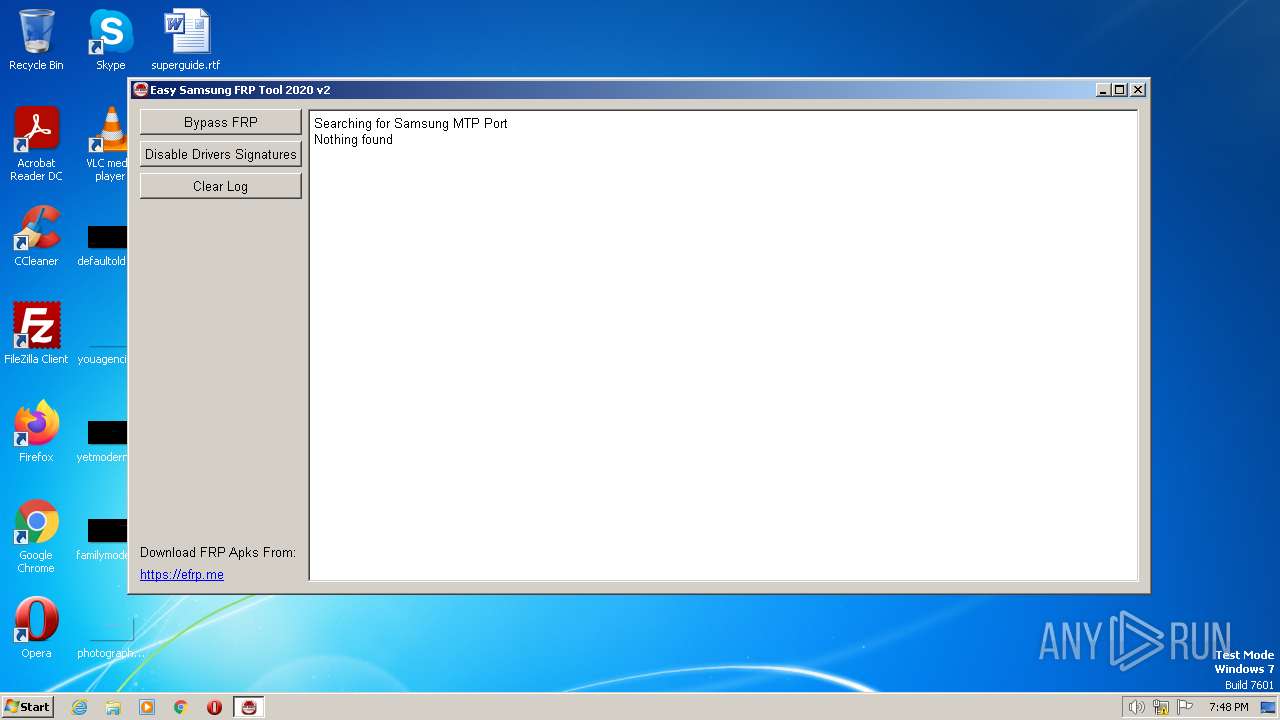
| File name: | SamsungFrp2020.exe |
| Full analysis: | https://app.any.run/tasks/f3e72a49-b273-4a92-9729-3000a6c1efcf |
| Verdict: | Malicious activity |
| Analysis date: | June 25, 2023, 18:47:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 258E7698054FC8EAF934C7E03FC96E9E |
| SHA1: | 0ED5251DE551C42A04F09153C7A1970D16CE2E87 |
| SHA256: | 7CFDF65B1F93BD600A4E7CADBCFECCC634D0C34B5B098740AF1CF2AFA7C64B97 |
| SSDEEP: | 98304:k2io0F6n4DKhOPqSUze/aEO0j514bP35GB2sB9mqq3zY+WziaHLwU9S2iZtJ:kA0pD8OPqZx0z64rB/8CiaHEU9SZtJ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads settings of System Certificates
- SamsungFrp2020.exe (PID: 3660)
Reads the Internet Settings
- SamsungFrp2020.exe (PID: 3660)
INFO
Checks supported languages
- SamsungFrp2020.exe (PID: 3660)
The process checks LSA protection
- SamsungFrp2020.exe (PID: 3660)
Reads the machine GUID from the registry
- SamsungFrp2020.exe (PID: 3660)
Reads the computer name
- SamsungFrp2020.exe (PID: 3660)
Application launched itself
- iexplore.exe (PID: 1788)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | DOS Executable Generic (100) |
|---|
EXIF
EXE
| Subsystem: | Windows GUI |
|---|---|
| SubsystemVersion: | 6 |
| ImageVersion: | - |
| OSVersion: | 6 |
| EntryPoint: | 0x1001000 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 6723072 |
| CodeSize: | 10220032 |
| LinkerVersion: | 14.16 |
| PEType: | PE32 |
| ImageFileCharacteristics: | Executable, 32-bit |
| TimeStamp: | 2020:10:03 16:16:20+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 03-Oct-2020 16:16:20 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0xCCCF |
| Pages in file: | 0xED78 |
| Relocations: | 0xB8F5 |
| Size of header: | 0xA76F |
| Min extra paragraphs: | 0xF05F |
| Max extra paragraphs: | 0x9DA4 |
| Initial SS value: | 0xF6CE |
| Initial SP value: | 0x54CA |
| Checksum: | 0x01AA |
| Initial IP value: | 0xE999 |
| Initial CS value: | 0xE04F |
| Overlay number: | 0xA079 |
| OEM identifier: | 0xEE16 |
| OEM information: | 0x56FA |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 03-Oct-2020 16:16:20 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
0x01001000 | 0x0001A000 | 0x00019B07 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99735 | |
.rsrc | 0x00FDE000 | 0x000212CC | 0x000212CC | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.34465 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.88996 | 387 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 5.24446 | 67624 | UNKNOWN | English - United States | RT_ICON |
3 | 5.58606 | 16936 | UNKNOWN | English - United States | RT_ICON |
4 | 5.82179 | 9640 | UNKNOWN | English - United States | RT_ICON |
5 | 6.02284 | 4264 | UNKNOWN | English - United States | RT_ICON |
6 | 6.24286 | 1128 | UNKNOWN | English - United States | RT_ICON |
46600 | 7.21291 | 299 | UNKNOWN | UNKNOWN | RT_RCDATA |
IDI_ICON1 | 2.79908 | 90 | UNKNOWN | English - United States | RT_GROUP_ICON |
Imports
advapi32.dll |
comctl32.dll |
kernel32.dll |
user32.dll |
Total processes
44
Monitored processes
4
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1788 | "C:\Program Files\Internet Explorer\iexplore.exe" https://www.google.com/url?sa=t&rct=j&q=&esrc=s&source=web&cd=&cad=rja&uact=8&ved=2ahUKEwi5lObcypTsAhVh-yoKHRUeAHIQFjAPegQICBAC&url=https%3A%2F%2Feasy-firmware.com%2Findex.php%3Fa%3Ddownloads%26b%3Dfolder%26id%3D5691&usg=AOvVaw1nTDxuCisH83j8a8AgvYGa | C:\Program Files\Internet Explorer\iexplore.exe | SamsungFrp2020.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2240 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1788 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3096 | "C:\Users\admin\AppData\Local\Temp\SamsungFrp2020.exe" | C:\Users\admin\AppData\Local\Temp\SamsungFrp2020.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
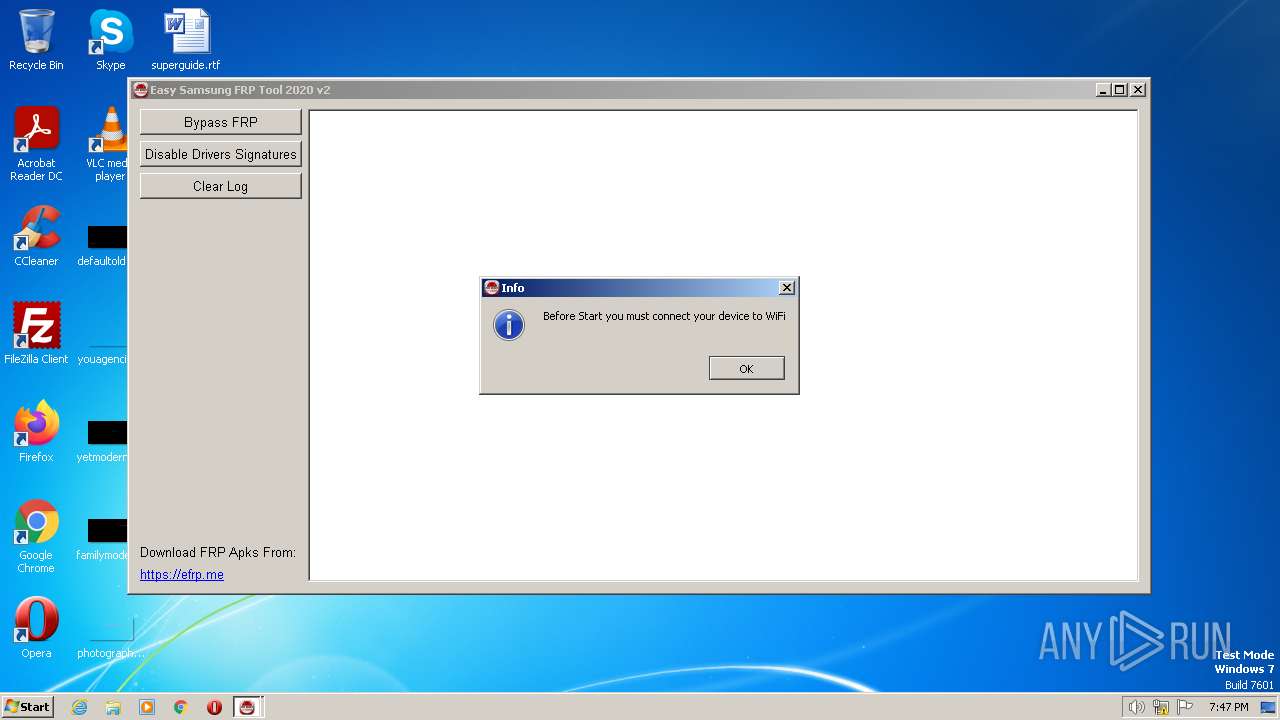
| 3660 | "C:\Users\admin\AppData\Local\Temp\SamsungFrp2020.exe" | C:\Users\admin\AppData\Local\Temp\SamsungFrp2020.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
19 110
Read events
18 982
Write events
127
Delete events
1
Modification events
| (PID) Process: | (3660) SamsungFrp2020.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: Explorer.EXE | |||
| (PID) Process: | (1788) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (1788) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (1788) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (1788) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1788) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1788) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1788) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1788) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1788) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
0
Suspicious files
50
Text files
82
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2240 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:AA62F8CE77E072C8160C71B5DF3099B0 | SHA256:3EB4927C4D9097DC924FCDE21B56D01D5D1EF61B7D22BFB6786E3B546B33E176 | |||
| 2240 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\30BCF8D79B1225AC4F40686E58D30D95 | binary | |
MD5:D0D9589C4266BE062C589B5AD3F9CB14 | SHA256:9615700CFE24D572D7EE92F119B1A449793C847B11A2E9B9B9315DEBCD5D1185 | |||
| 2240 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\30BCF8D79B1225AC4F40686E58D30D95 | binary | |
MD5:6444E4485DC73FD5385C0E69D7B8E7B8 | SHA256:C631EB0A49A82D19FE4B5227583CB1DB6AC8CFB65CBA6C379B0FDD3511B0D833 | |||
| 1788 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:75B643DE38DAA18961A38ECCFB227B11 | SHA256:CFC497117730A60F3D32FA816981151D1A318B0DE00F90D49F3B4E7A14333CFB | |||
| 2240 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\MQUZX72V.txt | text | |
MD5:93F7670C984415BD689BE89B63F8D1D1 | SHA256:1E9CE09AD62415B2B8AC06F2B18B25186E373BBF40A7CC790D1387EABCF4190C | |||
| 2240 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\5KNN5B42.txt | text | |
MD5:E2CE83915A4504F49C9C1D4F9E133DE0 | SHA256:29CA22762B8FD00D5BC4D1E44C2AAC2354AF72831ADF62BD2645CD60A55D17B4 | |||
| 2240 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\url[1].htm | html | |
MD5:61EF78C9585BD76DA31B6C98990F6D44 | SHA256:96793D29FE68E17F7BF6803118FC4D7DA587F505B02FCC48B2F7AEC063DBC204 | |||
| 2240 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:B00D8FAC34A9B3D508B6045AEF4829DD | SHA256:96E03E5F6E20F39165E095A9C89D55CD770F0422605839BE4B83289902957E18 | |||
| 2240 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | binary | |
MD5:C97B98CD6CD2D69900540DD6E9794C16 | SHA256:AB99180410D79D7B86514620E37D8A603B556DE2AEDED3552FFBED86B2C708B5 | |||
| 2240 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:B06B47D2896FDA1127A1A478556559FA | SHA256:F4A89F0458A9917A193C0D9AD067303C4810184711502DA9E7103670A98EE1AC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
59
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2240 | iexplore.exe | GET | — | 142.250.186.99:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDvWzeNIHPI5AnIjF4SMdR6 | US | — | — | whitelisted |
2240 | iexplore.exe | GET | 200 | 142.250.186.142:80 | http://crls.pki.goog/gts1c3/QOvJ0N1sT2A.crl | US | binary | 12.8 Kb | whitelisted |
2240 | iexplore.exe | GET | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | binary | 724 b | whitelisted |
2240 | iexplore.exe | GET | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDb66bCc7gzZgkLHTE8xKUO | US | binary | 472 b | whitelisted |
2240 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?d556fc7d578881e7 | US | compressed | 4.70 Kb | whitelisted |
1788 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | binary | 1.47 Kb | whitelisted |
2240 | iexplore.exe | GET | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | US | binary | 724 b | whitelisted |
2240 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?834acb3c09b67281 | US | compressed | 4.70 Kb | whitelisted |
2240 | iexplore.exe | GET | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | binary | 1.41 Kb | whitelisted |
2240 | iexplore.exe | GET | 200 | 104.18.15.101:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | binary | 1.42 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
820 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2240 | iexplore.exe | 142.250.185.164:443 | www.google.com | GOOGLE | US | whitelisted |
3660 | SamsungFrp2020.exe | 172.67.188.109:443 | code.eftp-server.com | CLOUDFLARENET | US | suspicious |
2240 | iexplore.exe | 142.250.186.99:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
2240 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2240 | iexplore.exe | 142.250.186.142:80 | crls.pki.goog | GOOGLE | US | whitelisted |
1788 | iexplore.exe | 2.23.209.130:443 | www.bing.com | Akamai International B.V. | GB | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
code.eftp-server.com |
| unknown |
www.google.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
crls.pki.goog |
| whitelisted |
easy-firmware.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |