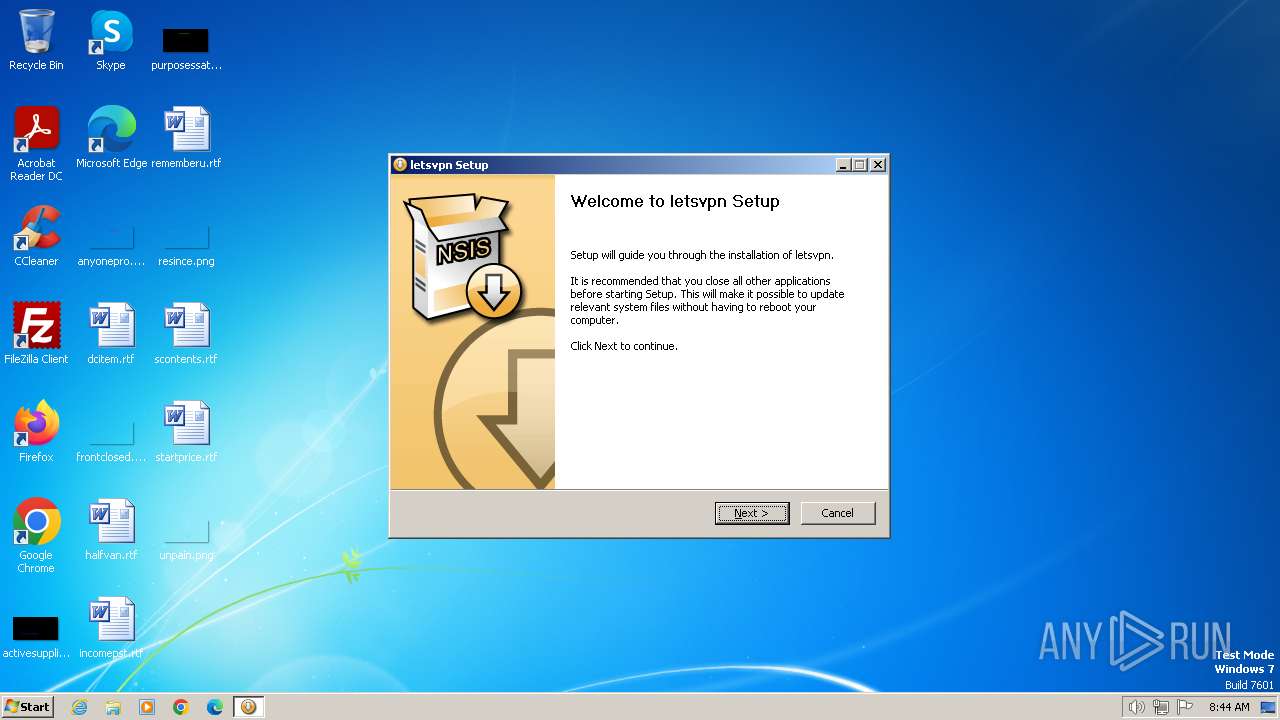
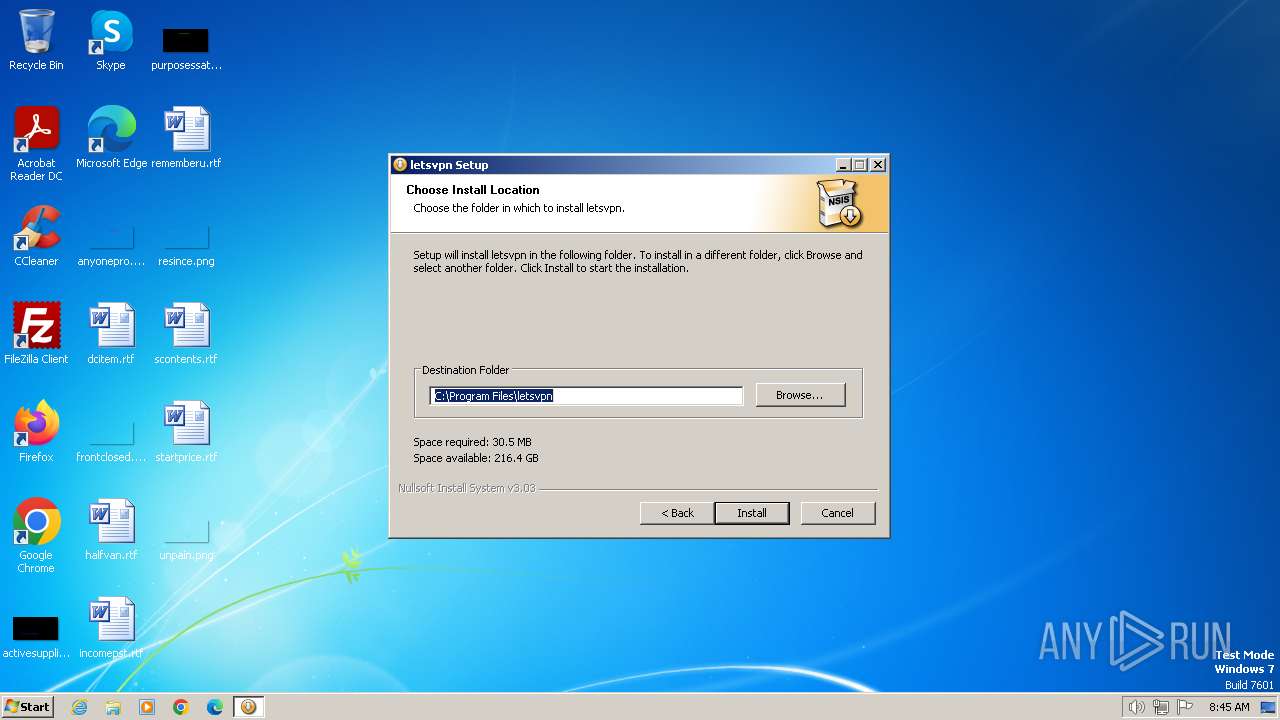
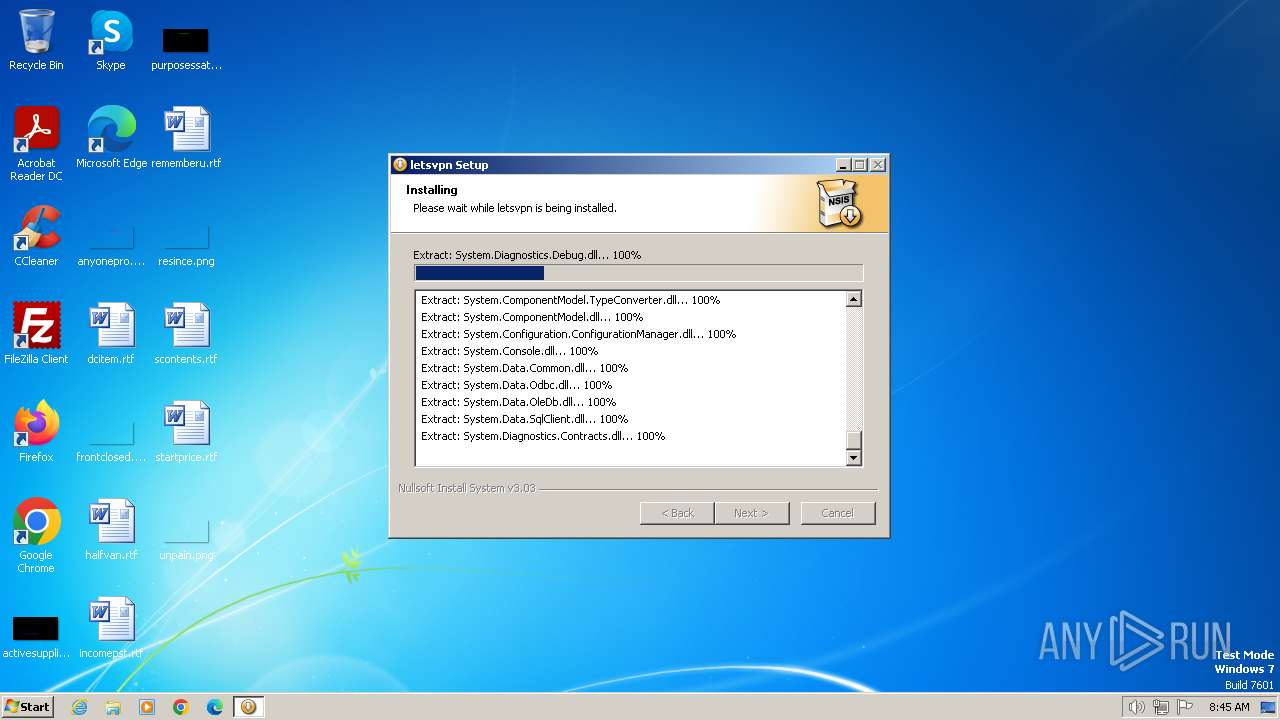
| File name: | letsvpn-latest.exe |
| Full analysis: | https://app.any.run/tasks/bbe69aab-1b67-4775-9060-ed0bdc476e36 |
| Verdict: | Malicious activity |
| Analysis date: | December 25, 2023, 08:44:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 40E916F7EF901E0AD09D4C6806F47E27 |
| SHA1: | C84027787F4E98DE92212EA320A4C272A62FAE10 |
| SHA256: | 7C4EAB9F4F2A5AFEC378FCF44CBDDB99B6CE571187364D8647F015E8768DA037 |
| SSDEEP: | 196608:0VRIovpt282cgoiKDBo5QuRdT50Vpim9hvn:0VmoxgegJWXuRdT50Vpim9xn |
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 268)
Creates a writable file in the system directory
- drvinst.exe (PID: 2312)
- drvinst.exe (PID: 2324)
Changes powershell execution policy (Bypass)
- ns712.tmp (PID: 2020)
SUSPICIOUS
The process creates files with name similar to system file names
- letsvpn-latest.exe (PID: 2256)
Starts POWERSHELL.EXE for commands execution
- ns712.tmp (PID: 2020)
Starts application with an unusual extension
- letsvpn-latest.exe (PID: 2256)
Reads security settings of Internet Explorer
- tapinstall.exe (PID: 1784)
- LetsPRO.exe (PID: 3144)
Checks Windows Trust Settings
- tapinstall.exe (PID: 1784)
- drvinst.exe (PID: 2312)
- drvinst.exe (PID: 2324)
- LetsPRO.exe (PID: 3144)
Reads settings of System Certificates
- tapinstall.exe (PID: 1784)
- rundll32.exe (PID: 2348)
- LetsPRO.exe (PID: 3144)
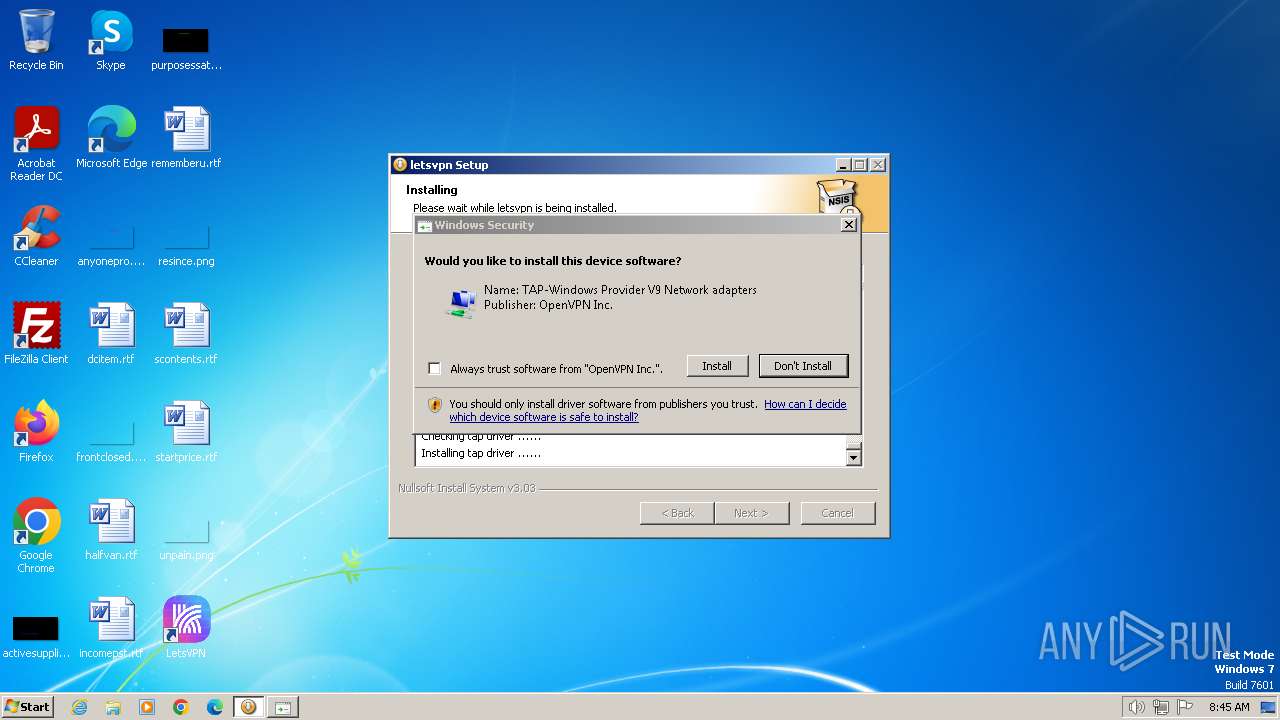
Drops a system driver (possible attempt to evade defenses)
- tapinstall.exe (PID: 1784)
- drvinst.exe (PID: 2312)
- drvinst.exe (PID: 2324)
- letsvpn-latest.exe (PID: 2256)
Creates files in the driver directory
- drvinst.exe (PID: 2312)
- drvinst.exe (PID: 2324)
Starts CMD.EXE for commands execution
- nsAD58.tmp (PID: 2888)
- nsAEB0.tmp (PID: 2528)
- nsAFAB.tmp (PID: 2852)
- nsB087.tmp (PID: 2356)
- LetsPRO.exe (PID: 3144)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 2176)
- cmd.exe (PID: 2376)
- cmd.exe (PID: 3024)
- cmd.exe (PID: 3068)
Reads the Internet Settings
- LetsPRO.exe (PID: 3144)
Adds/modifies Windows certificates
- LetsPRO.exe (PID: 3144)
Uses ROUTE.EXE to obtain the routing table information
- cmd.exe (PID: 4048)
Process uses IPCONFIG to discover network configuration
- cmd.exe (PID: 3500)
Process uses ARP to discover network configuration
- cmd.exe (PID: 3904)
Suspicious use of NETSH.EXE
- LetsPRO.exe (PID: 3144)
INFO
Checks supported languages
- letsvpn-latest.exe (PID: 2256)
- tapinstall.exe (PID: 2128)
- ns4872.tmp (PID: 1808)
- ns712.tmp (PID: 2020)
- tapinstall.exe (PID: 1784)
- drvinst.exe (PID: 2312)
- nsAD58.tmp (PID: 2888)
- drvinst.exe (PID: 2324)
- nsAEB0.tmp (PID: 2528)
- nsAFAB.tmp (PID: 2852)
- nsB163.tmp (PID: 3092)
- tapinstall.exe (PID: 2656)
- nsB087.tmp (PID: 2356)
- LetsPRO.exe (PID: 3236)
- LetsPRO.exe (PID: 3144)
- wmpnscfg.exe (PID: 3776)
- wmpnscfg.exe (PID: 3768)
- wmpnscfg.exe (PID: 3912)
- ns4787.tmp (PID: 1936)
Reads the computer name
- tapinstall.exe (PID: 2128)
- letsvpn-latest.exe (PID: 2256)
- tapinstall.exe (PID: 1784)
- drvinst.exe (PID: 2312)
- drvinst.exe (PID: 2324)
- tapinstall.exe (PID: 2656)
- LetsPRO.exe (PID: 3144)
- wmpnscfg.exe (PID: 3776)
- wmpnscfg.exe (PID: 3912)
- wmpnscfg.exe (PID: 3768)
Malware-specific behavior (creating "System.dll" in Temp)
- letsvpn-latest.exe (PID: 2256)
Create files in a temporary directory
- letsvpn-latest.exe (PID: 2256)
- tapinstall.exe (PID: 1784)
- LetsPRO.exe (PID: 3144)
Drops the executable file immediately after the start
- letsvpn-latest.exe (PID: 2256)
- tapinstall.exe (PID: 1784)
- drvinst.exe (PID: 2312)
- drvinst.exe (PID: 2324)
Reads the machine GUID from the registry
- tapinstall.exe (PID: 1784)
- drvinst.exe (PID: 2312)
- drvinst.exe (PID: 2324)
- LetsPRO.exe (PID: 3144)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 2348)
Executes as Windows Service
- VSSVC.exe (PID: 188)
Reads Environment values
- drvinst.exe (PID: 2324)
- LetsPRO.exe (PID: 3144)
Creates files in the program directory
- LetsPRO.exe (PID: 3144)
- letsvpn-latest.exe (PID: 2256)
Creates files or folders in the user directory
- LetsPRO.exe (PID: 3144)
- letsvpn-latest.exe (PID: 2256)
Reads Windows Product ID
- LetsPRO.exe (PID: 3144)
Manual execution by a user
- wmpnscfg.exe (PID: 3776)
- wmpnscfg.exe (PID: 3912)
- wmpnscfg.exe (PID: 3768)
Process drops legitimate windows executable
- letsvpn-latest.exe (PID: 2256)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:01:30 04:57:48+01:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 186368 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x338f |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
88
Monitored processes
38
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 268 | powershell.exe -inputformat none -ExecutionPolicy Bypass -Command "If ($env:PROCESSOR_ARCHITEW6432) { $env:PROCESSOR_ARCHITEW6432 } Else { $env:PROCESSOR_ARCHITECTURE }" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | ns712.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 968 | netsh advfirewall firewall Delete rule name=LetsPRO.exe | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1784 | "C:\Program Files\letsvpn\driver\tapinstall.exe" install "C:\Program Files\letsvpn\driver\OemVista.inf" tap0901 | C:\Program Files\letsvpn\driver\tapinstall.exe | — | ns4872.tmp | |||||||||||
User: admin Company: Windows (R) Win 7 DDK provider Integrity Level: HIGH Description: Windows Setup API Exit code: 0 Version: 6.1.7600.16385 built by: WinDDK Modules
| |||||||||||||||
| 1808 | "C:\Users\admin\AppData\Local\Temp\nse711.tmp\ns4872.tmp" "C:\Program Files\letsvpn\driver\tapinstall.exe" install "C:\Program Files\letsvpn\driver\OemVista.inf" tap0901 | C:\Users\admin\AppData\Local\Temp\nse711.tmp\ns4872.tmp | — | letsvpn-latest.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1936 | "C:\Users\admin\AppData\Local\Temp\nse711.tmp\ns4787.tmp" "C:\Program Files\letsvpn\driver\tapinstall.exe" findall tap0901 | C:\Users\admin\AppData\Local\Temp\nse711.tmp\ns4787.tmp | — | letsvpn-latest.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1956 | netsh advfirewall firewall Delete rule name=lets | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2020 | "C:\Users\admin\AppData\Local\Temp\nse711.tmp\ns712.tmp" powershell.exe -inputformat none -ExecutionPolicy Bypass -Command "If ($env:PROCESSOR_ARCHITEW6432) { $env:PROCESSOR_ARCHITEW6432 } Else { $env:PROCESSOR_ARCHITECTURE }" | C:\Users\admin\AppData\Local\Temp\nse711.tmp\ns712.tmp | — | letsvpn-latest.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2040 | "C:\Users\admin\AppData\Local\Temp\letsvpn-latest.exe" | C:\Users\admin\AppData\Local\Temp\letsvpn-latest.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2128 | "C:\Program Files\letsvpn\driver\tapinstall.exe" findall tap0901 | C:\Program Files\letsvpn\driver\tapinstall.exe | — | ns4787.tmp | |||||||||||
User: admin Company: Windows (R) Win 7 DDK provider Integrity Level: HIGH Description: Windows Setup API Exit code: 0 Version: 6.1.7600.16385 built by: WinDDK Modules
| |||||||||||||||
Total events
31 105
Read events
30 572
Write events
483
Delete events
50
Modification events
| (PID) Process: | (1784) tapinstall.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2312) drvinst.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2348) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2312) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 40000000000000009F5A7BD72FB0D90164030000840D0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2312) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 40000000000000009F5A7BD72FB0D90164030000840D0000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2312) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 73 | |||
| (PID) Process: | (2312) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 40000000000000008543C5D72FB0D90164030000840D0000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2312) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Leave) |
Value: 4000000000000000D1ABF1D82FB0D90164030000840D0000D3070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2312) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppAddInterestingComponents (Enter) |
Value: 4000000000000000D1ABF1D82FB0D90164030000840D0000D4070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2312) drvinst.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppAddInterestingComponents (Leave) |
Value: 4000000000000000475C02D92FB0D90164030000840D0000D4070000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
231
Suspicious files
38
Text files
9
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2256 | letsvpn-latest.exe | C:\Users\admin\AppData\Local\Temp\nse711.tmp\ns712.tmp | executable | |
MD5:3D366250FCF8B755FCE575C75F8C79E4 | SHA256:8BDD996AE4778C6F829E2BCB651C55EFC9EC37EEEA17D259E013B39528DDDBB6 | |||
| 268 | powershell.exe | C:\Users\admin\AppData\Local\Temp\1nftiuwn.02z.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2256 | letsvpn-latest.exe | C:\Users\admin\AppData\Local\Temp\nse711.tmp\nsExec.dll | executable | |
MD5:3D366250FCF8B755FCE575C75F8C79E4 | SHA256:8BDD996AE4778C6F829E2BCB651C55EFC9EC37EEEA17D259E013B39528DDDBB6 | |||
| 2256 | letsvpn-latest.exe | C:\Program Files\letsvpn\driver\OemVista.inf | binary | |
MD5:A00612A10E7AA4AFD6B2A15B1E4C5028 | SHA256:9D5C0548DE3C0F785A88FB1BDB220665F463DC9714D35B6285DCD79D6D72A9BE | |||
| 2256 | letsvpn-latest.exe | C:\Program Files\letsvpn\driver\tap0901.cat | binary | |
MD5:A25E93E90B79430155D97EE38D54979E | SHA256:2BDBA7B2ED13D9DFE10FDE74B5F2012D1B50C7173FFB21F487054E978162AE6C | |||
| 2256 | letsvpn-latest.exe | C:\Program Files\letsvpn\driver\tapinstall.exe | executable | |
MD5:8E30A1D0D2A9844B9DF15100450D41E4 | SHA256:F852A3DCB9B45583CF2361F4024B16ABE97A7C1DA560BF593E50EE61A43A04D7 | |||
| 2256 | letsvpn-latest.exe | C:\Program Files\letsvpn\packages\RELEASES | text | |
MD5:94FCB8D8B4357E38B63AB94D8794A9F4 | SHA256:CB9792CEFD5B0D92D68C1890FDF1ADEC46F4A18AF8AC7E5DF51CA741F77D3DC0 | |||
| 2256 | letsvpn-latest.exe | C:\Program Files\letsvpn\Update.exe | executable | |
MD5:D1ACEF26EC2374BBC71597AF8B98998E | SHA256:27F77EA97BD179D200824F42ADEF1E0E2D04DD41D9BCE6C16C6117AEAD233DEA | |||
| 2256 | letsvpn-latest.exe | C:\Program Files\letsvpn\driver\tap0901.sys | executable | |
MD5:815E58BC7EF97DF42D46D7A24F1251B3 | SHA256:C34A74FD751AAD0014D62CC7DDC879DE878E830B261138B5482943D888438C4D | |||
| 2256 | letsvpn-latest.exe | C:\Program Files\letsvpn\app-3.4.0\CommunityToolkit.Mvvm.dll | executable | |
MD5:60467181F416E9C020CA1179BBC629D1 | SHA256:A7EBA23798E2A3F195DF4069029C2C8EFEC95D1D77E8A2F326867C2C2A5AE863 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
30
DNS requests
10
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3144 | LetsPRO.exe | GET | 101 | 54.169.140.85:80 | http://ws-ap1.pusher.com/app/4fc436ef36f4026102d7?protocol=5&client=pusher-dotnet-client&version=1.1.2 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3144 | LetsPRO.exe | 54.169.140.85:80 | ws-ap1.pusher.com | AMAZON-02 | SG | unknown |
3144 | LetsPRO.exe | 8.8.8.8:53 | — | GOOGLE | US | unknown |
3144 | LetsPRO.exe | 2.23.209.149:443 | www.bing.com | Akamai International B.V. | GB | unknown |
3144 | LetsPRO.exe | 183.2.172.42:443 | www.baidu.com | Chinanet | CN | unknown |
3144 | LetsPRO.exe | 5.255.255.80:443 | www.yandex.com | YANDEX LLC | RU | whitelisted |
3144 | LetsPRO.exe | 142.250.185.196:443 | www.google.com | GOOGLE | US | whitelisted |
3144 | LetsPRO.exe | 52.222.250.220:443 | d1dmgcawtbm6l9.cloudfront.net | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ws-ap1.pusher.com |
| shared |
www.baidu.com |
| whitelisted |
www.yandex.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.google.com |
| whitelisted |
nal.fqoqehwib.com |
| unknown |
chr.alipayassets.com |
| unknown |
d1dmgcawtbm6l9.cloudfront.net |
| unknown |
nit.crash1ytics.com |
| unknown |
in.appcenter.ms |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3144 | LetsPRO.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Websocket update request to external network |