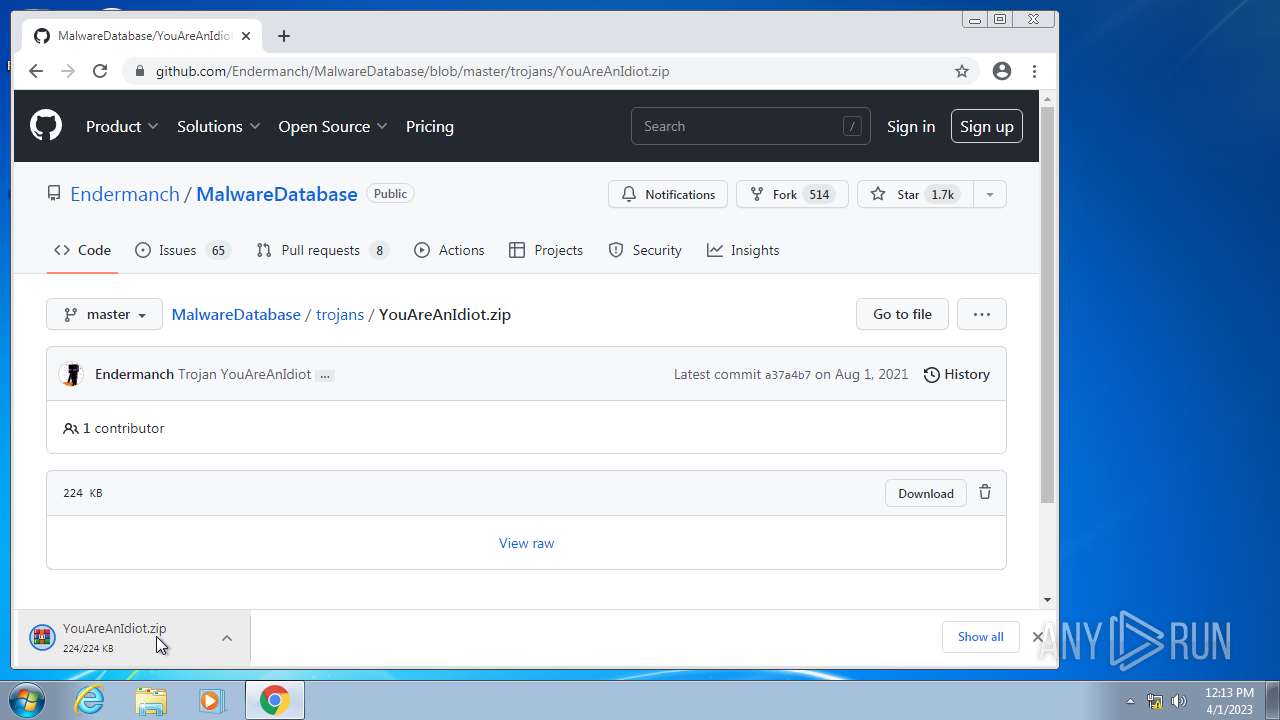
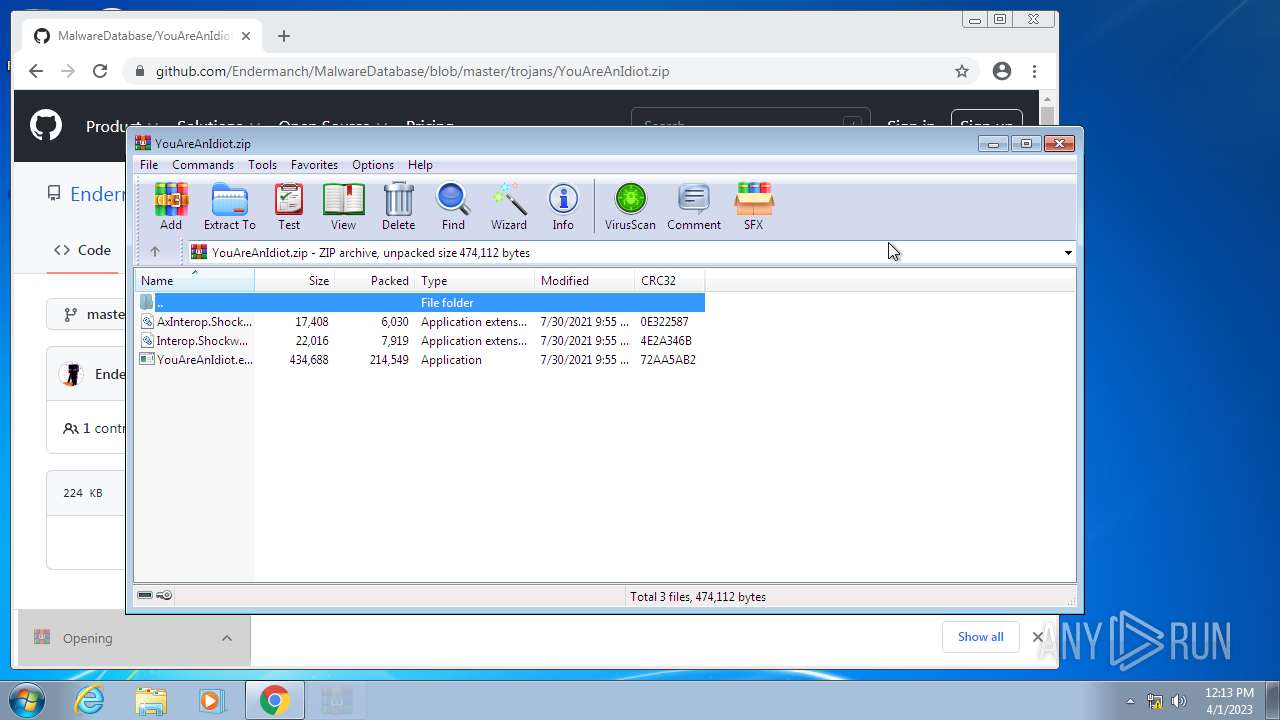
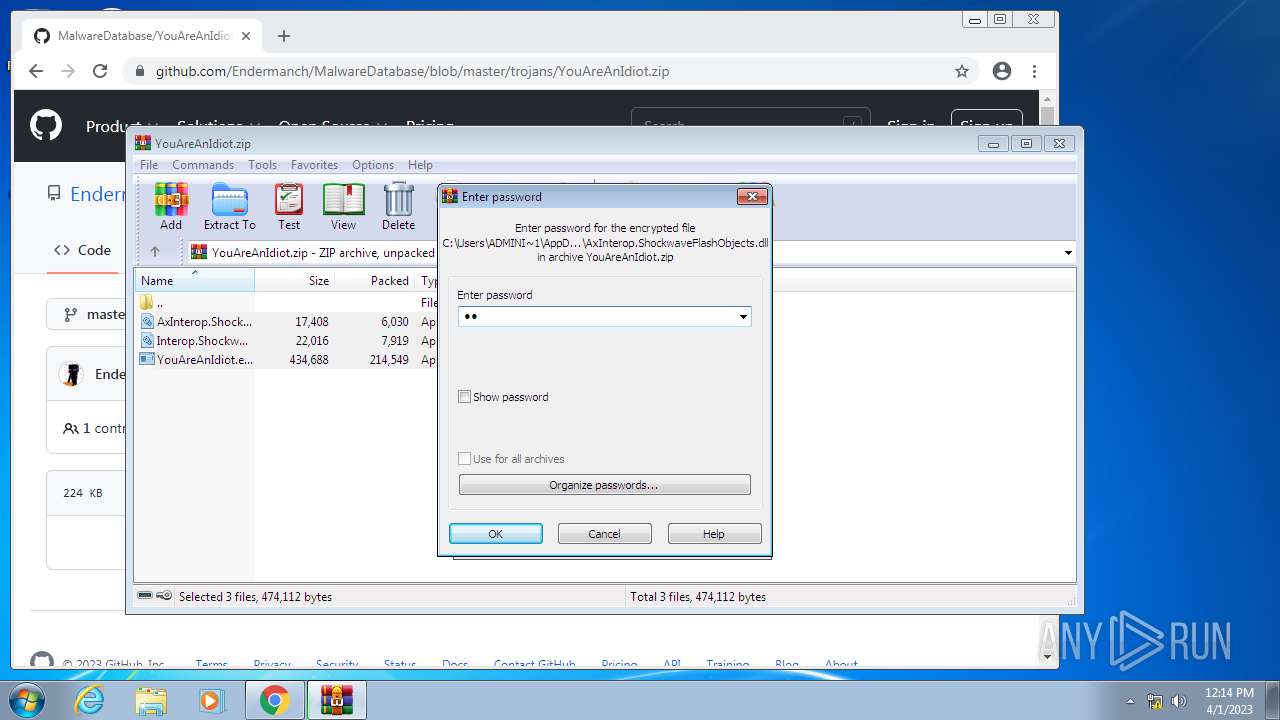
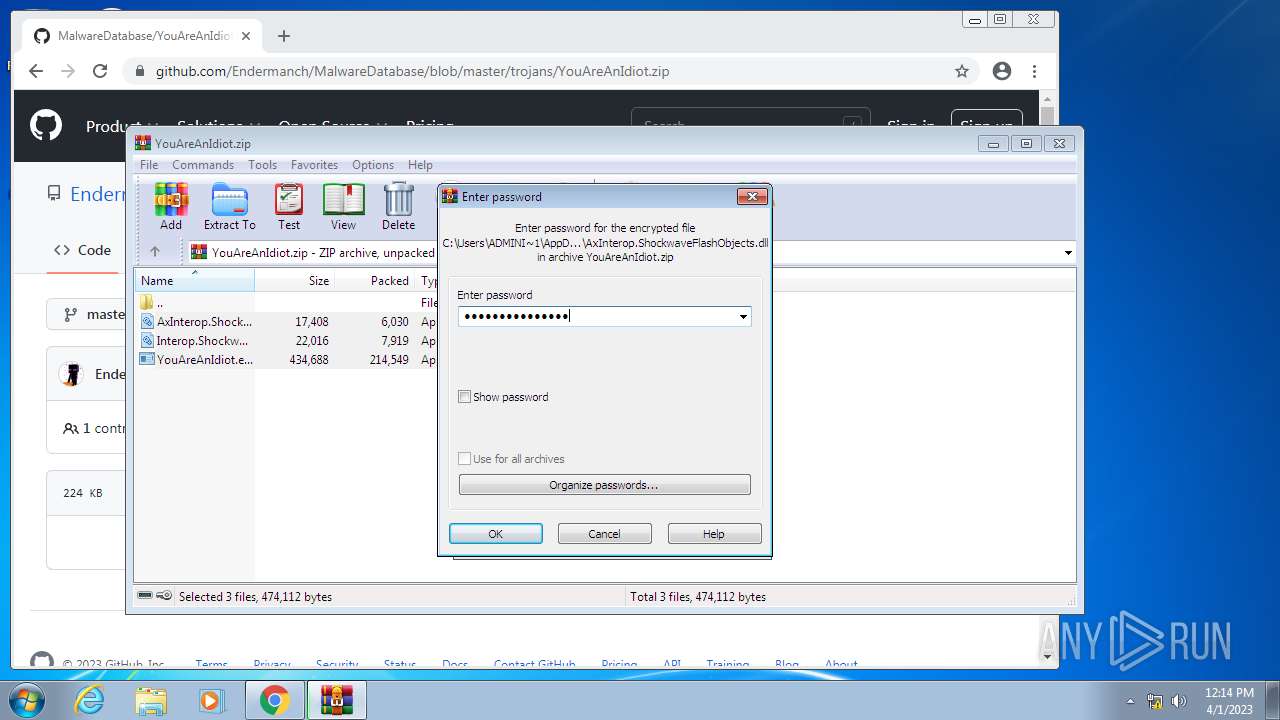
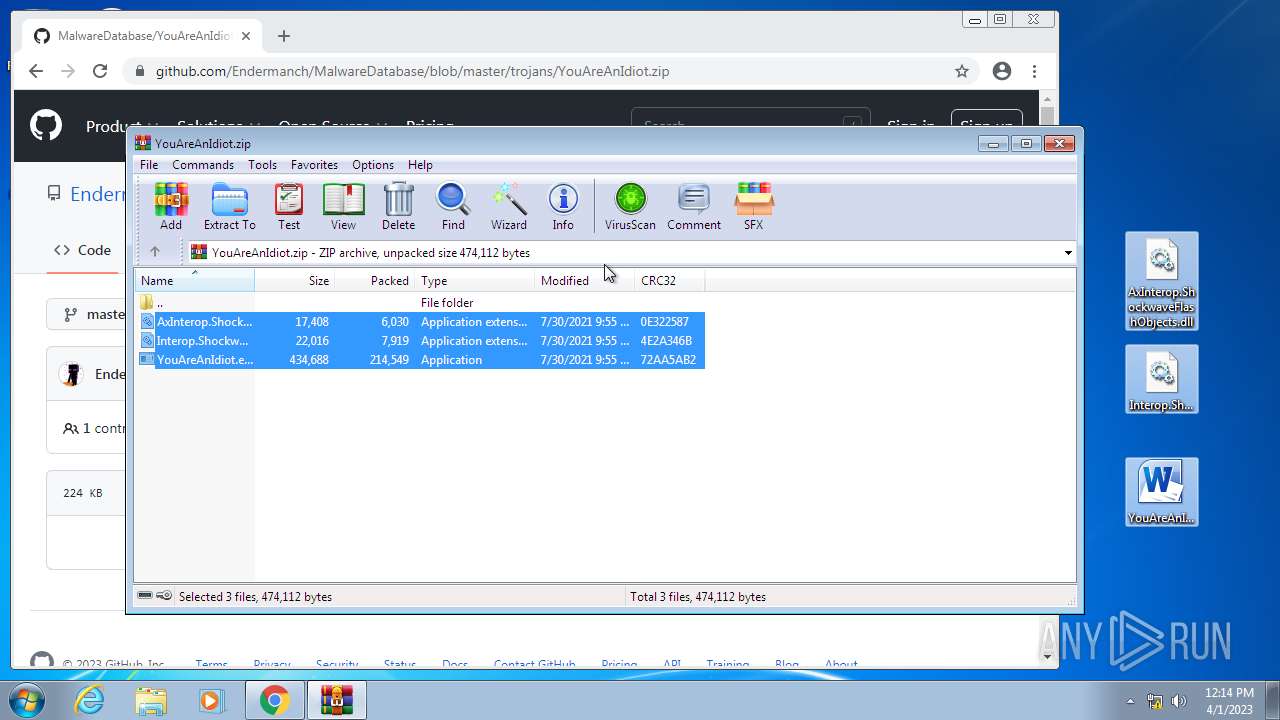
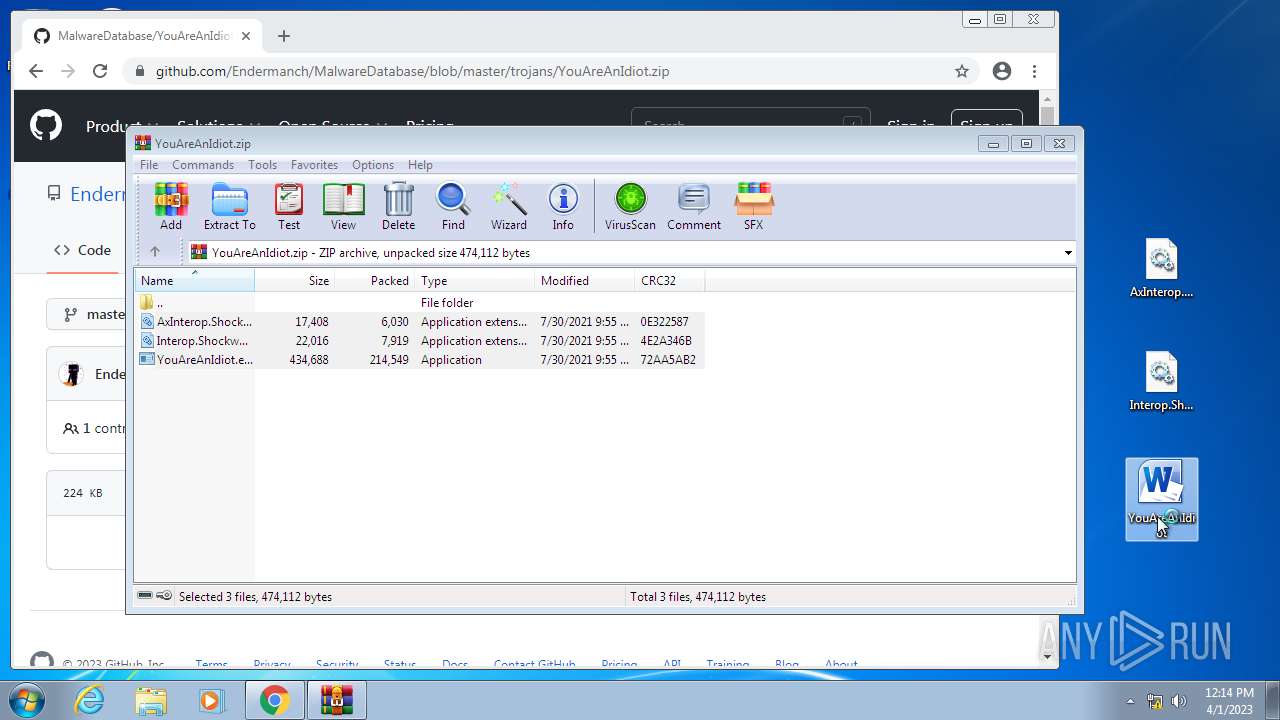
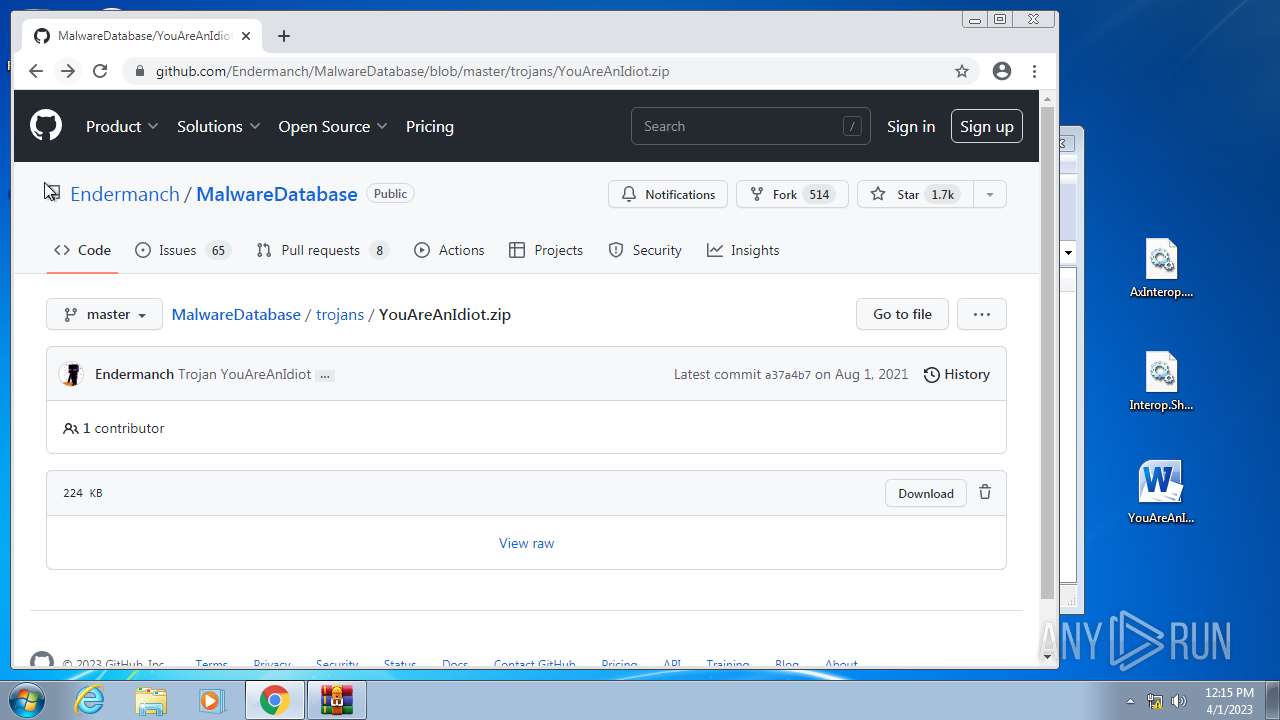
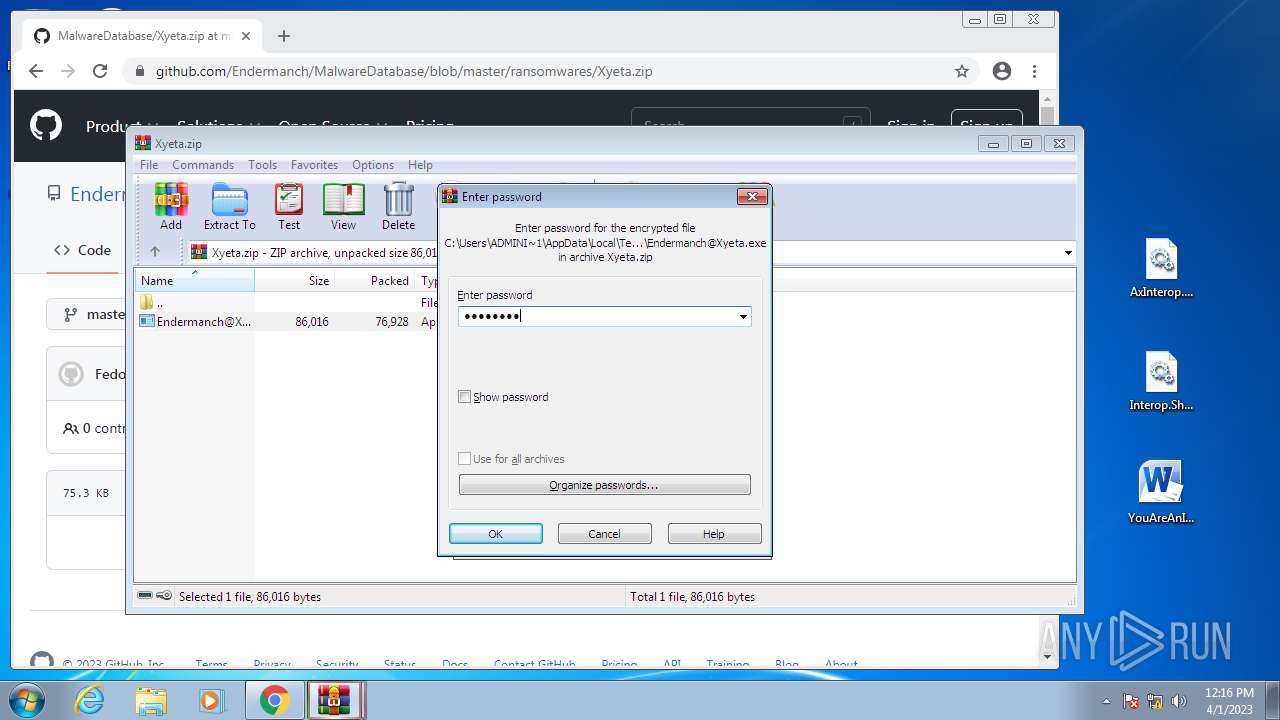
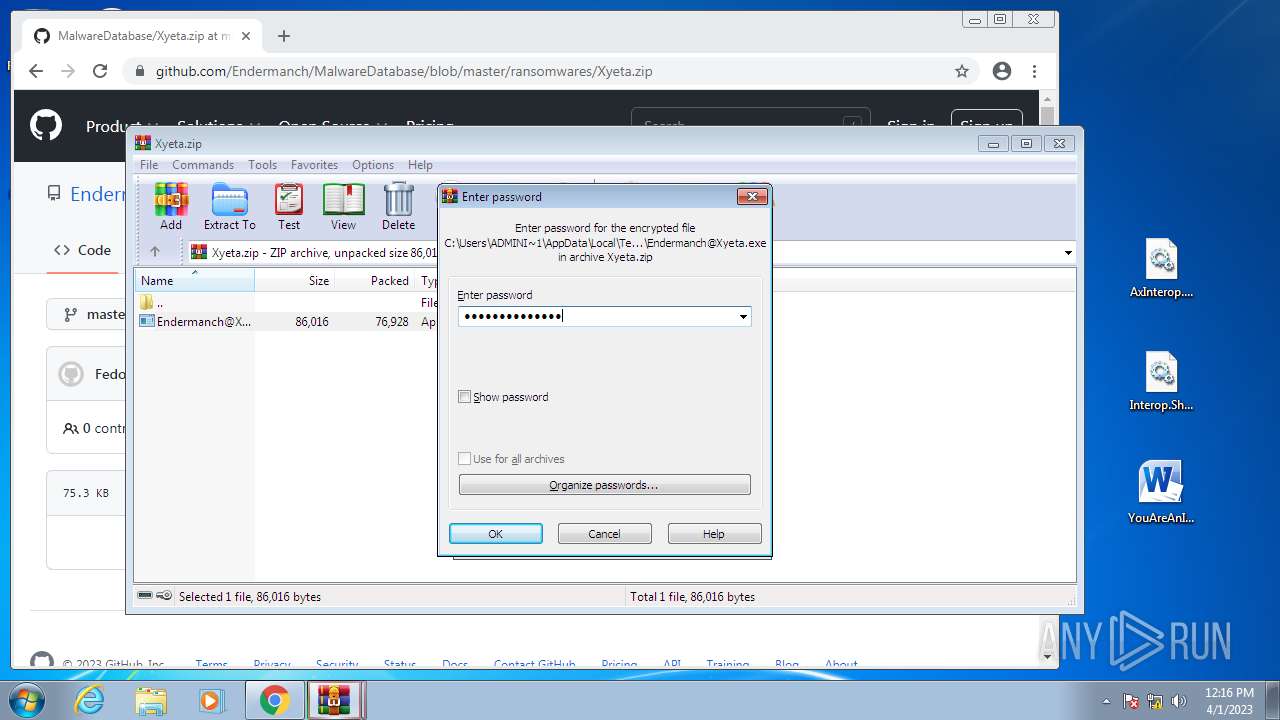
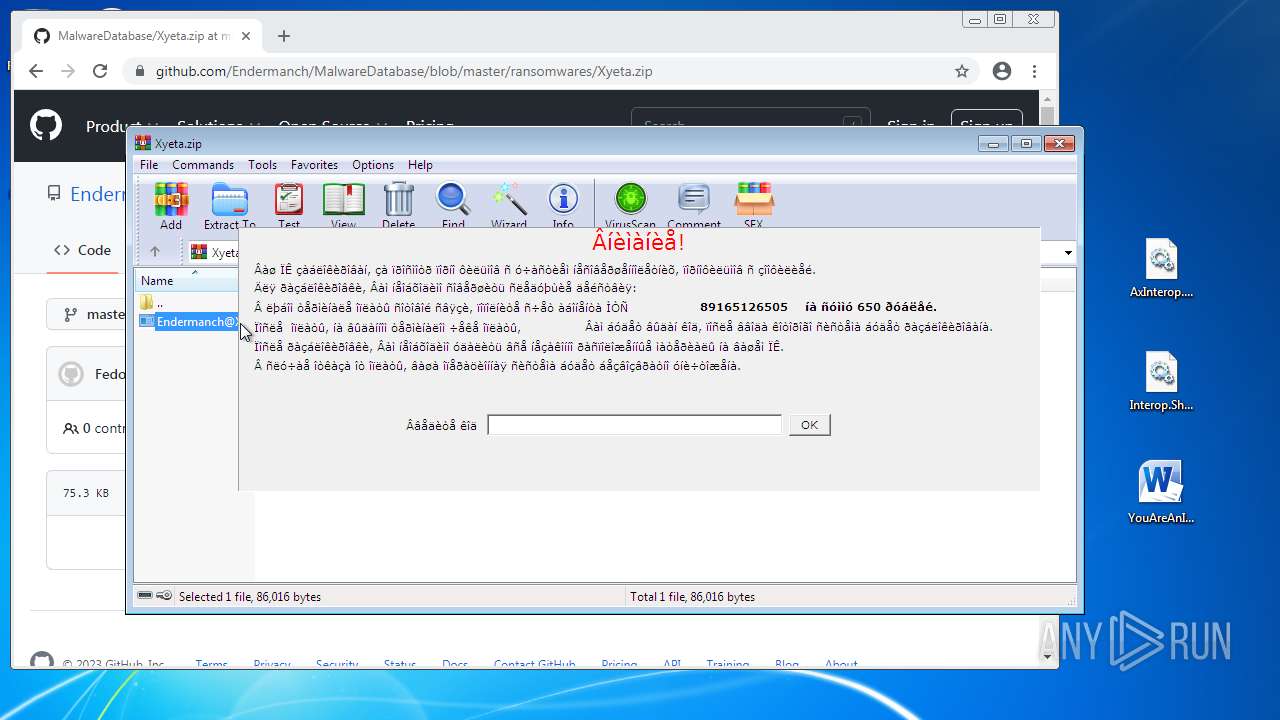
| File name: | CoinMine.exe |
| Full analysis: | https://app.any.run/tasks/ab085a6b-ebcd-4ea4-bce2-c3937550a435 |
| Verdict: | Malicious activity |
| Analysis date: | April 01, 2023, 11:11:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 49F6BDCF34BC0BE593A9E7DD64AA6E62 |
| SHA1: | CD523DDA29635FD2F159457C485C055D2920033B |
| SHA256: | 7D2E4A096CFB9DA6EF9B1757B36C6FB462B39ADBF927FECC4D10EF8D6A6DCCB1 |
| SSDEEP: | 24576:BO/yiVlOzZoncHBbqjDlnGacRBk17ti1BeNBrx2m97Mj59iM9rG:BHOyocRq1nGP6iWNBrxnlMj59iwrG |
MALICIOUS
Steals credentials from Web Browsers
- taskhost.exe (PID: 2900)
Changes the autorun value in the registry
- regsvr32.exe (PID: 3124)
- unregmp2.exe (PID: 2200)
Create files in the Startup directory
- regsvr32.exe (PID: 3124)
Application was dropped or rewritten from another process
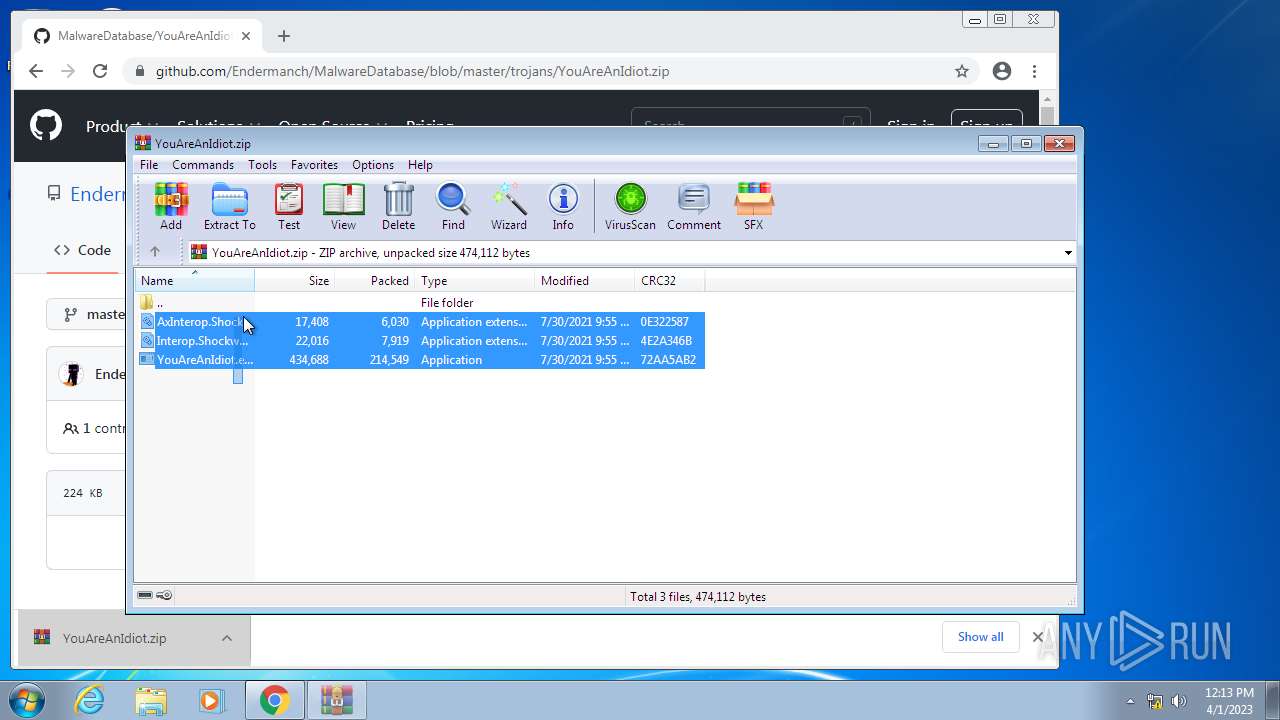
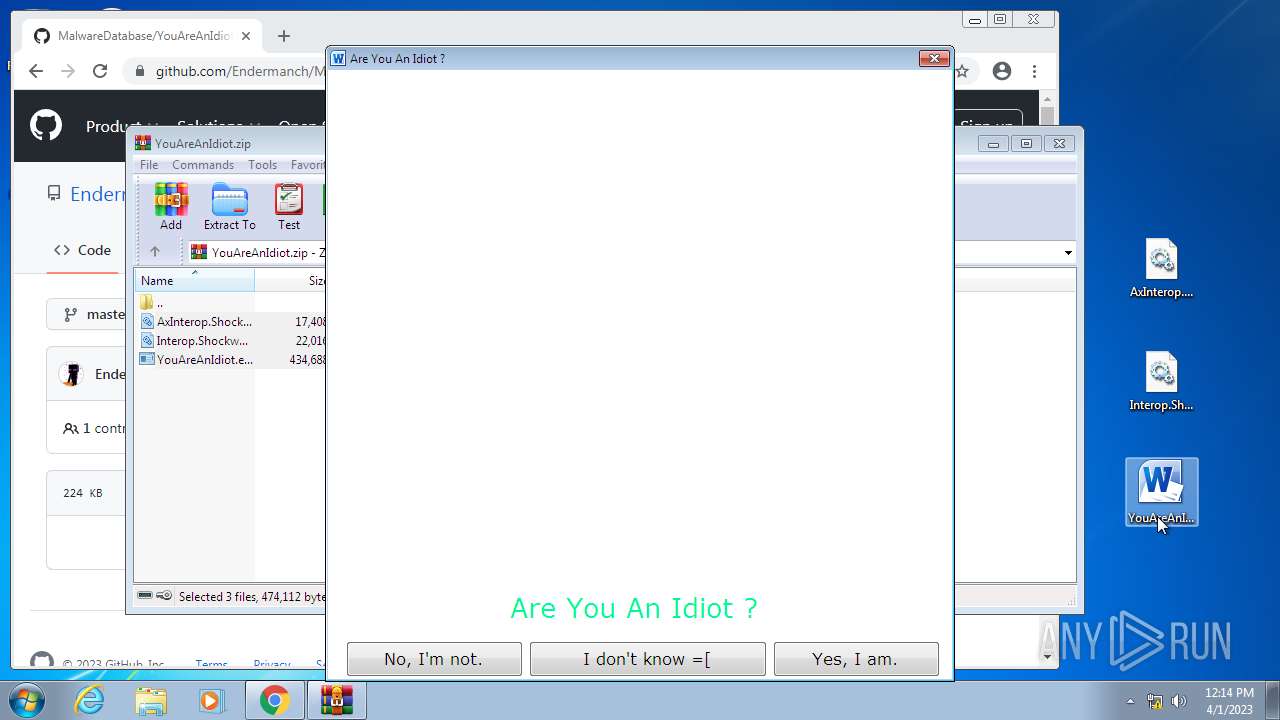
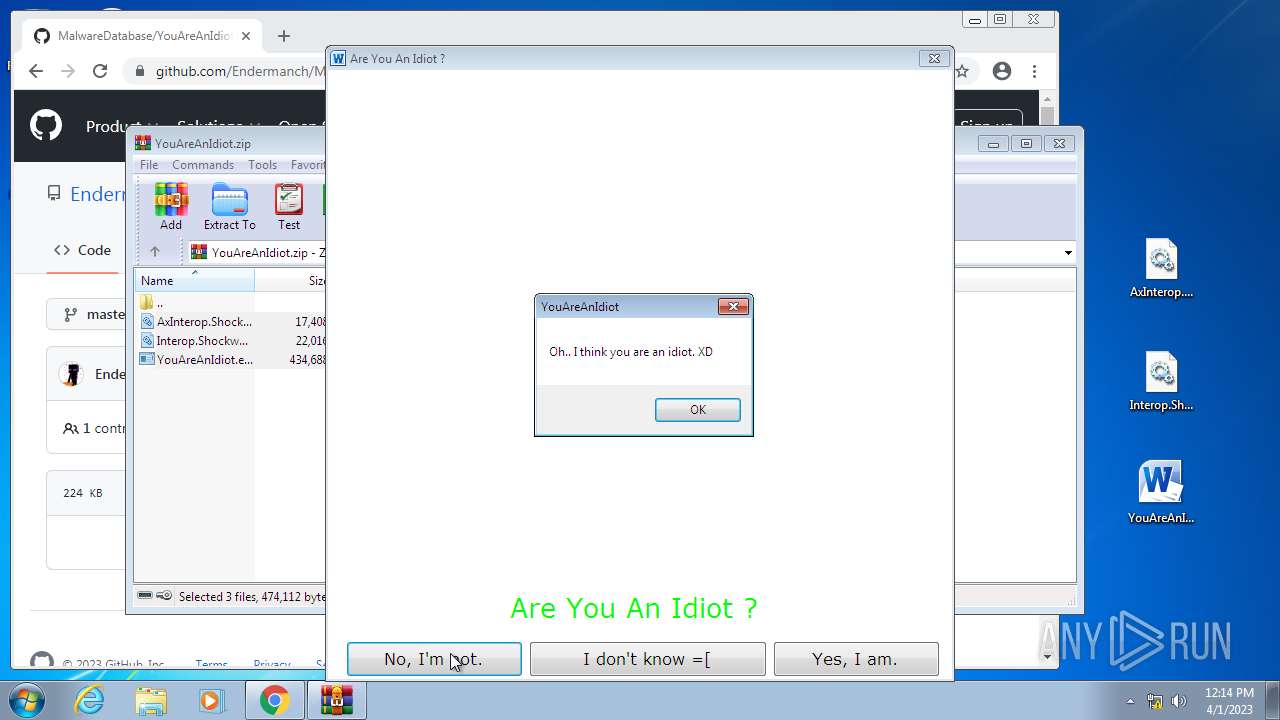
- YouAreAnIdiot.exe (PID: 1240)
- Endermanch@Xyeta.exe (PID: 580)
Changes the login/logoff helper path in the registry
- Endermanch@Xyeta.exe (PID: 580)
SUSPICIOUS
Application launched itself
- ie4uinit.exe (PID: 3868)
- rundll32.exe (PID: 2412)
Reads Internet Explorer settings
- ie4uinit.exe (PID: 3868)
Reads Microsoft Outlook installation path
- ie4uinit.exe (PID: 3868)
The process executes via Task Scheduler
- sipnotify.exe (PID: 3492)
Uses RUNDLL32.EXE to load library
- ie4uinit.exe (PID: 3868)
- rundll32.exe (PID: 2412)
Reads security settings of Internet Explorer
- ie4uinit.exe (PID: 3868)
- sipnotify.exe (PID: 3492)
Reads the Internet Settings
- rundll32.exe (PID: 2412)
- taskhost.exe (PID: 2900)
- ie4uinit.exe (PID: 3868)
- rundll32.exe (PID: 2012)
- ie4uinit.exe (PID: 3596)
- ie4uinit.exe (PID: 2968)
Executes as Windows Service
- taskhost.exe (PID: 2900)
- EOSNotify.exe (PID: 2424)
Changes internet zones settings
- ie4uinit.exe (PID: 3868)
Write to the desktop.ini file (may be used to cloak folders)
- ie4uinit.exe (PID: 3868)
- regsvr32.exe (PID: 3124)
- unregmp2.exe (PID: 2200)
Reads settings of System Certificates
- sipnotify.exe (PID: 3492)
- YouAreAnIdiot.exe (PID: 1240)
Changes default file association
- unregmp2.exe (PID: 2200)
The COM object is verified by Verclsid
- verclsid.exe (PID: 3024)
INFO
Checks supported languages
- CoinMine.exe (PID: 1900)
- IMEKLMG.EXE (PID: 2200)
- IMEKLMG.EXE (PID: 304)
- IMKRMIG.EXE (PID: 3248)
- wmpnscfg.exe (PID: 3740)
- wmpnscfg.exe (PID: 1868)
- YouAreAnIdiot.exe (PID: 1240)
- Endermanch@Xyeta.exe (PID: 580)
The process checks LSA protection
- ie4uinit.exe (PID: 3868)
- CoinMine.exe (PID: 1900)
- sipnotify.exe (PID: 3492)
- taskhost.exe (PID: 2900)
- unregmp2.exe (PID: 2200)
- regsvr32.exe (PID: 3124)
- wmpnscfg.exe (PID: 3740)
- wmpnscfg.exe (PID: 1868)
- YouAreAnIdiot.exe (PID: 1240)
Manual execution by a user
- ie4uinit.exe (PID: 3868)
- taskmgr.exe (PID: 2724)
- ie4uinit.exe (PID: 3596)
- unregmp2.exe (PID: 2200)
- ie4uinit.exe (PID: 2968)
- regsvr32.exe (PID: 3124)
- chrmstp.exe (PID: 3500)
- IMEKLMG.EXE (PID: 2200)
- IMEKLMG.EXE (PID: 304)
- wmpnscfg.exe (PID: 3740)
- wmpnscfg.exe (PID: 1868)
- chrome.exe (PID: 3488)
- YouAreAnIdiot.exe (PID: 1240)
- verclsid.exe (PID: 3024)
- taskmgr.exe (PID: 2084)
Reads the computer name
- CoinMine.exe (PID: 1900)
- IMEKLMG.EXE (PID: 2200)
- IMEKLMG.EXE (PID: 304)
- wmpnscfg.exe (PID: 1868)
- wmpnscfg.exe (PID: 3740)
- YouAreAnIdiot.exe (PID: 1240)
Creates files in the program directory
- ie4uinit.exe (PID: 3868)
- chrmstp.exe (PID: 3500)
- chrome.exe (PID: 3488)
- chrmstp.exe (PID: 3880)
Application launched itself
- chrmstp.exe (PID: 3500)
- chrome.exe (PID: 3488)
- chrmstp.exe (PID: 3880)
Process checks are UAC notifies on
- IMEKLMG.EXE (PID: 2200)
- IMEKLMG.EXE (PID: 304)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3740)
- wmpnscfg.exe (PID: 1868)
- YouAreAnIdiot.exe (PID: 1240)
The process uses the downloaded file
- chrome.exe (PID: 1352)
- WinRAR.exe (PID: 2996)
- chrome.exe (PID: 4004)
- WinRAR.exe (PID: 1364)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2996)
- WinRAR.exe (PID: 1364)
Reads CPU info
- YouAreAnIdiot.exe (PID: 1240)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (38.2) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (37.5) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.2) |
| .exe | | | Win32 Executable (generic) (6.3) |
| .exe | | | Win16/32 Executable Delphi generic (2.9) |
EXIF
EXE
| ProductVersion: | 1.0.0.0 |
|---|---|
| FileVersion: | 1.0.0.0 |
| CharacterSet: | Windows, Latin1 |
| LanguageCode: | English (U.S.) |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 1.0.0.0 |
| FileVersionNumber: | 1.0.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 5 |
| ImageVersion: | - |
| OSVersion: | 5 |
| EntryPoint: | 0x3b0160 |
| UninitializedDataSize: | 2650112 |
| InitializedDataSize: | 20480 |
| CodeSize: | 1216512 |
| LinkerVersion: | 2.25 |
| PEType: | PE32 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| TimeStamp: | 2016:07:08 05:36:35+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 08-Jul-2016 05:36:35 |
| Detected languages: |
|
| FileVersion: | 1.0.0.0 |
| ProductVersion: | 1.0.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 08-Jul-2016 05:36:35 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
UPX0 | 0x00001000 | 0x00287000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
UPX1 | 0x00288000 | 0x00129000 | 0x00128400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.92589 |
.rsrc | 0x003B1000 | 0x00005000 | 0x00004400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.36489 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.86531 | 714 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 7.21422 | 308 | UNKNOWN | English - United States | RT_CURSOR |
3 | 6.92854 | 308 | UNKNOWN | English - United States | RT_CURSOR |
4 | 7.09594 | 308 | UNKNOWN | English - United States | RT_CURSOR |
5 | 7.20732 | 308 | UNKNOWN | English - United States | RT_CURSOR |
6 | 7.04739 | 308 | UNKNOWN | English - United States | RT_CURSOR |
7 | 7.13266 | 308 | UNKNOWN | English - United States | RT_CURSOR |
3682 | 5.76431 | 76 | UNKNOWN | UNKNOWN | RT_STRING |
3683 | 6.76654 | 170 | UNKNOWN | UNKNOWN | RT_STRING |
3684 | 7.24462 | 390 | UNKNOWN | UNKNOWN | RT_STRING |
Imports
KERNEL32.DLL |
advapi32.dll |
comctl32.dll |
comdlg32.dll |
gdi32.dll |
msvcrt.dll |
ole32.dll |
oleaut32.dll |
shell32.dll |
user32.dll |
Total processes
156
Monitored processes
100
Malicious processes
8
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1100,5526722376860241208,3819627595130855882,131072 --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=58 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1008 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: Administrator Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 304 | "C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE" /SetPreload /KOR /Log | C:\Program Files\Common Files\microsoft shared\IME14\SHARED\IMEKLMG.EXE | — | explorer.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Office IME 2010 Exit code: 1 Version: 14.0.4734.1000 Modules
| |||||||||||||||
| 568 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1100,5526722376860241208,3819627595130855882,131072 --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1428 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: Administrator Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
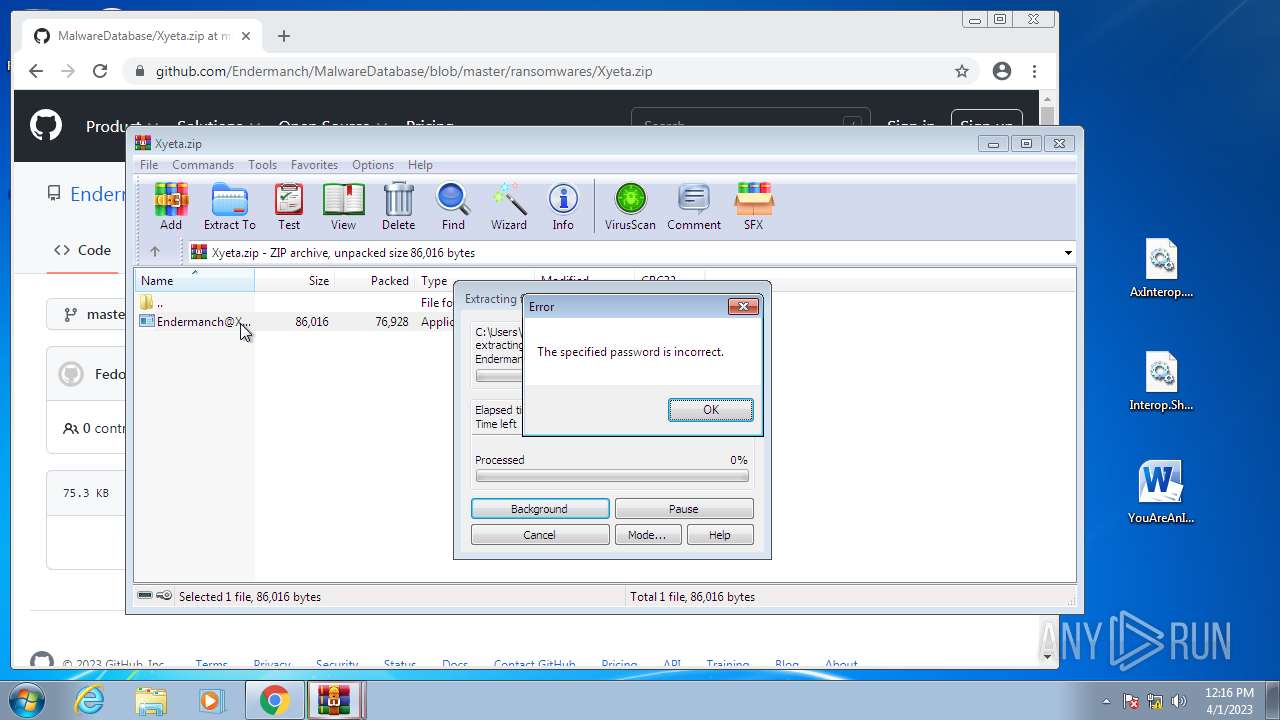
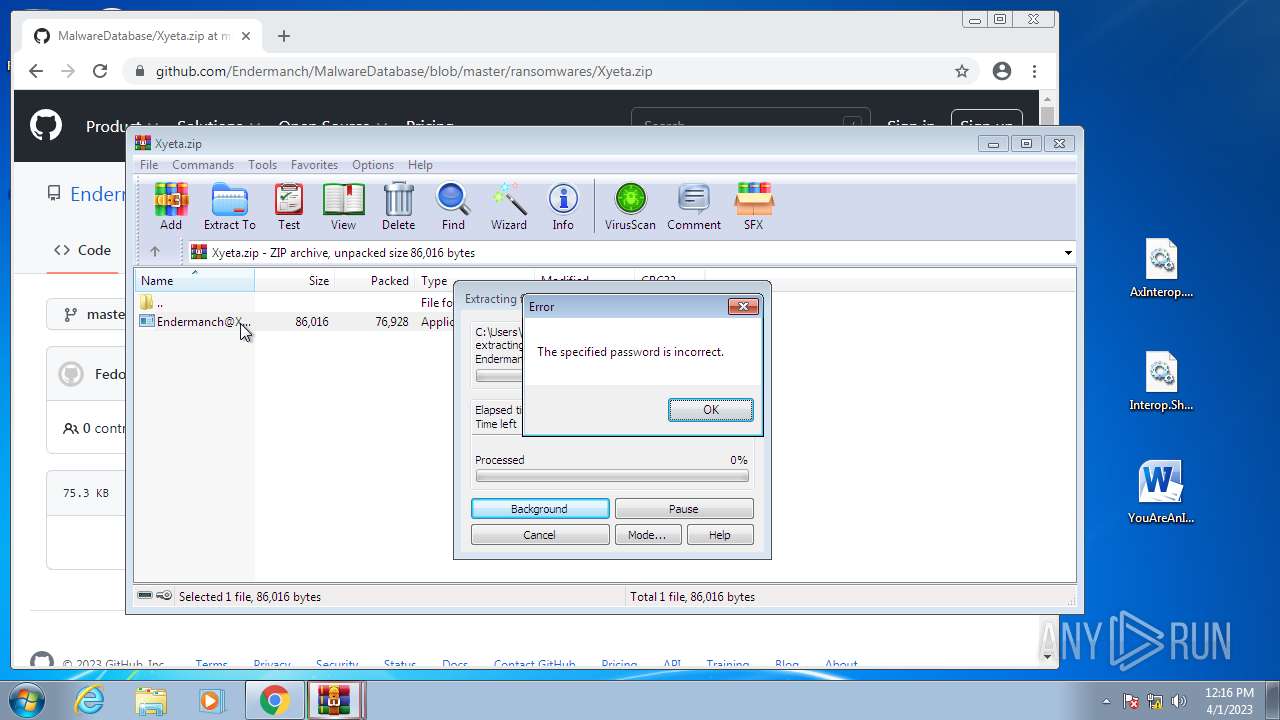
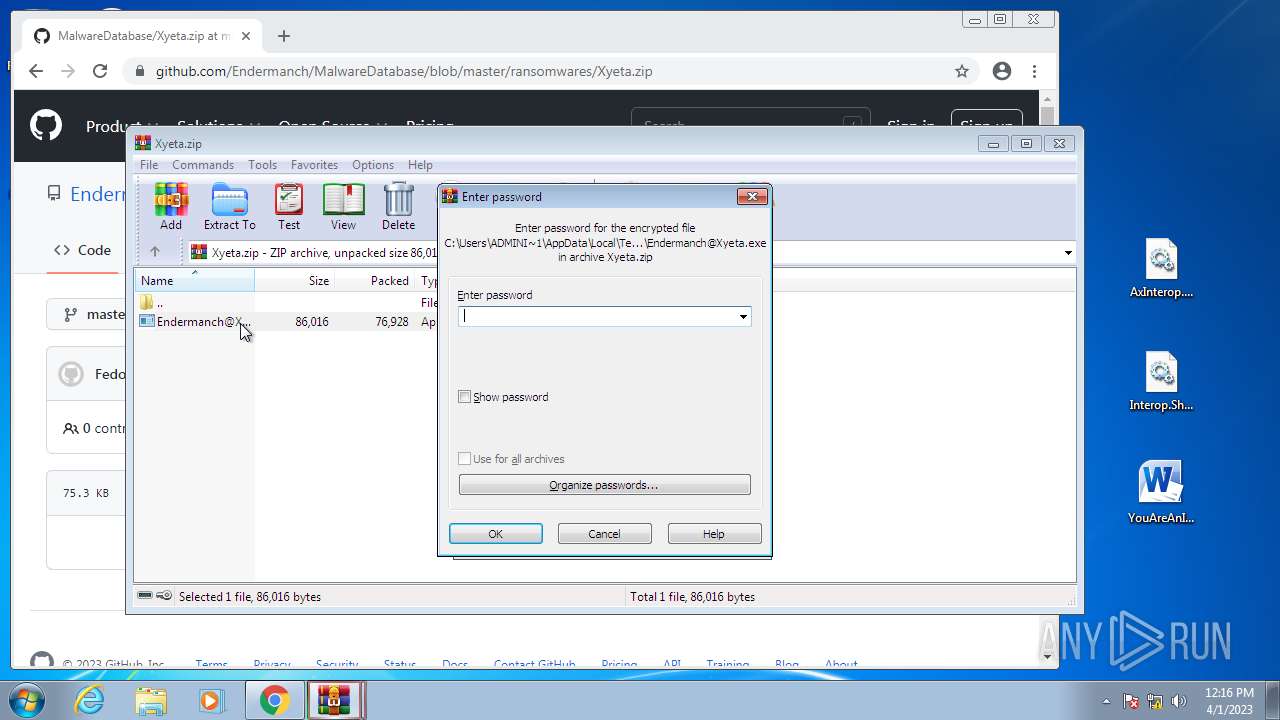
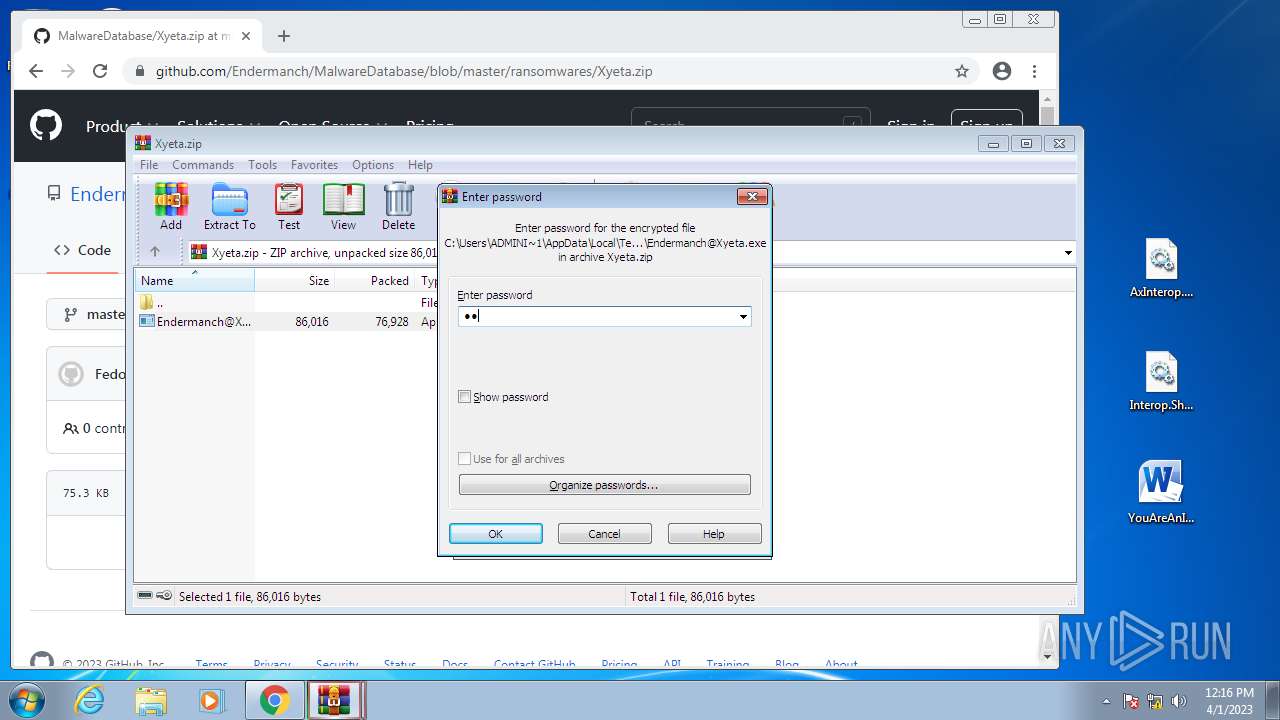
| 580 | "C:\Users\ADMINI~1\AppData\Local\Temp\Rar$EXb1364.26708\Endermanch@Xyeta.exe" | C:\Users\Administrator\AppData\Local\Temp\Rar$EXb1364.26708\Endermanch@Xyeta.exe | WinRAR.exe | ||||||||||||
User: Administrator Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 664 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.FileUtilService --field-trial-handle=1100,5526722376860241208,3819627595130855882,131072 --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3020 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: Administrator Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 976 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1100,5526722376860241208,3819627595130855882,131072 --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3336 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: Administrator Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 980 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1100,5526722376860241208,3819627595130855882,131072 --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=4380 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: Administrator Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 992 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1100,5526722376860241208,3819627595130855882,131072 --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2496 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: Administrator Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1048 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1100,5526722376860241208,3819627595130855882,131072 --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3940 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: Administrator Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1092 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1100,5526722376860241208,3819627595130855882,131072 --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1728 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: Administrator Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
62 062
Read events
60 164
Write events
1 852
Delete events
46
Modification events
| (PID) Process: | (3868) ie4uinit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\CLSID\{871C5380-42A0-1069-A2EA-08002B30309D}\ShellFolder |
| Operation: | write | Name: | Attributes |
Value: 0 | |||
| (PID) Process: | (3868) ie4uinit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Active Setup\Installed Components\>{26923b43-4d38-484f-9b9e-de460746276c} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3868) ie4uinit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\International\Scripts\3 |
| Operation: | write | Name: | IEPropFontName |
Value: Times New Roman | |||
| (PID) Process: | (3868) ie4uinit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\International\Scripts\3 |
| Operation: | write | Name: | IEFixedFontName |
Value: Courier New | |||
| (PID) Process: | (3868) ie4uinit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\International\Scripts\4 |
| Operation: | write | Name: | IEPropFontName |
Value: Times New Roman | |||
| (PID) Process: | (3868) ie4uinit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\International\Scripts\4 |
| Operation: | write | Name: | IEFixedFontName |
Value: Courier New | |||
| (PID) Process: | (3868) ie4uinit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\International\Scripts\5 |
| Operation: | write | Name: | IEPropFontName |
Value: Times New Roman | |||
| (PID) Process: | (3868) ie4uinit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\International\Scripts\5 |
| Operation: | write | Name: | IEFixedFontName |
Value: Courier New | |||
| (PID) Process: | (3868) ie4uinit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\International\Scripts\6 |
| Operation: | write | Name: | IEPropFontName |
Value: Times New Roman | |||
| (PID) Process: | (3868) ie4uinit.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\International\Scripts\6 |
| Operation: | write | Name: | IEFixedFontName |
Value: Courier New | |||
Executable files
8
Suspicious files
1 798
Text files
788
Unknown types
352
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2012 | rundll32.exe | C:\Users\Administrator\AppData\Local\Microsoft\Feeds Cache\E3EJU7ZL\fwlink[1] | — | |
MD5:— | SHA256:— | |||
| 2012 | rundll32.exe | C:\Users\Administrator\AppData\Local\Microsoft\Feeds Cache\4TD0KH3X\fwlink[1] | — | |
MD5:— | SHA256:— | |||
| 2012 | rundll32.exe | C:\Users\Administrator\AppData\Local\Microsoft\Feeds Cache\2HM2BW7R\fwlink[1] | — | |
MD5:— | SHA256:— | |||
| 2012 | rundll32.exe | C:\Users\Administrator\AppData\Local\Microsoft\Feeds Cache\EK4BLZQC\fwlink[1] | — | |
MD5:— | SHA256:— | |||
| 2012 | rundll32.exe | C:\Users\Administrator\AppData\Local\Microsoft\Feeds Cache\E3EJU7ZL\fwlink[2] | — | |
MD5:— | SHA256:— | |||
| 2012 | rundll32.exe | C:\Users\Administrator\AppData\Local\Microsoft\Feeds Cache\4TD0KH3X\fwlink[2] | — | |
MD5:— | SHA256:— | |||
| 2900 | taskhost.exe | C:\Users\Administrator\AppData\Local\Microsoft\Windows\WebCache\V01tmp.log | binary | |
MD5:— | SHA256:— | |||
| 2900 | taskhost.exe | C:\Users\Administrator\AppData\Local\Microsoft\Windows\WebCache\V01.log | binary | |
MD5:— | SHA256:— | |||
| 2900 | taskhost.exe | C:\Users\Administrator\AppData\Local\Microsoft\Windows\WebCache\WebCacheV01.dat | edb | |
MD5:— | SHA256:— | |||
| 3868 | ie4uinit.exe | C:\Windows\INF\setupapi.app.log | ini | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
31
TCP/UDP connections
61
DNS requests
44
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
860 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/dl6iudcrkm7tlleep5b7sio2si_2937/jflookgnkcckhobaglndicnbbgbonegd_2937_all_n6dma56ie7wmbezc4aw6zyp2jq.crx3 | US | — | — | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/dl6iudcrkm7tlleep5b7sio2si_2937/jflookgnkcckhobaglndicnbbgbonegd_2937_all_n6dma56ie7wmbezc4aw6zyp2jq.crx3 | US | binary | 5.77 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/dl6iudcrkm7tlleep5b7sio2si_2937/jflookgnkcckhobaglndicnbbgbonegd_2937_all_n6dma56ie7wmbezc4aw6zyp2jq.crx3 | US | binary | 18.2 Kb | whitelisted |
860 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/cxpsjblnoxgjoqggdsbvujtof4_58/khaoiebndkojlmppeemjhbpbandiljpe_58_win_advr4ucepztwtigvw3fduftsvbeq.crx3 | US | binary | 18.2 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/dl6iudcrkm7tlleep5b7sio2si_2937/jflookgnkcckhobaglndicnbbgbonegd_2937_all_n6dma56ie7wmbezc4aw6zyp2jq.crx3 | US | binary | 9.19 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/dl6iudcrkm7tlleep5b7sio2si_2937/jflookgnkcckhobaglndicnbbgbonegd_2937_all_n6dma56ie7wmbezc4aw6zyp2jq.crx3 | US | binary | 12.4 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/dl6iudcrkm7tlleep5b7sio2si_2937/jflookgnkcckhobaglndicnbbgbonegd_2937_all_n6dma56ie7wmbezc4aw6zyp2jq.crx3 | US | binary | 9.30 Kb | whitelisted |
1240 | YouAreAnIdiot.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
1240 | YouAreAnIdiot.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvN2MwQUFWdmlaX0VYMlk3YWlITHpVbV9MZw/0.57.44.2492_hnimpnehoodheedghdeeijklkeaacbdc.crx | US | binary | 174 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3956 | chrome.exe | 142.250.186.110:443 | clients2.google.com | GOOGLE | US | whitelisted |
3956 | chrome.exe | 173.194.187.170:443 | r5---sn-4g5e6nz7.gvt1.com | GOOGLE | US | whitelisted |
3492 | sipnotify.exe | 23.212.215.38:80 | query.prod.cms.rt.microsoft.com | AKAMAI-AS | AU | unknown |
3956 | chrome.exe | 142.250.74.193:443 | clients2.googleusercontent.com | GOOGLE | US | whitelisted |
3956 | chrome.exe | 142.250.185.163:443 | ssl.gstatic.com | GOOGLE | US | whitelisted |
3956 | chrome.exe | 142.250.186.45:443 | accounts.google.com | GOOGLE | US | suspicious |
3956 | chrome.exe | 142.250.185.78:443 | encrypted-tbn0.gstatic.com | GOOGLE | US | whitelisted |
3956 | chrome.exe | 142.250.181.238:443 | redirector.gvt1.com | GOOGLE | US | whitelisted |
3956 | chrome.exe | 172.217.23.106:443 | www.googleapis.com | GOOGLE | US | whitelisted |
3956 | chrome.exe | 172.217.16.196:443 | www.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
query.prod.cms.rt.microsoft.com |
| whitelisted |
accounts.google.com |
| shared |
clients2.google.com |
| whitelisted |
redirector.gvt1.com |
| whitelisted |
r5---sn-4g5e6nz7.gvt1.com |
| whitelisted |
clients2.googleusercontent.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
www.googleapis.com |
| whitelisted |
www.google.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3956 | chrome.exe | Generic Protocol Command Decode | SURICATA HTTP unable to match response to request |