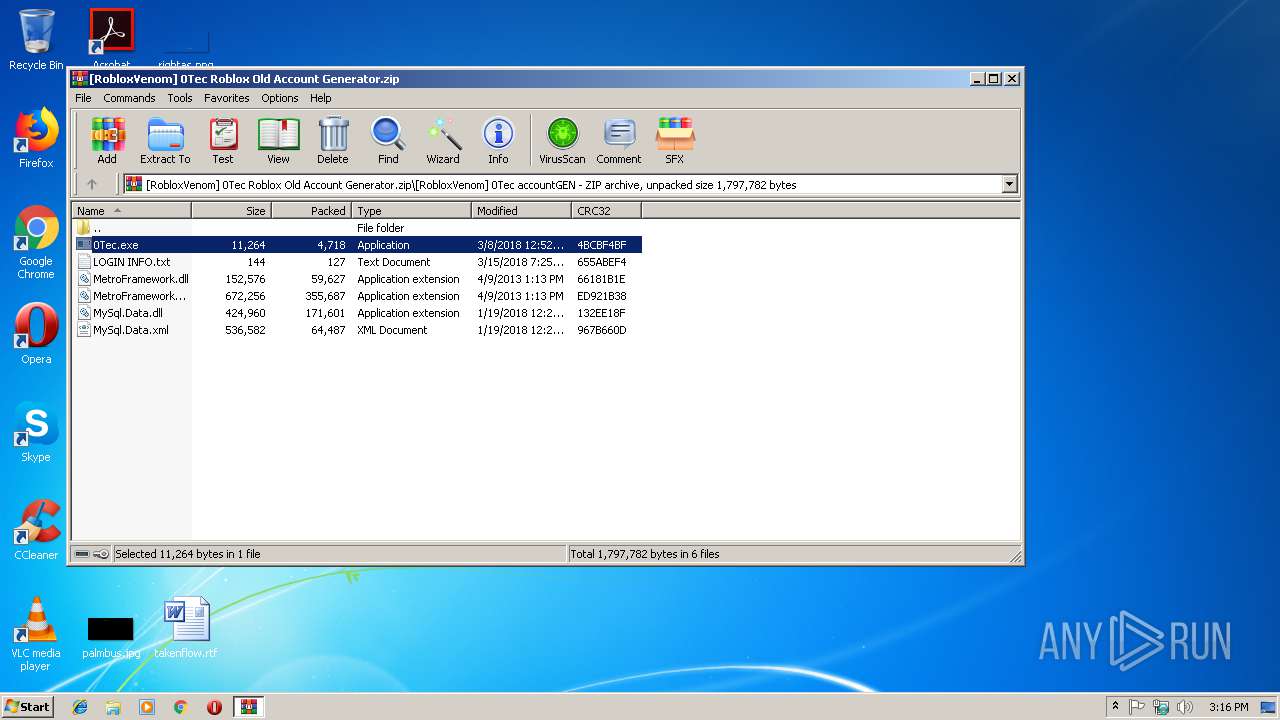
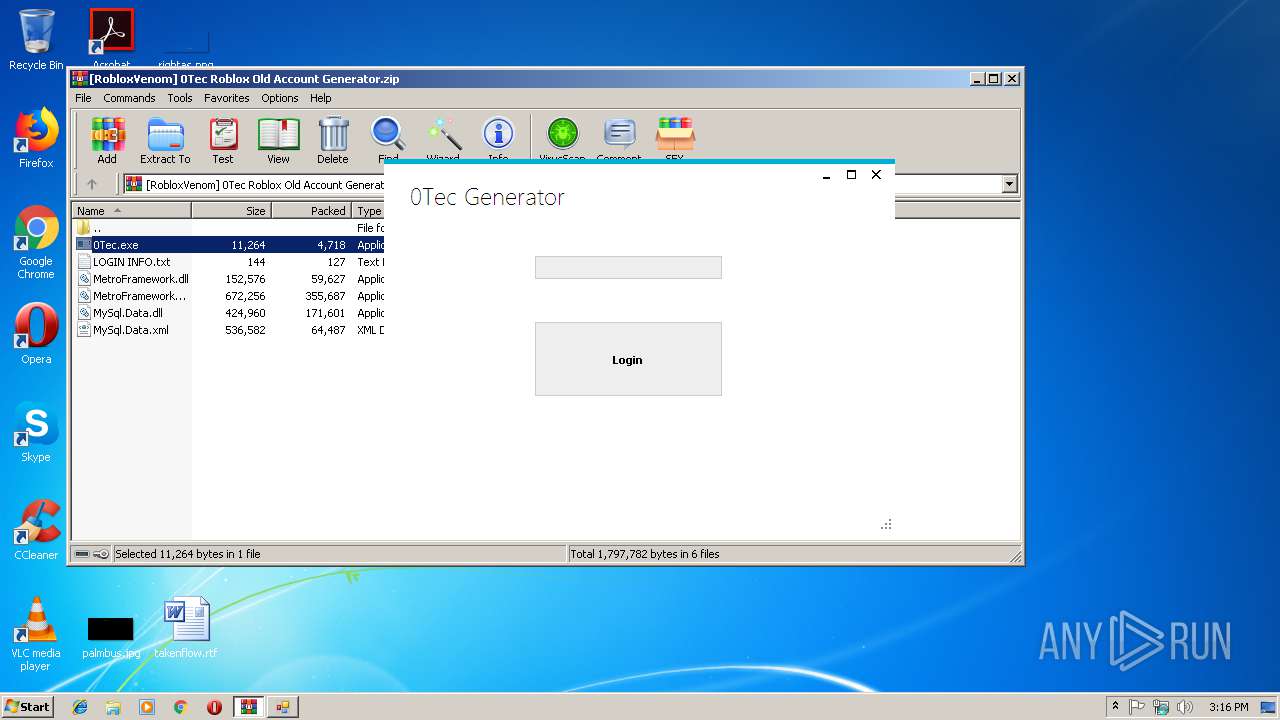
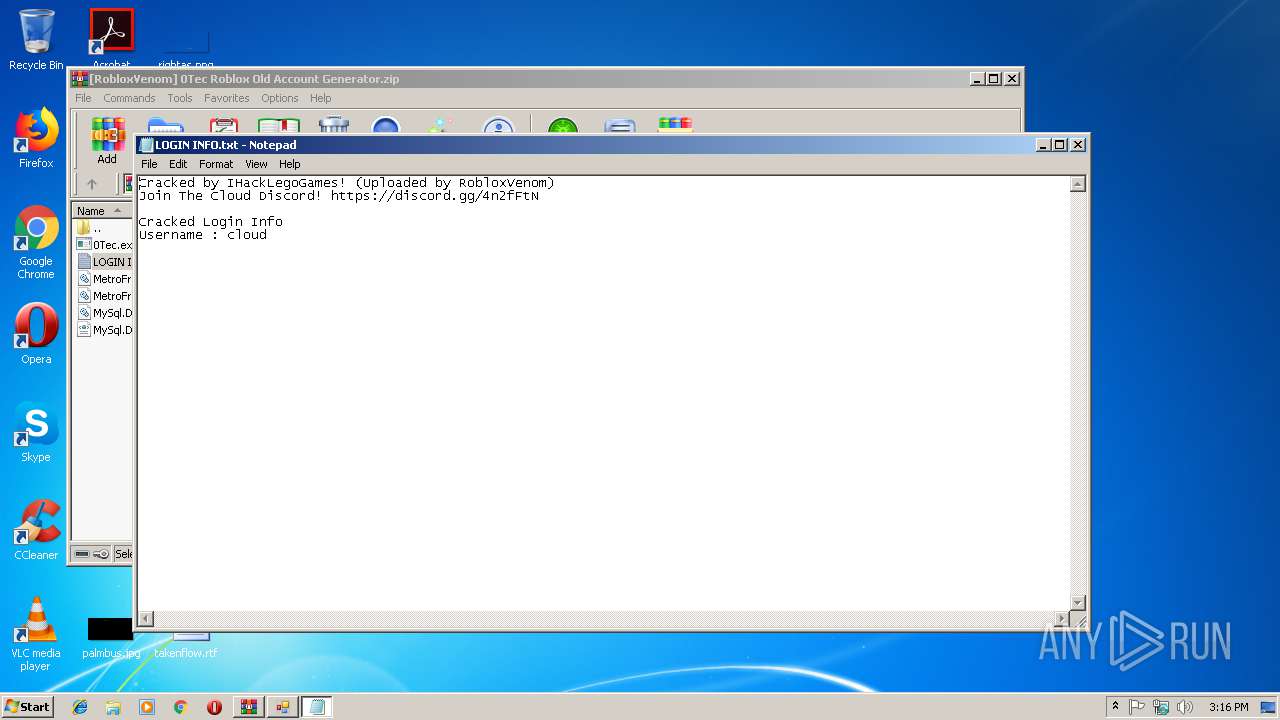
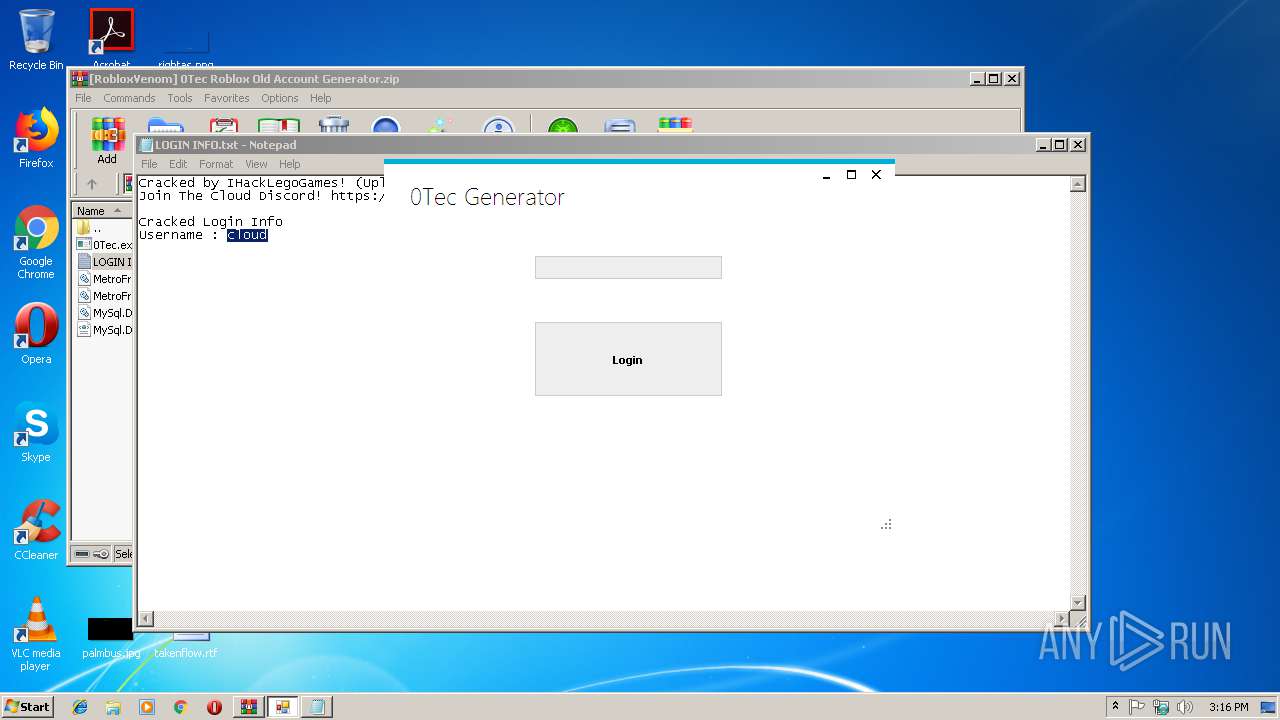
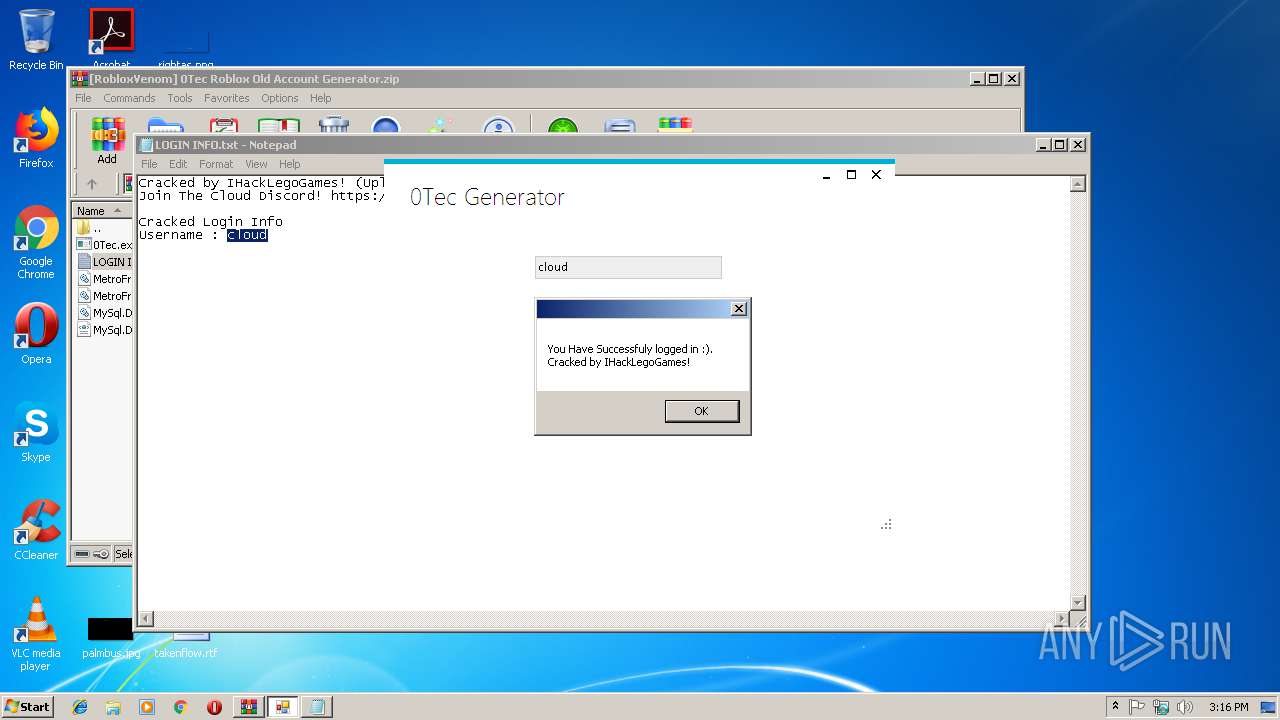
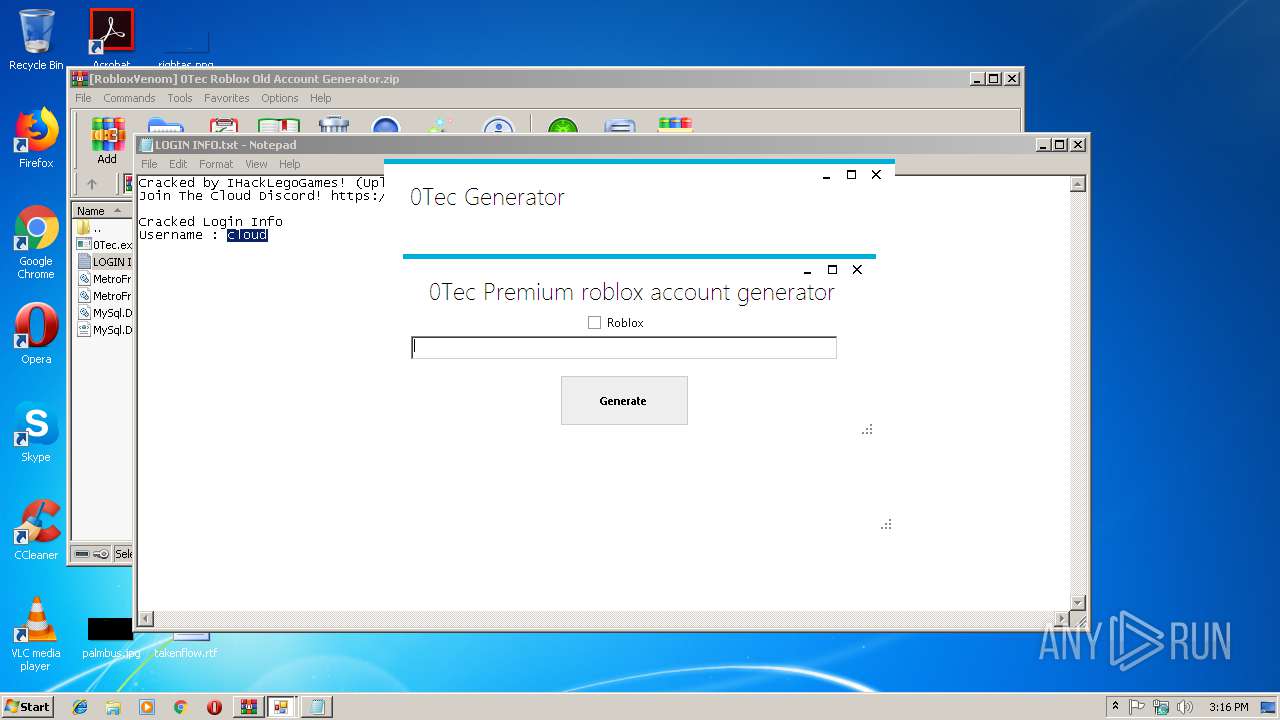
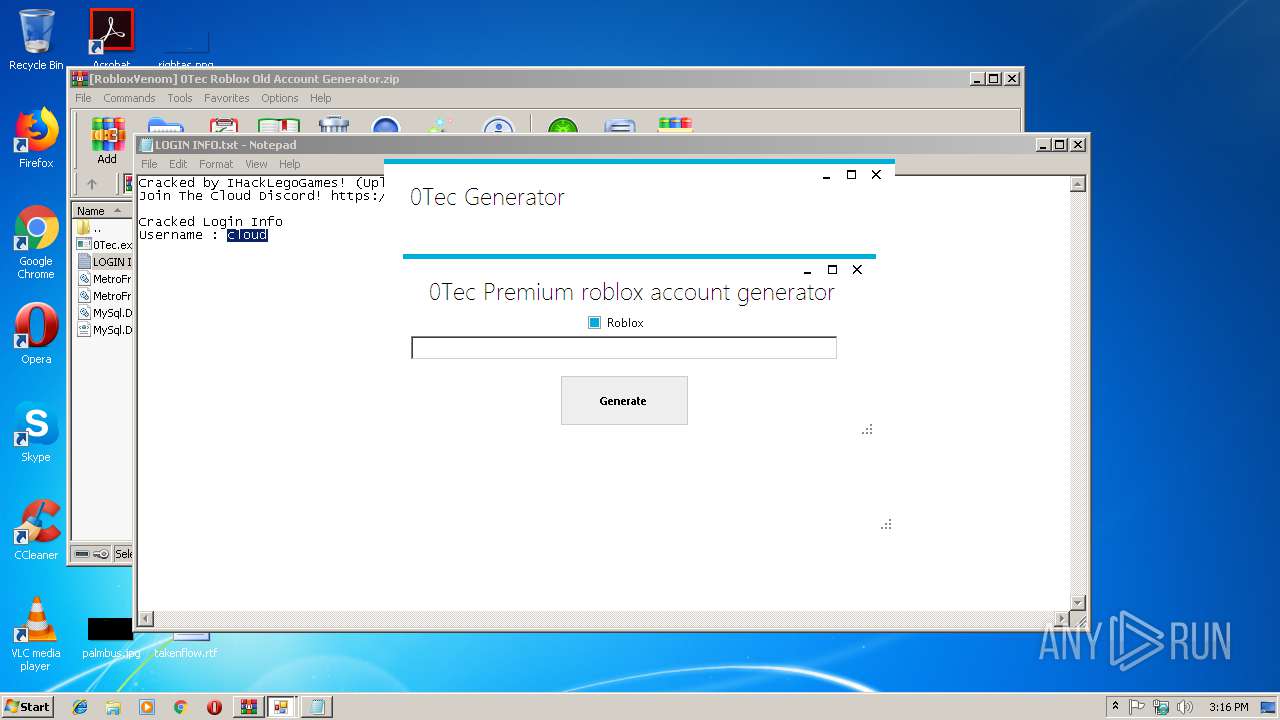
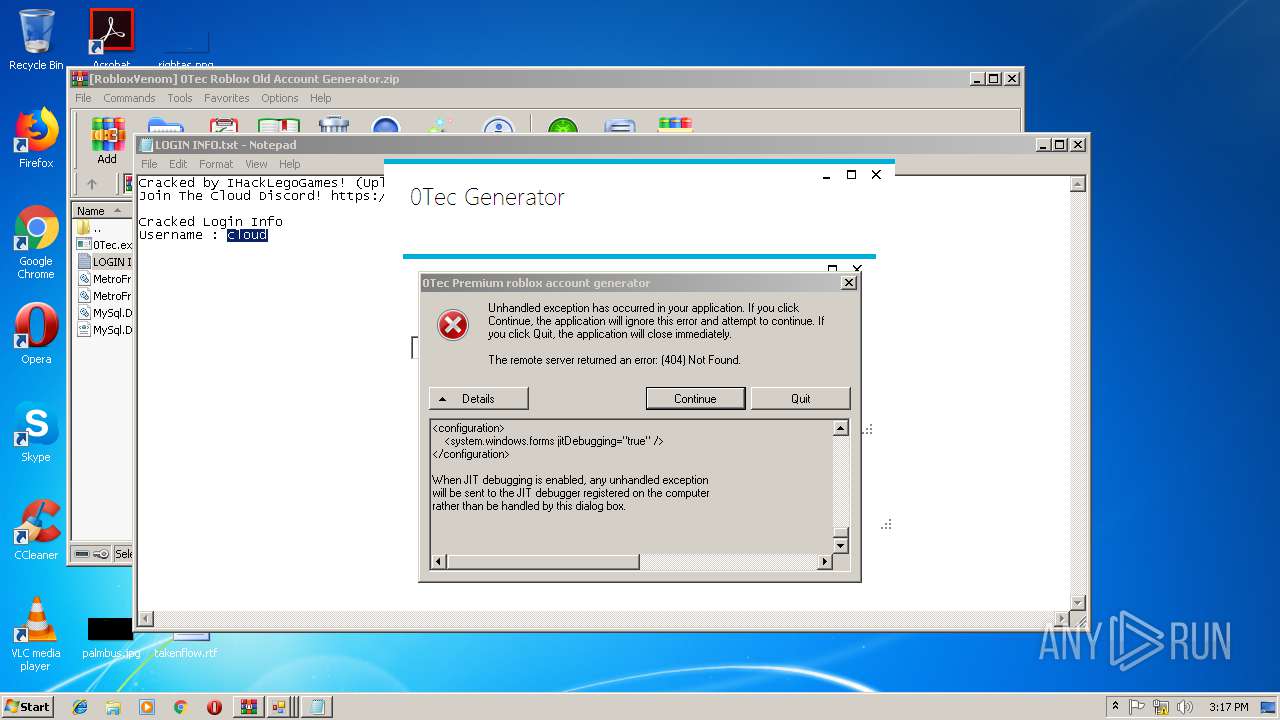
| File name: | [RobloxVenom] 0Tec Roblox Old Account Generator.zip |
| Full analysis: | https://app.any.run/tasks/5fc2567f-9a49-4345-a9f9-80dc602d6e89 |
| Verdict: | Malicious activity |
| Analysis date: | March 06, 2019, 15:15:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 894ED93F7B305911B98E8B337B8BED1E |
| SHA1: | 74BF1EB03D837108AD148F5BA51451E04AFA475B |
| SHA256: | 7D0B5759104B5EA80945FA587D0779AF9616F88DD58F1D999C7B7A95ED04334B |
| SSDEEP: | 12288:JG8AK2/solFivkuE1Hx7bhuxu8ELSqVTQdBl7CdZR3jdgex5Qd4xE4UGz6tD:nJ2/sqgkuE5VbEgd6L7idjZ5QuxE4U6W |
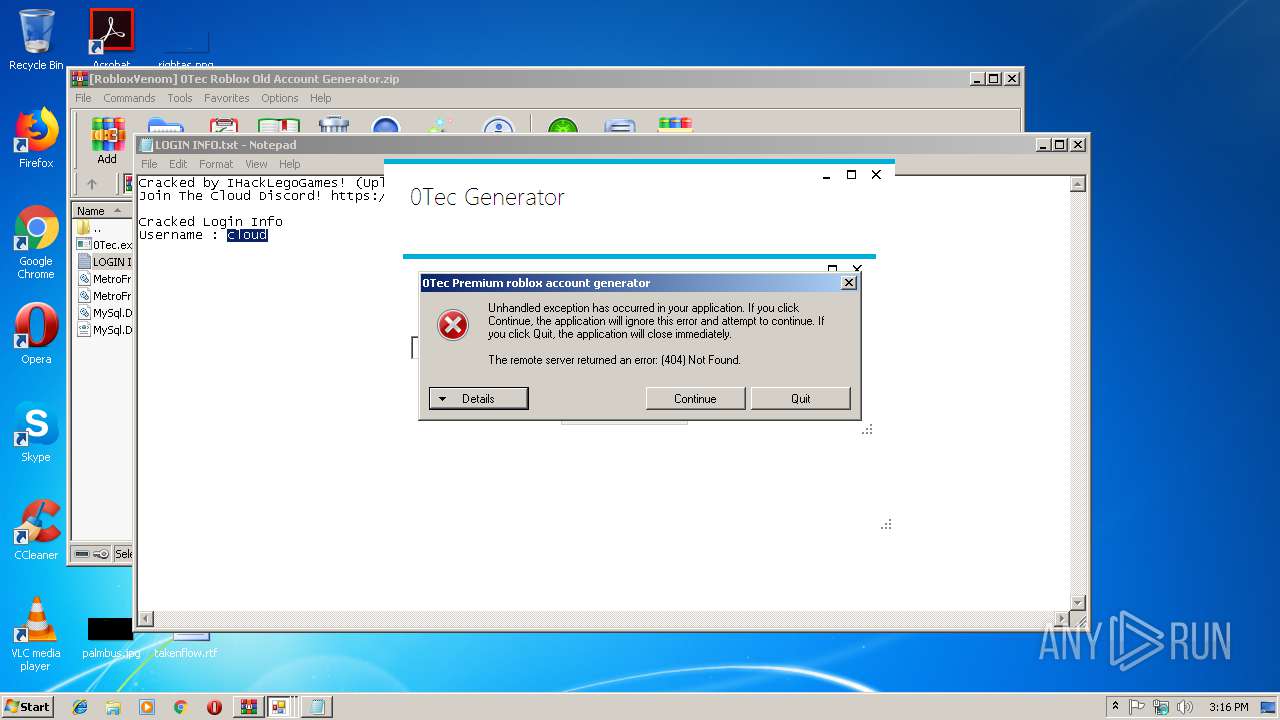
MALICIOUS
Loads dropped or rewritten executable
- 0Tec.exe (PID: 2812)
Application was dropped or rewritten from another process
- 0Tec.exe (PID: 2812)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2952)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2018:03:08 07:09:19 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | [RobloxVenom] 0Tec accountGEN/ |
Total processes
33
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
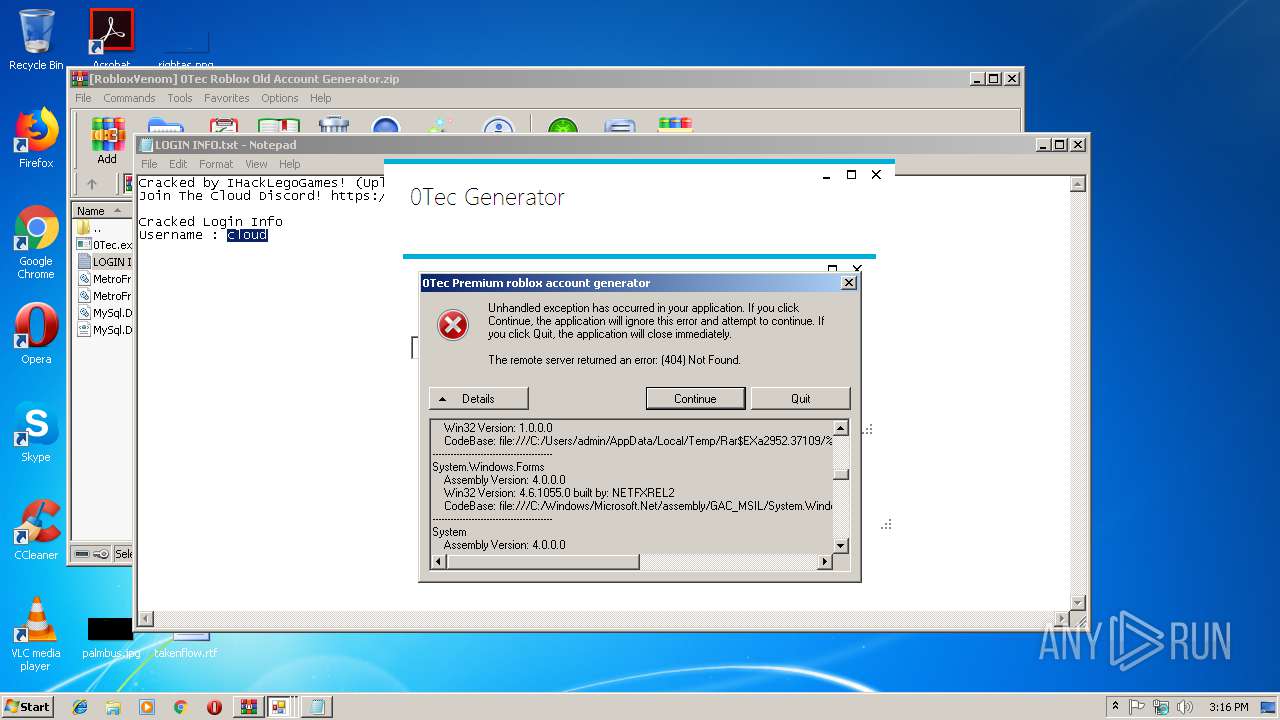
| 2688 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa2952.37531\LOGIN INFO.txt | C:\Windows\system32\NOTEPAD.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
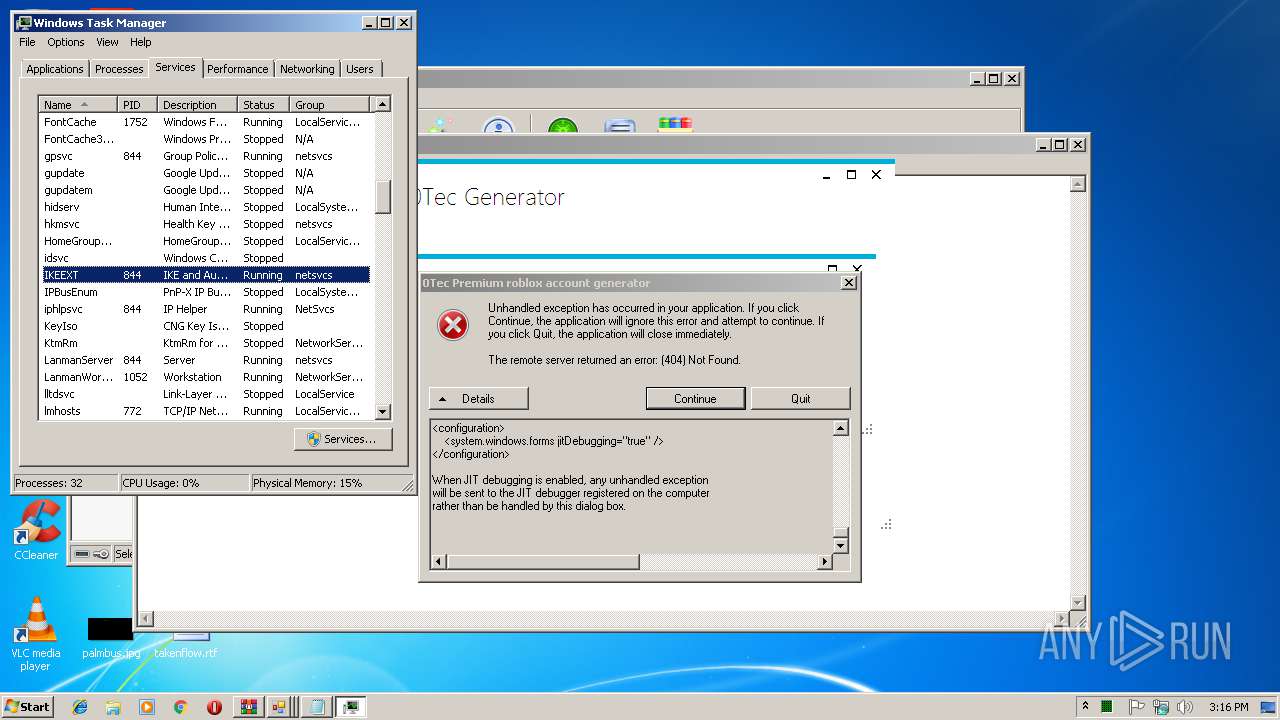
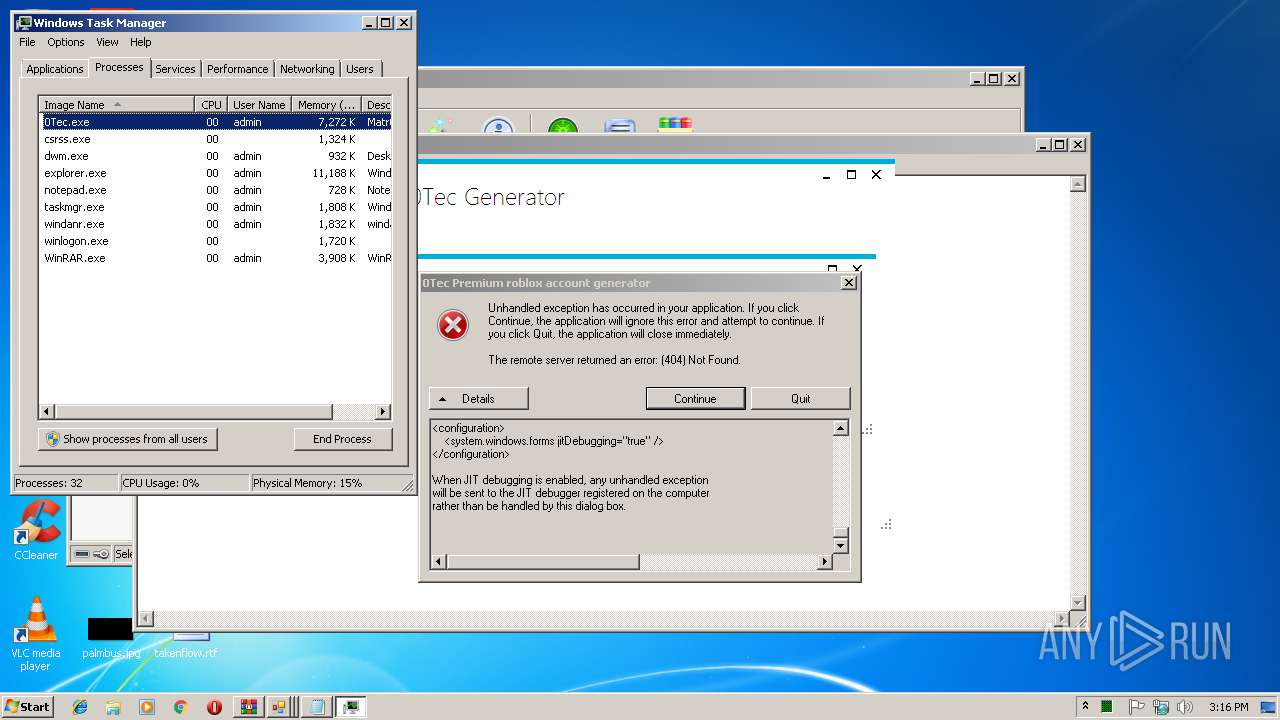
| 2812 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2952.37109\[RobloxVenom] 0Tec accountGEN\0Tec.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2952.37109\[RobloxVenom] 0Tec accountGEN\0Tec.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Matr0x Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2952 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\[RobloxVenom] 0Tec Roblox Old Account Generator.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3052 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
522
Read events
484
Write events
38
Delete events
0
Modification events
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\[RobloxVenom] 0Tec Roblox Old Account Generator.zip | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
4
Suspicious files
0
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2952 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2952.37109\[RobloxVenom] 0Tec accountGEN\LOGIN INFO.txt | text | |
MD5:3AD6B95C514E5A2089E0C7E06B9C11A1 | SHA256:2F90248049A43662A80098DC9439B054B4FE79836D6D2463A8CCA87E2506316C | |||
| 2952 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2952.37109\[RobloxVenom] 0Tec accountGEN\MySql.Data.dll | executable | |
MD5:BA7F4A03742A2A1D92302ED786B0523A | SHA256:3E59934D6A8DF2214484E7E5F9EDADD5974CC72FF687801A8B30C39BEC05B26F | |||
| 2952 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2952.37531\LOGIN INFO.txt | text | |
MD5:3AD6B95C514E5A2089E0C7E06B9C11A1 | SHA256:2F90248049A43662A80098DC9439B054B4FE79836D6D2463A8CCA87E2506316C | |||
| 2952 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2952.37109\[RobloxVenom] 0Tec accountGEN\MetroFramework.Fonts.dll | executable | |
MD5:612080028164B12939751DCCCBB68D4A | SHA256:E96030FDDAF7E78401567EE82480AD75EE48D3556199A3F85C0EC669EDAC2EF4 | |||
| 2952 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2952.37109\[RobloxVenom] 0Tec accountGEN\0Tec.exe | executable | |
MD5:B30C8585BAE1F83A08347976EE1B7455 | SHA256:026126EEF6D73253EAB5C532547BA88D5F6B351E60C29A61079E3F550D248EC9 | |||
| 2952 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2952.37109\[RobloxVenom] 0Tec accountGEN\MetroFramework.dll | executable | |
MD5:44538B311E9EC2BCF0A6452702628D99 | SHA256:BAF326F52D39155D722465947F4CC67E6E90CFD0F89954EAB959568E9BC342AA | |||
| 2952 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2952.37109\[RobloxVenom] 0Tec accountGEN\MySql.Data.xml | xml | |
MD5:113B94BA3230492ED6E263F0207D0AA1 | SHA256:CF3CF12F24A666026D18B1954E703D913FAA1C45A0D104444A2A18DDAAEF7CFF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2812 | 0Tec.exe | 104.20.209.21:443 | pastebin.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| malicious |