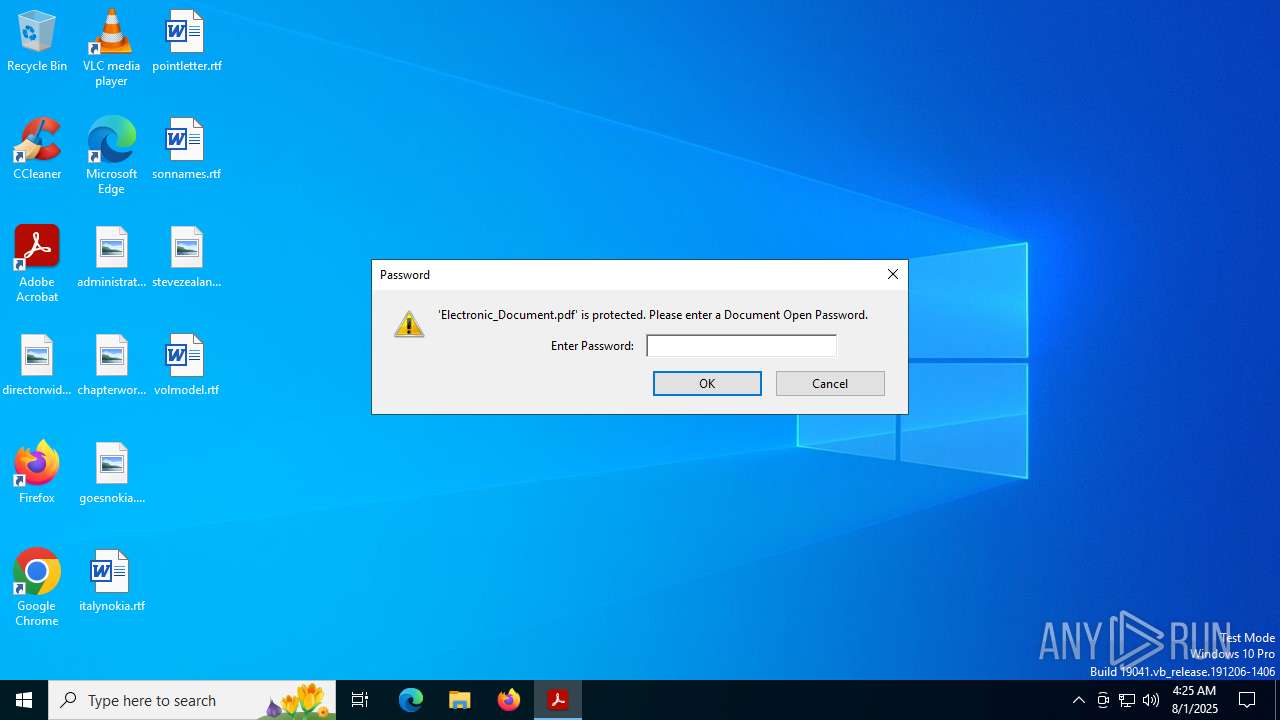
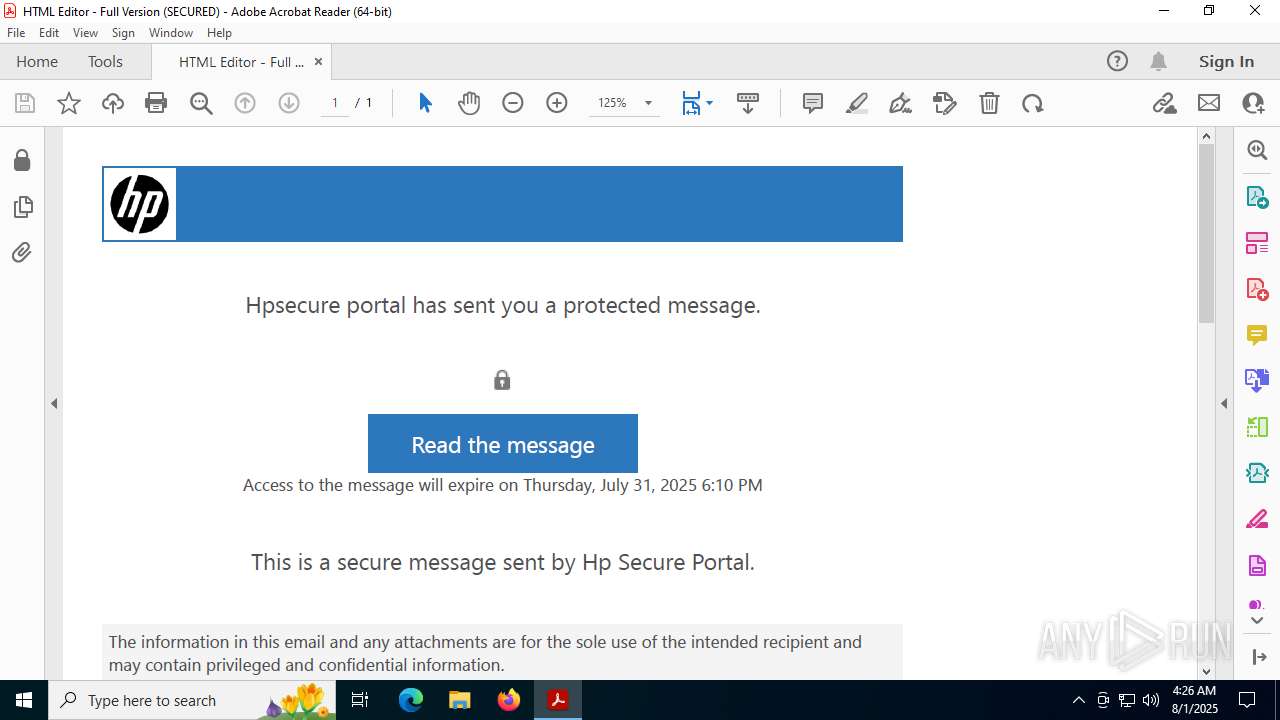
| File name: | Electronic_Document.pdf |
| Full analysis: | https://app.any.run/tasks/b8e30f81-9673-41ab-9f38-737f04901245 |
| Verdict: | Malicious activity |
| Analysis date: | August 01, 2025, 04:25:19 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.7, 1 page(s) |
| MD5: | 7F38468845DDAE6A525133006C1AB4EA |
| SHA1: | 67A9D15B354B1BC3C839427B50A7CB8653000338 |
| SHA256: | 7D7CA98F0DC3A9AD22A34A8131FD4F67EBCD2AC0111FC51074B5A58A3922AAD9 |
| SSDEEP: | 1536:j5ZN9znYn5j1ZnqPB7ClMvWHMSuHpCR8evyA/0LdHh:j5ZrjY5j1ZnqPzUyHpCR8evQB |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process executes via Task Scheduler
- updater.exe (PID: 7596)
Application launched itself
- updater.exe (PID: 7596)
There is functionality for taking screenshot (YARA)
- AcroCEF.exe (PID: 1128)
INFO
Checks supported languages
- updater.exe (PID: 7596)
- updater.exe (PID: 7624)
- identity_helper.exe (PID: 3852)
Reads the computer name
- updater.exe (PID: 7596)
- identity_helper.exe (PID: 3852)
Application launched itself
- Acrobat.exe (PID: 4724)
- AcroCEF.exe (PID: 3768)
- msedge.exe (PID: 2428)
Process checks whether UAC notifications are on
- updater.exe (PID: 7596)
