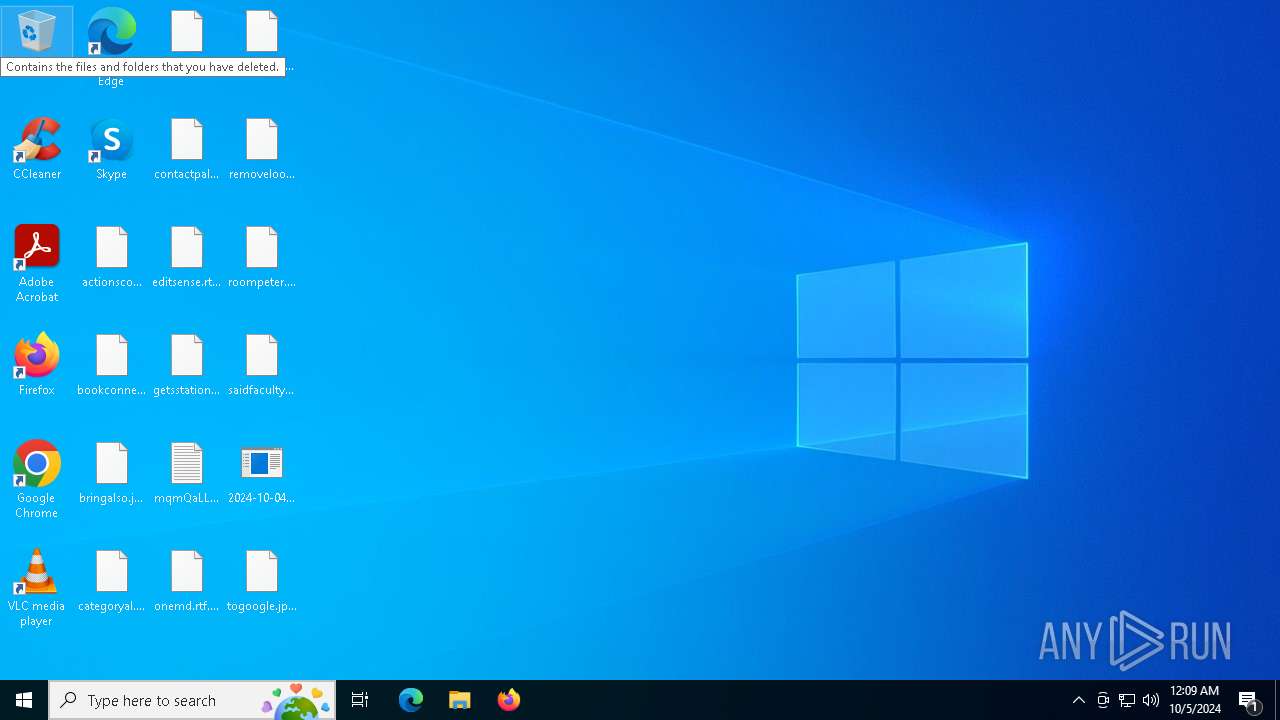
| File name: | 2024-10-04_23f8091893512fa2635817a2f51df391_darkside |
| Full analysis: | https://app.any.run/tasks/15389e17-2068-4bc1-bd92-c61a6992595d |
| Verdict: | Malicious activity |
| Threats: | LockBit, a ransomware variant, encrypts data on infected machines, demanding a ransom payment for decryption. Used in targeted attacks, It's a significant risk to organizations. |
| Analysis date: | October 05, 2024, 00:08:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 23F8091893512FA2635817A2F51DF391 |
| SHA1: | 9F7F2BA48752E37BAADD4C35FEBAA58D613E3194 |
| SHA256: | 7CB6F984F08296D33A4C316CF64FF96E352F07508A364B465A1A572BF73F4AD1 |
| SSDEEP: | 1536:pLnrGGho8OfmhXfwdO3uRpLD6fungFJSxcSXKLER7uuO4zT73C57Q4z6SsmMgBvR:imhXodguLLDzaJ/A7z7zT73B4OjmMVx |
MALICIOUS
Known privilege escalation attack
- dllhost.exe (PID: 6488)
Renames files like ransomware
- 2024-10-04_23f8091893512fa2635817a2f51df391_darkside.exe (PID: 2468)
[YARA] LockBit is detected
- 2024-10-04_23f8091893512fa2635817a2f51df391_darkside.exe (PID: 2468)
SUSPICIOUS
Write to the desktop.ini file (may be used to cloak folders)
- 2024-10-04_23f8091893512fa2635817a2f51df391_darkside.exe (PID: 2468)
Executes as Windows Service
- VSSVC.exe (PID: 2132)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 2584)
Executable content was dropped or overwritten
- 2024-10-04_23f8091893512fa2635817a2f51df391_darkside.exe (PID: 2468)
INFO
Reads the computer name
- 2024-10-04_23f8091893512fa2635817a2f51df391_darkside.exe (PID: 7032)
- 2024-10-04_23f8091893512fa2635817a2f51df391_darkside.exe (PID: 2468)
- ShellExperienceHost.exe (PID: 2584)
Checks supported languages
- 2024-10-04_23f8091893512fa2635817a2f51df391_darkside.exe (PID: 7032)
- 2024-10-04_23f8091893512fa2635817a2f51df391_darkside.exe (PID: 2468)
- ShellExperienceHost.exe (PID: 2584)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 6488)
Reads the machine GUID from the registry
- 2024-10-04_23f8091893512fa2635817a2f51df391_darkside.exe (PID: 7032)
The process uses the downloaded file
- dllhost.exe (PID: 6488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .dll | | | Win32 Dynamic Link Library (generic) (38.3) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (26.2) |
| .exe | | | Win16/32 Executable Delphi generic (12) |
| .exe | | | Generic Win/DOS Executable (11.6) |
| .exe | | | DOS Executable Generic (11.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:09:13 23:30:57+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.12 |
| CodeSize: | 99328 |
| InitializedDataSize: | 50688 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1946f |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
138
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1280 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2132 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2468 | "C:\Users\admin\Desktop\2024-10-04_23f8091893512fa2635817a2f51df391_darkside.exe" | C:\Users\admin\Desktop\2024-10-04_23f8091893512fa2635817a2f51df391_darkside.exe | dllhost.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2584 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3316 | "C:\WINDOWS\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe" -ServerName:App.AppXywbrabmsek0gm3tkwpr5kwzbs55tkqay.mca | C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6488 | C:\WINDOWS\SysWOW64\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7} | C:\Windows\SysWOW64\dllhost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7032 | "C:\Users\admin\Desktop\2024-10-04_23f8091893512fa2635817a2f51df391_darkside.exe" | C:\Users\admin\Desktop\2024-10-04_23f8091893512fa2635817a2f51df391_darkside.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
12 817
Read events
12 745
Write events
65
Delete events
7
Modification events
| (PID) Process: | (6488) dllhost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (2584) ShellExperienceHost.exe | Key: | \REGISTRY\A\{d13f65ad-91e2-6238-9eeb-e00912d3afa7}\LocalState |
| Operation: | write | Name: | PeekBadges |
Value: 5B005D0000001C1E33C9BA16DB01 | |||
| (PID) Process: | (3316) StartMenuExperienceHost.exe | Key: | \REGISTRY\A\{14f7b31d-6ef0-ee15-3f8b-5233752b9c5b}\LocalState\DataCorruptionRecovery |
| Operation: | write | Name: | InitializationAttemptCount |
Value: 010000004C721DFBBA16DB01 | |||
| (PID) Process: | (3316) StartMenuExperienceHost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\TileDataModel\Migration\StartNonLayoutProperties |
| Operation: | write | Name: | Completed |
Value: 1 | |||
| (PID) Process: | (3316) StartMenuExperienceHost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\TileDataModel\Migration\StartNonLayoutProperties_AppUsageData |
| Operation: | write | Name: | Completed |
Value: 1 | |||
| (PID) Process: | (3316) StartMenuExperienceHost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\TileDataModel\Migration\StartNonLayoutProperties_TargetedContentTiles |
| Operation: | write | Name: | Completed |
Value: 1 | |||
| (PID) Process: | (3316) StartMenuExperienceHost.exe | Key: | \REGISTRY\A\{14f7b31d-6ef0-ee15-3f8b-5233752b9c5b}\LocalState |
| Operation: | write | Name: | FirstRunSettingUTM |
Value: 01000000BE5048FBBA16DB01 | |||
| (PID) Process: | (3316) StartMenuExperienceHost.exe | Key: | \REGISTRY\A\{14f7b31d-6ef0-ee15-3f8b-5233752b9c5b}\LocalState |
| Operation: | write | Name: | FirstRunTimeUTM |
Value: BEAE18AEBB16DB01BE5048FBBA16DB01 | |||
| (PID) Process: | (3316) StartMenuExperienceHost.exe | Key: | \REGISTRY\A\{14f7b31d-6ef0-ee15-3f8b-5233752b9c5b}\LocalState |
| Operation: | write | Name: | AllAppsSeenTimeUTM |
Value: BEAE18AEBB16DB01BE5048FBBA16DB01 | |||
| (PID) Process: | (3316) StartMenuExperienceHost.exe | Key: | \REGISTRY\A\{14f7b31d-6ef0-ee15-3f8b-5233752b9c5b}\LocalState |
| Operation: | write | Name: | FirstRunAfterInstallOrUpdateVersion |
Value: 4D006900630072006F0073006F00660074002E00570069006E0064006F00770073002E00530074006100720074004D0065006E00750045007800700065007200690065006E006300650048006F00730074005F00310030002E0030002E00310039003000340031002E0033003600330036005F006E00650075007400720061006C005F006E00650075007400720061006C005F006300770035006E003100680032007400780079006500770079000000BE5048FBBA16DB01 | |||
Executable files
18
Suspicious files
1 946
Text files
2 170
Unknown types
40
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2468 | 2024-10-04_23f8091893512fa2635817a2f51df391_darkside.exe | C:\$Recycle.Bin\S-1-5-18\desktop.ini | binary | |
MD5:1BF74B967804B19C5D287C5593808D1C | SHA256:26B19EDD167168A63D5472DC9005D0863064E921111CE6C5E3F9E1211B49D845 | |||
| 2468 | 2024-10-04_23f8091893512fa2635817a2f51df391_darkside.exe | C:\$Recycle.Bin\S-1-5-18\AAAAAAAAAAA | binary | |
MD5:1BF74B967804B19C5D287C5593808D1C | SHA256:26B19EDD167168A63D5472DC9005D0863064E921111CE6C5E3F9E1211B49D845 | |||
| 2468 | 2024-10-04_23f8091893512fa2635817a2f51df391_darkside.exe | C:\mqmQaLLxg.README.txt | text | |
MD5:E660A65FCF9340820AFF87745A4B9074 | SHA256:1A0FF740DCFBD23A131C794C9B43A8CF3578B361814E89987A8CA752C936CD93 | |||
| 2468 | 2024-10-04_23f8091893512fa2635817a2f51df391_darkside.exe | C:\$Recycle.Bin\S-1-5-18\CCCCCCCCCCC | binary | |
MD5:1BF74B967804B19C5D287C5593808D1C | SHA256:26B19EDD167168A63D5472DC9005D0863064E921111CE6C5E3F9E1211B49D845 | |||
| 2468 | 2024-10-04_23f8091893512fa2635817a2f51df391_darkside.exe | C:\$Recycle.Bin\S-1-5-18\EEEEEEEEEEE | binary | |
MD5:1BF74B967804B19C5D287C5593808D1C | SHA256:26B19EDD167168A63D5472DC9005D0863064E921111CE6C5E3F9E1211B49D845 | |||
| 2468 | 2024-10-04_23f8091893512fa2635817a2f51df391_darkside.exe | C:\$Recycle.Bin\S-1-5-18\MMMMMMMMMMM | binary | |
MD5:1BF74B967804B19C5D287C5593808D1C | SHA256:26B19EDD167168A63D5472DC9005D0863064E921111CE6C5E3F9E1211B49D845 | |||
| 2468 | 2024-10-04_23f8091893512fa2635817a2f51df391_darkside.exe | C:\$Recycle.Bin\S-1-5-18\DDDDDDDDDDD | binary | |
MD5:1BF74B967804B19C5D287C5593808D1C | SHA256:26B19EDD167168A63D5472DC9005D0863064E921111CE6C5E3F9E1211B49D845 | |||
| 2468 | 2024-10-04_23f8091893512fa2635817a2f51df391_darkside.exe | C:\$Recycle.Bin\S-1-5-18\BBBBBBBBBBB | binary | |
MD5:1BF74B967804B19C5D287C5593808D1C | SHA256:26B19EDD167168A63D5472DC9005D0863064E921111CE6C5E3F9E1211B49D845 | |||
| 2468 | 2024-10-04_23f8091893512fa2635817a2f51df391_darkside.exe | C:\$Recycle.Bin\S-1-5-18\JJJJJJJJJJJ | binary | |
MD5:1BF74B967804B19C5D287C5593808D1C | SHA256:26B19EDD167168A63D5472DC9005D0863064E921111CE6C5E3F9E1211B49D845 | |||
| 2468 | 2024-10-04_23f8091893512fa2635817a2f51df391_darkside.exe | C:\$Recycle.Bin\S-1-5-18\GGGGGGGGGGG | binary | |
MD5:1BF74B967804B19C5D287C5593808D1C | SHA256:26B19EDD167168A63D5472DC9005D0863064E921111CE6C5E3F9E1211B49D845 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
43
TCP/UDP connections
33
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 404 | 104.126.37.160:443 | https://r.bing.com/rb/4N/jnc,nj/WHBHN5CD2X9iLHkLc7Ck-5t1mtg.js?bu=FpIs1Cr8AeQq5yrqKuwqkSuaLOAr5RH6K4Asniz8AfwBgyjDK-MR2hHXK8gr&or=w | unknown | — | — | unknown |
2952 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 104.126.37.153:443 | https://r.bing.com/rb/1a/cir3,ortl,cc,nc/CYGXBN1kkA_ojDY5vKbCoG4Zy0E.css?bu=C8MJmAO6BJ8KhAnuCPQGWlpaWg&or=w | unknown | text | 19.9 Kb | whitelisted |
— | — | GET | 200 | 104.126.37.160:443 | https://r.bing.com/rb/1a/cir3,ortl,cc,nc/eNojzGTgc6FFJi_kGAzzghOMEG4.css?bu=B8ECRa8ClwFaWswC&or=w | unknown | text | 5.92 Kb | whitelisted |
— | — | POST | 204 | 104.126.37.123:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | whitelisted |
— | — | POST | 204 | 104.126.37.123:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | whitelisted |
— | — | POST | 204 | 104.126.37.170:443 | https://www.bing.com/fd/ls/lsp.aspx? | unknown | — | — | whitelisted |
— | — | GET | 200 | 104.126.37.160:443 | https://r.bing.com/rp/-lxTjronWiCCazqIxFTp4HrDoXc.gz.js | unknown | binary | 950 b | whitelisted |
— | — | POST | 204 | 104.126.37.160:443 | https://www.bing.com/fd/ls/lsp.aspx? | unknown | — | — | whitelisted |
— | — | GET | 200 | 104.126.37.137:443 | https://r.bing.com/rp/0jUdtV12Tn_stZnlwEN7jHJWY2Y.gz.js | unknown | text | 1.44 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2952 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4324 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2952 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2952 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1280 | SearchApp.exe | 2.23.209.133:443 | r.bing.com | Akamai International B.V. | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
r.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |