| File name: | SDClient-Setup.exe |
| Full analysis: | https://app.any.run/tasks/bc7e2c17-b4ab-437d-a424-6496efc72c27 |
| Verdict: | Malicious activity |
| Analysis date: | November 08, 2018, 10:35:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | F28BA2C881AF54948C23C14F01F3E46B |
| SHA1: | FDC51E364063DDA572B145DB6EC08CABF0259EE9 |
| SHA256: | 7CF6F593C5E4A264A0C2CC50DC446D77BDE176941D109B3C4D4F3A3D7619D090 |
| SSDEEP: | 98304:MPmY8sjk2m5+0srtjnvuNkf29w2NcjJBY4eaCOB3SZW5IXCGLgkly3nQ:MNjbmETvMkO9Ji04twCGLgz3Q |
MALICIOUS
Application was dropped or rewritten from another process
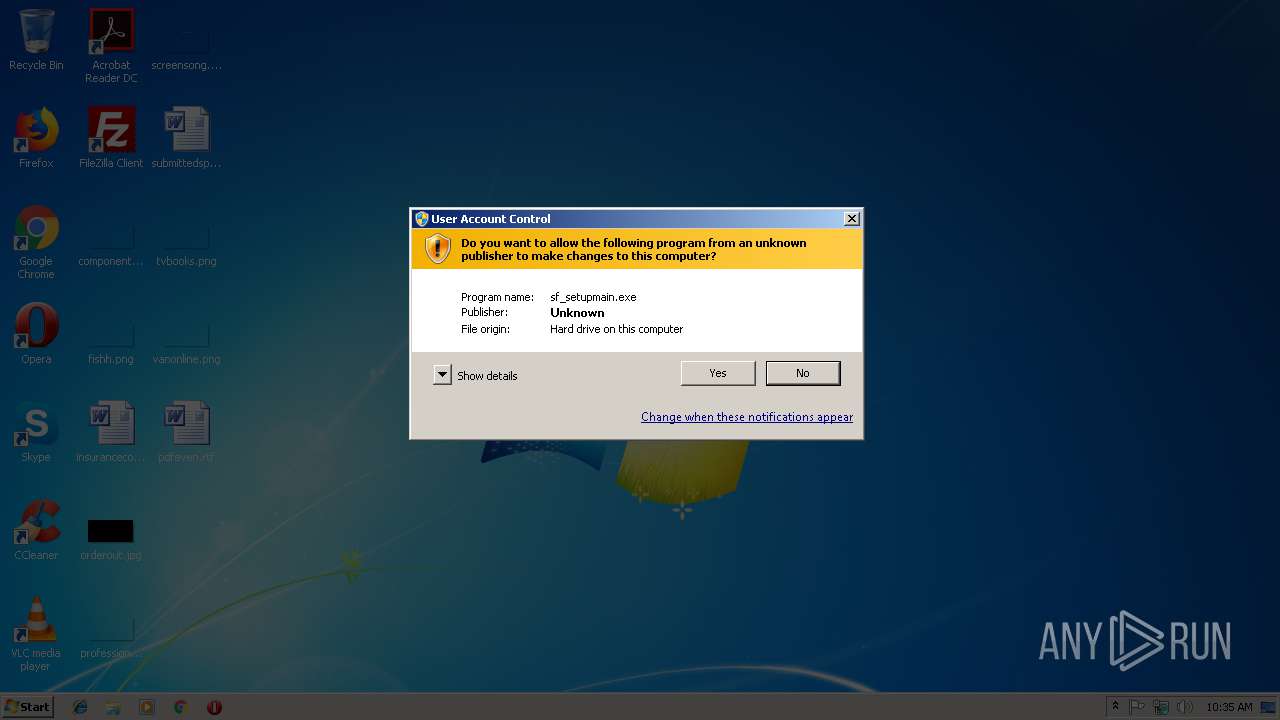
- sf_setupmain.exe (PID: 3184)
- sf_setupmain.exe (PID: 3644)
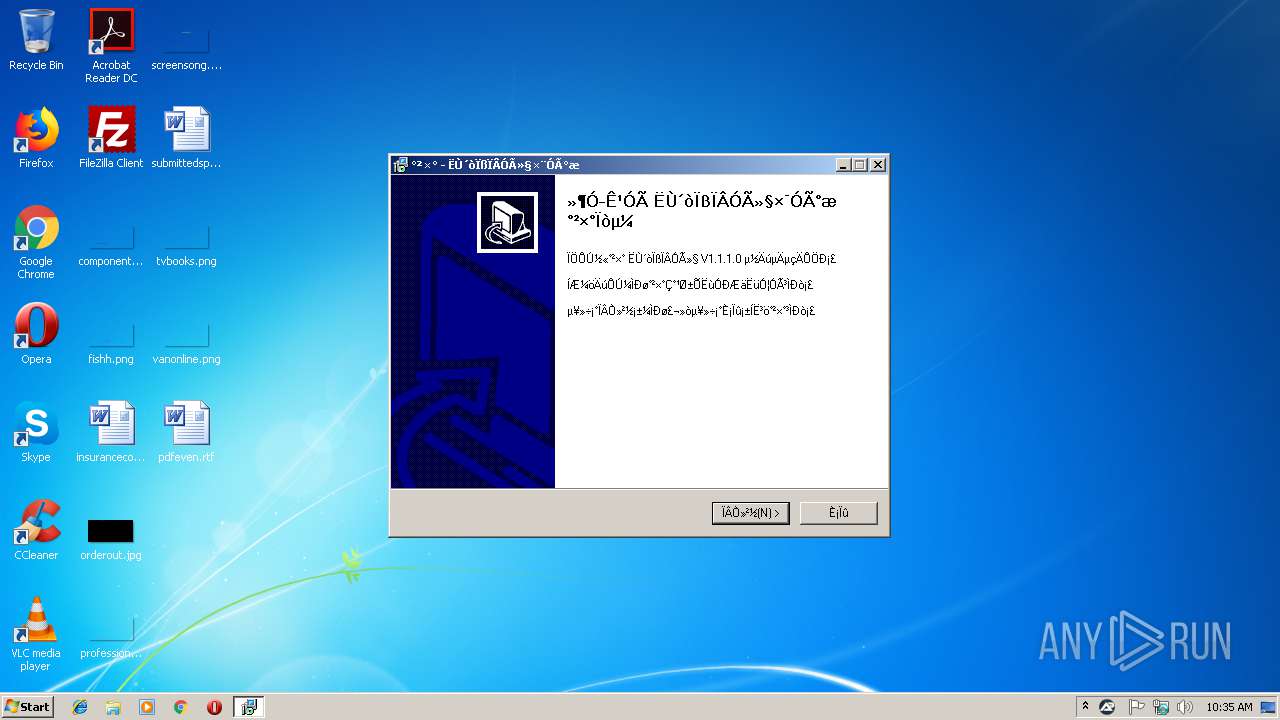
- suda.exe (PID: 3000)
- EasyPrint.exe (PID: 4004)
- EasyPrint.exe (PID: 2112)
SUSPICIOUS
Executable content was dropped or overwritten
- SDClient-Setup.exe (PID: 2276)
- suda.exe (PID: 3000)
- suda.tmp (PID: 2064)
Changes IE settings (feature browser emulation)
- EasyPrint.exe (PID: 2112)
INFO
Loads dropped or rewritten executable
- suda.tmp (PID: 2064)
Application was dropped or rewritten from another process
- suda.tmp (PID: 2064)
Creates a software uninstall entry
- suda.tmp (PID: 2064)
Creates files in the program directory
- suda.tmp (PID: 2064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:11:22 03:30:25+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 283648 |
| InitializedDataSize: | 191488 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x36d87 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.9.2.10735 |
| ProductVersionNumber: | 5.9.2.10735 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| FileVersion: | 5.9.2.10735 |
| ProductVersion: | 5.9 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 22-Nov-2016 02:30:25 |
| Detected languages: |
|
| Debug artifacts: |
|
| FileVersion: | 5.9.2.10735 |
| ProductVersion: | 5.9 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000108 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 22-Nov-2016 02:30:25 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0004527B | 0x00045400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.64156 |
.rdata | 0x00047000 | 0x00011A60 | 0x00011C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.73902 |
.data | 0x00059000 | 0x0000A180 | 0x00003A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.67134 |
.rsrc | 0x00064000 | 0x00013FDC | 0x00014000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.45203 |
.reloc | 0x00078000 | 0x000055E0 | 0x00005600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.48033 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.3159 | 1217 | Latin 1 / Western European | English - United States | RT_MANIFEST |
2 | 5.48625 | 4264 | Latin 1 / Western European | Chinese - PRC | RT_ICON |
3 | 5.4219 | 1128 | Latin 1 / Western European | Chinese - PRC | RT_ICON |
107 | 2.45849 | 48 | Latin 1 / Western European | Chinese - PRC | RT_GROUP_ICON |
129 | 3.66614 | 476 | Latin 1 / Western European | Chinese - PRC | RT_DIALOG |
131 | 7.16841 | 16478 | Latin 1 / Western European | Chinese - PRC | RT_BITMAP |
132 | 3.59875 | 758 | Latin 1 / Western European | Chinese - PRC | RT_DIALOG |
304 | 3.80658 | 336 | Latin 1 / Western European | Chinese - PRC | RT_DIALOG |
563 | 2.52313 | 82 | Latin 1 / Western European | Chinese - PRC | RT_STRING |
626 | 6.14053 | 436 | Latin 1 / Western European | Chinese - PRC | RT_STRING |
Imports
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
45
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2064 | "C:\Users\admin\AppData\Local\Temp\is-P82LJ.tmp\suda.tmp" /SL5="$80220,5211574,51712,C:\Users\admin\AppData\Local\Temp\suda.exe" | C:\Users\admin\AppData\Local\Temp\is-P82LJ.tmp\suda.tmp | suda.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: 安装/卸载 Exit code: 0 Version: 51.49.0.0 Modules
| |||||||||||||||
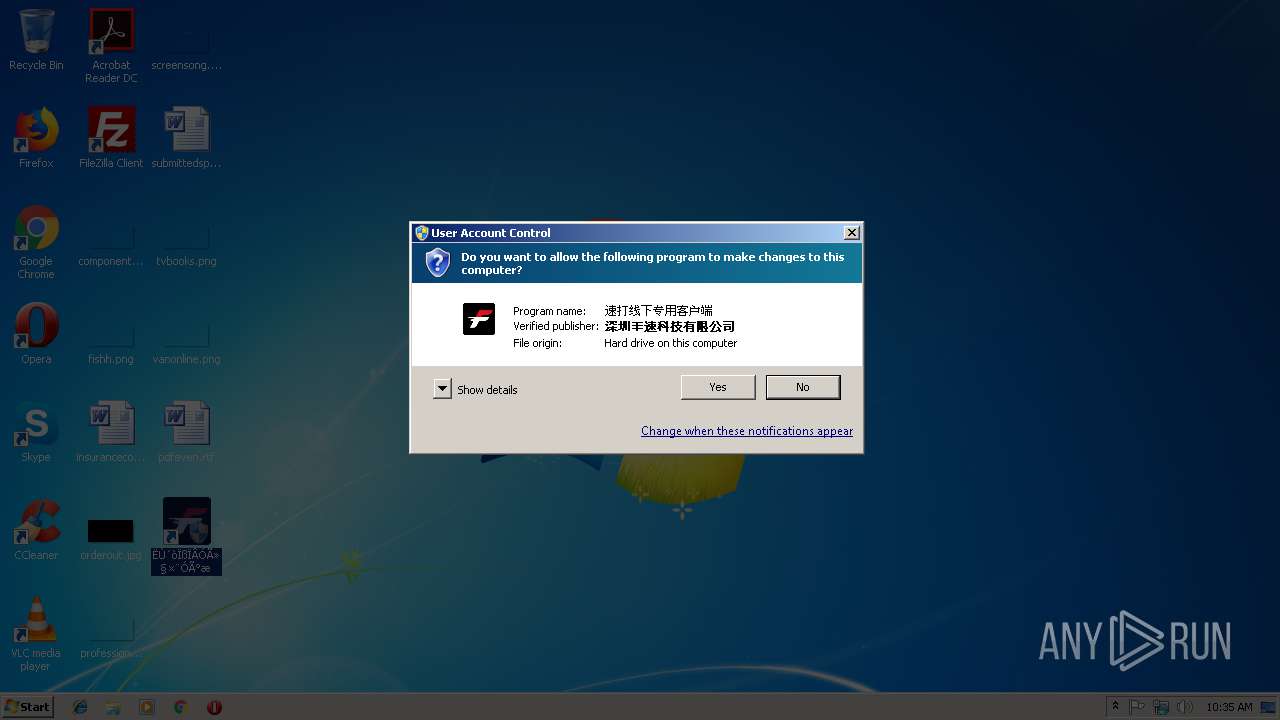
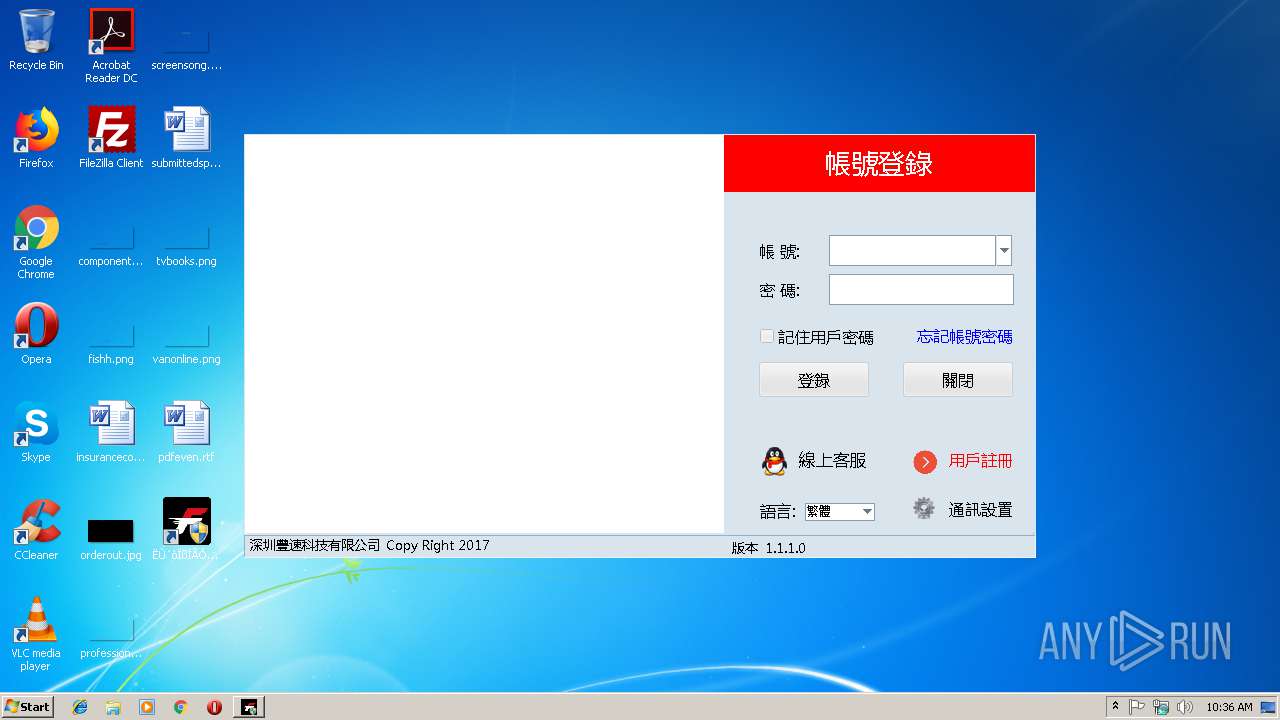
| 2112 | "C:\Program Files\ËÙ´òÏßÏÂÓû§×¨Óðæ\EasyPrint.exe" | C:\Program Files\ËÙ´òÏßÏÂÓû§×¨Óðæ\EasyPrint.exe | explorer.exe | ||||||||||||
User: admin Company: 深圳丰速科技有限公司 Integrity Level: HIGH Description: 速打线下专用客户端 Exit code: 0 Version: 1.1.1.0 Modules
| |||||||||||||||
| 2276 | "C:\Users\admin\Downloads\SDClient-Setup.exe" | C:\Users\admin\Downloads\SDClient-Setup.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 5.9.2.10735 Modules
| |||||||||||||||
| 3000 | C:\Users\admin\AppData\Local\Temp\suda.exe | C:\Users\admin\AppData\Local\Temp\suda.exe | sf_setupmain.exe | ||||||||||||
User: admin Company: 深圳丰速科技有限公司 Integrity Level: HIGH Description: 速打线下用户专用版 Setup Exit code: 0 Version: 1.1.1.0 Modules
| |||||||||||||||
| 3184 | "C:\Users\admin\AppData\Local\Temp\sf_setupmain.exe" | C:\Users\admin\AppData\Local\Temp\sf_setupmain.exe | SDClient-Setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Aut2Exe Exit code: 0 Version: 3.3.14.2 Modules
| |||||||||||||||
| 3644 | "C:\Users\admin\AppData\Local\Temp\sf_setupmain.exe" | C:\Users\admin\AppData\Local\Temp\sf_setupmain.exe | — | SDClient-Setup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Aut2Exe Exit code: 3221226540 Version: 3.3.14.2 Modules
| |||||||||||||||
| 4004 | "C:\Program Files\ËÙ´òÏßÏÂÓû§×¨Óðæ\EasyPrint.exe" | C:\Program Files\ËÙ´òÏßÏÂÓû§×¨Óðæ\EasyPrint.exe | — | explorer.exe | |||||||||||
User: admin Company: 深圳丰速科技有限公司 Integrity Level: MEDIUM Description: 速打线下专用客户端 Exit code: 3221226540 Version: 1.1.1.0 Modules
| |||||||||||||||
Total events
810
Read events
769
Write events
41
Delete events
0
Modification events
| (PID) Process: | (2276) SDClient-Setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2276) SDClient-Setup.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2064) suda.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{3a3003ed-2fb1-4546-8b04-5603fe2e0eb8}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.3.5 (a) | |||
| (PID) Process: | (2064) suda.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{3a3003ed-2fb1-4546-8b04-5603fe2e0eb8}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files\ËÙ´òÏßÏÂÓû§×¨Óðæ | |||
| (PID) Process: | (2064) suda.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{3a3003ed-2fb1-4546-8b04-5603fe2e0eb8}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files\ËÙ´òÏßÏÂÓû§×¨Óðæ\ | |||
| (PID) Process: | (2064) suda.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{3a3003ed-2fb1-4546-8b04-5603fe2e0eb8}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: ËÙ´òÏßÏÂÓû§×¨Óðæ | |||
| (PID) Process: | (2064) suda.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{3a3003ed-2fb1-4546-8b04-5603fe2e0eb8}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (2064) suda.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{3a3003ed-2fb1-4546-8b04-5603fe2e0eb8}_is1 |
| Operation: | write | Name: | Inno Setup: Selected Tasks |
Value: desktopicon | |||
| (PID) Process: | (2064) suda.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{3a3003ed-2fb1-4546-8b04-5603fe2e0eb8}_is1 |
| Operation: | write | Name: | Inno Setup: Deselected Tasks |
Value: quicklaunchicon | |||
| (PID) Process: | (2064) suda.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{3a3003ed-2fb1-4546-8b04-5603fe2e0eb8}_is1 |
| Operation: | write | Name: | DisplayName |
Value: ËÙ´òÏßÏÂÓû§ V1.1.1.0 | |||
Executable files
7
Suspicious files
20
Text files
95
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2064 | suda.tmp | C:\Program Files\ËÙ´òÏßÏÂÓû§×¨Óðæ\is-CFF4J.tmp | — | |
MD5:— | SHA256:— | |||
| 2064 | suda.tmp | C:\Program Files\ËÙ´òÏßÏÂÓû§×¨Óðæ\is-IB7SL.tmp | — | |
MD5:— | SHA256:— | |||
| 2064 | suda.tmp | C:\Program Files\ËÙ´òÏßÏÂÓû§×¨Óðæ\is-UBGK5.tmp | — | |
MD5:— | SHA256:— | |||
| 2064 | suda.tmp | C:\Program Files\ËÙ´òÏßÏÂÓû§×¨Óðæ\Images\is-3V560.tmp | — | |
MD5:— | SHA256:— | |||
| 2064 | suda.tmp | C:\Program Files\ËÙ´òÏßÏÂÓû§×¨Óðæ\Images\is-P10CG.tmp | — | |
MD5:— | SHA256:— | |||
| 2064 | suda.tmp | C:\Program Files\ËÙ´òÏßÏÂÓû§×¨Óðæ\Images\is-KTMF7.tmp | — | |
MD5:— | SHA256:— | |||
| 2064 | suda.tmp | C:\Program Files\ËÙ´òÏßÏÂÓû§×¨Óðæ\Images\is-HOJ83.tmp | — | |
MD5:— | SHA256:— | |||
| 2064 | suda.tmp | C:\Program Files\ËÙ´òÏßÏÂÓû§×¨Óðæ\Images\is-6BISK.tmp | — | |
MD5:— | SHA256:— | |||
| 2064 | suda.tmp | C:\Program Files\ËÙ´òÏßÏÂÓû§×¨Óðæ\Images\is-F97SK.tmp | — | |
MD5:— | SHA256:— | |||
| 2064 | suda.tmp | C:\Program Files\ËÙ´òÏßÏÂÓû§×¨Óðæ\Images\is-9OAQR.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
2
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2112 | EasyPrint.exe | GET | — | 120.55.144.90:80 | http://sd.1dadan.com/clienthtml/sd/index.html?Tag=43 | CN | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2112 | EasyPrint.exe | 120.55.144.90:80 | sd.1dadan.com | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
2112 | EasyPrint.exe | 103.235.46.39:80 | www.baidu.com | Beijing Baidu Netcom Science and Technology Co., Ltd. | HK | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.baidu.com |
| whitelisted |
sd.1dadan.com |
| unknown |