Reads Environment values
- identity_helper.exe (PID: 3852)
Checks proxy server information
- slui.exe (PID: 7908)
Reads the software policy settings
- slui.exe (PID: 7908)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| PDFVersion: | 1.7 |
|---|---|
| Linearized: | No |
| Encryption: | Standard V5.6 (256-bit) |
| UserAccess: | Print, Modify, Copy, Annotate, Fill forms, Extract, Assemble, Print high-res |
Total processes
170
Monitored processes
33
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 432 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=5904,i,10775589139464459950,13557551559838590176,262144 --variations-seed-version --mojo-platform-channel-handle=7036 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 868 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --always-read-main-dll --field-trial-handle=4344,i,10775589139464459950,13557551559838590176,262144 --variations-seed-version --mojo-platform-channel-handle=4360 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1128 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --type=gpu-process --log-severity=disable --user-agent-product="ReaderServices/23.1.20093 Chrome/105.0.0.0" --lang=en-US --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --use-gl=disabled --log-file="C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\debug.log" --mojo-platform-channel-handle=1828 --field-trial-handle=1612,i,8599852742678958524,4325167441909997033,131072 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,WinUseBrowserSpellChecker /prefetch:2 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | AcroCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 1880 | "C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6656,i,10775589139464459950,13557551559838590176,262144 --variations-seed-version --mojo-platform-channel-handle=6704 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 133.0.3065.92 Modules
| |||||||||||||||
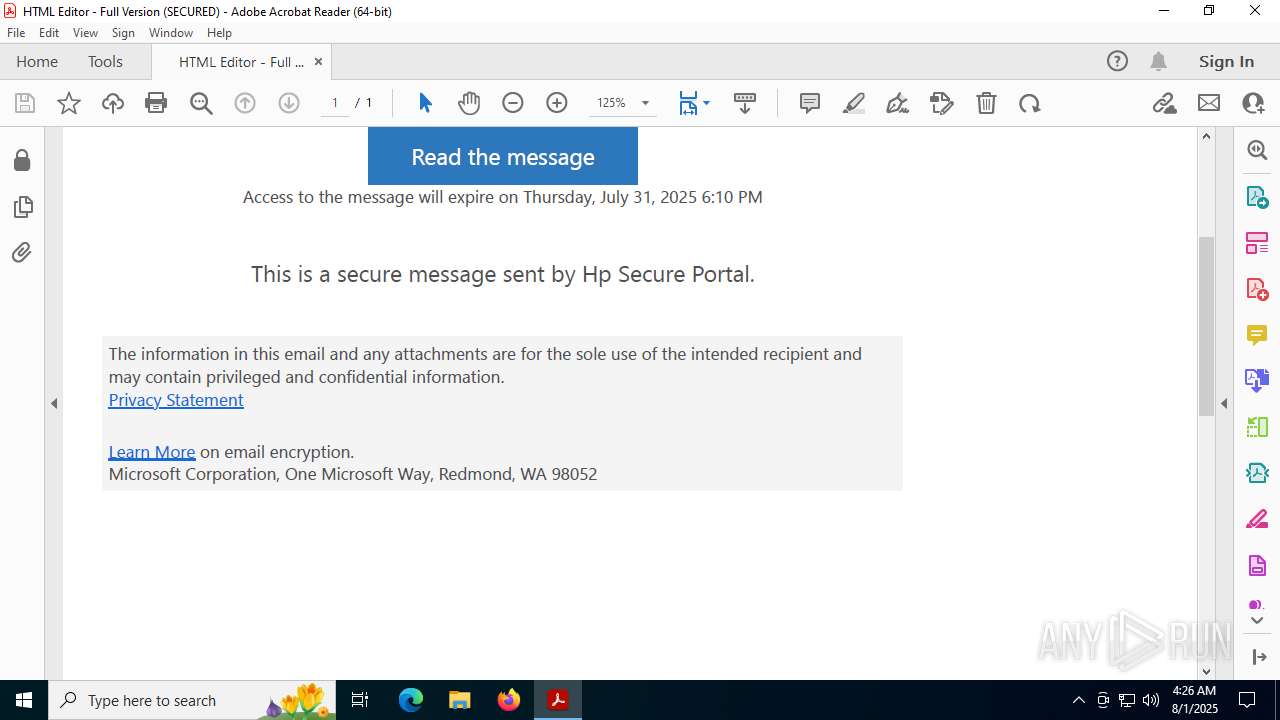
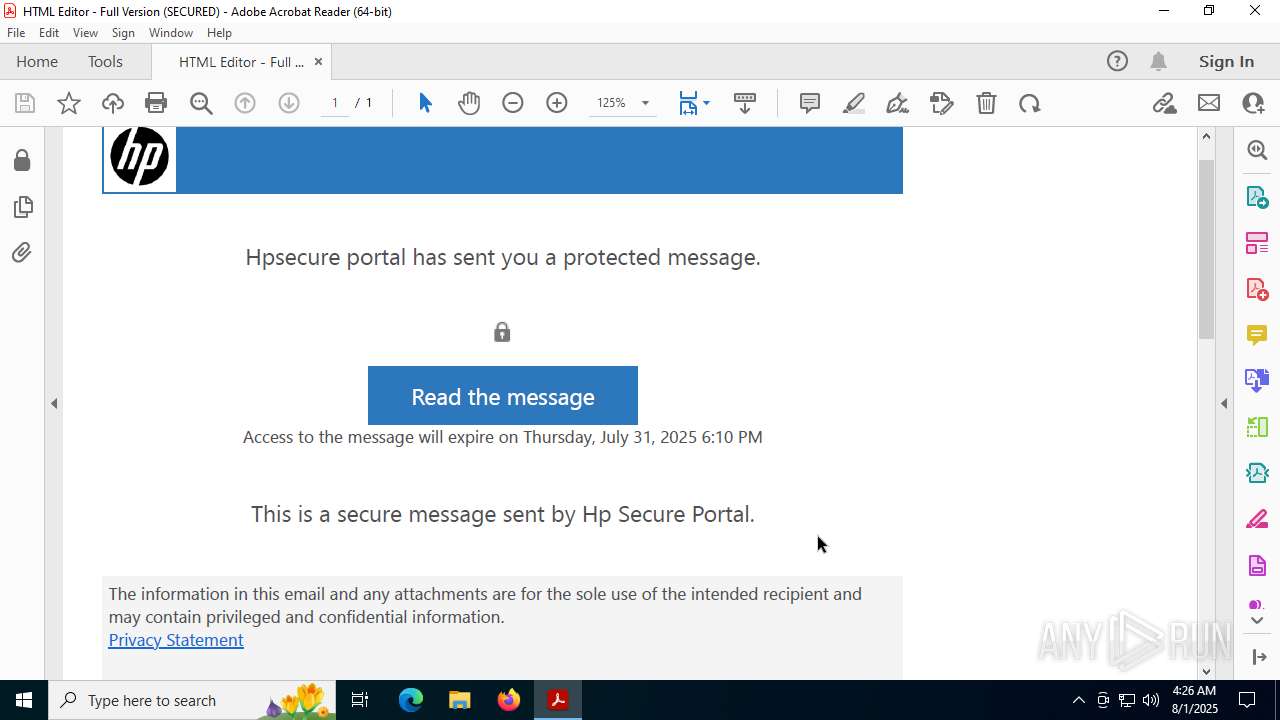
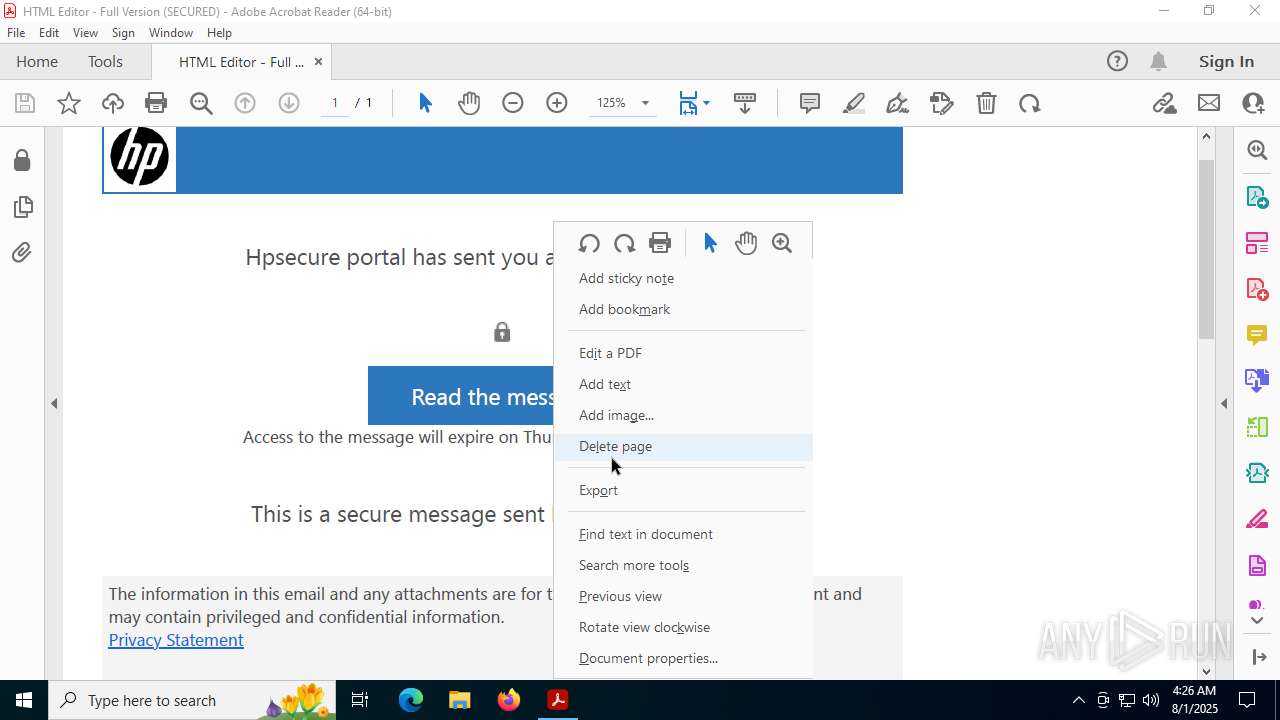
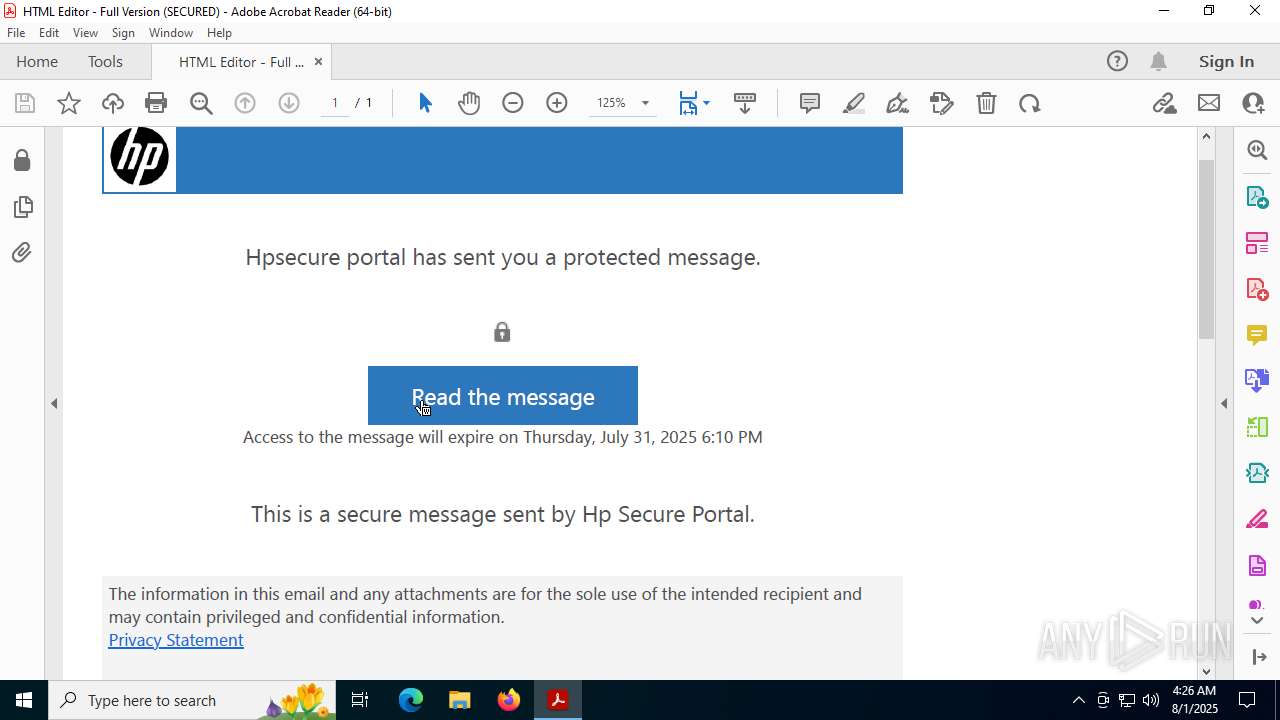
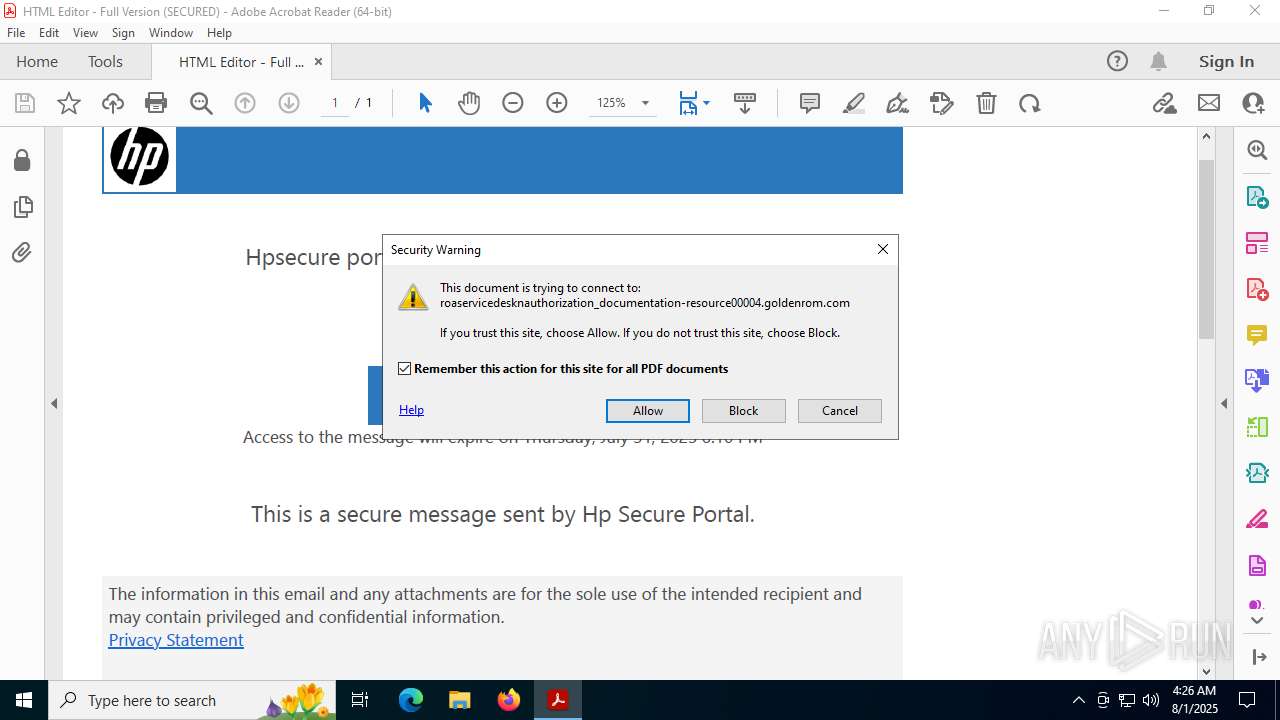
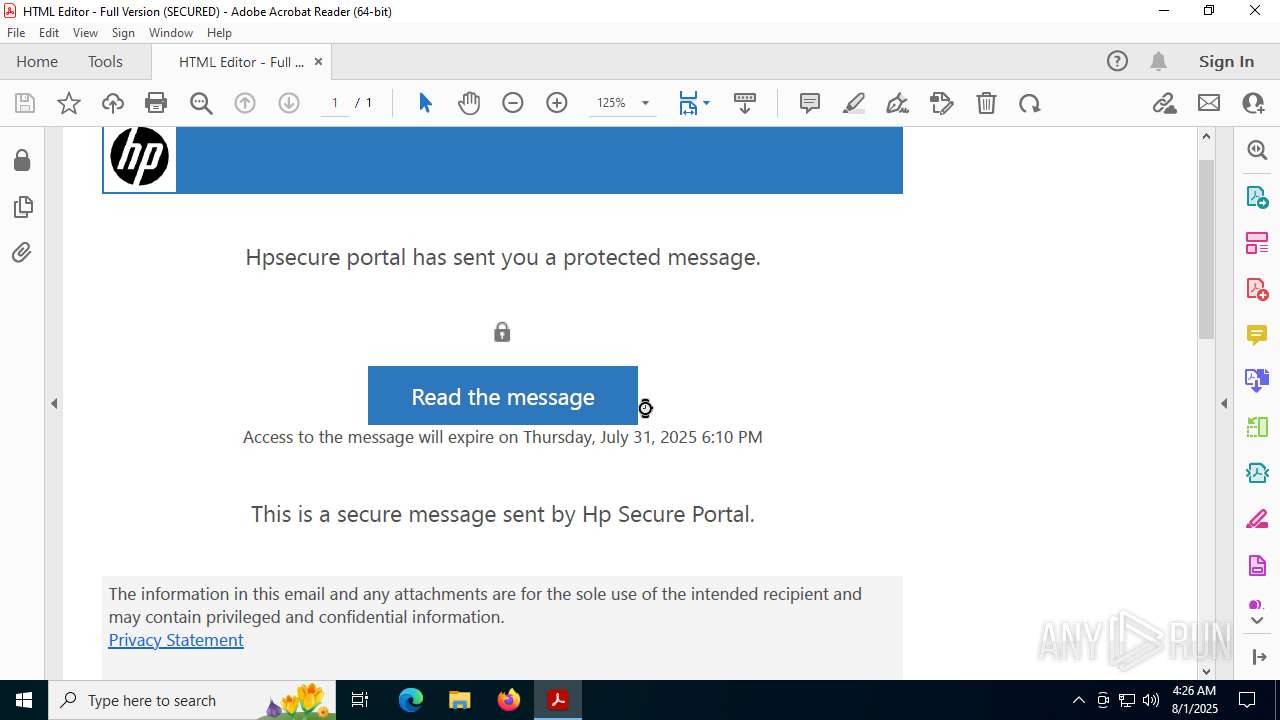
| 2428 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument https://roaservicedesknauthorization_documentation-resource00004.goldenrom.com/?utm=cm9sYW5kLmNhcnJlam9AaHAuY29t | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | Acrobat.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2716 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5856,i,10775589139464459950,13557551559838590176,262144 --variations-seed-version --mojo-platform-channel-handle=5940 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3100 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_xpay_wallet.mojom.EdgeXPayWalletService --lang=en-US --service-sandbox-type=utility --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=5460,i,10775589139464459950,13557551559838590176,262144 --variations-seed-version --mojo-platform-channel-handle=5292 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3768 | "C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat DC\Acrobat\acrocef_1\AcroCEF.exe | — | Acrobat.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe AcroCEF Version: 23.1.20093.0 Modules
| |||||||||||||||
| 3852 | "C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6656,i,10775589139464459950,13557551559838590176,262144 --variations-seed-version --mojo-platform-channel-handle=6704 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 3880 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=6980,i,10775589139464459950,13557551559838590176,262144 --variations-seed-version --mojo-platform-channel-handle=6576 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
21 508
Read events
21 386
Write events
120
Delete events
2
Modification events
| (PID) Process: | (4724) Acrobat.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Mappings\S-1-15-2-2034283098-2252572593-1072577386-2659511007-3245387615-27016815-3920691934 |
| Operation: | write | Name: | DisplayName |
Value: Adobe Acrobat Reader Protected Mode | |||
| (PID) Process: | (6820) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (6820) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Collab\cDocumentCenter |
| Operation: | write | Name: | bAlwaysUseServer |
Value: 0 | |||
| (PID) Process: | (6820) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Collab\cDocumentCenter |
| Operation: | write | Name: | bAlwaysUseServerFD |
Value: 0 | |||
| (PID) Process: | (6820) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Collab\cDocumentCenter |
| Operation: | write | Name: | bDefault |
Value: 1 | |||
| (PID) Process: | (6820) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Collab\cDocumentCenter |
| Operation: | write | Name: | bDefaultFD |
Value: 1 | |||
| (PID) Process: | (6820) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Collab\cDocumentCenter |
| Operation: | write | Name: | tDistMethod |
Value: UPLOAD | |||
| (PID) Process: | (6820) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Collab\cDocumentCenter\cSettings |
| Operation: | write | Name: | tcSetting |
Value: https://api.share.acrobat.com | |||
| (PID) Process: | (6820) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Collab\cDocumentCenter |
| Operation: | write | Name: | tUI |
Value: Adobe online services (Recommended) | |||
| (PID) Process: | (6820) Acrobat.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Adobe\Adobe Acrobat\DC\Collab\cDocumentCenter |
| Operation: | write | Name: | tURL |
Value: urn://ns.adobe.com/Collaboration/SharedReview/Acrobat.com | |||
Executable files
0
Suspicious files
338
Text files
65
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4724 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeSysFnt23.lst | ps | |
MD5:366B140BAFC863B7E366AA1E51604759 | SHA256:CBC8B288DBD2C72432081CF33CEF431572A94C7FB89DBCD59973B99E3871814E | |||
| 6820 | Acrobat.exe | C:\Users\admin\AppData\Local\Temp\acrobat_sbx\acroNGLLog.txt | text | |
MD5:07239CE5BF2628596535EC21643143E2 | SHA256:13356B6D4B451EA2231F4B4770D935426FB88E7FDCA0A174C6180AB2E338ED2E | |||
| 6820 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\SOPHIA.json | binary | |
MD5:837C1211E392A24D64C670DC10E8DA1B | SHA256:8013AC030684B86D754BBFBAB8A9CEC20CAA4DD9C03022715FF353DC10E14031 | |||
| 6820 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeFnt23.lst.6820 | ps | |
MD5:366B140BAFC863B7E366AA1E51604759 | SHA256:CBC8B288DBD2C72432081CF33CEF431572A94C7FB89DBCD59973B99E3871814E | |||
| 6820 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SOPHIA\Acrobat\Files\TESTING | mp3 | |
MD5:DC84B0D741E5BEAE8070013ADDCC8C28 | SHA256:81FF65EFC4487853BDB4625559E69AB44F19E0F5EFBD6D5B2AF5E3AB267C8E06 | |||
| 3768 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\4a0e94571d979b3c_0 | binary | |
MD5:B50517FCE8B39F726DEAAD567A5588EE | SHA256:D4870203F566025CCEAB8C91802FFFD0327784F09B0DF1E9FFDE914614C4C38D | |||
| 6820 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SharedDataEvents-journal | binary | |
MD5:FE27ED7BDF6034AC44EA8431AEB2CCC5 | SHA256:69BFA097830EDE5930656FEDE5F8A944EE8CDD490381663FE85F2F9EC83E3B14 | |||
| 6820 | Acrobat.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\SharedDataEvents | sqlite | |
MD5:03CF11C62BA29795591805B22EF45D49 | SHA256:D39B4A4219D68A3E87D413455E8D5FBA552C908C9633B3176C17A9A96F9D08C9 | |||
| 6820 | Acrobat.exe | C:\Users\admin\AppData\Local\Temp\acrobat_sbx\NGL\NGLClient_AcrobatReader123.1.20093.6 2025-08-01 04-25-31-341.log | text | |
MD5:460C6041966002D8384A18C895A65EB0 | SHA256:C83EC6E8FB3EC62481289C033238C1D9B08DB8076EAAD304099FD7A7F594F1B9 | |||
| 3768 | AcroCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Session Storage\LOG.old | text | |
MD5:EB1590F2607E1CE46DBF6A521F772EA0 | SHA256:4355D9A8A115BA4E41178B456A8A5578846EB1F7EC9509249C2405F758F31731 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
54
DNS requests
54
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7316 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:aKZgLcKOcnFuqH1acp10kuREe1fUQIsP5EqTP-CQGn4&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4724 | Acrobat.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | unknown | — | — | whitelisted |
4032 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7744 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 72.246.169.163:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
7744 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1632 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5716 | AcroCEF.exe | 23.35.236.137:443 | geo2.adobe.com | AKAMAI-AS | DE | whitelisted |
5716 | AcroCEF.exe | 50.16.47.176:443 | p13n.adobe.io | AMAZON-AES | US | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |