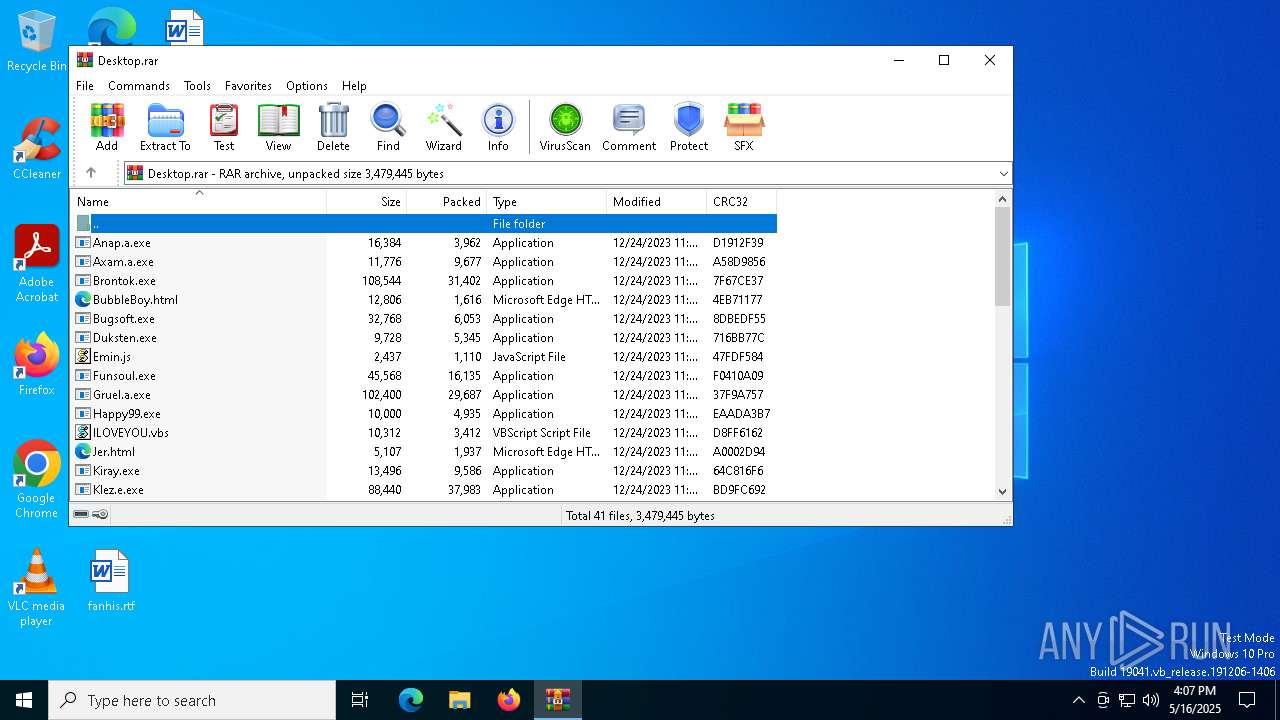
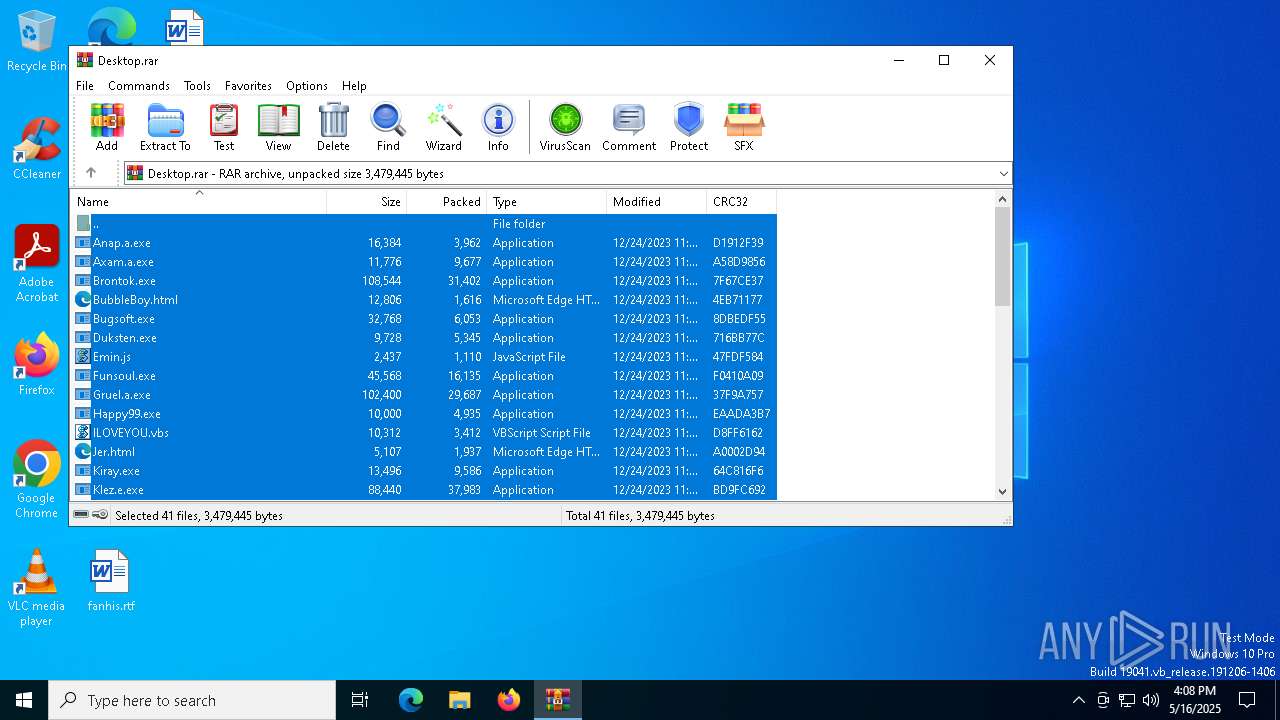
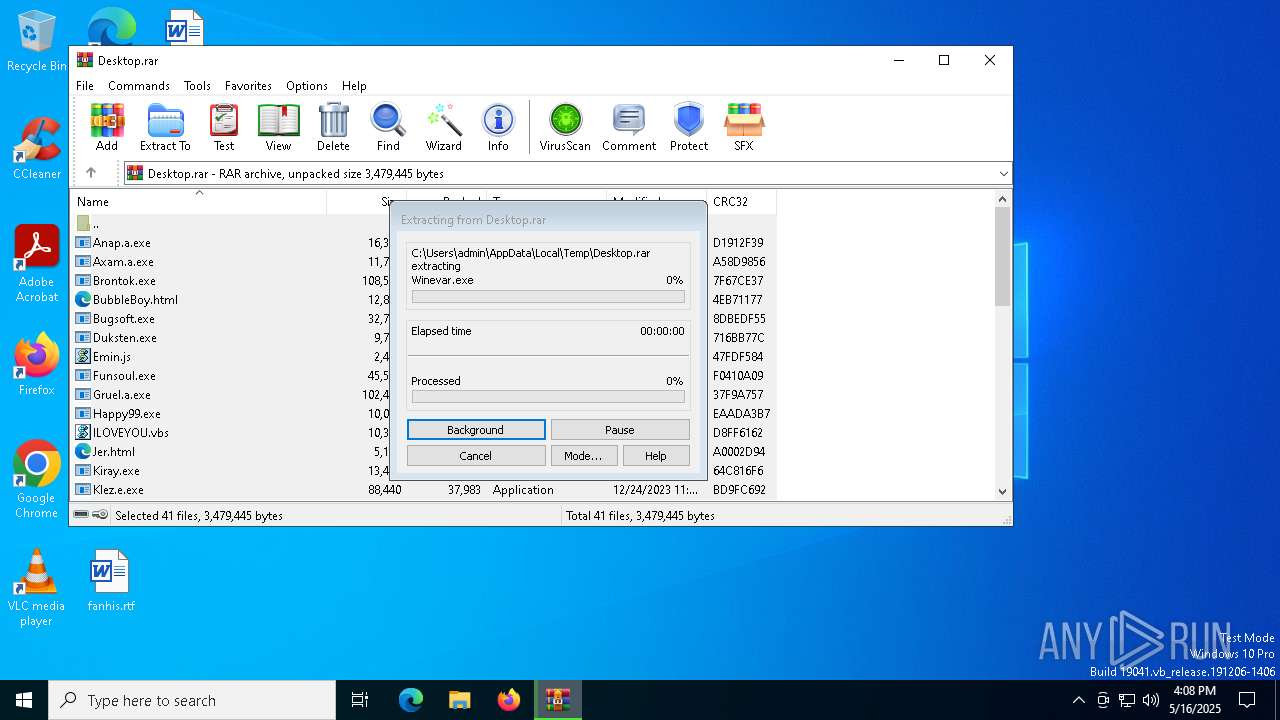
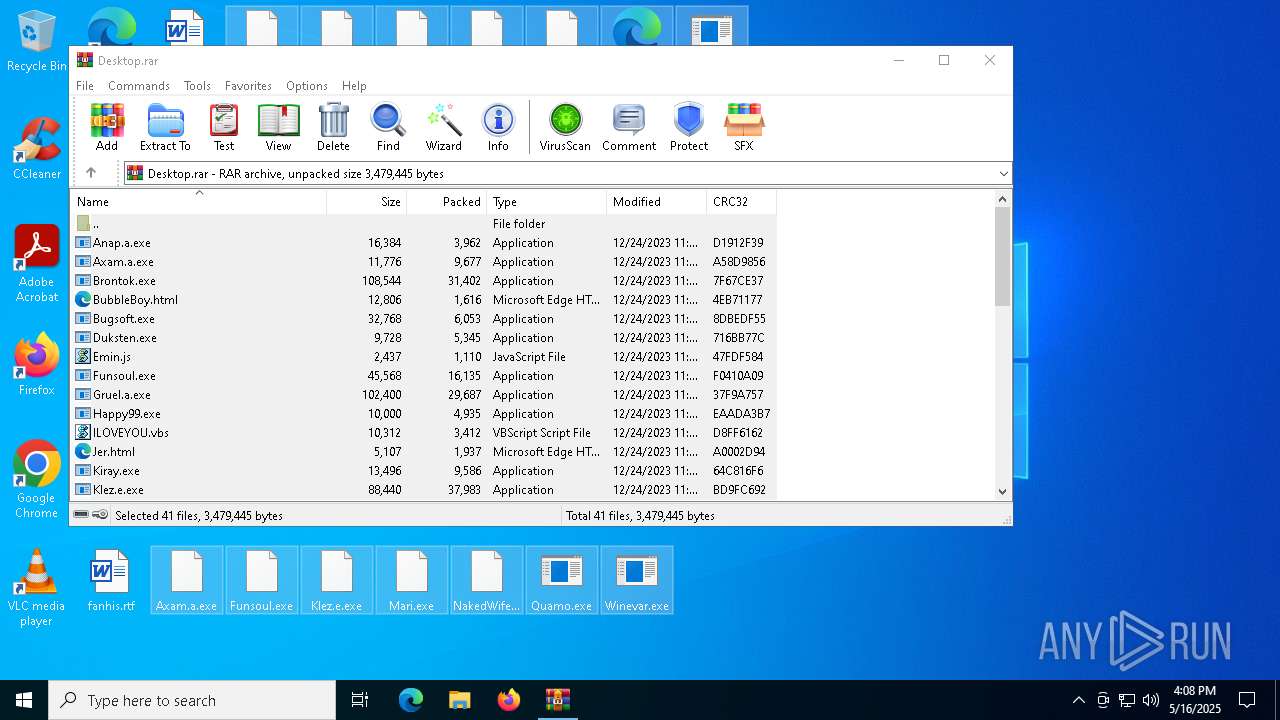
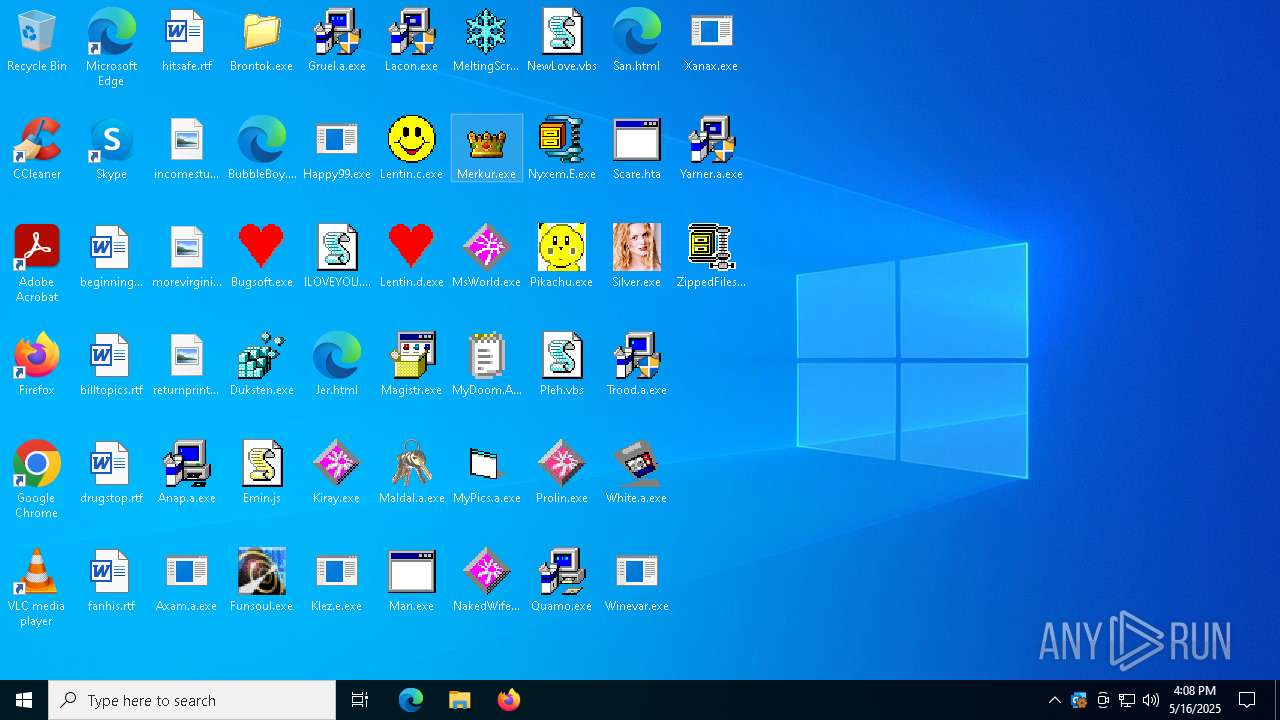
| File name: | Desktop.rar |
| Full analysis: | https://app.any.run/tasks/f55f8455-e835-4595-91b8-93a26015838a |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 16:07:07 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | E7AA9408EE2577D70DEC6B7B8B45B234 |
| SHA1: | D625011A040B62B7C91754344239E274CC2ED935 |
| SHA256: | 7CCFD9B52EA9C8F3FAF6AFAD17BABFF9C052B0B7561B912BCF4030EFB2E9EE78 |
| SSDEEP: | 98304:3Nm+xYOGxxZVEm+PcIPnjSduoiUILbRR9F3vfrgCyMSZdNx0kMmjP5YmTj3alrPK:4URHjy5 |
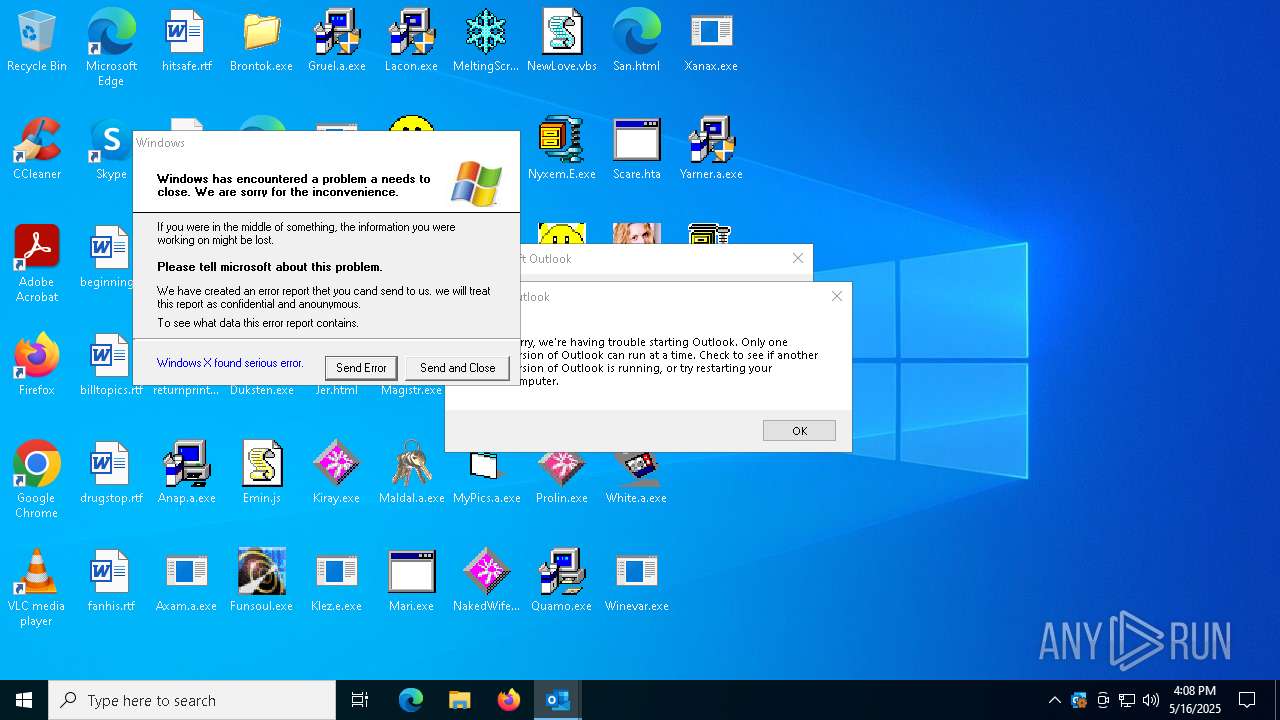
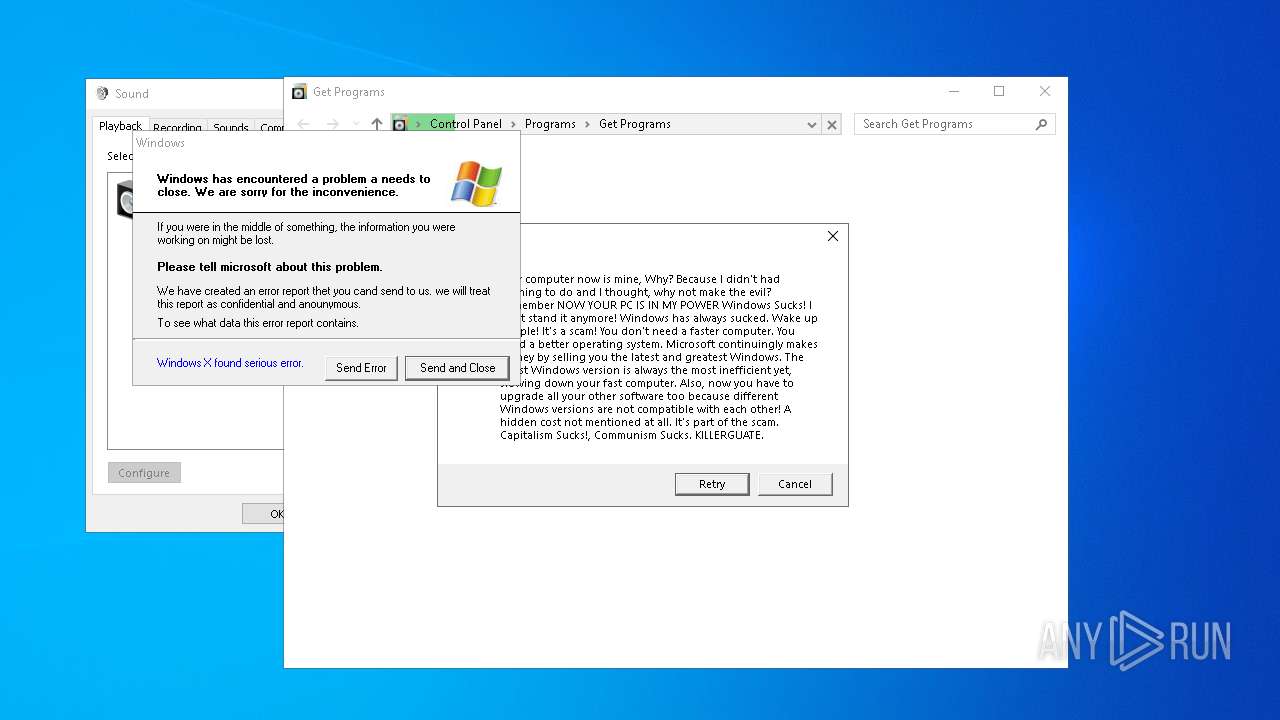
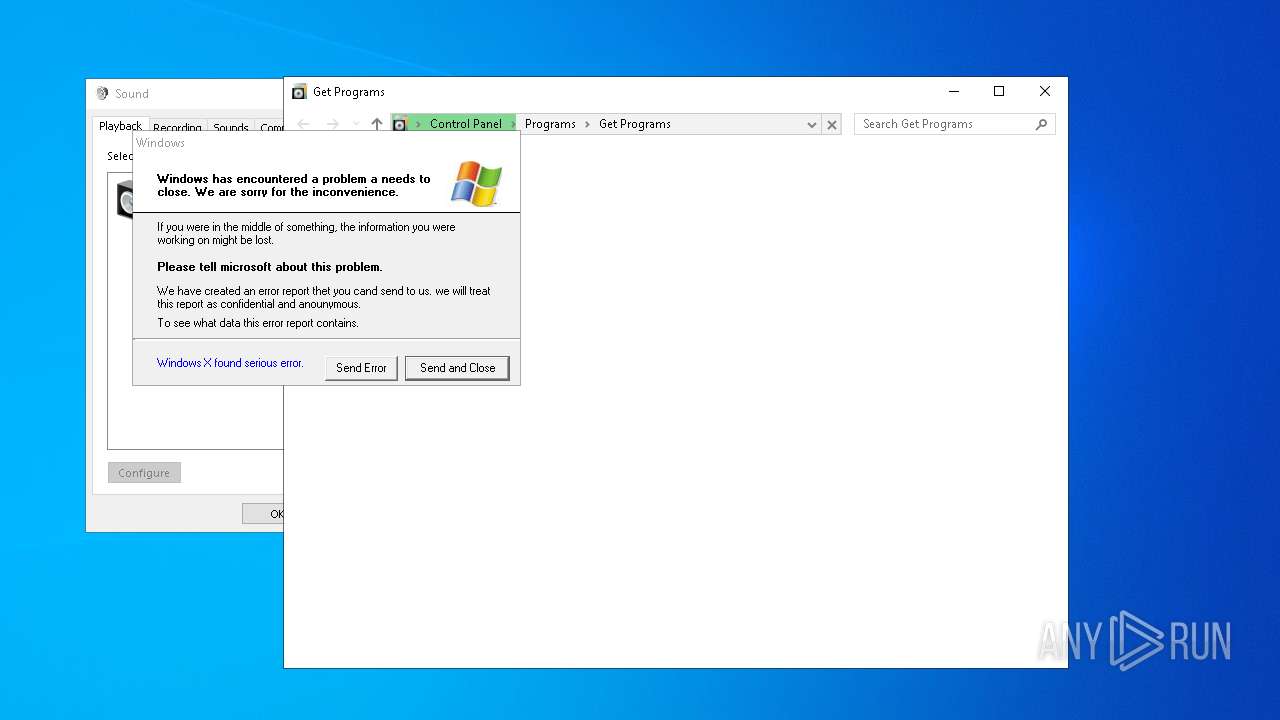
MALICIOUS
MYDOOM has been found (auto)
- WinRAR.exe (PID: 1532)
Generic archive extractor
- WinRAR.exe (PID: 1532)
Changes the autorun value in the registry
- Yarner.a.exe (PID: 664)
Creates a new registry key or changes the value of an existing one (SCRIPT)
- wscript.exe (PID: 5892)
Modifies registry startup key (SCRIPT)
- wscript.exe (PID: 5892)
SUSPICIOUS
Executable content was dropped or overwritten
- Yarner.a.exe (PID: 664)
- Lacon.exe (PID: 3676)
- Gruel.a.exe (PID: 5172)
Process drops legitimate windows executable
- Yarner.a.exe (PID: 664)
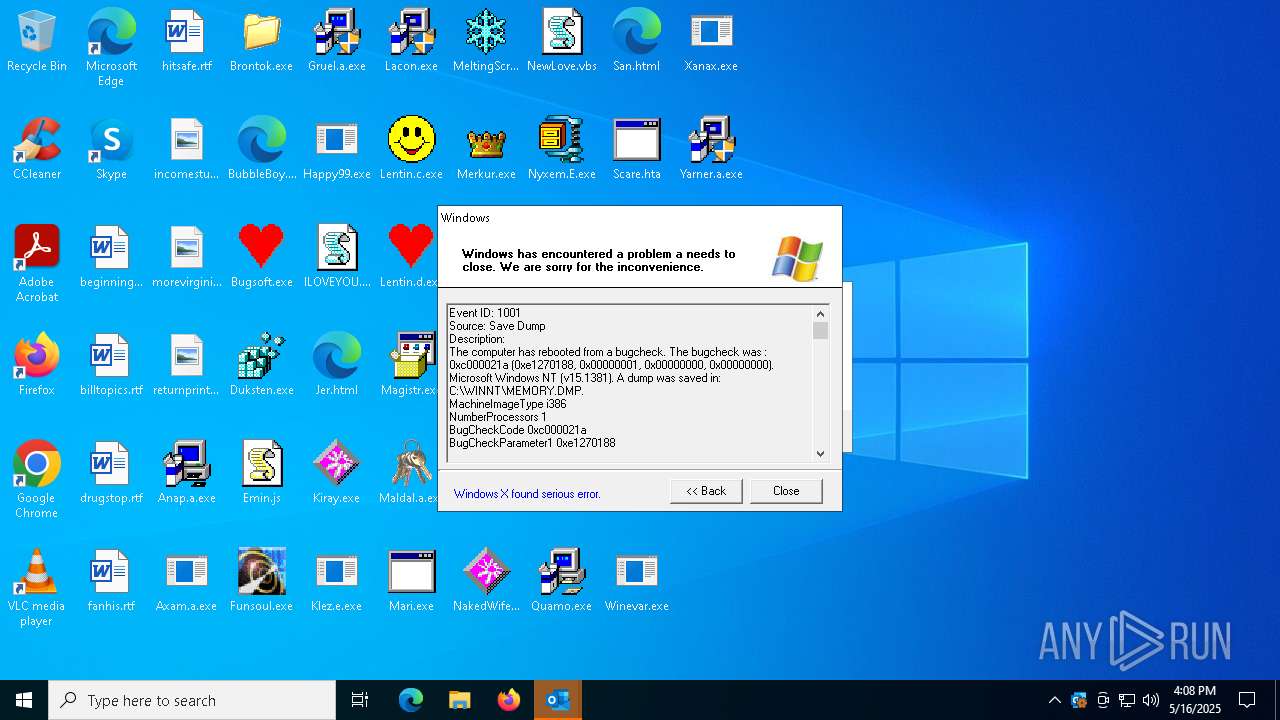
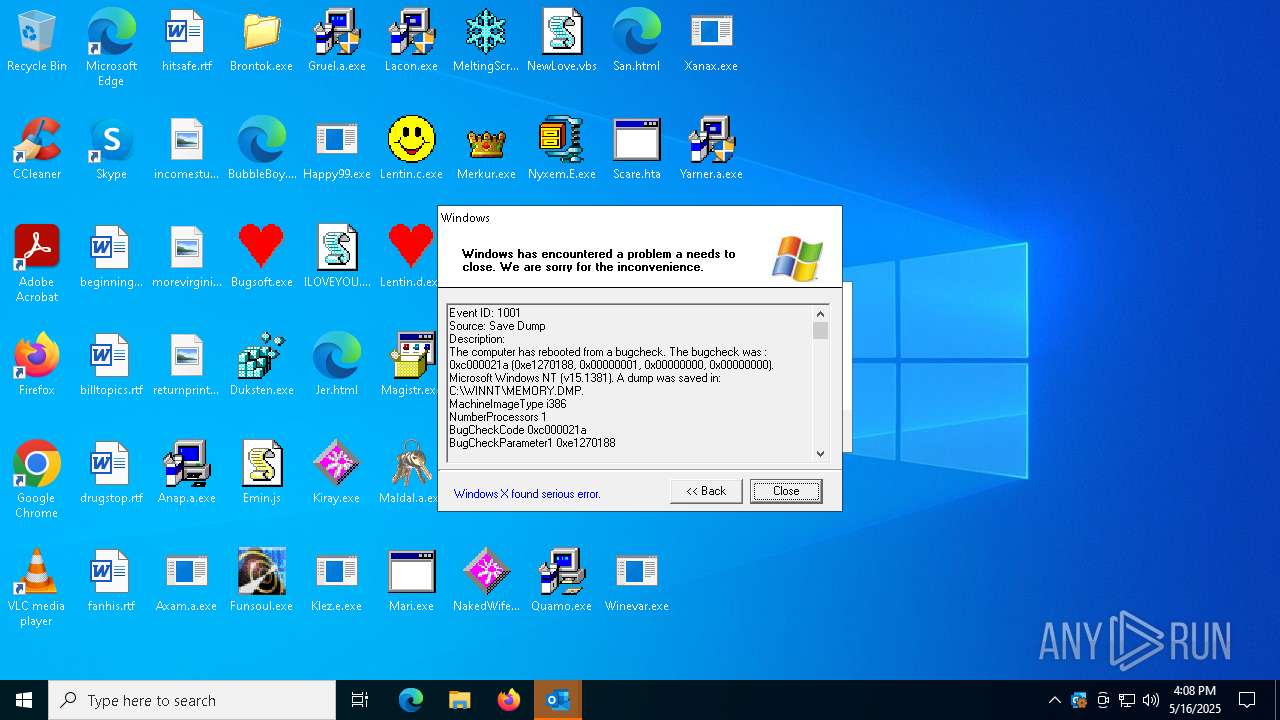
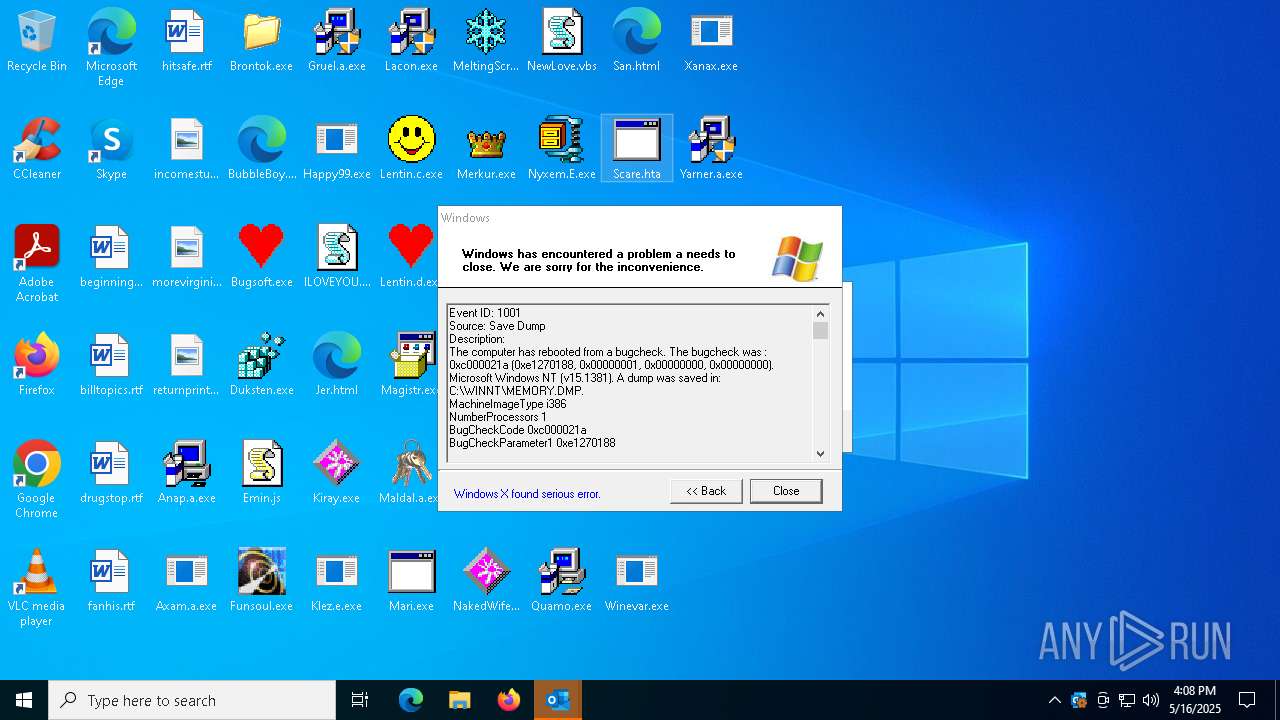
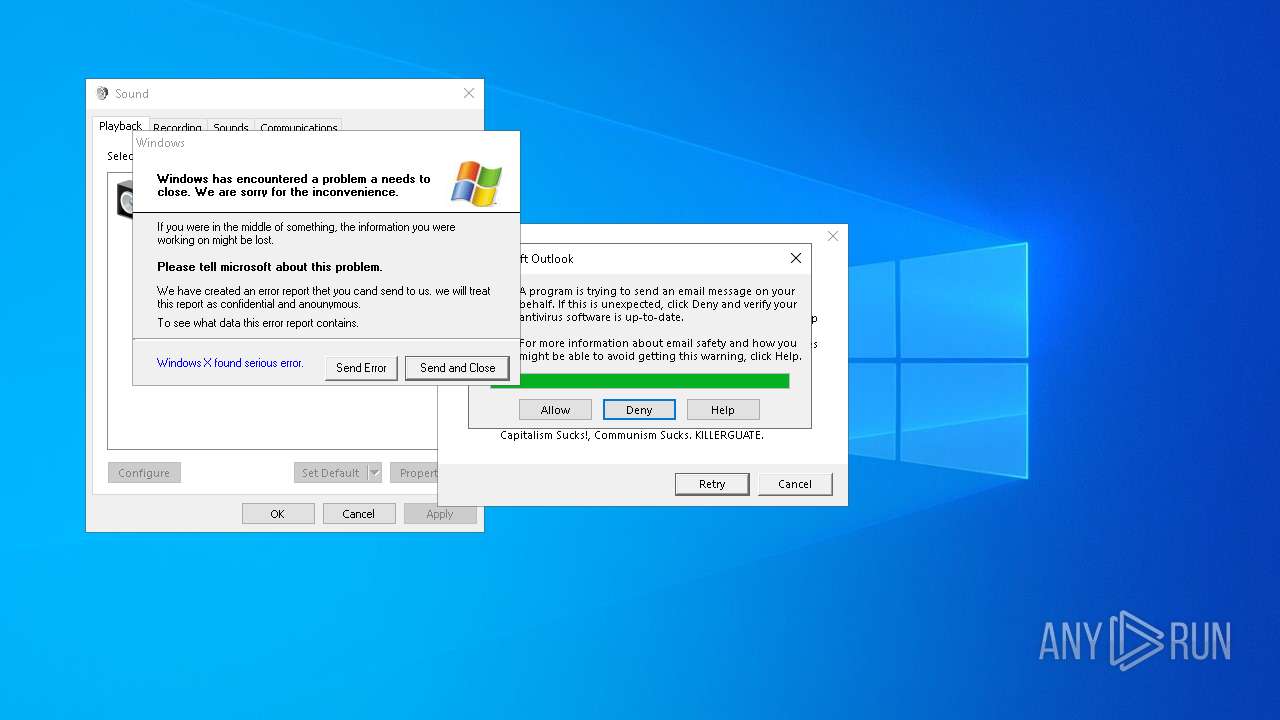
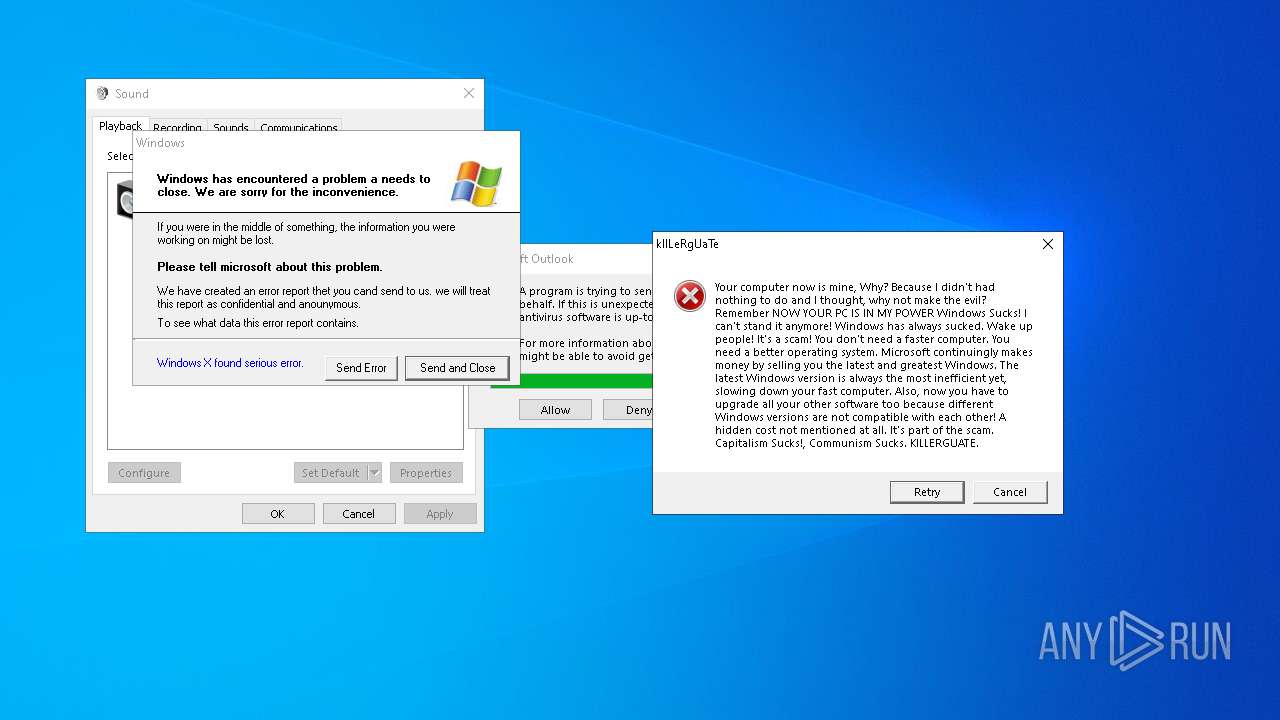
Executes application which crashes
- Xanax.exe (PID: 856)
- Nyxem.E.exe (PID: 6668)
Reads data from a binary Stream object (SCRIPT)
- wscript.exe (PID: 5892)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 5892)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 5892)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 5892)
Creates file in the systems drive root
- Merkur.exe (PID: 1852)
Uses REG/REGEDIT.EXE to modify registry
- Merkur.exe (PID: 1852)
There is functionality for taking screenshot (YARA)
- Yarner.a.exe (PID: 664)
Uses RUNDLL32.EXE to load library
- rundll32.exe (PID: 2084)
INFO
The sample compiled with spanish language support
- WinRAR.exe (PID: 1532)
- Gruel.a.exe (PID: 5172)
The sample compiled with english language support
- WinRAR.exe (PID: 1532)
- Yarner.a.exe (PID: 664)
- Lacon.exe (PID: 3676)
The sample compiled with korean language support
- WinRAR.exe (PID: 1532)
Manual execution by a user
- Yarner.a.exe (PID: 6676)
- Yarner.a.exe (PID: 664)
- Xanax.exe (PID: 856)
- Nyxem.E.exe (PID: 6668)
- Merkur.exe (PID: 1852)
- wscript.exe (PID: 5892)
- Lacon.exe (PID: 3676)
- Gruel.a.exe (PID: 4944)
- Gruel.a.exe (PID: 5172)
- Gruel.a.exe (PID: 3768)
- Gruel.a.exe (PID: 5624)
- Gruel.a.exe (PID: 3620)
- Lacon.exe (PID: 208)
- Gruel.a.exe (PID: 208)
The sample compiled with german language support
- WinRAR.exe (PID: 1532)
- Yarner.a.exe (PID: 664)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1532)
Checks supported languages
- Yarner.a.exe (PID: 664)
- Xanax.exe (PID: 856)
- Merkur.exe (PID: 1852)
Reads the computer name
- Yarner.a.exe (PID: 664)
- Merkur.exe (PID: 1852)
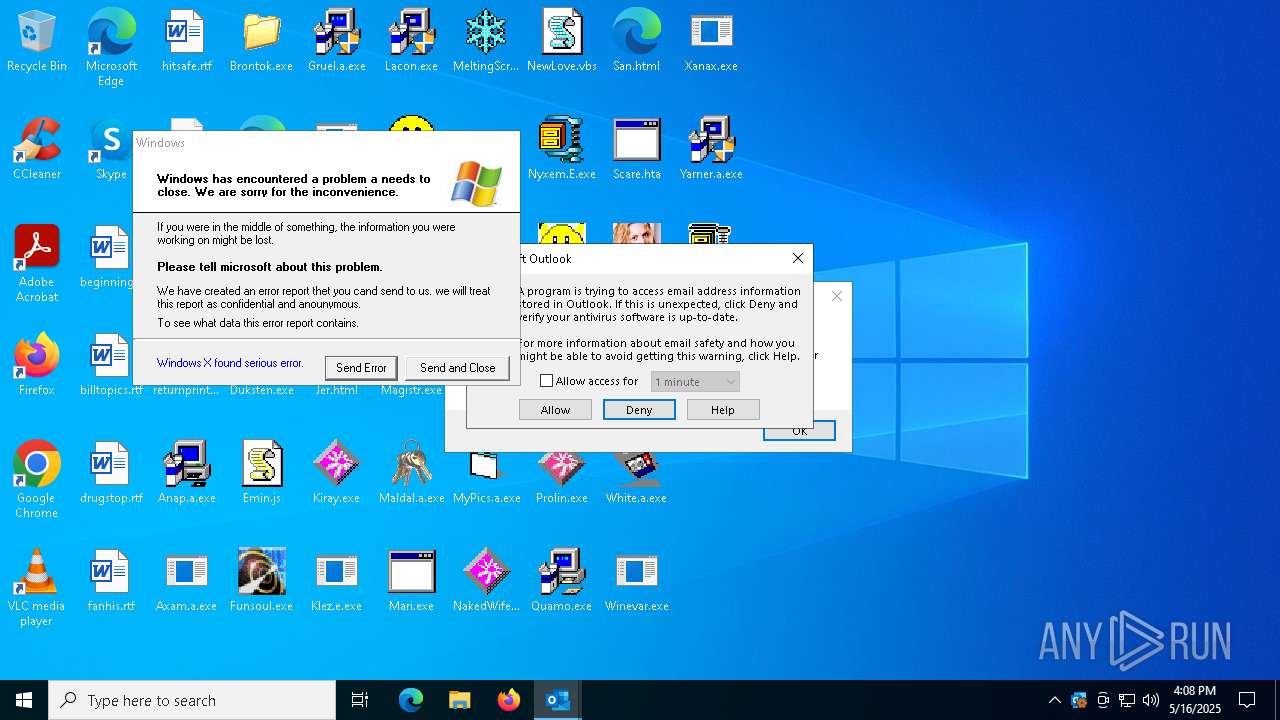
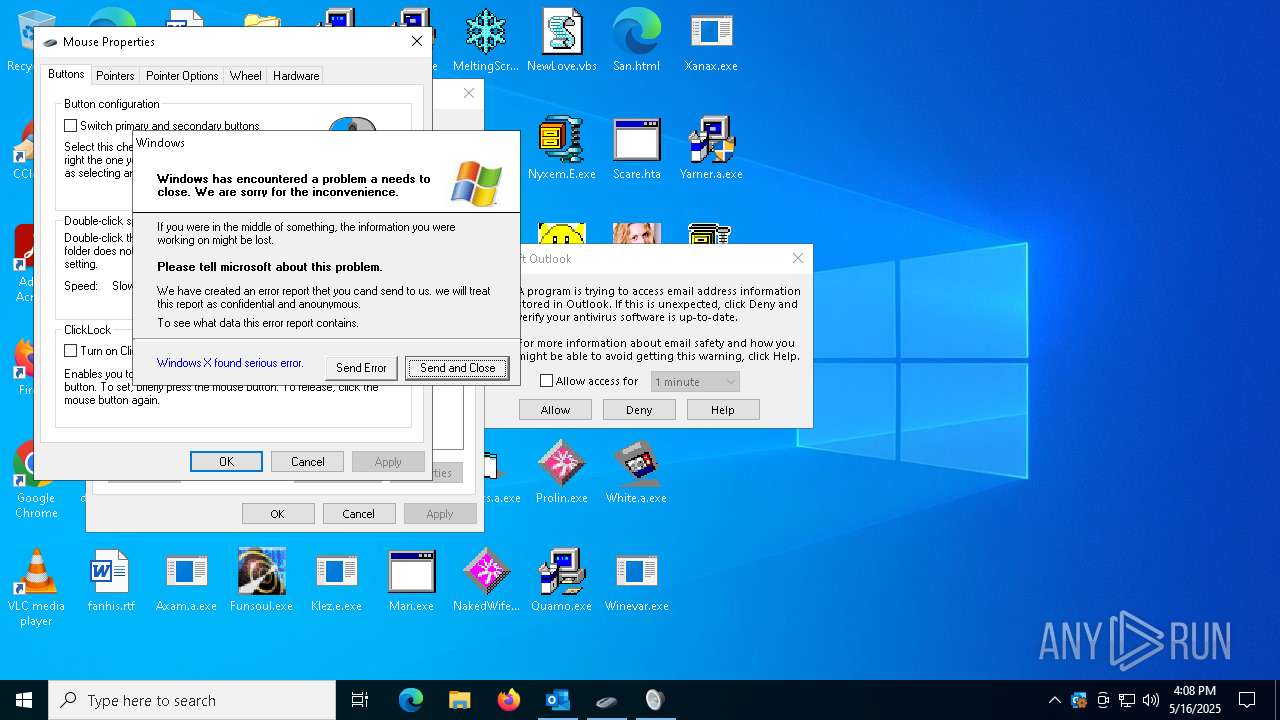
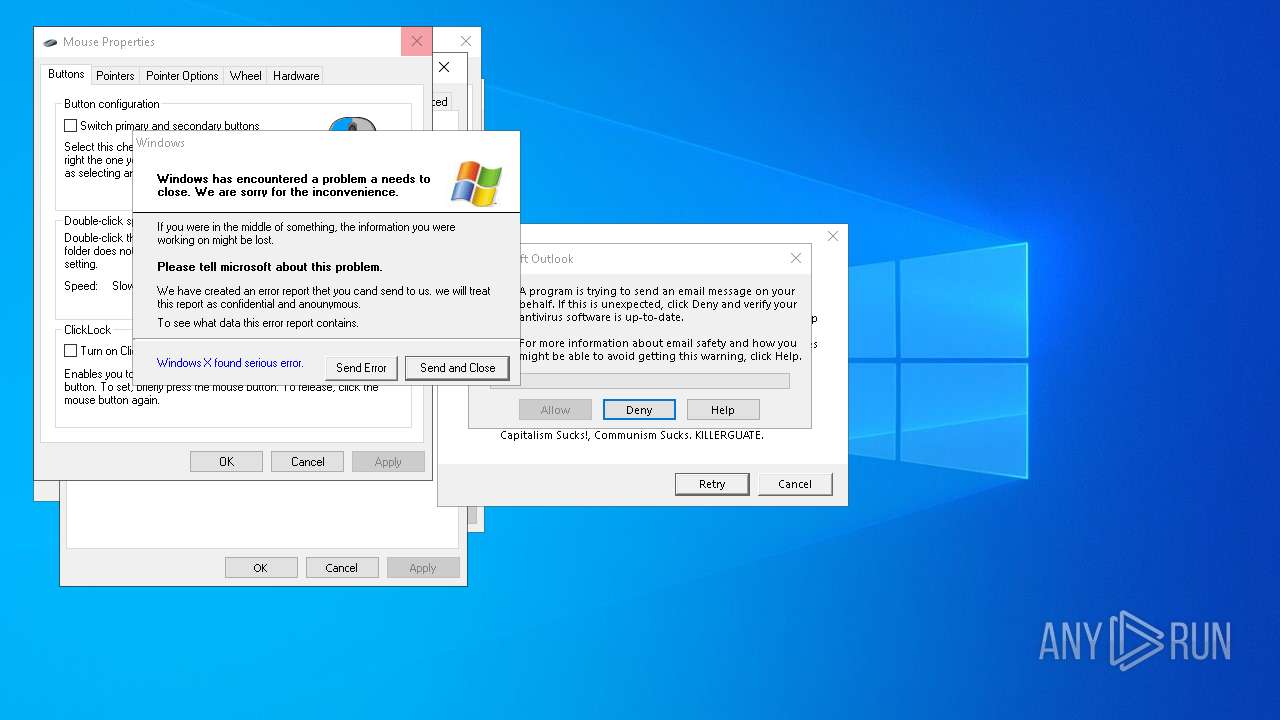
Failed to create an executable file in Windows directory
- Xanax.exe (PID: 856)
- Merkur.exe (PID: 1852)
Reads the bytes from the current stream and writes them to another stream(SCRIPT)
- wscript.exe (PID: 5892)
Creates files or folders in the user directory
- WerFault.exe (PID: 1188)
- WerFault.exe (PID: 5452)
Create files in a temporary directory
- Merkur.exe (PID: 1852)
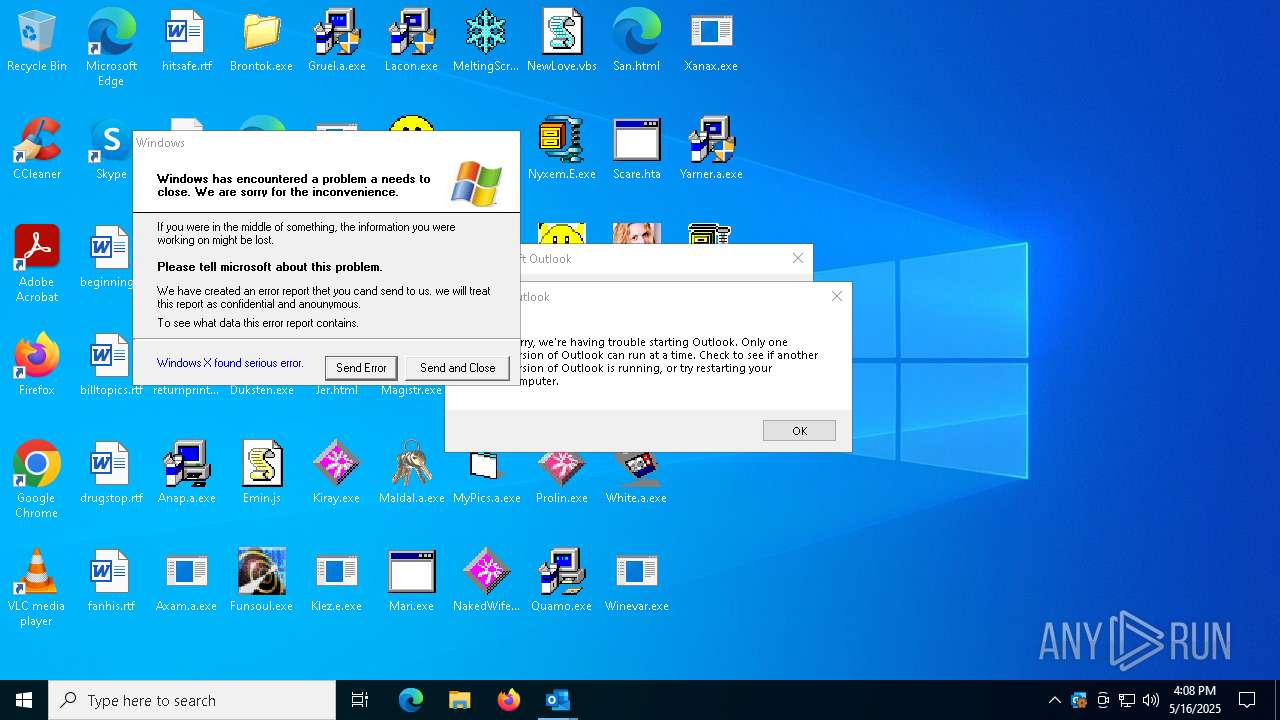
Compiled with Borland Delphi (YARA)
- Yarner.a.exe (PID: 664)
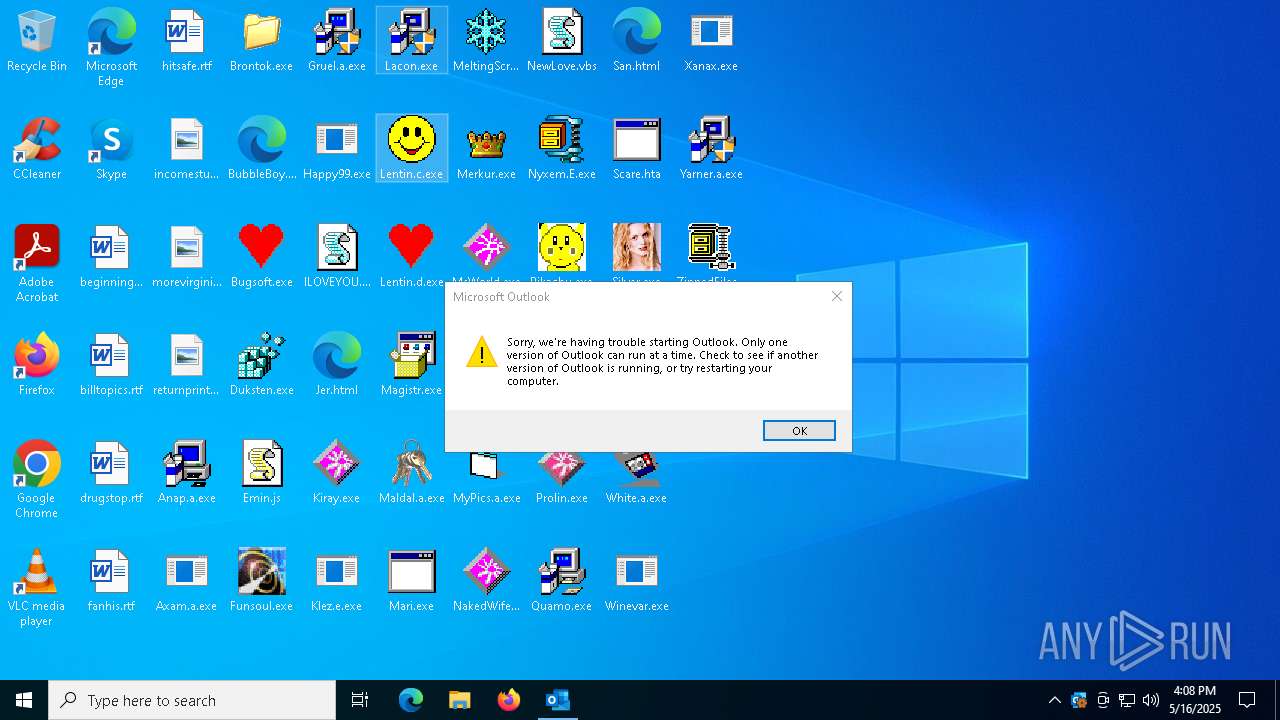
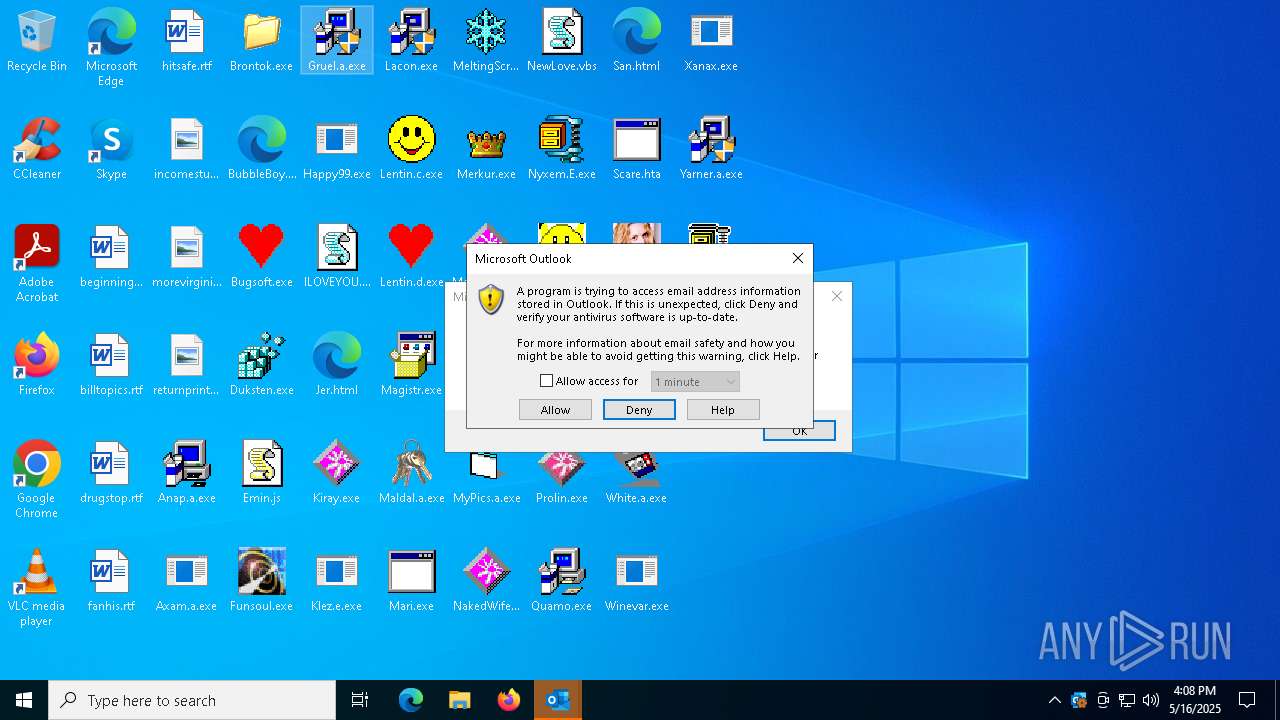
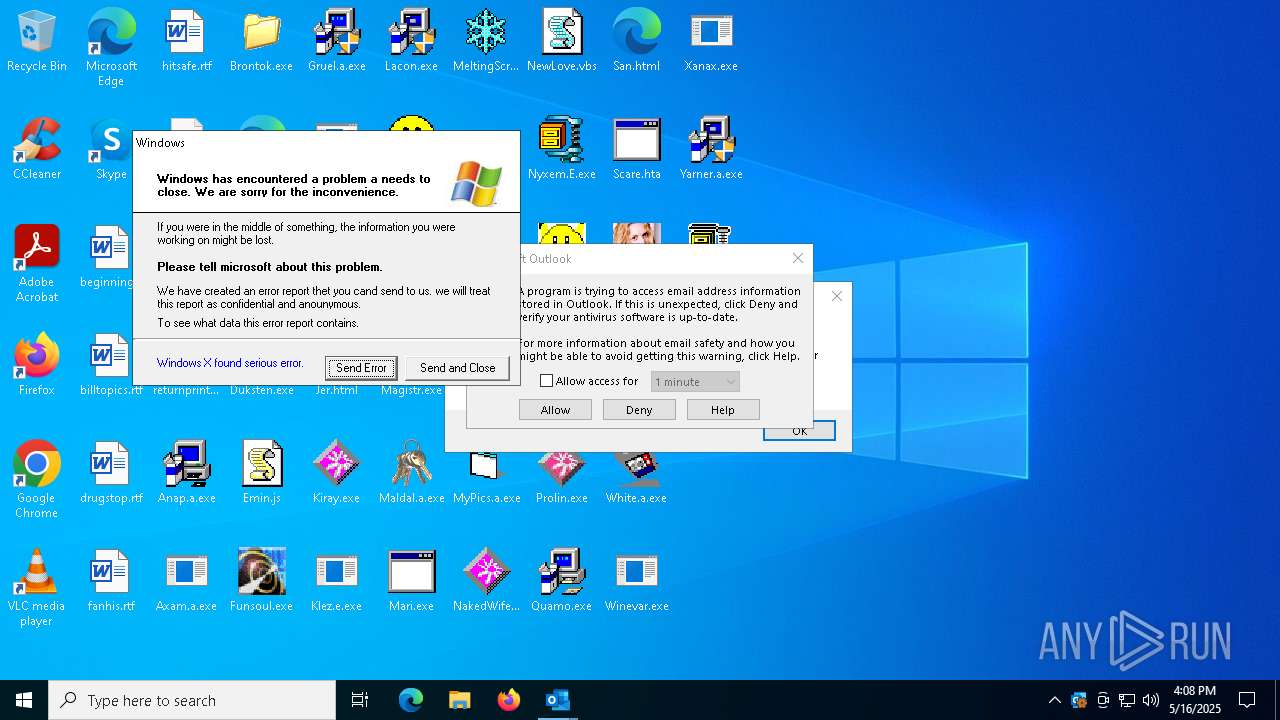
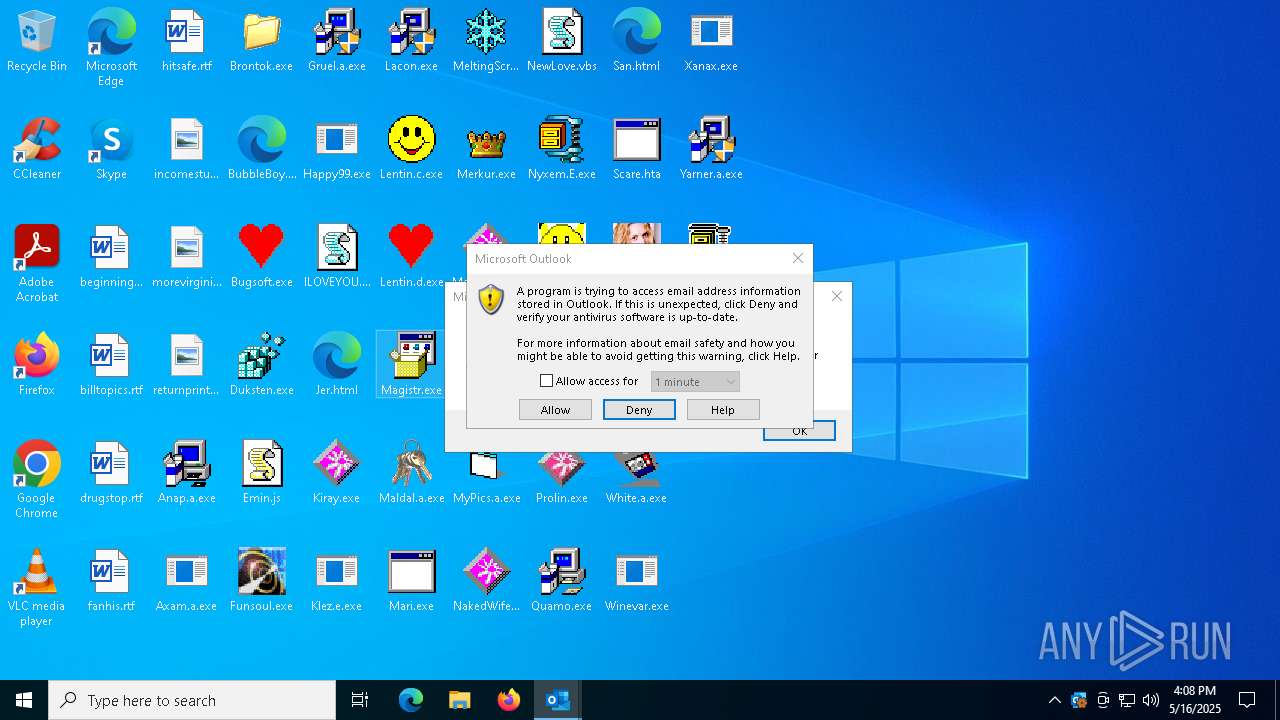
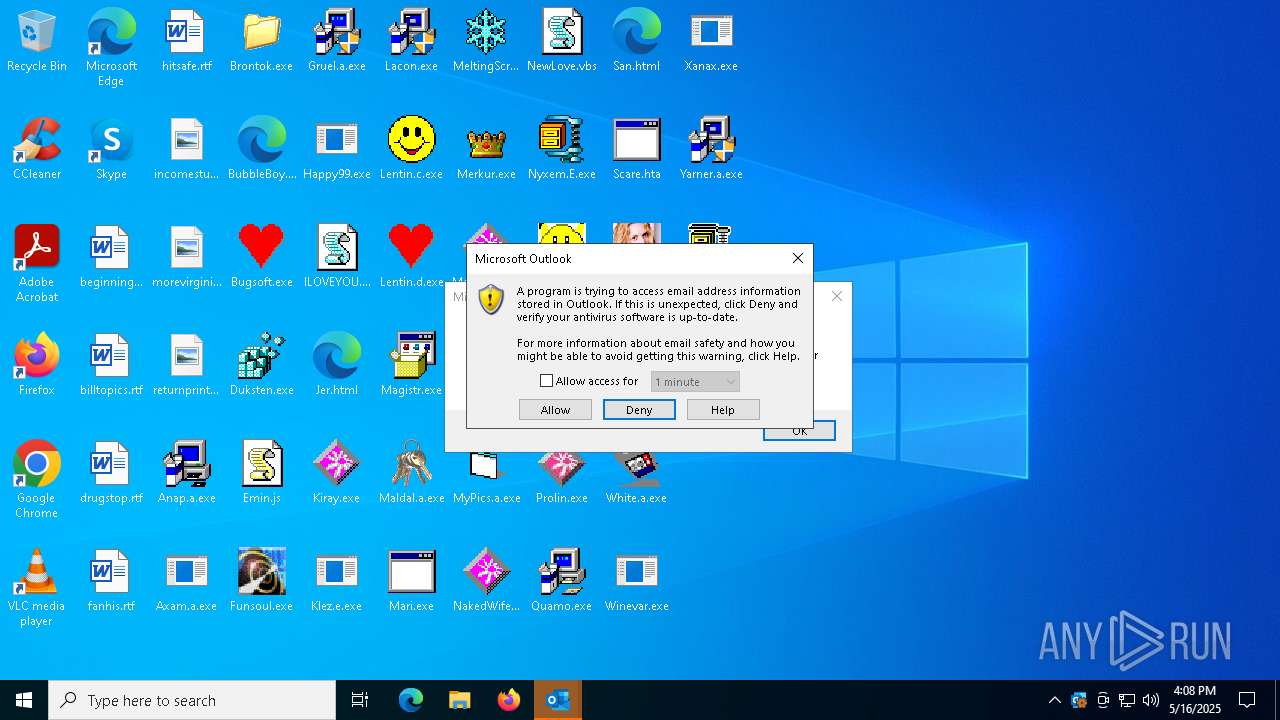
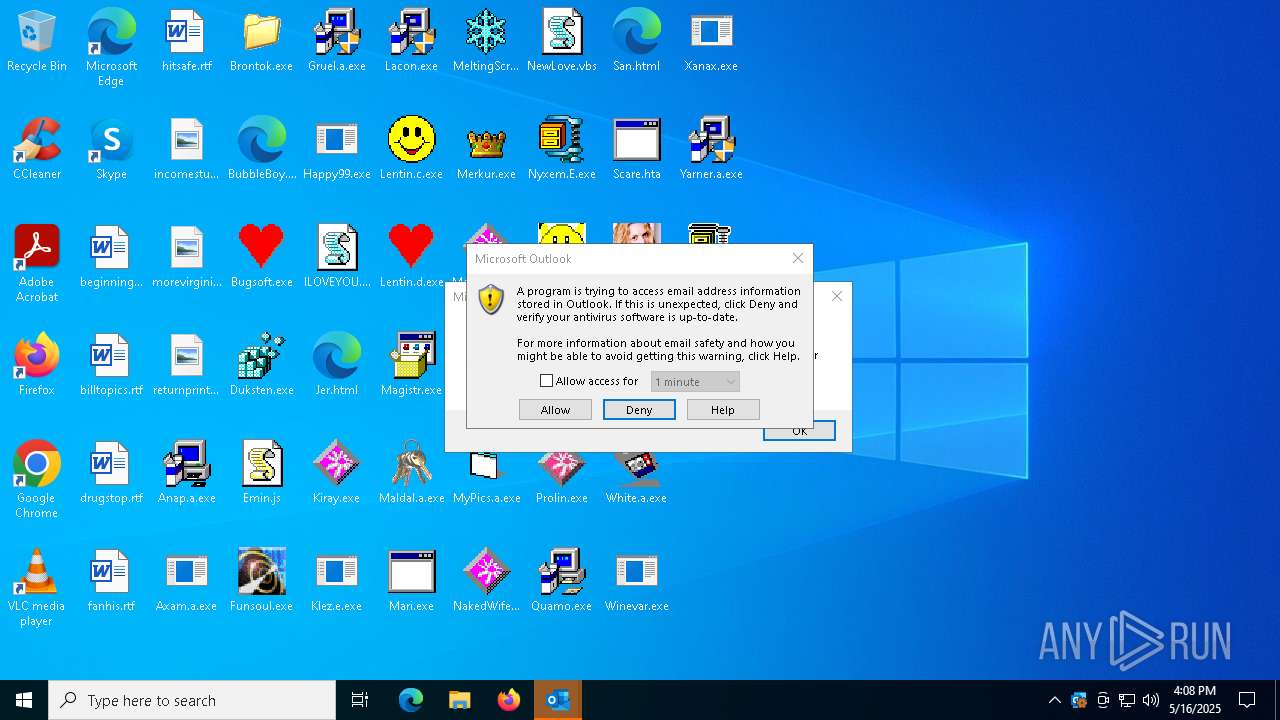
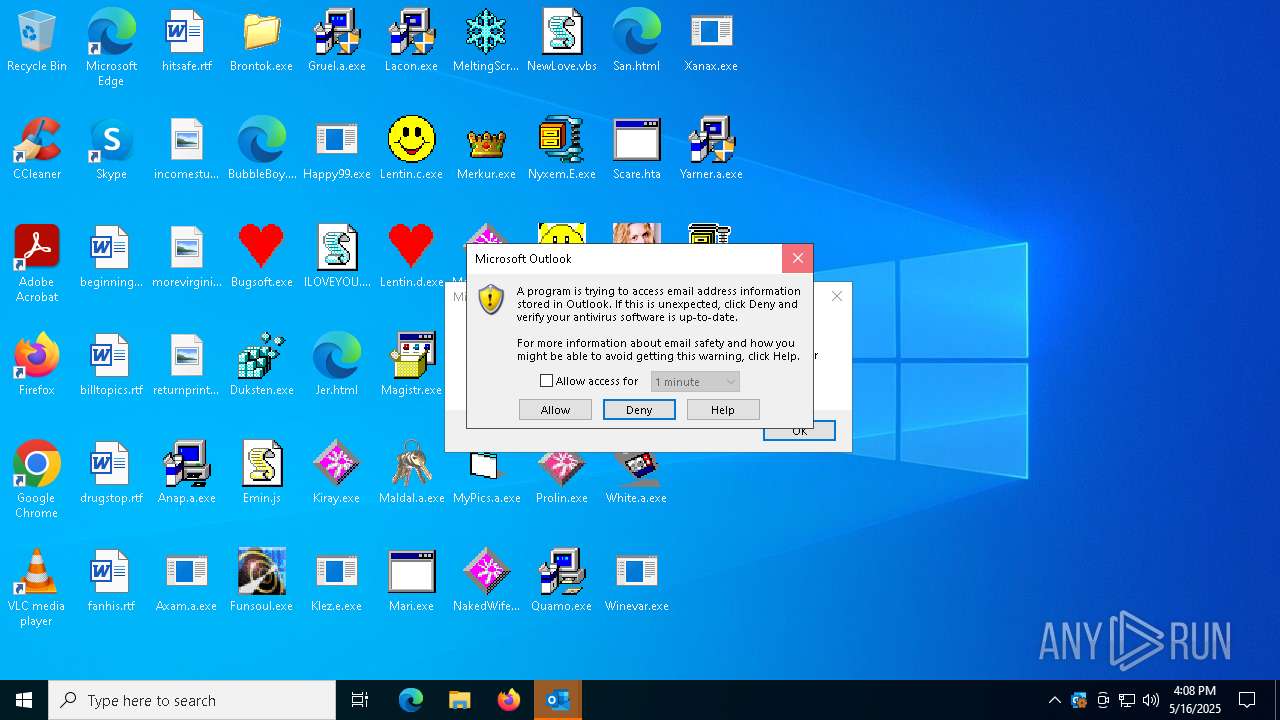
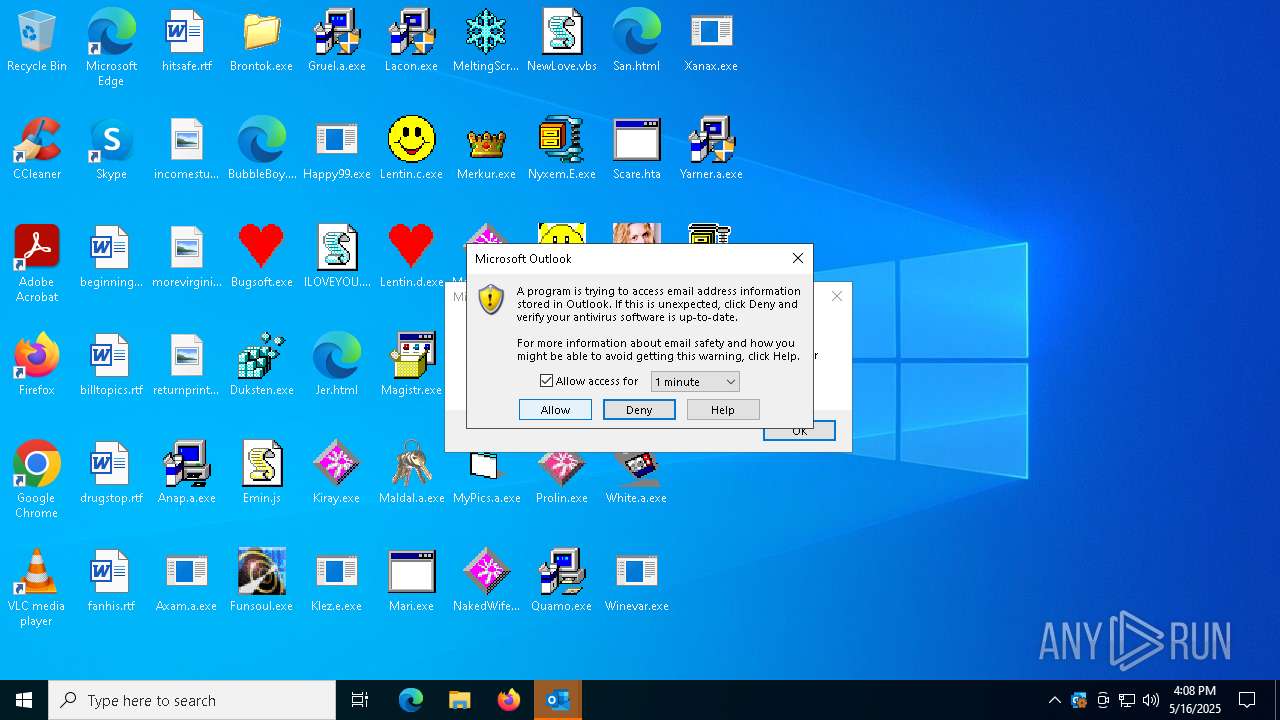
- OUTLOOK.EXE (PID: 1040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 10108 |
| UncompressedSize: | 34304 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | MyPics.a.exe |
Total processes
178
Monitored processes
38
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 132 | "C:\Users\admin\Desktop\Gruel.a.exe" C:\Windows\System32\SystemPropertiesComputerName.exe | C:\Users\admin\Desktop\Gruel.a.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: HIGH Version: 1.00 Modules
| |||||||||||||||
| 208 | "C:\Users\admin\Desktop\Lacon.exe" | C:\Users\admin\Desktop\Lacon.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.00 Modules
| |||||||||||||||
| 208 | "C:\Users\admin\Desktop\Gruel.a.exe" C:\Users\admin\Desktop\Lentin.c.exe | C:\Users\admin\Desktop\Gruel.a.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.00 Modules
| |||||||||||||||
| 208 | rundll32.exe shell32.dll,Control_RunDLL main.cpl @1 | C:\Windows\SysWOW64\rundll32.exe | — | Gruel.a.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 664 | "C:\Users\admin\Desktop\Yarner.a.exe" | C:\Users\admin\Desktop\Yarner.a.exe | explorer.exe | ||||||||||||
User: admin Company: trojaner-info.de Integrity Level: HIGH Description: YAW - Yet Another Warner Version: 2.0.54.554 Modules
| |||||||||||||||
| 856 | "C:\Users\admin\Desktop\Xanax.exe" | C:\Users\admin\Desktop\Xanax.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225477 Modules
| |||||||||||||||
| 1040 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" -Embedding | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 1188 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 856 -s 372 | C:\Windows\SysWOW64\WerFault.exe | — | Xanax.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | regedit /s c:\Windows\system32\regme.reg | C:\Windows\SysWOW64\regedit.exe | — | Merkur.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1532 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Desktop.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
22 148
Read events
21 676
Write events
443
Delete events
29
Modification events
| (PID) Process: | (1532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Desktop.rar | |||
| (PID) Process: | (1532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (1532) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
39
Suspicious files
8
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1532.104\MyPics.a.exe | executable | |
MD5:94EC47428DABB492AF96756E7C95C644 | SHA256:0AE040287546A70F8A2D5FC2DA45A83E253DA044BF10246AE77830AF971B3359 | |||
| 1532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1532.104\Quamo.exe | executable | |
MD5:A1F722324492FDA51077449EC2DB2827 | SHA256:FC2CED1D89845DCFAE55B6E854CD0E622FDF98BAEEB4A67A60852ECD1212F93B | |||
| 1532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1532.104\NewLove.vbs | text | |
MD5:D2B8EA4A267C69040C7D3AD80F64F8BA | SHA256:AA14A4BFB1E6DE52750CC89B91CACBE8BD318634CCB54FA835F5E2C5D1D2F633 | |||
| 1532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1532.104\Pikachu.exe | executable | |
MD5:715614E09261B39DFA439FA1326C0CEC | SHA256:E1DFC005D5403FB2F356276F0ABE19DF68249CE10E5035450926D56C2F8D3652 | |||
| 1532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1532.104\Trood.a.exe | executable | |
MD5:47D1F48A127736E63AAD709DDC9D81D0 | SHA256:24DD269B4D5EDEB591AD992DB33553D90F1848F58C06C9DD9FB3CDB4EAF812F5 | |||
| 1532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1532.104\Scare.hta | html | |
MD5:B4978D1E7542EAFDC7B3908A5F45B8A6 | SHA256:1A8083787B336B322510F93D930F52AEDEB90D2052501E864BFA5B1906E74D58 | |||
| 1532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1532.104\NakedWife.exe | executable | |
MD5:DA9DBA70DE70DC43D6535F2975CEC68D | SHA256:29CEEB3D763D307A0DD7068FA1B2009F2B0D85CA6D2AA5867B12C595BA96762A | |||
| 1532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1532.104\Nyxem.E.exe | executable | |
MD5:A0BDCE2F937FFBB7BA548845B24749C0 | SHA256:62F8364C46300BCE2E75C4CC65039DE3F060B854764DD90F0FA656EFAF31BEA9 | |||
| 1532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1532.104\Xanax.exe | executable | |
MD5:DF24E1CCCEB3C75DADA950A1C1ABCA4D | SHA256:910C03D210381F0443BFCEFE682717F28378DCFE5415071DD127A9837A97B0A6 | |||
| 1532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1532.104\White.a.exe | executable | |
MD5:DFF252D337A54D73C67E38BDA06B72EC | SHA256:C0ACEBEFD398F733123173ADEBAAC32C9BE2C2D52FCB17F6AFF72BE04F3569C4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
51
DNS requests
25
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2112 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4896 | SIHClient.exe | 20.109.210.53:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4896 | SIHClient.exe | 40.69.42.241:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 20.190.160.65:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
241.42.69.40.in-addr.arpa |
| unknown |
7.4.8.4.4.3.1.4.0.0.0.0.0.0.0.0.0.0.0.a.0.0.1.f.1.1.1.0.1.0.a.2.ip6.arpa |
| unknown |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |