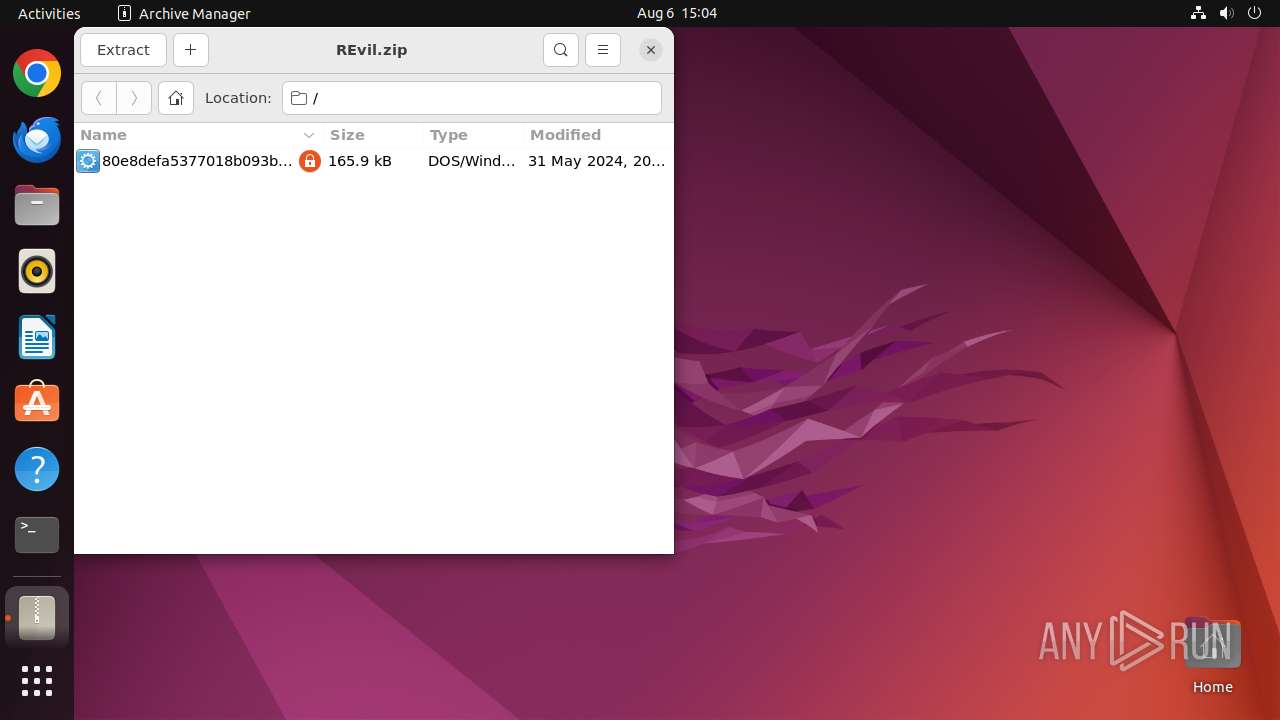
| File name: | REvil.zip |
| Full analysis: | https://app.any.run/tasks/3bed7686-bd94-4cf3-b19a-0e20dd7eb4ac |
| Verdict: | Malicious activity |
| Analysis date: | August 06, 2024, 14:04:18 |
| OS: | Ubuntu 22.04.2 |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 3C791F551555096C50690C5660813F21 |
| SHA1: | 9E6F64E327B9D1F1081DF409831C6CB3138DEDD1 |
| SHA256: | 7CC3E7B8B92C1FE81C82FF9B0A06BA91D505C9089E70445E396E862F172E431A |
| SSDEEP: | 6144:yk1Fo2xvphSSd1Z5xHuvCOFarYls/9OQk/BG:yk1FoSvphSSztuaOAEl2kZG |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executes commands using command-line interpreter
- gnome-terminal-server (PID: 12961)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2024:05:31 20:42:32 |
| ZipCRC: | 0xff8df7cf |
| ZipCompressedSize: | 163837 |
| ZipUncompressedSize: | 165888 |
| ZipFileName: | 80e8defa5377018b093b5b90de0f2957f7062144c83a09a56bba1fe4eda932ce.exe |
Total processes
242
Monitored processes
29
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 12927 | sh -c "file --mime-type /tmp/REvil\.zip" | /bin/sh | — | any-guest-agent |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 12928 | file --mime-type /tmp/REvil.zip | /usr/bin/file | — | sh |
User: root Integrity Level: UNKNOWN Exit code: 0 | ||||
| 12929 | /bin/sh -c "DISPLAY=:0 sudo -iu user file-roller /tmp/REvil\.zip " | /bin/sh | — | any-guest-agent |
User: user Integrity Level: UNKNOWN | ||||
| 12930 | sudo -iu user file-roller /tmp/REvil.zip | /usr/bin/sudo | — | sh |
User: user Integrity Level: UNKNOWN | ||||
| 12931 | file-roller /tmp/REvil.zip | /usr/bin/file-roller | — | sudo |
User: user Integrity Level: UNKNOWN | ||||
| 12932 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | file-roller |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 12946 | /usr/lib/p7zip/7z l -slt -bd -y -- /tmp/REvil.zip | /usr/lib/p7zip/7z | — | file-roller |
User: user Integrity Level: UNKNOWN Exit code: 482 | ||||
| 12948 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 482 | ||||
| 12949 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 482 | ||||
| 12950 | systemctl --user --global is-enabled snap.snapd-desktop-integration.snapd-desktop-integration.service | /usr/bin/systemctl | — | snapd |
User: root Integrity Level: UNKNOWN Exit code: 482 | ||||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
10
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 185.125.190.17:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
470 | avahi-daemon | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 91.189.91.48:80 | connectivity-check.ubuntu.com | Canonical Group Limited | US | unknown |
— | — | 185.125.190.49:80 | connectivity-check.ubuntu.com | Canonical Group Limited | GB | unknown |
— | — | 185.125.190.17:80 | connectivity-check.ubuntu.com | Canonical Group Limited | GB | unknown |
— | — | 138.199.37.37:443 | odrs.gnome.org | Datacamp Limited | DE | unknown |
485 | snapd | 185.125.188.54:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
485 | snapd | 185.125.188.59:443 | api.snapcraft.io | Canonical Group Limited | GB | unknown |
485 | snapd | 185.125.188.55:443 | api.snapcraft.io | Canonical Group Limited | GB | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
connectivity-check.ubuntu.com |
| whitelisted |
google.com |
| whitelisted |
odrs.gnome.org |
| whitelisted |
api.snapcraft.io |
| whitelisted |
233.100.168.192.in-addr.arpa |
| unknown |