| File name: | RE_ StateFarm Thanks You – Claim Your Fire Safety Kit!-_--------.eml |
| Full analysis: | https://app.any.run/tasks/5295ab9b-bcc3-42ec-8609-42e80cb85ce8 |
| Verdict: | Malicious activity |
| Analysis date: | April 05, 2025, 15:39:58 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-8 text, with very long lines (2048), with CRLF line terminators |
| MD5: | CF9D7F0261B7468EFD1D4A11D447AFF0 |
| SHA1: | EF49EAABD5661A901308DE2EF488447FC9DEE821 |
| SHA256: | 7D19B70D70B0175FFFF017844D844AD8FD1A9AC0106A3010C72E2C5FFB488F55 |
| SSDEEP: | 6144:18cBngbVSdDSLC9JC4QvJp86GfXOK1bsi6UhHnNFb9+p432KeTosrk:18cBCgdMco/89OK1SUhHnFgueTosQ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Email with suspicious attachment
- OUTLOOK.EXE (PID: 6048)
INFO
Email verification fail (SPF, DKIM or DMARC)
- OUTLOOK.EXE (PID: 6048)
Email with attachments
- OUTLOOK.EXE (PID: 6048)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 3) (100) |
|---|
Total processes
132
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5256 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5864 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
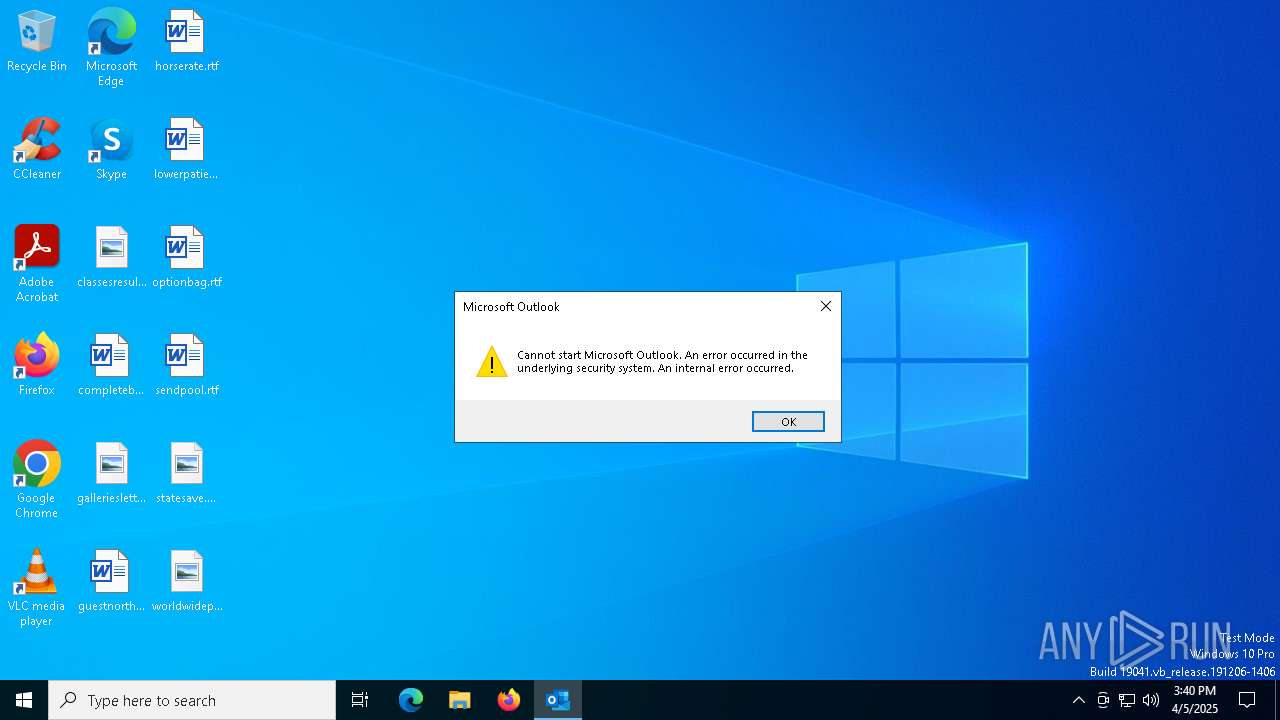
| 6048 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\RE_ StateFarm Thanks You – Claim Your Fire Safety Kit!-_--------.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
3 980
Read events
3 761
Write events
199
Delete events
20
Modification events
| (PID) Process: | (6048) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 6 |
Value: 01941A000000001000B24E9A3E06000000000000000600000000000000 | |||
| (PID) Process: | (6048) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\6048 |
| Operation: | write | Name: | 0 |
Value: 0B0E101EA721FA84DF1D4E9E7E7F970D570E81230046B2D0808F90C8E9ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511A02FD2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6048) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootCommand |
Value: | |||
| (PID) Process: | (6048) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | BootFailureCount |
Value: | |||
| (PID) Process: | (6048) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6048) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | CantBootResolution |
Value: BootSuccess | |||
| (PID) Process: | (6048) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | ProfileBeingOpened |
Value: Outlook | |||
| (PID) Process: | (6048) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | SessionId |
Value: C3D8E96E-C1AF-4750-8D52-F4E28119C131 | |||
| (PID) Process: | (6048) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics\BootDiagnosticsDataPreviousSession |
| Operation: | write | Name: | BootDiagnosticsLogFile |
Value: C:\Users\admin\AppData\Local\Temp\Outlook Logging\OUTLOOK_16_0_16026_20146-20240718T1116060318-1644.etl | |||
| (PID) Process: | (6048) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Diagnostics |
| Operation: | delete value | Name: | ProfileBeingOpened |
Value: | |||
Executable files
0
Suspicious files
10
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6048 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 6048 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DFDB60C12E8106EB9E.TMP | binary | |
MD5:7834EB84A9F009316BC310B0BA08D5C5 | SHA256:82C6BF5CF7D2301F05535D80AC86DCFAFF5088B5B6782337A9AF3956B162D8C2 | |||
| 6048 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF556AB76BAC842726.TMP | binary | |
MD5:8349A1B8733ACC20F1B420275E5230F2 | SHA256:F28B4549B409038F9D089115E465A988A84136A285EC6DAE0691C9D46B310D78 | |||
| 6048 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olkC47B.tmp | text | |
MD5:32982213F14AF3675FFB0B3107437EAE | SHA256:CB2FC9C4D0D9BEDAD8AFBE8A16F50DF70F48D11C192A22EFC5AAAD8298DA359C | |||
| 6048 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF36DDB47271F85B74.TMP | binary | |
MD5:8349A1B8733ACC20F1B420275E5230F2 | SHA256:F28B4549B409038F9D089115E465A988A84136A285EC6DAE0691C9D46B310D78 | |||
| 6048 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:0F40E2E2EE12AF61DCC0172AB074BE73 | SHA256:5411B12BEEDEE4FC0F9ECB6A37351B4382606C2C0D92730BB0292A6F3CFA5898 | |||
| 6048 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olkC48B.tmp | text | |
MD5:C8CE926F4EE1682C650D820837A924DF | SHA256:453ACEE83E80D2B74DABAE40BA656EB70FD1FC127B4F426D8215B8A9607E1936 | |||
| 6048 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\olkC4EA.tmp | text | |
MD5:6F4C7E65DB0306744E0540A47B436473 | SHA256:C8A78A41535B0B547D2F75582526283C26B00F9C8A9ACBDCC46458E6BECDD77C | |||
| 6048 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:A36A6F9FB0E84137C8040304649BF45B | SHA256:762DF2BBE6C1CDA5070DD2EDA64498B3DF85441EA698F74C9845FD4FFF15B42F | |||
| 6048 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\~DF192CFAF259F146F9.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
9
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.24.77.37:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6048 | OUTLOOK.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6048 | OUTLOOK.EXE | 52.123.129.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6048 | OUTLOOK.EXE | 52.109.76.243:443 | roaming.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6048 | OUTLOOK.EXE | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 20.7.2.167:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 40.126.32.138:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |