| File name: | 7d2cc57e27e849fb0617a3a73d68d302c6efc6d849c05fcb0776b82a74d4de9c |
| Full analysis: | https://app.any.run/tasks/2f692880-c8a6-4955-9ff6-4741428f23bf |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2019, 14:22:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 02DD4A91651B0DDADE7F32D040A27ED0 |
| SHA1: | C58351BD3B38EE593DD9A03BFFAD18B2F0D94705 |
| SHA256: | 7D2CC57E27E849FB0617A3A73D68D302C6EFC6D849C05FCB0776B82A74D4DE9C |
| SSDEEP: | 192:fMY3bfPwBgAyLCM0rzaGefWIgHa1uDv4YLLdm1C7lqKrT/rTRrTNGf:/LfkuirgfWINQv4YfdmQ57rT/rTRrTcf |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Internet Cache Settings
- WINWORD.EXE (PID: 2568)
Executed via COM
- EQNEDT32.EXE (PID: 2740)
Unusual connect from Microsoft Office
- WINWORD.EXE (PID: 2568)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2568)
Application was crashed
- EQNEDT32.EXE (PID: 2740)
Reads the machine GUID from the registry
- WINWORD.EXE (PID: 2568)
Creates files in the user directory
- WINWORD.EXE (PID: 2568)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2019:08:29 12:00:16 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | word/ |
XML
| Template: | BA481970.tmp |
|---|---|
| TotalEditTime: | 11 minutes |
| Pages: | 1 |
| Words: | 4 |
| Characters: | 28 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 1 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 31 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 12 |
| Keywords: | - |
| LastModifiedBy: | Windows User |
| RevisionNumber: | 7 |
| CreateDate: | 2019:07:17 10:07:00Z |
| ModifyDate: | 2019:08:29 10:59:00Z |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | Windows User |
| Description: | - |
Total processes
41
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2568 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\7d2cc57e27e849fb0617a3a73d68d302c6efc6d849c05fcb0776b82a74d4de9c.docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.5123.5000 Modules
| |||||||||||||||
| 2740 | "C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding | C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE | svchost.exe | ||||||||||||
User: admin Company: Design Science, Inc. Integrity Level: MEDIUM Description: Microsoft Equation Editor Exit code: 0 Version: 00110900 Modules
| |||||||||||||||
Total events
1 660
Read events
905
Write events
618
Delete events
137
Modification events
| (PID) Process: | (2568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | uc< |
Value: 75633C00080A0000010000000000000000000000 | |||
| (PID) Process: | (2568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (2568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2568) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
Executable files
0
Suspicious files
22
Text files
8
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2568 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR4F75.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2568 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{D4D9940D-3C3C-4098-8F37-0C336C61EFB6} | — | |
MD5:— | SHA256:— | |||
| 2568 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{173B1E30-46FE-4E0C-ADC9-4081F9DFE23B}.tmp | — | |
MD5:— | SHA256:— | |||
| 2568 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSF-CTBL.FSF | binary | |
MD5:— | SHA256:— | |||
| 2568 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{135D7336-E01D-49D4-8B8E-05C9E26A2A26} | binary | |
MD5:— | SHA256:— | |||
| 2568 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-CNRY.FSD | binary | |
MD5:— | SHA256:— | |||
| 2568 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\FSD-{541EFFAF-1635-450E-BB8A-96061EEFB99C}.FSD | binary | |
MD5:— | SHA256:— | |||
| 2568 | WINWORD.EXE | C:\Users\admin\Desktop\~$2cc57e27e849fb0617a3a73d68d302c6efc6d849c05fcb0776b82a74d4de9c.docx | pgc | |
MD5:— | SHA256:— | |||
| 2568 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\wp-content on comglobal.com.pk.url | text | |
MD5:— | SHA256:— | |||
| 2568 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSF-{0E1EEE64-E8C6-4E2A-9759-63CF07FD8988}.FSF | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
5
DNS requests
2
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
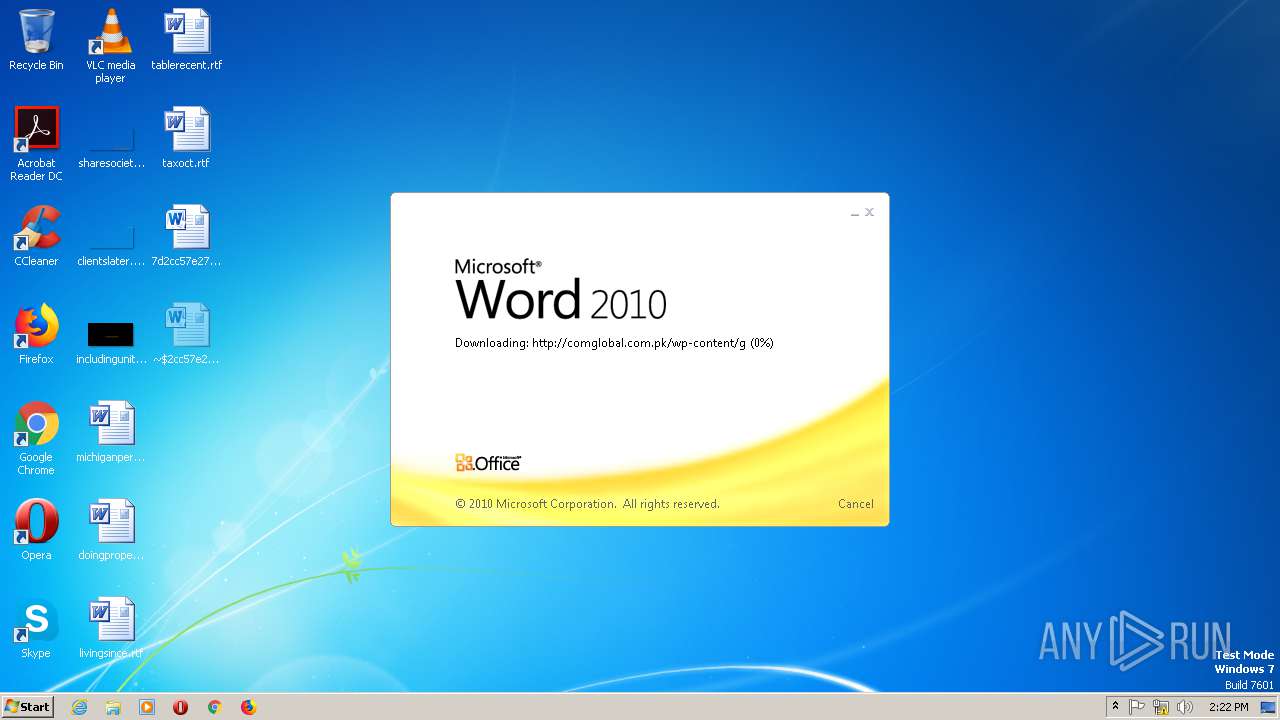
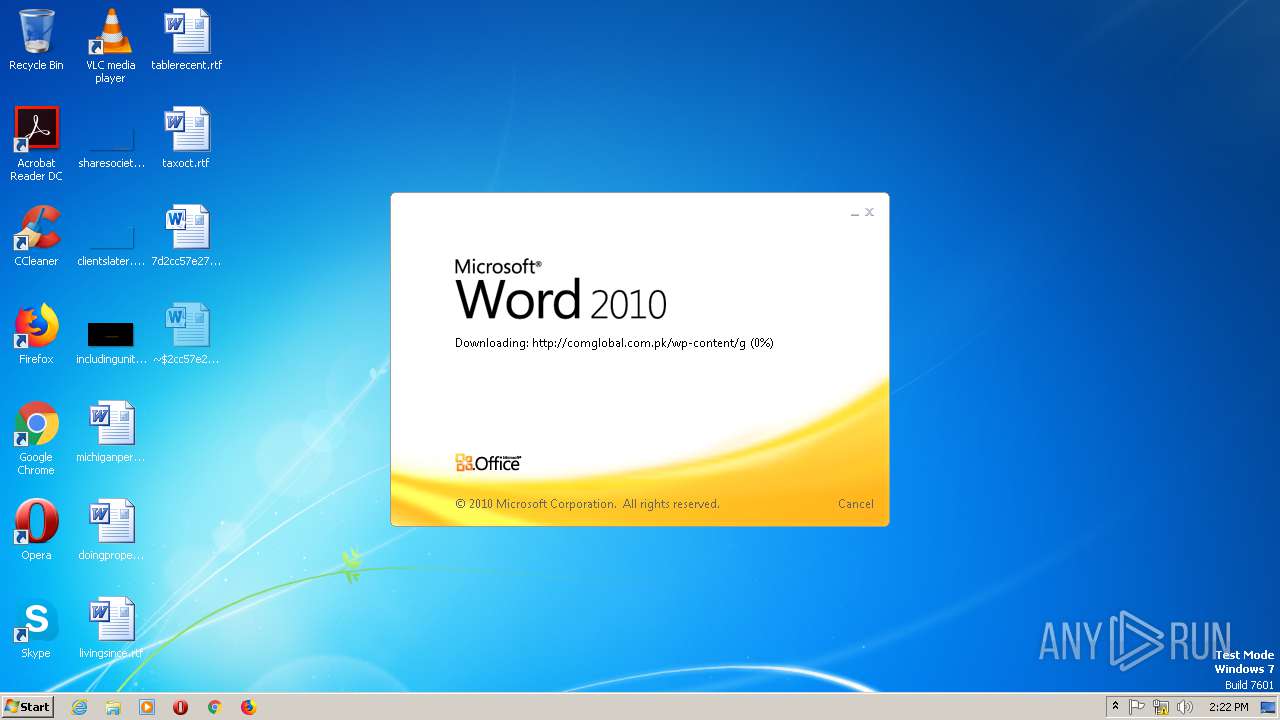
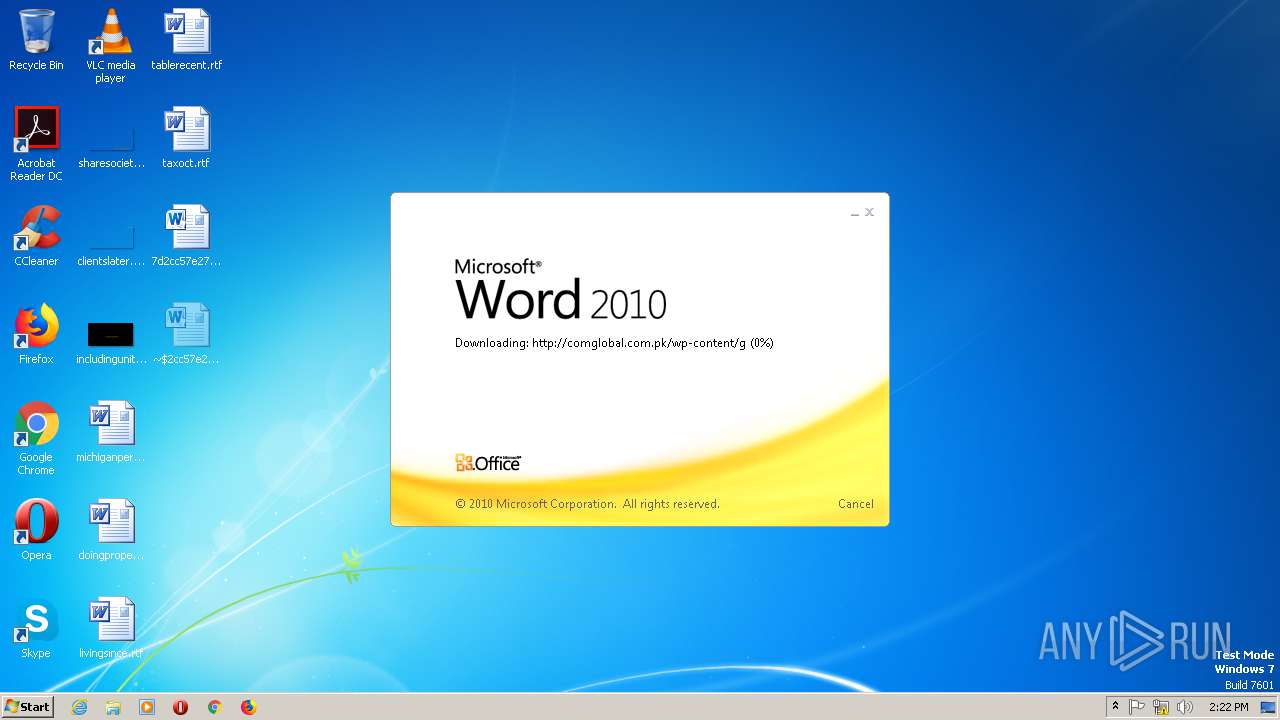
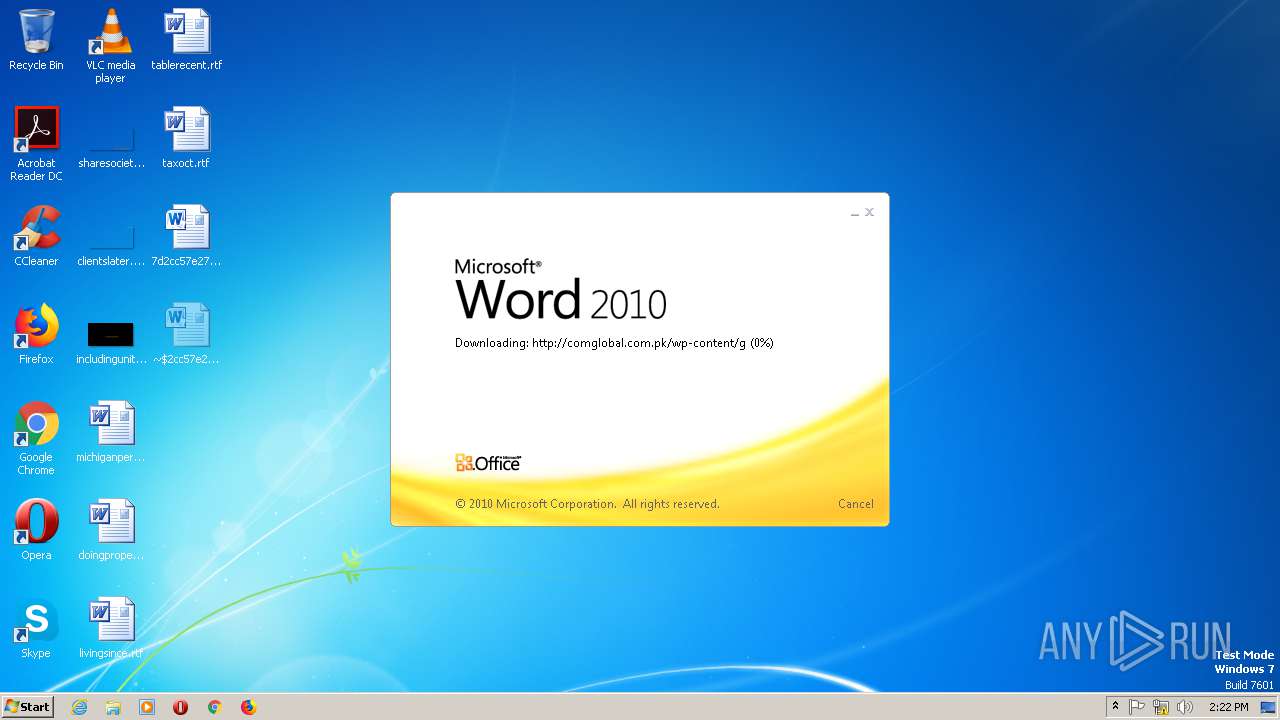
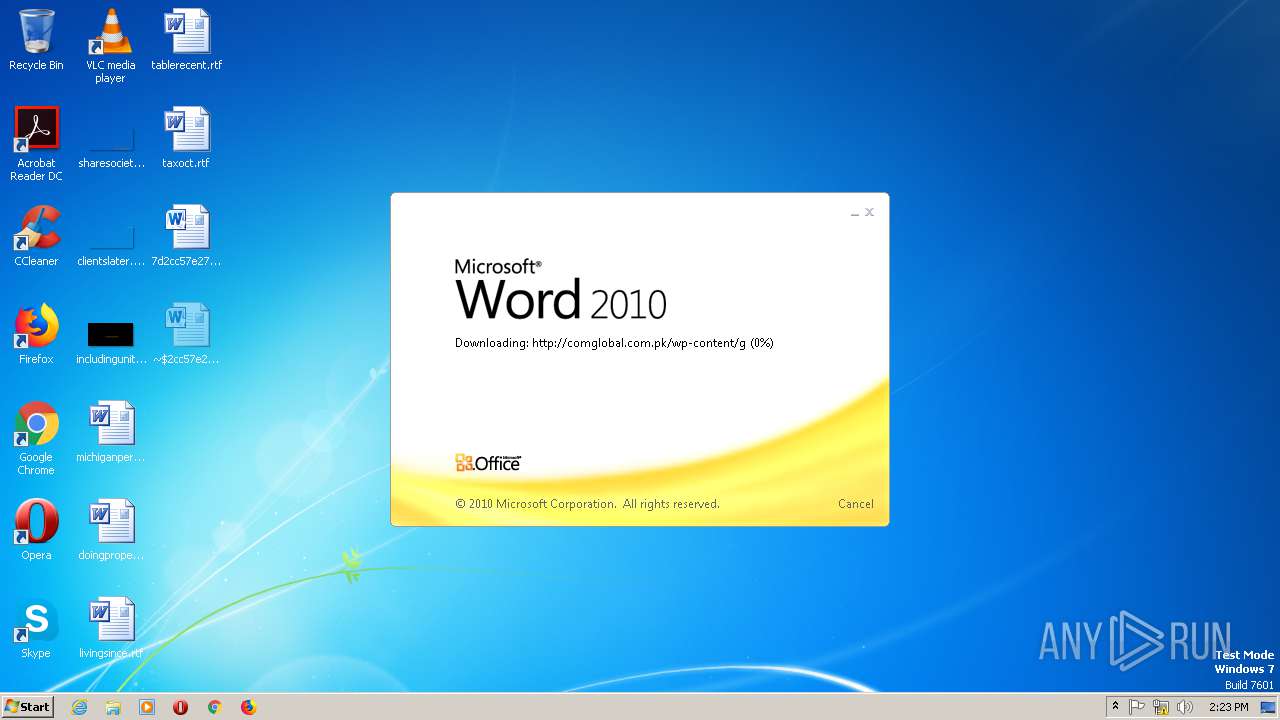
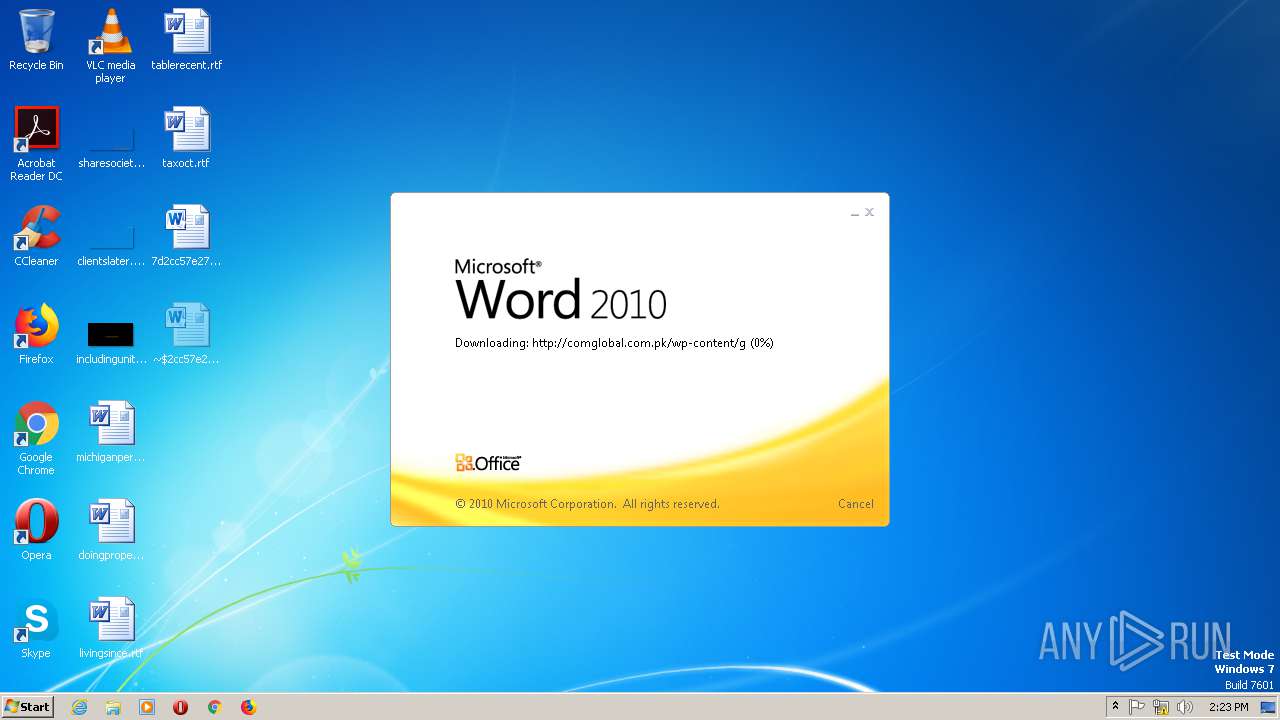
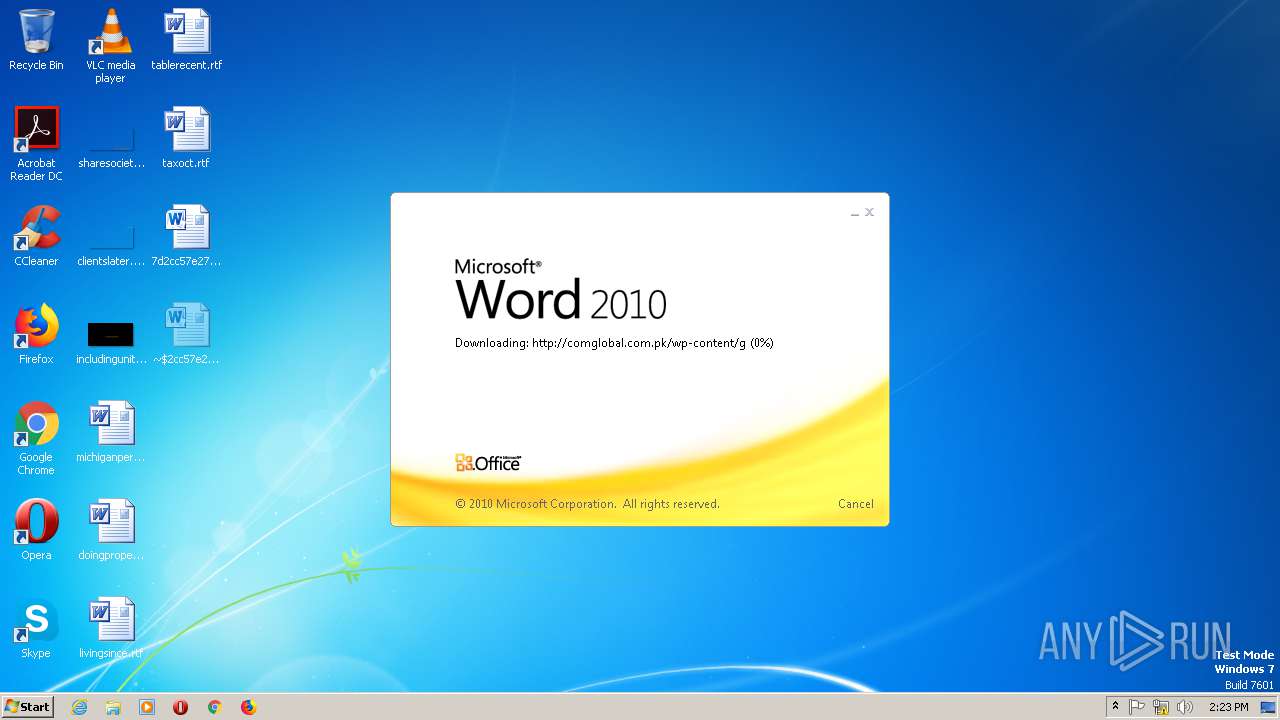
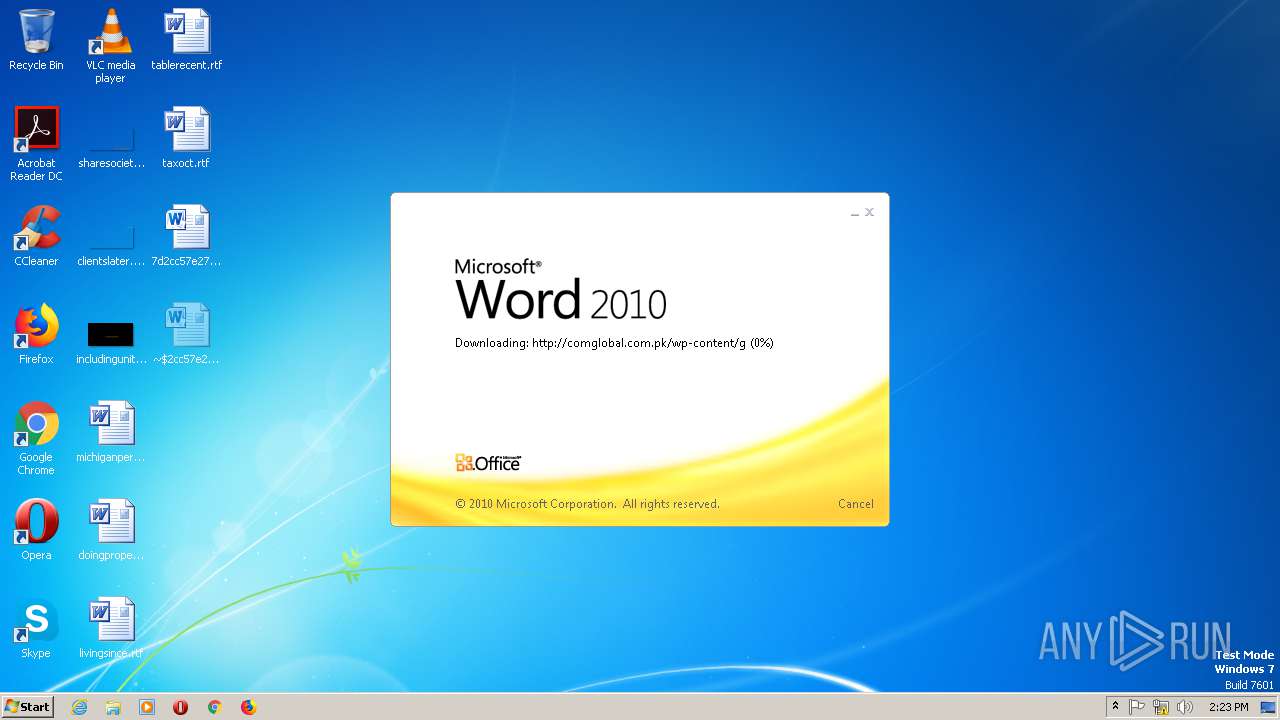
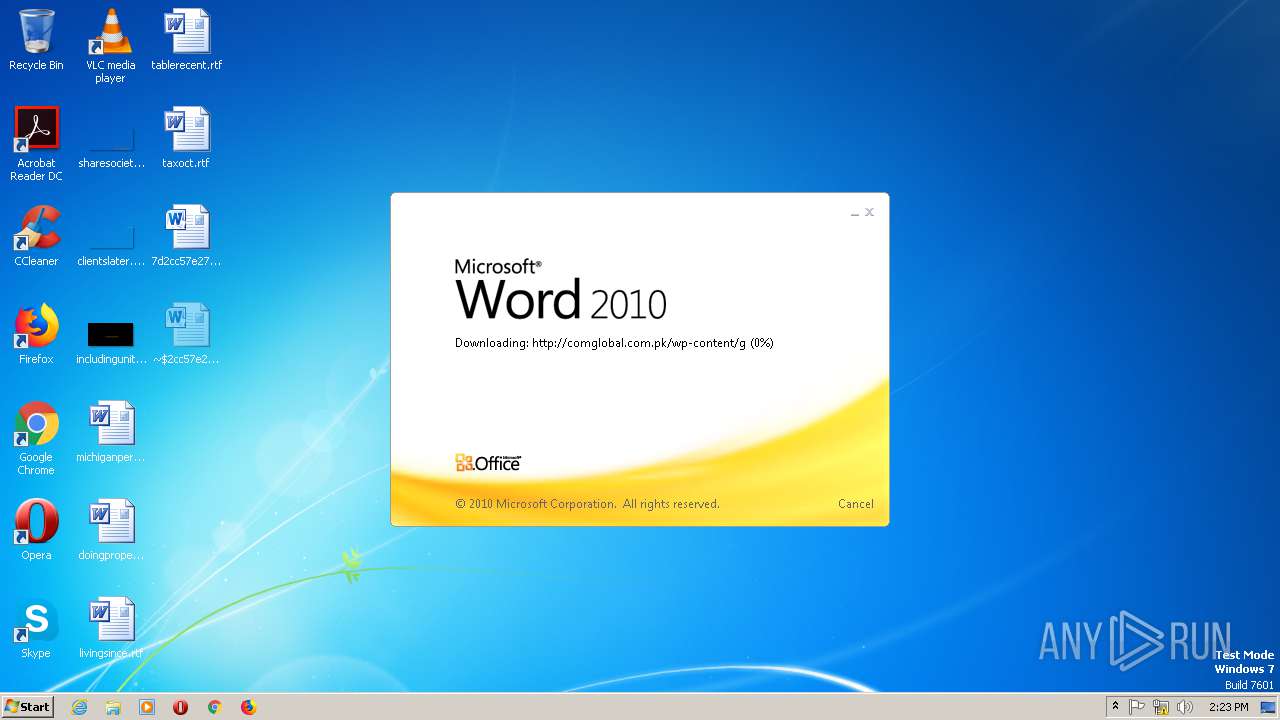
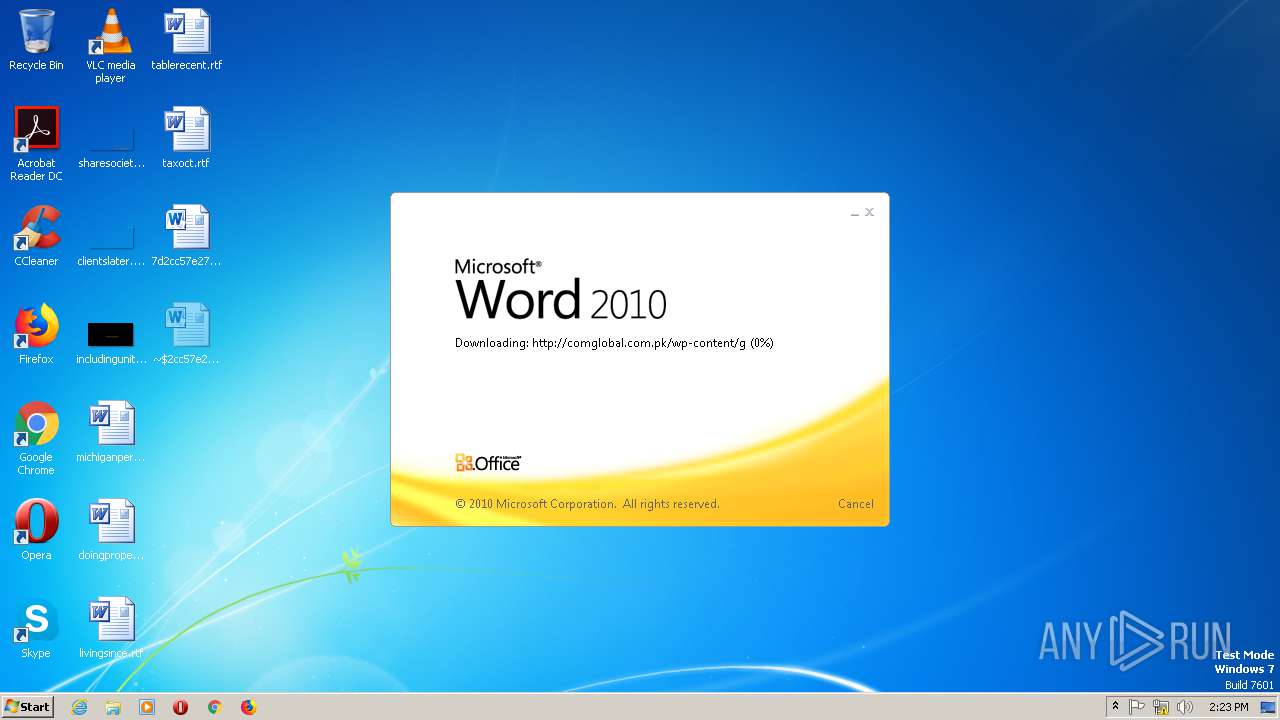
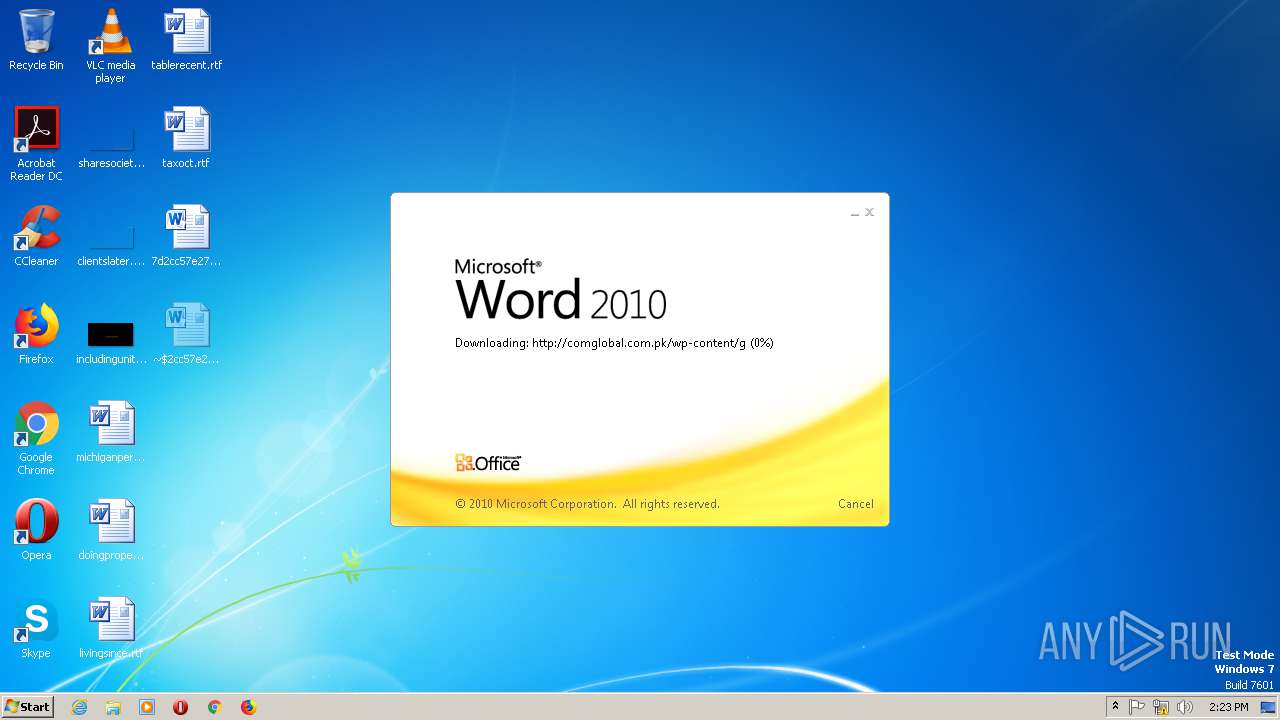
2568 | WINWORD.EXE | OPTIONS | 200 | 203.124.44.32:80 | http://comglobal.com.pk/wp-content/ | PK | — | — | suspicious |
2568 | WINWORD.EXE | HEAD | 200 | 203.124.44.32:80 | http://comglobal.com.pk/wp-content/g | PK | text | 9.13 Kb | suspicious |
2568 | WINWORD.EXE | HEAD | 200 | 203.124.44.32:80 | http://comglobal.com.pk/wp-content/g | PK | — | — | suspicious |
876 | svchost.exe | OPTIONS | 301 | 203.124.44.32:80 | http://comglobal.com.pk/wp-content | PK | — | — | suspicious |
876 | svchost.exe | OPTIONS | — | 203.124.44.32:80 | http://www.comglobal.com.pk/wp-content | PK | — | — | suspicious |
2568 | WINWORD.EXE | GET | 200 | 203.124.44.32:80 | http://comglobal.com.pk/wp-content/g | PK | text | 9.13 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2568 | WINWORD.EXE | 203.124.44.32:80 | comglobal.com.pk | Commission on Science and Technology for | PK | suspicious |
876 | svchost.exe | 203.124.44.32:80 | comglobal.com.pk | Commission on Science and Technology for | PK | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
comglobal.com.pk |
| suspicious |
www.comglobal.com.pk |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2568 | WINWORD.EXE | A Network Trojan was detected | ET CURRENT_EVENTS DRIVEBY GENERIC ShellExecute in Hex No Seps |
2568 | WINWORD.EXE | Potentially Bad Traffic | ET INFO Possible RTF File With Obfuscated Version Header |