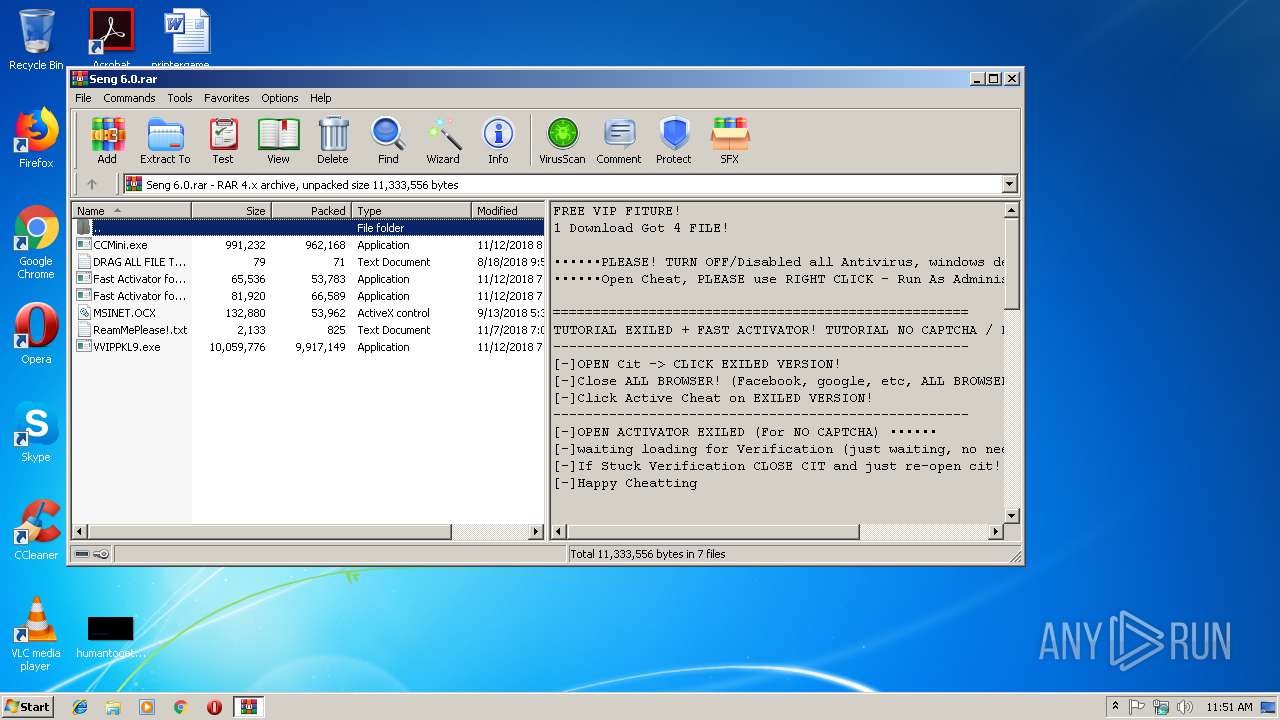
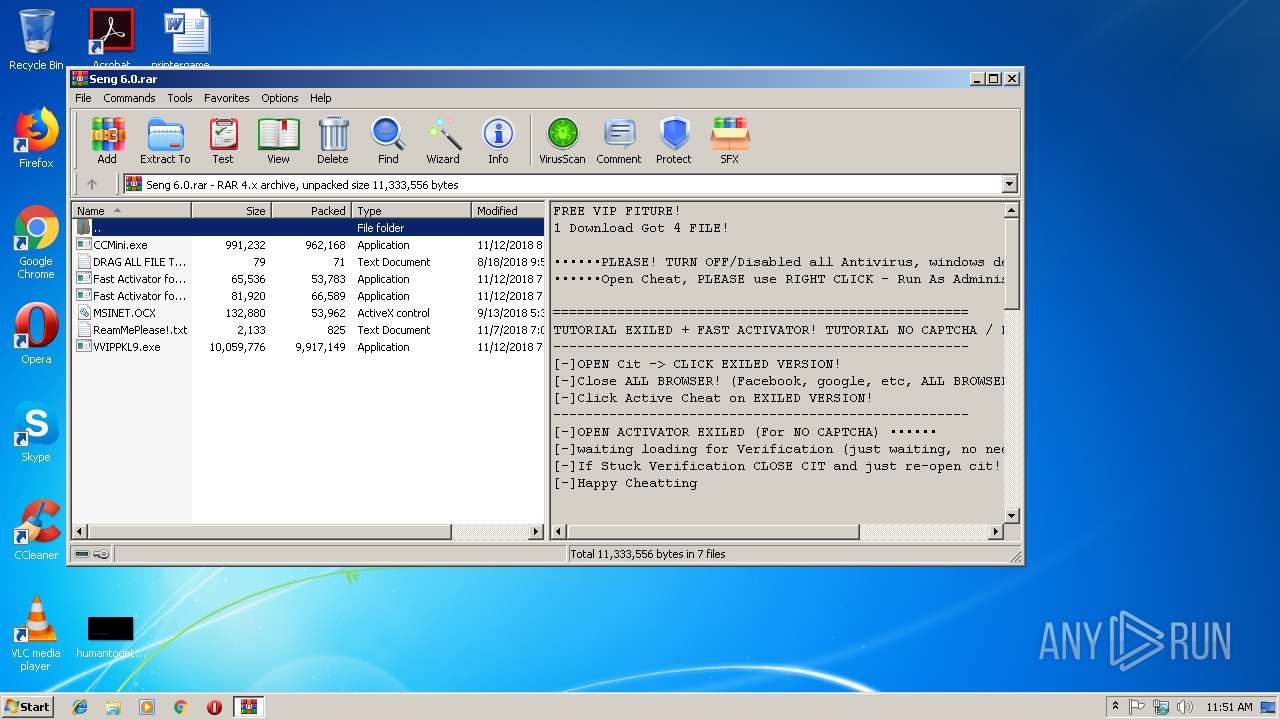
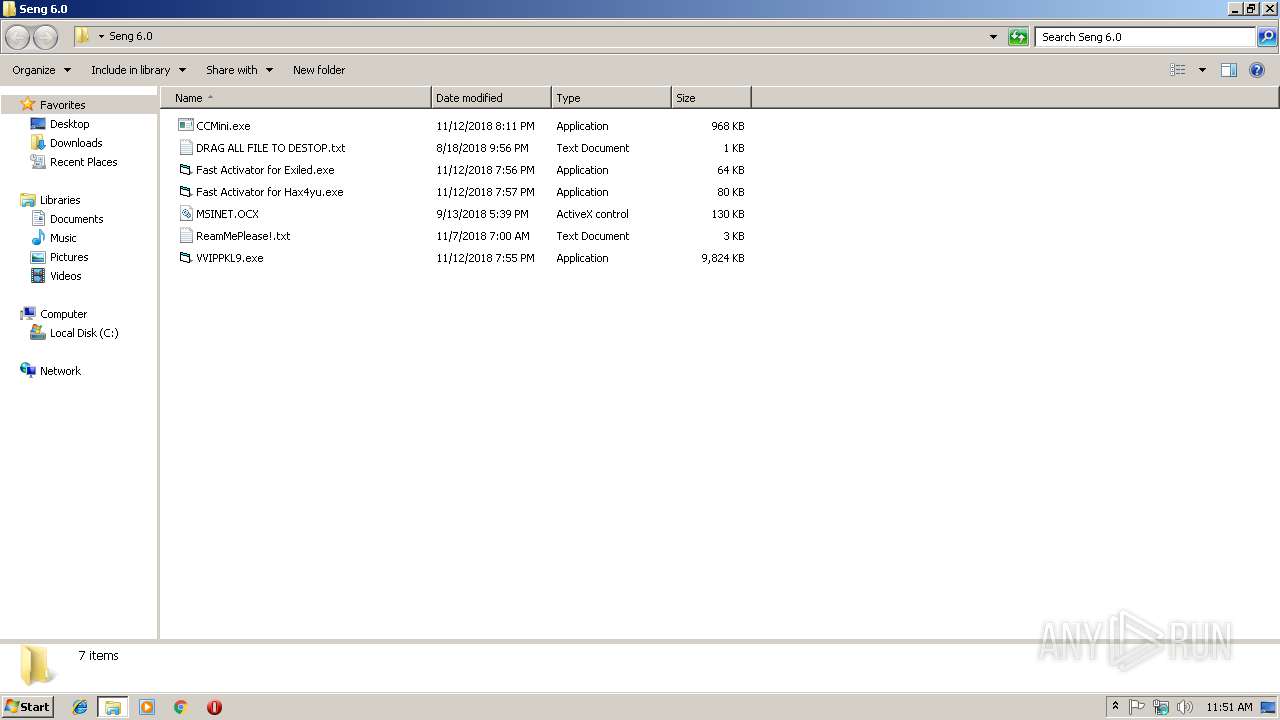
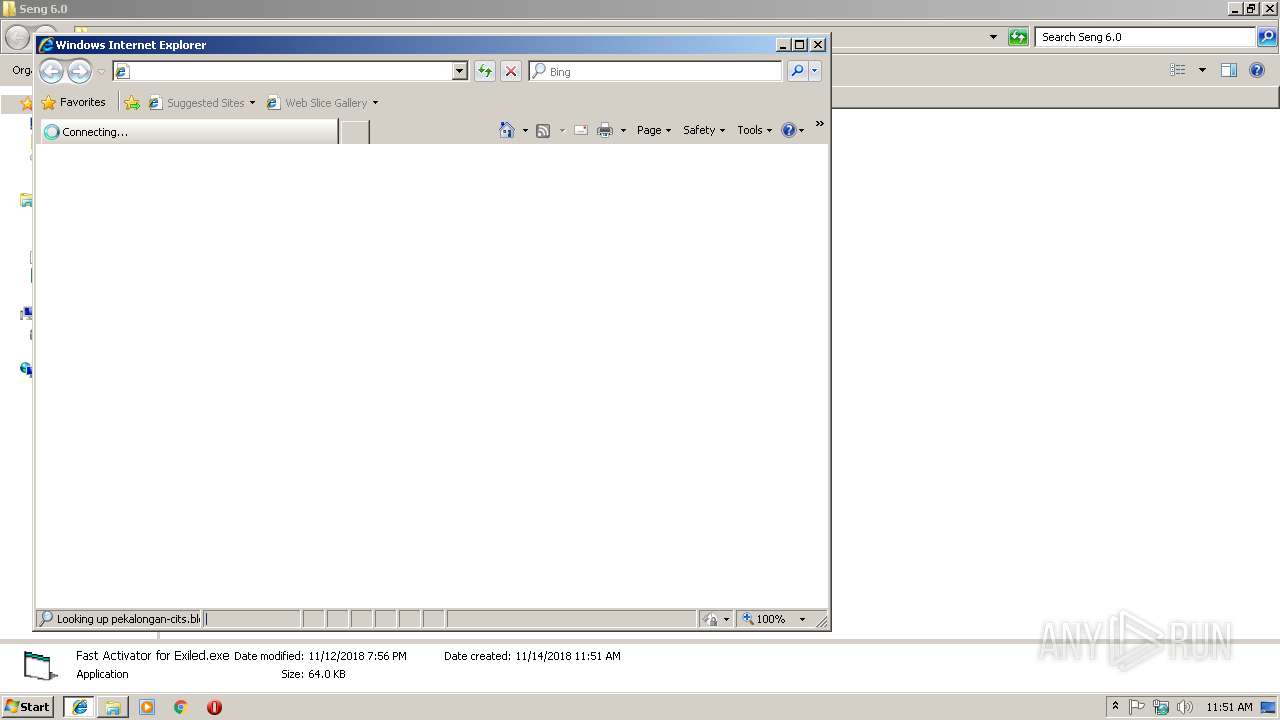
| File name: | Seng 6.0.rar |
| Full analysis: | https://app.any.run/tasks/a7619aca-95f9-450a-aea7-9f1d0dd21c58 |
| Verdict: | Malicious activity |
| Analysis date: | November 14, 2018, 11:50:59 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | BBF98295073BC535E69644524DCFEB9B |
| SHA1: | 9A5C57C614F259EC7FA2C5FFAE415EFAD0687373 |
| SHA256: | 7C775436928A8731AA372B9B627CF6BF88DB7C1323892D670A190A2E08EA351B |
| SSDEEP: | 196608:/5/OY0vfOwmQ4+cZE8rVYt120TDAx1QzFAjAScOSqXRusPux4EzKb/:5OYqOwyRXSt120DuyOjASceIzg |
MALICIOUS
Application was dropped or rewritten from another process
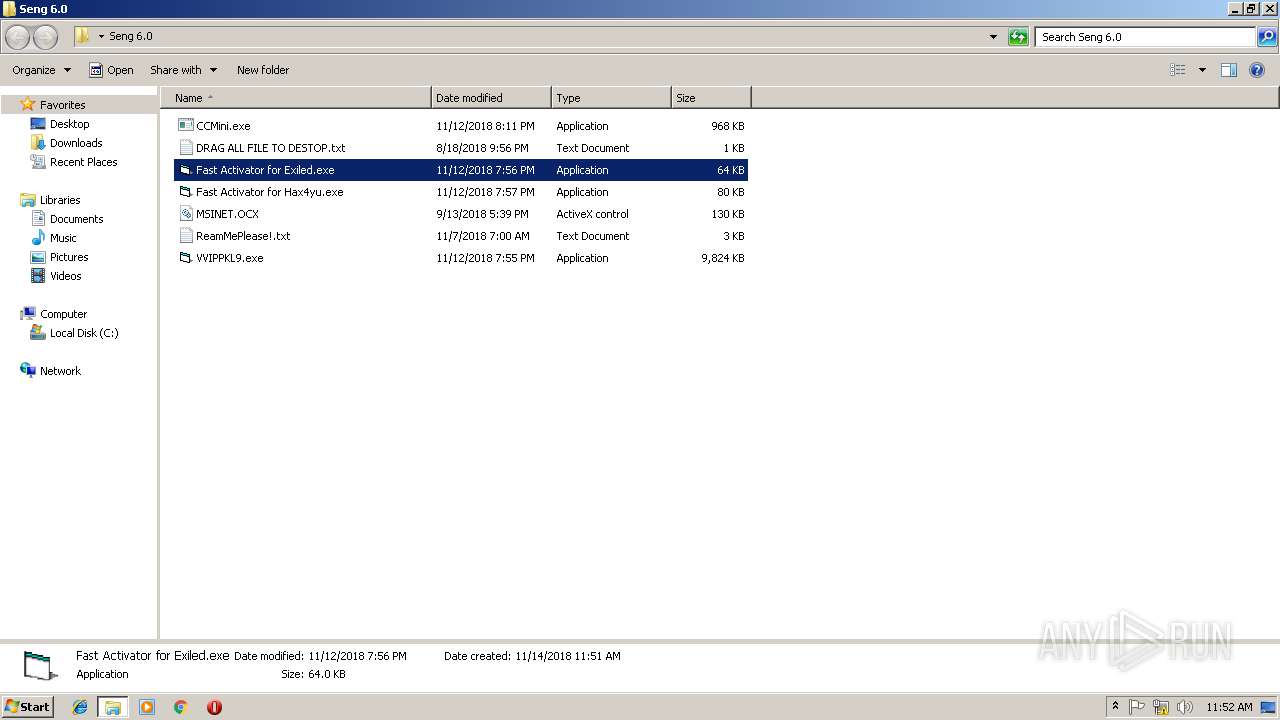
- Fast Activator for Exiled.exe (PID: 2836)
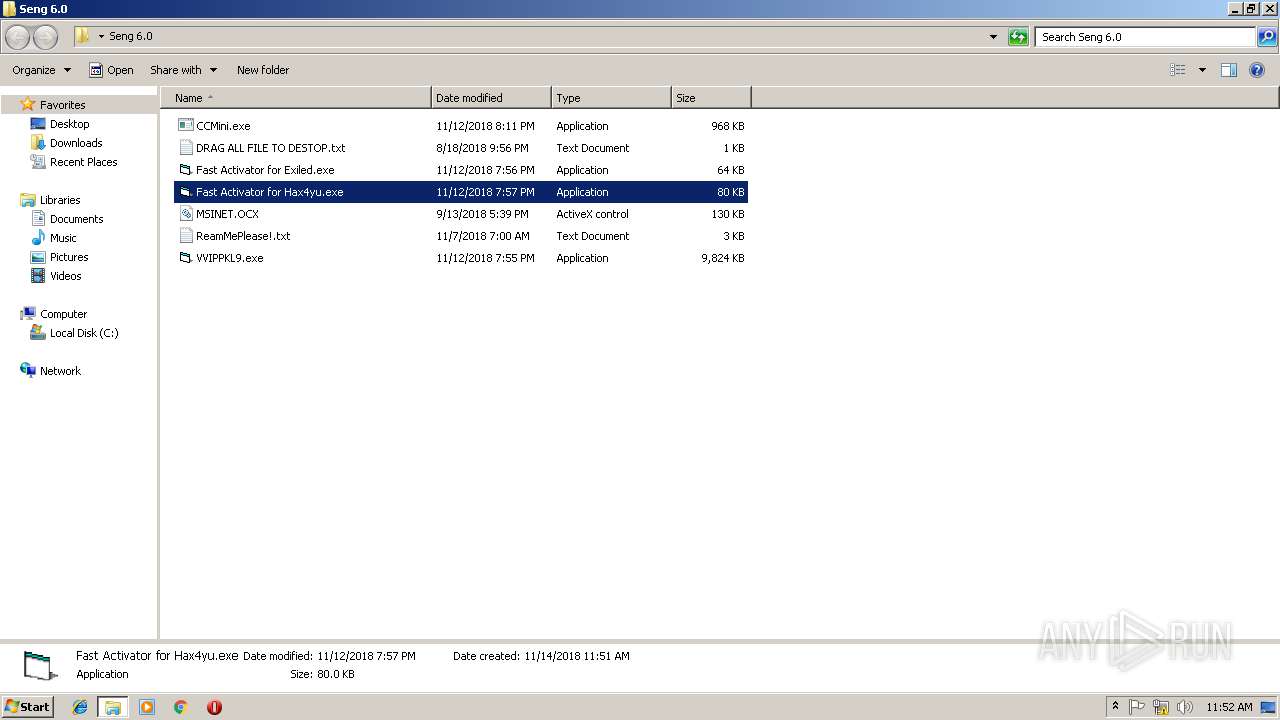
- Fast Activator for Hax4yu.exe (PID: 3876)
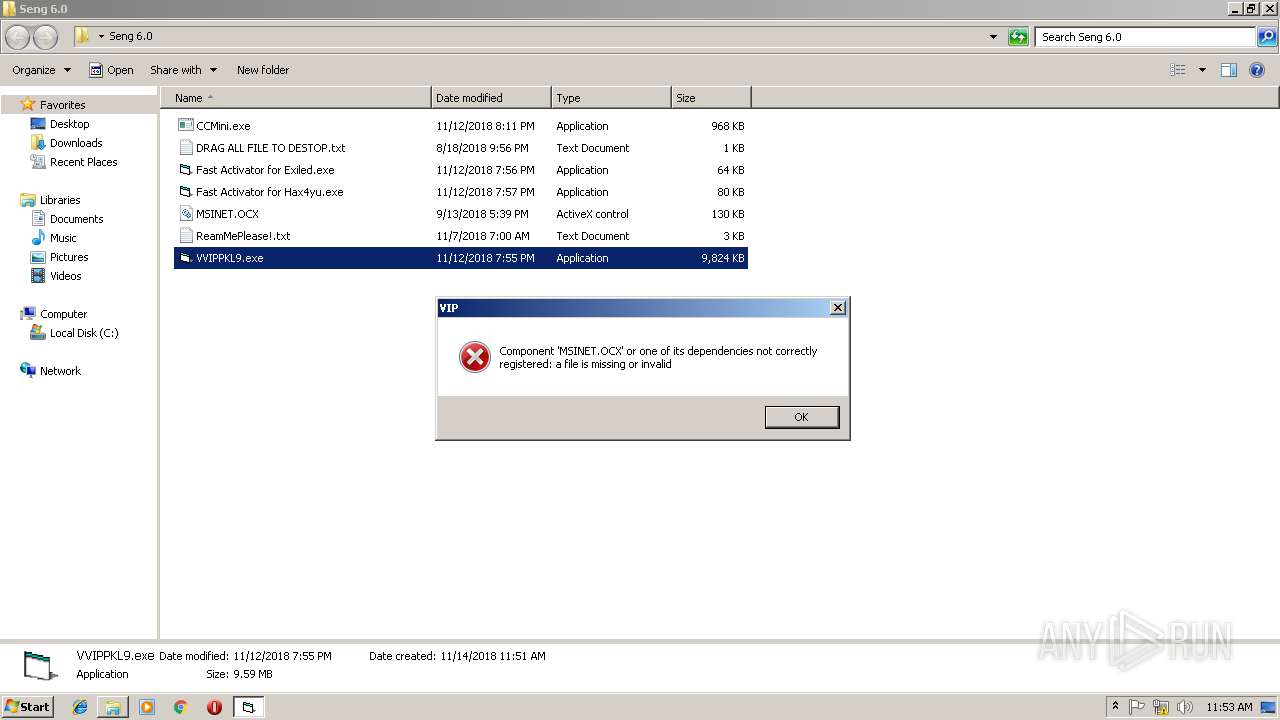
- VVIPPKL9.exe (PID: 3304)
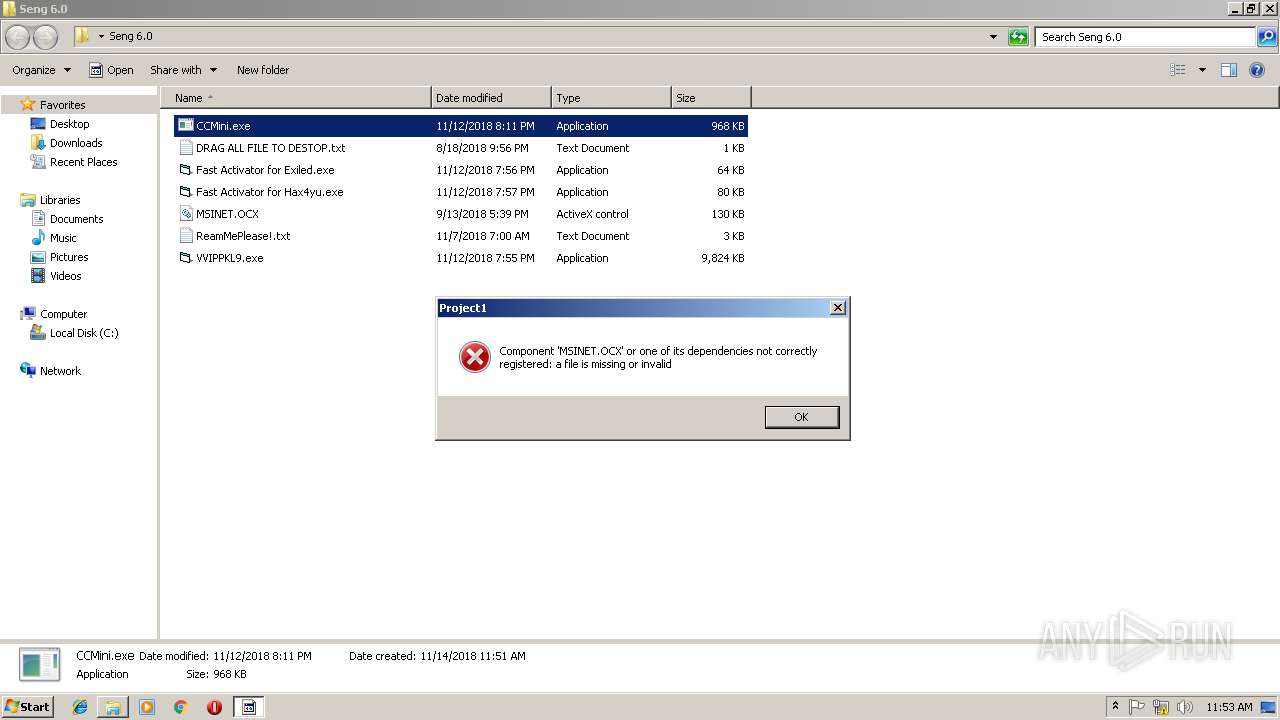
- CCMini.exe (PID: 4056)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1860)
- explorer.exe (PID: 1772)
- VVIPPKL9.exe (PID: 3304)
- CCMini.exe (PID: 4056)
SUSPICIOUS
Creates files in the user directory
- explorer.exe (PID: 1772)
Reads Internet Cache Settings
- explorer.exe (PID: 1772)
Starts Internet Explorer
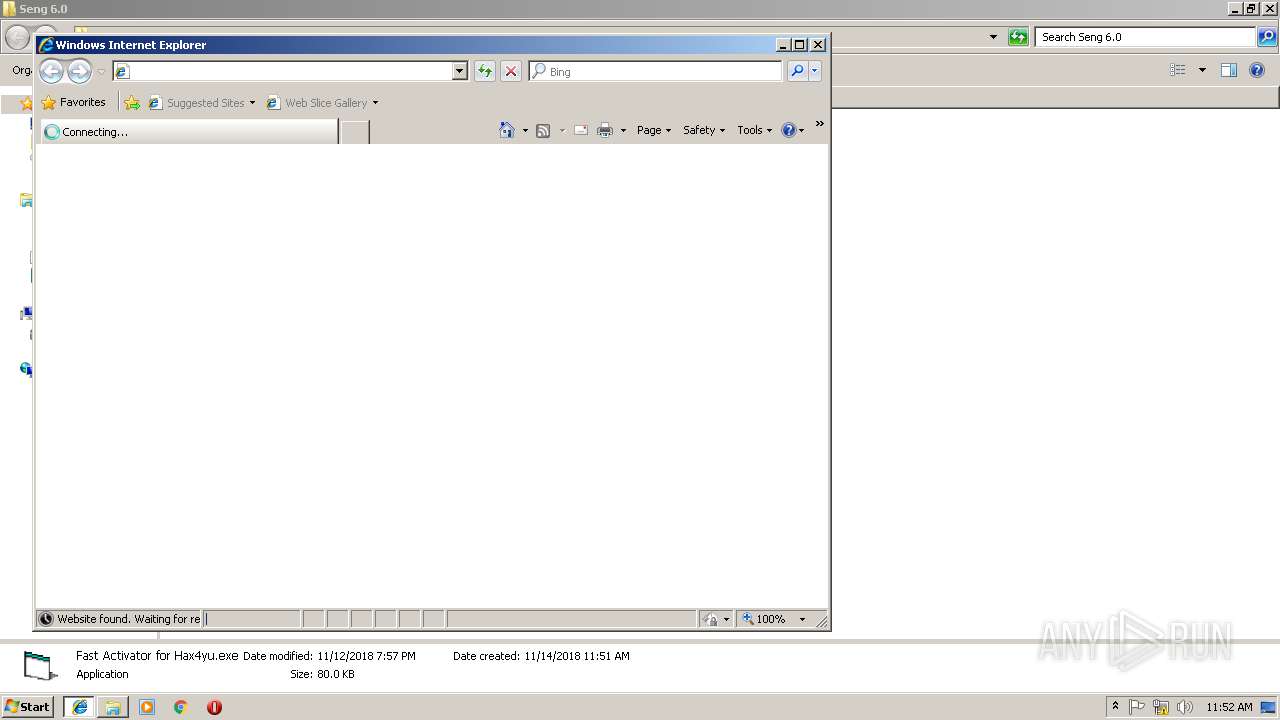
- Fast Activator for Hax4yu.exe (PID: 3876)
- Fast Activator for Exiled.exe (PID: 2836)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2664)
Uses RUNDLL32.EXE to load library
- explorer.exe (PID: 1772)
INFO
Reads internet explorer settings
- iexplore.exe (PID: 1728)
- iexplore.exe (PID: 3056)
Reads Internet Cache Settings
- iexplore.exe (PID: 1728)
- iexplore.exe (PID: 3056)
Creates files in the user directory
- iexplore.exe (PID: 1728)
- iexplore.exe (PID: 3056)
Changes internet zones settings
- iexplore.exe (PID: 4032)
- iexplore.exe (PID: 1264)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 124 |
|---|---|
| UncompressedSize: | 79 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2018:08:18 21:56:25 |
| PackingMethod: | Normal |
| ArchivedFileName: | DRAG ALL FILE TO DESTOP.txt |
Total processes
48
Monitored processes
12
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1264 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | Fast Activator for Hax4yu.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1728 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:4032 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1772 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1860 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2664 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Seng 6.0.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2836 | "C:\Users\admin\Desktop\Seng 6.0\Fast Activator for Exiled.exe" | C:\Users\admin\Desktop\Seng 6.0\Fast Activator for Exiled.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 3056 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1264 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
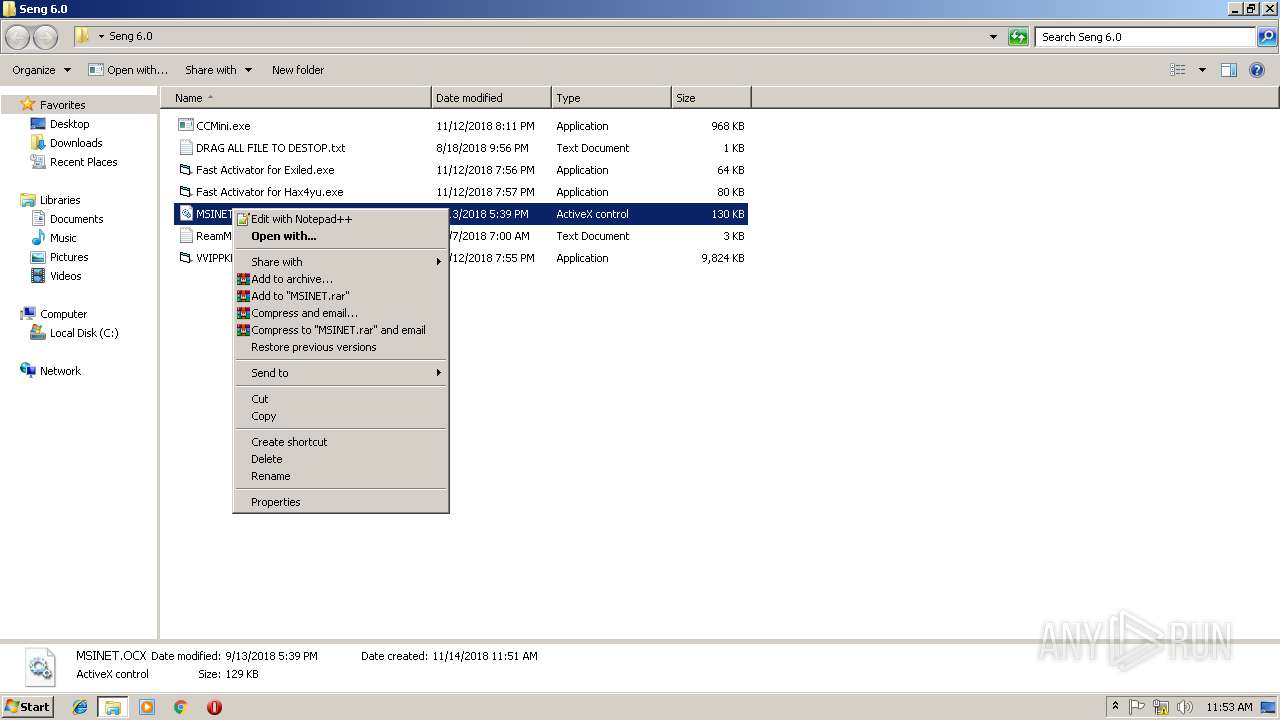
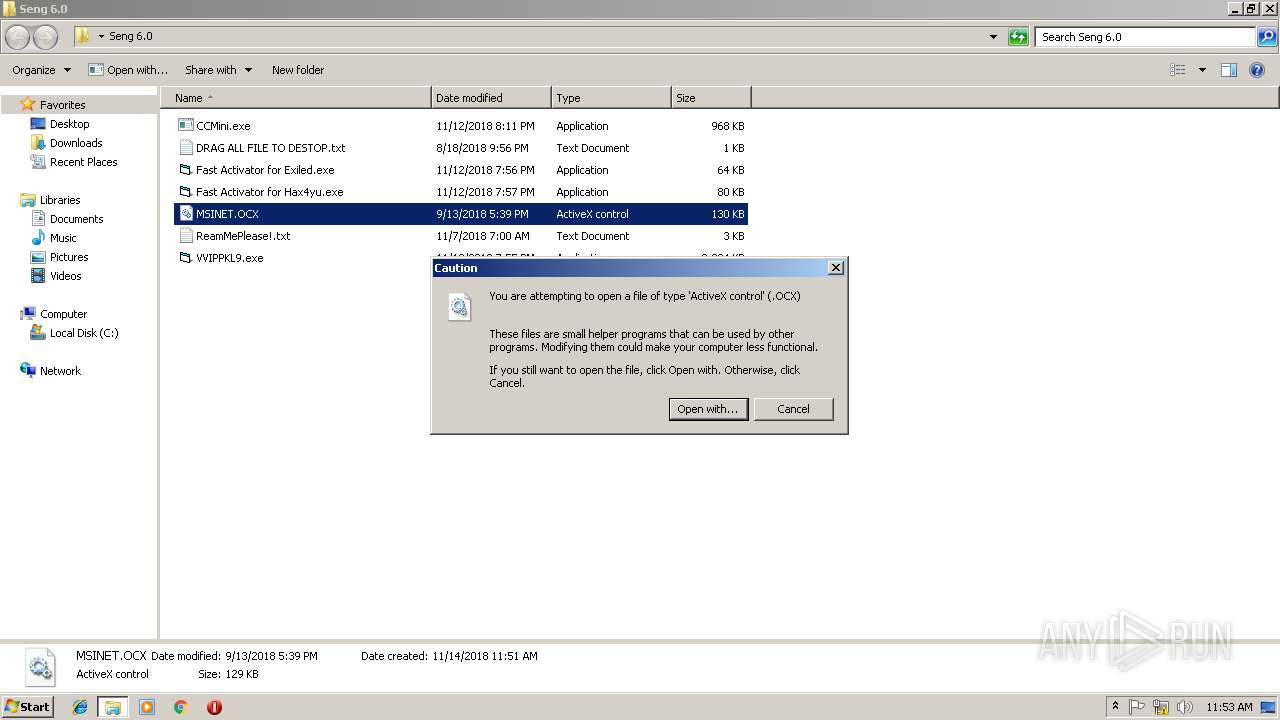
| 3284 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\Seng 6.0\MSINET.OCX | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3304 | "C:\Users\admin\Desktop\Seng 6.0\VVIPPKL9.exe" | C:\Users\admin\Desktop\Seng 6.0\VVIPPKL9.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 3876 | "C:\Users\admin\Desktop\Seng 6.0\Fast Activator for Hax4yu.exe" | C:\Users\admin\Desktop\Seng 6.0\Fast Activator for Hax4yu.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
Total events
3 657
Read events
3 422
Write events
231
Delete events
4
Modification events
| (PID) Process: | (1772) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB010000006821FD290F362A42A685E6961EA74BA8000000000200000000001066000000010000200000007700C3B06BD1BAA3CE2325E5AB0E9DEC0B35D607FD7178045894C2448400CE75000000000E80000000020000200000001088B2C06A213ACCE342FB8DEEB064B60840B328503040689B17AA126DB42D4830000000BCB10455A14F8DF52021970C7929A5EDAE299030CF15E50E9AD655064A4F08FA70C203E5EAA50BC0F75319177BB0A2614000000089559DA3F4F6098411E863FE39E987682A845895940198F7AD4E448A68B443FBD952D1428287681C9C45E6D4119E906B1C6B63B6772212A95FEBCA22650263A0 | |||
| (PID) Process: | (2664) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2664) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2664) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2664) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Seng 6.0.rar | |||
| (PID) Process: | (2664) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2664) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2664) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2664) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1772) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.rar\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
Executable files
5
Suspicious files
7
Text files
26
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4032 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 4032 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 1728 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@pushnest[1].txt | — | |
MD5:— | SHA256:— | |||
| 2664 | WinRAR.exe | C:\Users\admin\Desktop\Seng 6.0\VVIPPKL9.exe | executable | |
MD5:— | SHA256:— | |||
| 2664 | WinRAR.exe | C:\Users\admin\Desktop\Seng 6.0\CCMini.exe | executable | |
MD5:— | SHA256:— | |||
| 1772 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\History.IE5\MSHist012018111420181115\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2664 | WinRAR.exe | C:\Users\admin\Desktop\Seng 6.0\Fast Activator for Hax4yu.exe | executable | |
MD5:— | SHA256:— | |||
| 4032 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFDF0B97DEB450908A.TMP | — | |
MD5:— | SHA256:— | |||
| 2664 | WinRAR.exe | C:\Users\admin\Desktop\Seng 6.0\Fast Activator for Exiled.exe | executable | |
MD5:— | SHA256:— | |||
| 4032 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF270DD96DC81653E3.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
27
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4032 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
1264 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1728 | iexplore.exe | 188.72.202.170:443 | pushnest.com | Webzilla B.V. | NL | suspicious |
1728 | iexplore.exe | 188.72.202.222:443 | go.mobtrks.com | Webzilla B.V. | NL | unknown |
1728 | iexplore.exe | 172.217.19.201:443 | www.blogger.com | Google Inc. | US | whitelisted |
1728 | iexplore.exe | 209.197.3.15:443 | maxcdn.bootstrapcdn.com | Highwinds Network Group, Inc. | US | whitelisted |
1728 | iexplore.exe | 172.217.17.106:443 | firebasestorage.googleapis.com | Google Inc. | US | whitelisted |
1728 | iexplore.exe | 172.217.17.42:443 | ajax.googleapis.com | Google Inc. | US | whitelisted |
1728 | iexplore.exe | 213.196.2.1:443 | pl14317197.puserving.com | Servers.com, Inc. | NL | suspicious |
1264 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3056 | iexplore.exe | 172.217.19.201:443 | www.blogger.com | Google Inc. | US | whitelisted |
3056 | iexplore.exe | 209.197.3.15:443 | maxcdn.bootstrapcdn.com | Highwinds Network Group, Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
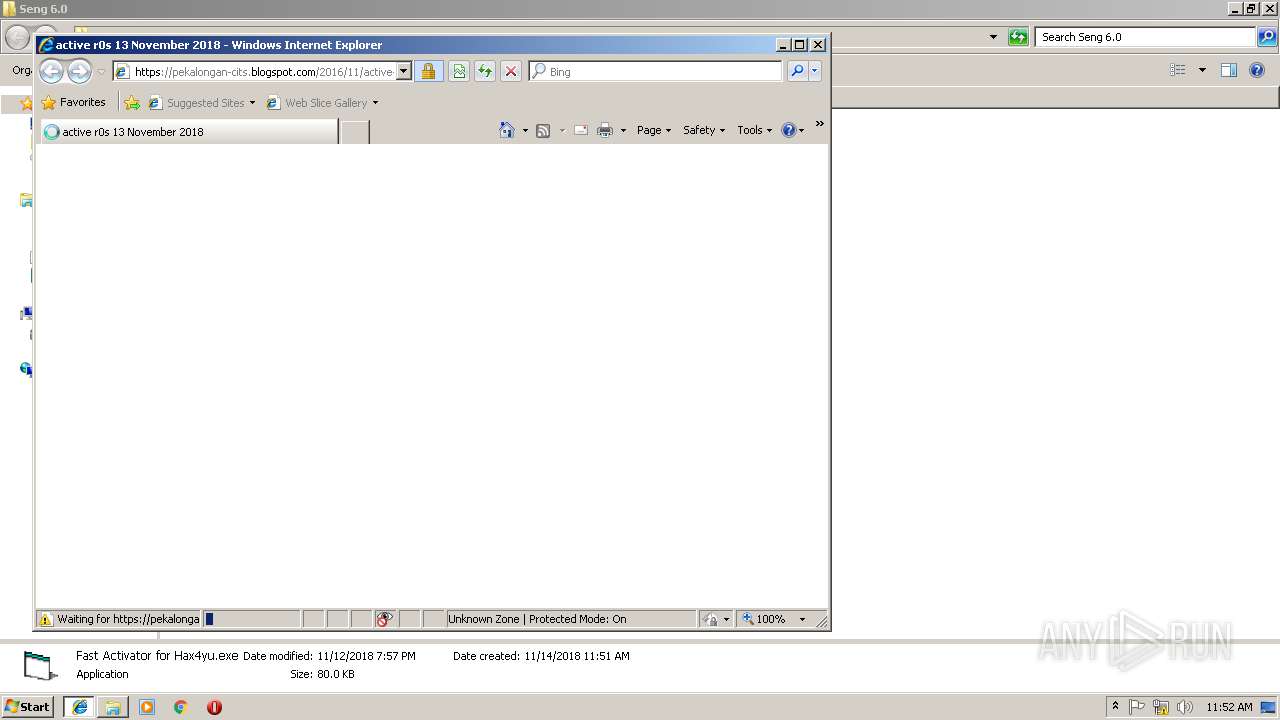
pekalongan-cits.blogspot.com |
| whitelisted |
pushnest.com |
| whitelisted |
go.mobtrks.com |
| malicious |
ajax.googleapis.com |
| whitelisted |
www.blogger.com |
| shared |
pl14317197.puserving.com |
| suspicious |
maxcdn.bootstrapcdn.com |
| whitelisted |
firebasestorage.googleapis.com |
| whitelisted |