| File name: | 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368 |
| Full analysis: | https://app.any.run/tasks/ecae961f-ce9b-4bdb-80fb-8af7cfe980af |
| Verdict: | Malicious activity |
| Analysis date: | February 22, 2019, 12:58:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, RAR self-extracting archive |
| MD5: | 5A720669642C3055DCCD13B0540814CF |
| SHA1: | 3494401925F765A1F94052D368172E6D6250B050 |
| SHA256: | 7D17EB0420C69953B5A29A68A7D2372EC0935898612F950B0633EA9CEB680368 |
| SSDEEP: | 196608:R2esreAAnL+4Zo0GzZMvDg7I1i9rTuzjwxo:RorePn68Mik7I1cAwW |
MALICIOUS
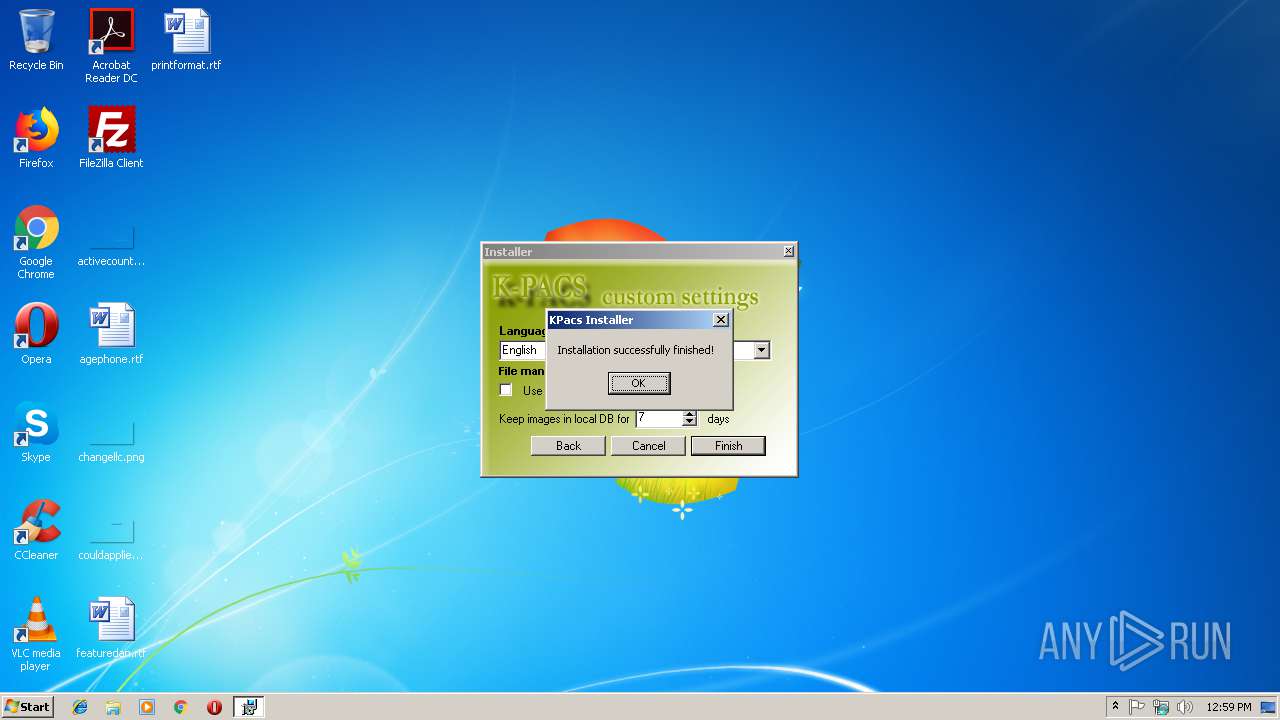
Application was dropped or rewritten from another process
- Install-Eng.exe (PID: 3572)
- k-pacs.exe (PID: 2136)
- k-pacs.exe (PID: 2420)
Loads dropped or rewritten executable
- k-pacs.exe (PID: 2136)
- k-pacs.exe (PID: 2420)
SUSPICIOUS
Executable content was dropped or overwritten
- 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe (PID: 3772)
- Install-Eng.exe (PID: 3572)
Reads internet explorer settings
- 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe (PID: 3772)
Changes tracing settings of the file or console
- 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe (PID: 3772)
Creates files in the Windows directory
- Install-Eng.exe (PID: 3572)
Creates files in the program directory
- Install-Eng.exe (PID: 3572)
Starts CMD.EXE for commands execution
- Install-Eng.exe (PID: 3572)
Creates a software uninstall entry
- Install-Eng.exe (PID: 3572)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | WinRAR Self Extracting archive (94.3) |
|---|---|---|
| .scr | | | Windows screen saver (2.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.1) |
| .exe | | | Win32 Executable (generic) (0.8) |
| .exe | | | Win32 Executable Watcom C++ (generic) (0.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2005:06:26 11:05:32+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 5 |
| CodeSize: | 77824 |
| InitializedDataSize: | 22016 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 26-Jun-2005 09:05:32 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000200 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 26-Jun-2005 09:05:32 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00013000 | 0x00012600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.45699 |
.data | 0x00014000 | 0x00007000 | 0x00000A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.73447 |
.idata | 0x0001B000 | 0x00001000 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.02033 |
.rsrc | 0x0001C000 | 0x00004000 | 0x00003C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.13725 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.10885 | 531 | Latin 1 / Western European | Russian - Russia | RT_MANIFEST |
7 | 3.24143 | 556 | Latin 1 / Western European | Russian - Russia | RT_STRING |
8 | 3.28574 | 946 | Latin 1 / Western European | Russian - Russia | RT_STRING |
9 | 3.04375 | 530 | Latin 1 / Western European | Russian - Russia | RT_STRING |
10 | 3.15563 | 638 | Latin 1 / Western European | Russian - Russia | RT_STRING |
100 | 1.7815 | 20 | Latin 1 / Western European | Process Default Language | RT_GROUP_ICON |
101 | 4.19099 | 2998 | Latin 1 / Western European | Russian - Russia | RT_BITMAP |
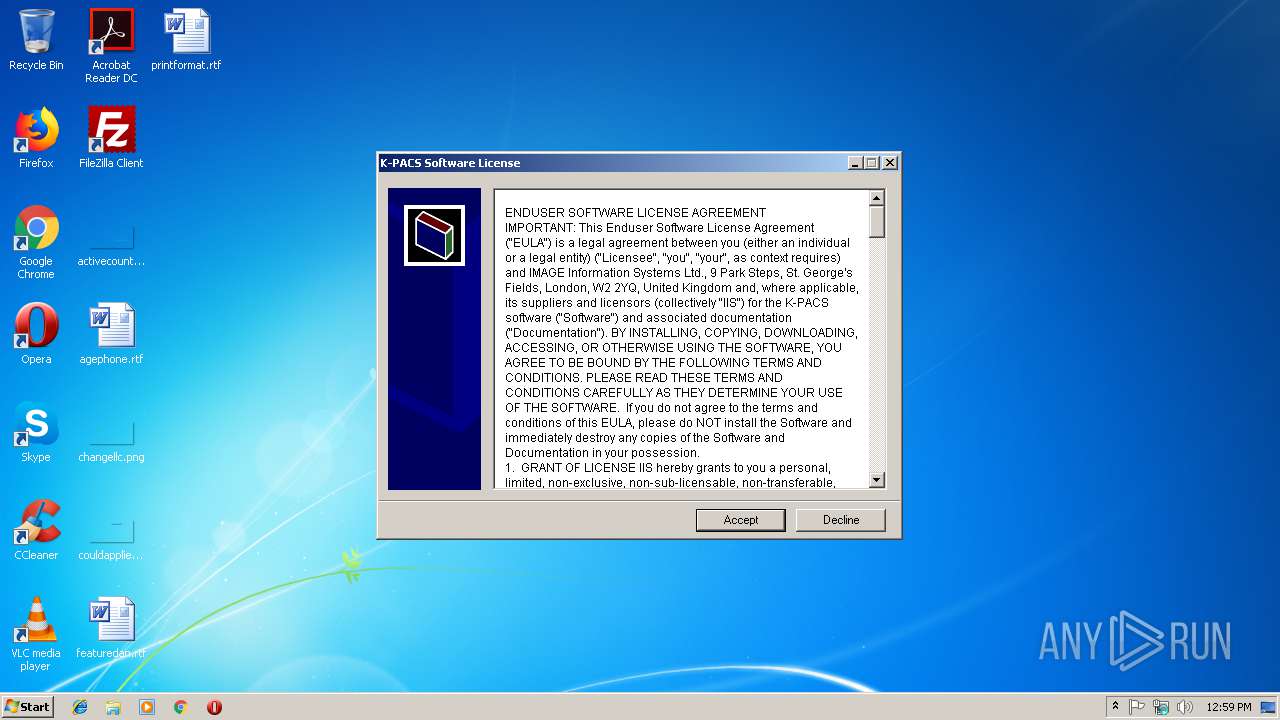
ASKNEXTVOL | 3.42532 | 642 | Latin 1 / Western European | Russian - Russia | RT_DIALOG |
GETPASSWORD1 | 3.29928 | 314 | Latin 1 / Western European | Russian - Russia | RT_DIALOG |
LICENSEDLG | 3.17045 | 232 | Latin 1 / Western European | Russian - Russia | RT_DIALOG |
Imports
ADVAPI32.DLL |
COMCTL32.DLL |
COMDLG32.DLL |
GDI32.DLL |
KERNEL32.DLL |
OLE32.DLL |
SHELL32.DLL |
USER32.DLL |
Total processes
41
Monitored processes
6
Malicious processes
0
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
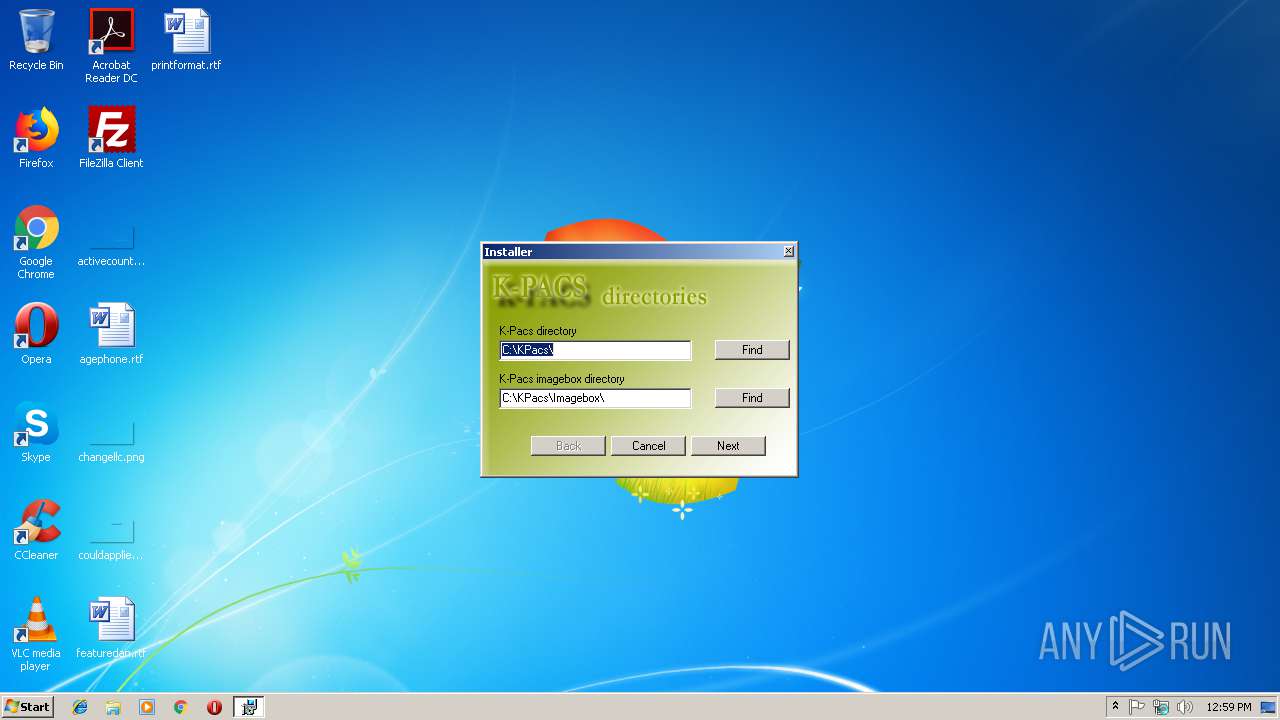
| 2136 | "C:\KPacs\k-pacs.exe" | C:\KPacs\k-pacs.exe | — | explorer.exe | |||||||||||
User: admin Company: Image Information Systems Ltd. Integrity Level: MEDIUM Description: Free Diagnostic Workstation Exit code: 0 Version: 1.5.0.29 Modules
| |||||||||||||||
| 2420 | "C:\KPacs\k-pacs.exe" | C:\KPacs\k-pacs.exe | — | explorer.exe | |||||||||||
User: admin Company: Image Information Systems Ltd. Integrity Level: MEDIUM Description: Free Diagnostic Workstation Exit code: 0 Version: 1.5.0.29 Modules
| |||||||||||||||
| 3036 | cmd /c C:\Users\admin\AppData\Local\Temp\uis536E.bat | C:\Windows\system32\cmd.exe | — | Install-Eng.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3264 | "C:\Users\admin\AppData\Local\Temp\7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe" | C:\Users\admin\AppData\Local\Temp\7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 | |||||||||||||||
| 3572 | "C:\Users\admin\AppData\Local\Temp\Install-Eng.exe" | C:\Users\admin\AppData\Local\Temp\Install-Eng.exe | 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3772 | "C:\Users\admin\AppData\Local\Temp\7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe" | C:\Users\admin\AppData\Local\Temp\7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
665
Read events
629
Write events
36
Delete events
0
Modification events
| (PID) Process: | (3772) 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3772) 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3772) 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3772) 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3772) 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (3772) 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (3772) 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (3772) 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (3772) 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (3772) 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASMANCS |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
Executable files
40
Suspicious files
0
Text files
19
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
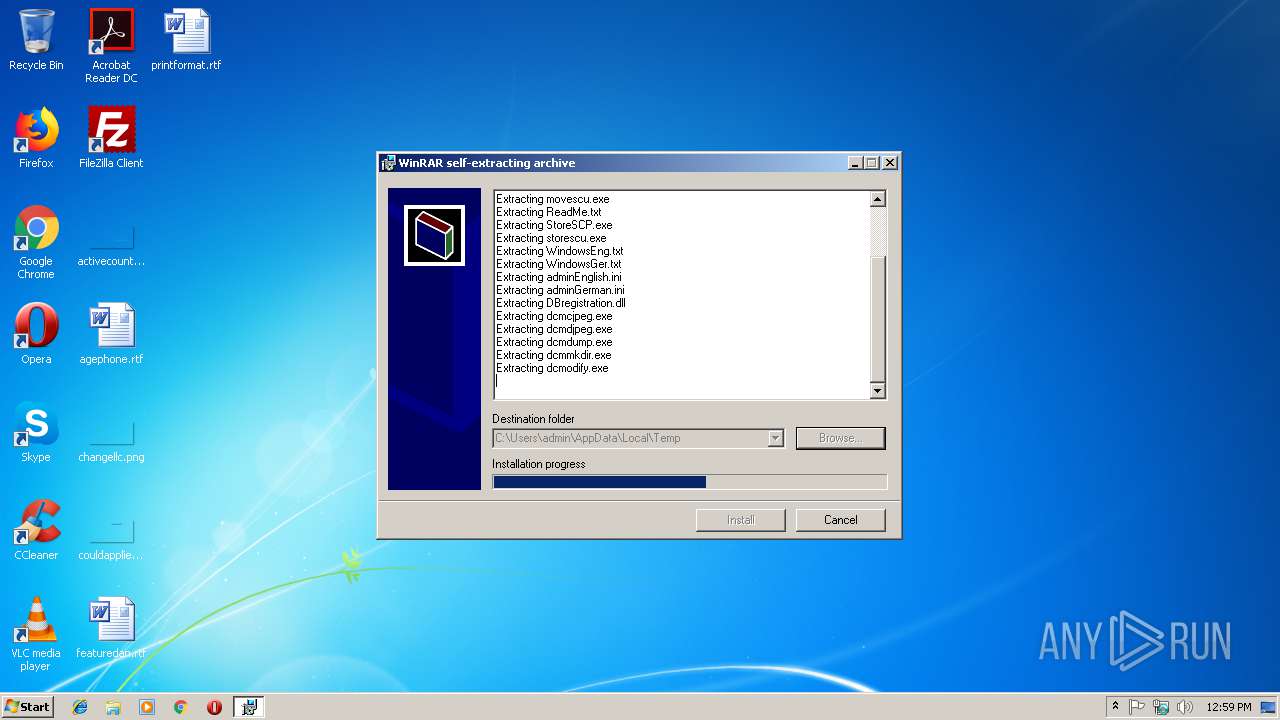
| 3772 | 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe | C:\Users\admin\AppData\Local\Temp\StoreSCP.exe | executable | |
MD5:8C5F4F660C2B27B5556EAE23685F98CA | SHA256:02C1EAB7E5E534EE523B3CD4005A05EC45D1F796E3D5C98D4BBCA6E5ACEB04B7 | |||
| 3772 | 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe | C:\Users\admin\AppData\Local\Temp\KPUninstaller.exe | executable | |
MD5:5579A3764C2A20064C2BADB5E023281D | SHA256:B300DB4EC42A99A4F200D0CE6C6E622966D16A6784A830EFEC0F05CAC34978DF | |||
| 3772 | 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe | C:\Users\admin\AppData\Local\Temp\English.ini | text | |
MD5:5B690614D497DE2FB9B6F9BC67011B9B | SHA256:B7CF03CBACDBC635D7F7B6F459C6CD1F4AF0C27C235FBA59D6301D8F65C70C1F | |||
| 3772 | 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe | C:\Users\admin\AppData\Local\Temp\German.ini | text | |
MD5:F3003E90E4F2D56C1ED1897AC355A232 | SHA256:638A0280F490BA3D965F7B494219A337A5469F5DBD3E80B5FE1E06DAA65F3564 | |||
| 3772 | 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe | C:\Users\admin\AppData\Local\Temp\Install-Eng.exe | executable | |
MD5:41CCA10FD569BE8E50653D442C651197 | SHA256:2D6244198297BAE1FA90BE002C15D5DFB5BF0E2C340A5A541042EC85F44EB412 | |||
| 3772 | 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe | C:\Users\admin\AppData\Local\Temp\kpserver-nt-service.exe | executable | |
MD5:16C98880D2B2C445E8059F58E60A25C3 | SHA256:94DCB2353EF000AABDECA125F6AA6F0FE581CDD86F153A4E9104443E40EE5D2E | |||
| 3772 | 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe | C:\Users\admin\AppData\Local\Temp\findscu.exe | executable | |
MD5:A0BA3355014DF8E21FF69BFAAB175328 | SHA256:031310F25949A8D90159AB5F050FFD0CADF6EFC65F892FAAB27586EE9819E263 | |||
| 3772 | 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe | C:\Users\admin\AppData\Local\Temp\K-PACS EULA Evaluation.txt | text | |
MD5:6832A8535BA4DDC19C867360A56EDFF7 | SHA256:496972FAB9698FA9EC9B7DEE8027F80570863648D13DAEA3EBD65B91BAFCB840 | |||
| 3772 | 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe | C:\Users\admin\AppData\Local\Temp\adminGerman.ini | text | |
MD5:BC9CAA42BE4F8BFD015BCBFEA26ECF32 | SHA256:CE322F4460E66271D52D795FAF08BD9601C095B05EA697988351FCFB147E33B7 | |||
| 3772 | 7d17eb0420c69953b5a29a68a7d2372ec0935898612f950b0633ea9ceb680368.exe | C:\Users\admin\AppData\Local\Temp\DBregistration.dll | executable | |
MD5:004D7F139945736A0DFB040245D8E65A | SHA256:135F09A08478ACB9A7F2FC779853B1A95A17BBCB5B1140FF0B2EFB96A18CC96C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report