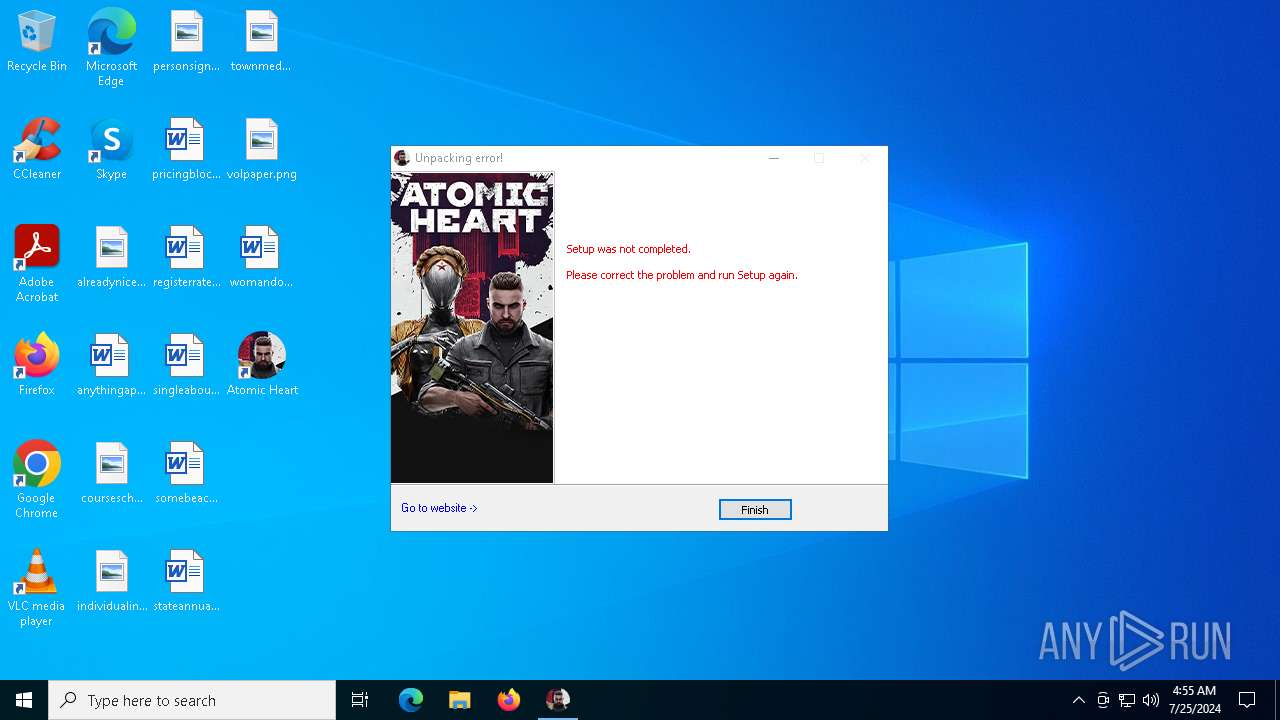
| File name: | Setup.exe |
| Full analysis: | https://app.any.run/tasks/65cbc76c-82b4-4eb7-a5d1-21095fa917c7 |
| Verdict: | Malicious activity |
| Analysis date: | July 25, 2024, 04:54:58 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 10542DCE0AF390A220E444A2B94B78E4 |
| SHA1: | 85E0B1B74AE36884D214C88FE55F6965A5BFD28B |
| SHA256: | 7CB6E3F3FAEC644F4DFFB8A0D85F27BC7BB9AE7E66CD520789937063CD01CF61 |
| SSDEEP: | 49152:MR7SjLwUizO7MPVhH1ZMzd5hwDzC8XGVgFZNOBVz+BpKuWRxg/ZBzuwYY+tywWTv:cuI7zbfH1ZMfhCzHGVg7Nc+7CRxgfznD |
MALICIOUS
Drops the executable file immediately after the start
- Setup.exe (PID: 4188)
- Setup.tmp (PID: 5688)
- unins000.exe (PID: 2988)
- _iu14D2N.tmp (PID: 6604)
Uses Task Scheduler to run other applications
- _iu14D2N.tmp (PID: 6604)
SUSPICIOUS
Executable content was dropped or overwritten
- Setup.exe (PID: 4188)
- Setup.tmp (PID: 5688)
- unins000.exe (PID: 2988)
- _iu14D2N.tmp (PID: 6604)
Reads the Windows owner or organization settings
- Setup.tmp (PID: 5688)
- _iu14D2N.tmp (PID: 6604)
Process drops legitimate windows executable
- Setup.tmp (PID: 5688)
- _iu14D2N.tmp (PID: 6604)
Starts itself from another location
- unins000.exe (PID: 2988)
Starts application with an unusual extension
- unins000.exe (PID: 2988)
Reads the date of Windows installation
- _iu14D2N.tmp (PID: 6604)
INFO
Reads the computer name
- Setup.tmp (PID: 5688)
- unins000.exe (PID: 2988)
- _iu14D2N.tmp (PID: 6604)
Checks supported languages
- Setup.exe (PID: 4188)
- Setup.tmp (PID: 5688)
- unins000.exe (PID: 2988)
- _iu14D2N.tmp (PID: 6604)
Create files in a temporary directory
- Setup.exe (PID: 4188)
- Setup.tmp (PID: 5688)
- unins000.exe (PID: 2988)
- _iu14D2N.tmp (PID: 6604)
Creates files in the program directory
- Setup.tmp (PID: 5688)
Creates a software uninstall entry
- Setup.tmp (PID: 5688)
Process checks computer location settings
- _iu14D2N.tmp (PID: 6604)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (81.5) |
|---|---|---|
| .exe | | | Win32 Executable Delphi generic (10.5) |
| .exe | | | Win32 Executable (generic) (3.3) |
| .exe | | | Win16/32 Executable Delphi generic (1.5) |
| .exe | | | Generic Win/DOS Executable (1.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 37888 |
| InitializedDataSize: | 151040 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x9c14 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
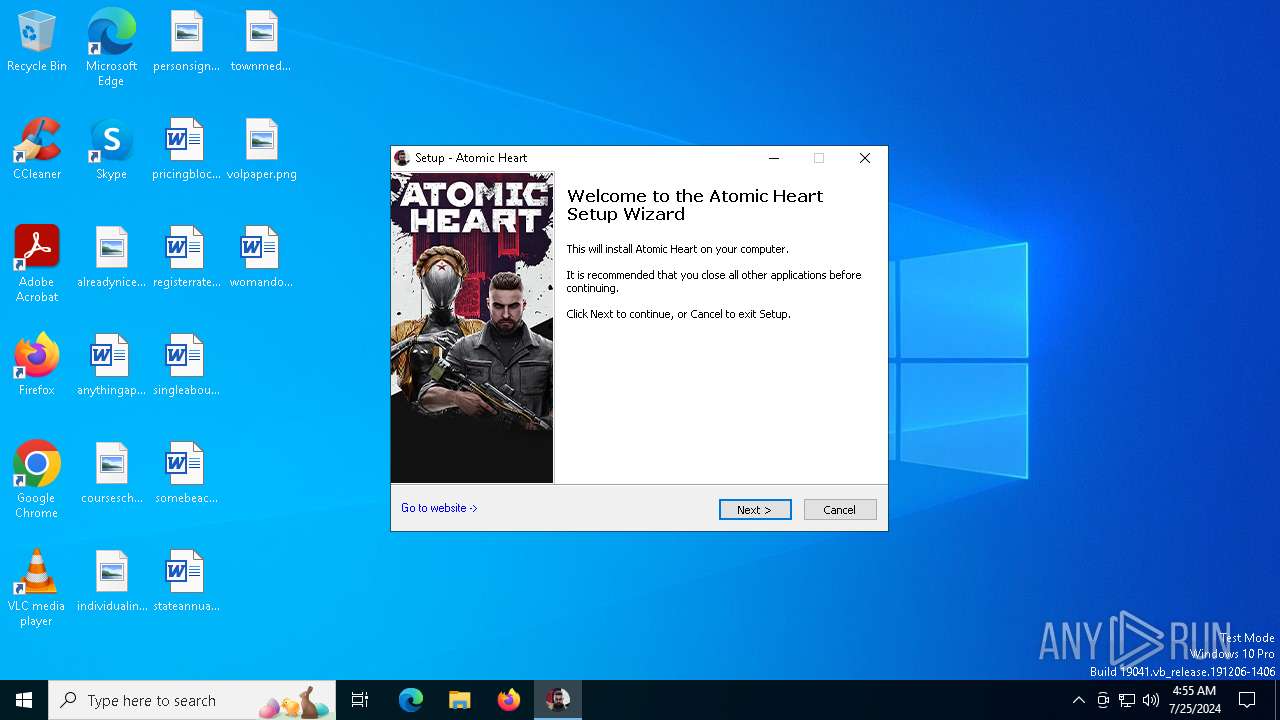
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | RePack |
| FileDescription: | Atomic Heart Setup |
| FileVersion: | 1.0.0.0 |
| LegalCopyright: | RePack |
| ProductName: | Atomic Heart |
| ProductVersion: | 1.0.0.0 |
Total processes
144
Monitored processes
8
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2988 | "C:\Program Files (x86)\Atomic Heart\unins000.exe" /VERYSILENT | C:\Program Files (x86)\Atomic Heart\unins000.exe | Setup.tmp | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 3488 | "schtasks.exe" /create /XML C:\Users\admin\Documents\unins000.dat /tn admin | C:\Windows\SysWOW64\schtasks.exe | — | _iu14D2N.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4188 | "C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Setup.exe | explorer.exe | ||||||||||||
User: admin Company: RePack Integrity Level: HIGH Description: Atomic Heart Setup Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 5052 | "C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\Setup.exe | — | explorer.exe | |||||||||||
User: admin Company: RePack Integrity Level: MEDIUM Description: Atomic Heart Setup Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 5688 | "C:\Users\admin\AppData\Local\Temp\is-JA24O.tmp\Setup.tmp" /SL5="$401E2,1093975,189952,C:\Users\admin\AppData\Local\Temp\Setup.exe" | C:\Users\admin\AppData\Local\Temp\is-JA24O.tmp\Setup.tmp | Setup.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 6592 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6604 | "C:\Users\admin\AppData\Local\Temp\_iu14D2N.tmp" /SECONDPHASE="C:\Program Files (x86)\Atomic Heart\unins000.exe" /FIRSTPHASEWND=$40314 /VERYSILENT | C:\Users\admin\AppData\Local\Temp\_iu14D2N.tmp | unins000.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 7100 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | schtasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 860
Read events
2 831
Write events
24
Delete events
5
Modification events
| (PID) Process: | (5688) Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 38160000B98D8CD04EDEDA01 | |||
| (PID) Process: | (5688) Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: A3EAADF9AB66CBC030581DE3A5F6D475252223C955ECE721298C72B19EC4484D | |||
| (PID) Process: | (5688) Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (5688) Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Atomic Heart_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 5.5.1.ee2 (a) | |||
| (PID) Process: | (5688) Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Atomic Heart_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
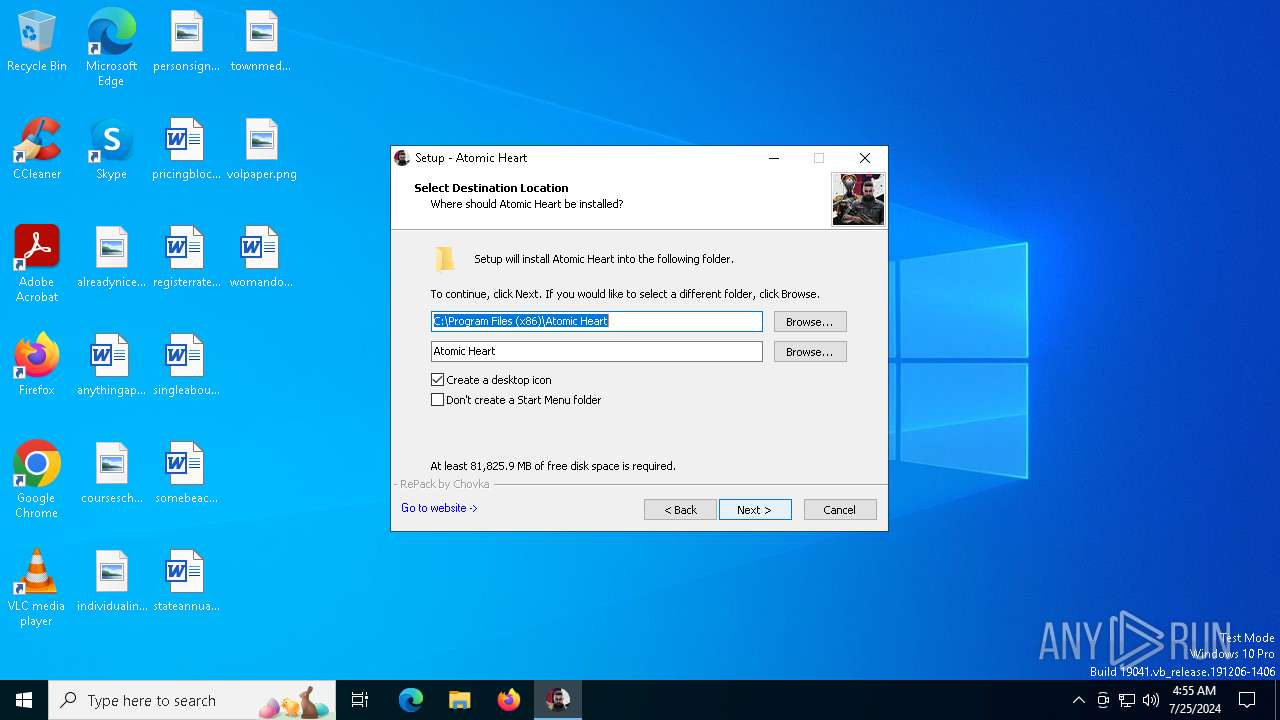
Value: C:\Program Files (x86)\Atomic Heart | |||
| (PID) Process: | (5688) Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Atomic Heart_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files (x86)\Atomic Heart\ | |||
| (PID) Process: | (5688) Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Atomic Heart_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: Atomic Heart | |||
| (PID) Process: | (5688) Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Atomic Heart_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (5688) Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Atomic Heart_is1 |
| Operation: | write | Name: | Inno Setup: Setup Type |
Value: full | |||
| (PID) Process: | (5688) Setup.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Atomic Heart_is1 |
| Operation: | write | Name: | Inno Setup: Selected Components |
Value: | |||
Executable files
22
Suspicious files
3
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5688 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-CJIJ4.tmp\ISDone.dll | executable | |
MD5:4FEAFA8B5E8CDB349125C8AF0AC43974 | SHA256:BB8A0245DCC5C10A1C7181BAD509B65959855009A8105863EF14F2BB5B38AC71 | |||
| 5688 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-CJIJ4.tmp\cls-srep_x64.exe | executable | |
MD5:87AE304A743949A832CC4F4FCD9A8D4E | SHA256:E60078EDA61791AED38399ABDA56A1B333922AFEE05BAD1D3B775A4C831507BE | |||
| 5688 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-CJIJ4.tmp\_isetup\_RegDLL.tmp | executable | |
MD5:0EE914C6F0BB93996C75941E1AD629C6 | SHA256:4DC09BAC0613590F1FAC8771D18AF5BE25A1E1CB8FDBF4031AA364F3057E74A2 | |||
| 5688 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-CJIJ4.tmp\_isetup\_setup64.tmp | executable | |
MD5:4FF75F505FDDCC6A9AE62216446205D9 | SHA256:A4C86FC4836AC728D7BD96E7915090FD59521A9E74F1D06EF8E5A47C8695FD81 | |||
| 5688 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-CJIJ4.tmp\cls-lolz_x86.exe | executable | |
MD5:7CBE7DB7FC9258B6A43551140C343BB3 | SHA256:6EA07AA4F5565AC289402ADE3B2E52BF8089AD6185E0ECF0E1F36CEA39C091A9 | |||
| 5688 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-CJIJ4.tmp\unarc.dll | executable | |
MD5:56A2BCECBD3CDDD6F4A35361BF4920D6 | SHA256:5FCFAC18758A12E0E717A5189F379922A32B5AC12F26491E638D70B54AE1DCAB | |||
| 5688 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-CJIJ4.tmp\cls-srep.dll | executable | |
MD5:9E1E200472D66356A4AE5D597B01DABC | SHA256:87DF573AC240E09EA4941E169FB2D15D5316A1B0E053446B8144E04B1154F061 | |||
| 5688 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-CJIJ4.tmp\arc.ini | text | |
MD5:8ABB2610F5AAF97F559CCB2D1019FCB3 | SHA256:5E6117B8833BDD412048530B3684971D4597623561756279733CFA4652EB093F | |||
| 5688 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-CJIJ4.tmp\cls-bpk.dll | executable | |
MD5:D31067A2843518379A3166D031BE68E5 | SHA256:20C1C8F1A70470E18C898D35136FCADE1FA1CABDD069C564415DEBFD1A26C403 | |||
| 5688 | Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-CJIJ4.tmp\cls-lolz_x64.exe | executable | |
MD5:7234C4334A7523B1AC6F51C072497071 | SHA256:D92F7C60256509F74E36D9B5AAB041FE44999B1A3910D70AA83C9D01F062EA29 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
43
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5272 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5728 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1816 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6604 | _iu14D2N.tmp | GET | 200 | 188.114.96.3:80 | http://update-repack.info/games/OpenRePackSite.txt | unknown | — | — | whitelisted |
6604 | _iu14D2N.tmp | GET | 200 | 188.114.96.3:80 | http://update-repack.info/games/id/StartUpdate.txt | unknown | — | — | whitelisted |
6604 | _iu14D2N.tmp | GET | 200 | 188.114.96.3:80 | http://update-repack.info/games/id/EndUpdate.txt | unknown | — | — | whitelisted |
6604 | _iu14D2N.tmp | GET | 200 | 188.114.96.3:80 | http://update-repack.info/games/check.txt | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6012 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3488 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4516 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 184.86.251.9:443 | — | Akamai International B.V. | DE | unknown |
4204 | svchost.exe | 4.208.221.206:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
4516 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6720 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |