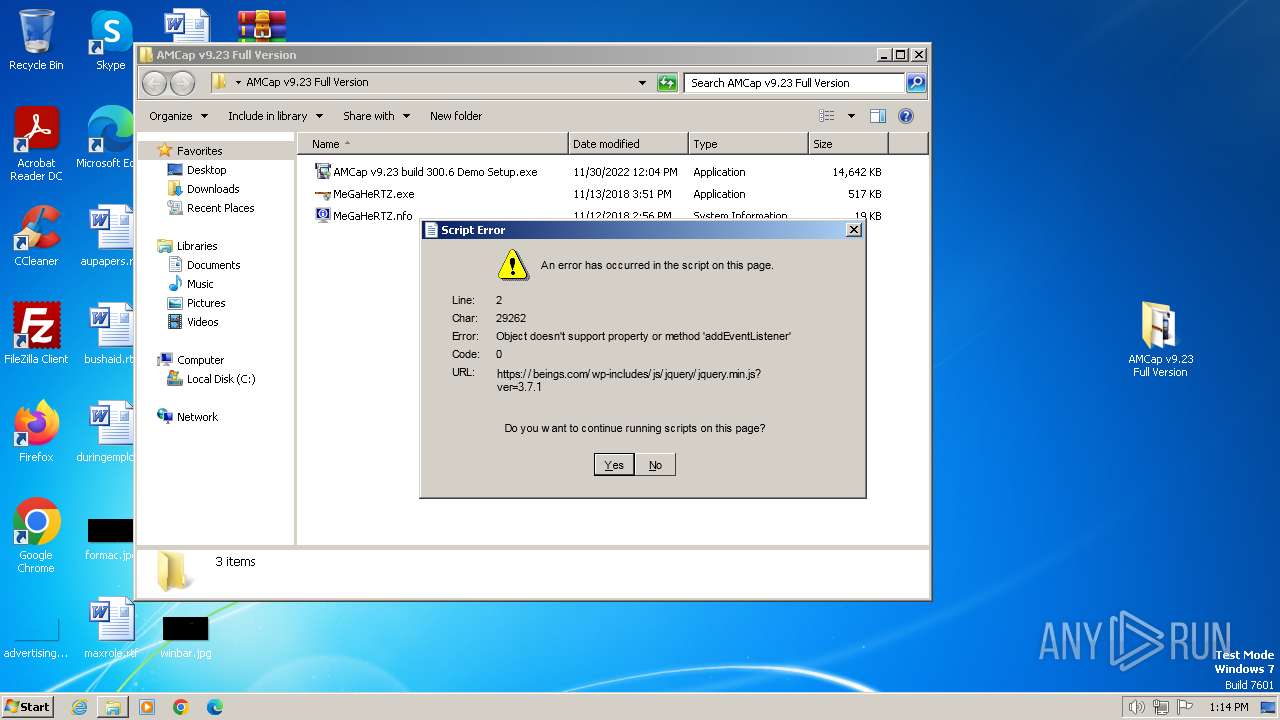
- MeGaHeRTZ.exe (PID: 2976)
- amcap.exe (PID: 2592)
Reads Microsoft Outlook installation path
- MeGaHeRTZ.exe (PID: 2976)
- amcap.exe (PID: 2592)
Reads security settings of Internet Explorer
- MeGaHeRTZ.exe (PID: 2976)
- amcap.exe (PID: 2592)
- WinRAR.exe (PID: 3396)
Checks Windows Trust Settings
- MeGaHeRTZ.exe (PID: 2976)
Reads settings of System Certificates
- MeGaHeRTZ.exe (PID: 2976)
Adds/modifies Windows certificates
- MeGaHeRTZ.exe (PID: 2976)
Reads Internet Explorer settings
- MeGaHeRTZ.exe (PID: 2976)
- amcap.exe (PID: 2592)
INFO
Checks supported languages
- AMCap v9.23 build 300.6 Demo Setup.exe (PID: 2232)
- vcredist_x86.exe (PID: 3996)
- vcredist_x86.exe (PID: 2408)
- amcap.exe (PID: 2728)
- amcap.exe (PID: 2592)
- MeGaHeRTZ.exe (PID: 2976)
Reads the computer name
- AMCap v9.23 build 300.6 Demo Setup.exe (PID: 2232)
- vcredist_x86.exe (PID: 2408)
- vcredist_x86.exe (PID: 3996)
- amcap.exe (PID: 2728)
- MeGaHeRTZ.exe (PID: 2976)
- amcap.exe (PID: 2592)
Manual execution by a user
- AMCap v9.23 build 300.6 Demo Setup.exe (PID: 3304)
- AMCap v9.23 build 300.6 Demo Setup.exe (PID: 2232)
- msedge.exe (PID: 1728)
- amcap.exe (PID: 2592)
- MeGaHeRTZ.exe (PID: 3668)
- MeGaHeRTZ.exe (PID: 2976)
- WinRAR.exe (PID: 3396)
- chrome.exe (PID: 3768)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4052)
Create files in a temporary directory
- AMCap v9.23 build 300.6 Demo Setup.exe (PID: 2232)
- vcredist_x86.exe (PID: 2408)
- MeGaHeRTZ.exe (PID: 2976)
- amcap.exe (PID: 2592)
Reads the machine GUID from the registry
- AMCap v9.23 build 300.6 Demo Setup.exe (PID: 2232)
- amcap.exe (PID: 2728)
- MeGaHeRTZ.exe (PID: 2976)
- amcap.exe (PID: 2592)
Creates files in the program directory
- AMCap v9.23 build 300.6 Demo Setup.exe (PID: 2232)
- WinRAR.exe (PID: 3148)
Application launched itself
- msedge.exe (PID: 2260)
- msedge.exe (PID: 1728)
- chrome.exe (PID: 3768)
Checks proxy server information
- MeGaHeRTZ.exe (PID: 2976)
- amcap.exe (PID: 2592)
Process checks whether UAC notifications are on
- MeGaHeRTZ.exe (PID: 2976)
Creates files or folders in the user directory
- MeGaHeRTZ.exe (PID: 2976)
- amcap.exe (PID: 2728)
- amcap.exe (PID: 2592)
Reads the software policy settings
- MeGaHeRTZ.exe (PID: 2976)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
104
Monitored processes
48
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 668 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6a648b38,0x6a648b48,0x6a648b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 848 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3124 --field-trial-handle=1152,i,3429856264645971496,6644769175058411504,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 920 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1412 --field-trial-handle=1148,i,3375176476739027884,297027236399192885,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 924 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1428 --field-trial-handle=1152,i,3429856264645971496,6644769175058411504,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1020 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=1616 --field-trial-handle=1152,i,3429856264645971496,6644769175058411504,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1216 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1216 --field-trial-handle=1148,i,3375176476739027884,297027236399192885,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1728 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --flag-switches-begin --flag-switches-end --do-not-de-elevate "C:\Program Files\Noël Danjou\AMCap\readme.htm" | C:\Program Files\Microsoft\Edge\Application\msedge.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1992 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=2236 --field-trial-handle=1152,i,3429856264645971496,6644769175058411504,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2072 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1496 --field-trial-handle=1152,i,3429856264645971496,6644769175058411504,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
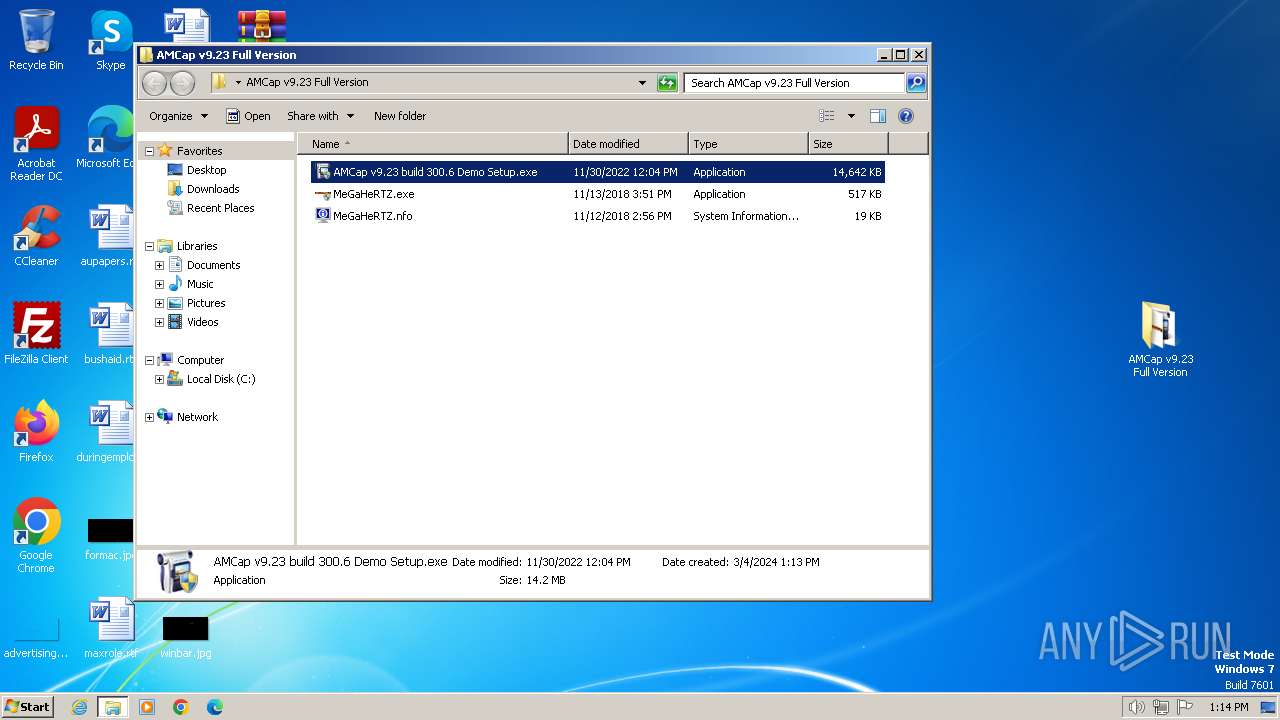
| 2232 | "C:\Users\admin\Desktop\AMCap v9.23 Full Version\AMCap v9.23 build 300.6 Demo Setup.exe" | C:\Users\admin\Desktop\AMCap v9.23 Full Version\AMCap v9.23 build 300.6 Demo Setup.exe | explorer.exe | ||||||||||||
User: admin Company: Noël Danjou Integrity Level: HIGH Description: AMCap Installer Exit code: 0 Version: 9.23.94.1 Modules
| |||||||||||||||
Total events
29 301
Read events
28 823
Write events
442
Delete events
36
Modification events
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\AMCap v9.23 Full Version.rar | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4052) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
18
Suspicious files
73
Text files
166
Unknown types
57
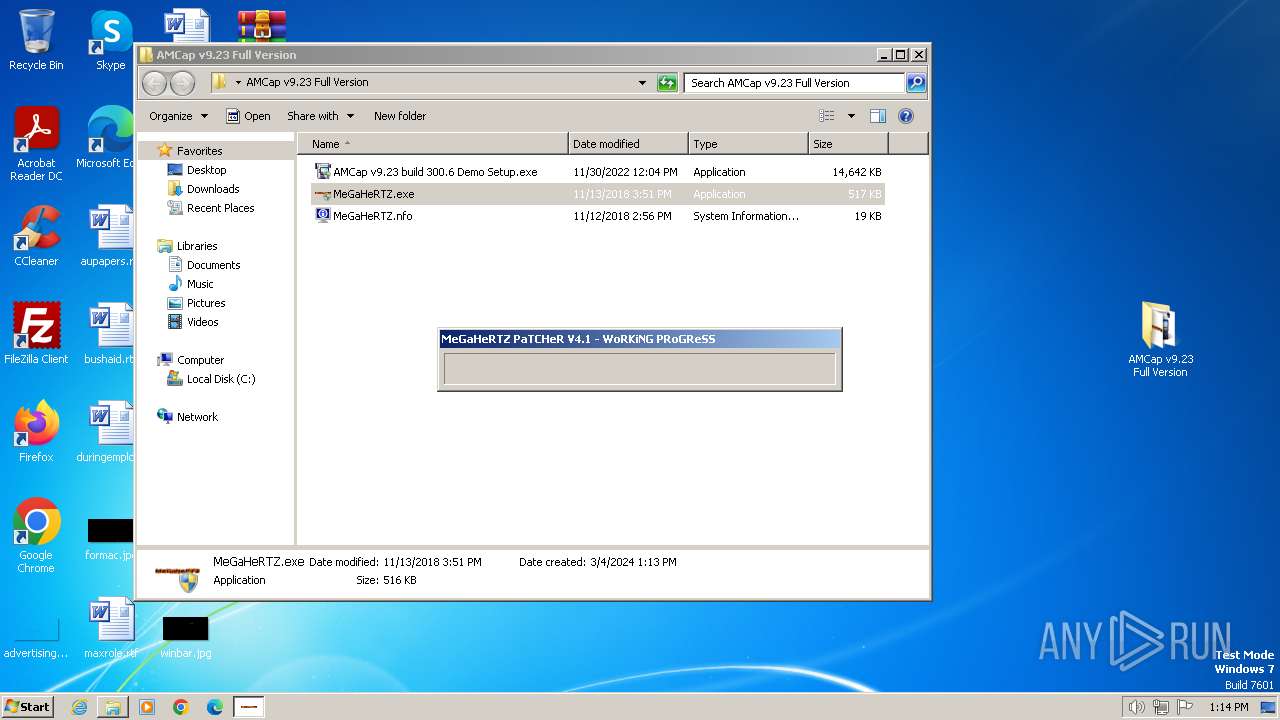
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2232 | AMCap v9.23 build 300.6 Demo Setup.exe | C:\Users\admin\AppData\Local\Temp\nsw372A.tmp\System.dll | executable | |
MD5:9625D5B1754BC4FF29281D415D27A0FD | SHA256:C2F405D7402F815D0C3FADD9A50F0BBBB1BAB9AA38FE347823478A2587299448 | |||
| 2232 | AMCap v9.23 build 300.6 Demo Setup.exe | C:\Users\admin\AppData\Local\Temp\nsw372A.tmp\LockedList.dll | executable | |
MD5:CA238F4ABE4B70A4A85A9D2FBF5CA3D9 | SHA256:6D0F6E9B326A4D3E249D728FC471681281855013094F337296F5B89D78303943 | |||
| 2408 | vcredist_x86.exe | C:\Users\admin\AppData\Local\Temp\{404c9c27-8377-4fd1-b607-7ca635db4e49}\.ba1\wixstdba.dll | executable | |
MD5:A973CFA4951D519E032F42DC98A198B0 | SHA256:25EE85C14C9BE619B4F0BF783963ACE1DC0AF0E802014728C2A2CA8DA213D31D | |||
| 2232 | AMCap v9.23 build 300.6 Demo Setup.exe | C:\Users\admin\AppData\Local\Temp\nsw372A.tmp\modern-wizard.bmp | image | |
MD5:2BE7498FCDAB7F7AAD95AA818E41DA2D | SHA256:13010BBBB7B4832E645CDB1CD2E837FB32339AE3E899E6B7653E80A8664BD889 | |||
| 2232 | AMCap v9.23 build 300.6 Demo Setup.exe | C:\Users\admin\AppData\Local\Temp\nsw372A.tmp\nsDialogs.dll | executable | |
MD5:D2E45DD852A659E11897DF573832F381 | SHA256:86C8EE210E6611383A634DCB8C60455063DDAE3D7ADCCBEACF3ADF7BF2A46676 | |||
| 2232 | AMCap v9.23 build 300.6 Demo Setup.exe | C:\Users\admin\AppData\Local\Temp\vcredist_x86.exe | executable | |
MD5:8DAC0E58FDCD659C9DE1715AED297CF2 | SHA256:2DA11E22A276BE85970EAED255DAF3D92AF84E94142EC04252326A882E57303E | |||
| 2408 | vcredist_x86.exe | C:\Users\admin\AppData\Local\Temp\{404c9c27-8377-4fd1-b607-7ca635db4e49}\.ba1\1028\license.rtf | text | |
MD5:CBEFFF78F4E80A5693DA65050A8A6E32 | SHA256:CADA21198E68FAB0B914BCEB92EFE3475487596115D9C0C7C75CAAC0301004B2 | |||
| 2408 | vcredist_x86.exe | C:\Users\admin\AppData\Local\Temp\{404c9c27-8377-4fd1-b607-7ca635db4e49}\.ba1\1029\license.rtf | text | |
MD5:1D7D728D9B7CF5FFC10130880C6130CB | SHA256:BF62AD166798EF53BC303F650B6BB06085E258650CA2823F2B0D1D4F1E3836BD | |||
| 2408 | vcredist_x86.exe | C:\Users\admin\AppData\Local\Temp\{404c9c27-8377-4fd1-b607-7ca635db4e49}\.ba1\1036\license.rtf | text | |
MD5:1DA77B492870266E67626CE000528425 | SHA256:84CFC67F98D7553AB6AF43E9B8D89138A9F46D0FD9291A441D7FE73F5C1A9DC6 | |||
| 2408 | vcredist_x86.exe | C:\Users\admin\AppData\Local\Temp\{404c9c27-8377-4fd1-b607-7ca635db4e49}\.ba1\1041\license.rtf | text | |
MD5:BC180530B16725A57DEA69DB5E5EC41E | SHA256:0C9AC52FDE4EDBF79033345C19274A47860D53EF61359E3FE71B3F44FED44E7C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
48
DNS requests
49
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2976 | MeGaHeRTZ.exe | GET | 304 | 95.101.11.9:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b920279959cebafb | unknown | — | — | unknown |
2976 | MeGaHeRTZ.exe | GET | 301 | 3.96.23.237:80 | http://beam.to/mhzstatistics | unknown | html | 79 b | unknown |
2976 | MeGaHeRTZ.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
2976 | MeGaHeRTZ.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
— | — | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
— | — | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEH1ZfRmkcbmIEJt1GKpWSOU%3D | unknown | binary | 471 b | unknown |
2976 | MeGaHeRTZ.exe | GET | 200 | 108.138.2.107:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | unknown | binary | 2.02 Kb | unknown |
2976 | MeGaHeRTZ.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootca3.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRkNawYMzz%2BjKSfYbTyFR0AXuhs6QQUq7bb1waeN6wwhgeRcMecxBmxeMACEwdzEnA9eVH9TrLXPKuCavuqCA0%3D | unknown | binary | 822 b | unknown |
2976 | MeGaHeRTZ.exe | GET | 200 | 95.101.11.9:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?ba800a0a96be5fde | unknown | compressed | 67.5 Kb | unknown |
— | — | GET | 200 | 18.245.39.64:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEowz8xPdLX1MG5U07e%2BCsM%3D | unknown | binary | 1.49 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
920 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1728 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
920 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1728 | msedge.exe | 224.0.0.251:5353 | — | — | — | unknown |
920 | msedge.exe | 23.222.16.80:443 | www.bing.com | Akamai International B.V. | US | unknown |
920 | msedge.exe | 152.199.21.175:443 | msedgeextensions.sf.tlu.dl.delivery.mp.microsoft.com | EDGECAST | DE | whitelisted |
2976 | MeGaHeRTZ.exe | 3.96.23.237:80 | beam.to | AMAZON-02 | CA | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
msedgeextensions.sf.tlu.dl.delivery.mp.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
beam.to |
| whitelisted |
beings.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
static.hotjar.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .to TLD |