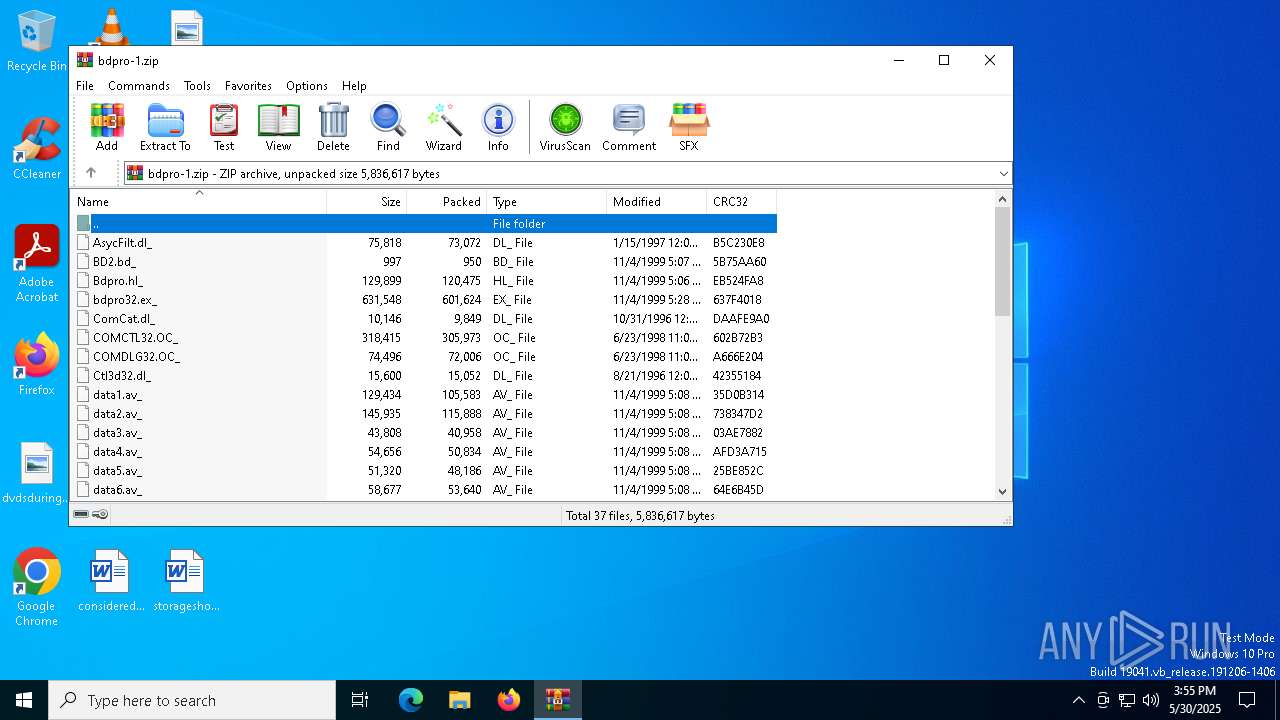
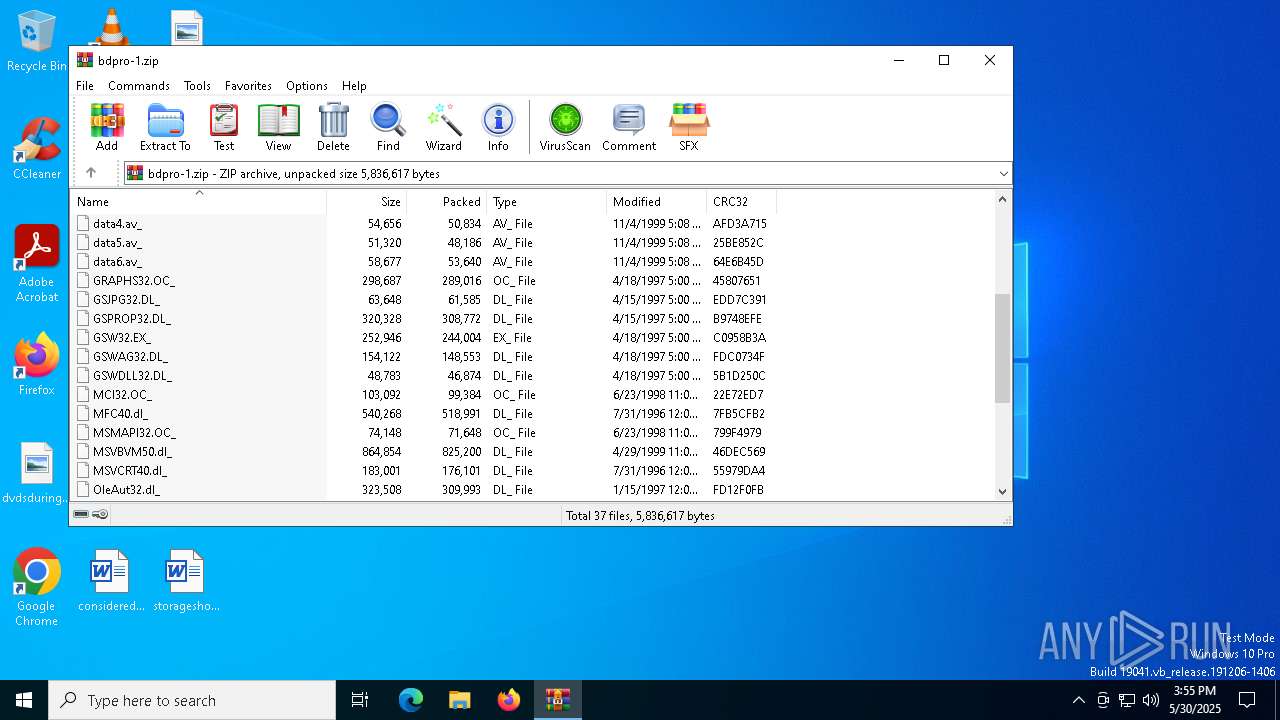
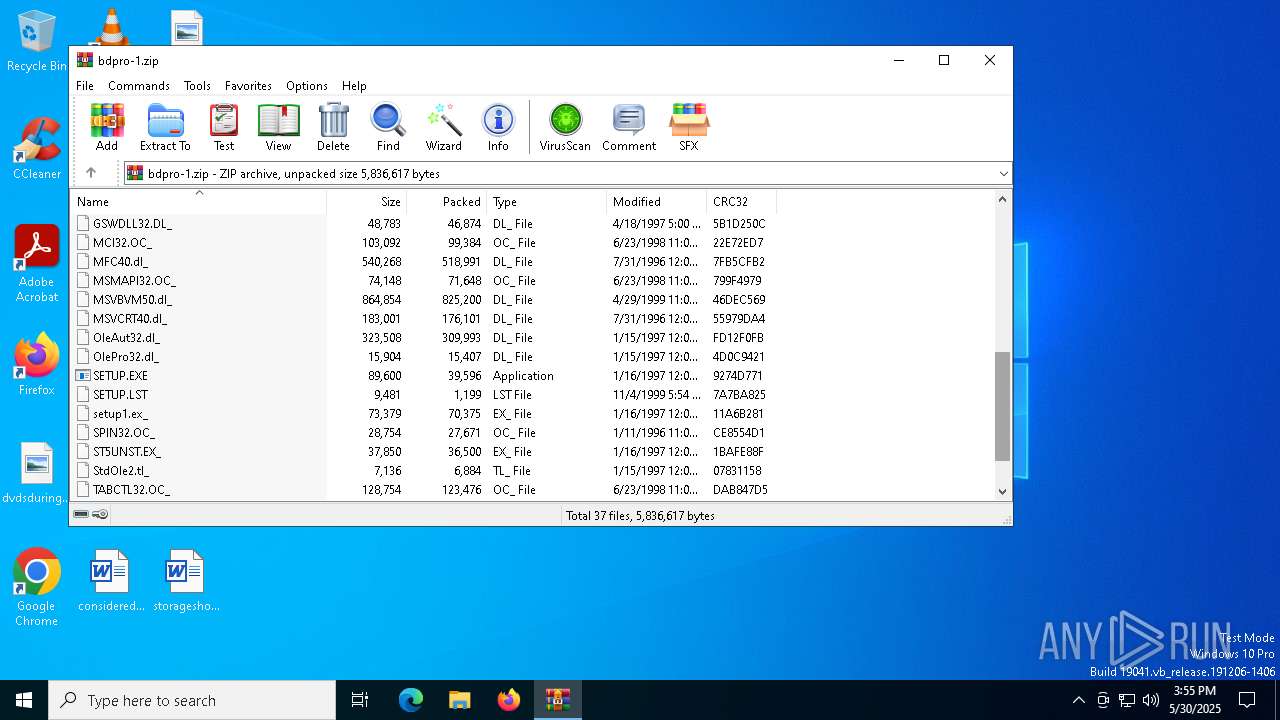
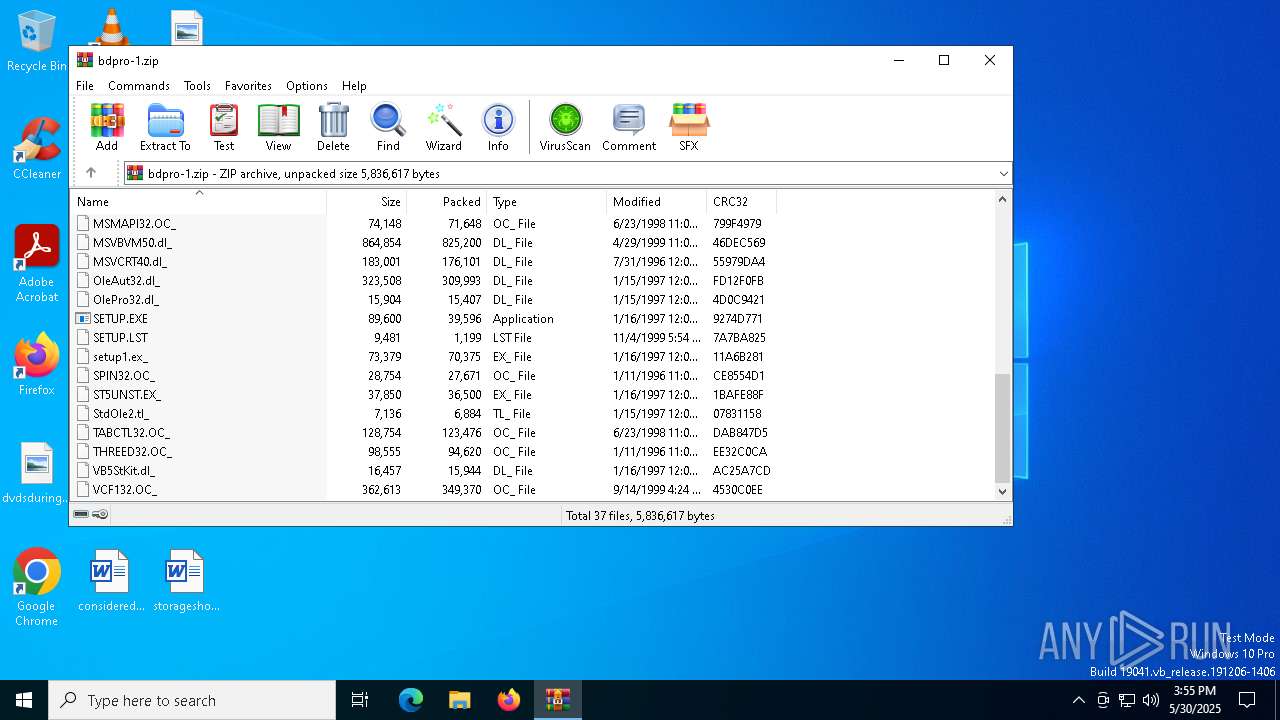
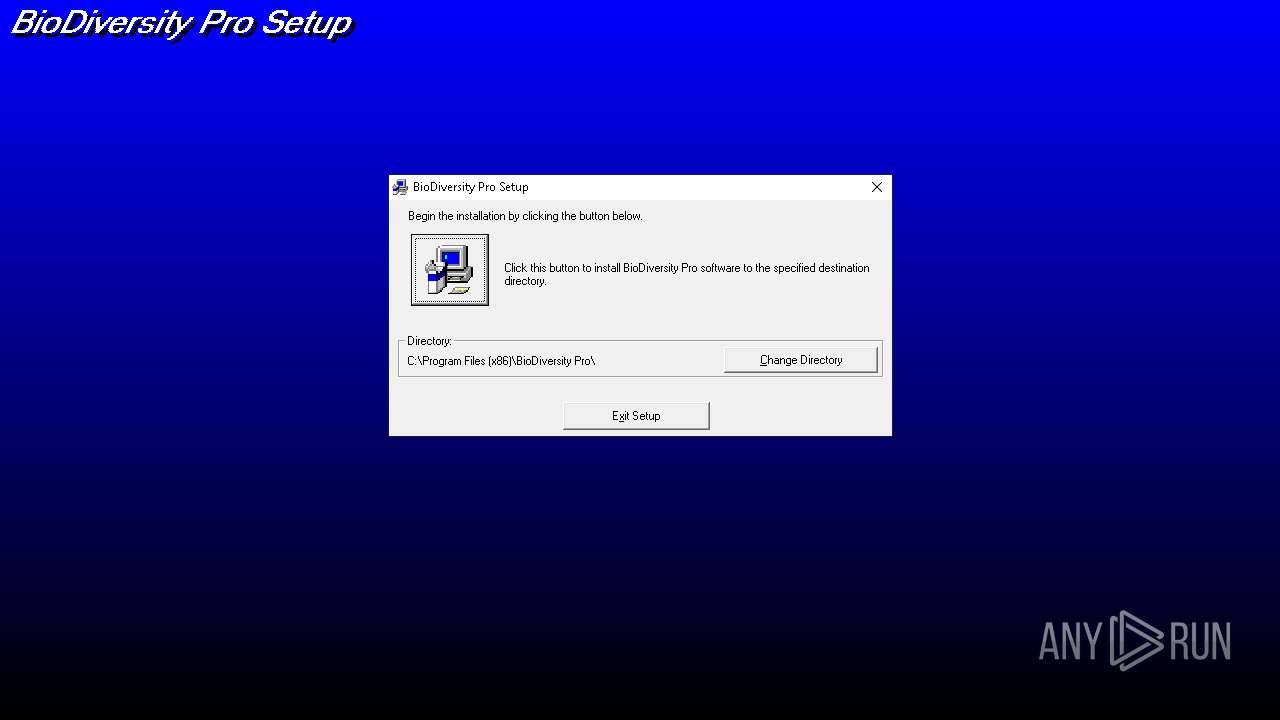
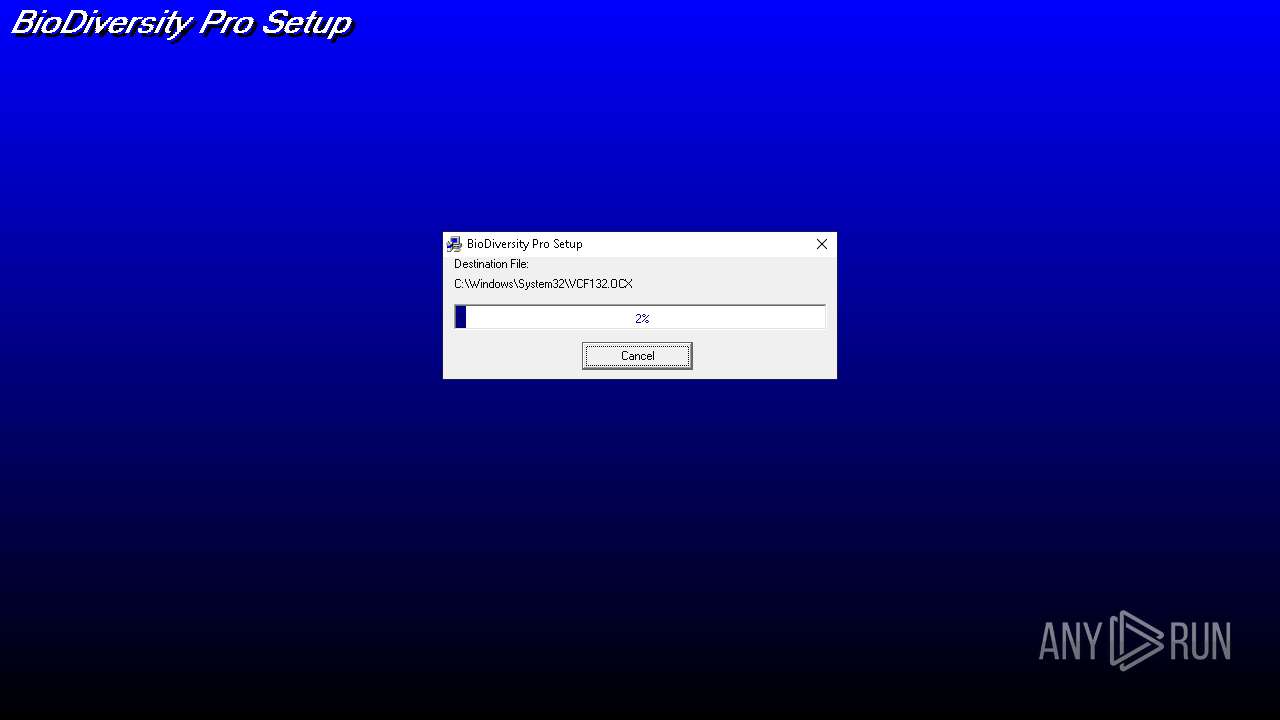
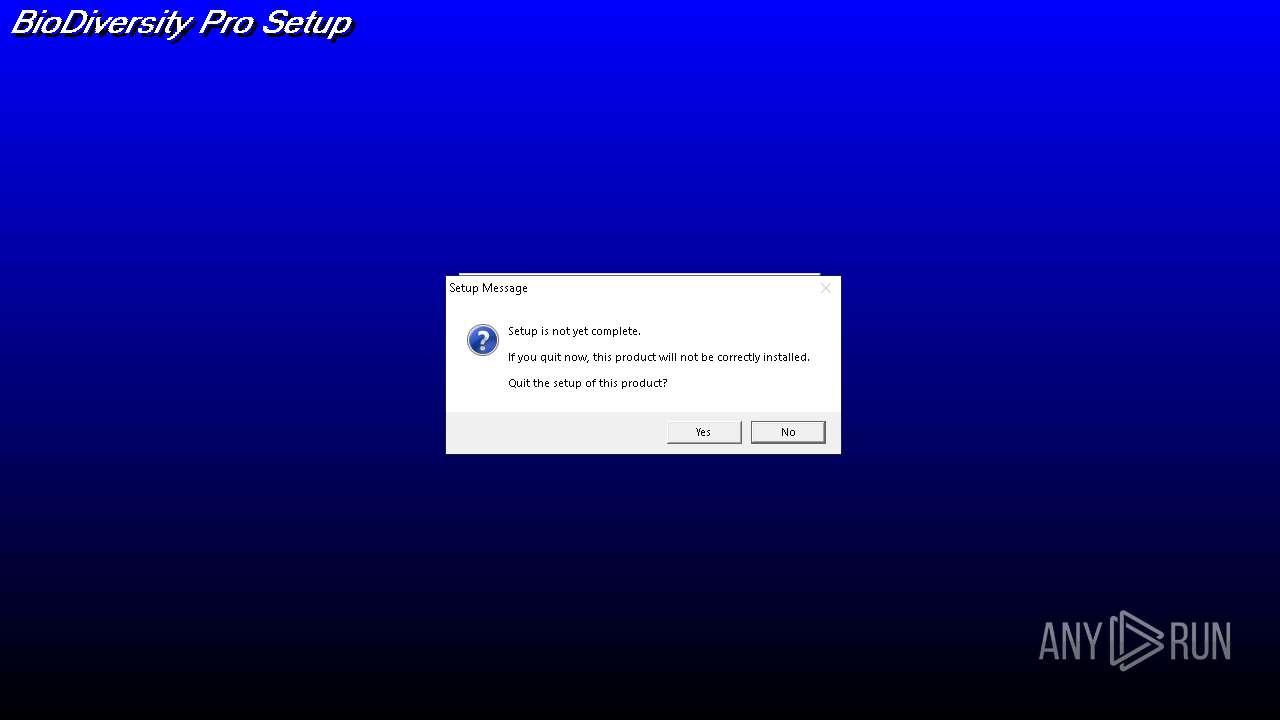
| File name: | bdpro-1.zip |
| Full analysis: | https://app.any.run/tasks/a7352731-9a76-4bc5-b89d-e553e5ddc3fb |
| Verdict: | Malicious activity |
| Analysis date: | May 30, 2025, 15:55:14 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | C2D1472B2716C6004500B51E6C4CFF34 |
| SHA1: | 838549605A384C96B523DAA0904808B2EC41F248 |
| SHA256: | 7C46BC5255A90978381FFF8C558D9EDE6819E3E4D44D84A42E8BD03E92510382 |
| SSDEEP: | 98304:ZigVVczv6y7+Q1c6Ew0ixOpTJ812UU2q8gULHbu+eqPxbPDFW81LmoLdjQJnru5S:QSJ49RbiFcg |
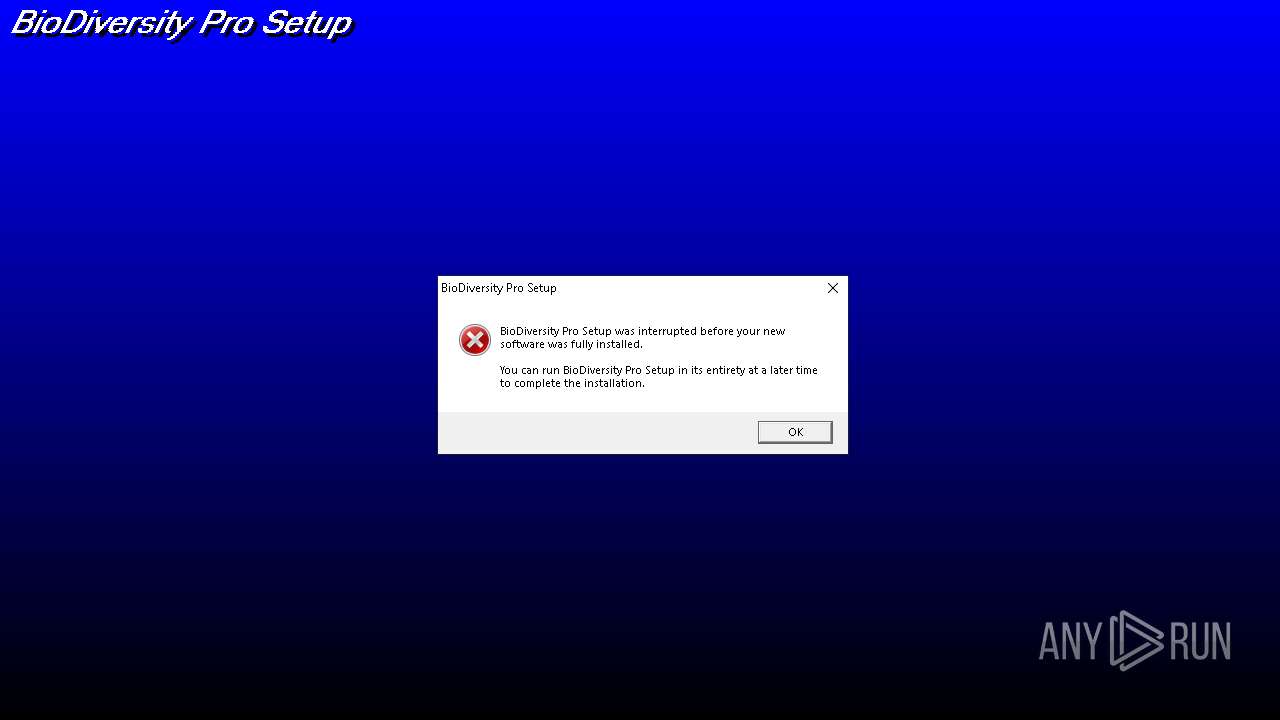
MALICIOUS
Create files in the Startup directory
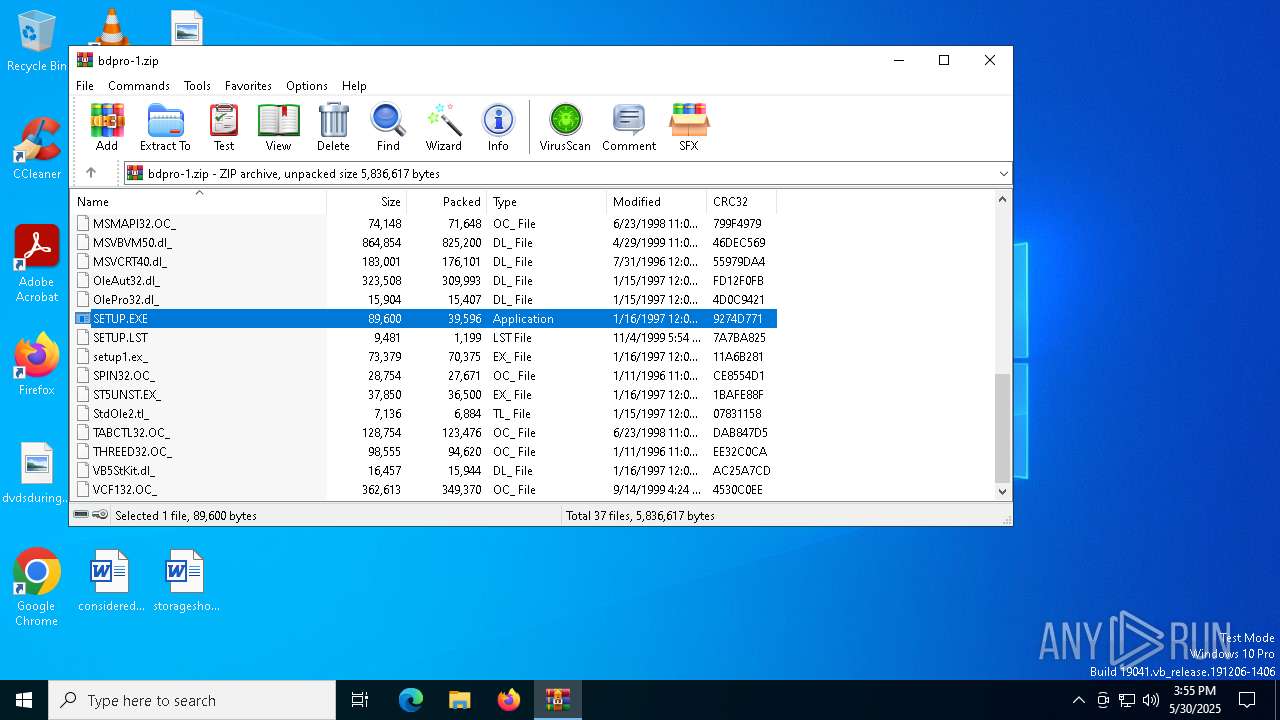
- SETUP.EXE (PID: 736)
SUSPICIOUS
Starts a Microsoft application from unusual location
- SETUP.EXE (PID: 5452)
- SETUP.EXE (PID: 736)
Process drops legitimate windows executable
- WinRAR.exe (PID: 4700)
- SETUP.EXE (PID: 736)
- setup1.exe (PID: 3996)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4700)
Executable content was dropped or overwritten
- SETUP.EXE (PID: 736)
- setup1.exe (PID: 3996)
Creates/Modifies COM task schedule object
- setup1.exe (PID: 3996)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 4700)
- SETUP.EXE (PID: 736)
- setup1.exe (PID: 3996)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4700)
Checks supported languages
- SETUP.EXE (PID: 736)
- setup1.exe (PID: 3996)
- ST5UNST.EXE (PID: 7856)
- bdpro32.exe (PID: 5048)
- bdpro32.exe (PID: 6488)
Reads the computer name
- SETUP.EXE (PID: 736)
- setup1.exe (PID: 3996)
- ST5UNST.EXE (PID: 7856)
- bdpro32.exe (PID: 5048)
- bdpro32.exe (PID: 6488)
Creates files or folders in the user directory
- SETUP.EXE (PID: 736)
Launch of the file from Startup directory
- SETUP.EXE (PID: 736)
Create files in a temporary directory
- setup1.exe (PID: 3996)
Creates files in the program directory
- setup1.exe (PID: 3996)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1999:11:04 17:08:04 |
| ZipCRC: | 0xafd3a715 |
| ZipCompressedSize: | 50834 |
| ZipUncompressedSize: | 54656 |
| ZipFileName: | data4.av_ |
Total processes
130
Monitored processes
9
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
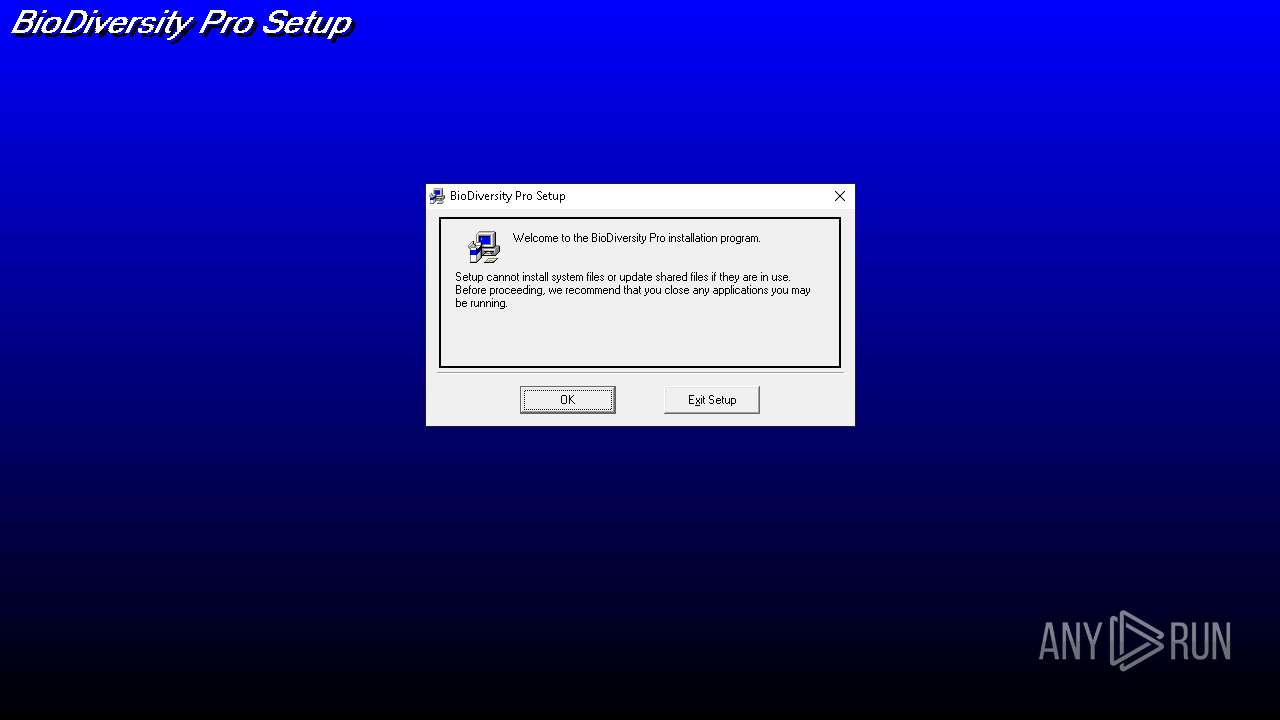
| 736 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa4700.34406\SETUP.EXE" | C:\Users\admin\AppData\Local\Temp\Rar$EXa4700.34406\SETUP.EXE | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Setup Bootstrap for Visual Basic Setup Toolkit Exit code: 0 Version: 5.00.3716 Modules
| |||||||||||||||
| 3996 | C:\Windows\setup1.exe "C:\Users\admin\AppData\Local\Temp\Rar$EXa4700.34406\" "C:\WINDOWS\ST5UNST.000" "C:\WINDOWS\ST5UNST.EXE" | C:\Windows\setup1.exe | SETUP.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual Basic 5.0 Setup Toolkit Exit code: 0 Version: 5.00.3716 Modules
| |||||||||||||||
| 4700 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\bdpro-1.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5048 | "C:\Program Files (x86)\BioDiversity Pro\bdpro32.exe" /REGSERVER | C:\Program Files (x86)\BioDiversity Pro\bdpro32.exe | — | setup1.exe | |||||||||||
User: admin Company: The Natural History Museum & The Scottish Association For Marine Science Integrity Level: HIGH Description: Ecological Analysis package Exit code: 0 Version: 2.00 Modules
| |||||||||||||||
| 5064 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5452 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa4700.34406\SETUP.EXE" | C:\Users\admin\AppData\Local\Temp\Rar$EXa4700.34406\SETUP.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Setup Bootstrap for Visual Basic Setup Toolkit Exit code: 3221226540 Version: 5.00.3716 Modules
| |||||||||||||||
| 5776 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6488 | "C:\Program Files (x86)\BioDiversity Pro\bdpro32.exe" /UnRegServer | C:\Program Files (x86)\BioDiversity Pro\bdpro32.exe | — | ST5UNST.EXE | |||||||||||
User: admin Company: The Natural History Museum & The Scottish Association For Marine Science Integrity Level: HIGH Description: Ecological Analysis package Exit code: 0 Version: 2.00 Modules
| |||||||||||||||
| 7856 | C:\WINDOWS\ST5UNST.EXE -n "C:\Windows\ST5UNST.000" -e 2 -f -w 3996 | C:\Windows\ST5UNST.EXE | — | setup1.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Application Removal Program for Visual Basic Setup Toolkit Version: 5.00.3716 Modules
| |||||||||||||||
Total events
3 663
Read events
2 664
Write events
263
Delete events
736
Modification events
| (PID) Process: | (4700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\bdpro-1.zip | |||
| (PID) Process: | (4700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4700) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (736) SETUP.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\Windows\System32\VB5StKit.dll |
Value: 1 | |||
| (PID) Process: | (736) SETUP.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\SharedDlls |
| Operation: | write | Name: | C:\Windows\System32\StdOle2.tlb |
Value: 2 | |||
Executable files
54
Suspicious files
1
Text files
6
Unknown types
57
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4700.34406\Bdpro.hl_ | ex_ | |
MD5:FF7E4628061F66DA2FB59BF5715C9B3C | SHA256:D878E547F0B98E8C07FD24DBBF158E2C0EC2FD60D0EE366C90899DAEA021F46D | |||
| 4700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4700.34406\BD2.bd_ | ex_ | |
MD5:2CE39EC2C9C5EDDBC7C3D92BD5D6C336 | SHA256:D9781E0B48A268E2F5025C479764C290C8A80D71ABF4FEB539C9E14AC1991DD1 | |||
| 4700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4700.34406\COMDLG32.OC_ | ex_ | |
MD5:BF6DCF6167B5F115806F20A23173BFC3 | SHA256:671AC95F997EA4686BC51EB833B13D7CFAFD4A369663BF136561E663B9C0A408 | |||
| 4700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4700.34406\data4.av_ | ex_ | |
MD5:7802553ACF1EC2BEA5239D20CA7C57B1 | SHA256:E40BF7CDAE45B25360FB57279A80EAE8E8446C511BC74E3A47082F1273BCA63F | |||
| 4700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4700.34406\bdpro32.ex_ | ex_ | |
MD5:0269ACAB6F62D4B964DD75A469941BAC | SHA256:829F30EFEEE9DE66DB01735B745F56D973522F38429EE10900EC7247E327B315 | |||
| 4700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4700.34406\COMCTL32.OC_ | ex_ | |
MD5:EC24FC1B3C360D4C623CB48ECE1F94AD | SHA256:2F4DA8F70991ECE6C96DC0B574506A794EBA9EF6CF0FCDA2A35B3E97BF35FE29 | |||
| 4700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4700.34406\GSPROP32.DL_ | ex_ | |
MD5:29F3F2B7074BDE34ED9E841ED7D1A772 | SHA256:76B1249648A590D9A59D0692CA68284ED7B7DF094ABEF6D5A99B008B42A63EC6 | |||
| 4700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4700.34406\GSW32.EX_ | ex_ | |
MD5:7D6EA9D13E22EE2A1638B19A07D1C13C | SHA256:399B448BDFF21B289BD44819316CFB550A59BE6FA85EA59CFC19B31778D12471 | |||
| 4700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4700.34406\data6.av_ | ex_ | |
MD5:21175E88ED87E8A73D9AB8CF7D25CD18 | SHA256:AEAC2B1C321060580268469047225D62F3ACB13B13D69981CE2170ECAB804640 | |||
| 4700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa4700.34406\GSJPG32.DL_ | ex_ | |
MD5:D379432DDE5BFFB968B006964FF2EDBB | SHA256:A9620E627792EE3248AFF4D22814C76FBFB27DFC0BA718B21B36D55ACC2366B5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
19
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6572 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6572 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
3896 | RUXIMICS.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7548 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 20.190.160.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |