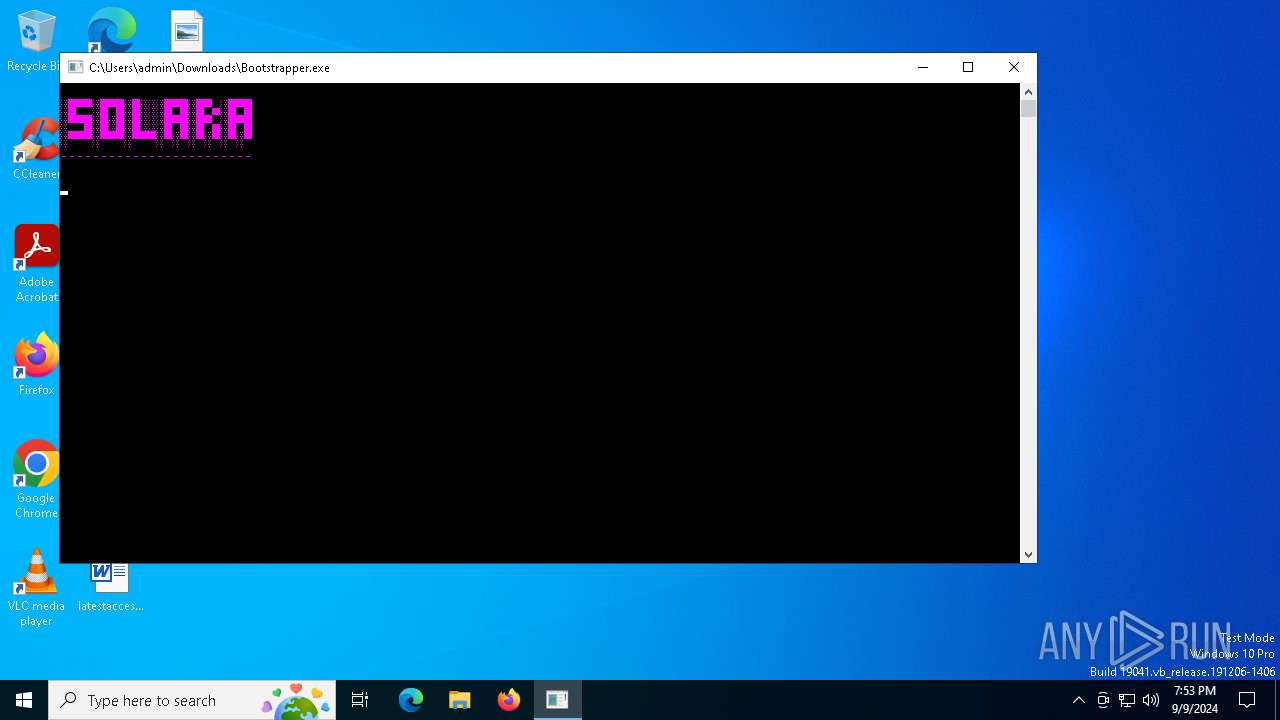
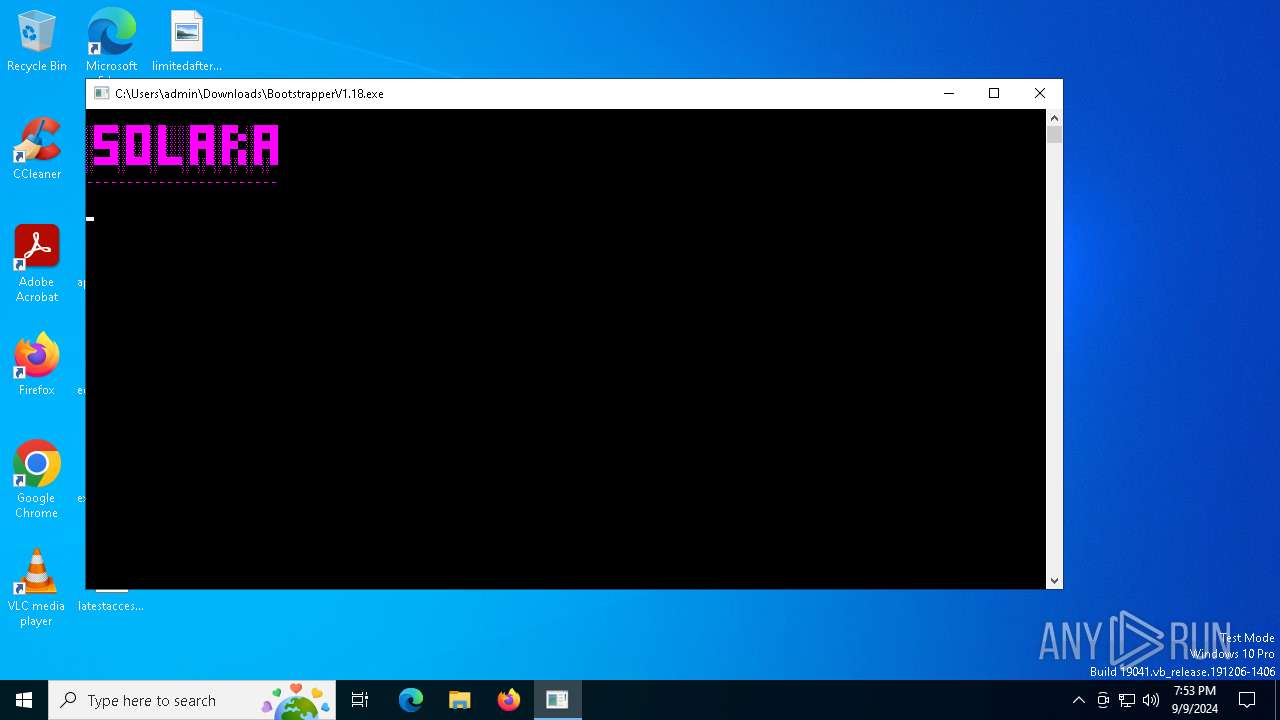
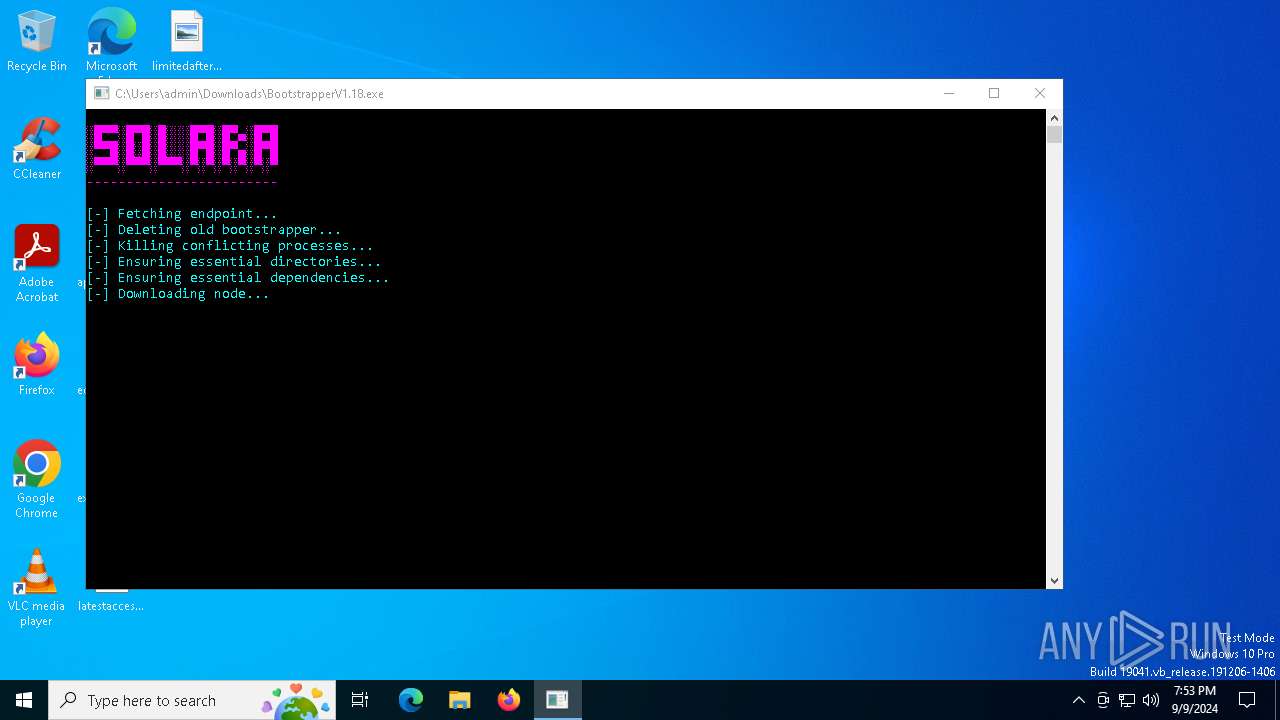
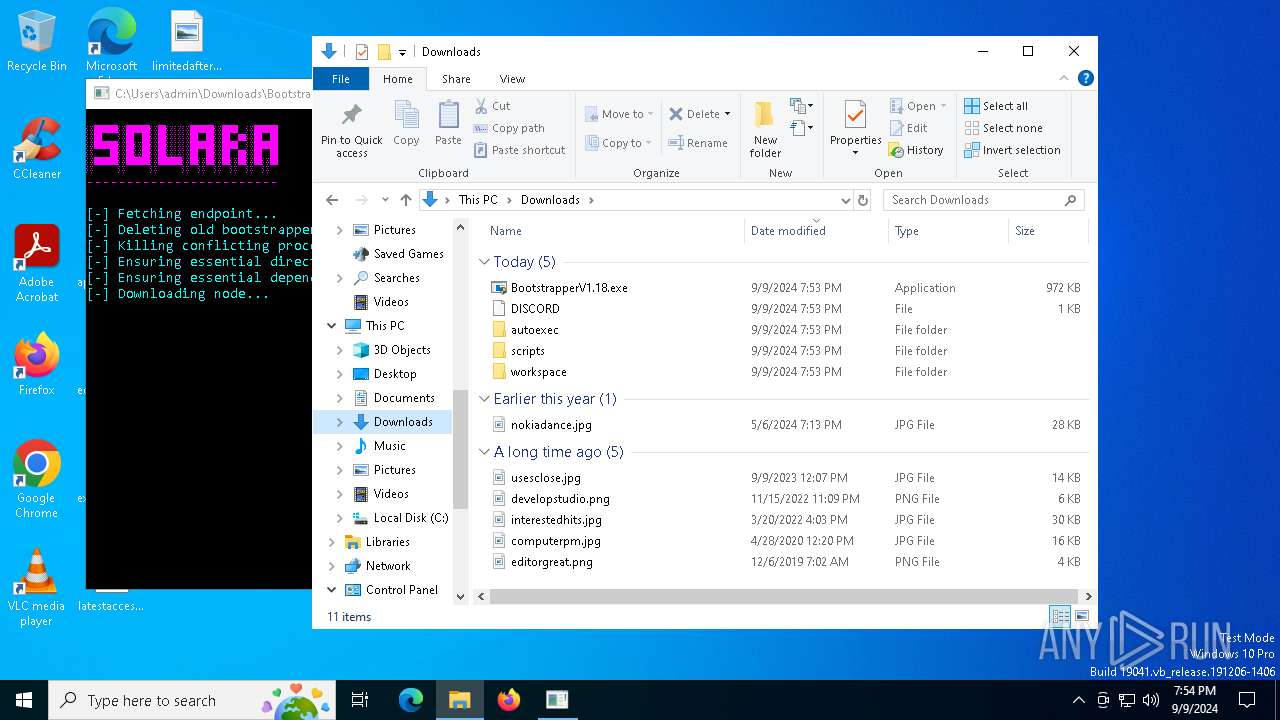
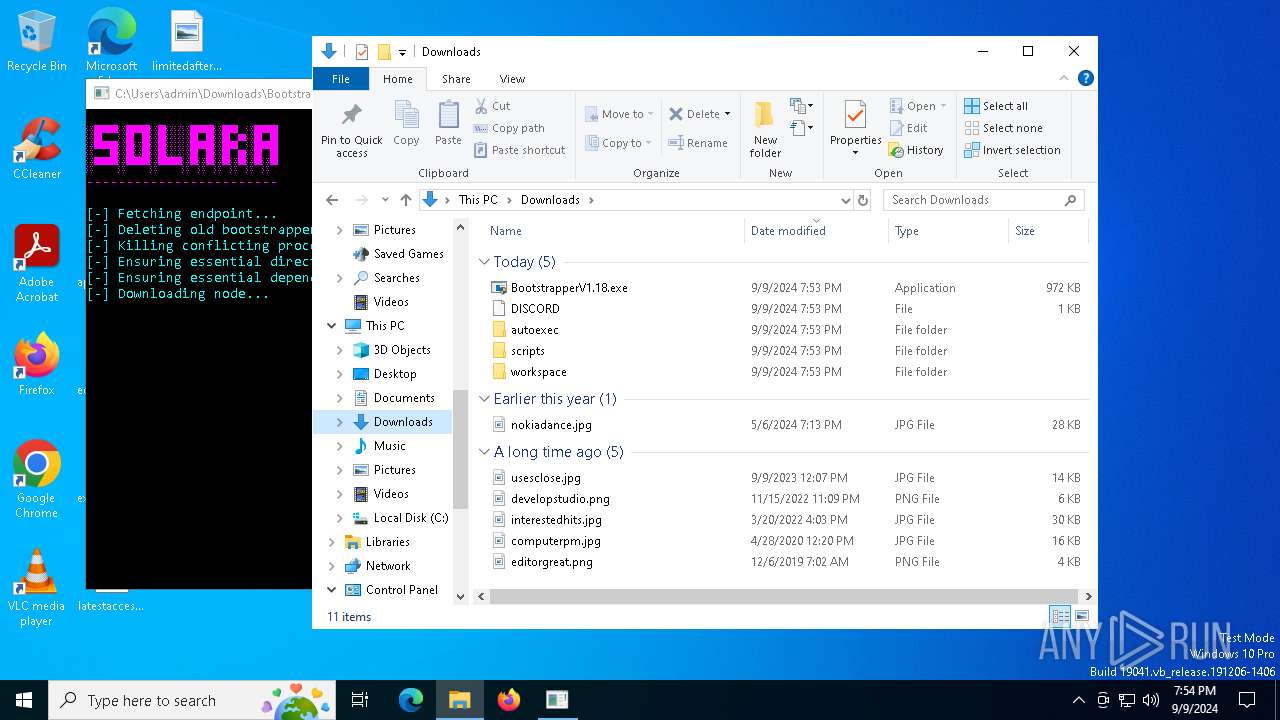
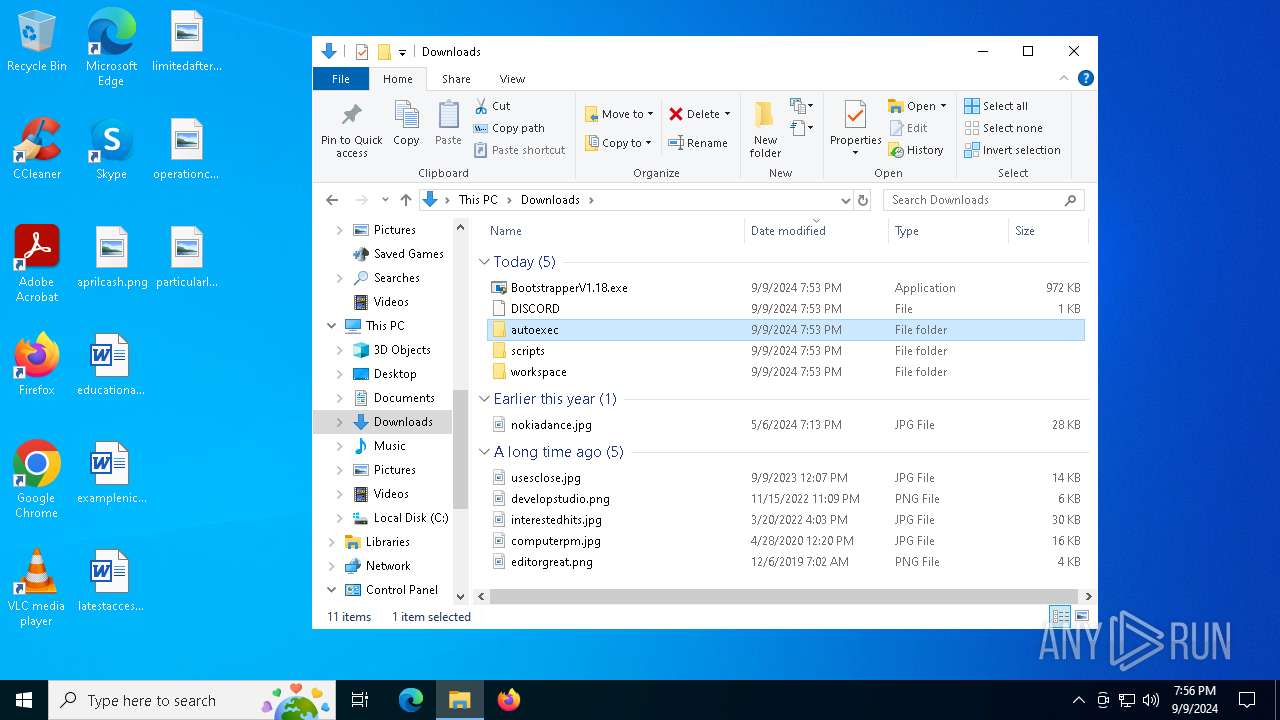
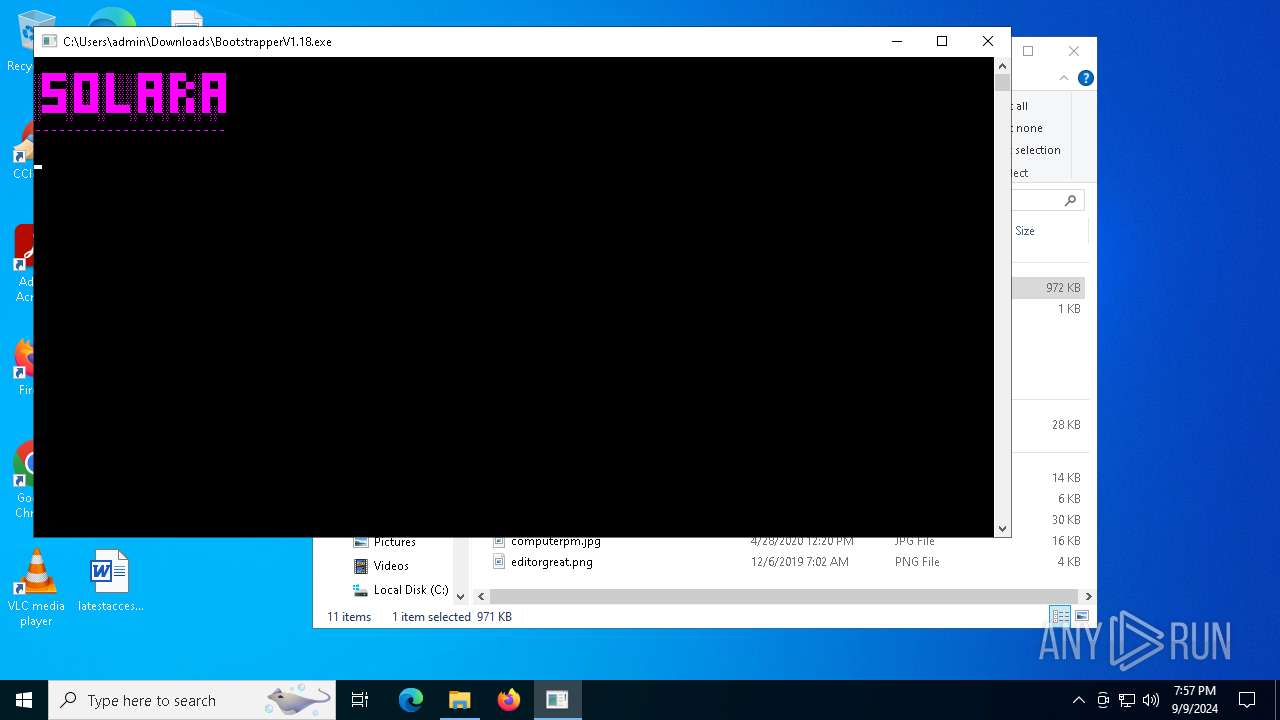
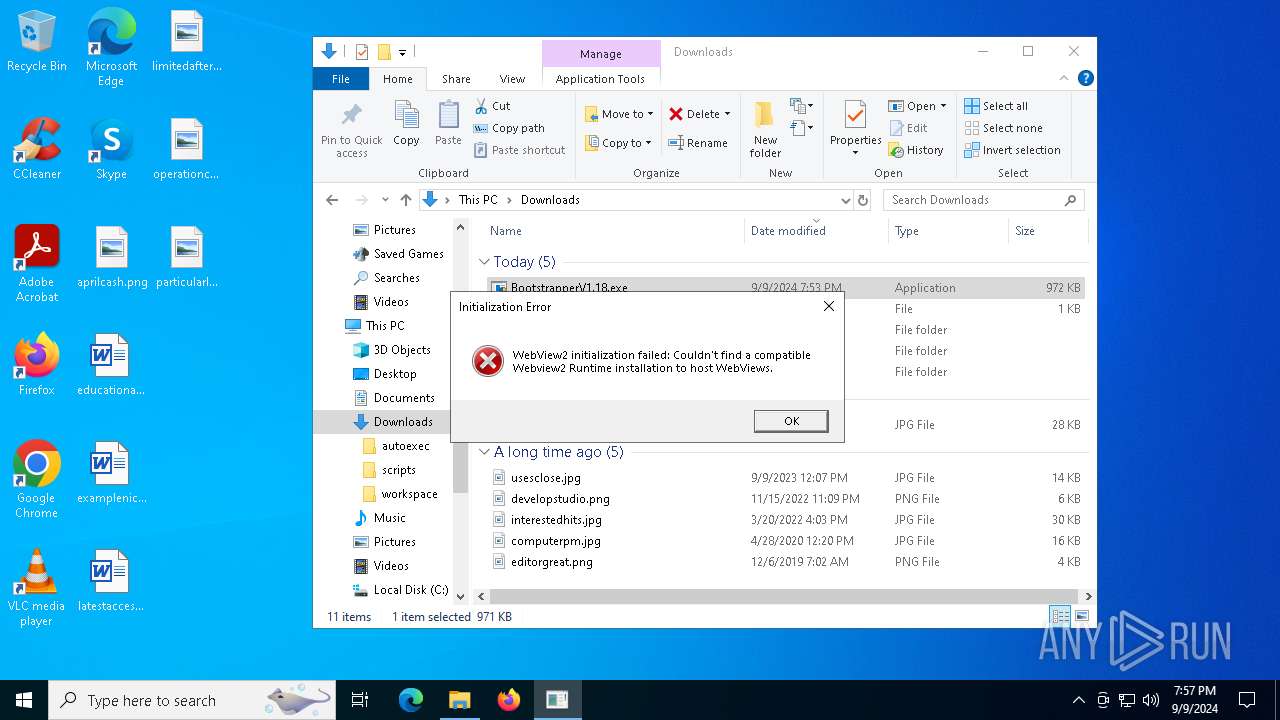
| File name: | Bootstrapper.exe |
| Full analysis: | https://app.any.run/tasks/30b41394-d5ca-4617-83cd-b1fb3fab7ada |
| Verdict: | Malicious activity |
| Analysis date: | September 09, 2024, 19:53:25 