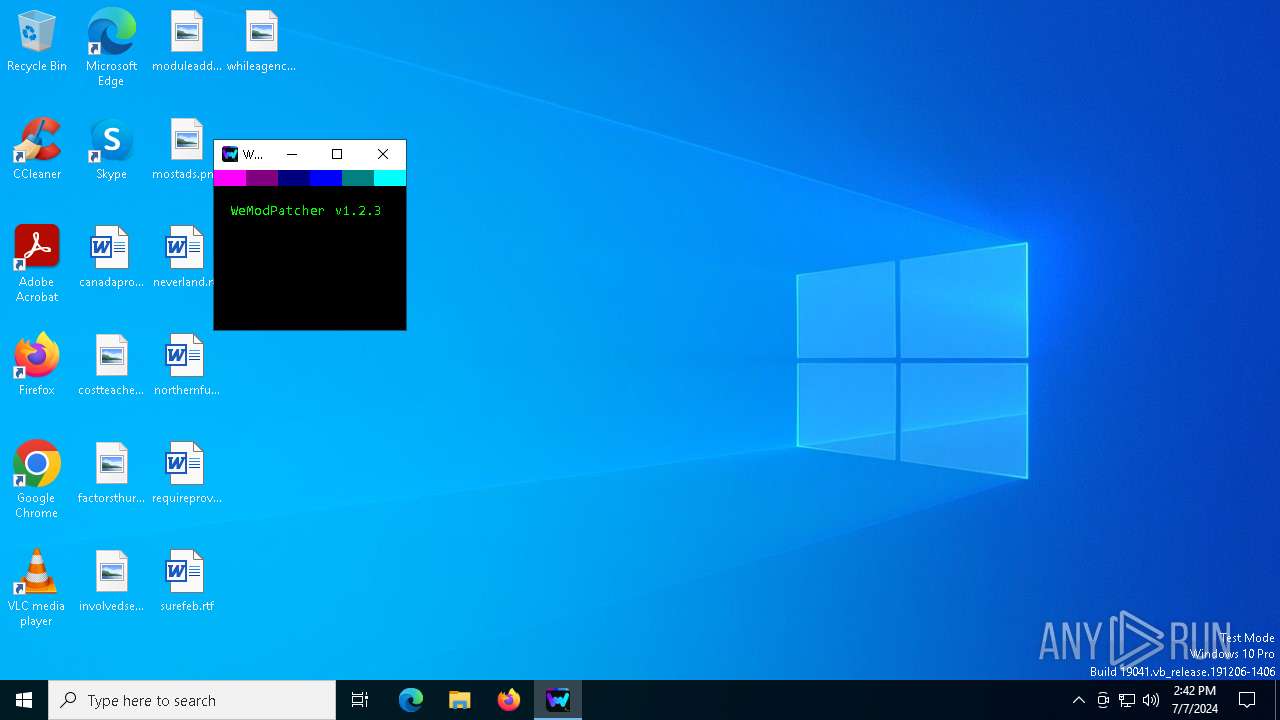
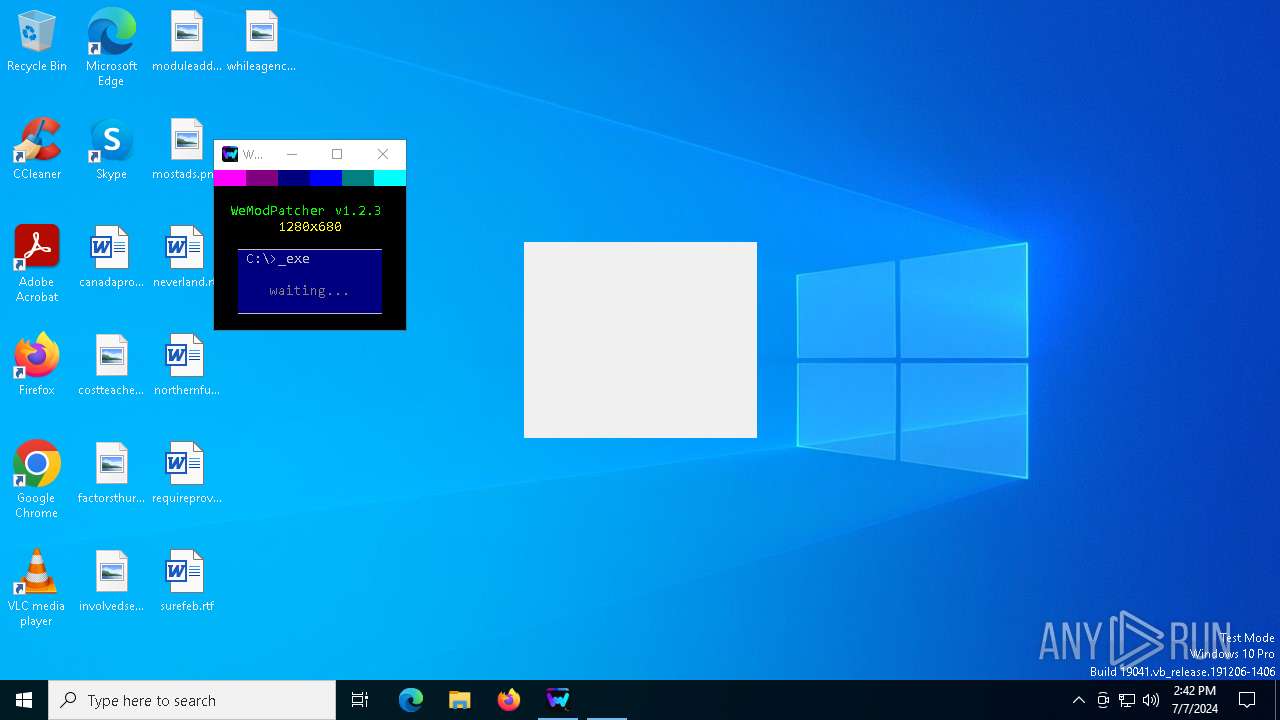
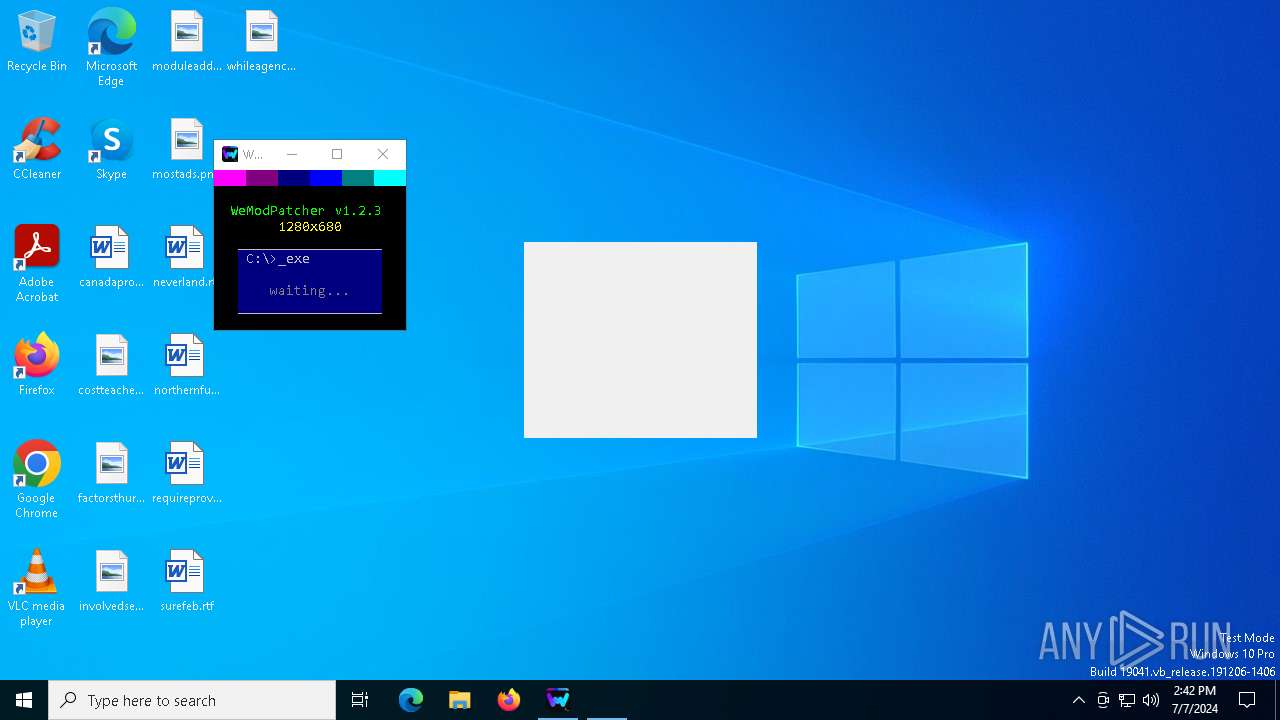
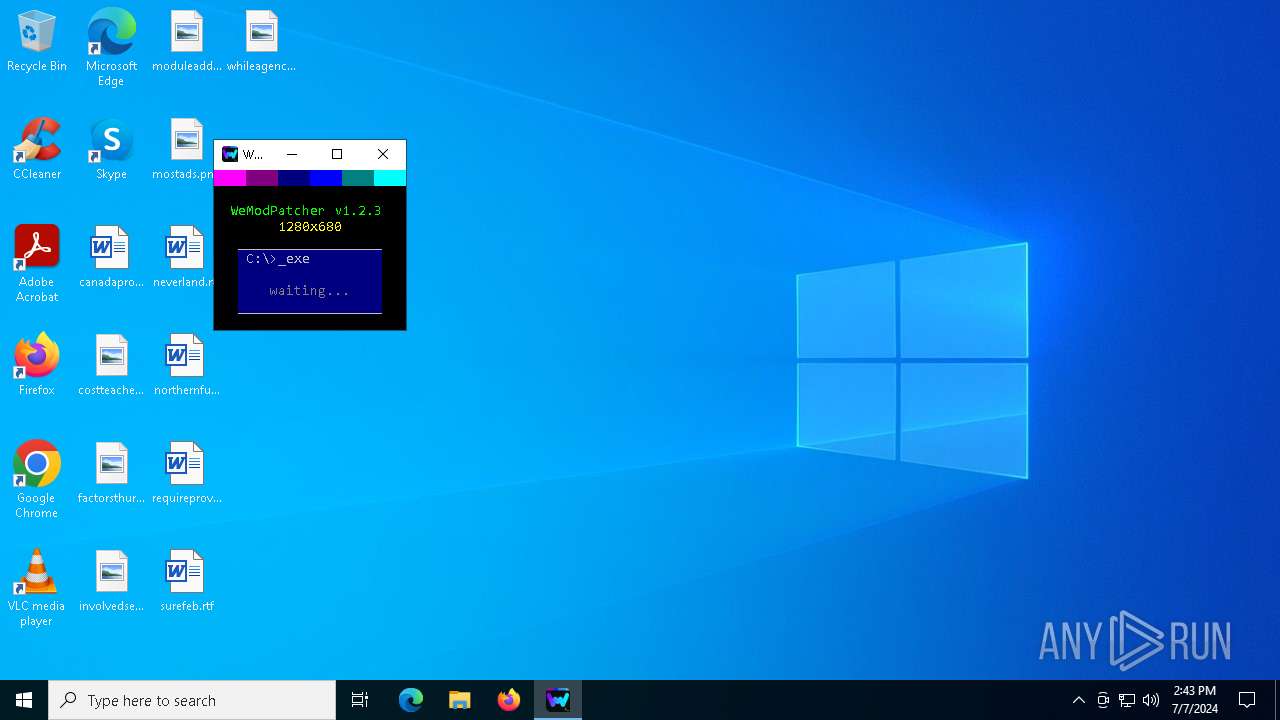
| File name: | WeModPatcher.exe |
| Full analysis: | https://app.any.run/tasks/84c455b9-6950-478b-8b27-16cba259c608 |
| Verdict: | Malicious activity |
| Analysis date: | July 07, 2024, 14:42:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64, for MS Windows |
| MD5: | 5758554FF6B8058B9CCD7A53A300F09D |
| SHA1: | 6C1BB4DA87D29F24F5B83781DB8A726E9ED02BBD |
| SHA256: | 7C5C4A323BB0BFAF0804A29C77223DFD635B2EC05AB07BCA5584D7C5A5F03670 |
| SSDEEP: | 98304:w0RkUTfCh2HVNYDlDWWcixy/s2EAfzjlWaNOG+cHpB9Loa9/ztqcxDxU2fR2Wvq/:D7XSh |
MALICIOUS
Drops the executable file immediately after the start
- WeModPatcher.exe (PID: 2784)
SUSPICIOUS
Drops 7-zip archiver for unpacking
- WeModPatcher.exe (PID: 2784)
Starts CMD.EXE for commands execution
- WeModPatcher.exe (PID: 2784)
- cmd.exe (PID: 1496)
Executing commands from a ".bat" file
- WeModPatcher.exe (PID: 2784)
Application launched itself
- cmd.exe (PID: 1496)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3996)
- cmd.exe (PID: 1496)
- cmd.exe (PID: 4216)
- cmd.exe (PID: 6152)
- cmd.exe (PID: 5244)
- cmd.exe (PID: 6872)
- cmd.exe (PID: 1188)
- cmd.exe (PID: 2064)
- cmd.exe (PID: 2064)
- cmd.exe (PID: 6248)
- cmd.exe (PID: 7120)
- cmd.exe (PID: 240)
- cmd.exe (PID: 1304)
- cmd.exe (PID: 1832)
Get information on the list of running processes
- cmd.exe (PID: 7100)
- cmd.exe (PID: 1496)
- cmd.exe (PID: 4216)
- cmd.exe (PID: 6200)
Starts application with an unusual extension
- cmd.exe (PID: 1496)
- cmd.exe (PID: 740)
Creates FileSystem object to access computer's file system (SCRIPT)
- mshta.exe (PID: 3668)
- mshta.exe (PID: 6804)
- mshta.exe (PID: 376)
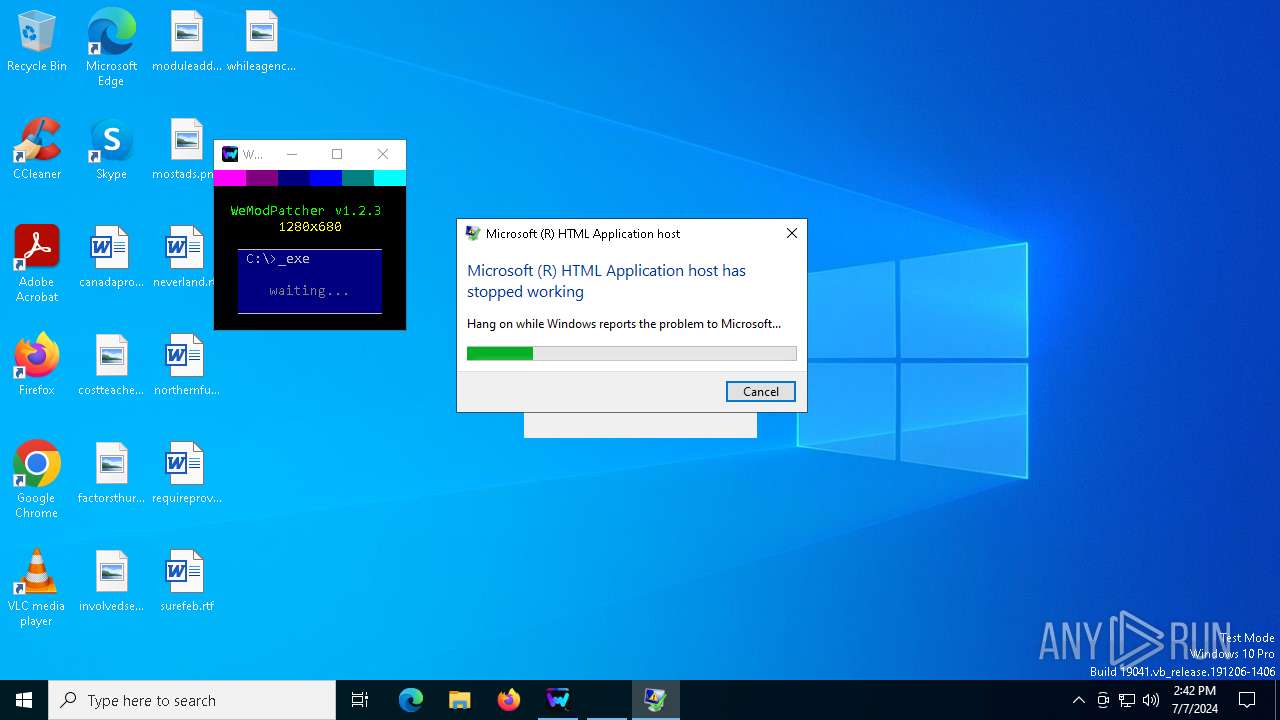
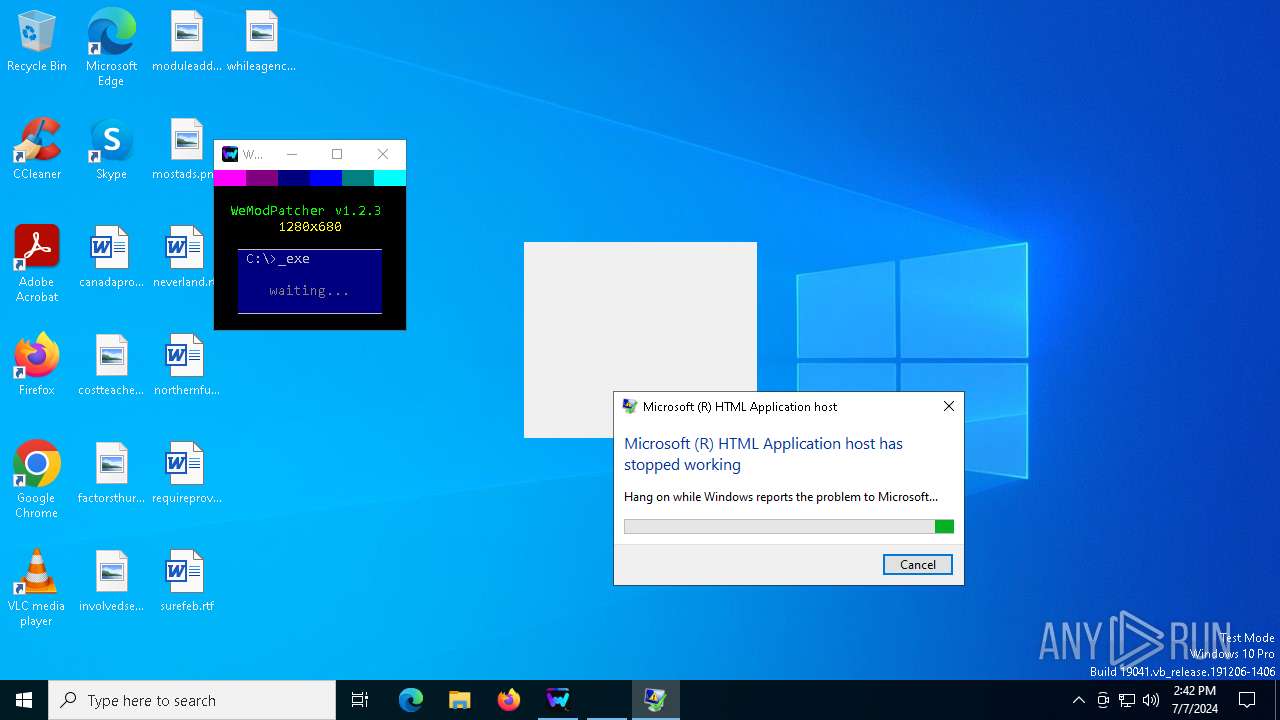
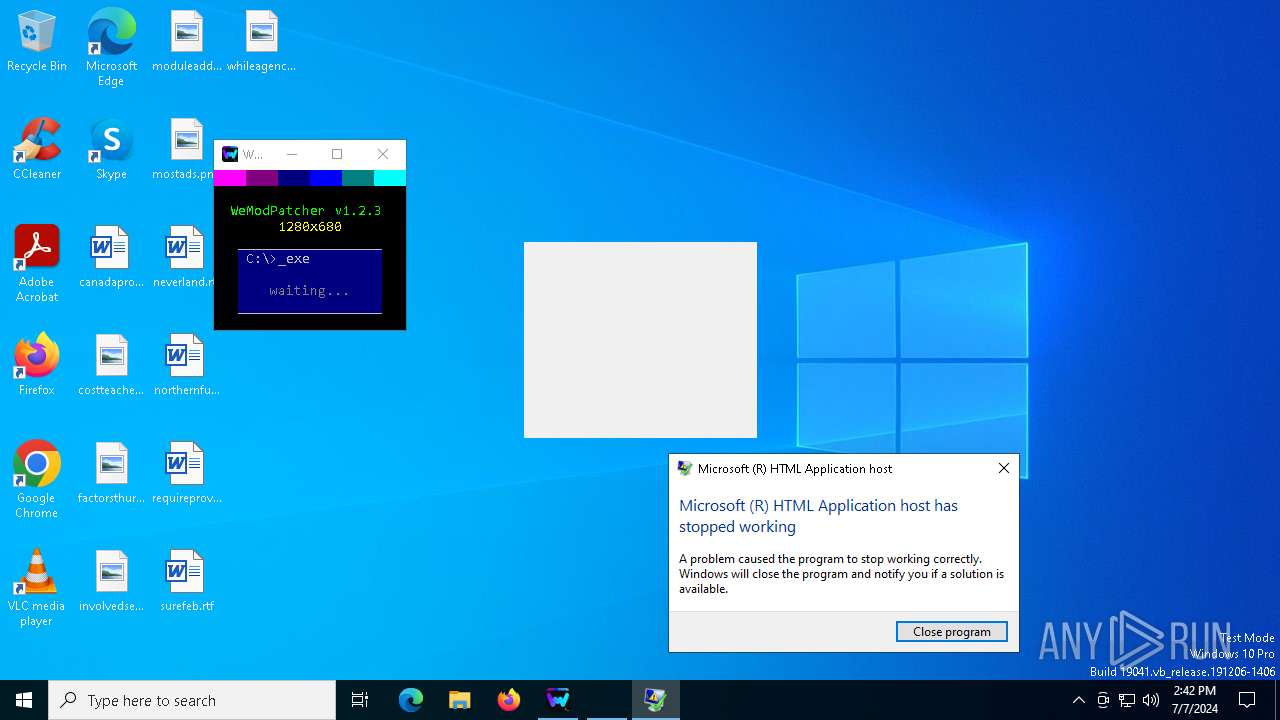
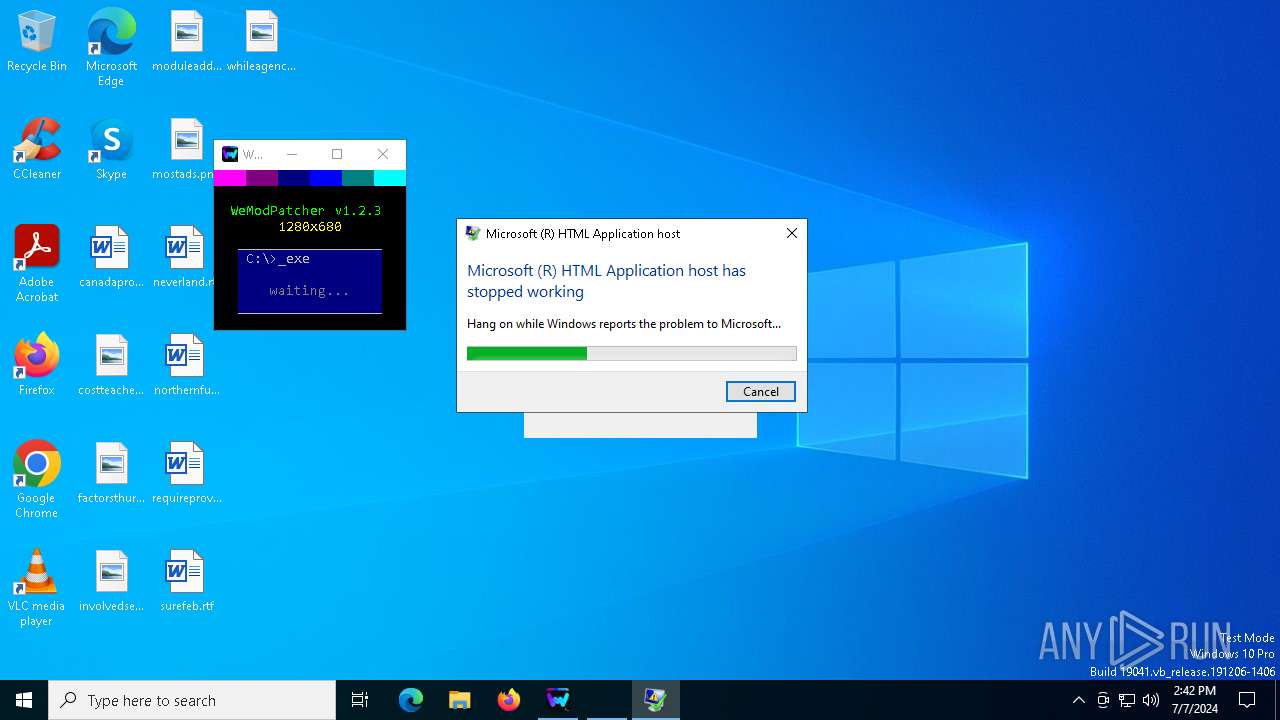
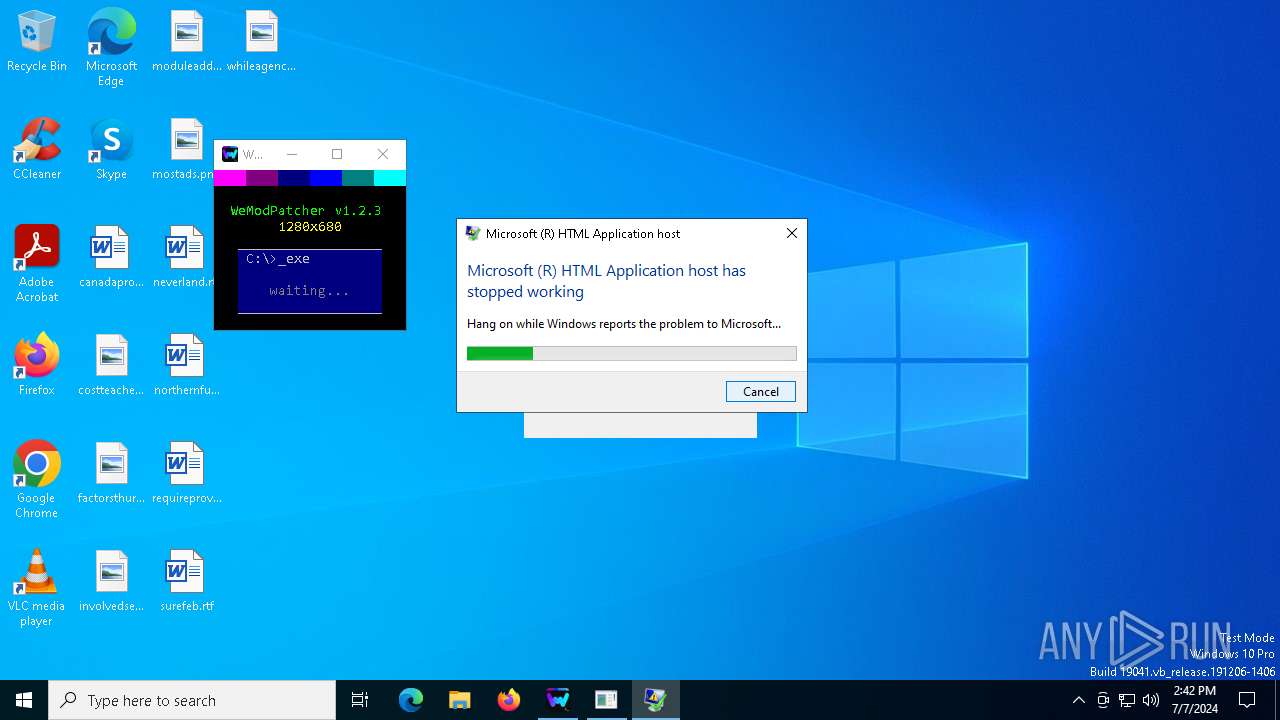
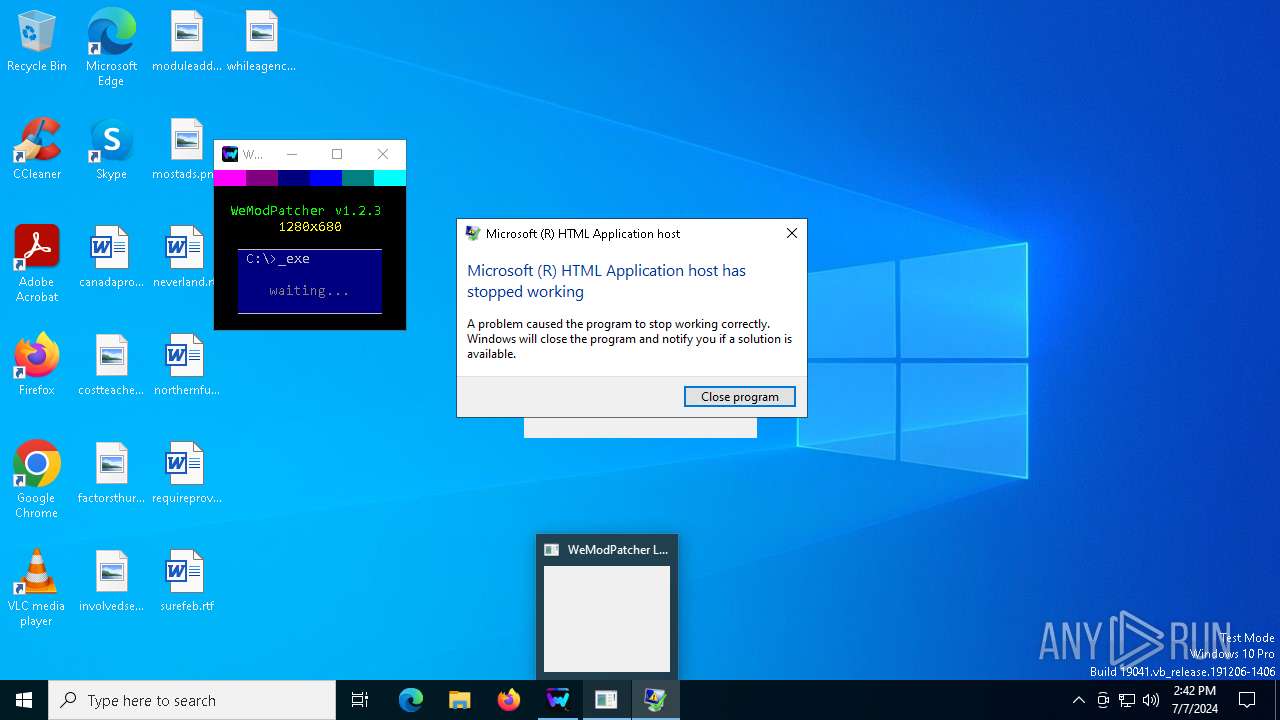
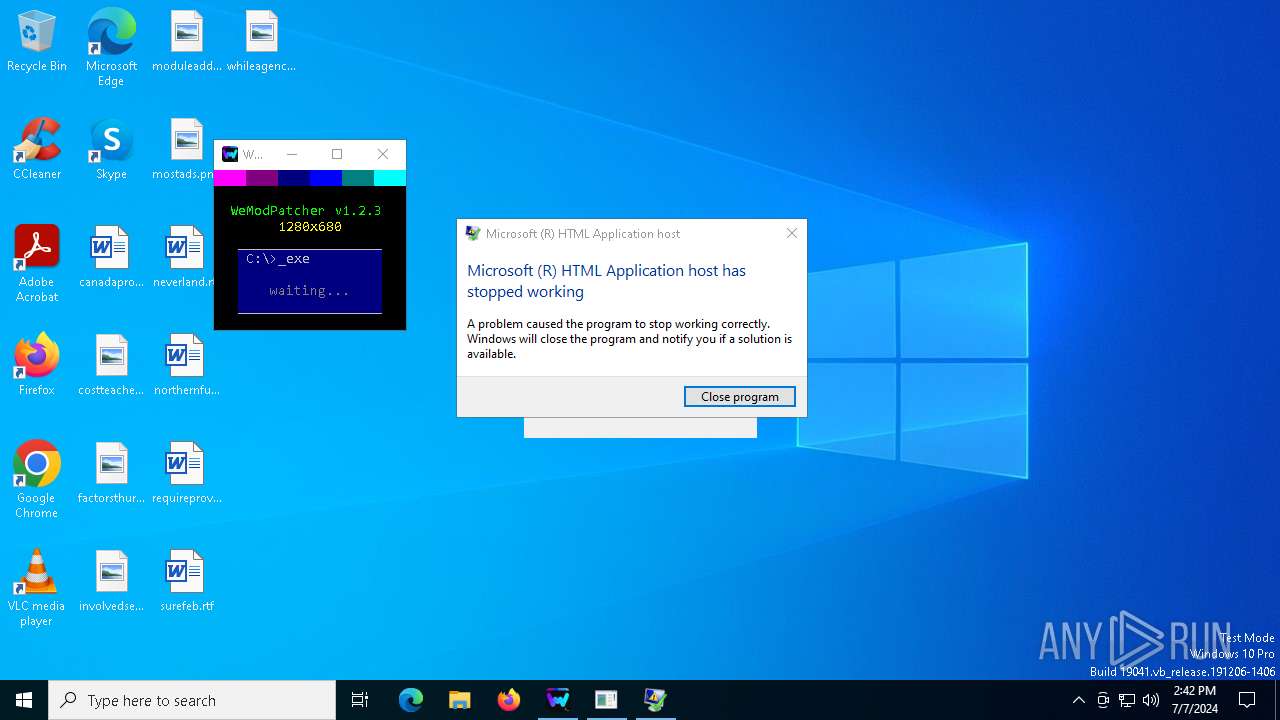
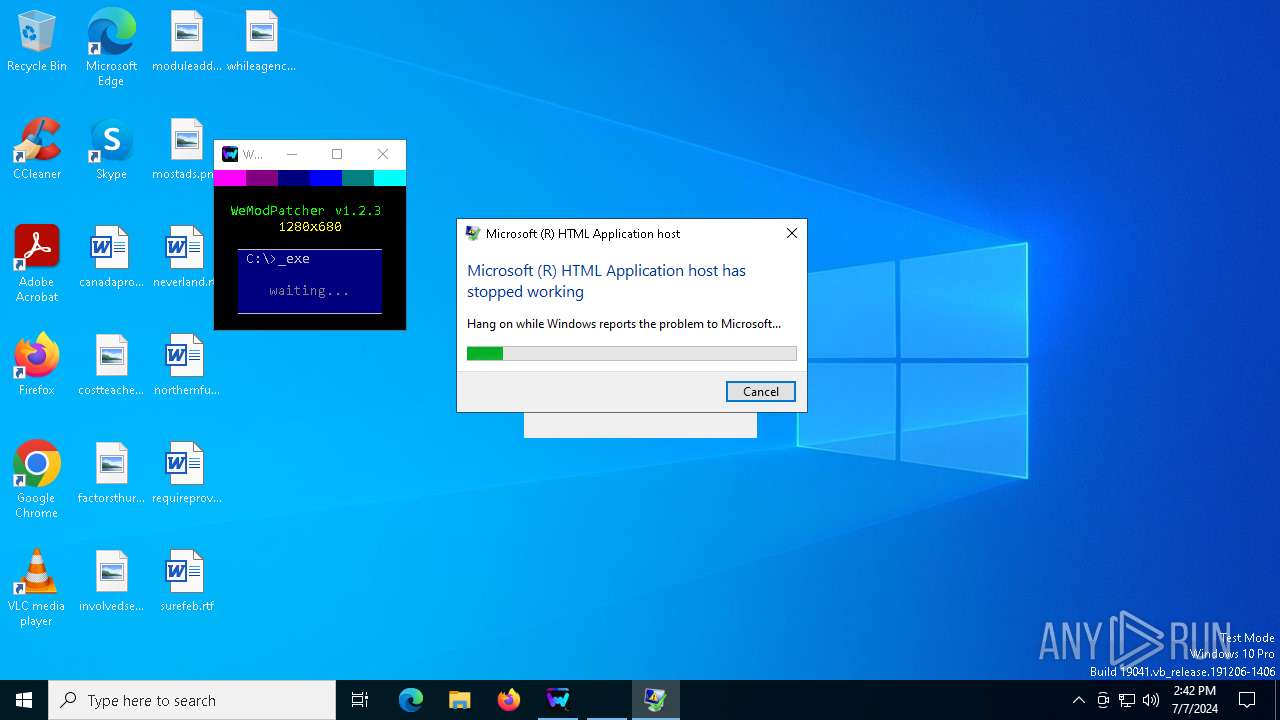
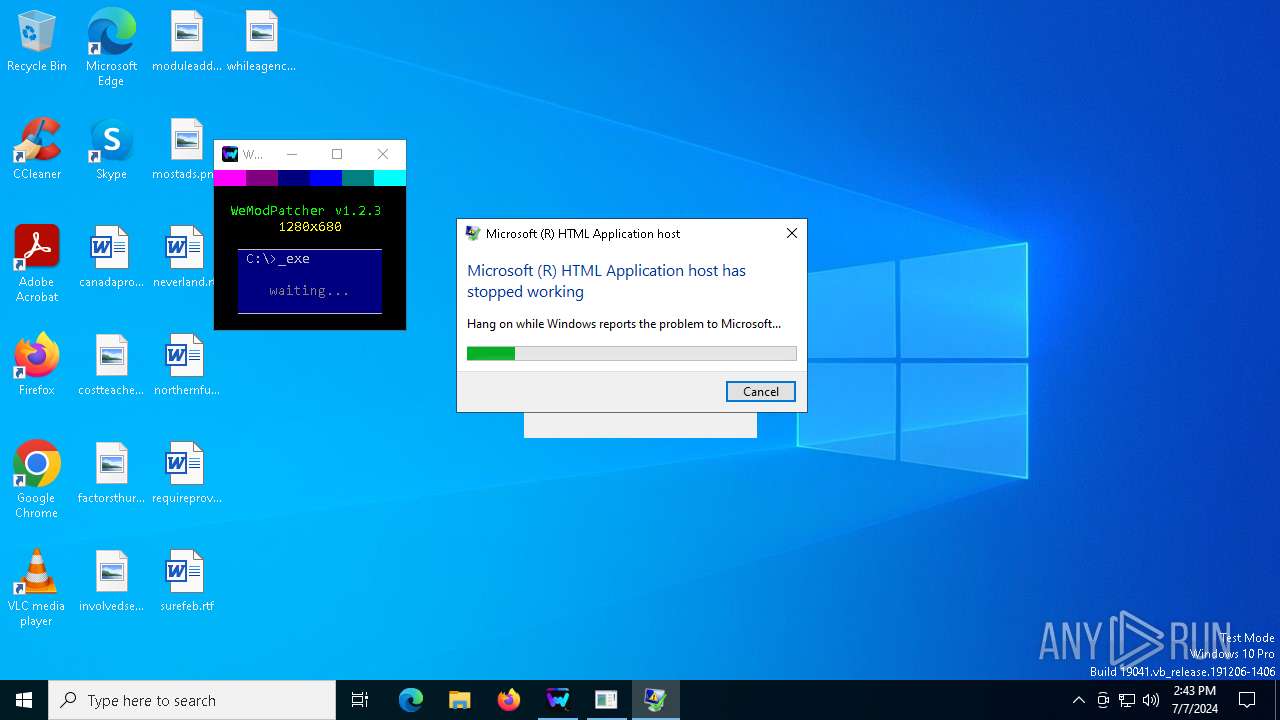
Executes application which crashes
- mshta.exe (PID: 3668)
- mshta.exe (PID: 6804)
- mshta.exe (PID: 376)
- mshta.exe (PID: 244)
- mshta.exe (PID: 7136)
- mshta.exe (PID: 2088)
The process creates files with name similar to system file names
- WerFault.exe (PID: 1384)
- WerFault.exe (PID: 6448)
- WerFault.exe (PID: 1296)
INFO
Checks supported languages
- WeModPatcher.exe (PID: 2784)
- curl.exe (PID: 3628)
- chcp.com (PID: 2028)
- chcp.com (PID: 5184)
- mode.com (PID: 5484)
- chcp.com (PID: 6552)
- chcp.com (PID: 3624)
- chcp.com (PID: 4556)
- chcp.com (PID: 7152)
Create files in a temporary directory
- WeModPatcher.exe (PID: 2784)
Reads the computer name
- curl.exe (PID: 3628)
Reads Internet Explorer settings
- mshta.exe (PID: 3668)
- mshta.exe (PID: 6804)
- mshta.exe (PID: 376)
Gets data length (POWERSHELL)
- powershell.exe (PID: 5048)
Checks proxy server information
- mshta.exe (PID: 3668)
- WerFault.exe (PID: 1384)
- mshta.exe (PID: 6804)
- WerFault.exe (PID: 6448)
- mshta.exe (PID: 376)
- WerFault.exe (PID: 1296)
Reads the software policy settings
- WerFault.exe (PID: 1384)
- WerFault.exe (PID: 6448)
- WerFault.exe (PID: 1296)
Creates files or folders in the user directory
- WerFault.exe (PID: 1384)
- WerFault.exe (PID: 6448)
- WerFault.exe (PID: 1296)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.2) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2019:07:30 08:52:08+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 2.5 |
| CodeSize: | 92672 |
| InitializedDataSize: | 1955328 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.2.3.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug, Pre-release, Private build |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileVersion: | 1.2.3.0 |
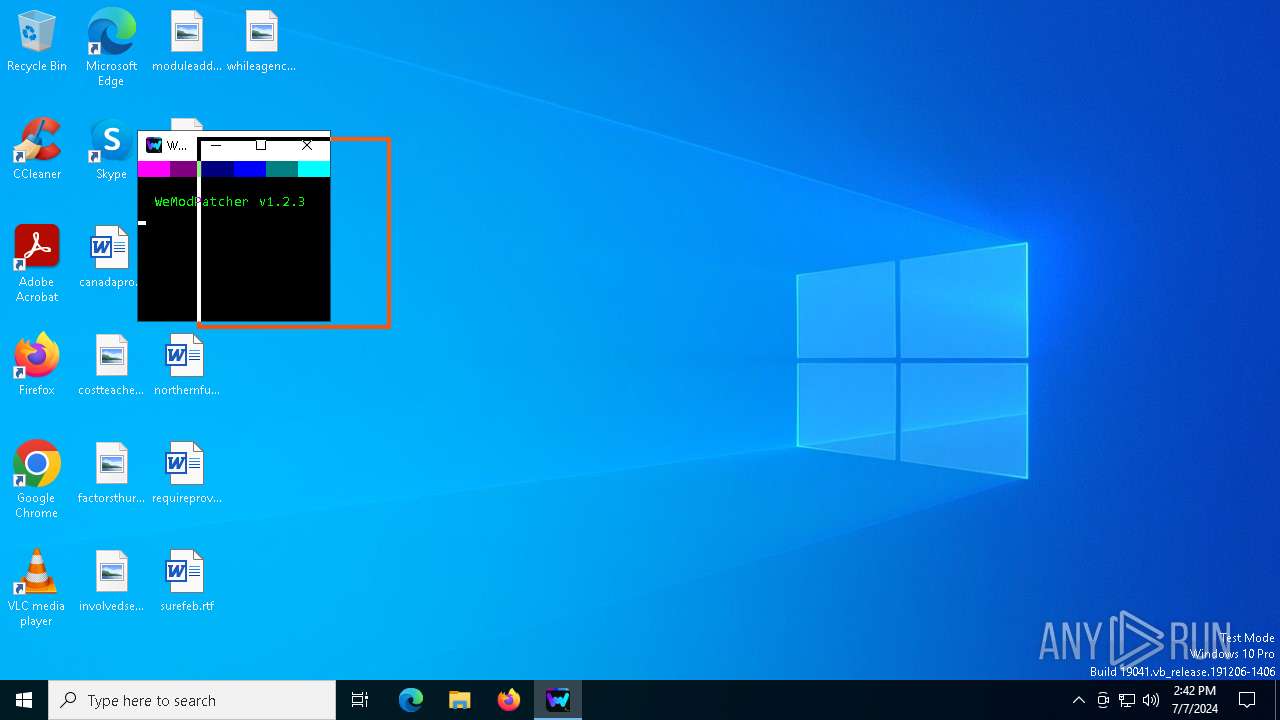
| ProductVersion: | 1.2.3 |
| ProductName: | WeModPatcher |
| OriginalFileName: | WeModPatcher.bat |
| FileDescription: | WeModPatcher |
| LegalCopyright: | brunolee® |
Total processes
222
Monitored processes
74
Malicious processes
2
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 8 | tasklist /NH /FI "WindowTitle eq "WeModPatcher"" | C:\Windows\System32\tasklist.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Lists the current running tasks Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 240 | powershell -Command "Write-Host -B 13 -F 13 '....' -NoNewline; Write-Host -B 5 -F 5 '....' -NoNewline; Write-Host -B 1 -F 1 '....' -NoNewline; Write-Host -B 9 -F 9 '....' -NoNewline; Write-Host -B 3 -F 3 '....' -NoNewline; Write-Host -B 11 -F 11 '...' `n`n -NoNewline; Write-Host -B 0 -F 10 ' WeModPatcher v1.2.3'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 240 | C:\WINDOWS\system32\cmd.exe /c powershell -Command "(Get-FileHash Options.ini -Algorithm MD5).Hash" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 244 | mshta.exe "C:\Users\admin\AppData\Local\Temp\Launcher.hta" | C:\Windows\System32\mshta.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 3221225477 Version: 11.00.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 376 | mshta.exe "C:\Users\admin\AppData\Local\Temp\Launcher.hta" | C:\Windows\System32\mshta.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 3221225477 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 648 | C:\WINDOWS\system32\cmd.exe /c curl -s https://raw.githubusercontent.com/brunolee-GIT/W3M0dP4tch32/main/W3M0dP4tch32L1nk5 | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 648 | powershell -Command "Add-Type -AssemblyName System.Windows.Forms;([System.Windows.Forms.Screen]::AllScreens).WorkingArea.Width" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 652 | C:\WINDOWS\system32\cmd.exe /c mshta.exe "C:\Users\admin\AppData\Local\Temp\Launcher.hta" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225477 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 740 | C:\WINDOWS\system32\cmd.exe /c chcp | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1112 | powershell -Command "(Get-FileHash Options.ini -Algorithm MD5).Hash" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
Total events
86 232
Read events
86 204
Write events
28
Delete events
0
Modification events
| (PID) Process: | (3668) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3668) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3668) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3668) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1384) WerFault.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IdentityCRL\Immersive\production\Property |
| Operation: | write | Name: | 0018400FF15A8C16 |
Value: 0100000001000000D08C9DDF0115D1118C7A00C04FC297EB01000000E906BC3EB1876647B546C767417EA5090000000002000000000010660000000100002000000014186432714A06AD576F9BDBB7927FDBDE6B4682833922100CEC62DC1FFB9EA0000000000E8000000002000020000000B2571315451331840E56E9A104944CC016695CB2F09F621A7A0AE6A2C5B78D5E80000000EEC56B1D0D758AEF428457F4E2F30AC241EE5234D4350DF988D59A14021C53F54E50961709C897F8E0EBAD7C65B3E9E43550E3BF16AD06CC415B6406B8850E624464D9878B9EF9891B78E3AAA57A71667D546B3566DB8F8533EE6161099376BEBC2BE15F1379AC14E6DE62A81DB293788493357E9088F15C8650A7E2AB064790400000000B01A9CC611945159DB20CDE7C9FF0EE45F91AFCCD6F9F32DC5845E3304B5FDF903D89171E0625FCD84BDB4A9136D91DE38C78453D5E2C8D33359C3F67CF6DD7 | |||
| (PID) Process: | (1384) WerFault.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IdentityCRL\Immersive\production\Token\{67082621-8D18-4333-9C64-10DE93676363} |
| Operation: | write | Name: | DeviceTicket |
Value: 0100000001000000D08C9DDF0115D1118C7A00C04FC297EB01000000E906BC3EB1876647B546C767417EA50900000000020000000000106600000001000020000000F7752A623BF6965730DD054304FDB1A5102484564BBCBE31346EED42CC22F191000000000E8000000002000020000000035BF4EA58E84E5716ED85B1FD25D983F13EEB1962ABD6B51091A220C925FF5020080000E576B232D5BA8B0731F7FF15FD4BA9B85410B5527DD6D4BB50724EAB98FCB6EE5B5CDAA5A2136B75A1F458C81EE8899FA09982DEFE42E6BDFD8F03E2F487079394E2C55A458502B57F06AFFEF0F1615F7A329D099290C16508E5ACDD974AF40675440A46E7251DD626F217872071E6A5FB270EC4EFFEED55FDD58A7A511030C5937F7F3AE0C427F32D4E1C74F087F720F4BBD007E2FBEDCE38CEC2919AA6D507ECFC26F9753488BB2C6106BC46C7BAFE1723F749E15EF92BF53E4384E2B8483FA5D207B43D8D1E988A7CFFE71F032D2A89D3BB868E0C462CA53A428DEACA2692E9B8F678543D850A60CB1B82D292DA0C176327B4822554ECD82ADEBEF3EEB928E00F34B615DA0E6C3726911843BA4B70F08A0B035203E165744EA9812DAAA5F06C8E127A8E891CC8272018B7DF50B8474339A78A902B06BA994B0B06A472B3087AB6F913A506F14D0C8905620B15A45CD0DE65965AAEE32CDEF9F79E543952B6CDFA1FBDFEAA2F0D0201B35DD4AA0C907CA9E5F764FD55715CE1818731FC441386D9A3CABE504F3CD550857112409051E31376FBC9CE49469C458AA7BDE15E84EB92C7C31E2111AE400E01A895791D89D9FA6C6728C6F1ECA7D3EB62475844EC5EFA004F86FD52275D2ED72BA51AC03BEC39780398DB8E68B93DB2DC08BC26845B8D9C2EE08F6CC3C3A0F00E83ED965F2923CB8B9A428762B31AA6B33D8AB598F7B96DAA3D643FE6961A12BAEF33A2458FA2379D430F54B289828ADCDADCC85B3B08FE2BA003B289E3FF3425BBC77C6BD465711FC14D4E379CD1A7E4E85035E2E55018486ED9BF24E2A68ABBAD1372F92CC36EA7F2BA3FC00C1CD5DDC4A4480B0C369F2BF0A3491D3F382AA74844130B9F1ABD3F74413E24D4B6C80BB1DEEFAADF1CD36B03F02A6CE2DDC226B6BC764EC25848A82BEE81026096801A0CC37AE8FD2E292BB440BC70E9EB5605555DE8ABCA68422AD565103848721619EE361CD87FFF7C0CA2C9AD721B9F373C6D4C39A26C9AD9AD5864109D1656BDE639A084AD917D90F9B32632FB436C1D3FC13E3A5B2CBD6CCFB1B3E4BC3F97287D572959EBA433BDE51AFAD5D586C6918227A94E98FABEE20492F0C720F323A3F8E198C177E349210588082F9767E959C1CB9092361954A1CB966995D6E037D47F5532E464E99B6A1D31A5B3CF4BE9FD80560C8A59F6C4B29D600CAE30D2018FDA792161BA2B8DC3AD097B52C53A80CED678790D32C829F2EF55FAB2EFE58EA73F18B59052CFE3370FD918DE04321C3F10CE7BF4AD6FA488F65C7917285E63ADB3AA2A0A2B357E784D194829B4F035F9BCAB35F6BD219CF7021DB6A642A606AD8704B08CFCF275E54339BF950674F8C486DA56F2885FD08023505345EEE688168053802E6CD681049498876DE2AB11802351054519075FEFA5CEA515065D0C94B21F97A5F7831C6220260597A68098F49D08BE0D6F0B0D7F22D1A9967798099547D10319C25ACB2B52A8473178F6E303B89A4A0F4FAE28F2CA11246AB212FBD2631AFB477CAEDBDE1BAD2044AC6E221586A0FFC05D09B3F1B0F59D834CAAE6062B0A008913F4B7093CE4EB9D2AE985C62CDDF1AF08A363F57B1245FDD0202074AF739DBAE4B42F2583A7AD2397D24BFE72404C03F926BE8A540D194973F6C145BABEDDD0D58107A341E3BA71CEF20897D2F4C37C32C171369A9AD5BFD0BDE519CEEDB6D6CD8CF0D0A7EE0F7205F6E0B3457BA7C62EA02671E4937262393C8F4CC52FBC515433946FD6B6CFFABDAFA28F588360D74AC153E8EF3CAD37D343E91D91CD955280BCB06F1562574A46634045DB7F85EBACF92C98996DF0967327BDF09629CC4DB2B38D7FC9FA6CAFB568ECC7884D929D5CA953BB170E314A362F9AD147F4A507279E9386C0FA4EDE4E5616C39E2EB2C7376D53DBB611AD3F09AFA3DA9100F8434B8BFEB021E573741A0AF45A63D5EECA56660F8B5698FEB148F78433E48F8A7052C4B2A0AD993FA4D6085B4249210CDBAD837F100F9E4709792069D9D7FF95A8981A1F587B7822BF90E0B374239A75984FB6707A13813D37ED9517B300F0087CA26C5DC551BCF49CA89288919AB82FE53AC198B6E1B00FB9078FD776D179A559027B31896FF6F724A7ED3BECB65AB7AB86BCC5568E280DB0B32FB24A83E9D7ECBA54F19BE8266FD15D5856508421066FA3D9E0B7B1D2953F3EAECF3CA449EFEF06AF7B2299B94815D5F30C8F349EE6E899F877B4CA662E58F242E60A02C906651A70F47EB49F13B49FEA315CBB7476FF8B77B7CB59794394D3E06D2AFC3F6BCF911C5D3596DC9104770000493DFDE11DBE0F937558288BA2896549158B7A85855F6DC6C68ACDDD5604E7AB83B6158ADBDAAD97AEB1ABBAC5895970686B47366BC145EE68B528CA10338C32583065E75474CDC9B425291EF3A74D904BA5CC2629C8390BC5CC1F6C31A4F11BC252AF72A8B353EF58E3BC9C070C65E83CF4B9961604E9DB6BD25FA3629C7A48785D09EDF66F743448472907E42E458EE860F54E471AE4CAEF0AC788EC74AA4A9FF4A7F69ECB32E94B06F0EE49BE80DD41DB1382246B9C8DF74231C47A330B0D22B3C6096A800285531B4FC1F5E3975CBF931B7F7BD08586C11A5CCB4228AA83D91BF2115E9603B6613CA2D81DB154254C32E2EECF21E84DC2664A871BA30FFF8993A12BD4F1072B9425D3AF346A91DA10FD5C6606249DF1C8EC1D2AD38E417D139067F0E9B8FA392C8F242C6AA0A8B7B60AAFE284BA26D62B3667F56530FCA67D7D149A97DF51FBE5314ADF5844B90B8CB3556E1899AC4FFDEE75E7F474C59D6E14BCDEDFC82535985E0D685327EA701068A65F3D9CE454F88785E743302E480D0F2E914111E7380E0AD0C3166D9214BFC3E1ADC0C761C56B5797703822484A403EE57BB66C1E7CAB845879209BB79FDDD4277A08D340000000D026A847762412869F3D719A7923010146FFBDBDED8822A28FB13E1367EE78CA120A53E40B75F2C8441C74AF527A18F5F8A681C8170394351968F503BA935219 | |||
| (PID) Process: | (1384) WerFault.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IdentityCRL\Immersive\production\Token\{67082621-8D18-4333-9C64-10DE93676363} |
| Operation: | write | Name: | DeviceId |
Value: 0018400FF15A8C16 | |||
| (PID) Process: | (1384) WerFault.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IdentityCRL\Immersive\production\Token\{67082621-8D18-4333-9C64-10DE93676363} |
| Operation: | write | Name: | ApplicationFlags |
Value: 1 | |||
| (PID) Process: | (6804) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6804) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
0
Suspicious files
17
Text files
58
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2784 | WeModPatcher.exe | C:\Users\admin\AppData\Local\Temp\Options.hta | html | |
MD5:C0826786D1B58B03C4C134865CD0A0A6 | SHA256:E4CDEA4433591103E4C416165B9B7EEBFF79C30B011EEE839064C0621FE0B209 | |||
| 2784 | WeModPatcher.exe | C:\Users\admin\AppData\Local\Temp\E8B2.tmp\E8C2.tmp\E8C3.bat | bib | |
MD5:4B4EAA0DD7E6595C80571771551C807C | SHA256:D880E1B0336ED1B358758BC386D782942FE9321C850143C0061379067AF30D3B | |||
| 2784 | WeModPatcher.exe | C:\Users\admin\AppData\Local\Temp\lang\lang_en.ini | text | |
MD5:DA7F78CEA561177B4593E43E472B8A61 | SHA256:5CE043FA53863E2FC94E42D72D870DA746D94CA5CDBC1E1F6FBD364681D69F26 | |||
| 2784 | WeModPatcher.exe | C:\Users\admin\AppData\Local\Temp\lang\lang_de.ini | text | |
MD5:56F718D833D85B64D368A746CEC7D311 | SHA256:9296A56AE3F33183E5DD78159EEDC14E7C55D58B6FF984D30480927F3491A0A6 | |||
| 2784 | WeModPatcher.exe | C:\Users\admin\AppData\Local\Temp\WeModPatcherTools | compressed | |
MD5:7D2DBEC2395D4CF262EAF10C9B944F4C | SHA256:43F2B4E8D63A62055E8A2CDF80C8809ED6A9FE1574141A9083CA998B65C7E082 | |||
| 2784 | WeModPatcher.exe | C:\Users\admin\AppData\Local\Temp\lang\lang_es.ini | text | |
MD5:EFE851D125CBF4EA90D87CF1F469E331 | SHA256:5D75679F3A5CD60EA5700C5F83AF9411D404B1A6077EB994D90597BDFE9855D9 | |||
| 2784 | WeModPatcher.exe | C:\Users\admin\AppData\Local\Temp\lang\lang_pt.ini | text | |
MD5:98D8CB666E73522D7478520D685183CC | SHA256:E56FB42EA5361EDF06D352ADCB3C46CD2A675C59D455B2FAF7D14727ACA1ADE3 | |||
| 2784 | WeModPatcher.exe | C:\Users\admin\AppData\Local\Temp\Options.ini | text | |
MD5:83503A2A8B9F78CFFA4ED444885C4959 | SHA256:E217B87EA4F57FA0FBF70BED27EDA1DA7FF3A4D3B7A989BF15B1261E6735387A | |||
| 2784 | WeModPatcher.exe | C:\Users\admin\AppData\Local\Temp\lang\lang_ru.ini | text | |
MD5:0CA2E71373B332E16C4DD703DD55D7D2 | SHA256:B2AD6A04B335B3421A7B180B5AFB3CFCDF965380F4AC46F0652BEE5F8BD982FD | |||
| 2784 | WeModPatcher.exe | C:\Users\admin\AppData\Local\Temp\lang\lang_fr.ini | text | |
MD5:EA19B7BB4D40D45A8F8A7DD1AC50F71B | SHA256:1C7F187AED0221D27937884A433425D351AA85CEB907F2CBD59794F2437E5801 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
65
DNS requests
22
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6284 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
1384 | WerFault.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
6788 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
6788 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
3992 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
1384 | WerFault.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
2448 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
2448 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
768 | lsass.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAz1vQYrVgL0erhQLCPM8GY%3D | unknown | — | — | unknown |
6364 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2448 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3628 | curl.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
768 | lsass.exe | 192.229.221.95:80 | — | EDGECAST | US | whitelisted |
2140 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2060 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4656 | SearchApp.exe | 104.126.37.128:443 | — | Akamai International B.V. | DE | unknown |
— | — | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.229.221.95:80 | — | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
raw.githubusercontent.com |
| shared |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2168 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |