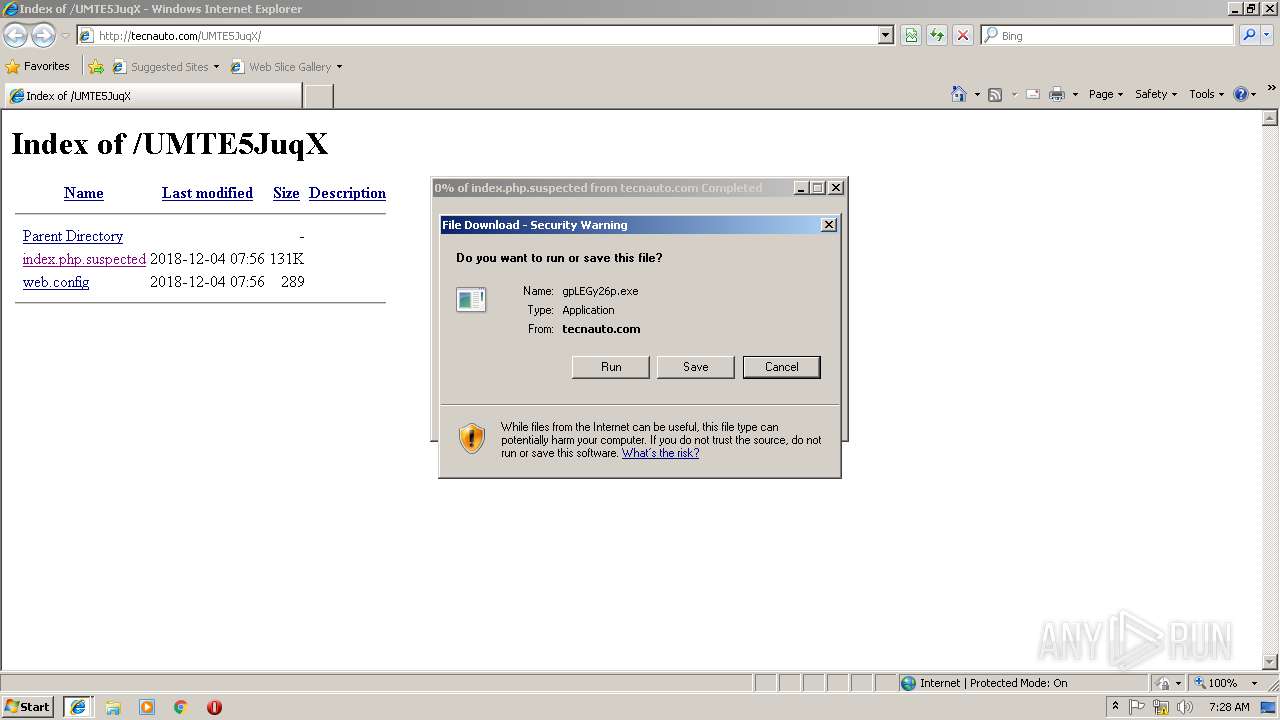
| URL: | http://burnbrighter.com/mQ5tBipU |
| Full analysis: | https://app.any.run/tasks/ade58be0-dcf7-4584-8a2a-768552956337 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | December 06, 2018, 07:26:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | B76D656E801F1B38276A4F4624B7779A |
| SHA1: | 4011C4386860A4F3A662ED04CA90A0F6FCA76C2D |
| SHA256: | 7D0710B1FC0138AD76D42C8D3D9F8CDB86A7131D965ECB8C41A26CE30274148A |
| SSDEEP: | 3:N1KcCzcOgfQ6an:Ccoua |
MALICIOUS
Downloads executable files from the Internet
- iexplore.exe (PID: 2416)
- iexplore.exe (PID: 3092)
Application was dropped or rewritten from another process
- index.php[1].exe (PID: 3880)
- index.php[1].exe (PID: 2632)
- archivesymbol.exe (PID: 3868)
- archivesymbol.exe (PID: 2404)
Changes the autorun value in the registry
- archivesymbol.exe (PID: 2404)
EMOTET was detected
- archivesymbol.exe (PID: 2404)
SUSPICIOUS
Executable content was dropped or overwritten
- iexplore.exe (PID: 2416)
- iexplore.exe (PID: 3792)
- index.php[1].exe (PID: 2632)
Starts itself from another location
- index.php[1].exe (PID: 2632)
Cleans NTFS data-stream (Zone Identifier)
- index.php[1].exe (PID: 2632)
Connects to unusual port
- archivesymbol.exe (PID: 2404)
INFO
Application launched itself
- iexplore.exe (PID: 3792)
- iexplore.exe (PID: 2952)
Reads internet explorer settings
- iexplore.exe (PID: 2416)
Reads Internet Cache Settings
- iexplore.exe (PID: 2416)
- iexplore.exe (PID: 3092)
Changes internet zones settings
- iexplore.exe (PID: 3792)
- iexplore.exe (PID: 2952)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
40
Monitored processes
8
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2404 | "C:\Users\admin\AppData\Local\archivesymbol\archivesymbol.exe" | C:\Users\admin\AppData\Local\archivesymbol\archivesymbol.exe | archivesymbol.exe | ||||||||||||
User: admin Company: Nexon Corp. Integrity Level: MEDIUM Description: Softpub Forwarder DLL Exit code: 0 Version: 6.1.7600.1 Modules
| |||||||||||||||
| 2416 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3792 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2632 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\index.php[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\index.php[1].exe | index.php[1].exe | ||||||||||||
User: admin Company: Nexon Corp. Integrity Level: MEDIUM Description: Softpub Forwarder DLL Exit code: 0 Version: 6.1.7600.1 Modules
| |||||||||||||||
| 2952 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3092 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2952 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3792 | "C:\Program Files\Internet Explorer\iexplore.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3868 | "C:\Users\admin\AppData\Local\archivesymbol\archivesymbol.exe" | C:\Users\admin\AppData\Local\archivesymbol\archivesymbol.exe | — | index.php[1].exe | |||||||||||
User: admin Company: Nexon Corp. Integrity Level: MEDIUM Description: Softpub Forwarder DLL Exit code: 0 Version: 6.1.7600.1 Modules
| |||||||||||||||
| 3880 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\index.php[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\index.php[1].exe | — | iexplore.exe | |||||||||||
User: admin Company: Nexon Corp. Integrity Level: MEDIUM Description: Softpub Forwarder DLL Exit code: 0 Version: 6.1.7600.1 Modules
| |||||||||||||||
Total events
1 083
Read events
953
Write events
126
Delete events
4
Modification events
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {49309993-F928-11E8-91D7-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E2070C000400060007001A002F001A01 | |||
Executable files
3
Suspicious files
1
Text files
7
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2952 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2952 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFC4BD6E1242B26269.TMP | — | |
MD5:— | SHA256:— | |||
| 3792 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\0UU90R59\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3792 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2952 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF5BCC051E6E74E7E1.TMP | — | |
MD5:— | SHA256:— | |||
| 2952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{49309993-F928-11E8-91D7-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
| 2416 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\UMTE5JuqX[1].txt | — | |
MD5:— | SHA256:— | |||
| 2952 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{49309994-F928-11E8-91D7-5254004A04AF}.dat | binary | |
MD5:— | SHA256:— | |||
| 2416 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\UMTE5JuqX[1].htm | html | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
7
DNS requests
4
Threats
9
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3792 | iexplore.exe | GET | 404 | 80.172.234.6:80 | http://tecnauto.com/favicon.ico | PT | — | — | whitelisted |
2416 | iexplore.exe | GET | 301 | 80.172.234.6:80 | http://tecnauto.com/UMTE5JuqX | PT | html | 238 b | whitelisted |
3092 | iexplore.exe | GET | 301 | 64.90.43.227:80 | http://burnbrighter.com/mQ5tBipU | US | html | 199 b | malicious |
3092 | iexplore.exe | GET | 200 | 64.90.43.227:80 | http://burnbrighter.com/mQ5tBipU/ | US | executable | 120 Kb | malicious |
2416 | iexplore.exe | GET | 200 | 80.172.234.6:80 | http://tecnauto.com/UMTE5JuqX/ | PT | html | 973 b | whitelisted |
2416 | iexplore.exe | GET | 200 | 80.172.234.6:80 | http://tecnauto.com/UMTE5JuqX/index.php.suspected | PT | executable | 120 Kb | whitelisted |
2404 | archivesymbol.exe | GET | 200 | 190.220.69.69:990 | http://190.220.69.69:990/ | AR | binary | 132 b | suspicious |
2952 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
3792 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2952 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3092 | iexplore.exe | 64.90.43.227:80 | burnbrighter.com | New Dream Network, LLC | US | suspicious |
3792 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2416 | iexplore.exe | 80.172.234.6:80 | tecnauto.com | Claranet Ltd | PT | suspicious |
3792 | iexplore.exe | 80.172.234.6:80 | tecnauto.com | Claranet Ltd | PT | suspicious |
2404 | archivesymbol.exe | 190.220.69.69:990 | — | Techtel LMDS Comunicaciones Interactivas S.A. | AR | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
burnbrighter.com |
| malicious |
tecnauto.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3092 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3092 | iexplore.exe | A Network Trojan was detected | ET TROJAN VBScript Redirect Style Exe File Download |
3092 | iexplore.exe | Misc activity | ET INFO EXE CheckRemoteDebuggerPresent (Used in Malware Anti-Debugging) |
3092 | iexplore.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2416 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2416 | iexplore.exe | Misc activity | ET INFO EXE CheckRemoteDebuggerPresent (Used in Malware Anti-Debugging) |
2416 | iexplore.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
2404 | archivesymbol.exe | A Network Trojan was detected | SC SPYWARE Spyware Emotet Win32 |
2404 | archivesymbol.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |