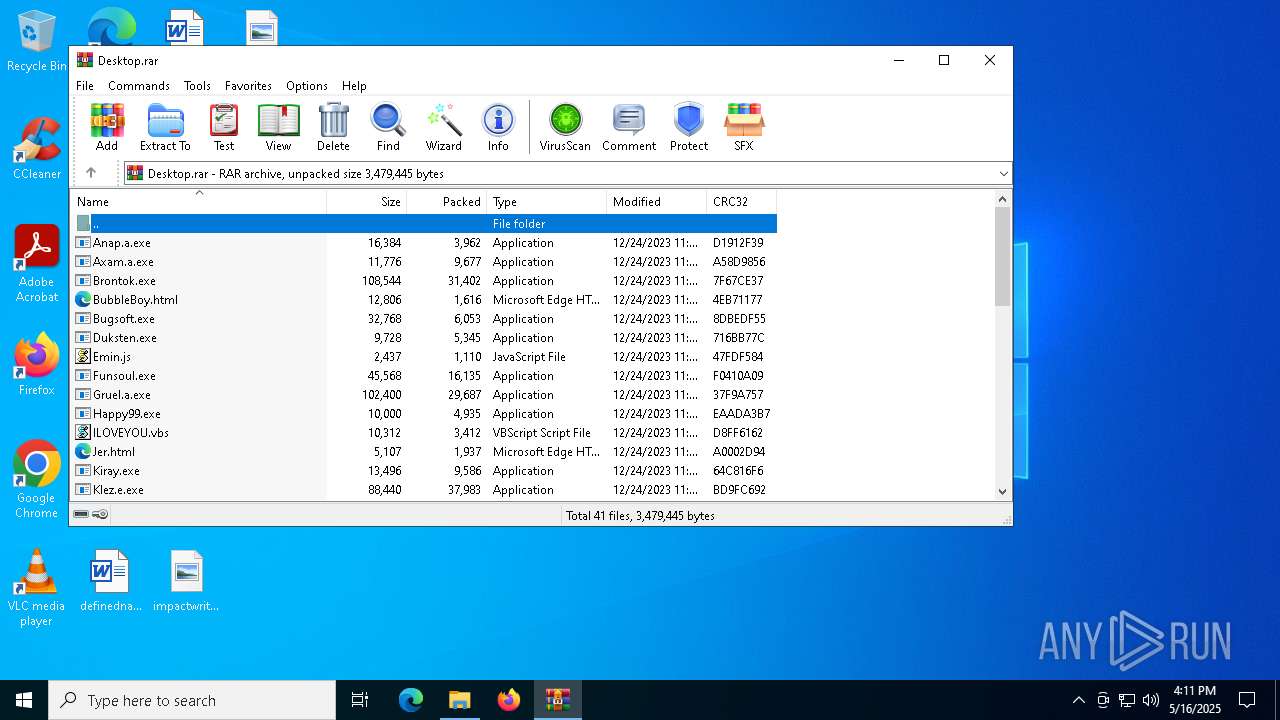
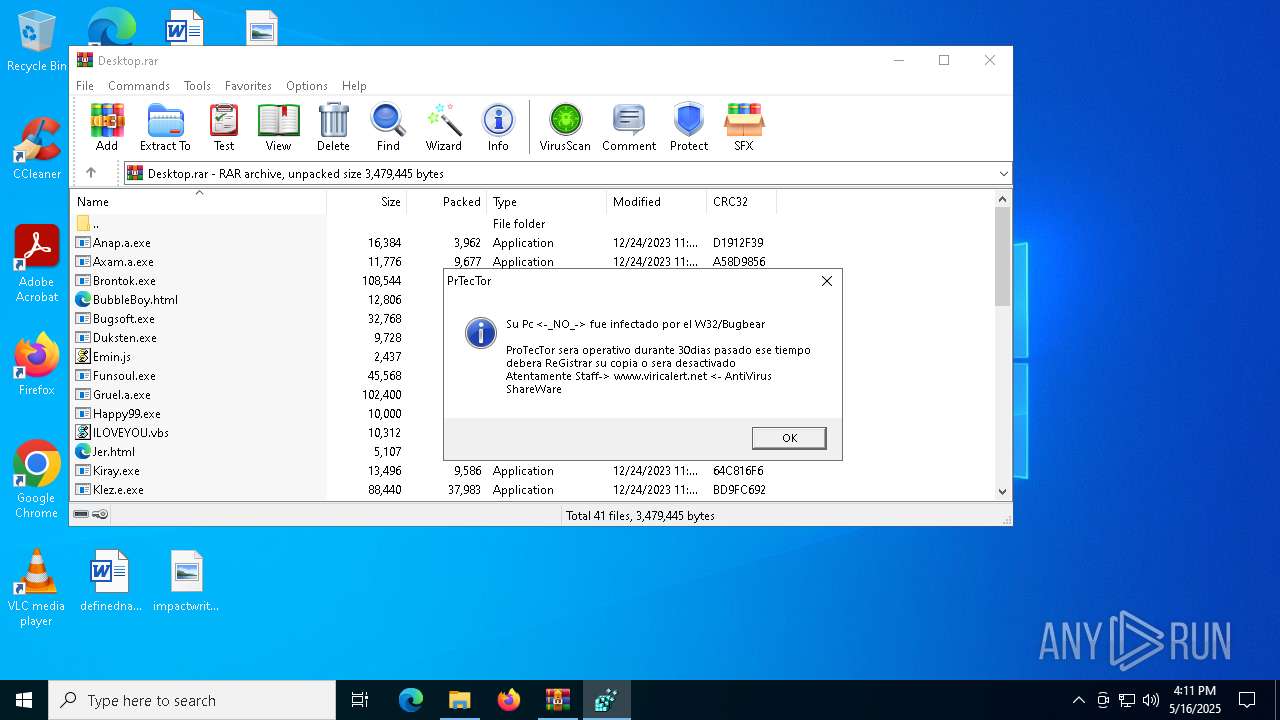
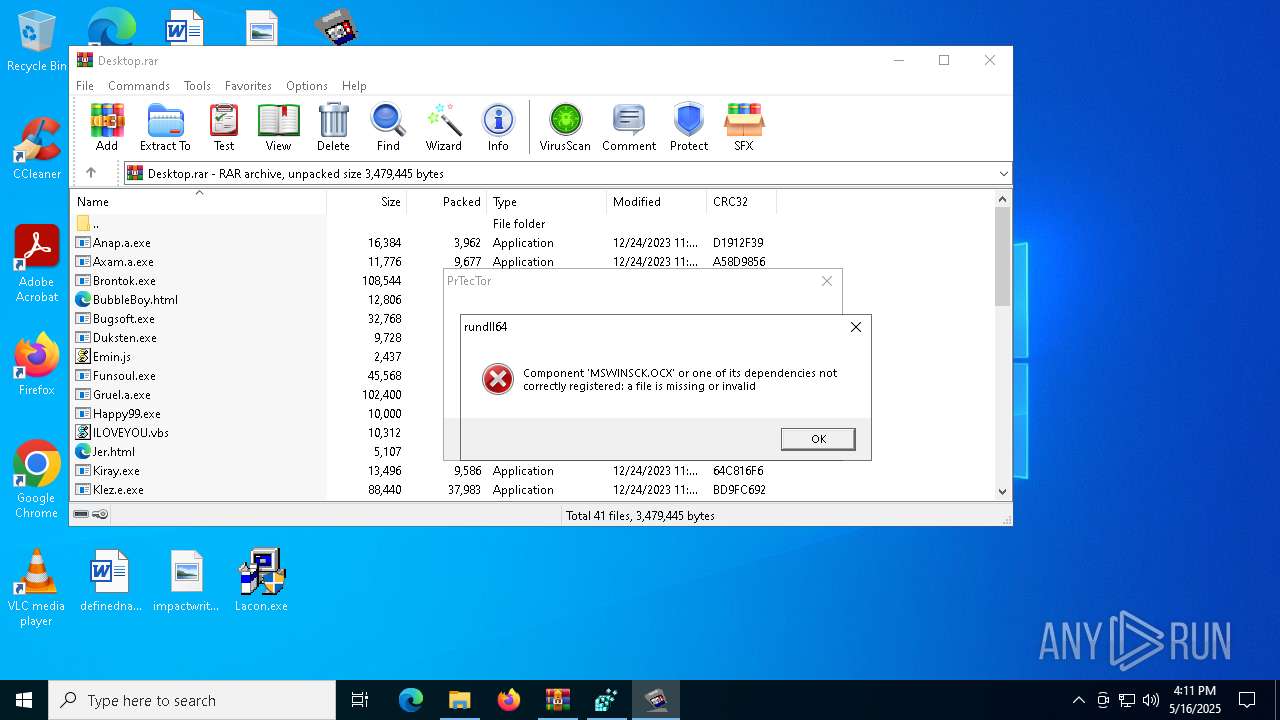
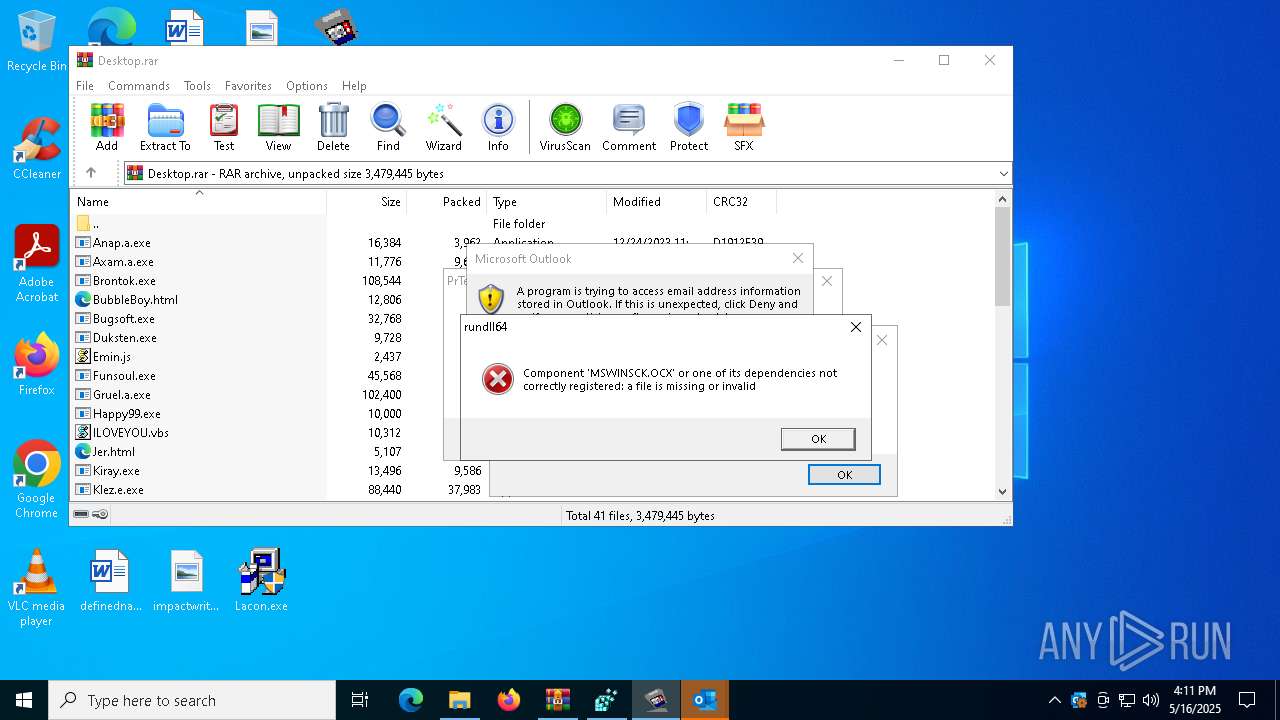
| File name: | Desktop.rar |
| Full analysis: | https://app.any.run/tasks/af3d42fb-2b24-4a71-840e-1ebb5584ebfb |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 16:10:52 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | E7AA9408EE2577D70DEC6B7B8B45B234 |
| SHA1: | D625011A040B62B7C91754344239E274CC2ED935 |
| SHA256: | 7CCFD9B52EA9C8F3FAF6AFAD17BABFF9C052B0B7561B912BCF4030EFB2E9EE78 |
| SSDEEP: | 98304:3Nm+xYOGxxZVEm+PcIPnjSduoiUILbRR9F3vfrgCyMSZdNx0kMmjP5YmTj3alrPK:4URHjy5 |
MALICIOUS
Changes the autorun value in the registry
- Duksten.exe (PID: 7540)
- Lacon.exe (PID: 7676)
Generic archive extractor
- WinRAR.exe (PID: 7392)
Create files in the Startup directory
- Lacon.exe (PID: 7676)
SUSPICIOUS
Executable content was dropped or overwritten
- Lacon.exe (PID: 7676)
Creates file in the systems drive root
- Merkur.exe (PID: 7844)
Uses REG/REGEDIT.EXE to modify registry
- Merkur.exe (PID: 7844)
INFO
Manual execution by a user
- Duksten.exe (PID: 7540)
- Lacon.exe (PID: 7628)
- White.a.exe (PID: 7700)
- Lacon.exe (PID: 7676)
- Kiray.exe (PID: 7768)
- Merkur.exe (PID: 7844)
- Configuration Utility.exe (PID: 7808)
Auto-launch of the file from Registry key
- Duksten.exe (PID: 7540)
- Lacon.exe (PID: 7676)
Failed to create an executable file in Windows directory
- Duksten.exe (PID: 7540)
- Merkur.exe (PID: 7844)
Checks supported languages
- Duksten.exe (PID: 7540)
- White.a.exe (PID: 7700)
- Lacon.exe (PID: 7676)
- Merkur.exe (PID: 7844)
- Kiray.exe (PID: 7768)
Reads the computer name
- Duksten.exe (PID: 7540)
- Lacon.exe (PID: 7676)
- White.a.exe (PID: 7700)
- Kiray.exe (PID: 7768)
- Merkur.exe (PID: 7844)
Create files in a temporary directory
- White.a.exe (PID: 7700)
- Kiray.exe (PID: 7768)
- Merkur.exe (PID: 7844)
The sample compiled with english language support
- Lacon.exe (PID: 7676)
Creates files or folders in the user directory
- Lacon.exe (PID: 7676)
Auto-launch of the file from Startup directory
- Lacon.exe (PID: 7676)
UPX packer has been detected
- Lacon.exe (PID: 7676)
Reads the software policy settings
- slui.exe (PID: 5116)
Checks proxy server information
- slui.exe (PID: 5116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 10108 |
| UncompressedSize: | 34304 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | MyPics.a.exe |
Total processes
141
Monitored processes
13
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5116 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5772 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" -Embedding | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 7392 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Desktop.rar | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7540 | "C:\Users\admin\Desktop\Duksten.exe" | C:\Users\admin\Desktop\Duksten.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 7628 | "C:\Users\admin\Desktop\Lacon.exe" | C:\Users\admin\Desktop\Lacon.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.00 Modules
| |||||||||||||||
| 7676 | "C:\Users\admin\Desktop\Lacon.exe" | C:\Users\admin\Desktop\Lacon.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Version: 1.00 Modules
| |||||||||||||||
| 7700 | "C:\Users\admin\Desktop\White.a.exe" | C:\Users\admin\Desktop\White.a.exe | — | explorer.exe | |||||||||||
User: admin Company: [P54C]-133mhz Integrity Level: MEDIUM Version: 1.01 Modules
| |||||||||||||||
| 7748 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" -Embedding | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 7768 | "C:\Users\admin\Desktop\Kiray.exe" | C:\Users\admin\Desktop\Kiray.exe | — | explorer.exe | |||||||||||
User: admin Company: Macromedia, Inc. Integrity Level: MEDIUM Description: 4,0,7,0 Version: 1.00 Modules
| |||||||||||||||
| 7808 | "C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Configuration Utility.exe" | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Configuration Utility.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.00 Modules
| |||||||||||||||
Total events
16 419
Read events
15 804
Write events
568
Delete events
47
Modification events
| (PID) Process: | (7392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Desktop.rar | |||
| (PID) Process: | (7392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7392) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7540) Duksten.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | XRF |
Value: C:\WINDOWS\system32\PrTecTor.exe | |||
| (PID) Process: | (7676) Lacon.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Bndt32 |
Value: C:\Windows\System32\Bndt32.exe | |||
Executable files
3
Suspicious files
4
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7748 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 7676 | Lacon.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Configuration Utility.exe | executable | |
MD5:CB0F7B3FD927CF0D0BA36302E6F9AF86 | SHA256:9B3F73A12A793D1648F3209E1E3F10BBB548B1EC21D53B8AC060B7B95AE4EF1F | |||
| 7748 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:8E35DC631CCB2DBB28FBF0DF540CEAE8 | SHA256:CA060F4A1029C5C8021E06769747408F20A48934F5A1E601E03B4236A1F94AD8 | |||
| 7676 | Lacon.exe | C:\Windows\SysWOW64\No Call List.exe | executable | |
MD5:CB0F7B3FD927CF0D0BA36302E6F9AF86 | SHA256:9B3F73A12A793D1648F3209E1E3F10BBB548B1EC21D53B8AC060B7B95AE4EF1F | |||
| 7748 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_TableViewPreviewPrefs_2_D0EAFA910A9204429B596EC8AF0EE5AE.dat | xml | |
MD5:0E092DB99AEE99FDFF9B5B222C732CFD | SHA256:D1614AD99ADED9F6F5C1BE7FE7FFA5124BD04A526580DA3818EA8A954E852AA6 | |||
| 7748 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 7700 | White.a.exe | C:\Users\admin\AppData\Local\Temp\~DFE6F33016443E6B8C.TMP | binary | |
MD5:0D3301281760CD82244BF687A73A6936 | SHA256:EBEDEDE617AB650E58C43E4B3F0D43B8DBA0D0876772F0B8281BD3438C1F7353 | |||
| 7676 | Lacon.exe | C:\Windows\SysWOW64\Bndt32.exe | executable | |
MD5:CB0F7B3FD927CF0D0BA36302E6F9AF86 | SHA256:9B3F73A12A793D1648F3209E1E3F10BBB548B1EC21D53B8AC060B7B95AE4EF1F | |||
| 7748 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:CEB94DBC03667053AD3FF6ECEC88C59B | SHA256:25E965AA32B7CC3303E509AB90EE5435756127F8676EEE00E528F58FAA908FD3 | |||
| 7748 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\outlook.exe_Rules.xml | xml | |
MD5:6717E5764CF1DFD429511F96259F7BFC | SHA256:D4C88959519231CD296F4C2E83A627E0C570E66D8C735D82DA302AB0D017C9D9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
59
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7180 | SIHClient.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7180 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
7180 | SIHClient.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
7180 | SIHClient.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
7180 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7180 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
7180 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
7180 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.126.31.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.31.0:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7748 | OUTLOOK.EXE | 52.109.89.18:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
google.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |