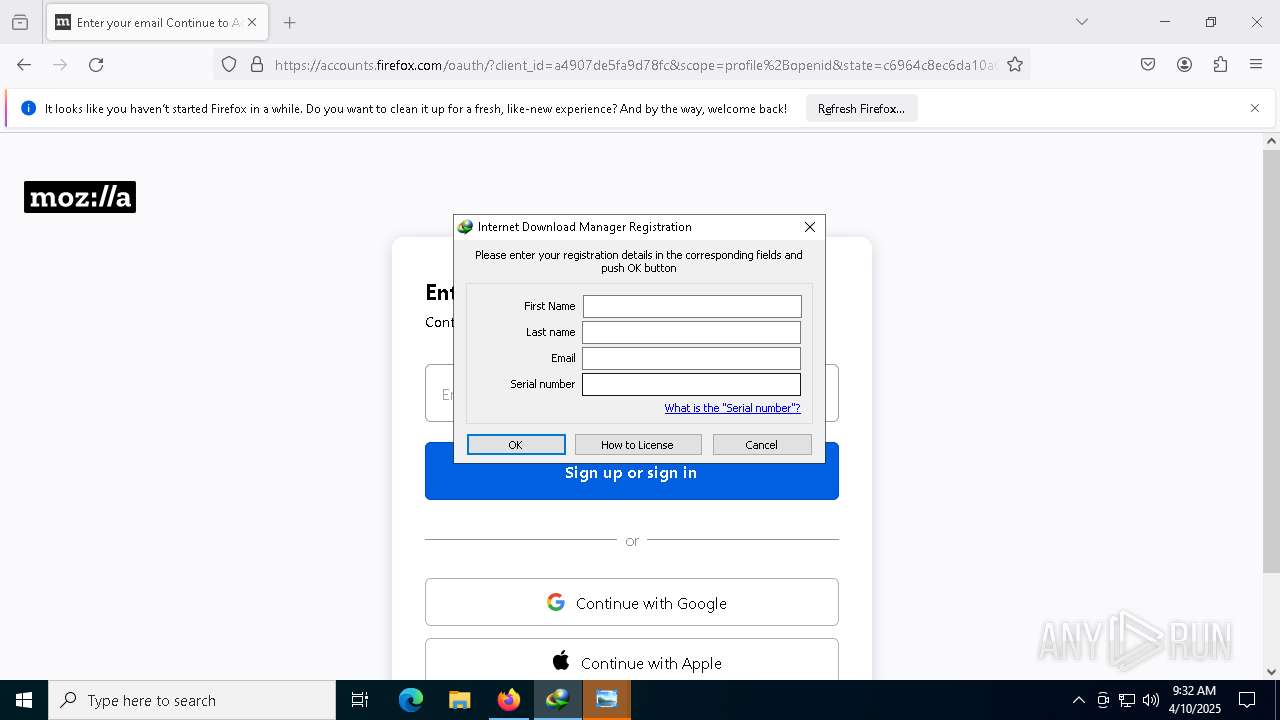
| File name: | idman642build32f.exe |
| Full analysis: | https://app.any.run/tasks/b7888f1e-a73b-4571-b7cc-bf6b36c48f77 |
| Verdict: | Malicious activity |
| Analysis date: | April 10, 2025, 09:30:25 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | D27C6C6E8BB840E05BFE9C89FDC1B3EF |
| SHA1: | 583B7CD447E3DC3F77BBCEDF517ADBC819DB155B |
| SHA256: | 7C617CD9EAE5FCE05FF30755A71A04458518C42E92899848E0A786236627FCA6 |
| SSDEEP: | 98304:78JZXlBGJ73REIxBfQtAOESn18u2KK8/3ju93w9RpqN2r5//MByyorDx+HDQ8i0U:l14nSsI8YOwz9JZjkb3djCek33SSGea |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- IDM1.tmp (PID: 5244)
- IDMan.exe (PID: 2384)
- Uninstall.exe (PID: 6592)
Changes the autorun value in the registry
- rundll32.exe (PID: 2064)
- IDMan.exe (PID: 2384)
Starts NET.EXE for service management
- Uninstall.exe (PID: 6592)
- net.exe (PID: 7920)
SUSPICIOUS
Starts application with an unusual extension
- idman642build32f.exe (PID: 2136)
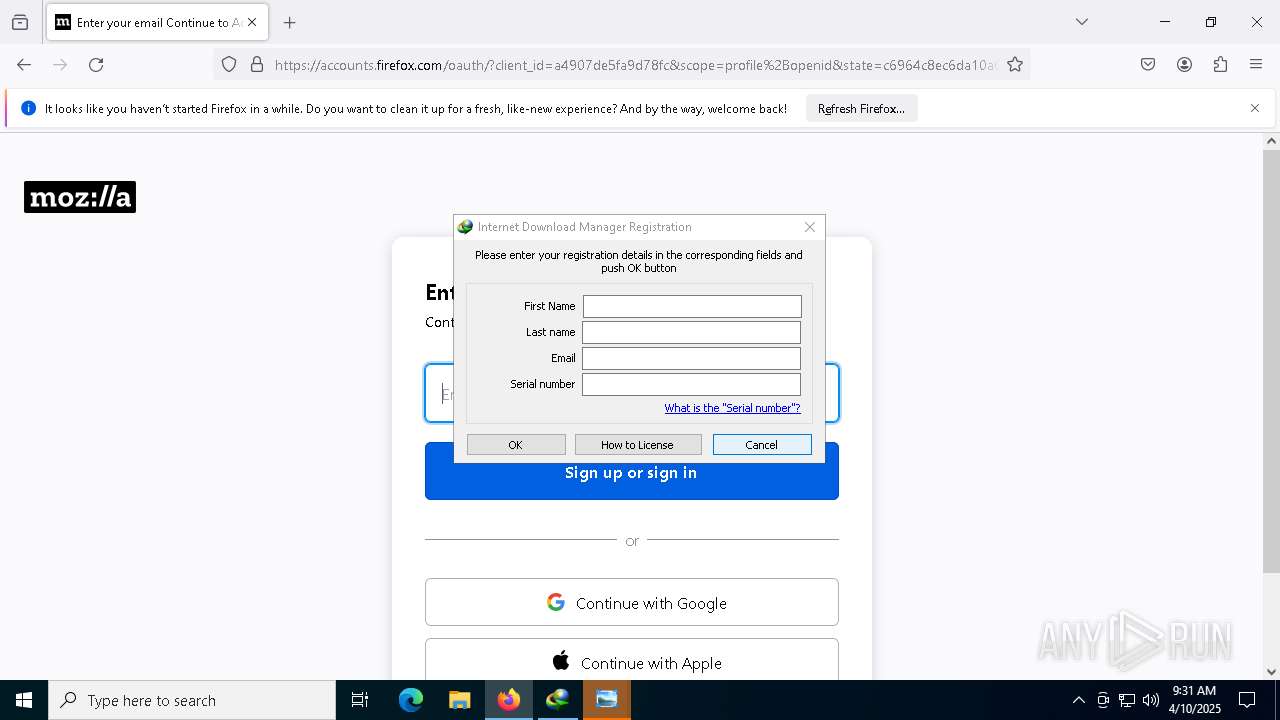
Creates a software uninstall entry
- IDM1.tmp (PID: 5244)
The process creates files with name similar to system file names
- IDM1.tmp (PID: 5244)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 4488)
- IDM1.tmp (PID: 5244)
- regsvr32.exe (PID: 4200)
- regsvr32.exe (PID: 6652)
- regsvr32.exe (PID: 2244)
- regsvr32.exe (PID: 5936)
- regsvr32.exe (PID: 6108)
- regsvr32.exe (PID: 5344)
- IDMan.exe (PID: 2384)
- regsvr32.exe (PID: 8028)
Reads security settings of Internet Explorer
- IDMan.exe (PID: 2384)
- IDM1.tmp (PID: 5244)
- Uninstall.exe (PID: 6592)
Executable content was dropped or overwritten
- IDMan.exe (PID: 2384)
- rundll32.exe (PID: 2064)
- drvinst.exe (PID: 5600)
Uses RUNDLL32.EXE to load library
- Uninstall.exe (PID: 6592)
Drops a system driver (possible attempt to evade defenses)
- rundll32.exe (PID: 2064)
- drvinst.exe (PID: 5600)
Creates files in the driver directory
- drvinst.exe (PID: 5600)
Creates or modifies Windows services
- drvinst.exe (PID: 7440)
- Uninstall.exe (PID: 6592)
INFO
The sample compiled with english language support
- idman642build32f.exe (PID: 2136)
- IDMan.exe (PID: 2384)
- rundll32.exe (PID: 2064)
- drvinst.exe (PID: 5600)
Checks supported languages
- IDM1.tmp (PID: 5244)
- idman642build32f.exe (PID: 2136)
- IDMan.exe (PID: 2384)
- idmBroker.exe (PID: 4436)
- Uninstall.exe (PID: 6592)
- drvinst.exe (PID: 5600)
- drvinst.exe (PID: 7440)
Reads the computer name
- idman642build32f.exe (PID: 2136)
- IDM1.tmp (PID: 5244)
- IDMan.exe (PID: 2384)
- idmBroker.exe (PID: 4436)
- Uninstall.exe (PID: 6592)
- drvinst.exe (PID: 5600)
- drvinst.exe (PID: 7440)
Create files in a temporary directory
- idman642build32f.exe (PID: 2136)
- IDM1.tmp (PID: 5244)
- IDMan.exe (PID: 2384)
- rundll32.exe (PID: 2064)
INTERNETDOWNLOADMANAGER mutex has been found
- IDM1.tmp (PID: 5244)
- IDMan.exe (PID: 2384)
Creates files in the program directory
- IDM1.tmp (PID: 5244)
- IDMan.exe (PID: 2384)
Creates files or folders in the user directory
- IDM1.tmp (PID: 5244)
- IDMan.exe (PID: 2384)
Disables trace logs
- IDMan.exe (PID: 2384)
Reads the machine GUID from the registry
- IDMan.exe (PID: 2384)
- drvinst.exe (PID: 5600)
Reads the software policy settings
- IDMan.exe (PID: 2384)
- drvinst.exe (PID: 5600)
- slui.exe (PID: 4724)
Process checks computer location settings
- IDM1.tmp (PID: 5244)
- IDMan.exe (PID: 2384)
- Uninstall.exe (PID: 6592)
Application launched itself
- firefox.exe (PID: 6584)
- firefox.exe (PID: 5204)
Manual execution by a user
- firefox.exe (PID: 6584)
- OpenWith.exe (PID: 7904)
- OpenWith.exe (PID: 8068)
- wscript.exe (PID: 7444)
- rundll32.exe (PID: 5400)
- rundll32.exe (PID: 7920)
- rundll32.exe (PID: 1600)
- OpenWith.exe (PID: 1040)
- rundll32.exe (PID: 4056)
Checks proxy server information
- IDMan.exe (PID: 2384)
Reads the time zone
- runonce.exe (PID: 7700)
Reads security settings of Internet Explorer
- runonce.exe (PID: 7700)
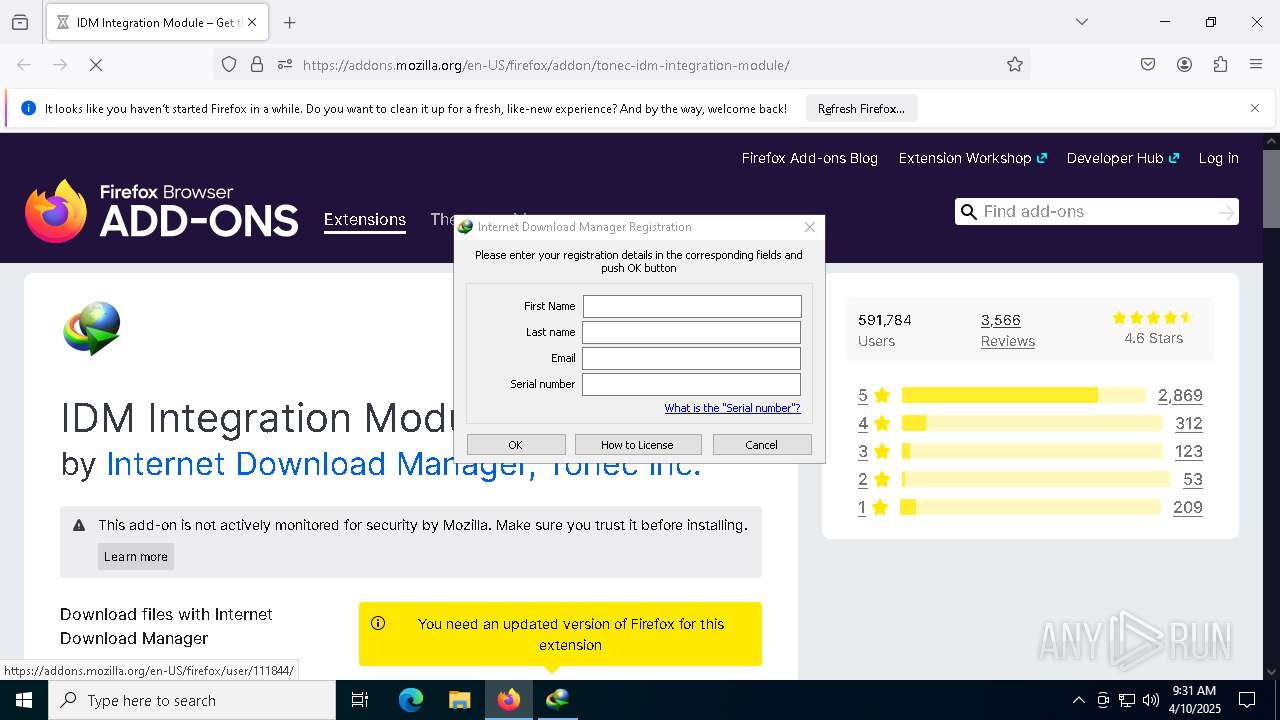
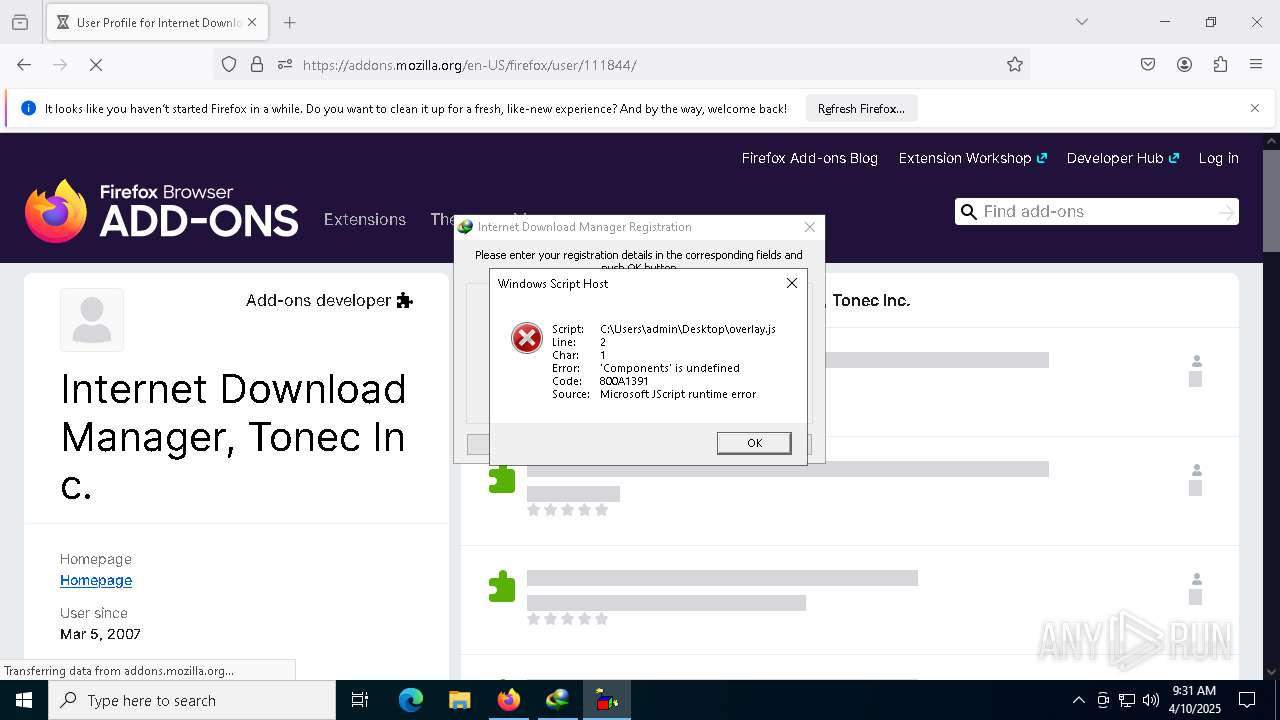
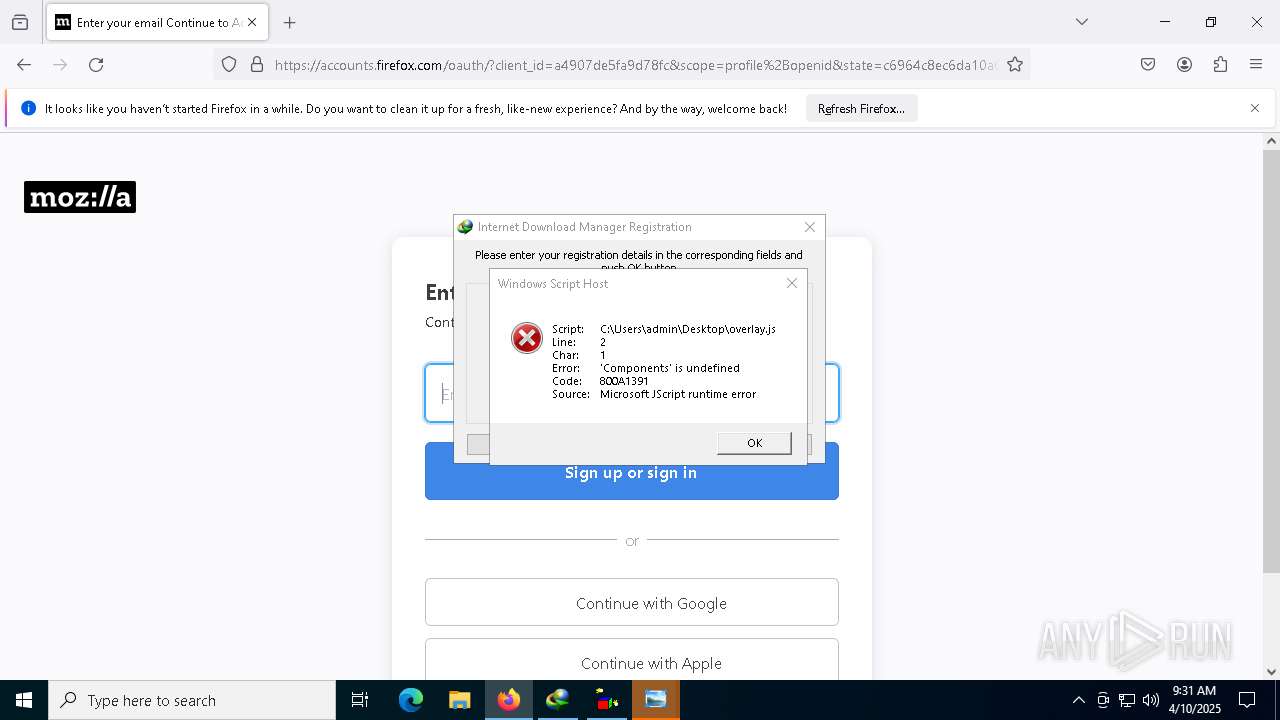
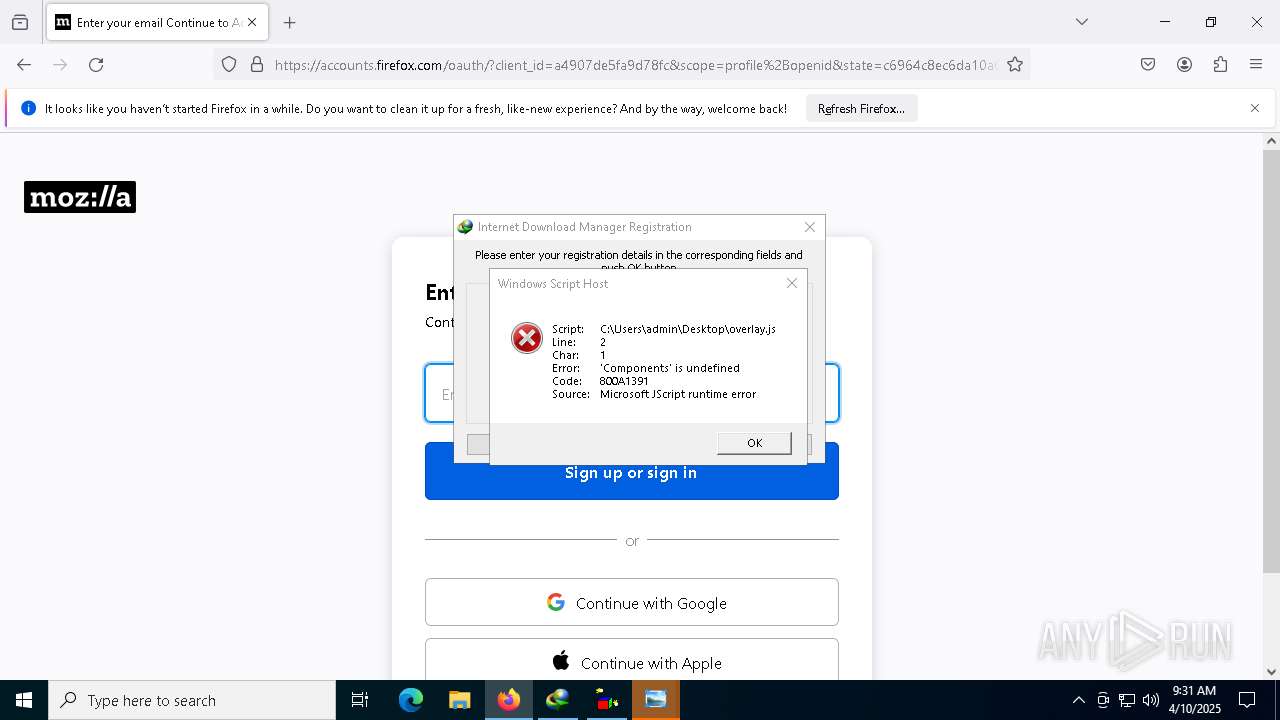
JScript runtime error (SCRIPT)
- wscript.exe (PID: 7444)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 7904)
- OpenWith.exe (PID: 8068)
- OpenWith.exe (PID: 1040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:04:04 16:03:46+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 47104 |
| InitializedDataSize: | 51200 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5b7a |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.42.32.1 |
| ProductVersionNumber: | 6.42.32.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | Please visit http://www.internetdownloadmanager.com |
| CompanyName: | Tonec Inc. |
| FileDescription: | Internet Download Manager installer |
| FileVersion: | 6, 42, 32, 1 |
| InternalName: | installer |
| LegalCopyright: | © 1999-2025. Tonec FZE. All rights reserved. |
| LegalTrademarks: | Internet Download Manager (IDM) |
| OriginalFileName: | installer.exe |
| ProductName: | Internet Download Manager installer |
| ProductVersion: | 6, 42, 32, 1 |
Total processes
188
Monitored processes
54
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 684 | "C:\Program Files\Mozilla Firefox\firefox.exe" https://www.internetdownloadmanager.com/support/installffextfrommozillasite.html | C:\Program Files\Mozilla Firefox\firefox.exe | — | IDMan.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: HIGH Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 732 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1912 -parentBuildID 20240213221259 -prefsHandle 1840 -prefMapHandle 1832 -prefsLen 31031 -prefMapSize 244583 -appDir "C:\Program Files\Mozilla Firefox\browser" - {8a08efbf-c5e5-4f2e-a8a0-a9a924103964} 5204 "\\.\pipe\gecko-crash-server-pipe.5204" 17b17fef910 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 780 | "C:\Windows\System32\regsvr32.exe" /s "C:\Program Files (x86)\Internet Download Manager\downlWithIDM64.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | IDM1.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | "C:\Windows\System32\regsvr32.exe" /s "C:\Program Files (x86)\Internet Download Manager\IDMGetAll64.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | IDM1.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1040 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\overlay.xul | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1280 | "C:\Users\admin\AppData\Local\Temp\idman642build32f.exe" | C:\Users\admin\AppData\Local\Temp\idman642build32f.exe | — | explorer.exe | |||||||||||
User: admin Company: Tonec Inc. Integrity Level: MEDIUM Description: Internet Download Manager installer Exit code: 3221226540 Version: 6, 42, 32, 1 Modules
| |||||||||||||||
| 1600 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\Desktop\dwnlAll.png | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2064 | "C:\WINDOWS\Sysnative\RUNDLL32.EXE" SETUPAPI.DLL,InstallHinfSection DefaultInstall 128 C:\Program Files (x86)\Internet Download Manager\idmwfp.inf | C:\Windows\System32\rundll32.exe | Uninstall.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2108 | "C:\Windows\System32\regsvr32.exe" /s "C:\Program Files (x86)\Internet Download Manager\IDMIECC64.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | IDMan.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | "C:\Users\admin\AppData\Local\Temp\idman642build32f.exe" | C:\Users\admin\AppData\Local\Temp\idman642build32f.exe | explorer.exe | ||||||||||||
User: admin Company: Tonec Inc. Integrity Level: HIGH Description: Internet Download Manager installer Exit code: 0 Version: 6, 42, 32, 1 Modules
| |||||||||||||||
Total events
29 296
Read events
28 898
Write events
285
Delete events
113
Modification events
| (PID) Process: | (5244) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Internet Download Manager |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files (x86)\Internet Download Manager\Uninstall.exe | |||
| (PID) Process: | (5244) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Internet Download Manager |
| Operation: | write | Name: | DisplayName |
Value: Internet Download Manager | |||
| (PID) Process: | (5244) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Internet Download Manager |
| Operation: | write | Name: | DisplayVersion |
Value: 6.42.32 | |||
| (PID) Process: | (5244) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Internet Download Manager |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files (x86)\Internet Download Manager\IDMan.exe | |||
| (PID) Process: | (5244) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Internet Download Manager |
| Operation: | write | Name: | Publisher |
Value: Tonec Inc. | |||
| (PID) Process: | (5244) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Internet Download Manager |
| Operation: | write | Name: | URLInfoAbout |
Value: http://www.internetdownloadmanager.com | |||
| (PID) Process: | (5244) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\Internet Download Manager |
| Operation: | write | Name: | HelpLink |
Value: http://www.internetdownloadmanager.com/contact_us.html | |||
| (PID) Process: | (5244) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{94D09862-1875-4FC9-B434-91CF25C840A1}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (5244) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{94D09862-1875-4FC9-B434-91CF25C840A1}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
| (PID) Process: | (5244) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{4BD46AAE-C51F-4BF7-8BC0-2E86E33D1873}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.0 | |||
Executable files
14
Suspicious files
194
Text files
29
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5244 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Grabber Help.lnk | binary | |
MD5:F1045B27BD10AF77E7DA9D1216DFAA65 | SHA256:09F4B04F17EAEC234DA4668ACCBAC41EB7DAD1A94468E9DC6B4361E790DD9161 | |||
| 5244 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Uninstall IDM.lnk | binary | |
MD5:11797F245B363C05DB868C5FE9A52F4A | SHA256:C5B1B1C1EF4B7536F5D2DE4C1CBFD224E6DA58D51A51B9DD4073CBE97AC5E543 | |||
| 2384 | IDMan.exe | C:\Users\admin\AppData\Roaming\IDM\idmfc.dat | binary | |
MD5:4D53E569C5C22188F53287911E66AFDE | SHA256:DA7DF55C4DD4CE767C8251624693328C87A9406B437D9B5EDDC44D8431718794 | |||
| 5244 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\TUTORIALS.lnk | binary | |
MD5:7428EA9F4EE4E9ECC3B0A3F98DE9CCAE | SHA256:A2A7911E8EA15FB12B69CEA990D911974452E2D6C7CD6BF7FBD2BAF30F473F5F | |||
| 5244 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Internet Download Manager.lnk | binary | |
MD5:071B352A4A348D07FF3CFF8122649D01 | SHA256:209F905DFC0EB8F737DD8545016F08D95AD6C5798A4735A94A427FA4FF8871A5 | |||
| 5244 | IDM1.tmp | C:\Users\admin\Desktop\Internet Download Manager.lnk | binary | |
MD5:BAE3826946A6A3B3F043327AFA7B45D3 | SHA256:65C94FFCDF0E8605B85D0CBB37060476765D41DB357431C0BBE093CE4098B722 | |||
| 2384 | IDMan.exe | C:\Users\admin\AppData\Roaming\IDM\idmmzcc5\META-INF\zigbert.rsa | binary | |
MD5:0C24A5190F932C3FC2B12B879C230BFA | SHA256:1D096EA115EC7CBF3CD66FA2911C8E655E939D9C00A5ABB6625504F14CC7C85A | |||
| 5244 | IDM1.tmp | C:\Users\admin\AppData\Local\Temp\~DF67AC10BFE82579F7.TMP | binary | |
MD5:A8F36DAAC6B08AE84A5B3ABE0408B58D | SHA256:0EDC9DC438F97900DA7ECA4754328F3CF1AEBBAD500EBA4E7A454E7E19888FA2 | |||
| 2384 | IDMan.exe | C:\Users\admin\AppData\Roaming\IDM\urlexclist.dat | binary | |
MD5:A888334864A80B8F3265FAB16FF94D9E | SHA256:8461E920DB212A96A8CB8BF404FD27A5890836E910AD923BDBED9F07623206D2 | |||
| 5244 | IDM1.tmp | C:\Program Files (x86)\Internet Download Manager\IDMSetup2.log | binary | |
MD5:E571B9F7F8462CF2E232B8C018E53F28 | SHA256:9C1E2874D7135A2C7BACC46FFA1D967AAC23FE766498486DFCE0DFC39C4B3BD3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
90
DNS requests
139
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3888 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3888 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.29:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5204 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
5204 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
5204 | firefox.exe | POST | 200 | 23.53.40.154:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
5204 | firefox.exe | POST | 200 | 142.250.184.227:80 | http://o.pki.goog/s/wr3/cgo | unknown | — | — | whitelisted |
5204 | firefox.exe | POST | 200 | 23.53.40.161:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
5204 | firefox.exe | POST | 200 | 23.53.40.161:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.216.77.29:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
www.internetdownloadmanager.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |