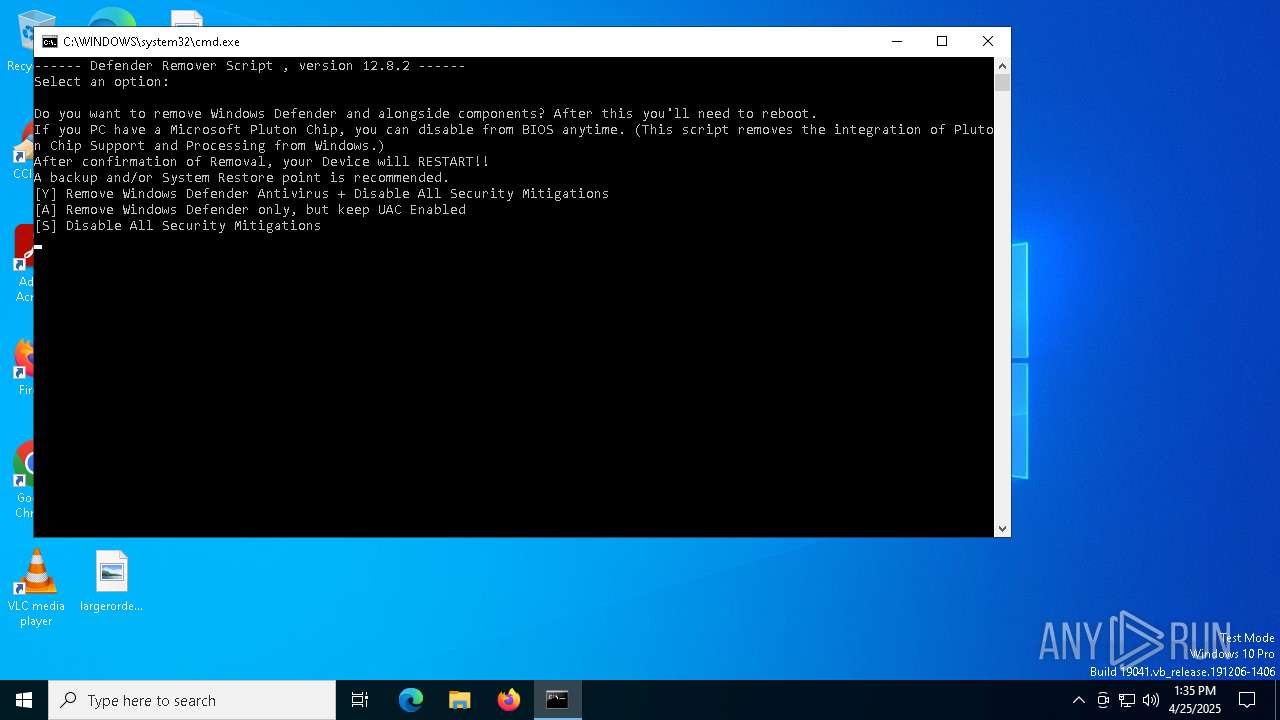
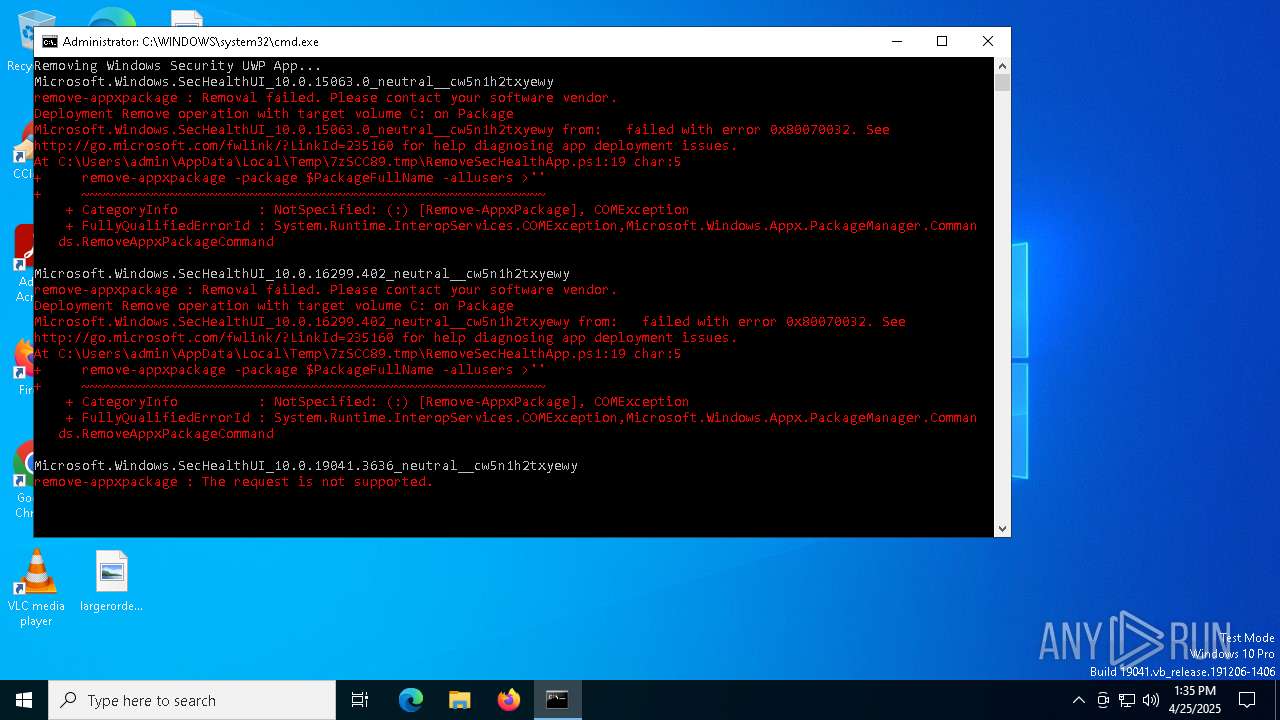
| File name: | DefenderRemover.exe |
| Full analysis: | https://app.any.run/tasks/1779db99-dd46-4c4b-88fd-789939dffbe2 |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2025, 13:35:14 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 29DF6172DA4B804F803E8987F6DF4CEA |
| SHA1: | 301CC52CB52207712FAC2E287D1E4ED8B17E253B |
| SHA256: | 7D5785C1760909AC5DC68CE57AABCF86AF2444AE42E19B568EB1E32D8A414913 |
| SSDEEP: | 24576:ghUhnNLVkbQOLIArg79Ie2cLKifsRHFhU4Ccqpzz4hzhm:ghUhnNLVkcOLIArg79Ie2cLKifsRHFhu |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 4620)
Disables Windows Defender
- regedit.exe (PID: 1628)
- regedit.exe (PID: 2772)
Changes Security Center notification settings
- regedit.exe (PID: 1628)
- regedit.exe (PID: 2772)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 2096)
UAC/LUA settings modification
- regedit.exe (PID: 5528)
SUSPICIOUS
The process creates files with name similar to system file names
- powershell.exe (PID: 4620)
Executable content was dropped or overwritten
- powershell.exe (PID: 4620)
- DefenderRemover.exe (PID: 4776)
Process drops legitimate windows executable
- powershell.exe (PID: 4620)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 2096)
Starts CMD.EXE for commands execution
- DefenderRemover.exe (PID: 4776)
- PowerRun.exe (PID: 644)
- PowerRun.exe (PID: 5132)
- PowerRun.exe (PID: 4188)
- PowerRun.exe (PID: 5008)
- PowerRun.exe (PID: 1452)
- PowerRun.exe (PID: 4652)
- PowerRun.exe (PID: 864)
- PowerRun.exe (PID: 6372)
- PowerRun.exe (PID: 4696)
- PowerRun.exe (PID: 3332)
- PowerRun.exe (PID: 1096)
- PowerRun.exe (PID: 5344)
- PowerRun.exe (PID: 7156)
- PowerRun.exe (PID: 1764)
- PowerRun.exe (PID: 6068)
- PowerRun.exe (PID: 5720)
- PowerRun.exe (PID: 856)
- PowerRun.exe (PID: 1096)
- PowerRun.exe (PID: 2800)
- PowerRun.exe (PID: 5936)
- PowerRun.exe (PID: 6184)
- PowerRun.exe (PID: 5544)
- PowerRun.exe (PID: 6108)
- PowerRun.exe (PID: 3008)
- PowerRun.exe (PID: 4164)
- PowerRun.exe (PID: 5528)
- PowerRun.exe (PID: 6828)
- PowerRun.exe (PID: 2420)
- PowerRun.exe (PID: 4728)
- PowerRun.exe (PID: 6112)
- PowerRun.exe (PID: 6468)
- PowerRun.exe (PID: 5512)
- PowerRun.exe (PID: 5212)
- PowerRun.exe (PID: 960)
- PowerRun.exe (PID: 6640)
- PowerRun.exe (PID: 5380)
- PowerRun.exe (PID: 4436)
- PowerRun.exe (PID: 5228)
- PowerRun.exe (PID: 2420)
- PowerRun.exe (PID: 864)
- PowerRun.exe (PID: 4736)
- PowerRun.exe (PID: 1132)
- PowerRun.exe (PID: 3896)
- PowerRun.exe (PID: 4728)
- PowerRun.exe (PID: 1168)
- PowerRun.exe (PID: 5512)
- PowerRun.exe (PID: 5408)
- PowerRun.exe (PID: 1272)
- PowerRun.exe (PID: 5008)
- PowerRun.exe (PID: 664)
- PowerRun.exe (PID: 2644)
- PowerRun.exe (PID: 3032)
- PowerRun.exe (PID: 6660)
- PowerRun.exe (PID: 2644)
- PowerRun.exe (PID: 3020)
- PowerRun.exe (PID: 5892)
- PowerRun.exe (PID: 6080)
- PowerRun.exe (PID: 6872)
- PowerRun.exe (PID: 2288)
Executing commands from a ".bat" file
- DefenderRemover.exe (PID: 4776)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2096)
The executable file from the user directory is run by the CMD process
- PowerRun.exe (PID: 3896)
- PowerRun.exe (PID: 3300)
- PowerRun.exe (PID: 2800)
- PowerRun.exe (PID: 5352)
- PowerRun.exe (PID: 3008)
- PowerRun.exe (PID: 6744)
- PowerRun.exe (PID: 4652)
- PowerRun.exe (PID: 4040)
- PowerRun.exe (PID: 4696)
- PowerRun.exe (PID: 780)
- PowerRun.exe (PID: 1180)
- PowerRun.exe (PID: 2552)
- PowerRun.exe (PID: 6676)
- PowerRun.exe (PID: 6108)
- PowerRun.exe (PID: 1240)
- PowerRun.exe (PID: 6004)
- PowerRun.exe (PID: 644)
- PowerRun.exe (PID: 6808)
- PowerRun.exe (PID: 5260)
- PowerRun.exe (PID: 1096)
- PowerRun.exe (PID: 6828)
- PowerRun.exe (PID: 6184)
- PowerRun.exe (PID: 5936)
- PowerRun.exe (PID: 736)
- PowerRun.exe (PID: 856)
- PowerRun.exe (PID: 6468)
- PowerRun.exe (PID: 4620)
- PowerRun.exe (PID: 6252)
- PowerRun.exe (PID: 5892)
- PowerRun.exe (PID: 5084)
- PowerRun.exe (PID: 2984)
- PowerRun.exe (PID: 5136)
- PowerRun.exe (PID: 4436)
- PowerRun.exe (PID: 1452)
- PowerRun.exe (PID: 632)
- PowerRun.exe (PID: 5360)
- PowerRun.exe (PID: 6080)
- PowerRun.exe (PID: 4528)
- PowerRun.exe (PID: 864)
- PowerRun.exe (PID: 5400)
- PowerRun.exe (PID: 4652)
- PowerRun.exe (PID: 5360)
- PowerRun.exe (PID: 2552)
- PowerRun.exe (PID: 5280)
- PowerRun.exe (PID: 4436)
- PowerRun.exe (PID: 4220)
- PowerRun.exe (PID: 960)
- PowerRun.exe (PID: 6872)
- PowerRun.exe (PID: 5380)
- PowerRun.exe (PID: 3896)
- PowerRun.exe (PID: 3020)
- PowerRun.exe (PID: 6112)
- PowerRun.exe (PID: 4696)
- PowerRun.exe (PID: 5212)
- PowerRun.exe (PID: 5304)
- PowerRun.exe (PID: 1912)
- PowerRun.exe (PID: 5260)
- PowerRun.exe (PID: 856)
- PowerRun.exe (PID: 872)
- PowerRun.exe (PID: 2420)
- PowerRun.exe (PID: 1272)
- PowerRun.exe (PID: 4164)
- PowerRun.exe (PID: 6828)
Application launched itself
- PowerRun.exe (PID: 3896)
- PowerRun.exe (PID: 3300)
- PowerRun.exe (PID: 5304)
- PowerRun.exe (PID: 2800)
- PowerRun.exe (PID: 5384)
- PowerRun.exe (PID: 960)
- PowerRun.exe (PID: 5352)
- PowerRun.exe (PID: 5360)
- PowerRun.exe (PID: 3008)
- PowerRun.exe (PID: 780)
- PowerRun.exe (PID: 6744)
- PowerRun.exe (PID: 4400)
- PowerRun.exe (PID: 4652)
- PowerRun.exe (PID: 5324)
- PowerRun.exe (PID: 4040)
- PowerRun.exe (PID: 4696)
- PowerRun.exe (PID: 5304)
- PowerRun.exe (PID: 968)
- PowerRun.exe (PID: 780)
- PowerRun.exe (PID: 6080)
- PowerRun.exe (PID: 1180)
- PowerRun.exe (PID: 2552)
- PowerRun.exe (PID: 4188)
- PowerRun.exe (PID: 4400)
- PowerRun.exe (PID: 6676)
- PowerRun.exe (PID: 2600)
- PowerRun.exe (PID: 6108)
- PowerRun.exe (PID: 5008)
- PowerRun.exe (PID: 1240)
- PowerRun.exe (PID: 5984)
- PowerRun.exe (PID: 6004)
- PowerRun.exe (PID: 904)
- PowerRun.exe (PID: 644)
- PowerRun.exe (PID: 5260)
- PowerRun.exe (PID: 5008)
- PowerRun.exe (PID: 1096)
- PowerRun.exe (PID: 1228)
- PowerRun.exe (PID: 6828)
- PowerRun.exe (PID: 5304)
- PowerRun.exe (PID: 1628)
- PowerRun.exe (PID: 904)
- PowerRun.exe (PID: 6184)
- PowerRun.exe (PID: 4880)
- PowerRun.exe (PID: 5780)
- PowerRun.exe (PID: 736)
- PowerRun.exe (PID: 5936)
- PowerRun.exe (PID: 6468)
- PowerRun.exe (PID: 4040)
- PowerRun.exe (PID: 3300)
- PowerRun.exe (PID: 856)
- PowerRun.exe (PID: 6808)
- PowerRun.exe (PID: 1764)
- PowerRun.exe (PID: 4620)
- PowerRun.exe (PID: 2420)
- PowerRun.exe (PID: 904)
- PowerRun.exe (PID: 6252)
- PowerRun.exe (PID: 6184)
- PowerRun.exe (PID: 2984)
- PowerRun.exe (PID: 5892)
- PowerRun.exe (PID: 1096)
- PowerRun.exe (PID: 5084)
- PowerRun.exe (PID: 632)
- PowerRun.exe (PID: 4436)
- PowerRun.exe (PID: 5892)
- PowerRun.exe (PID: 5228)
- PowerRun.exe (PID: 3332)
- PowerRun.exe (PID: 1452)
- PowerRun.exe (PID: 5380)
- PowerRun.exe (PID: 5136)
- PowerRun.exe (PID: 5544)
- PowerRun.exe (PID: 5400)
- PowerRun.exe (PID: 5360)
- PowerRun.exe (PID: 6372)
- PowerRun.exe (PID: 6080)
- PowerRun.exe (PID: 5400)
- PowerRun.exe (PID: 4528)
- PowerRun.exe (PID: 6660)
- PowerRun.exe (PID: 864)
- PowerRun.exe (PID: 4068)
- PowerRun.exe (PID: 5528)
- PowerRun.exe (PID: 6108)
- PowerRun.exe (PID: 4652)
- PowerRun.exe (PID: 5360)
- PowerRun.exe (PID: 2552)
- PowerRun.exe (PID: 6112)
- PowerRun.exe (PID: 660)
- PowerRun.exe (PID: 1052)
- PowerRun.exe (PID: 4436)
- PowerRun.exe (PID: 5576)
- PowerRun.exe (PID: 4220)
- PowerRun.exe (PID: 1240)
- PowerRun.exe (PID: 960)
- PowerRun.exe (PID: 5280)
- PowerRun.exe (PID: 2656)
- PowerRun.exe (PID: 4400)
- PowerRun.exe (PID: 6872)
- PowerRun.exe (PID: 6028)
- PowerRun.exe (PID: 5380)
- PowerRun.exe (PID: 2268)
- PowerRun.exe (PID: 3020)
- PowerRun.exe (PID: 4736)
- PowerRun.exe (PID: 5212)
- PowerRun.exe (PID: 5084)
- PowerRun.exe (PID: 4696)
- PowerRun.exe (PID: 4844)
- PowerRun.exe (PID: 6112)
- PowerRun.exe (PID: 3896)
- PowerRun.exe (PID: 4728)
- PowerRun.exe (PID: 968)
- PowerRun.exe (PID: 5260)
- PowerRun.exe (PID: 2064)
- PowerRun.exe (PID: 5984)
- PowerRun.exe (PID: 856)
- PowerRun.exe (PID: 1764)
- PowerRun.exe (PID: 1912)
- PowerRun.exe (PID: 1132)
- PowerRun.exe (PID: 2420)
- PowerRun.exe (PID: 1272)
- PowerRun.exe (PID: 5136)
- PowerRun.exe (PID: 6828)
- PowerRun.exe (PID: 4880)
- PowerRun.exe (PID: 6036)
- PowerRun.exe (PID: 872)
- PowerRun.exe (PID: 1052)
- PowerRun.exe (PID: 4164)
- PowerRun.exe (PID: 5304)
Reads security settings of Internet Explorer
- PowerRun.exe (PID: 4696)
- PowerRun.exe (PID: 5084)
- PowerRun.exe (PID: 1128)
- PowerRun.exe (PID: 1616)
- PowerRun.exe (PID: 5132)
- PowerRun.exe (PID: 4188)
- PowerRun.exe (PID: 5008)
- PowerRun.exe (PID: 1452)
- PowerRun.exe (PID: 4652)
- PowerRun.exe (PID: 864)
- PowerRun.exe (PID: 644)
- PowerRun.exe (PID: 6372)
- PowerRun.exe (PID: 3332)
- PowerRun.exe (PID: 4696)
- PowerRun.exe (PID: 1096)
- PowerRun.exe (PID: 7156)
- PowerRun.exe (PID: 5344)
- PowerRun.exe (PID: 856)
- PowerRun.exe (PID: 1096)
- PowerRun.exe (PID: 2800)
- PowerRun.exe (PID: 5936)
- PowerRun.exe (PID: 5544)
- PowerRun.exe (PID: 6184)
- PowerRun.exe (PID: 6108)
- PowerRun.exe (PID: 3008)
- PowerRun.exe (PID: 4728)
- PowerRun.exe (PID: 4164)
Uses REG/REGEDIT.EXE to modify registry
- PowerRun.exe (PID: 4696)
- PowerRun.exe (PID: 5084)
- cmd.exe (PID: 2096)
- PowerRun.exe (PID: 1128)
- PowerRun.exe (PID: 1616)
Reads the date of Windows installation
- PowerRun.exe (PID: 4696)
- PowerRun.exe (PID: 5084)
- PowerRun.exe (PID: 1128)
- PowerRun.exe (PID: 1616)
- PowerRun.exe (PID: 644)
- PowerRun.exe (PID: 4188)
- PowerRun.exe (PID: 5132)
- PowerRun.exe (PID: 1452)
- PowerRun.exe (PID: 5008)
- PowerRun.exe (PID: 4652)
- PowerRun.exe (PID: 864)
- PowerRun.exe (PID: 4696)
- PowerRun.exe (PID: 3332)
- PowerRun.exe (PID: 1096)
- PowerRun.exe (PID: 5344)
- PowerRun.exe (PID: 6068)
- PowerRun.exe (PID: 1764)
- PowerRun.exe (PID: 856)
- PowerRun.exe (PID: 1096)
- PowerRun.exe (PID: 2800)
- PowerRun.exe (PID: 5936)
- PowerRun.exe (PID: 5544)
- PowerRun.exe (PID: 6108)
- PowerRun.exe (PID: 4728)
The process executes Powershell scripts
- cmd.exe (PID: 2096)
Detected use of alternative data streams (AltDS)
- powershell.exe (PID: 4620)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 6080)
The process deletes folder without confirmation
- PowerRun.exe (PID: 4436)
- PowerRun.exe (PID: 5228)
- PowerRun.exe (PID: 6640)
- PowerRun.exe (PID: 2420)
- PowerRun.exe (PID: 864)
- PowerRun.exe (PID: 4736)
- PowerRun.exe (PID: 4728)
- PowerRun.exe (PID: 1132)
- PowerRun.exe (PID: 3896)
- PowerRun.exe (PID: 5512)
- PowerRun.exe (PID: 5408)
- PowerRun.exe (PID: 1272)
- PowerRun.exe (PID: 1168)
- PowerRun.exe (PID: 5008)
- PowerRun.exe (PID: 664)
- PowerRun.exe (PID: 2644)
- PowerRun.exe (PID: 6660)
- PowerRun.exe (PID: 2644)
- PowerRun.exe (PID: 5892)
- PowerRun.exe (PID: 2288)
- PowerRun.exe (PID: 3020)
- PowerRun.exe (PID: 3032)
- PowerRun.exe (PID: 6080)
- PowerRun.exe (PID: 6872)
Found strings related to reading or modifying Windows Defender settings
- PowerRun.exe (PID: 6640)
- PowerRun.exe (PID: 864)
- PowerRun.exe (PID: 5228)
- PowerRun.exe (PID: 2420)
- PowerRun.exe (PID: 1132)
- PowerRun.exe (PID: 1272)
- PowerRun.exe (PID: 2644)
- PowerRun.exe (PID: 5008)
- PowerRun.exe (PID: 664)
- PowerRun.exe (PID: 6660)
- PowerRun.exe (PID: 2644)
- PowerRun.exe (PID: 3032)
- PowerRun.exe (PID: 5892)
- PowerRun.exe (PID: 6872)
The system shut down or reboot
- cmd.exe (PID: 2096)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2096)
INFO
Reads the computer name
- DefenderRemover.exe (PID: 4776)
- DismHost.exe (PID: 6080)
- PowerRun.exe (PID: 3896)
- PowerRun.exe (PID: 5304)
- PowerRun.exe (PID: 3300)
- PowerRun.exe (PID: 2800)
- PowerRun.exe (PID: 5384)
- PowerRun.exe (PID: 4696)
- PowerRun.exe (PID: 960)
- PowerRun.exe (PID: 5084)
- PowerRun.exe (PID: 1128)
- PowerRun.exe (PID: 5352)
- PowerRun.exe (PID: 3008)
- PowerRun.exe (PID: 1616)
- PowerRun.exe (PID: 780)
- PowerRun.exe (PID: 6744)
- PowerRun.exe (PID: 644)
- PowerRun.exe (PID: 5360)
- PowerRun.exe (PID: 4652)
- PowerRun.exe (PID: 5132)
- PowerRun.exe (PID: 4400)
- PowerRun.exe (PID: 4040)
- PowerRun.exe (PID: 4188)
- PowerRun.exe (PID: 5324)
- PowerRun.exe (PID: 4696)
- PowerRun.exe (PID: 5008)
- PowerRun.exe (PID: 968)
- PowerRun.exe (PID: 5304)
- PowerRun.exe (PID: 780)
- PowerRun.exe (PID: 1452)
- PowerRun.exe (PID: 1180)
- PowerRun.exe (PID: 6080)
- PowerRun.exe (PID: 4652)
- PowerRun.exe (PID: 2552)
- PowerRun.exe (PID: 4188)
- PowerRun.exe (PID: 864)
- PowerRun.exe (PID: 6676)
- PowerRun.exe (PID: 4400)
- PowerRun.exe (PID: 2600)
- PowerRun.exe (PID: 6372)
- PowerRun.exe (PID: 6108)
- PowerRun.exe (PID: 1240)
- PowerRun.exe (PID: 5984)
- PowerRun.exe (PID: 3332)
- PowerRun.exe (PID: 4696)
- PowerRun.exe (PID: 6004)
- PowerRun.exe (PID: 904)
- PowerRun.exe (PID: 5780)
- PowerRun.exe (PID: 7156)
- PowerRun.exe (PID: 6808)
- PowerRun.exe (PID: 644)
- PowerRun.exe (PID: 5344)
- PowerRun.exe (PID: 1228)
- PowerRun.exe (PID: 1764)
- PowerRun.exe (PID: 6068)
- PowerRun.exe (PID: 6828)
- PowerRun.exe (PID: 5304)
- PowerRun.exe (PID: 6184)
- PowerRun.exe (PID: 904)
- PowerRun.exe (PID: 856)
- PowerRun.exe (PID: 5936)
- PowerRun.exe (PID: 736)
- PowerRun.exe (PID: 4040)
- PowerRun.exe (PID: 6468)
- PowerRun.exe (PID: 3300)
- PowerRun.exe (PID: 5936)
- PowerRun.exe (PID: 856)
- PowerRun.exe (PID: 5544)
- PowerRun.exe (PID: 6184)
- PowerRun.exe (PID: 4620)
- PowerRun.exe (PID: 1764)
- PowerRun.exe (PID: 904)
- PowerRun.exe (PID: 5892)
- PowerRun.exe (PID: 3008)
- PowerRun.exe (PID: 2984)
- PowerRun.exe (PID: 1096)
- PowerRun.exe (PID: 4728)
- PowerRun.exe (PID: 4164)
Checks supported languages
- DismHost.exe (PID: 6080)
- DefenderRemover.exe (PID: 4776)
- PowerRun.exe (PID: 3896)
- PowerRun.exe (PID: 5304)
- PowerRun.exe (PID: 3300)
- PowerRun.exe (PID: 5384)
- PowerRun.exe (PID: 4696)
- PowerRun.exe (PID: 2800)
- PowerRun.exe (PID: 960)
- PowerRun.exe (PID: 5084)
- PowerRun.exe (PID: 1128)
- PowerRun.exe (PID: 5360)
- PowerRun.exe (PID: 3008)
- PowerRun.exe (PID: 5352)
- PowerRun.exe (PID: 1616)
- PowerRun.exe (PID: 780)
- PowerRun.exe (PID: 644)
- PowerRun.exe (PID: 4400)
- PowerRun.exe (PID: 4652)
- PowerRun.exe (PID: 5324)
- PowerRun.exe (PID: 5132)
- PowerRun.exe (PID: 4040)
- PowerRun.exe (PID: 4188)
- PowerRun.exe (PID: 4696)
- PowerRun.exe (PID: 5304)
- PowerRun.exe (PID: 968)
- PowerRun.exe (PID: 5008)
- PowerRun.exe (PID: 780)
- PowerRun.exe (PID: 6744)
- PowerRun.exe (PID: 1452)
- PowerRun.exe (PID: 6080)
- PowerRun.exe (PID: 1180)
- PowerRun.exe (PID: 4652)
- PowerRun.exe (PID: 4188)
- PowerRun.exe (PID: 2552)
- PowerRun.exe (PID: 864)
- PowerRun.exe (PID: 6676)
- PowerRun.exe (PID: 2600)
- PowerRun.exe (PID: 6372)
- PowerRun.exe (PID: 4400)
- PowerRun.exe (PID: 6108)
- PowerRun.exe (PID: 4696)
- PowerRun.exe (PID: 5008)
- PowerRun.exe (PID: 1240)
- PowerRun.exe (PID: 3332)
- PowerRun.exe (PID: 5984)
- PowerRun.exe (PID: 6004)
- PowerRun.exe (PID: 1096)
- PowerRun.exe (PID: 644)
- PowerRun.exe (PID: 904)
- PowerRun.exe (PID: 7156)
- PowerRun.exe (PID: 6808)
- PowerRun.exe (PID: 5780)
- PowerRun.exe (PID: 5260)
- PowerRun.exe (PID: 5008)
- PowerRun.exe (PID: 1228)
- PowerRun.exe (PID: 1096)
- PowerRun.exe (PID: 5344)
- PowerRun.exe (PID: 1764)
- PowerRun.exe (PID: 6068)
- PowerRun.exe (PID: 6828)
- PowerRun.exe (PID: 5720)
- PowerRun.exe (PID: 6184)
- PowerRun.exe (PID: 5304)
- PowerRun.exe (PID: 904)
- PowerRun.exe (PID: 1096)
- PowerRun.exe (PID: 856)
- PowerRun.exe (PID: 5936)
- PowerRun.exe (PID: 736)
- PowerRun.exe (PID: 2800)
- PowerRun.exe (PID: 4880)
- PowerRun.exe (PID: 6468)
- PowerRun.exe (PID: 5936)
- PowerRun.exe (PID: 3300)
- PowerRun.exe (PID: 4040)
- PowerRun.exe (PID: 856)
- PowerRun.exe (PID: 6184)
- PowerRun.exe (PID: 5544)
- PowerRun.exe (PID: 2420)
- PowerRun.exe (PID: 6252)
- PowerRun.exe (PID: 1764)
- PowerRun.exe (PID: 4620)
- PowerRun.exe (PID: 6108)
- PowerRun.exe (PID: 904)
- PowerRun.exe (PID: 5892)
- PowerRun.exe (PID: 4164)
- PowerRun.exe (PID: 1096)
- PowerRun.exe (PID: 3008)
- PowerRun.exe (PID: 2984)
- PowerRun.exe (PID: 6184)
- PowerRun.exe (PID: 5084)
- PowerRun.exe (PID: 4728)
- PowerRun.exe (PID: 5380)
- PowerRun.exe (PID: 5136)
- PowerRun.exe (PID: 6828)
The sample compiled with english language support
- DefenderRemover.exe (PID: 4776)
- powershell.exe (PID: 4620)
Create files in a temporary directory
- DefenderRemover.exe (PID: 4776)
- PowerRun.exe (PID: 3896)
- PowerRun.exe (PID: 2800)
- PowerRun.exe (PID: 3300)
- PowerRun.exe (PID: 5352)
- PowerRun.exe (PID: 3008)
- PowerRun.exe (PID: 6744)
- PowerRun.exe (PID: 4652)
- PowerRun.exe (PID: 4040)
- PowerRun.exe (PID: 4696)
- PowerRun.exe (PID: 780)
- PowerRun.exe (PID: 1180)
- PowerRun.exe (PID: 2552)
- PowerRun.exe (PID: 6676)
- PowerRun.exe (PID: 6108)
- PowerRun.exe (PID: 1240)
- PowerRun.exe (PID: 644)
- PowerRun.exe (PID: 6004)
- PowerRun.exe (PID: 6808)
- PowerRun.exe (PID: 5260)
- PowerRun.exe (PID: 6828)
- PowerRun.exe (PID: 1096)
- PowerRun.exe (PID: 6184)
- PowerRun.exe (PID: 5936)
- PowerRun.exe (PID: 736)
- PowerRun.exe (PID: 6468)
- PowerRun.exe (PID: 856)
- PowerRun.exe (PID: 4620)
- PowerRun.exe (PID: 6252)
- PowerRun.exe (PID: 5892)
- PowerRun.exe (PID: 2984)
- PowerRun.exe (PID: 5084)
The executable file from the user directory is run by the Powershell process
- DismHost.exe (PID: 6080)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4620)
Reads Environment values
- DismHost.exe (PID: 6080)
Reads mouse settings
- PowerRun.exe (PID: 3896)
- PowerRun.exe (PID: 3300)
- PowerRun.exe (PID: 5304)
- PowerRun.exe (PID: 5384)
- PowerRun.exe (PID: 4696)
- PowerRun.exe (PID: 2800)
- PowerRun.exe (PID: 5084)
- PowerRun.exe (PID: 960)
- PowerRun.exe (PID: 1128)
- PowerRun.exe (PID: 5352)
- PowerRun.exe (PID: 5360)
- PowerRun.exe (PID: 3008)
- PowerRun.exe (PID: 1616)
- PowerRun.exe (PID: 780)
- PowerRun.exe (PID: 6744)
- PowerRun.exe (PID: 644)
- PowerRun.exe (PID: 4652)
- PowerRun.exe (PID: 4400)
- PowerRun.exe (PID: 5132)
- PowerRun.exe (PID: 5324)
- PowerRun.exe (PID: 4040)
- PowerRun.exe (PID: 4188)
- PowerRun.exe (PID: 5304)
- PowerRun.exe (PID: 4696)
- PowerRun.exe (PID: 5008)
- PowerRun.exe (PID: 968)
- PowerRun.exe (PID: 780)
- PowerRun.exe (PID: 1452)
- PowerRun.exe (PID: 6080)
- PowerRun.exe (PID: 1180)
- PowerRun.exe (PID: 4652)
- PowerRun.exe (PID: 4188)
- PowerRun.exe (PID: 2552)
- PowerRun.exe (PID: 4400)
- PowerRun.exe (PID: 6372)
- PowerRun.exe (PID: 2600)
- PowerRun.exe (PID: 864)
- PowerRun.exe (PID: 6676)
- PowerRun.exe (PID: 6108)
- PowerRun.exe (PID: 4696)
- PowerRun.exe (PID: 5008)
- PowerRun.exe (PID: 3332)
- PowerRun.exe (PID: 5984)
- PowerRun.exe (PID: 1240)
- PowerRun.exe (PID: 1096)
- PowerRun.exe (PID: 904)
- PowerRun.exe (PID: 644)
- PowerRun.exe (PID: 7156)
- PowerRun.exe (PID: 6808)
- PowerRun.exe (PID: 5344)
- PowerRun.exe (PID: 5780)
- PowerRun.exe (PID: 5260)
- PowerRun.exe (PID: 5008)
- PowerRun.exe (PID: 1228)
- PowerRun.exe (PID: 1096)
- PowerRun.exe (PID: 6828)
- PowerRun.exe (PID: 1764)
- PowerRun.exe (PID: 6068)
- PowerRun.exe (PID: 5720)
- PowerRun.exe (PID: 6184)
- PowerRun.exe (PID: 856)
- PowerRun.exe (PID: 5304)
- PowerRun.exe (PID: 904)
- PowerRun.exe (PID: 1096)
- PowerRun.exe (PID: 736)
- PowerRun.exe (PID: 4880)
- PowerRun.exe (PID: 2800)
- PowerRun.exe (PID: 5936)
- PowerRun.exe (PID: 3300)
- PowerRun.exe (PID: 4040)
- PowerRun.exe (PID: 6468)
- PowerRun.exe (PID: 6184)
- PowerRun.exe (PID: 1764)
- PowerRun.exe (PID: 856)
- PowerRun.exe (PID: 6252)
- PowerRun.exe (PID: 6108)
- PowerRun.exe (PID: 904)
- PowerRun.exe (PID: 5892)
- PowerRun.exe (PID: 3008)
- PowerRun.exe (PID: 6184)
- PowerRun.exe (PID: 2984)
- PowerRun.exe (PID: 4164)
- PowerRun.exe (PID: 5084)
- PowerRun.exe (PID: 4728)
- PowerRun.exe (PID: 5380)
- PowerRun.exe (PID: 5136)
- PowerRun.exe (PID: 6828)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:11:18 16:27:35+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 104960 |
| InitializedDataSize: | 314368 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x14b04 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 12.8.2.0 |
| ProductVersionNumber: | 12.8.2.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Gallery Inc |
| FileDescription: | Defender Remover |
| FileVersion: | 12.8.2 |
| LegalCopyright: | Gallery Inc. |
| ProductName: | Defender Remover |
| ProductVersion: | 12.8.2 |
Total processes
460
Monitored processes
328
Malicious processes
8
Suspicious processes
25
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | "C:\WINDOWS\regedit.exe" /s "C:\Users\admin\AppData\Local\Temp\7zSCC89.tmp\Remove_defender\NomoreDelayandTimeouts.reg" | C:\Windows\regedit.exe | — | PowerRun.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Registry Editor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | PowerRun cmd.exe /c del /f ""C:\Windows\SysWOW64\DeviceCensus.exe"" | C:\Users\admin\AppData\Local\Temp\7zSCC89.tmp\PowerRun.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Description: PowerRun Exit code: 0 Version: 1.6.0.0 Modules
| |||||||||||||||
| 644 | "C:\Users\admin\AppData\Local\Temp\7zSCC89.tmp\PowerRun.exe" /TI/ cmd.exe /c del /f ""C:\Windows\System32\SecurityAndMaintenance_Error.png"" | C:\Users\admin\AppData\Local\Temp\7zSCC89.tmp\PowerRun.exe | — | PowerRun.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: PowerRun Exit code: 0 Version: 1.6.0.0 Modules
| |||||||||||||||
| 644 | PowerRun cmd.exe /c del /f ""C:\Windows\System32\wscproxystub.dll"" | C:\Users\admin\AppData\Local\Temp\7zSCC89.tmp\PowerRun.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Description: PowerRun Exit code: 0 Version: 1.6.0.0 Modules
| |||||||||||||||
| 660 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | "C:\WINDOWS\system32\cmd.exe" /c del /f ""C:\Windows\System32\SecurityHealthProxyStub.dll"" | C:\Windows\System32\cmd.exe | — | PowerRun.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | "C:\Users\admin\AppData\Local\Temp\7zSCC89.tmp\PowerRun.exe" cmd.exe /c rmdir "C:\Program Files (x86)\Windows Defender Advanced Threat Protection" /s /q | C:\Users\admin\AppData\Local\Temp\7zSCC89.tmp\PowerRun.exe | PowerRun.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: PowerRun Exit code: 0 Version: 1.6.0.0 Modules
| |||||||||||||||
| 664 | "C:\WINDOWS\system32\cmd.exe" /c del /f ""C:\Windows\SysWOW64\smartscreenps.dll"" | C:\Windows\System32\cmd.exe | — | PowerRun.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 664 | "C:\Users\admin\AppData\Local\Temp\7zSCC89.tmp\PowerRun.exe" /TI/ cmd.exe /c rmdir "C:\Windows\System32\WindowsPowerShell\v1.0\Modules\DefenderPerformance" /s /q | C:\Users\admin\AppData\Local\Temp\7zSCC89.tmp\PowerRun.exe | — | PowerRun.exe | |||||||||||
User: SYSTEM Integrity Level: SYSTEM Description: PowerRun Exit code: 0 Version: 1.6.0.0 Modules
| |||||||||||||||
| 664 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
29 933
Read events
29 279
Write events
414
Delete events
240
Modification events
| (PID) Process: | (856) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | VerboseStatus |
Value: 0 | |||
| (PID) Process: | (856) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Reliability |
| Operation: | write | Name: | ShutdownReasonOn |
Value: 0 | |||
| (PID) Process: | (856) regedit.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Reliability |
| Operation: | write | Name: | ShutdownReasonOn |
Value: 0 | |||
| (PID) Process: | (856) regedit.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | AutoEndTasks |
Value: 1 | |||
| (PID) Process: | (856) regedit.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | MenuShowDelay |
Value: 1 | |||
| (PID) Process: | (856) regedit.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | ForegroundLockTimeout |
Value: 0 | |||
| (PID) Process: | (856) regedit.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | WaitToKillAppTimeout |
Value: 1 | |||
| (PID) Process: | (856) regedit.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | WaitToKillServiceTimeout |
Value: 1 | |||
| (PID) Process: | (856) regedit.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | HungAppTimeout |
Value: 1000 | |||
| (PID) Process: | (856) regedit.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop |
| Operation: | write | Name: | LowLevelHooksTimeout |
Value: 1 | |||
Executable files
51
Suspicious files
568
Text files
200
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4776 | DefenderRemover.exe | C:\Users\admin\AppData\Local\Temp\7zSCC89.tmp\Remove_Defender\NomoreDelayandTimeouts.reg | text | |
MD5:59D99738DE1C67233FA6C5595AE6BB66 | SHA256:FFB369C1B359A99845D2B1C4FC8CAAFBA2E157FB7D152C2AEBC4E38ACCFB9BA7 | |||
| 4776 | DefenderRemover.exe | C:\Users\admin\AppData\Local\Temp\7zSCC89.tmp\Script_Run.bat | text | |
MD5:44104C19893590DE7BBC2A2CBBA9B6E7 | SHA256:32AD97E2B83D1EB8B49C2E54ED30C22E36DC21933CA6BAC3F66635868AAAA7CB | |||
| 4620 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_lmwjg4d1.2w3.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4620 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_y4ykotht.s0a.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4620 | powershell.exe | C:\Users\admin\AppData\Local\Temp\BB860238-90D7-4990-9647-7B57FC22C373\AppxProvider.dll | executable | |
MD5:396C483D62FEA5FA0FD442C8DC99D4EF | SHA256:36F2AF43F10FD76FEEF65BF574D79D3E27FD40DAF61249880511543C1F17AD91 | |||
| 4620 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_31xzeh0y.2gu.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4620 | powershell.exe | C:\Users\admin\AppData\Local\Temp\BB860238-90D7-4990-9647-7B57FC22C373\AssocProvider.dll | executable | |
MD5:B7DB592706D3EEFBCF0D5A166D462E56 | SHA256:DE21321272862E7C332E1724DC315F06F3ABE7A0340E61D351CAB208D6BBF059 | |||
| 4620 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_juyp5ppa.3hs.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4776 | DefenderRemover.exe | C:\Users\admin\AppData\Local\Temp\7zSCC89.tmp\Remove_SecurityComp\Remove_SecurityComp.reg | text | |
MD5:3B9A9024F8959120754A6BEFAF12E4BD | SHA256:C717111084EC331D2D5476D86ED098F5ACF939ECD6A15EFDEB5214FC2F6CF674 | |||
| 4776 | DefenderRemover.exe | C:\Users\admin\AppData\Local\Temp\7zSCC89.tmp\Remove_Defender\Output.reg | text | |
MD5:8FEF3E73F3DA0CF6B5CB34DA20309236 | SHA256:9DDB1443316F09391064D02668608E881C15E25DB9C6667418D086A8F234BD16 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
18
DNS requests
14
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.16.148:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3180 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3180 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.16.148:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3180 | SIHClient.exe | 52.149.20.212:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |