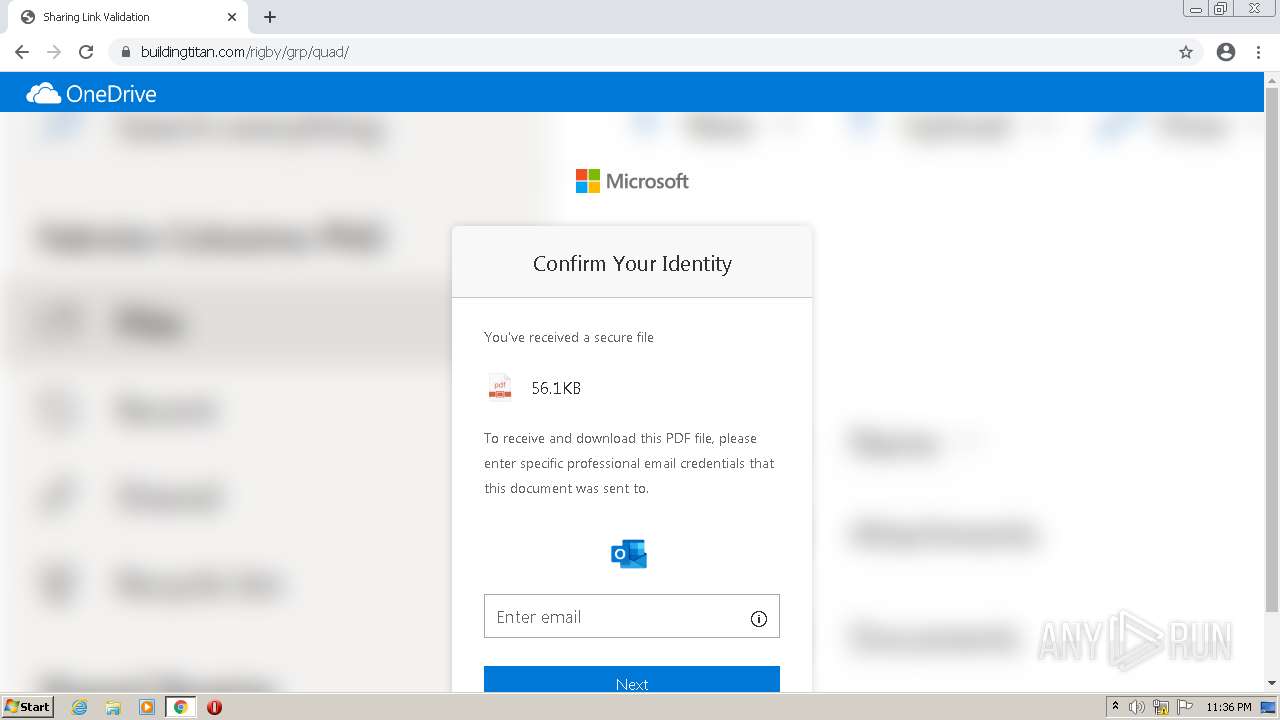
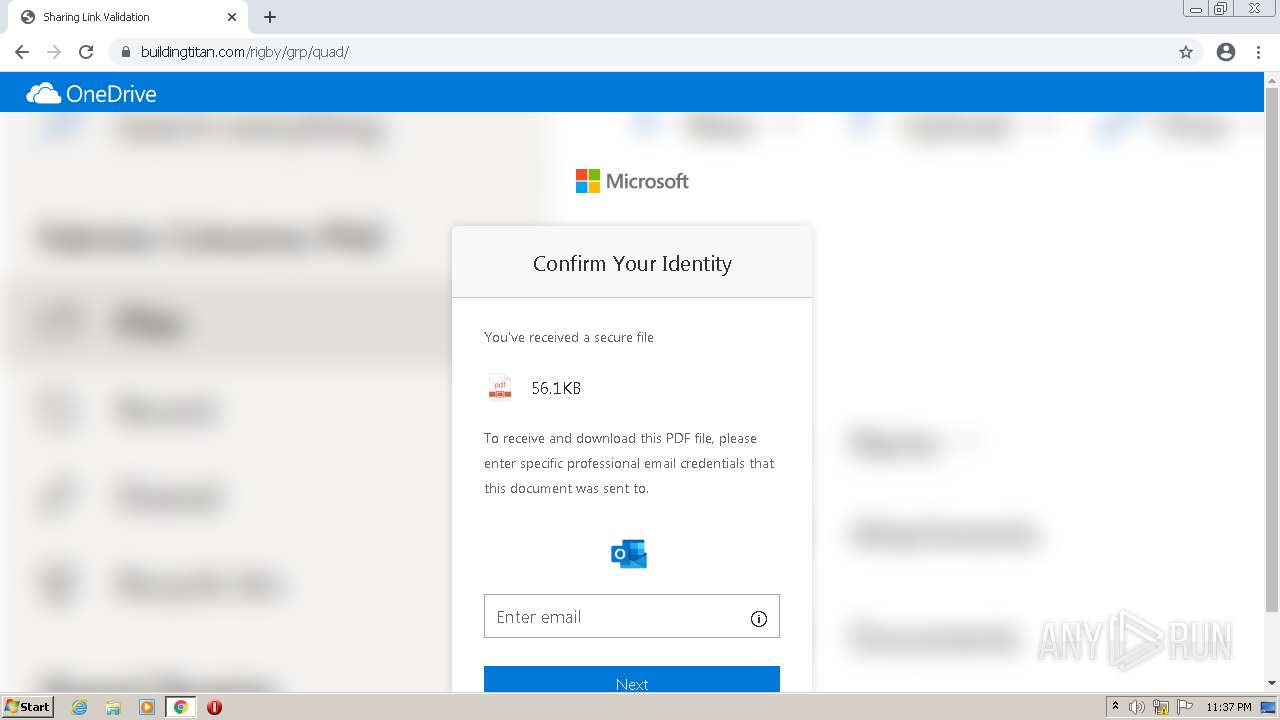
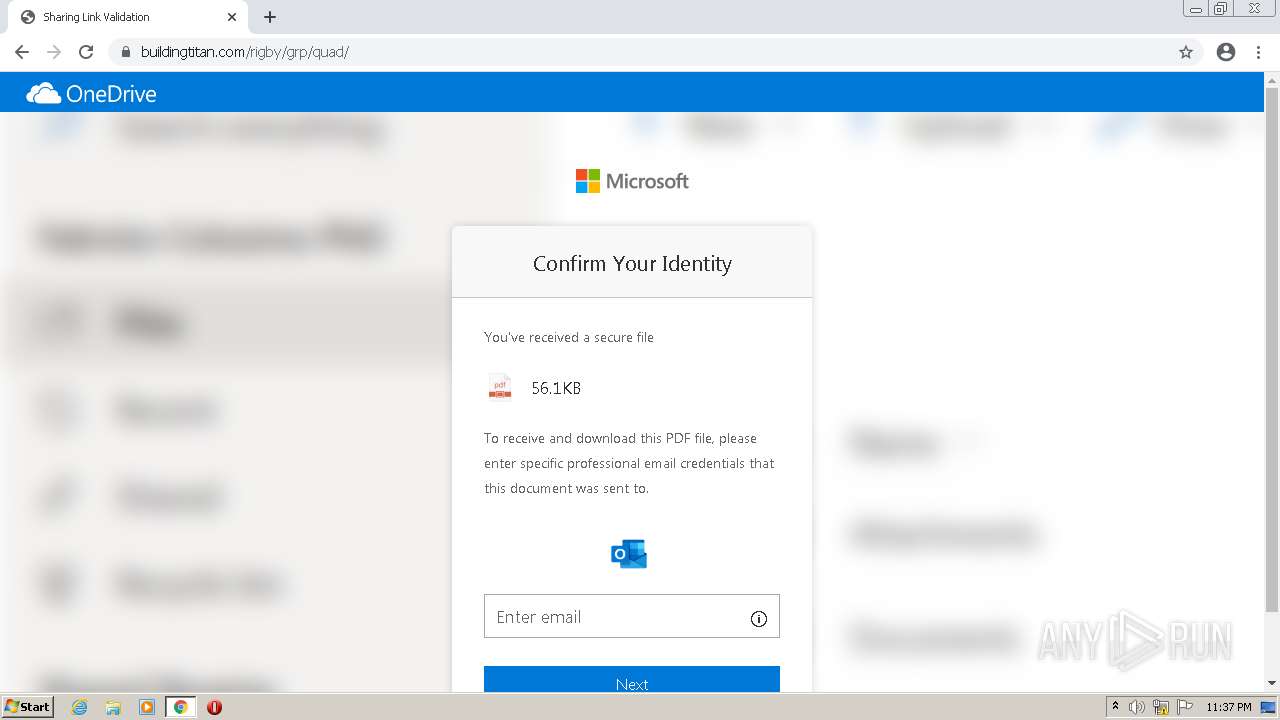
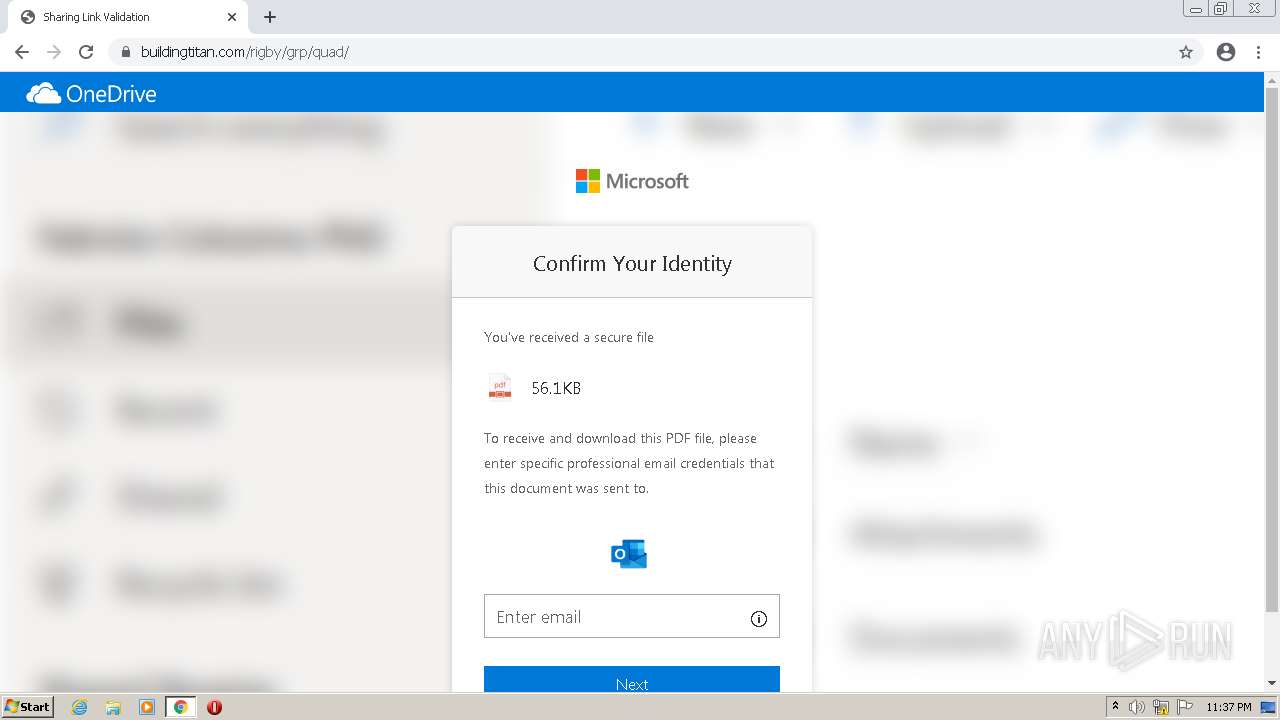
| URL: | https://erigby.clickfunnels.com/optinewmslb58 |
| Full analysis: | https://app.any.run/tasks/cb956a0b-5300-4d0e-bfda-8915683eaef9 |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2022, 22:36:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | CC461C3FE81F8A73C94FEB88140FC9AB |
| SHA1: | 047CB19870F59D0B4DB8DAB4A4796264AA8BB814 |
| SHA256: | 7CBEA2CE8DF607F13F9BD1BE53728520E2E561A93242EBCE1B8CB294CB3D1CF1 |
| SSDEEP: | 3:N8W0DetIRVR2redn:2ZecVYqd |
MALICIOUS
Drops executable file immediately after starts
- chrome.exe (PID: 3820)
SUSPICIOUS
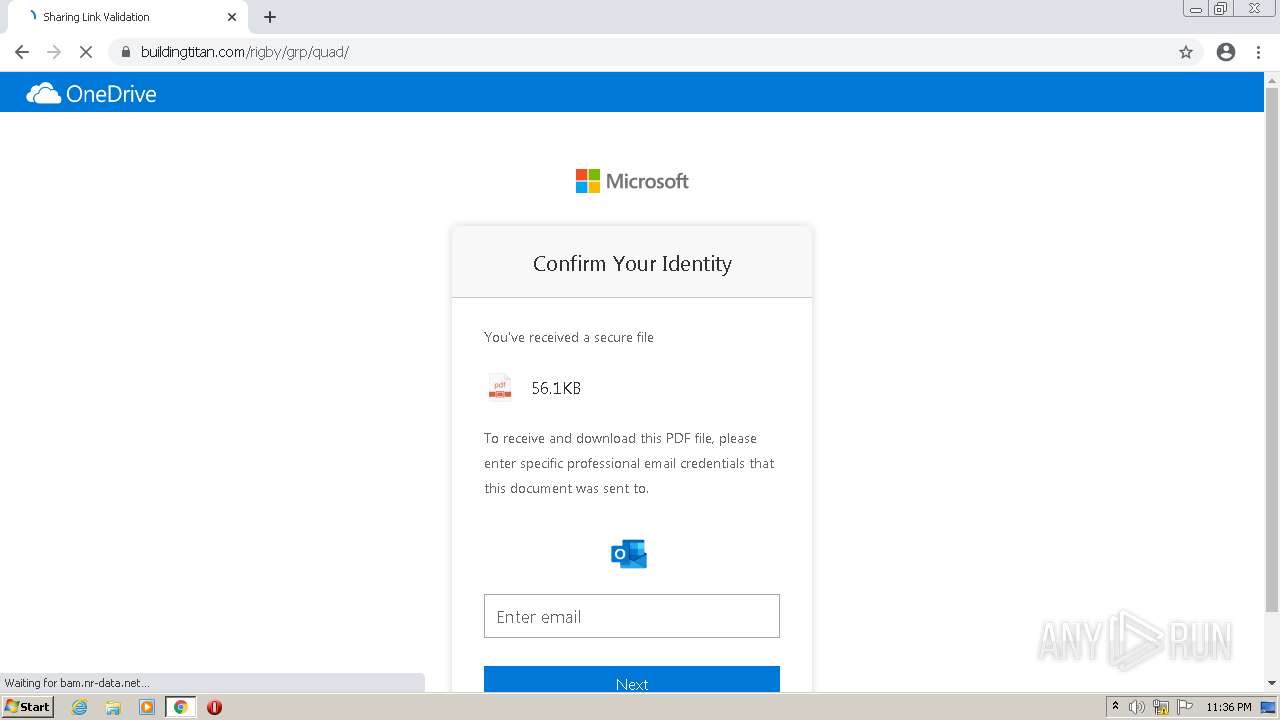
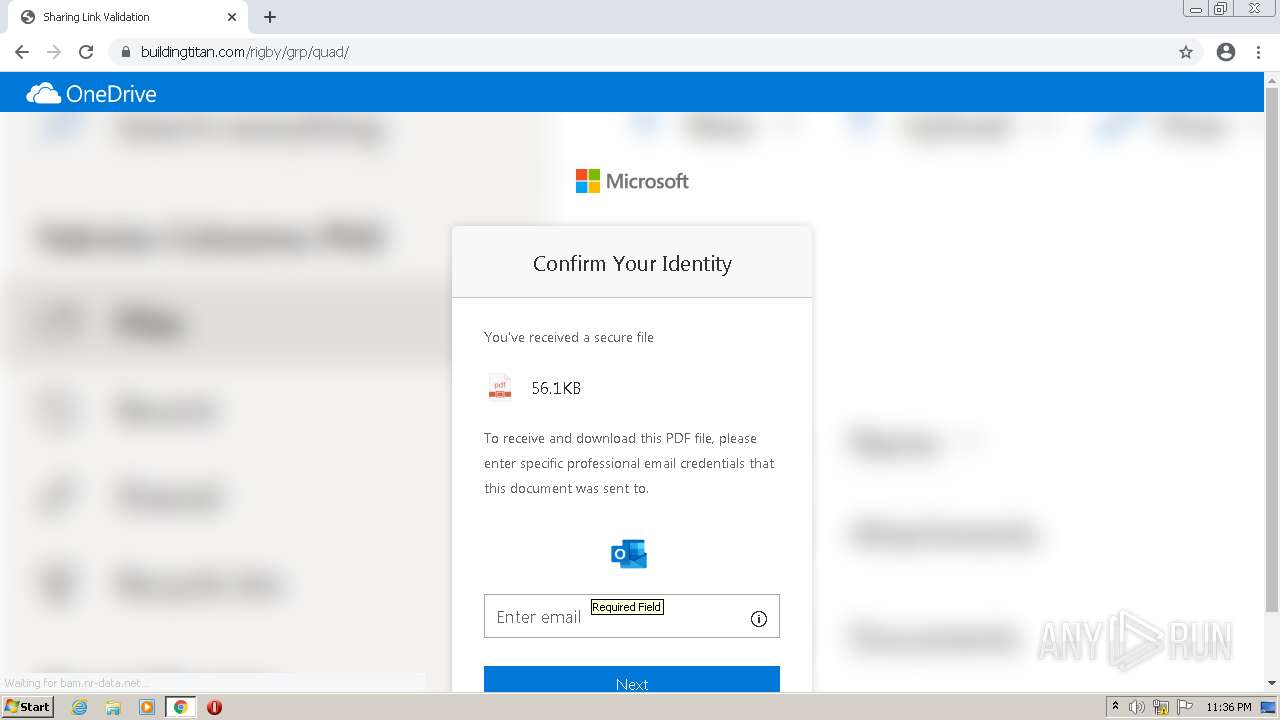
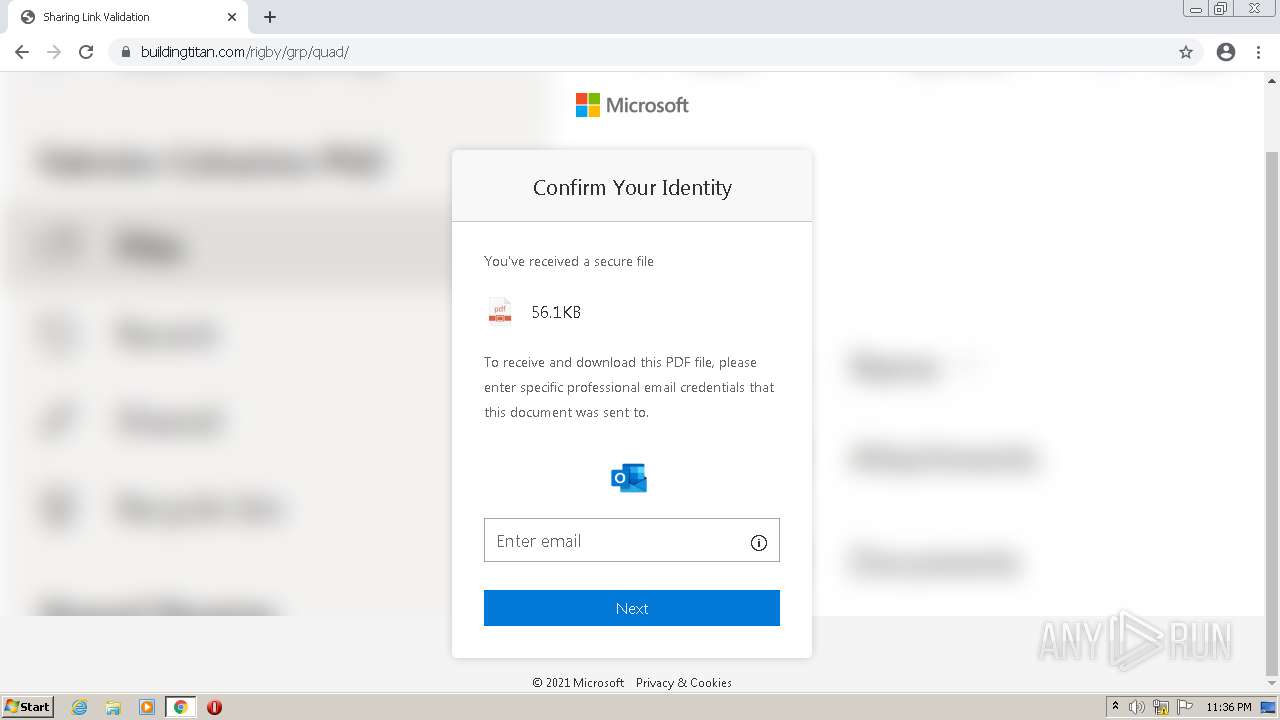
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2564)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2164)
Drops a file with a compile date too recent
- chrome.exe (PID: 3820)
Executable content was dropped or overwritten
- chrome.exe (PID: 3820)
INFO
Checks supported languages
- iexplore.exe (PID: 3068)
- iexplore.exe (PID: 2564)
- chrome.exe (PID: 2164)
- chrome.exe (PID: 2808)
- chrome.exe (PID: 1156)
- chrome.exe (PID: 2764)
- chrome.exe (PID: 1788)
- chrome.exe (PID: 2548)
- chrome.exe (PID: 2632)
- chrome.exe (PID: 3664)
- chrome.exe (PID: 2068)
- chrome.exe (PID: 2392)
- chrome.exe (PID: 2272)
- chrome.exe (PID: 972)
- chrome.exe (PID: 3764)
- chrome.exe (PID: 1144)
- chrome.exe (PID: 2612)
- chrome.exe (PID: 2968)
- chrome.exe (PID: 2428)
- chrome.exe (PID: 468)
- chrome.exe (PID: 3204)
- chrome.exe (PID: 952)
- chrome.exe (PID: 2692)
- chrome.exe (PID: 3996)
- chrome.exe (PID: 1132)
- chrome.exe (PID: 3820)
Changes internet zones settings
- iexplore.exe (PID: 3068)
Reads the computer name
- iexplore.exe (PID: 3068)
- iexplore.exe (PID: 2564)
- chrome.exe (PID: 2164)
- chrome.exe (PID: 2764)
- chrome.exe (PID: 2808)
- chrome.exe (PID: 2068)
- chrome.exe (PID: 972)
- chrome.exe (PID: 3996)
- chrome.exe (PID: 2428)
- chrome.exe (PID: 952)
Application launched itself
- iexplore.exe (PID: 3068)
- chrome.exe (PID: 2164)
Reads settings of System Certificates
- iexplore.exe (PID: 2564)
- iexplore.exe (PID: 3068)
- chrome.exe (PID: 2808)
Checks Windows Trust Settings
- iexplore.exe (PID: 2564)
- iexplore.exe (PID: 3068)
Manual execution by user
- chrome.exe (PID: 2164)
Reads internet explorer settings
- iexplore.exe (PID: 2564)
Reads the date of Windows installation
- iexplore.exe (PID: 3068)
- chrome.exe (PID: 3996)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
63
Monitored processes
26
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 468 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,169889283274455307,4591252358172910343,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=16 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3460 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 952 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1016,169889283274455307,4591252358172910343,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=948 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 972 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1016,169889283274455307,4591252358172910343,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3416 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1132 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1016,169889283274455307,4591252358172910343,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=964 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1144 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1016,169889283274455307,4591252358172910343,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3216 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1156 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=86.0.4240.198 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6e35d988,0x6e35d998,0x6e35d9a4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1788 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,169889283274455307,4591252358172910343,131072 --enable-features=PasswordImport --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1916 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2068 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1016,169889283274455307,4591252358172910343,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=2936 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2164 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | Explorer.EXE | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1016,169889283274455307,4591252358172910343,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2948 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
29 511
Read events
29 258
Write events
244
Delete events
9
Modification events
| (PID) Process: | (3068) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3068) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3068) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30977691 | |||
| (PID) Process: | (3068) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 15352918 | |||
| (PID) Process: | (3068) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30977692 | |||
| (PID) Process: | (3068) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3068) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3068) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3068) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3068) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1
Suspicious files
182
Text files
143
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2164 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-62F6D5F1-874.pma | — | |
MD5:— | SHA256:— | |||
| 2564 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\0M8GA4LB.txt | text | |
MD5:— | SHA256:— | |||
| 2564 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\3WHC3Y7N.txt | text | |
MD5:— | SHA256:— | |||
| 2564 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2564 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_28DEA62A0AE77228DD387E155AD0BA27 | der | |
MD5:— | SHA256:— | |||
| 2564 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\cf-errors[1].css | text | |
MD5:— | SHA256:— | |||
| 2564 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\v1[1].js | html | |
MD5:— | SHA256:— | |||
| 2564 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\I6X193N8.txt | text | |
MD5:— | SHA256:— | |||
| 3068 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\RB6M7CTZ.txt | text | |
MD5:— | SHA256:— | |||
| 3068 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\82CB34DD3343FE727DF8890D352E0D8F | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
69
DNS requests
45
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
880 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvODJiQUFYYVJaZ0k5di1hUFlXS1prX2xDZw/1.0.0.13_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | US | — | — | whitelisted |
2564 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
3068 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
880 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvZjE0QUFYTUR2NXNIakJsbE5jbXNrUkdfQQ/4.10.2391.0_oimompecagnajdejgnnjijobebaeigek.crx | US | binary | 9.74 Kb | whitelisted |
880 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvZjE0QUFYTUR2NXNIakJsbE5jbXNrUkdfQQ/4.10.2391.0_oimompecagnajdejgnnjijobebaeigek.crx | US | binary | 7.39 Kb | whitelisted |
880 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvZjE0QUFYTUR2NXNIakJsbE5jbXNrUkdfQQ/4.10.2391.0_oimompecagnajdejgnnjijobebaeigek.crx | US | binary | 9.74 Kb | whitelisted |
880 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvZjE0QUFYTUR2NXNIakJsbE5jbXNrUkdfQQ/4.10.2391.0_oimompecagnajdejgnnjijobebaeigek.crx | US | binary | 20.9 Kb | whitelisted |
880 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvZjE0QUFYTUR2NXNIakJsbE5jbXNrUkdfQQ/4.10.2391.0_oimompecagnajdejgnnjijobebaeigek.crx | US | binary | 88.5 Kb | whitelisted |
880 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvZjE0QUFYTUR2NXNIakJsbE5jbXNrUkdfQQ/4.10.2391.0_oimompecagnajdejgnnjijobebaeigek.crx | US | binary | 43.5 Kb | whitelisted |
880 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvZjE0QUFYTUR2NXNIakJsbE5jbXNrUkdfQQ/4.10.2391.0_oimompecagnajdejgnnjijobebaeigek.crx | US | binary | 358 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 104.21.63.54:443 | use.fontawesome.com | Cloudflare Inc | US | suspicious |
2808 | chrome.exe | 104.21.63.54:443 | use.fontawesome.com | Cloudflare Inc | US | suspicious |
2564 | iexplore.exe | 8.248.133.254:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | malicious |
2564 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3068 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
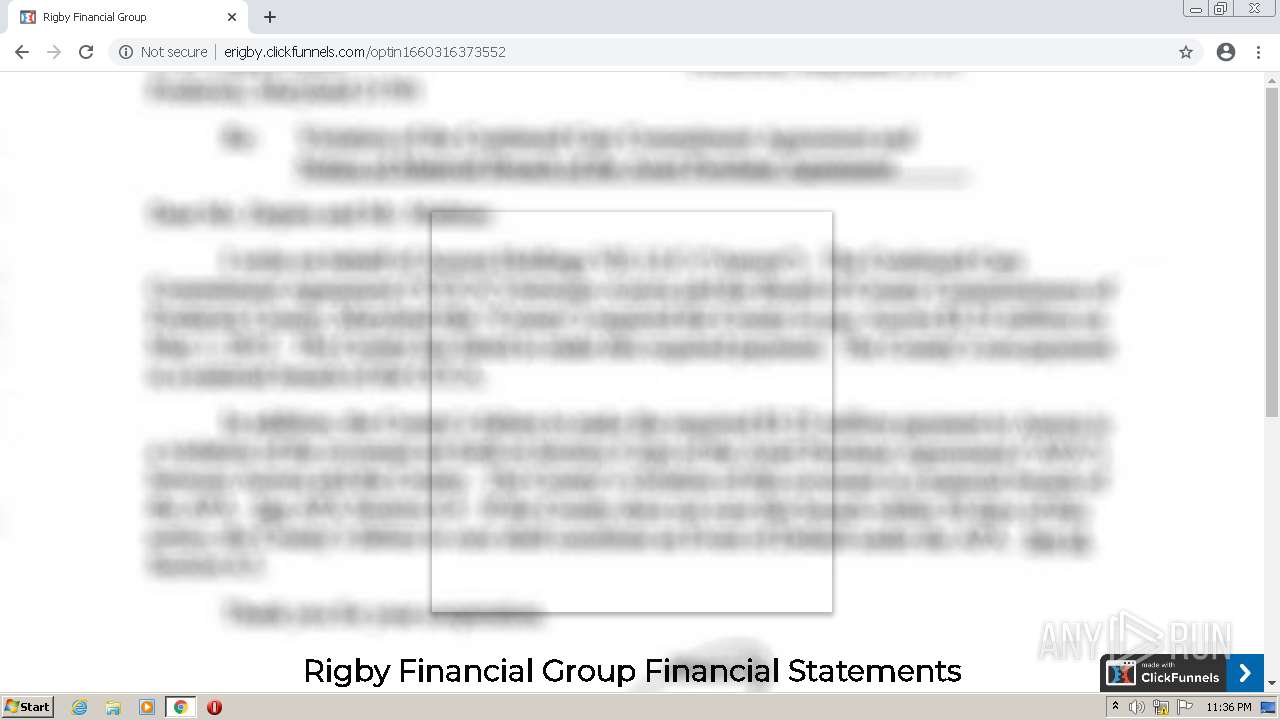
3068 | iexplore.exe | 104.16.15.194:443 | erigby.clickfunnels.com | Cloudflare Inc | US | shared |
3068 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2808 | chrome.exe | 142.250.185.68:443 | www.google.com | Google Inc. | US | whitelisted |
2808 | chrome.exe | 142.250.185.227:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2808 | chrome.exe | 142.250.185.174:443 | clients2.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
erigby.clickfunnels.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
clients2.google.com |
| whitelisted |