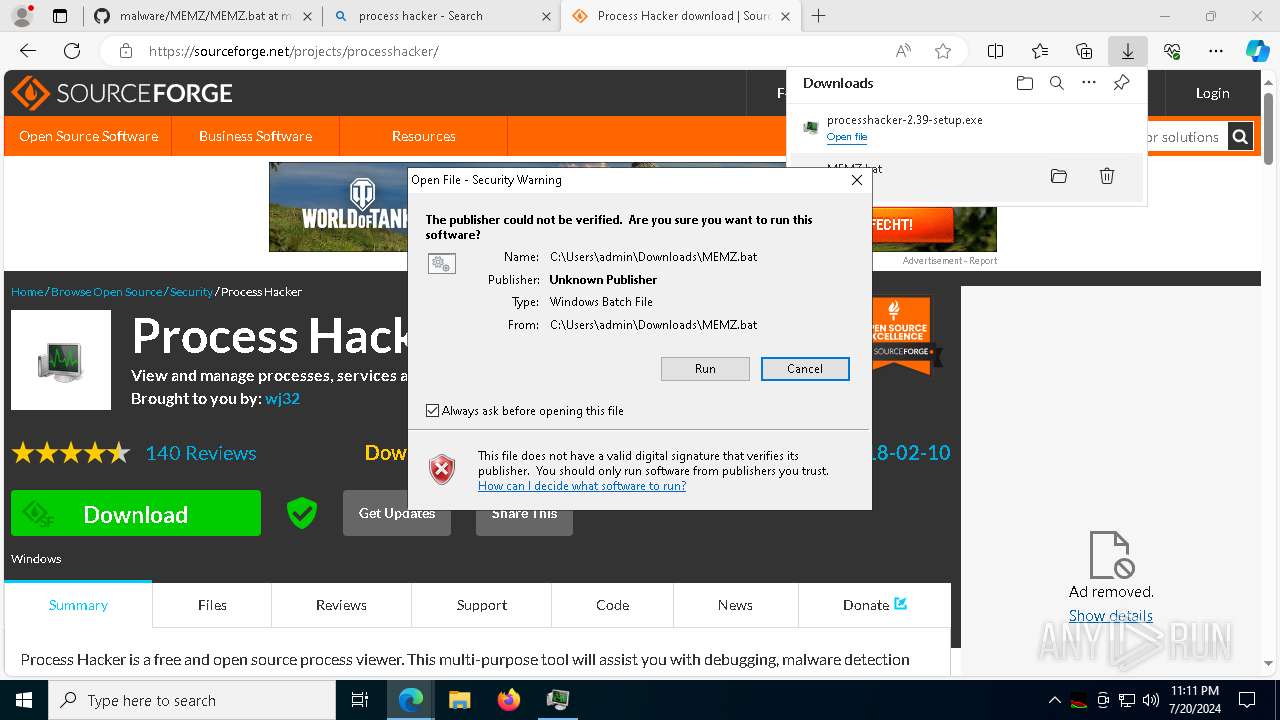
| URL: | https://github.com/Viper4K/malware/blob/master/MEMZ/MEMZ.bat |
| Full analysis: | https://app.any.run/tasks/539f37f9-955a-43d2-b02a-39e03f9215f5 |
| Verdict: | Malicious activity |
| Analysis date: | July 20, 2024, 23:10:27 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 9CD14358FFD3D802CC97FAF272A2709C |
| SHA1: | CCCA4208E597C488FFE672724436F9F547DEC22B |
| SHA256: | 7D587C2551E990553B06F5F6255B3EF875CD439E457FDBBEE0B39984B3E43F97 |
| SSDEEP: | 3:N8tEdQqXJJ3vJcTEHB+:2umsJs+k |
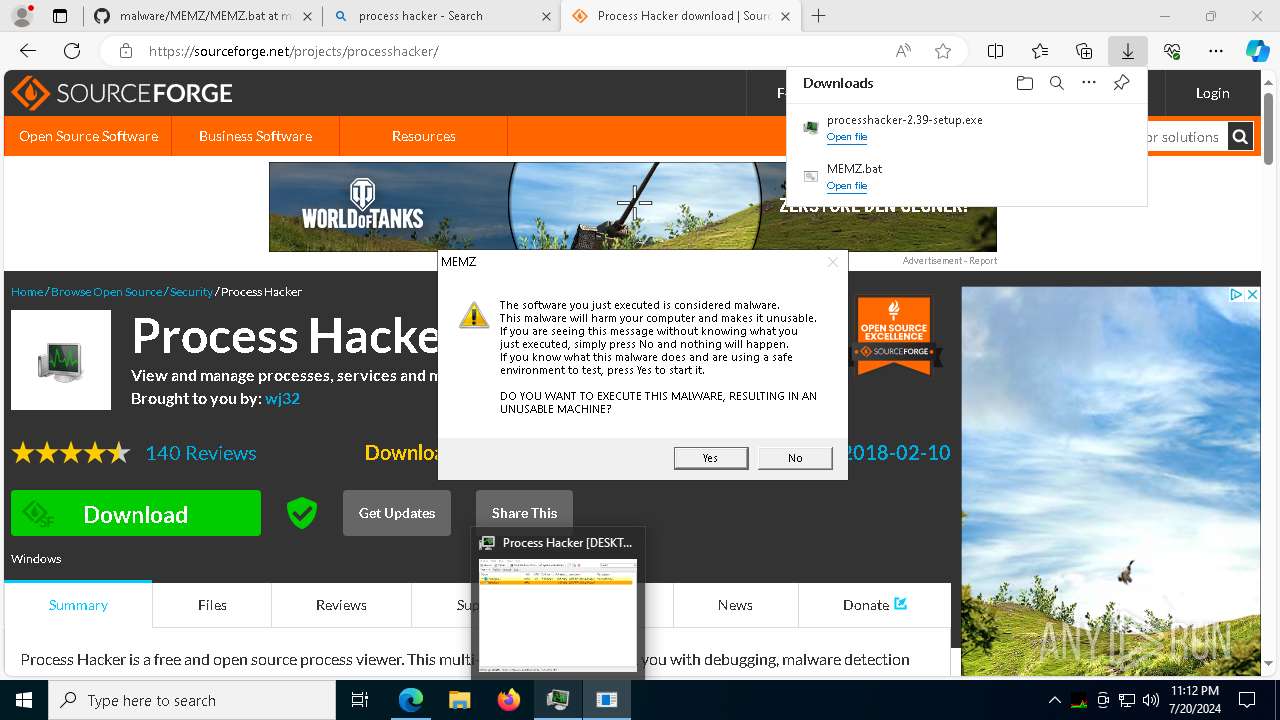
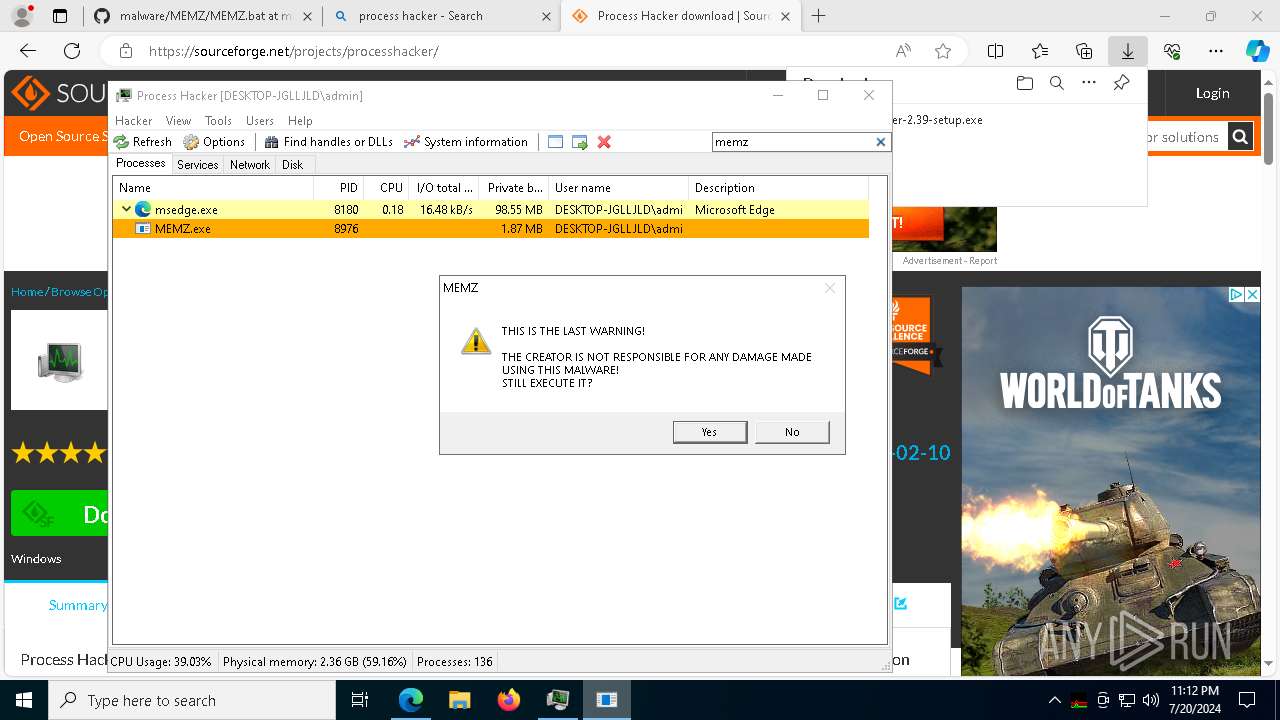
MALICIOUS
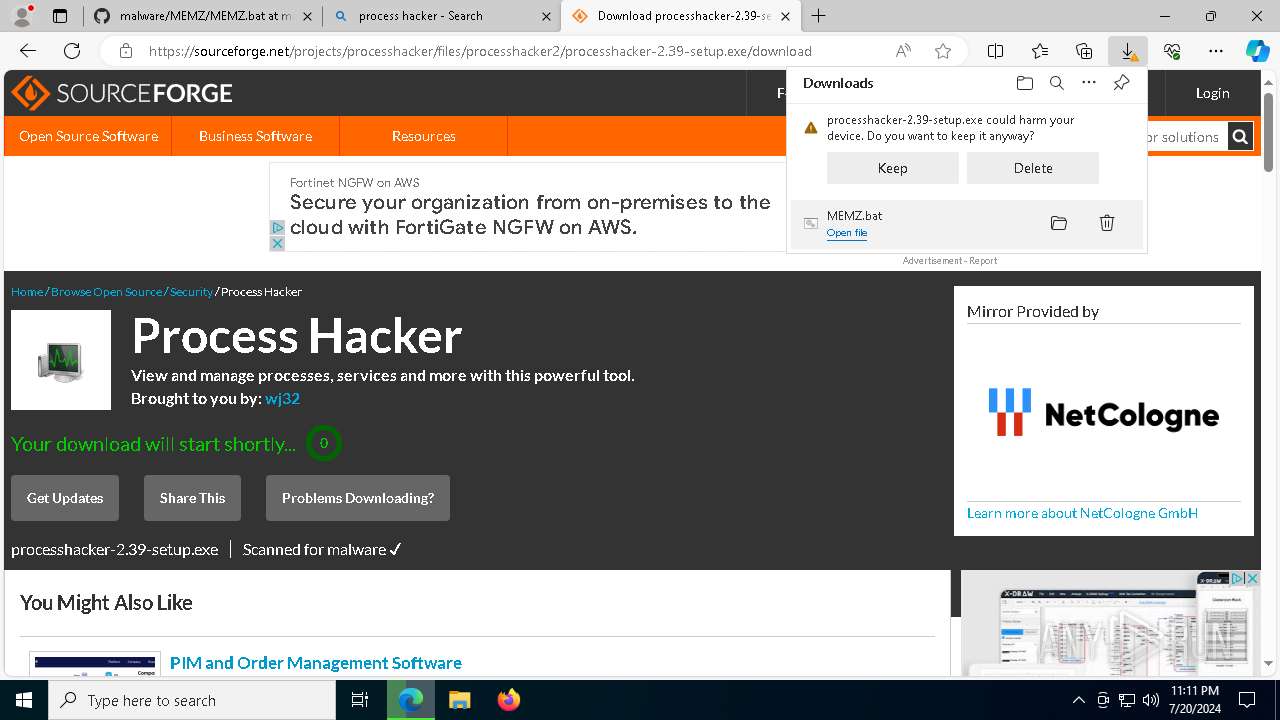
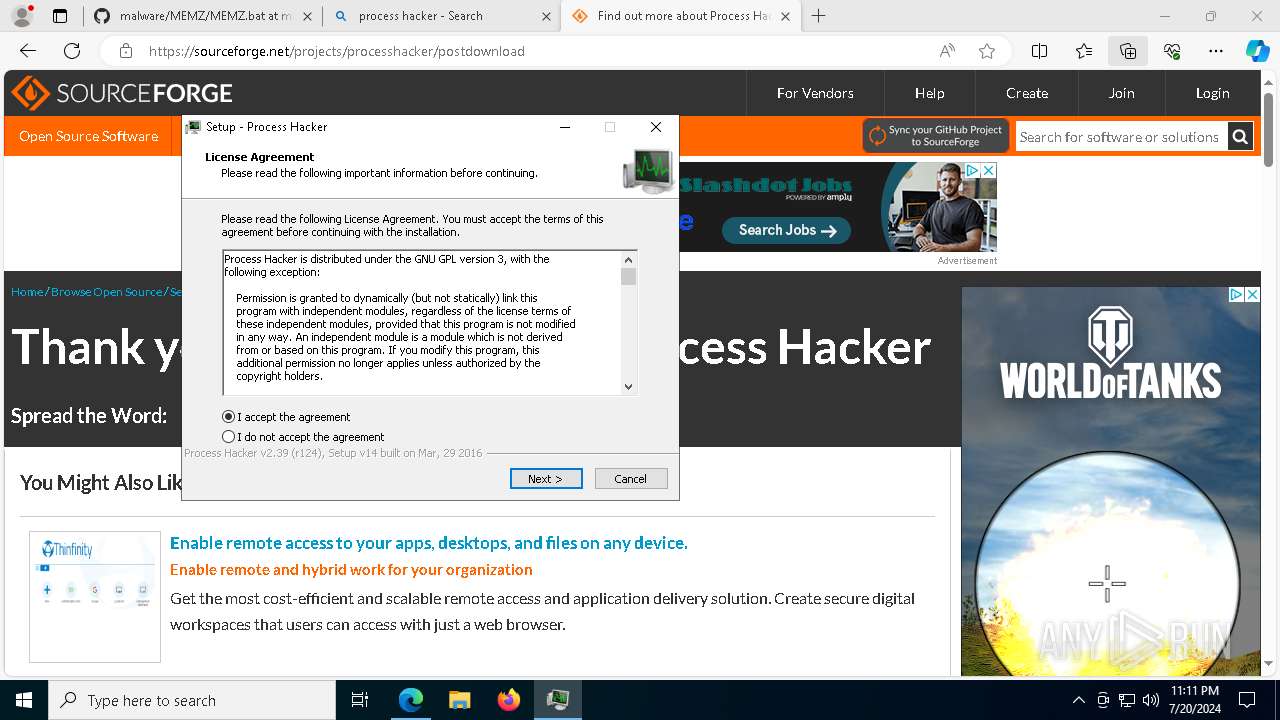
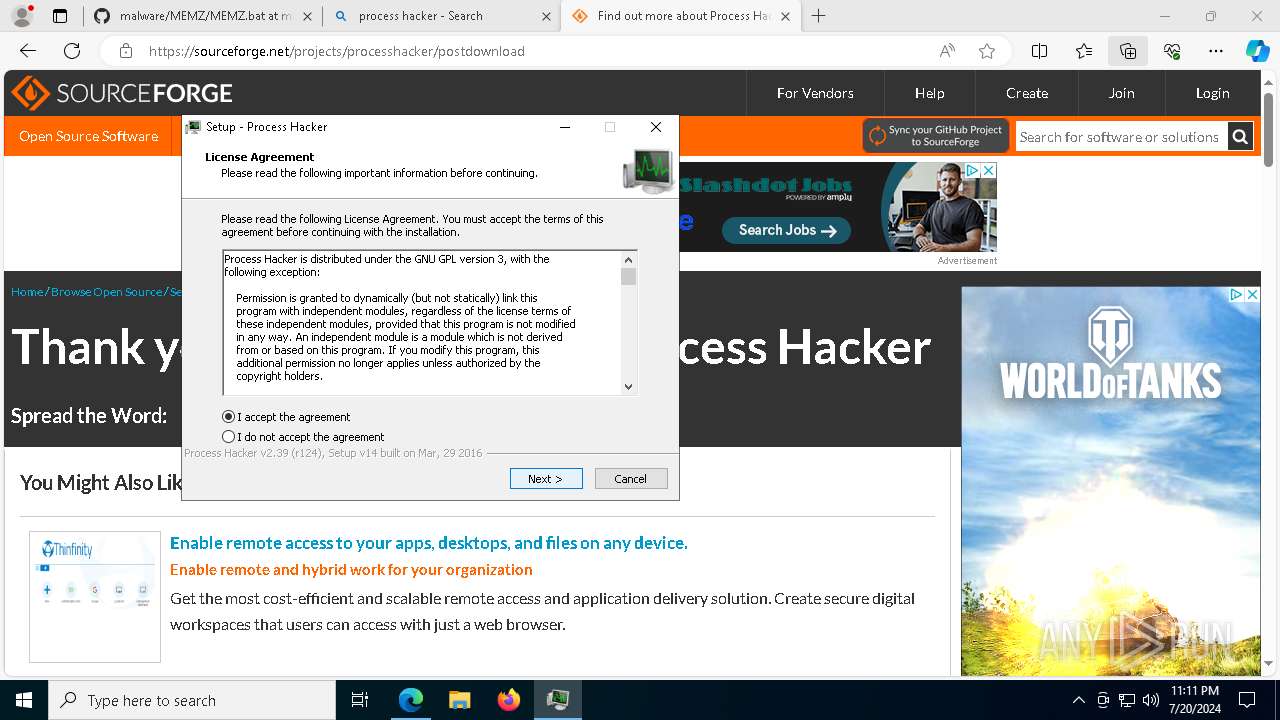
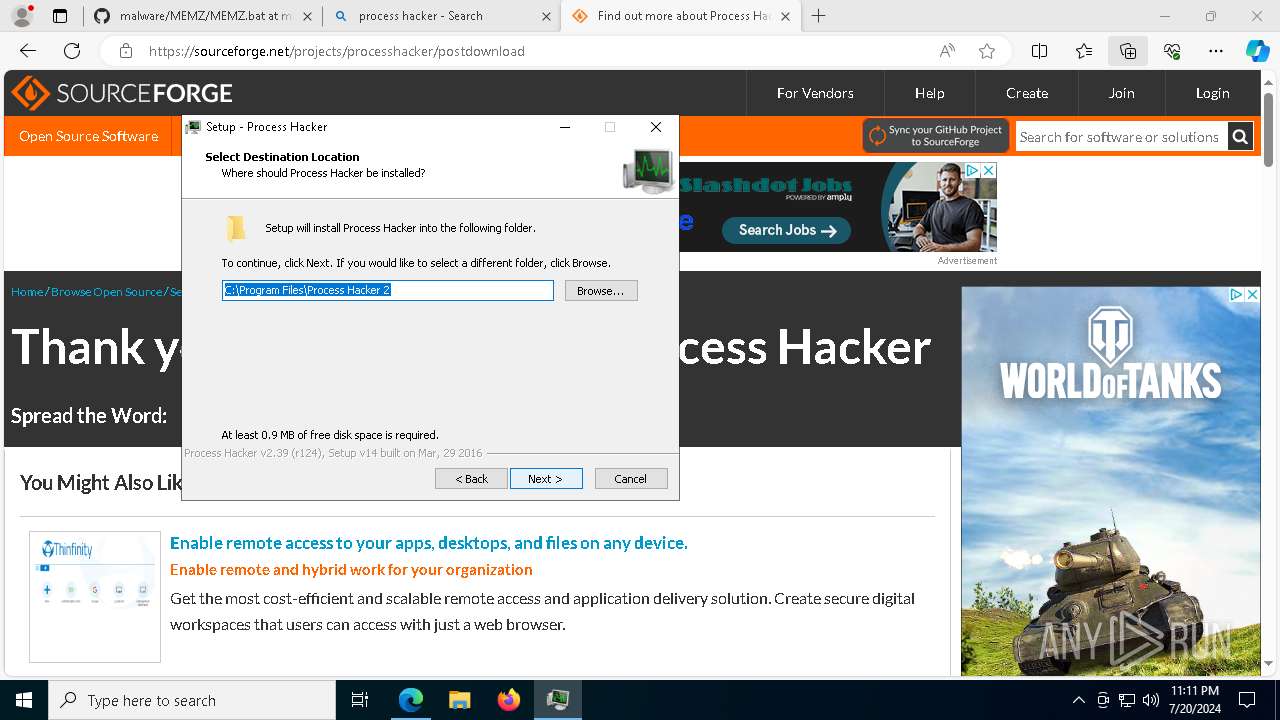
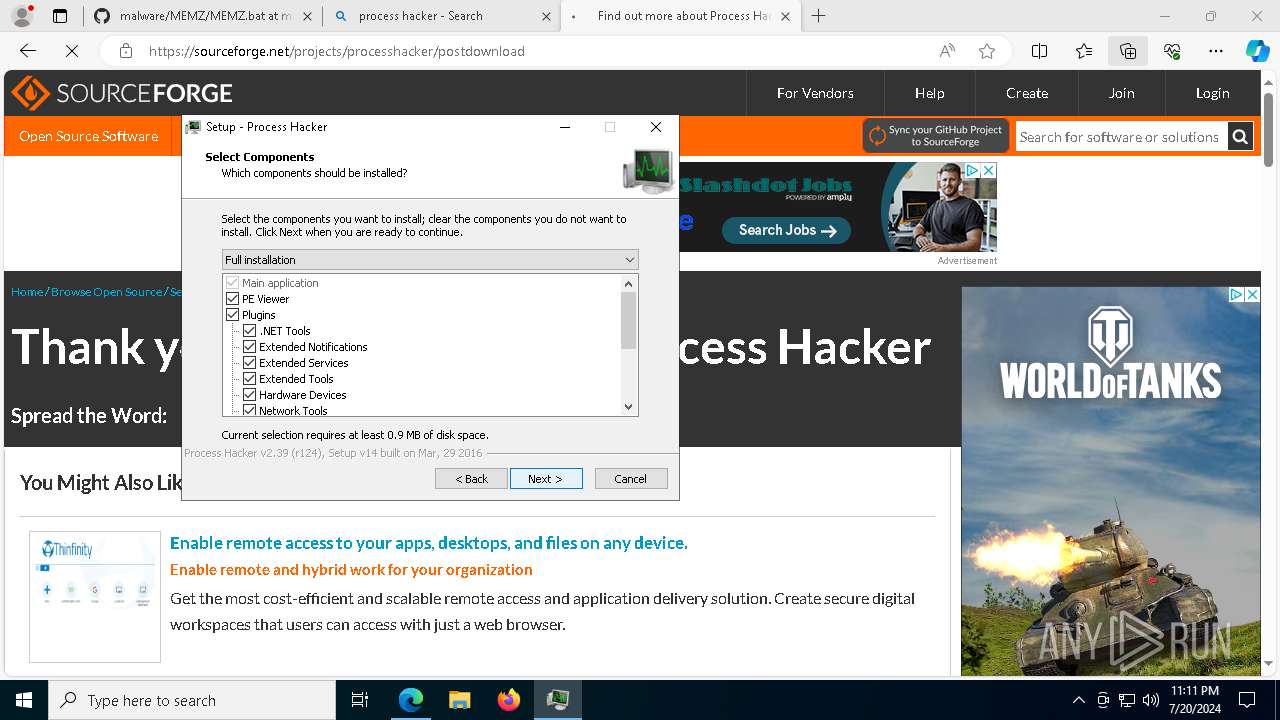
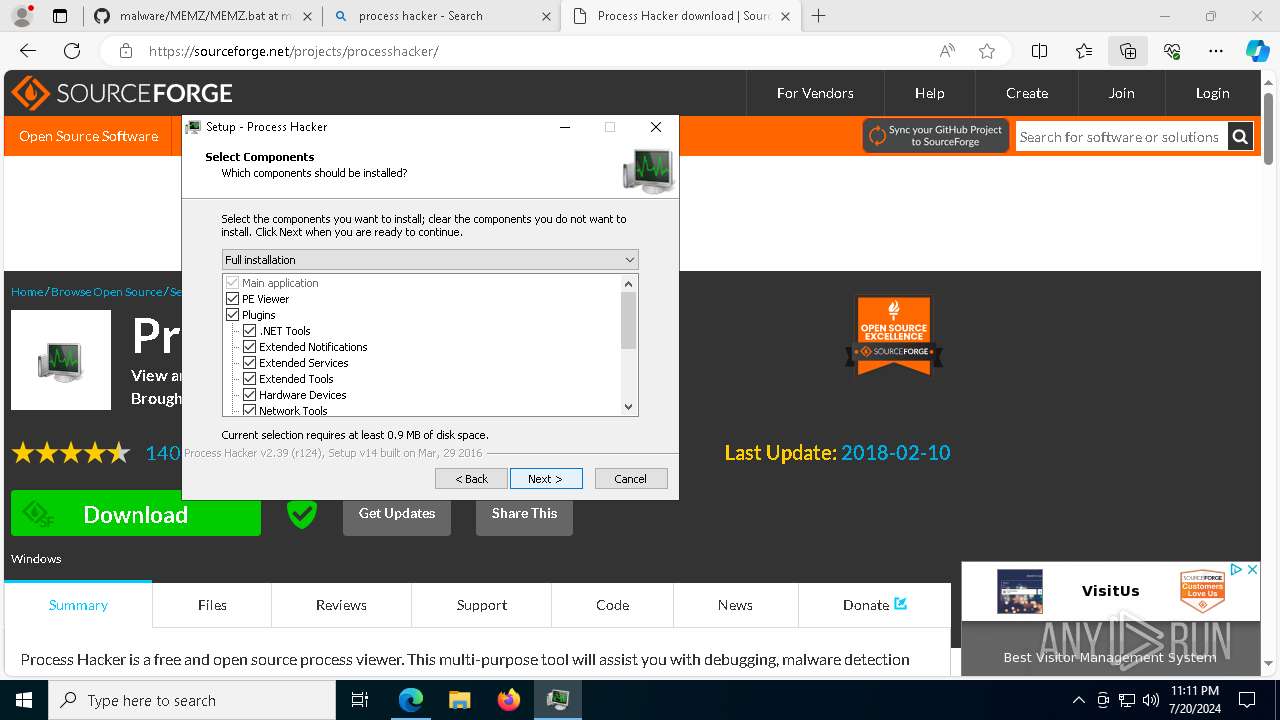
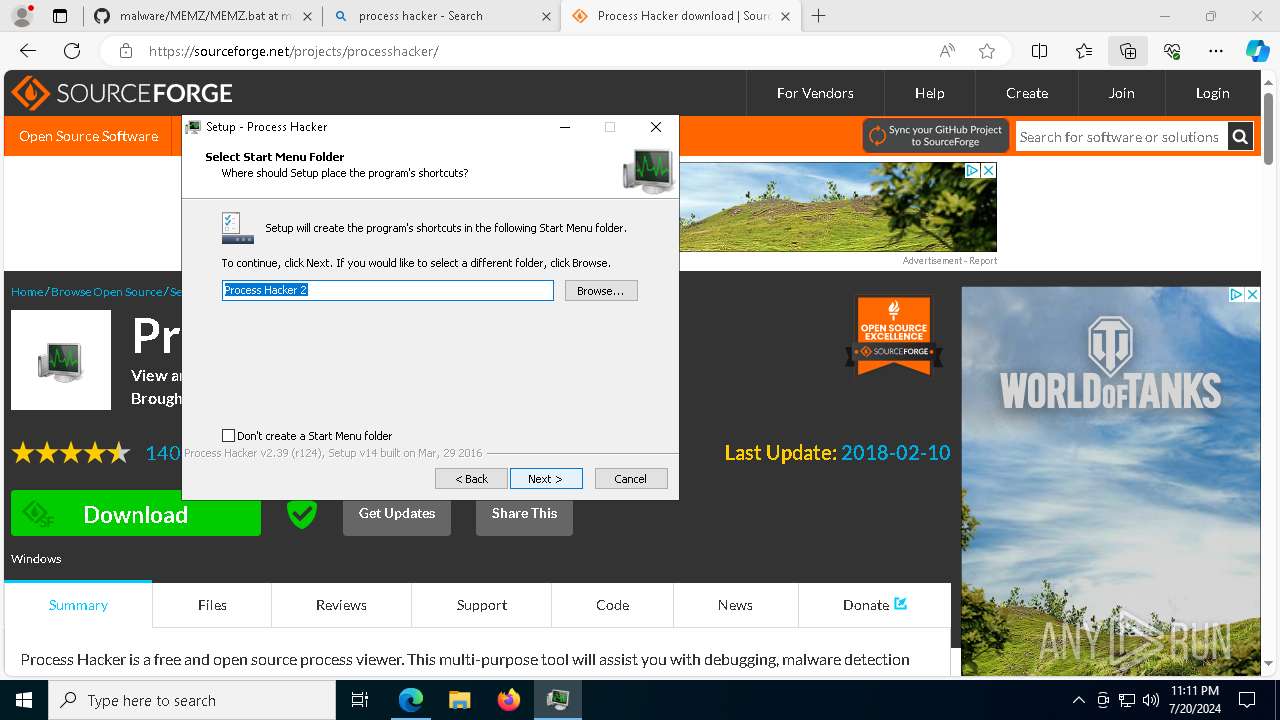
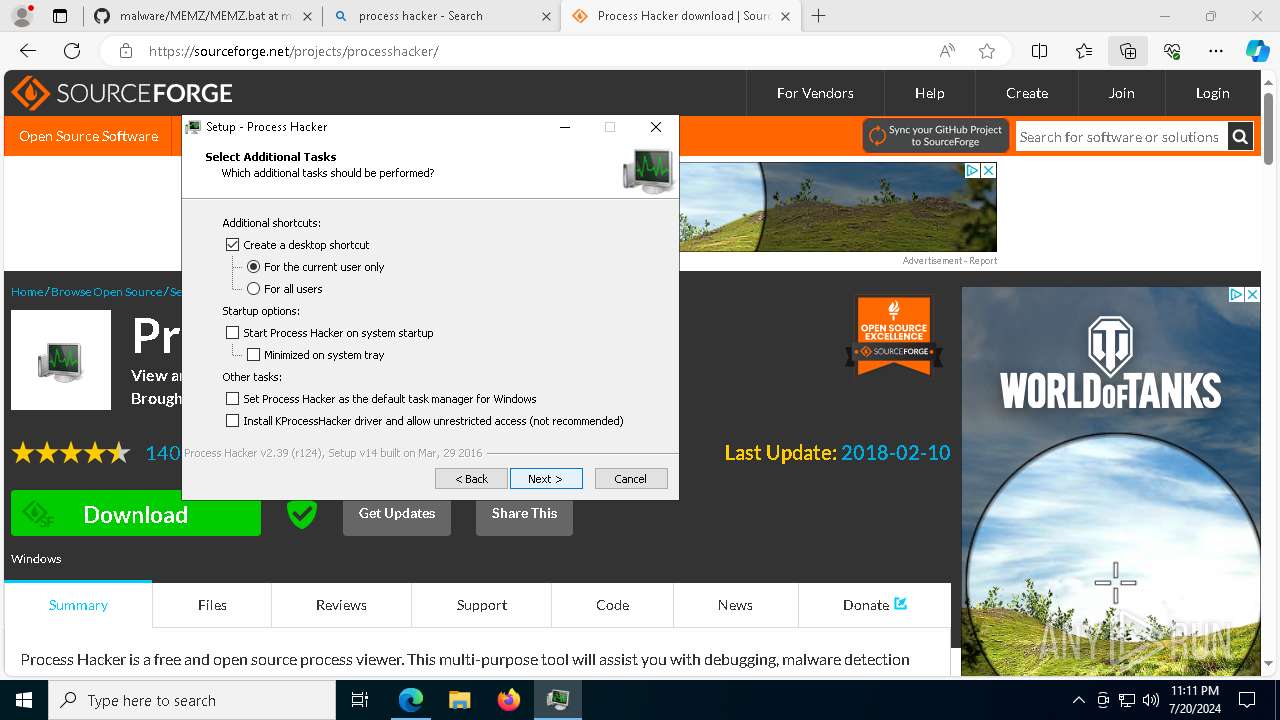
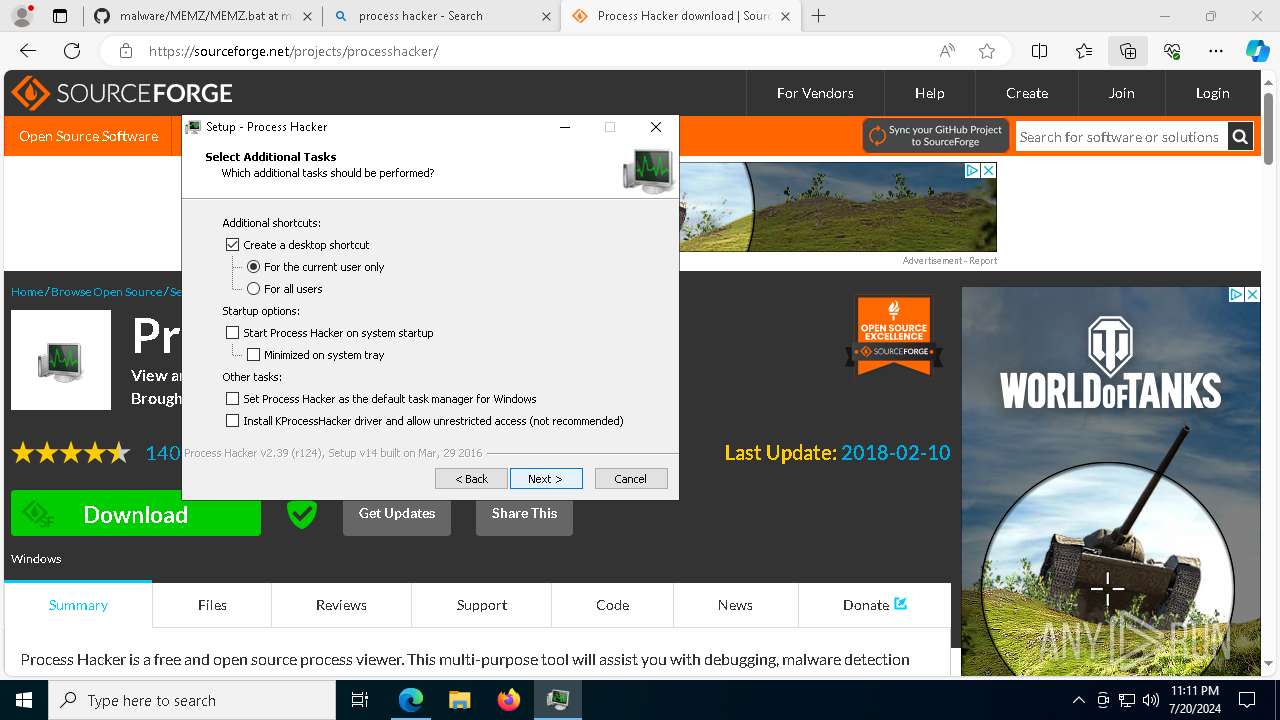
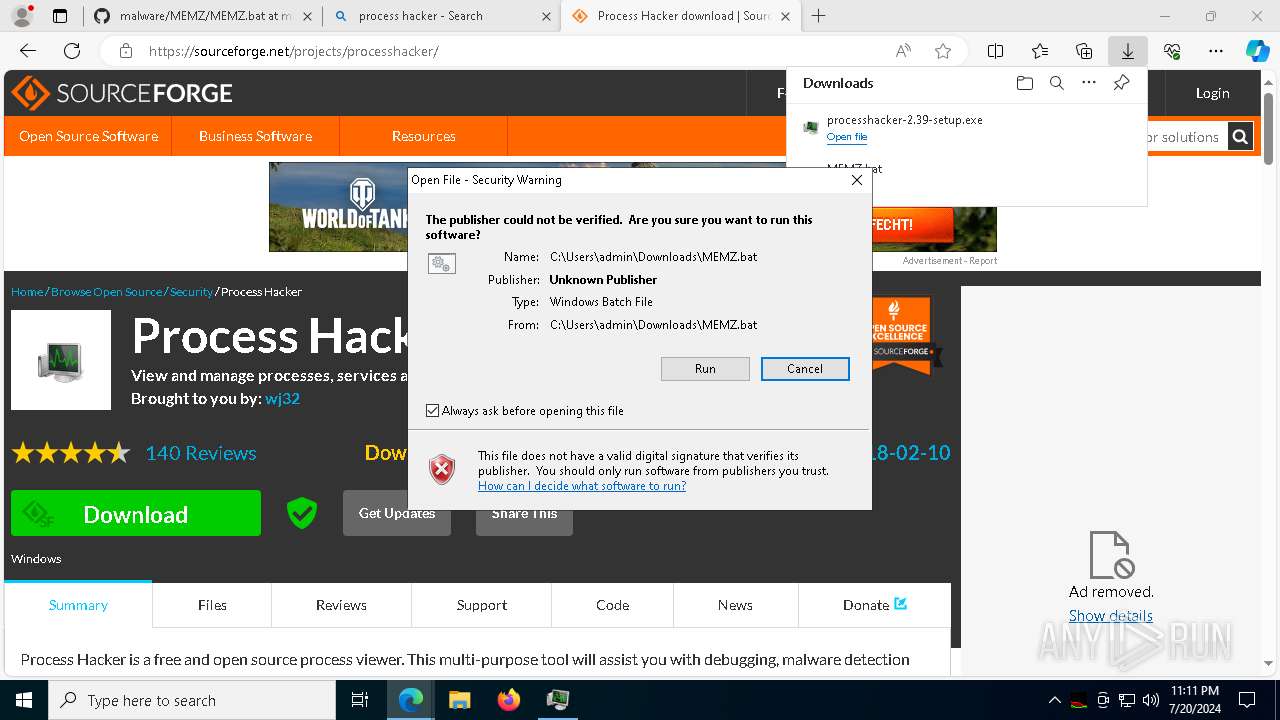
Drops the executable file immediately after the start
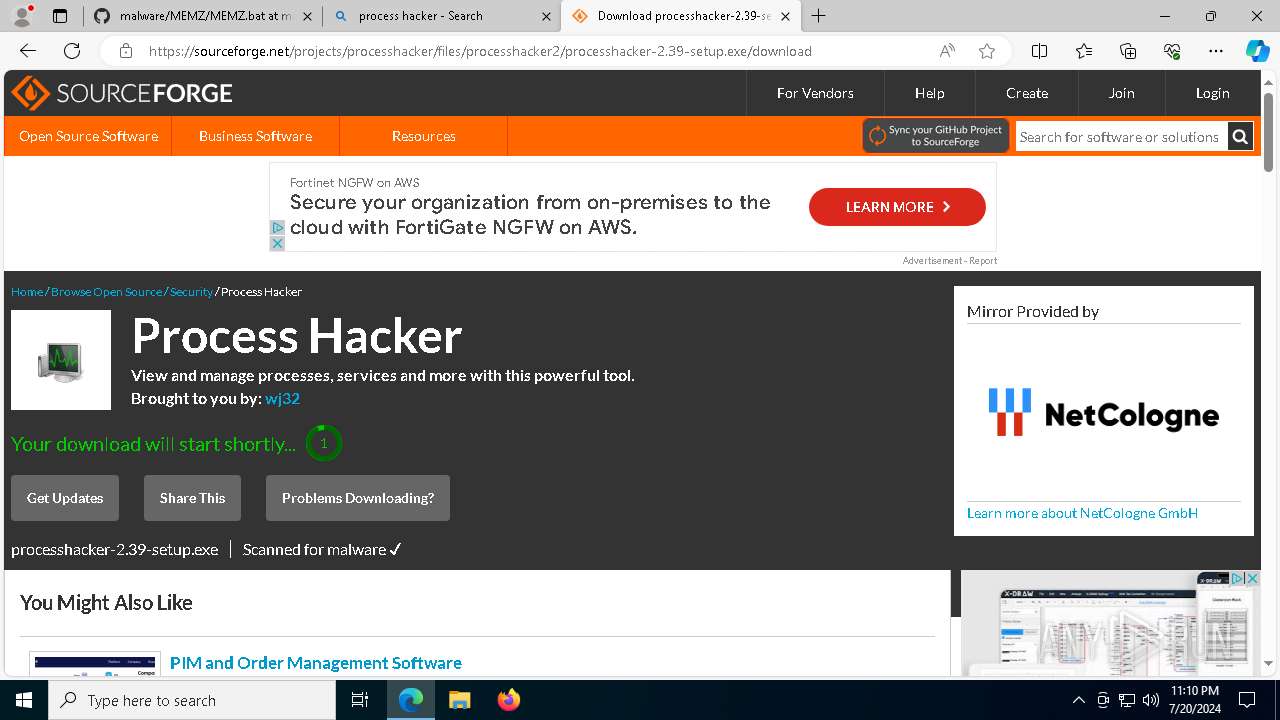
- processhacker-2.39-setup.exe (PID: 8884)
- processhacker-2.39-setup.tmp (PID: 8912)
- processhacker-2.39-setup.exe (PID: 8792)
Gets a file object corresponding to the file in a specified path (SCRIPT)
- cscript.exe (PID: 8496)
Uses base64 encoding (SCRIPT)
- cscript.exe (PID: 8496)
Starts CMD.EXE for commands execution
- msedge.exe (PID: 8180)
SUSPICIOUS
Reads security settings of Internet Explorer
- cookie_exporter.exe (PID: 7212)
- processhacker-2.39-setup.tmp (PID: 8812)
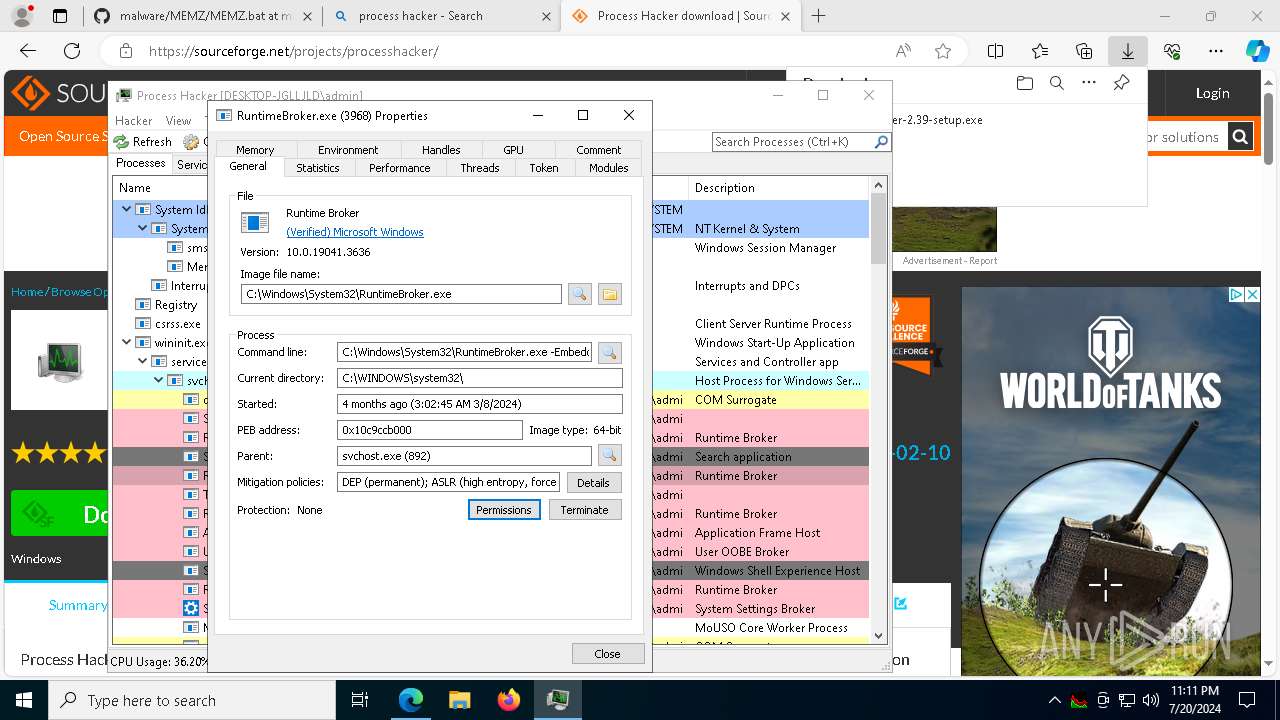
- ProcessHacker.exe (PID: 6260)
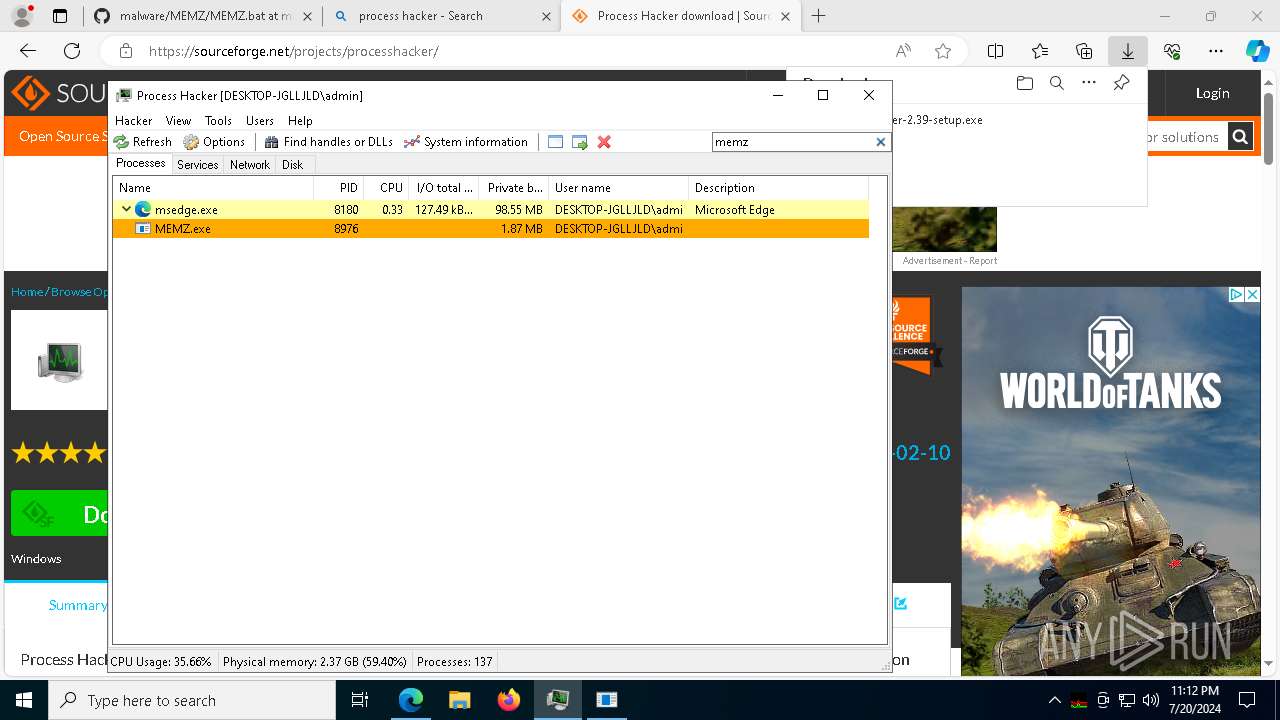
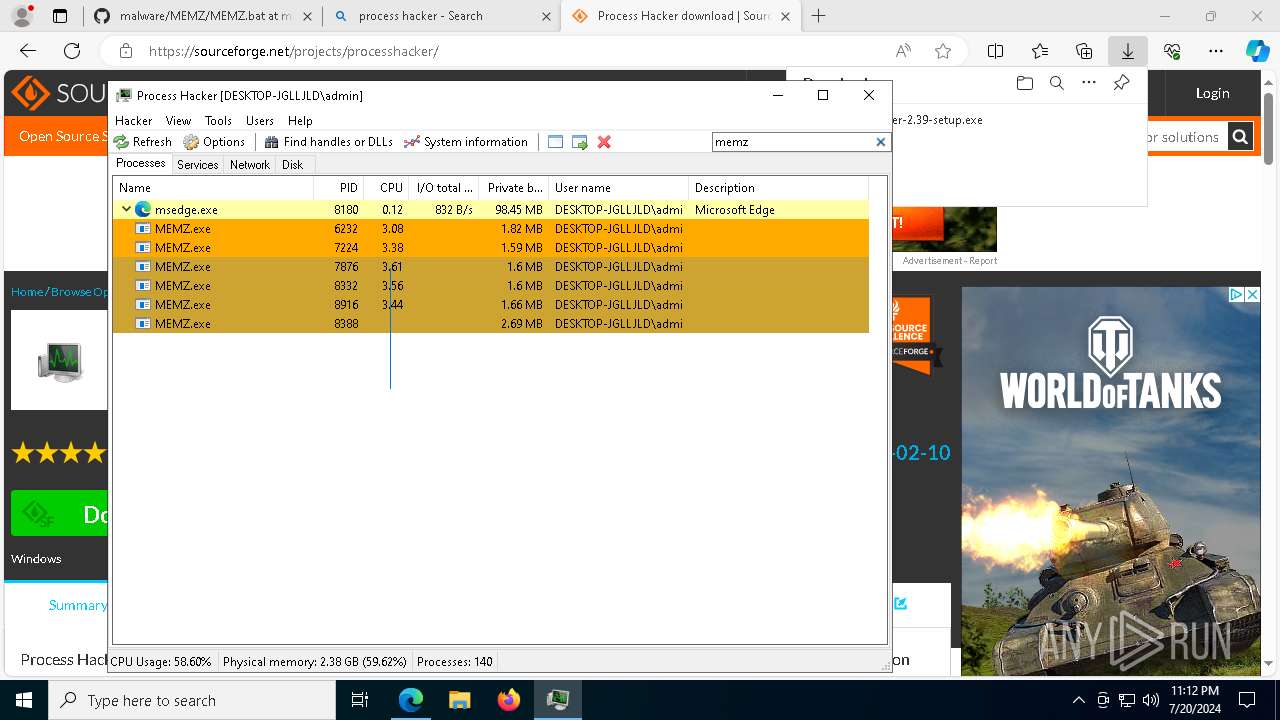
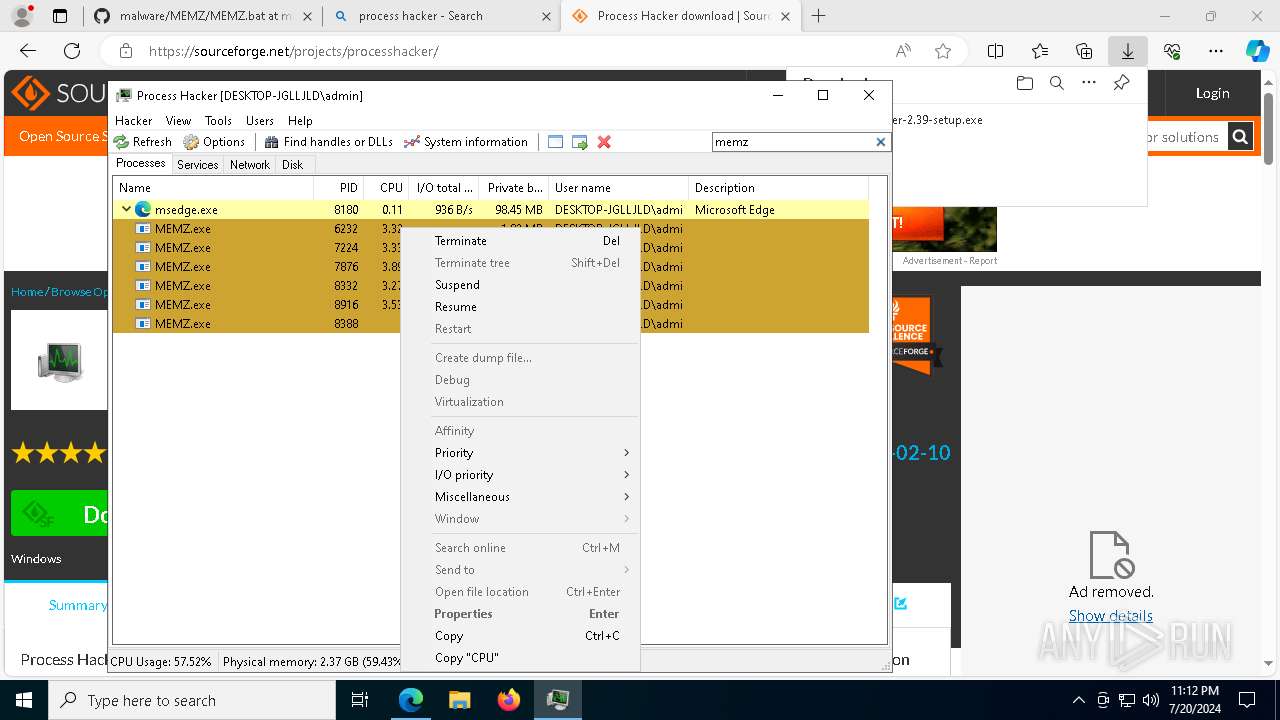
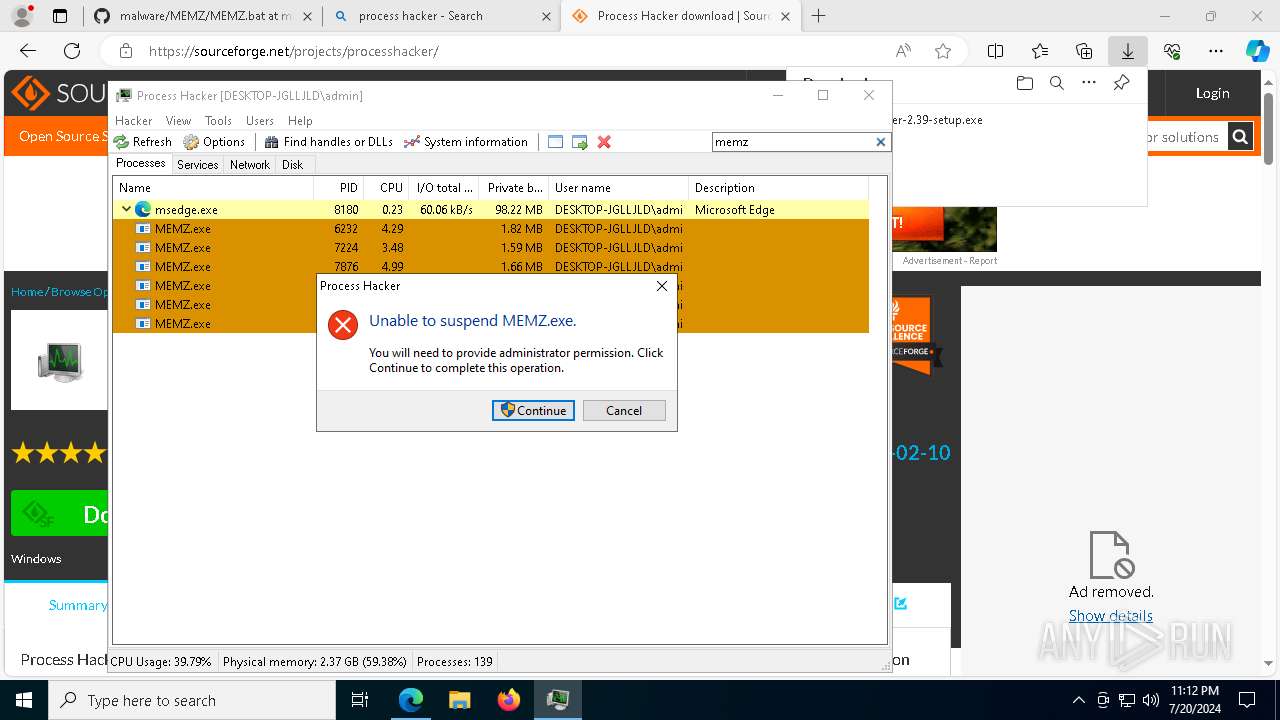
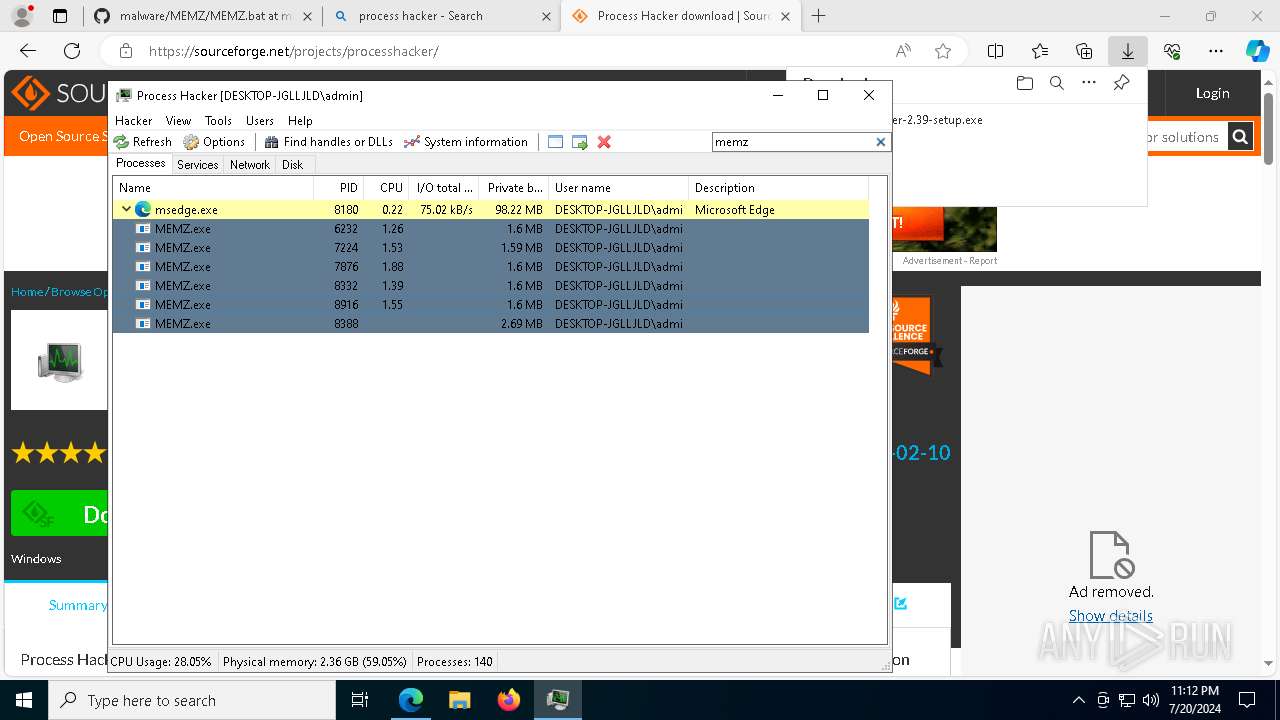
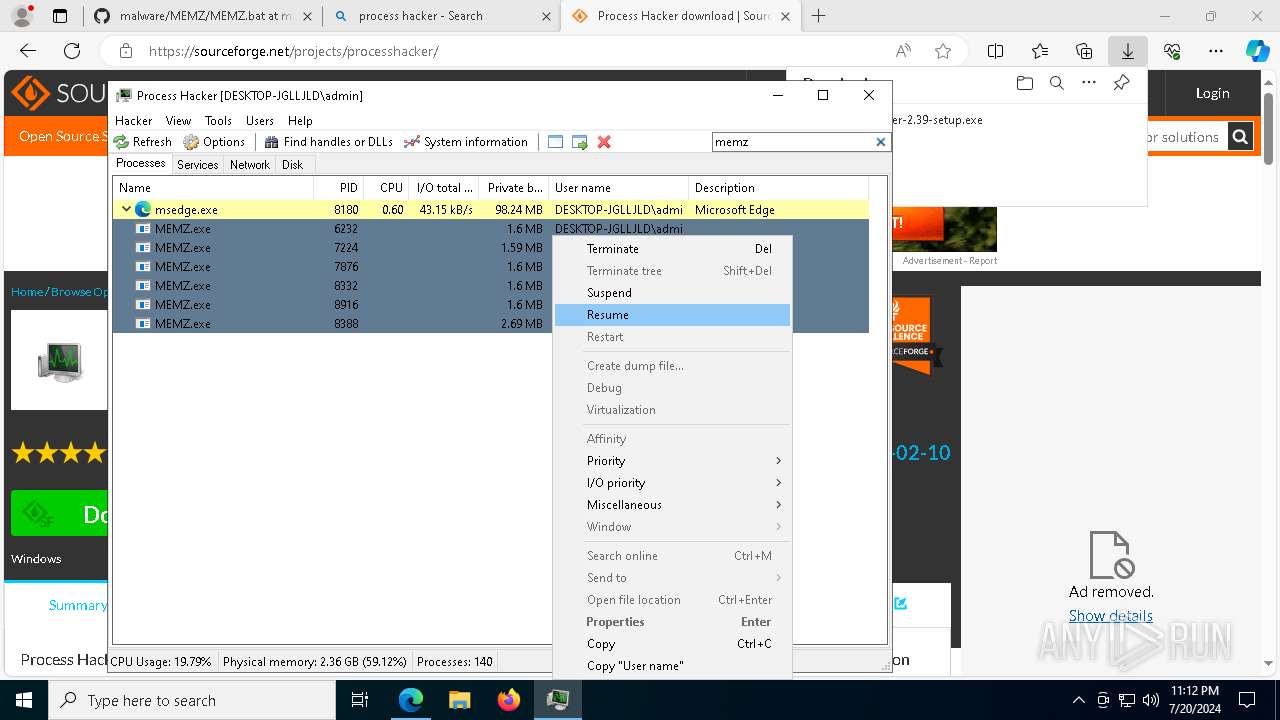
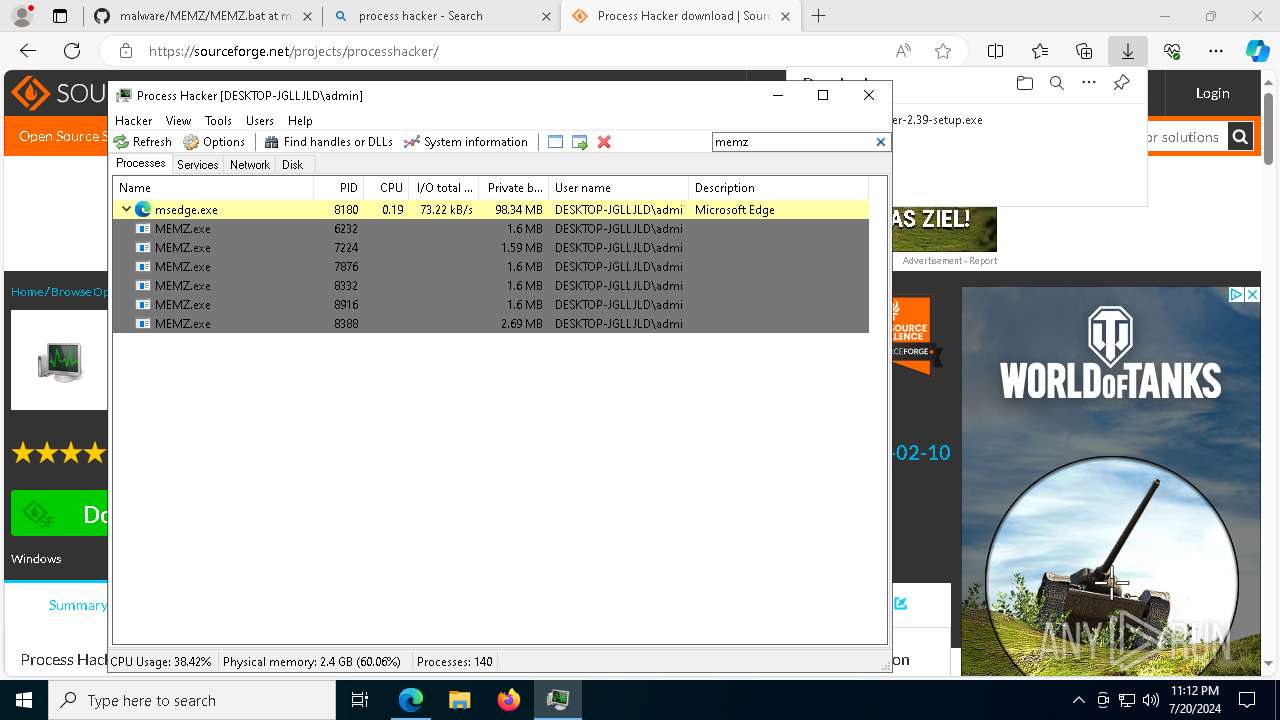
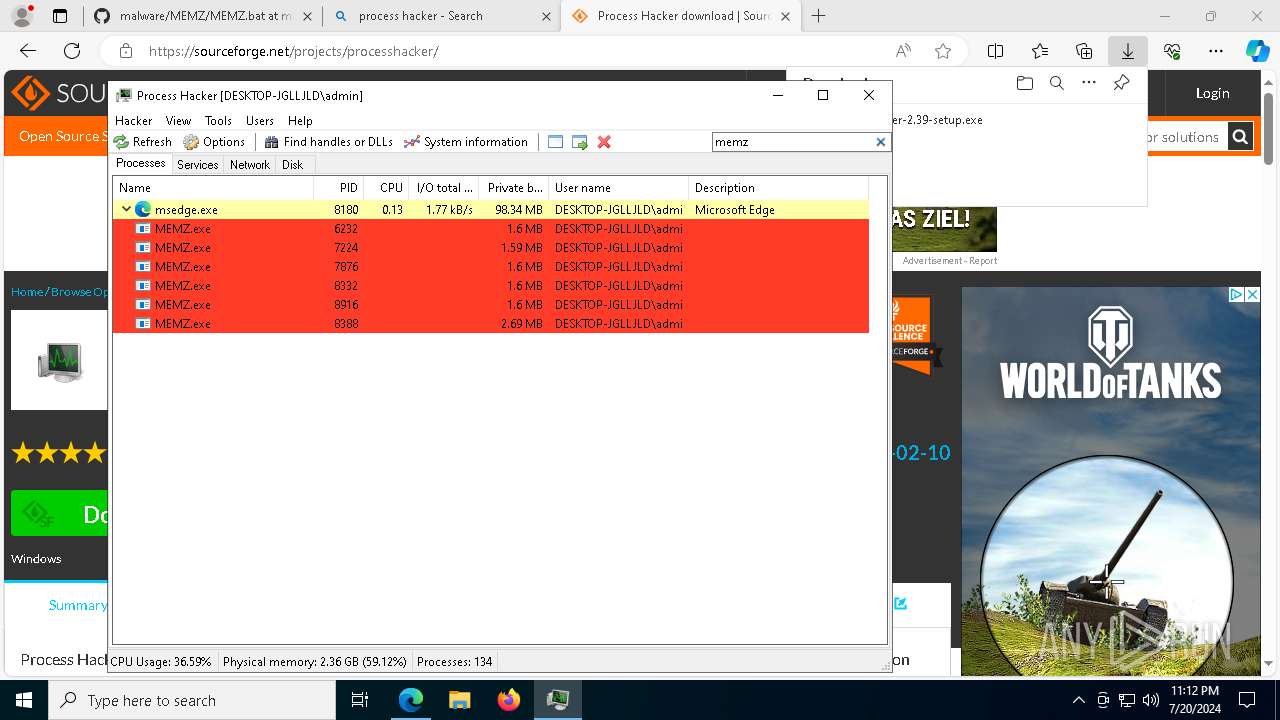
- MEMZ.exe (PID: 8976)
- MEMZ.exe (PID: 8388)
Executable content was dropped or overwritten
- processhacker-2.39-setup.exe (PID: 8792)
- processhacker-2.39-setup.exe (PID: 8884)
- processhacker-2.39-setup.tmp (PID: 8912)
- cscript.exe (PID: 8496)
Reads the date of Windows installation
- processhacker-2.39-setup.tmp (PID: 8812)
- MEMZ.exe (PID: 8976)
- MEMZ.exe (PID: 8388)
- ProcessHacker.exe (PID: 6260)
Process drops legitimate windows executable
- processhacker-2.39-setup.tmp (PID: 8912)
Reads the Windows owner or organization settings
- processhacker-2.39-setup.tmp (PID: 8912)
Checks Windows Trust Settings
- ProcessHacker.exe (PID: 6260)
Drops a system driver (possible attempt to evade defenses)
- processhacker-2.39-setup.tmp (PID: 8912)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 8496)
Creates XML DOM element (SCRIPT)
- cscript.exe (PID: 8496)
Script creates XML DOM node (SCRIPT)
- cscript.exe (PID: 8496)
Creates a Folder object (SCRIPT)
- cscript.exe (PID: 8496)
Sets XML DOM element text (SCRIPT)
- cscript.exe (PID: 8496)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- cscript.exe (PID: 8496)
Saves data to a binary file (SCRIPT)
- cscript.exe (PID: 8496)
Executing commands from a ".bat" file
- msedge.exe (PID: 8180)
The process executes JS scripts
- cmd.exe (PID: 5312)
Writes binary data to a Stream object (SCRIPT)
- cscript.exe (PID: 8496)
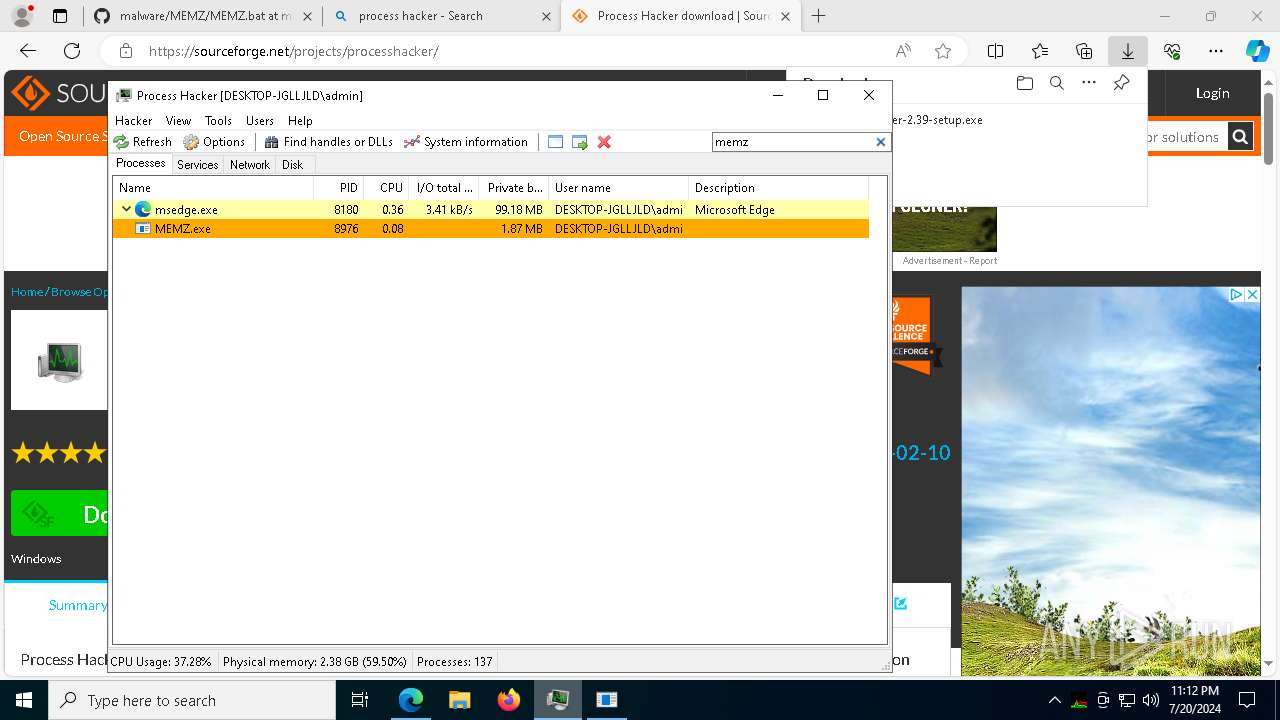
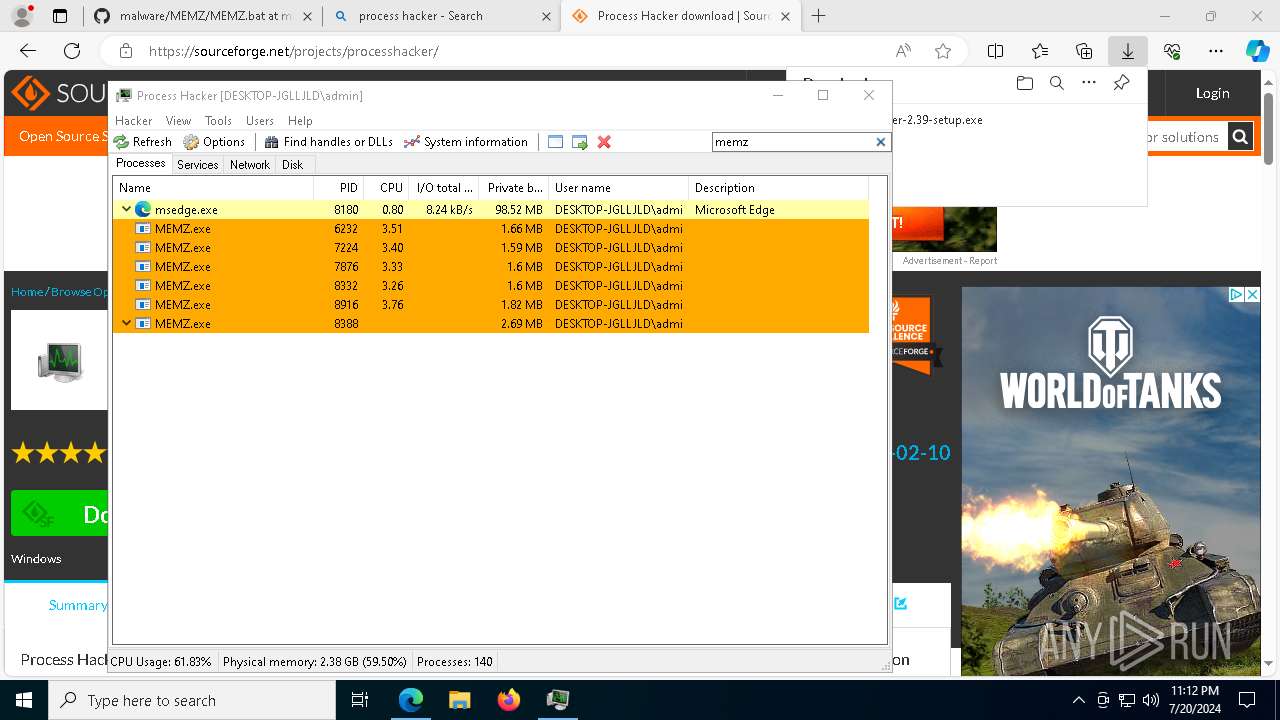
The executable file from the user directory is run by the CMD process
- MEMZ.exe (PID: 7764)
- MEMZ.exe (PID: 4424)
- MEMZ.exe (PID: 8976)
Application launched itself
- MEMZ.exe (PID: 8976)
- ProcessHacker.exe (PID: 6260)
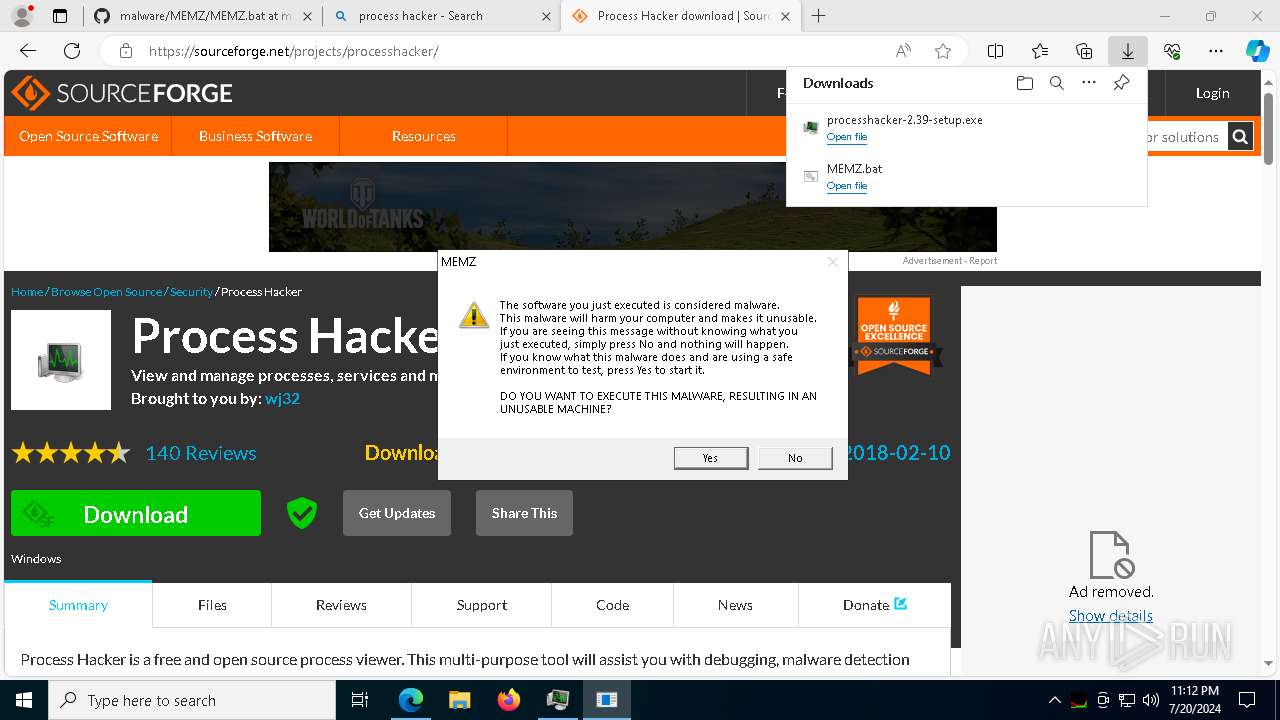
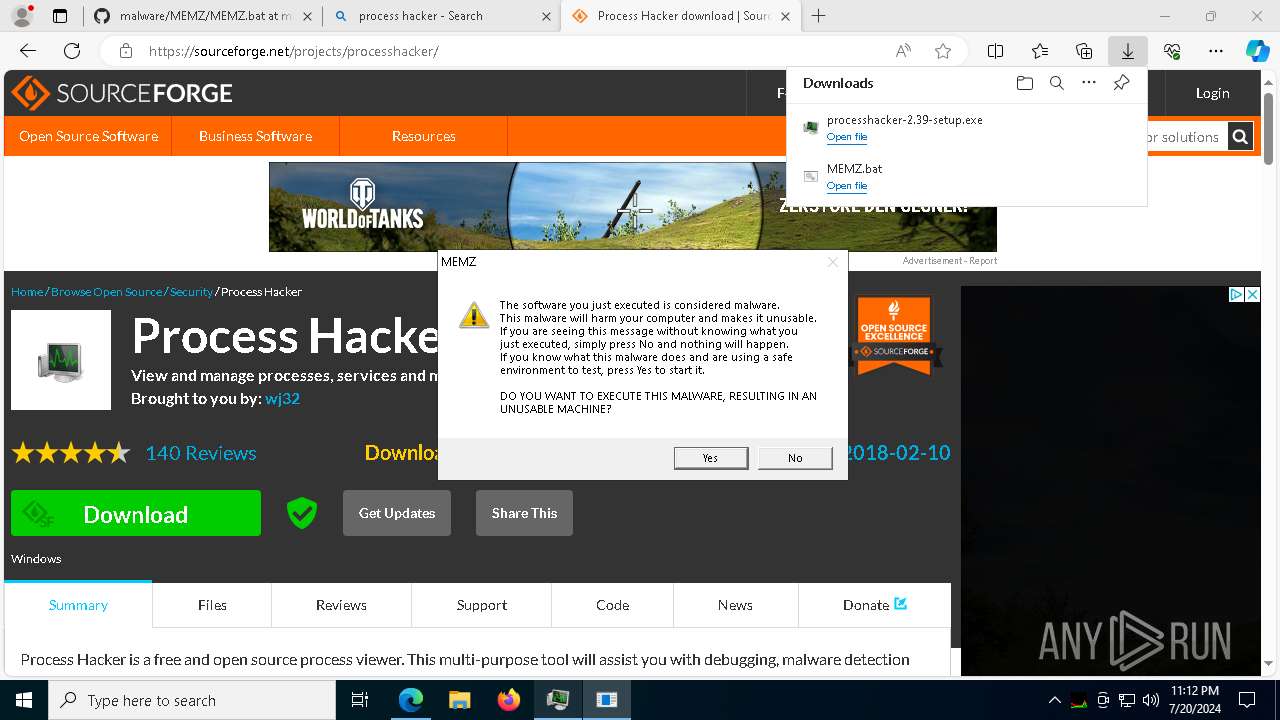
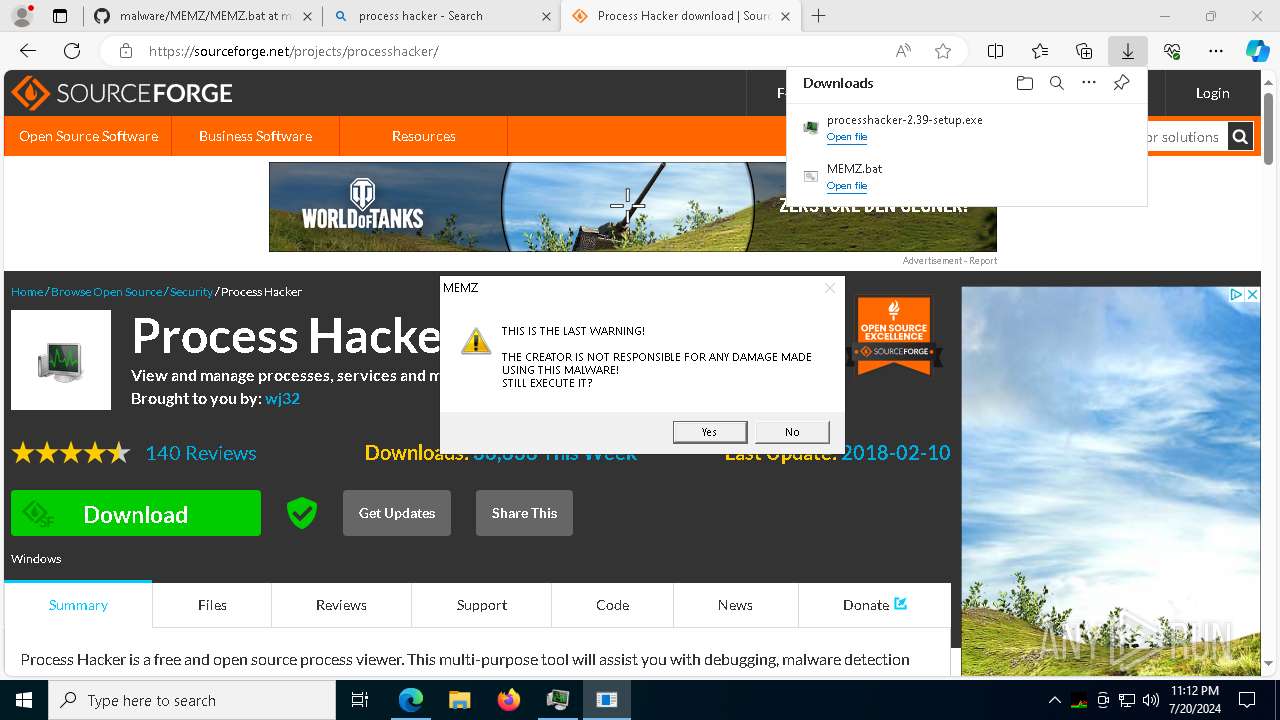
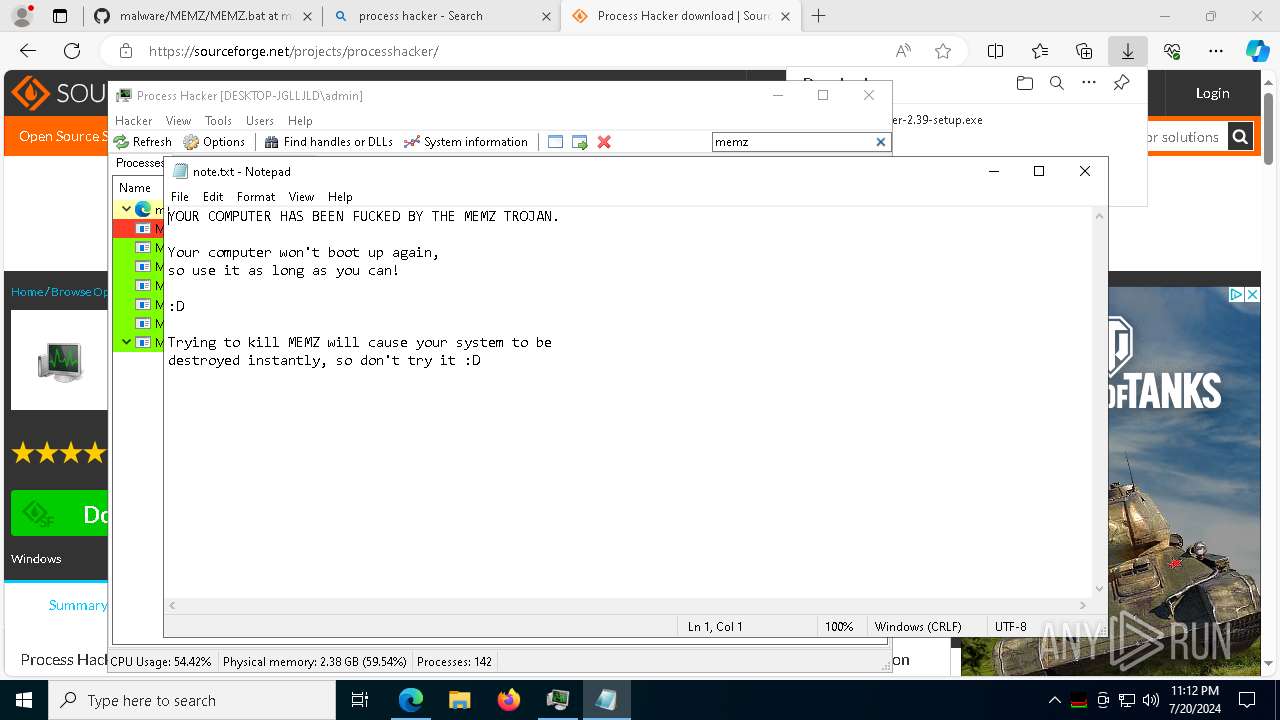
Start notepad (likely ransomware note)
- MEMZ.exe (PID: 8388)
Creates file in the systems drive root
- notepad.exe (PID: 8924)
- MEMZ.exe (PID: 8388)
INFO
Reads Microsoft Office registry keys
- msedge.exe (PID: 8180)
Executable content was dropped or overwritten
- msedge.exe (PID: 8180)
- msedge.exe (PID: 7076)
Checks supported languages
- cookie_exporter.exe (PID: 7212)
- identity_helper.exe (PID: 7744)
- processhacker-2.39-setup.exe (PID: 8884)
- processhacker-2.39-setup.tmp (PID: 8912)
- ProcessHacker.exe (PID: 6260)
- identity_helper.exe (PID: 8560)
- MEMZ.exe (PID: 8976)
- MEMZ.exe (PID: 6232)
- MEMZ.exe (PID: 7224)
- MEMZ.exe (PID: 8388)
- ProcessHacker.exe (PID: 8624)
- MEMZ.exe (PID: 8332)
- MEMZ.exe (PID: 8916)
- MEMZ.exe (PID: 7876)
- processhacker-2.39-setup.exe (PID: 8792)
- processhacker-2.39-setup.tmp (PID: 8812)
The process uses the downloaded file
- msedge.exe (PID: 6304)
- msedge.exe (PID: 8648)
- msedge.exe (PID: 8180)
Reads the computer name
- cookie_exporter.exe (PID: 7212)
- identity_helper.exe (PID: 7744)
- processhacker-2.39-setup.tmp (PID: 8812)
- processhacker-2.39-setup.tmp (PID: 8912)
- ProcessHacker.exe (PID: 6260)
- identity_helper.exe (PID: 8560)
- MEMZ.exe (PID: 8976)
- MEMZ.exe (PID: 8388)
- ProcessHacker.exe (PID: 8624)
Checks proxy server information
- cookie_exporter.exe (PID: 7212)
- ProcessHacker.exe (PID: 6260)
Drops the executable file immediately after the start
- msedge.exe (PID: 8180)
- msedge.exe (PID: 7076)
- cscript.exe (PID: 8496)
Application launched itself
- msedge.exe (PID: 8180)
Create files in a temporary directory
- processhacker-2.39-setup.exe (PID: 8792)
- processhacker-2.39-setup.exe (PID: 8884)
- processhacker-2.39-setup.tmp (PID: 8912)
Process checks computer location settings
- processhacker-2.39-setup.tmp (PID: 8812)
- MEMZ.exe (PID: 8976)
- MEMZ.exe (PID: 8388)
- ProcessHacker.exe (PID: 6260)
Creates a software uninstall entry
- processhacker-2.39-setup.tmp (PID: 8912)
Reads the machine GUID from the registry
- ProcessHacker.exe (PID: 6260)
Reads Environment values
- ProcessHacker.exe (PID: 6260)
Reads the software policy settings
- ProcessHacker.exe (PID: 6260)
Creates files in the program directory
- processhacker-2.39-setup.tmp (PID: 8912)
Reads security settings of Internet Explorer
- cscript.exe (PID: 8496)
- notepad.exe (PID: 8924)
Creates files or folders in the user directory
- cscript.exe (PID: 8496)
- ProcessHacker.exe (PID: 6260)
Reads CPU info
- ProcessHacker.exe (PID: 8624)
Reads the time zone
- ProcessHacker.exe (PID: 8624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
232
Monitored processes
85
Malicious processes
10
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 68 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=4956 --field-trial-handle=2372,i,14350803702288117847,85138565459493527,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 116 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7320 --field-trial-handle=2372,i,14350803702288117847,85138565459493527,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1540 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6096 --field-trial-handle=2372,i,14350803702288117847,85138565459493527,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2056 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2068 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --instant-process --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=55 --mojo-platform-channel-handle=6184 --field-trial-handle=2372,i,14350803702288117847,85138565459493527,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2112 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://github.com/Viper4K/malware/blob/master/MEMZ/MEMZ.bat" | C:\Program Files\Internet Explorer\iexplore.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2868 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5504 --field-trial-handle=2372,i,14350803702288117847,85138565459493527,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3108 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=42 --mojo-platform-channel-handle=8344 --field-trial-handle=2372,i,14350803702288117847,85138565459493527,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3360 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5308 --field-trial-handle=2372,i,14350803702288117847,85138565459493527,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3624 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6588 --field-trial-handle=2372,i,14350803702288117847,85138565459493527,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
41 461
Read events
41 235
Write events
215
Delete events
11
Modification events
| (PID) Process: | (2112) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkLowPart |
Value: 0 | |||
| (PID) Process: | (2112) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | L1WatermarkHighPart |
Value: 0 | |||
| (PID) Process: | (2112) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 0 | |||
| (PID) Process: | (2112) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 0 | |||
| (PID) Process: | (2112) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 376168655 | |||
| (PID) Process: | (2112) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\UrlBlock |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31120122 | |||
| (PID) Process: | (2112) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2112) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2112) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2112) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
Executable files
58
Suspicious files
663
Text files
160
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 8180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\BrowserMetrics\BrowserMetrics-669C43E7-1FF4.pma | — | |
MD5:— | SHA256:— | |||
| 8180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF428c9f.TMP | — | |
MD5:— | SHA256:— | |||
| 8180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 8180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF428c9f.TMP | — | |
MD5:— | SHA256:— | |||
| 8180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 8180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF428cae.TMP | — | |
MD5:— | SHA256:— | |||
| 8180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 8180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF428cae.TMP | — | |
MD5:— | SHA256:— | |||
| 8180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 8180 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF428cdd.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
253
DNS requests
242
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
9100 | svchost.exe | HEAD | 200 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/6e6d05a2-47e8-42b8-85a0-e8b7ee48333a?P1=1722029678&P2=404&P3=2&P4=Y4pLmG2r2omwimRsI0PDPWBBZbTuEpQ5MpbIkTXSND9gopYhwOR70taRRSAUSYNsh3Hr29cpNBEDBLOttEC8Ug%3d%3d | unknown | — | — | whitelisted |
8180 | msedge.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRm%2FrYSaqNr0YBIv29H4pMHhv2XmQQUl0gD6xUIa7myWCPMlC7xxmXSZI4CEA%2Fx72a9Yhxlt0tN5BQlcX8%3D | unknown | — | — | whitelisted |
8180 | msedge.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEALE0eWKSmgMVo2jBH5%2BTV8%3D | unknown | — | — | whitelisted |
9100 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/6e6d05a2-47e8-42b8-85a0-e8b7ee48333a?P1=1722029678&P2=404&P3=2&P4=Y4pLmG2r2omwimRsI0PDPWBBZbTuEpQ5MpbIkTXSND9gopYhwOR70taRRSAUSYNsh3Hr29cpNBEDBLOttEC8Ug%3d%3d | unknown | — | — | whitelisted |
9100 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/6e6d05a2-47e8-42b8-85a0-e8b7ee48333a?P1=1722029678&P2=404&P3=2&P4=Y4pLmG2r2omwimRsI0PDPWBBZbTuEpQ5MpbIkTXSND9gopYhwOR70taRRSAUSYNsh3Hr29cpNBEDBLOttEC8Ug%3d%3d | unknown | — | — | whitelisted |
9100 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/6e6d05a2-47e8-42b8-85a0-e8b7ee48333a?P1=1722029678&P2=404&P3=2&P4=Y4pLmG2r2omwimRsI0PDPWBBZbTuEpQ5MpbIkTXSND9gopYhwOR70taRRSAUSYNsh3Hr29cpNBEDBLOttEC8Ug%3d%3d | unknown | — | — | whitelisted |
9100 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/6e6d05a2-47e8-42b8-85a0-e8b7ee48333a?P1=1722029678&P2=404&P3=2&P4=Y4pLmG2r2omwimRsI0PDPWBBZbTuEpQ5MpbIkTXSND9gopYhwOR70taRRSAUSYNsh3Hr29cpNBEDBLOttEC8Ug%3d%3d | unknown | — | — | whitelisted |
9100 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/6e6d05a2-47e8-42b8-85a0-e8b7ee48333a?P1=1722029678&P2=404&P3=2&P4=Y4pLmG2r2omwimRsI0PDPWBBZbTuEpQ5MpbIkTXSND9gopYhwOR70taRRSAUSYNsh3Hr29cpNBEDBLOttEC8Ug%3d%3d | unknown | — | — | whitelisted |
9100 | svchost.exe | GET | 206 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/6e6d05a2-47e8-42b8-85a0-e8b7ee48333a?P1=1722029678&P2=404&P3=2&P4=Y4pLmG2r2omwimRsI0PDPWBBZbTuEpQ5MpbIkTXSND9gopYhwOR70taRRSAUSYNsh3Hr29cpNBEDBLOttEC8Ug%3d%3d | unknown | — | — | whitelisted |
9100 | svchost.exe | HEAD | 200 | 152.199.19.161:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/63790111-8455-46c9-a54a-83249ebbe39a?P1=1722067048&P2=404&P3=2&P4=YC0DlQAoJ8uZ8g7NwQ322BB%2bKMeEF7wDdzJC6vrGShMgQ7rfm7A3XTKm1unEVdy5y%2flwuVhMcVgxkvmMEACw5Q%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5620 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4716 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
7856 | svchost.exe | 4.209.32.198:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7076 | msedge.exe | 140.82.121.4:443 | github.com | GITHUB | US | unknown |
8180 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7076 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7076 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
google.com |
| whitelisted |
github.com |
| shared |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
github.githubassets.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7076 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
7076 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
7076 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
7076 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] An application monitoring request to newrelic .com |