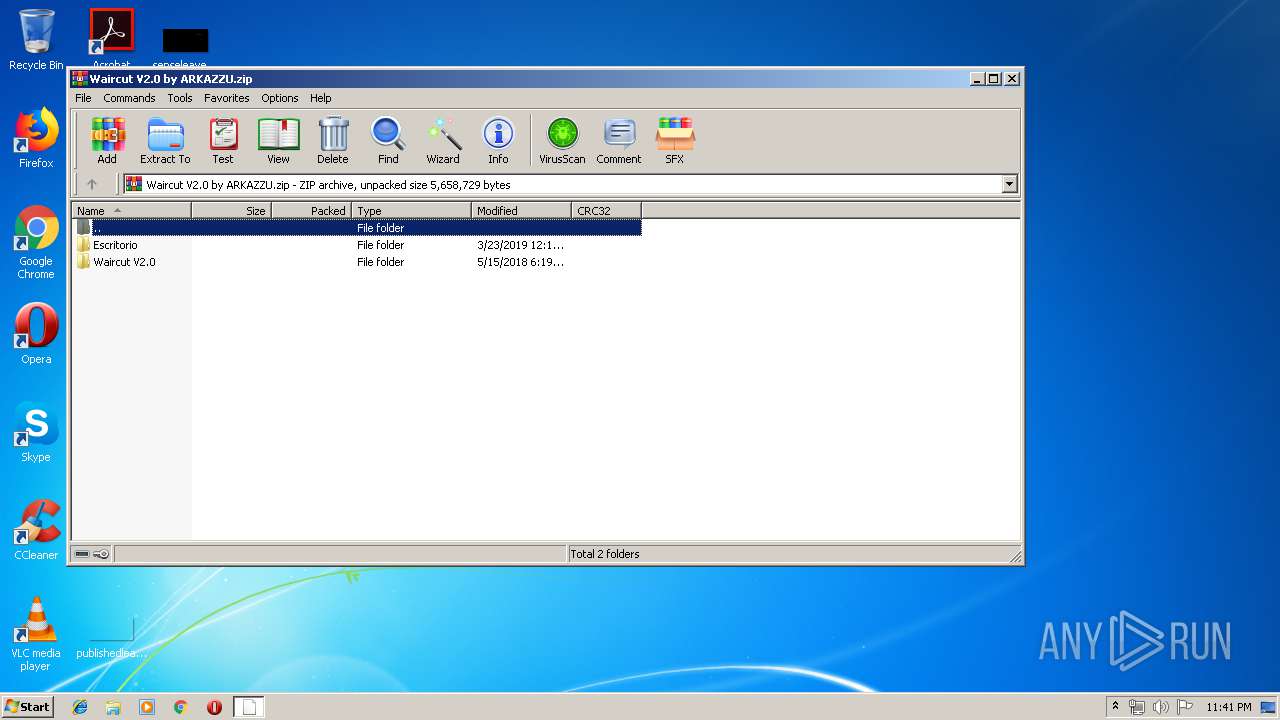
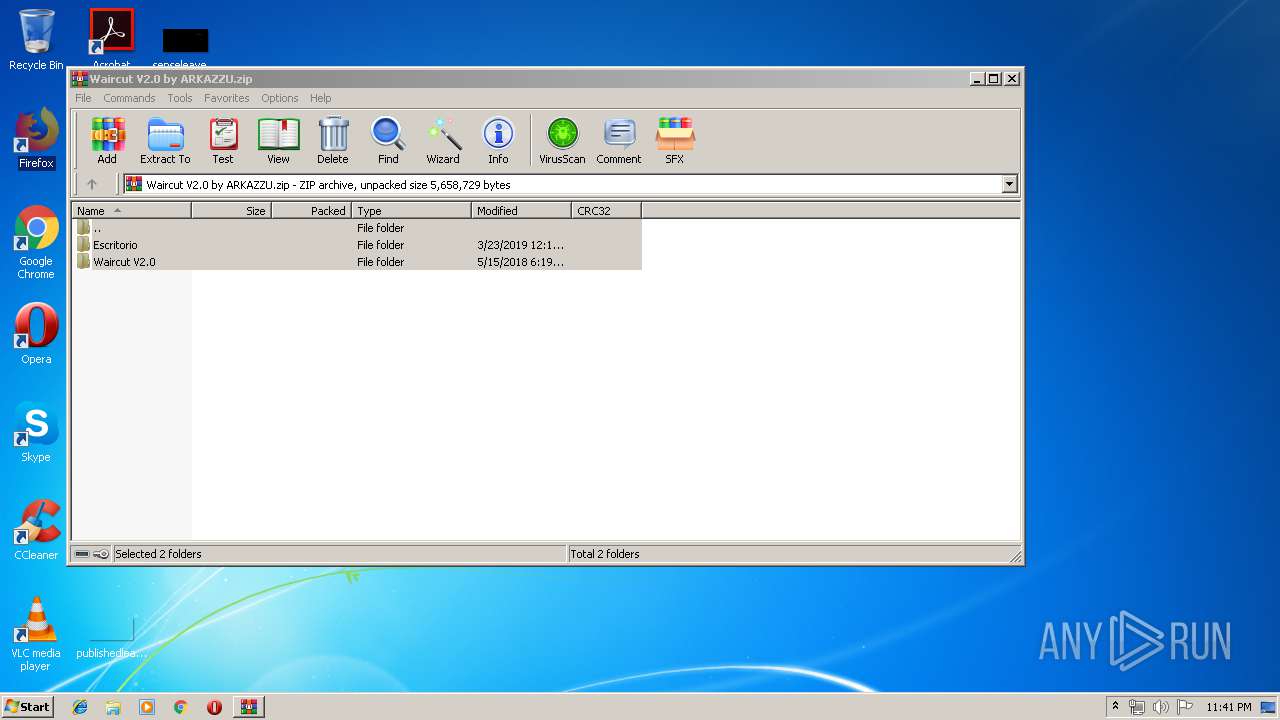
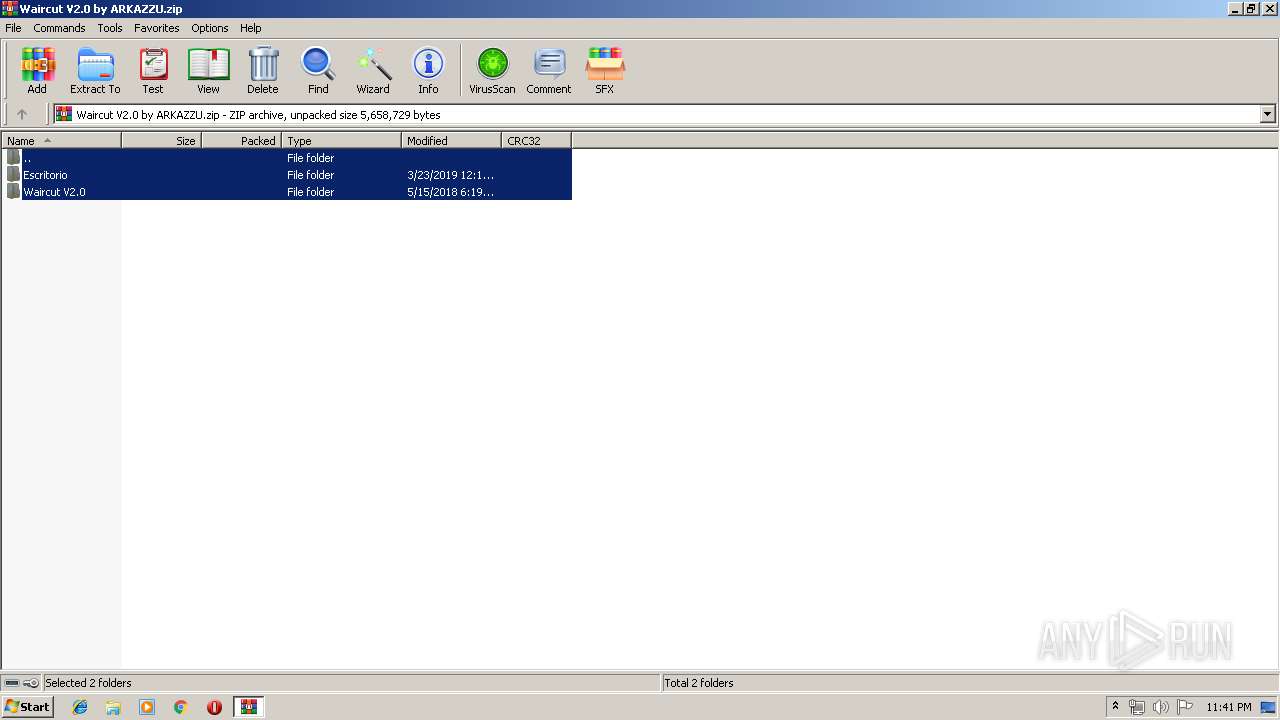
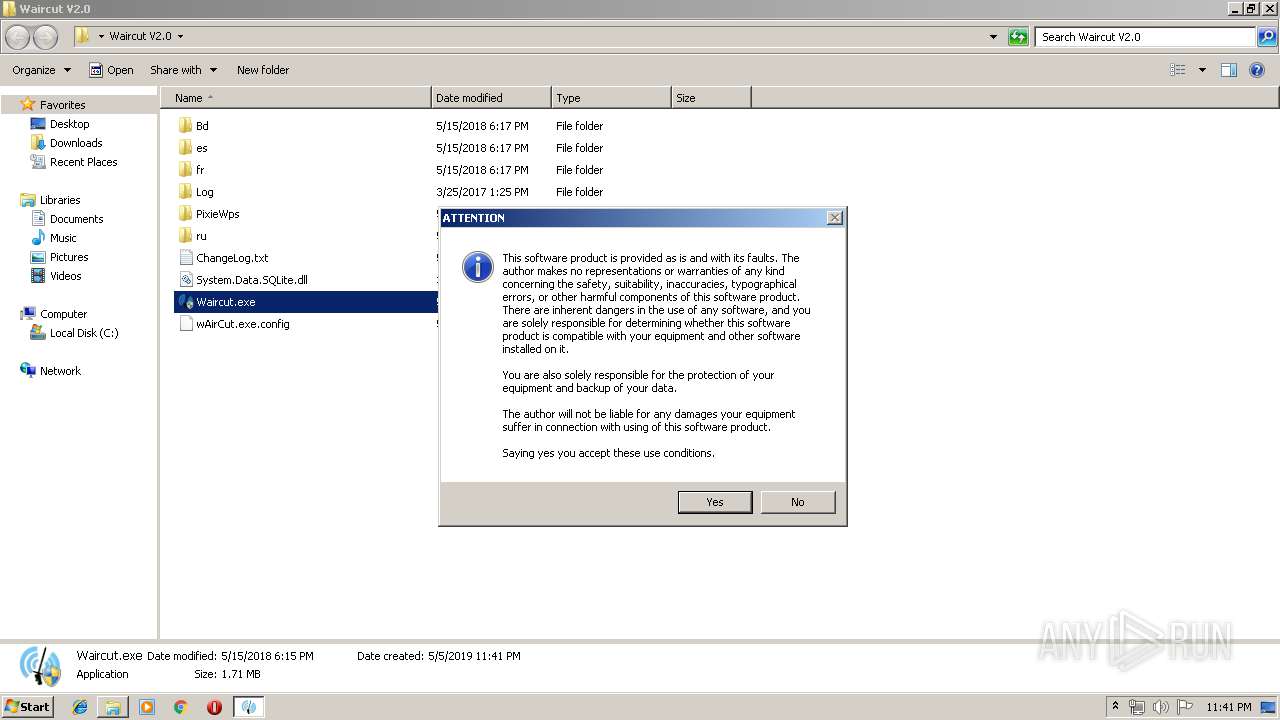
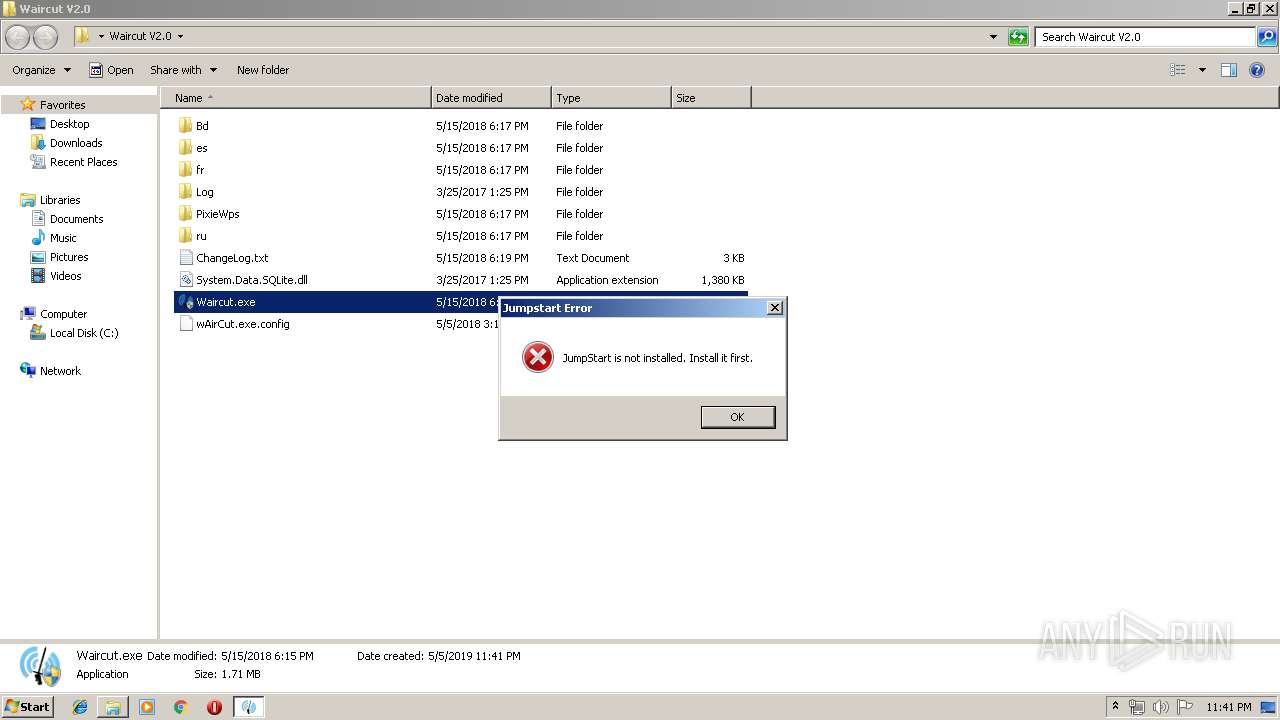
| File name: | Waircut V2.0 by ARKAZZU.zip |
| Full analysis: | https://app.any.run/tasks/9e29e6d3-be27-431f-a75f-22e000031498 |
| Verdict: | Malicious activity |
| Analysis date: | May 05, 2019, 22:40:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 8E8B99321B4EB57105C80742879DE02C |
| SHA1: | 744F849CB1831BFBC96F7C88E789771EFA4B9773 |
| SHA256: | 7D0925FDA57958CB6945BCF020AB9693A59601156194FC8370E1A7D5F64EE19B |
| SSDEEP: | 49152:txvfIKVG0MJfDZFkbB9zhStmAAkwgmyDwtIU77C4O4Ou22lSlV3Syth3h8TZo18z:txvfFVG0MFF6VCabHyUtBC4O41YlV3SD |
MALICIOUS
Application was dropped or rewritten from another process
- Waircut.exe (PID: 2316)
- Waircut.exe (PID: 2860)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3092)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4000)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2018:05:15 19:19:01 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Waircut V2.0/ |
Total processes
37
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2316 | "C:\Users\admin\Desktop\Waircut V2.0\Waircut.exe" | C:\Users\admin\Desktop\Waircut V2.0\Waircut.exe | explorer.exe | ||||||||||||
User: admin Company: Patcher Integrity Level: HIGH Description: waircut Exit code: 0 Version: 2.0 Modules
| |||||||||||||||
| 2860 | "C:\Users\admin\Desktop\Waircut V2.0\Waircut.exe" | C:\Users\admin\Desktop\Waircut V2.0\Waircut.exe | — | explorer.exe | |||||||||||
User: admin Company: Patcher Integrity Level: MEDIUM Description: waircut Exit code: 3221226540 Version: 2.0 Modules
| |||||||||||||||
| 3092 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe5_ Global\UsGthrCtrlFltPipeMssGthrPipe5 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4000 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Waircut V2.0 by ARKAZZU.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
848
Read events
823
Write events
25
Delete events
0
Modification events
| (PID) Process: | (4000) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4000) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4000) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4000) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Waircut V2.0 by ARKAZZU.zip | |||
| (PID) Process: | (4000) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4000) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4000) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4000) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3092) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3092) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
Executable files
6
Suspicious files
0
Text files
5
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2316 | Waircut.exe | C:\Users\admin\AppData\Local\Patcher\Waircut.exe_StrongName_hu55jcqz1l0xzwol4xdhfkxzesvt1zhm\2.0.0.0\0y5ccy5y.newcfg | — | |
MD5:— | SHA256:— | |||
| 4000 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4000.8008\Waircut V2.0\PixieWps\PixieWps.exe | executable | |
MD5:2DE73A1D6D43C3CF9ED9AFC4792FC26E | SHA256:9657EFA0A8C63C8B53923BDC46980B85B7DDDC688FFF9F3C3A1C0545B045235A | |||
| 4000 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4000.8008\Waircut V2.0\Bd\WpsProbePin.db | sqlite | |
MD5:1484B2BFFF2CFB2A6F02BCDC9713F079 | SHA256:BE6C085B1A29D131C78D76EBDA033E7FDF434E152E81A97A87F5BFB41ED355F7 | |||
| 4000 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4000.8008\Waircut V2.0\ChangeLog.txt | text | |
MD5:AE7F9DF96C5304BA802BDB5B32476E48 | SHA256:5CFD82232FC4603228C8F9AE239126B3FE6930150AFFEC8336D9ABA19DEE349D | |||
| 2316 | Waircut.exe | C:\Users\admin\AppData\Local\Patcher\Waircut.exe_StrongName_hu55jcqz1l0xzwol4xdhfkxzesvt1zhm\2.0.0.0\user.config | xml | |
MD5:— | SHA256:— | |||
| 4000 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4000.8008\Waircut V2.0\System.Data.SQLite.dll | executable | |
MD5:DEAF98E10B82FC9BC2476A432724492F | SHA256:3CCAF0BF3B927ACEDA3645F0A592C2DB6B9AFB7680E766042BF9CA6D51774886 | |||
| 4000 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4000.8008\Waircut V2.0\Waircut.exe | executable | |
MD5:9D11A8641AAE3C20C2F39C89E75798AB | SHA256:600986E9892988BA772CE853C559FB7C28186E84422AF9AED53F2327F5FF45DE | |||
| 4000 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4000.8008\Waircut V2.0\Bd\ApLog.db | sqlite | |
MD5:8B9F4E200FABD3D75D00EAB9AEDB3C2E | SHA256:8C115D8E85DCC74130A152ACE7F8BA65AE23FF6E1928F9D984B6B9F017A64C4D | |||
| 4000 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4000.8008\Waircut V2.0\ru\Waircut.resources.dll | executable | |
MD5:A3F3D0098FB43D970873281FE07AF65F | SHA256:F7D494BBBA03B8BEF611E6A91D92EA5490EDAF384E421AF8342244836F1CE6F7 | |||
| 4000 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4000.8008\Waircut V2.0\es\Waircut.resources.dll | executable | |
MD5:1849C11F96636115D8BB784824472295 | SHA256:71CEE5AC2078AE405EC8D0F2305A8987FE08D7E608F6062659D22160DC4B7851 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report