| File name: | Martizio Bypass.zip |
| Full analysis: | https://app.any.run/tasks/ffc4264f-3c10-4a32-a5aa-b61ab12b407c |
| Verdict: | Malicious activity |
| Analysis date: | July 24, 2021, 05:55:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 011AEED6BA9B57C4BAD7D75AE31918DB |
| SHA1: | ED168B8C8785E24D09996D251D80D1CCD05CECF0 |
| SHA256: | 7CE45EC8E7B39D7BDD9BA6F1440054BD3AA696464C57C034179221B2DEBFF55E |
| SSDEEP: | 6144:AHc3s9i66Hc3s9i61oRRRRRRRRq27SUc0VfUr/UplrzIEpKcX+03vsq+IM41BstG:Ucp6acp6WRRRRRRRRoUc0Vf4WrzlpKc7 |
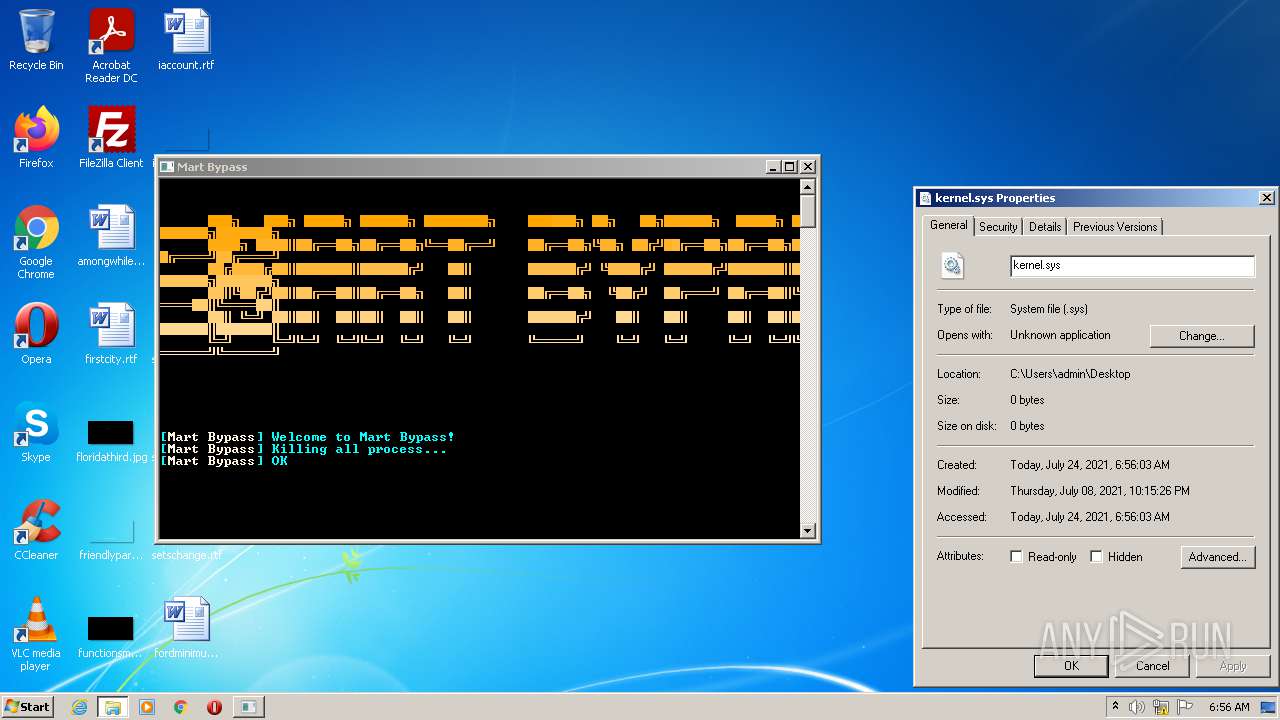
MALICIOUS
Loads dropped or rewritten executable
- Martizio Bypass.exe (PID: 4000)
- SearchProtocolHost.exe (PID: 2380)
Application was dropped or rewritten from another process
- Martizio Bypass.exe (PID: 2540)
- Martizio Bypass.exe (PID: 4000)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 2256)
- Martizio Bypass.exe (PID: 4000)
Checks supported languages
- WinRAR.exe (PID: 2256)
- Martizio Bypass.exe (PID: 4000)
Reads Environment values
- Martizio Bypass.exe (PID: 4000)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2256)
- Martizio Bypass.exe (PID: 4000)
Reads default file associations for system extensions
- SearchProtocolHost.exe (PID: 2380)
- WinRAR.exe (PID: 2256)
Drops a file with too old compile date
- WinRAR.exe (PID: 2256)
- Martizio Bypass.exe (PID: 4000)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 2256)
- Martizio Bypass.exe (PID: 4000)
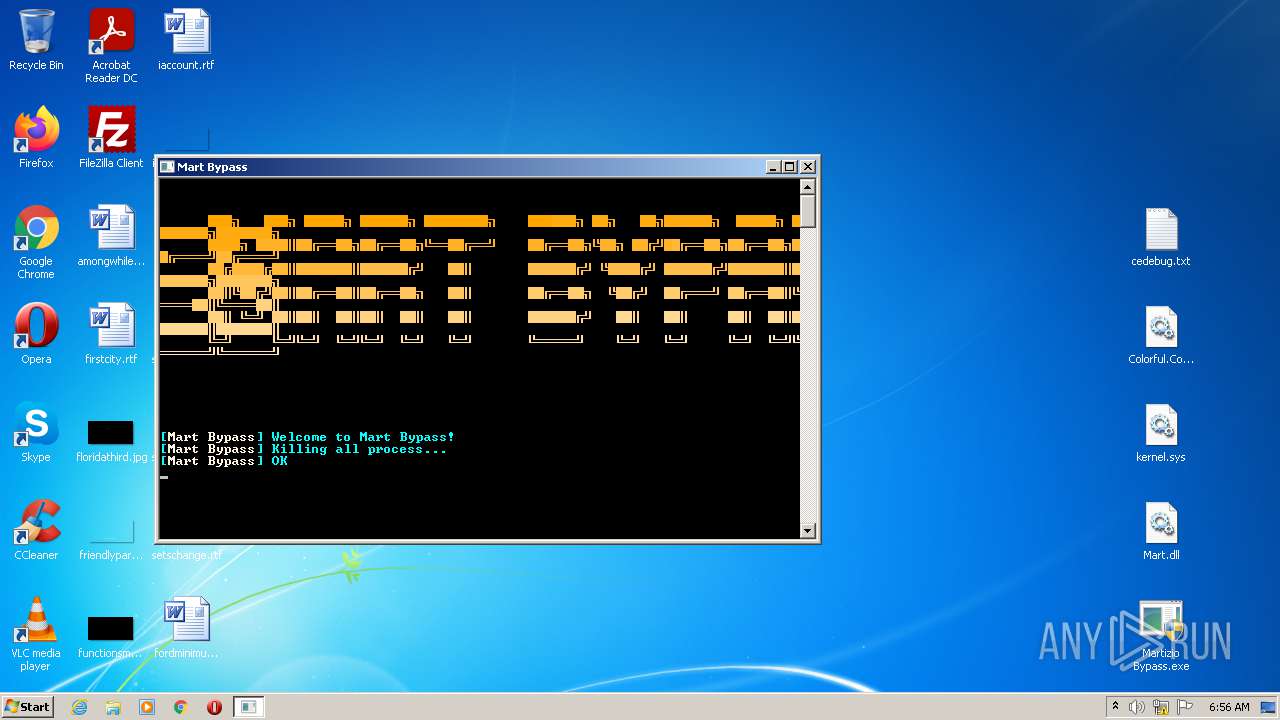
Creates files in the user directory
- Martizio Bypass.exe (PID: 4000)
INFO
Reads settings of System Certificates
- Martizio Bypass.exe (PID: 4000)
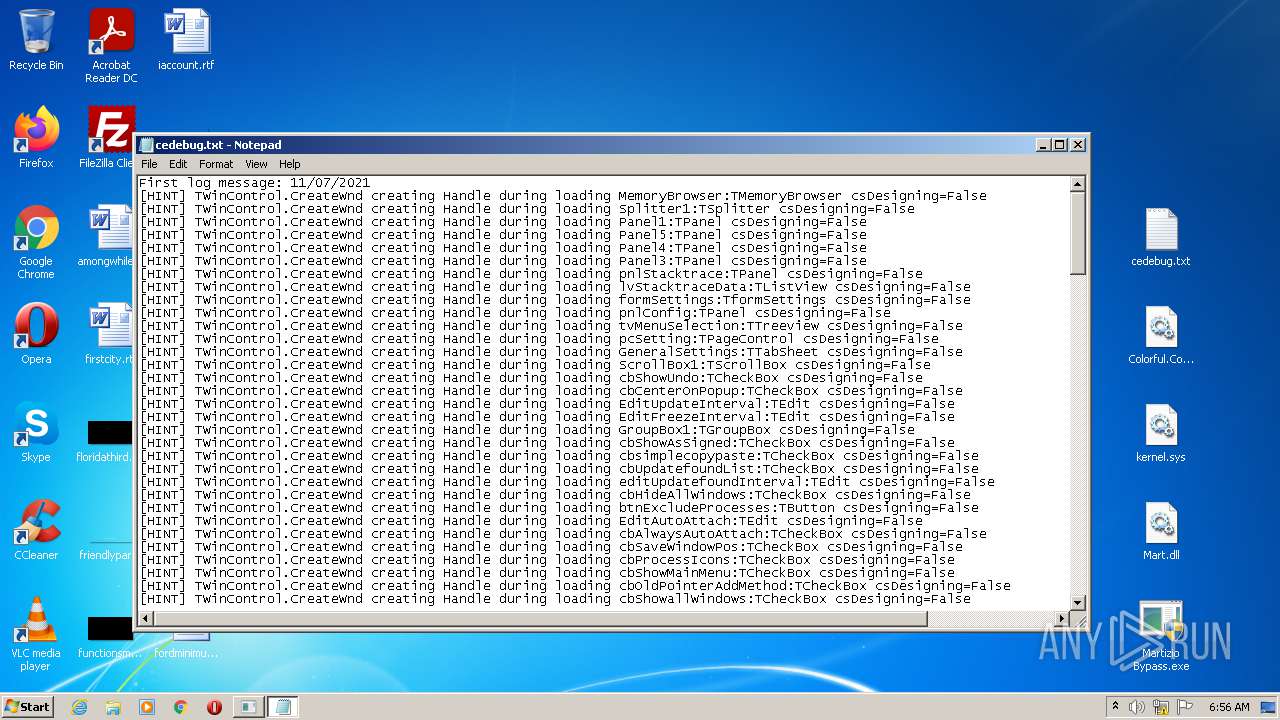
Manual execution by user
- NOTEPAD.EXE (PID: 2716)
- Martizio Bypass.exe (PID: 4000)
- Martizio Bypass.exe (PID: 2540)
Checks supported languages
- NOTEPAD.EXE (PID: 2716)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:07:11 12:00:05 |
| ZipCRC: | 0x8164b9a9 |
| ZipCompressedSize: | 1536 |
| ZipUncompressedSize: | 16555 |
| ZipFileName: | cedebug.txt |
Total processes
42
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2256 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Martizio Bypass.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2380 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 2540 | "C:\Users\admin\Desktop\Martizio Bypass.exe" | C:\Users\admin\Desktop\Martizio Bypass.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: Martizio Bypass Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2716 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\cedebug.txt | C:\Windows\system32\NOTEPAD.EXE | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4000 | "C:\Users\admin\Desktop\Martizio Bypass.exe" | C:\Users\admin\Desktop\Martizio Bypass.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Description: Martizio Bypass Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
4 277
Read events
4 229
Write events
48
Delete events
0
Modification events
| (PID) Process: | (2256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2256) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Martizio Bypass.zip | |||
| (PID) Process: | (2256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2256) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2256) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
Executable files
40
Suspicious files
3
Text files
100
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4000 | Martizio Bypass.exe | C:\Users\admin\AppData\Roaming\Mart_Bypass\Temp\unpacked.zip | — | |
MD5:— | SHA256:— | |||
| 2256 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2256.31890\Martizio Bypass.exe | executable | |
MD5:— | SHA256:— | |||
| 2256 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2256.31890\cedebug.txt | text | |
MD5:— | SHA256:— | |||
| 4000 | Martizio Bypass.exe | C:\Users\admin\AppData\Roaming\Martizio_Bypass\allochook-x86_64.dll | executable | |
MD5:BA991541C10506A7BD4A9DC6A7382E2E | SHA256:060F98F88F6280234578B06894C35136887DDD4C635C84A98E0297F5EF381870 | |||
| 4000 | Martizio Bypass.exe | C:\Users\admin\AppData\Roaming\Martizio_Bypass\allochook-i386.dll | executable | |
MD5:6E808A8B417331EA7645B6A9FFA4B8FE | SHA256:B8DF41C3153C2A3212523099C71BC81AC97304DC886D8B4670A4F9A7AE6C3568 | |||
| 4000 | Martizio Bypass.exe | C:\Users\admin\AppData\Roaming\Martizio_Bypass\autorun\addtonewgroup.lua | text | |
MD5:3E20F1013FB48A67FE59BEDE7B8E341B | SHA256:96E4429192F9AB26F8BF9F9429F36B388AA69C3624781C61EA6DF7E1BCA9B49B | |||
| 4000 | Martizio Bypass.exe | C:\Users\admin\AppData\Roaming\Martizio_Bypass\autorun\autosave.lua | text | |
MD5:40D6BFE593194CF938E19622A3C13A5E | SHA256:C4CEF60489B067C8E7ABCDD5594643A27D0720B21523753DD462D53024287116 | |||
| 4000 | Martizio Bypass.exe | C:\Users\admin\AppData\Roaming\Martizio_Bypass\autorun\bigendian.lua | text | |
MD5:E76FCD2ECD5B956D4579A676AA3EEA01 | SHA256:0339BA0043AF5C058CF3A19DE9F90312D18F6BB2728F454EF403B531BD57AE42 | |||
| 2256 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2256.31890\Colorful.Console.dll | executable | |
MD5:9F6CE7FF934FB2E786CED3516705EFAD | SHA256:59A3696950AC3525E31CDD26727DABD9FECD2E1BDC1C47C370D4B04420592436 | |||
| 2256 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2256.31890\Mart.dll | executable | |
MD5:9F6CE7FF934FB2E786CED3516705EFAD | SHA256:59A3696950AC3525E31CDD26727DABD9FECD2E1BDC1C47C370D4B04420592436 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4000 | Martizio Bypass.exe | 162.159.133.233:443 | cdn.discordapp.com | Cloudflare Inc | — | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cdn.discordapp.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |