| URL: | http://89.248.165.207 |
| Full analysis: | https://app.any.run/tasks/55c1aa3f-08b2-42f0-adfb-c8c84021f7f4 |
| Verdict: | Malicious activity |
| Analysis date: | June 27, 2022, 07:41:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | AF8356E8B55EBFC71CDB7037004D6906 |
| SHA1: | 4D5050E652124D8722B1CFC6EECA8B1B9D202E09 |
| SHA256: | 7CB2C0AADB2F3895671481784DB509A38440FCC07052D3F360401291B2988AB2 |
| SSDEEP: | 3:N1K/fU7:CXU7 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3360)
INFO
Application launched itself
- iexplore.exe (PID: 2952)
Changes internet zones settings
- iexplore.exe (PID: 2952)
Checks supported languages
- iexplore.exe (PID: 2952)
- iexplore.exe (PID: 3360)
Reads the computer name
- iexplore.exe (PID: 2952)
- iexplore.exe (PID: 3360)
Reads internet explorer settings
- iexplore.exe (PID: 3360)
Checks Windows Trust Settings
- iexplore.exe (PID: 3360)
- iexplore.exe (PID: 2952)
Reads settings of System Certificates
- iexplore.exe (PID: 3360)
- iexplore.exe (PID: 2952)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2952 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://89.248.165.207" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3360 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2952 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
12 177
Read events
12 066
Write events
111
Delete events
0
Modification events
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30968313 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30968313 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2952) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
10
Text files
30
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3360 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\info[1].htm | html | |
MD5:— | SHA256:— | |||
| 3360 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\6HMN2EP3.htm | text | |
MD5:FDA44910DEB1A460BE4AC5D56D61D837 | SHA256:933B971C6388D594A23FA1559825DB5BEC8ADE2DB1240AA8FC9D0C684949E8C9 | |||
| 3360 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\popper.min[1].js | text | |
MD5:940017F4A5906E1E6783DE73D8322038 | SHA256:FE3DC4C4826441004AE9788FC603B1A1B387E1D9FAFEE000EAB4BBB8159E554C | |||
| 3360 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\bootstrap.min[1].js | text | |
MD5:14D449EB8876FA55E1EF3C2CC52B0C17 | SHA256:E7ED36CEEE5450B4243BBC35188AFABDFB4280C7C57597001DE0ED167299B01B | |||
| 3360 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\extras[1].css | text | |
MD5:21036554D3EA3CBF3043006437A6AE25 | SHA256:EC6ADB047379B86AAF7E403D5214BA1D85BF8FBA912D921714DD3DB29779EB26 | |||
| 3360 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\slicknav[1].css | text | |
MD5:5F7827BC33AB7C4E38A3EC55C503D6CB | SHA256:E89CCED242D493F2A2871748D51D810C03D8E4DFD2A70B6A32D329A8BADA4E7B | |||
| 3360 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\owl.carousel[1].css | text | |
MD5:061D0708E0A0AD9550C13FDDB8D1A4ED | SHA256:1520498F29FDA7E4EEB3A913B4BFE38D71784E2629267544B27300B9FE60D5BF | |||
| 3360 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\owl.theme[1].css | text | |
MD5:F23CF727E4FCCA9A5470658DA5E755C9 | SHA256:91EE720F3C25EC6B209D88019C20E2592340FF1FE1C94F3D5431E5FD1E77E5DC | |||
| 3360 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\jquery.mixitup[1].js | text | |
MD5:BEC025347C983564A795E075222CC054 | SHA256:CB98E531576E1A8CEC189CD2E94AF39CC28932F270CC515E2C07CB8FAD6FB68D | |||
| 3360 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\jquery-min[1].js | text | |
MD5:F9C7AFD05729F10F55B689F36BB20172 | SHA256:F16AB224BB962910558715C82F58C10C3ED20F153DDFAA199029F141B5B0255C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
32
TCP/UDP connections
38
DNS requests
11
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3360 | iexplore.exe | GET | 301 | 89.248.165.207:80 | http://89.248.165.207/ | SC | — | — | suspicious |
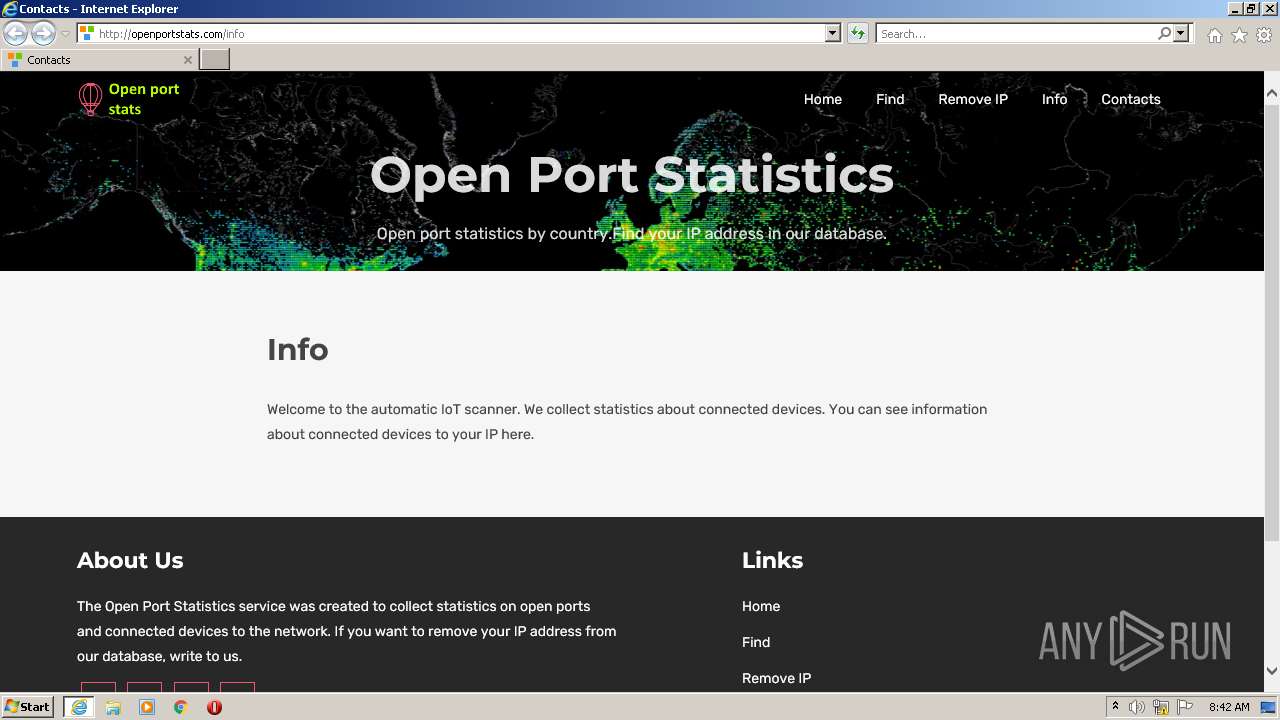
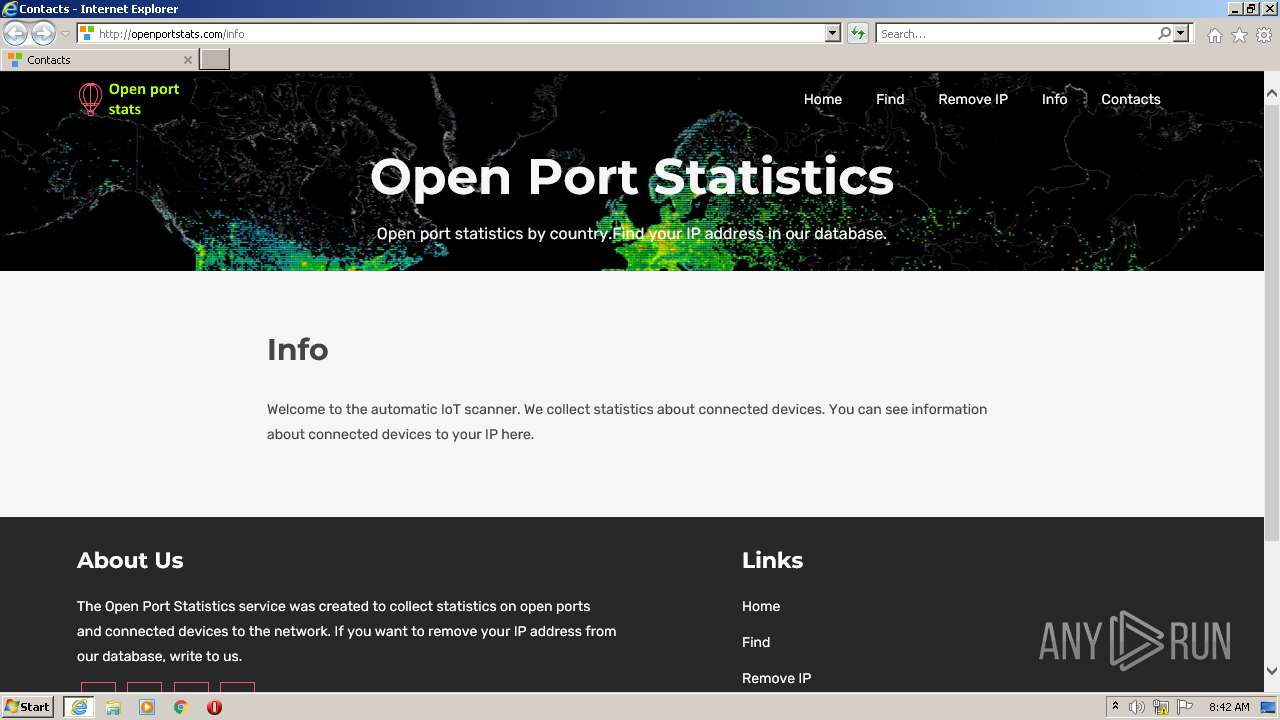
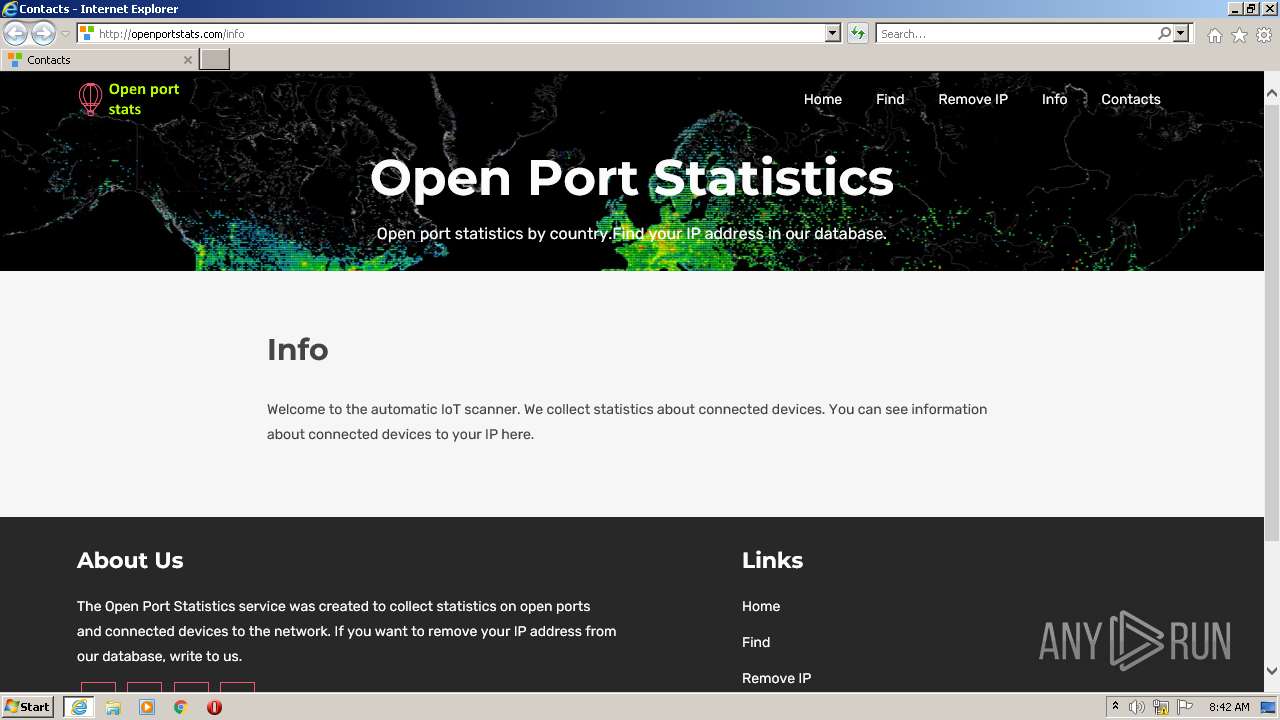
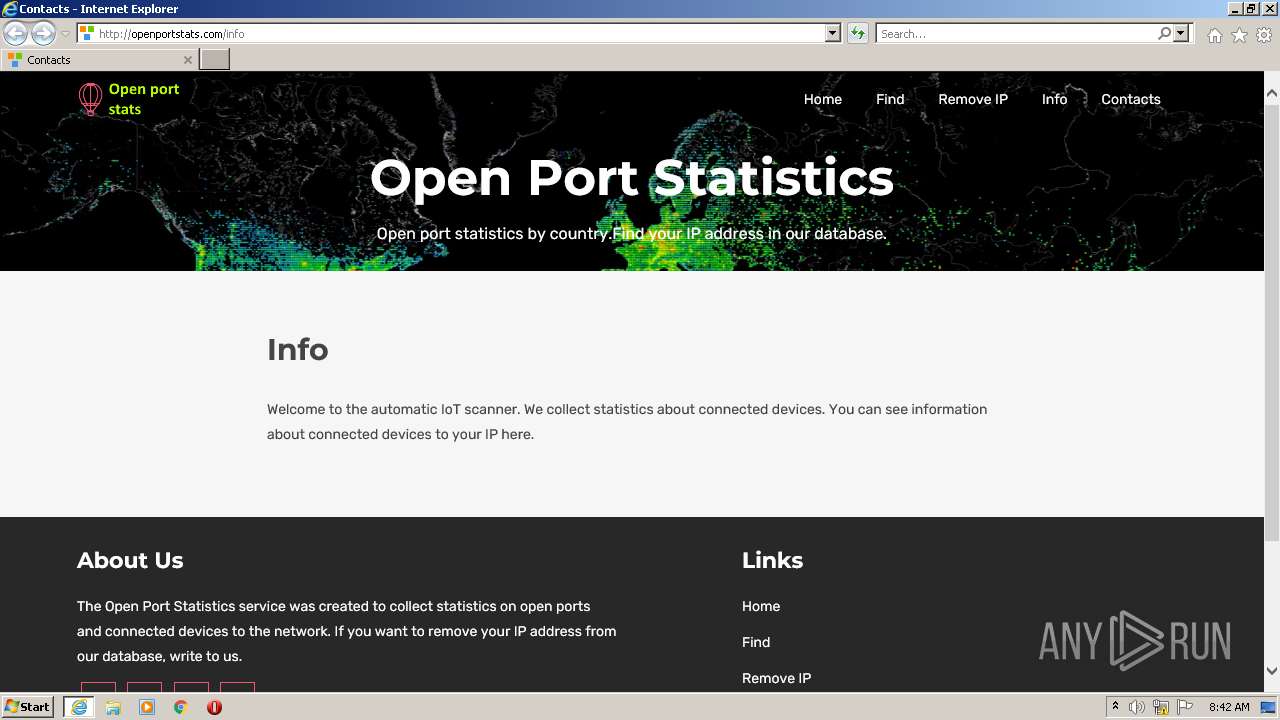
3360 | iexplore.exe | GET | 200 | 51.159.21.96:80 | http://openportstats.com/info | GB | html | 2.40 Kb | malicious |
3360 | iexplore.exe | GET | 200 | 51.159.21.96:80 | http://openportstats.com/js/bootstrap.min.js | GB | text | 47.8 Kb | malicious |
3360 | iexplore.exe | GET | 200 | 51.159.21.96:80 | http://openportstats.com/css/owl.carousel.css | GB | text | 3.30 Kb | malicious |
3360 | iexplore.exe | GET | 200 | 51.159.21.96:80 | http://openportstats.com/js/popper.min.js | GB | text | 18.5 Kb | malicious |
3360 | iexplore.exe | GET | 200 | 51.159.21.96:80 | http://openportstats.com/css/owl.theme.css | GB | text | 1.63 Kb | malicious |
3360 | iexplore.exe | GET | 200 | 51.159.21.96:80 | http://openportstats.com/js/jquery-min.js | GB | text | 82.3 Kb | malicious |
3360 | iexplore.exe | GET | 200 | 51.159.21.96:80 | http://openportstats.com/js/jquery.slicknav.js | GB | text | 16.3 Kb | malicious |
3360 | iexplore.exe | GET | 200 | 51.159.21.96:80 | http://openportstats.com/js/jquery.mixitup.js | GB | text | 49.7 Kb | malicious |
3360 | iexplore.exe | GET | 200 | 51.159.21.96:80 | http://openportstats.com/js/owl.carousel.min.js | GB | text | 14.5 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3360 | iexplore.exe | 89.248.165.207:80 | — | Quasi Networks LTD. | SC | suspicious |
3360 | iexplore.exe | 51.159.21.96:80 | openportstats.com | — | GB | unknown |
3360 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
3360 | iexplore.exe | 142.251.36.42:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2952 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3360 | iexplore.exe | 142.250.185.67:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2952 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3360 | iexplore.exe | 142.250.186.67:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
— | — | 51.159.21.96:80 | openportstats.com | — | GB | unknown |
2952 | iexplore.exe | 51.159.21.96:80 | openportstats.com | — | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
openportstats.com |
| malicious |
fonts.googleapis.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3360 | iexplore.exe | Misc Attack | ET DROP Dshield Block Listed Source group 1 |