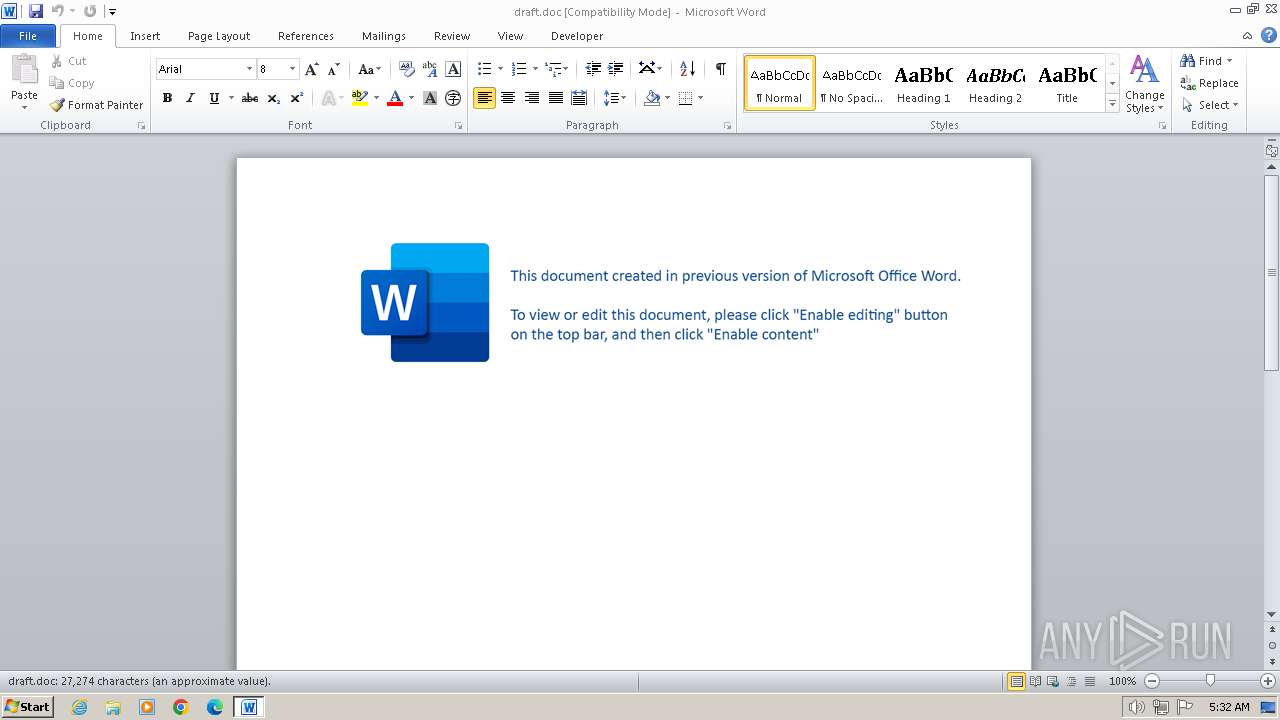
| File name: | draft.doc |
| Full analysis: | https://app.any.run/tasks/bdd030fe-f754-4193-886b-779f83f787dd |
| Verdict: | Malicious activity |
| Analysis date: | January 30, 2024, 05:32:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Author: admin, Template: Normal, Last Saved By: admin, Revision Number: 9, Name of Creating Application: Microsoft Office Word, Total Editing Time: 30:00, Create Time/Date: Wed Sep 1 14:59:00 2021, Last Saved Time/Date: Wed Nov 2 15:16:00 2022, Number of Pages: 1, Number of Words: 4936, Number of Characters: 28141, Security: 0 |
| MD5: | F79F5606111733C8A0793D75C6C29F9B |
| SHA1: | EEFC8DCBDF4C4D2B434A43331E4EF40EB570068A |
| SHA256: | 7D59D3E513588E2DEE9F841FEC1EB5E6EA35CA6CC549F7635DCB0841D7870829 |
| SSDEEP: | 3072:j4+AH+hXlPnopRLht+cYDyfeD6SYwe/lItucKzp+Fnb9+CsBw+ysaI6pZOCIC2gk:xvIiGY4X |
MALICIOUS
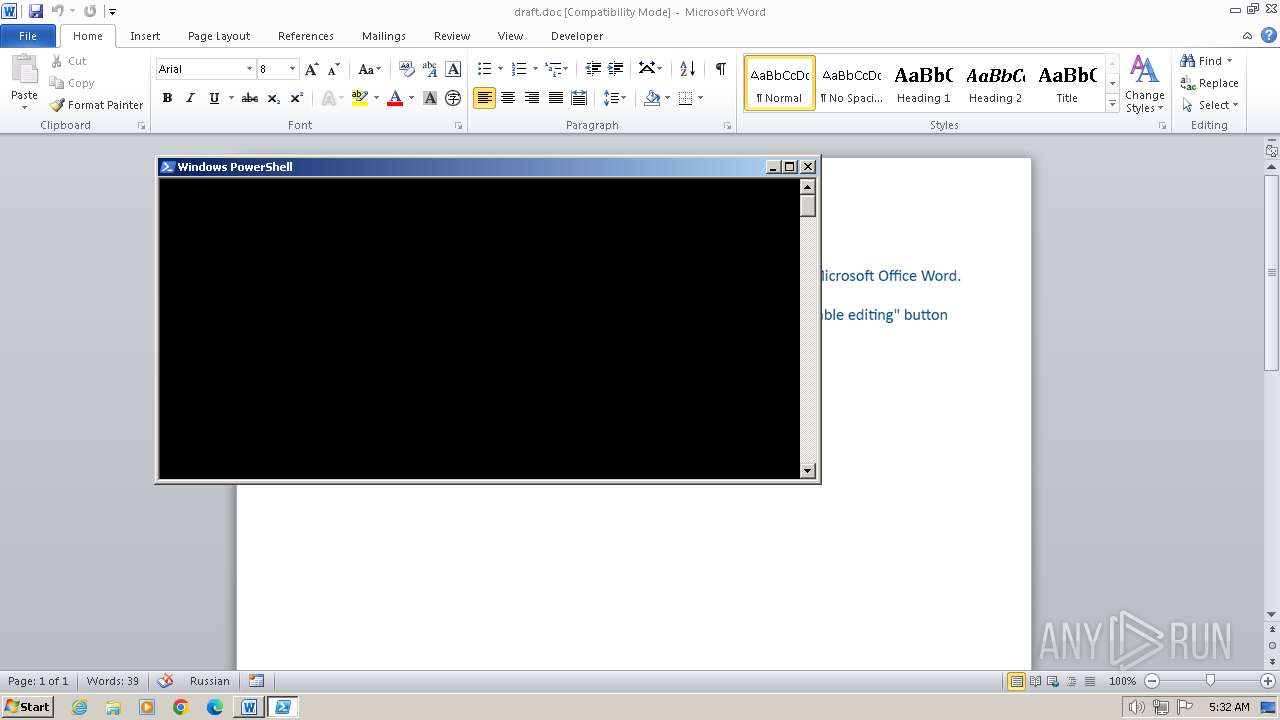
Unusual execution from MS Office
- WINWORD.EXE (PID: 752)
SUSPICIOUS
Runs shell command (SCRIPT)
- WINWORD.EXE (PID: 752)
Reads the Internet Settings
- mshta.exe (PID: 392)
- powershell.exe (PID: 3356)
Likely accesses (executes) a file from the Public directory
- powershell.exe (PID: 3356)
Starts POWERSHELL.EXE for commands execution
- mshta.exe (PID: 392)
The process executes Powershell scripts
- mshta.exe (PID: 392)
Connects to unusual port
- powershell.exe (PID: 3356)
The Powershell connects to the Internet
- powershell.exe (PID: 3356)
Unusual connection from system programs
- powershell.exe (PID: 3356)
INFO
Checks proxy server information
- mshta.exe (PID: 392)
Reads the Internet Settings
- explorer.exe (PID: 2028)
Reads Internet Explorer settings
- mshta.exe (PID: 392)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | - |
| Subject: | - |
| Author: | admin |
| Keywords: | - |
| Comments: | - |
| Template: | Normal |
| LastModifiedBy: | admin |
| Software: | Microsoft Office Word |
| CreateDate: | 2021:09:01 13:59:00 |
| ModifyDate: | 2022:11:02 15:16:00 |
| Security: | None |
| CodePage: | Unicode (UTF-8) |
| Category: | - |
| Manager: | - |
| Company: | - |
| Bytes: | 26624 |
| CharCountWithSpaces: | 33011 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 9 |
| TotalEditTime: | 30 minutes |
| Words: | 4936 |
| Characters: | 28141 |
| Pages: | 1 |
| Paragraphs: | 66 |
| Lines: | 234 |
Total processes
43
Monitored processes
5
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 392 | "C:\Windows\System32\mshta.exe" "C:\Users\admin\AppData\Local\Temp\1.hta" | C:\Windows\System32\mshta.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 752 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\draft.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2028 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2736 | c:\\windows\\explorer 1.hta | C:\Windows\explorer.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3356 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" c:\users\public\winExDir.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | mshta.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
8 569
Read events
8 009
Write events
433
Delete events
127
Modification events
| (PID) Process: | (752) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (752) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (752) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (752) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (752) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (752) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (752) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (752) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (752) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (752) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
0
Suspicious files
17
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 752 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR3889.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 752 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:20CF5513DE060D248F943FDEBA40BDD5 | SHA256:282E2C40D57058036F8E054E5FA8A0296EB90F2EF2B662605C9F5322484665FB | |||
| 392 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BCB67D7ECB470284AF35679F339E879F | binary | |
MD5:39C4BB921467B2A65E923250A307E51A | SHA256:5BE052F7D4C44D6472CFDD22CEF5B17E880AE50F755A861C9AB0EB1420C0A0BE | |||
| 2028 | explorer.exe | C:\Users\admin\AppData\Local\Temp\1.hta | binary | |
MD5:81345739066ECD7059170F1F1C599BCD | SHA256:5BDC59BDE13CFC190ABA532180859B36FC8711E8B7531CF098422339C331ED0F | |||
| 392 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:124AA5132188A670960FE74DE3CC2CA3 | SHA256:BBE0836E9C75D8117EB95A105EF6CA04D2FC4CC2A8E5DC35181FEEE6242E8116 | |||
| 752 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$draft.doc | binary | |
MD5:B324AE4317035EBCF09D644092FD9242 | SHA256:4695AA09C76A76FA09F8AEE3BC92C53A91107B5BAA945F0087019964D3F8CB27 | |||
| 392 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\75CA58072B9926F763A91F0CC2798706_B5D3A17E5BEDD2EDA793611A0A74E1E8 | binary | |
MD5:B9A0E8D523667C7619A0D0974915CF09 | SHA256:34C107FD13BFD307A892977D6B434F4FF37CF0844DB1300630D82C26E5B151EA | |||
| 392 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_B5D3A17E5BEDD2EDA793611A0A74E1E8 | binary | |
MD5:92494F8176949A4415B701EB6540E99B | SHA256:3E4D05544224B4E2468DD5E54889D94DE5BAE4D3BE24ABE20E85185C414070A0 | |||
| 3356 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:42E3956892291F5EE35E1B989213EF05 | SHA256:D4E6947871B5FD00AD32F8707479DD6EC92AB65D8C6D157B1C0C3D99D575E468 | |||
| 392 | mshta.exe | C:\users\public\winExDir.ps1 | text | |
MD5:A2AE66DEF22B7D6A51680A5164AAAFCB | SHA256:BA922A4FCFAABC7B1066284274C8B15C98E409870CD555EC1A5AC890358ADC2B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
12
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
392 | mshta.exe | GET | 304 | 23.32.238.178:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?69ffe22c7f5d1fb1 | unknown | — | — | unknown |
392 | mshta.exe | GET | — | 18.245.39.64:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | unknown | — | — | unknown |
392 | mshta.exe | GET | 200 | 108.138.2.173:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | unknown | binary | 2.02 Kb | unknown |
392 | mshta.exe | GET | 200 | 18.245.31.88:80 | http://crl.rootg2.amazontrust.com/rootg2.crl | unknown | binary | 713 b | unknown |
392 | mshta.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEjgLnWaIozse2b%2BczaaODg8%3D | unknown | binary | 1.37 Kb | unknown |
1080 | svchost.exe | GET | 304 | 23.53.40.35:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0754c686571bd23f | unknown | compressed | 65.2 Kb | unknown |
1080 | svchost.exe | GET | 200 | 23.53.40.35:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?3e412f7b4eff0943 | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
392 | mshta.exe | 108.138.2.225:443 | d2h2vj880gd6v8.cloudfront.net | AMAZON-02 | US | unknown |
392 | mshta.exe | 23.32.238.178:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
392 | mshta.exe | 108.138.2.173:80 | o.ss2.us | AMAZON-02 | US | unknown |
392 | mshta.exe | 18.245.39.64:80 | ocsp.rootg2.amazontrust.com | — | US | unknown |
392 | mshta.exe | 18.245.31.88:80 | crl.rootg2.amazontrust.com | — | US | unknown |
3356 | powershell.exe | 34.237.194.191:8888 | — | AMAZON-AES | US | unknown |
1080 | svchost.exe | 23.53.40.35:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
d2h2vj880gd6v8.cloudfront.net |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
crl.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
dns.msftncsi.com |
| shared |