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (console) x86-64 Mono/.Net assembly, for MS Windows |
| MD5: | 4B94B989B0FE7BEC6311153B309DFE81 |
| SHA1: | BB50A4BB8A66F0105C5B74F32CD114C672010B22 |
| SHA256: | 7C4283F5E620B2506BCB273F947DEF4435D95E143AE3067A783FD3ADC873A659 |
| SSDEEP: | 24576:fe/C5Nf3boaQlh2a1opZx73dbbfygeedN:nToaQlhP1opZx73eed |
MALICIOUS
No malicious indicators.SUSPICIOUS
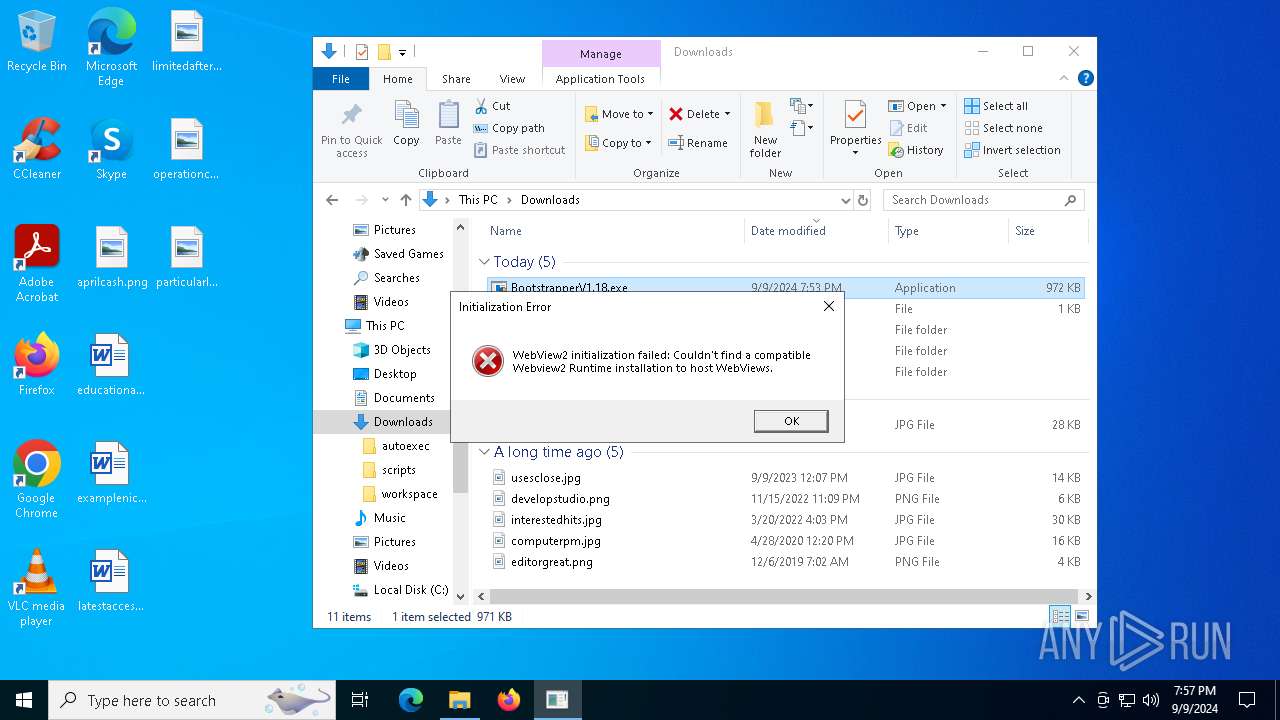
Reads security settings of Internet Explorer
- Bootstrapper.exe (PID: 5516)
- BootstrapperV1.18.exe (PID: 6352)
- msiexec.exe (PID: 740)
- msiexec.exe (PID: 6768)
- BootstrapperV1.18.exe (PID: 3272)
- Solara.exe (PID: 6744)
- BootstrapperV1.18.exe (PID: 7036)
- Solara.exe (PID: 2628)
Executable content was dropped or overwritten
- Bootstrapper.exe (PID: 5516)
- BootstrapperV1.18.exe (PID: 6352)
Reads the date of Windows installation
- Bootstrapper.exe (PID: 5516)
- BootstrapperV1.18.exe (PID: 6352)
- BootstrapperV1.18.exe (PID: 3272)
- BootstrapperV1.18.exe (PID: 7036)
Checks Windows Trust Settings
- msiexec.exe (PID: 5760)
Uses WEVTUTIL.EXE to install publishers and event logs from the manifest
- wevtutil.exe (PID: 6928)
- msiexec.exe (PID: 740)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 5760)
The process drops C-runtime libraries
- BootstrapperV1.18.exe (PID: 6352)
Process drops legitimate windows executable
- BootstrapperV1.18.exe (PID: 6352)
Executes script using NodeJS
- node.exe (PID: 6668)
- node.exe (PID: 6916)
Reads the BIOS version
- Solara.exe (PID: 6744)
- Solara.exe (PID: 2628)
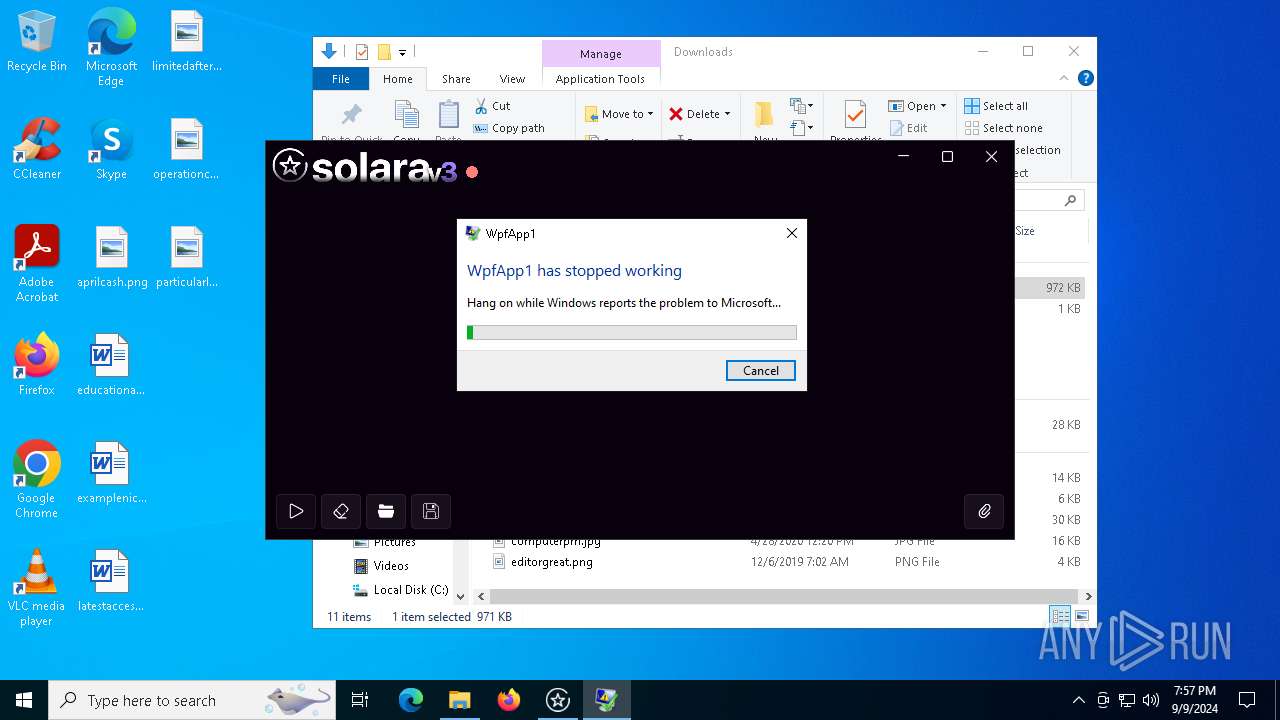
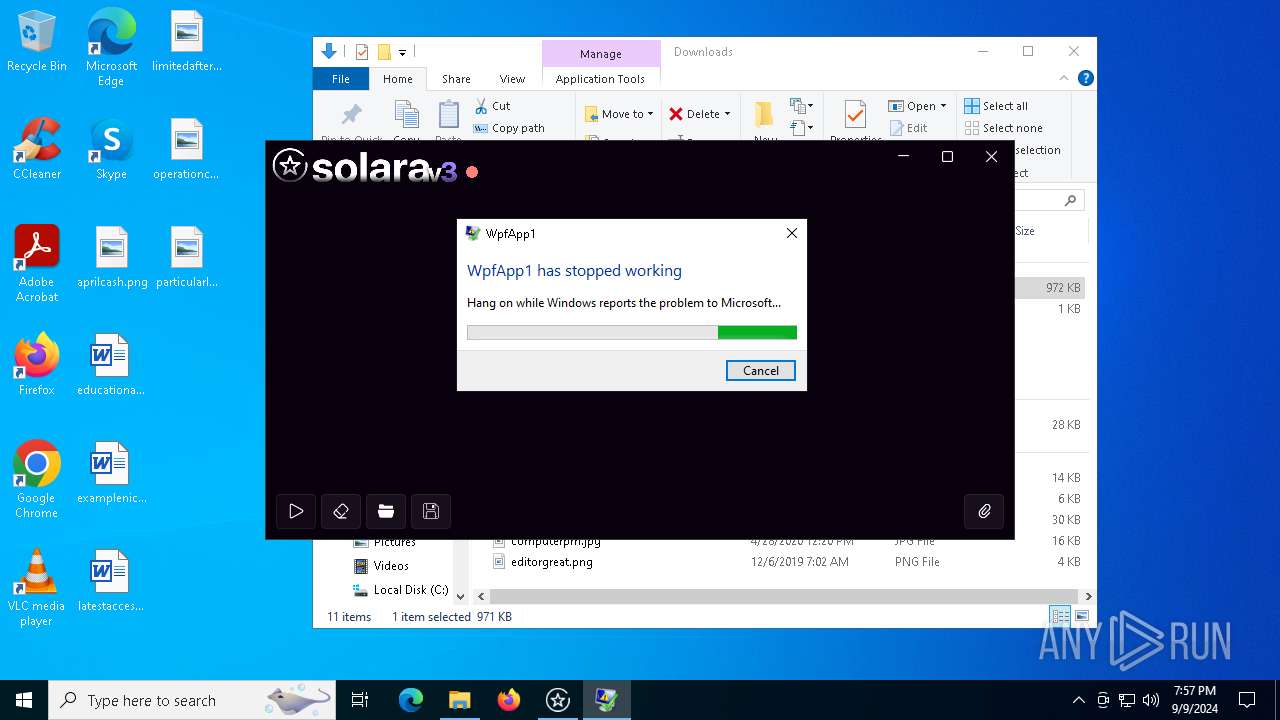
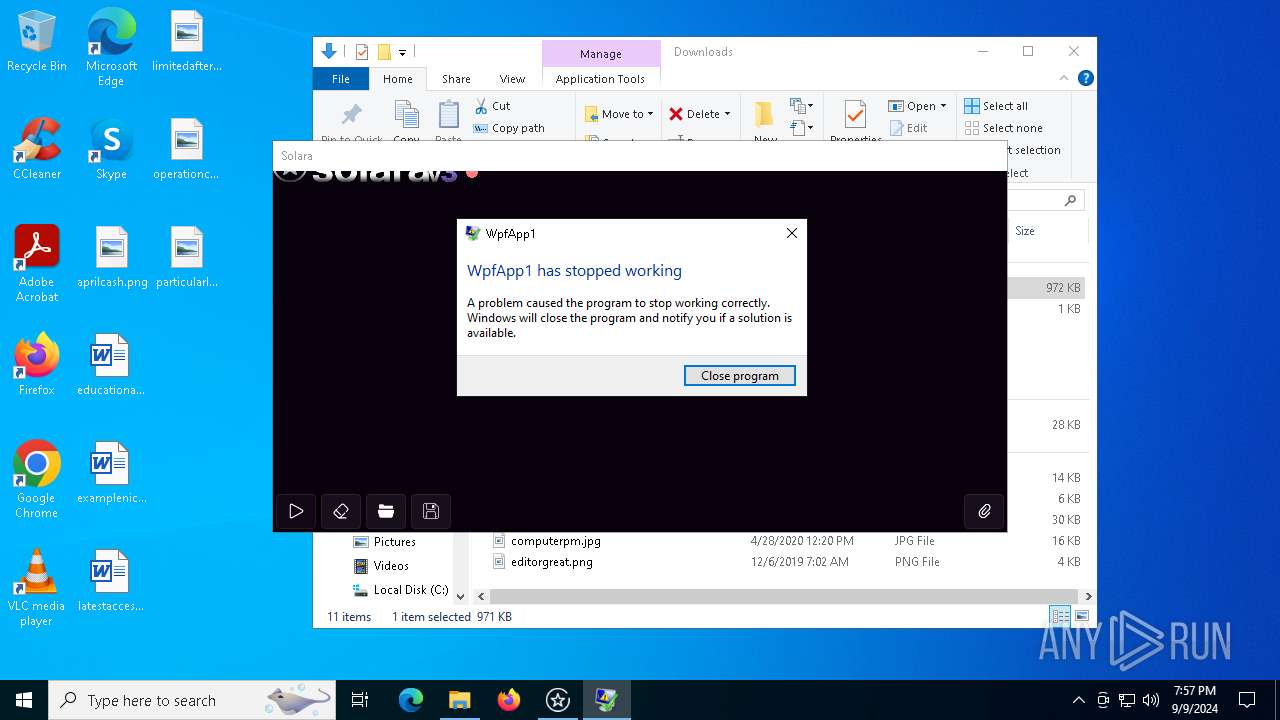
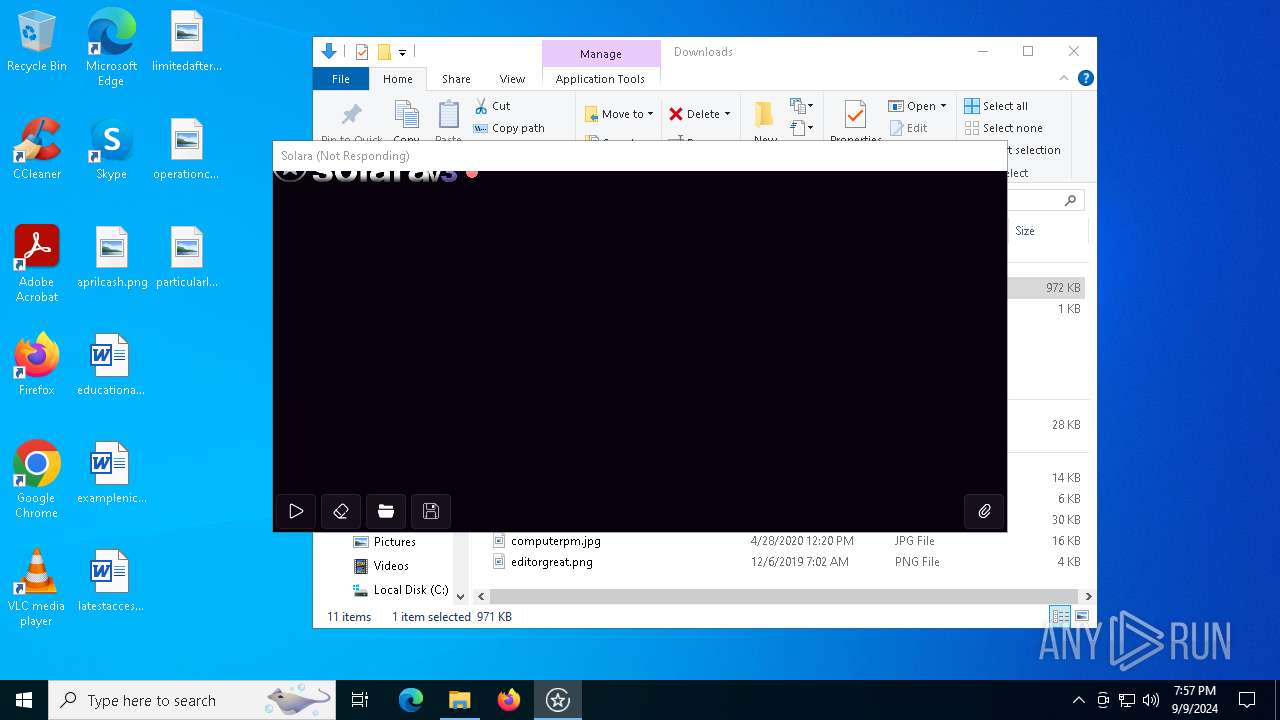
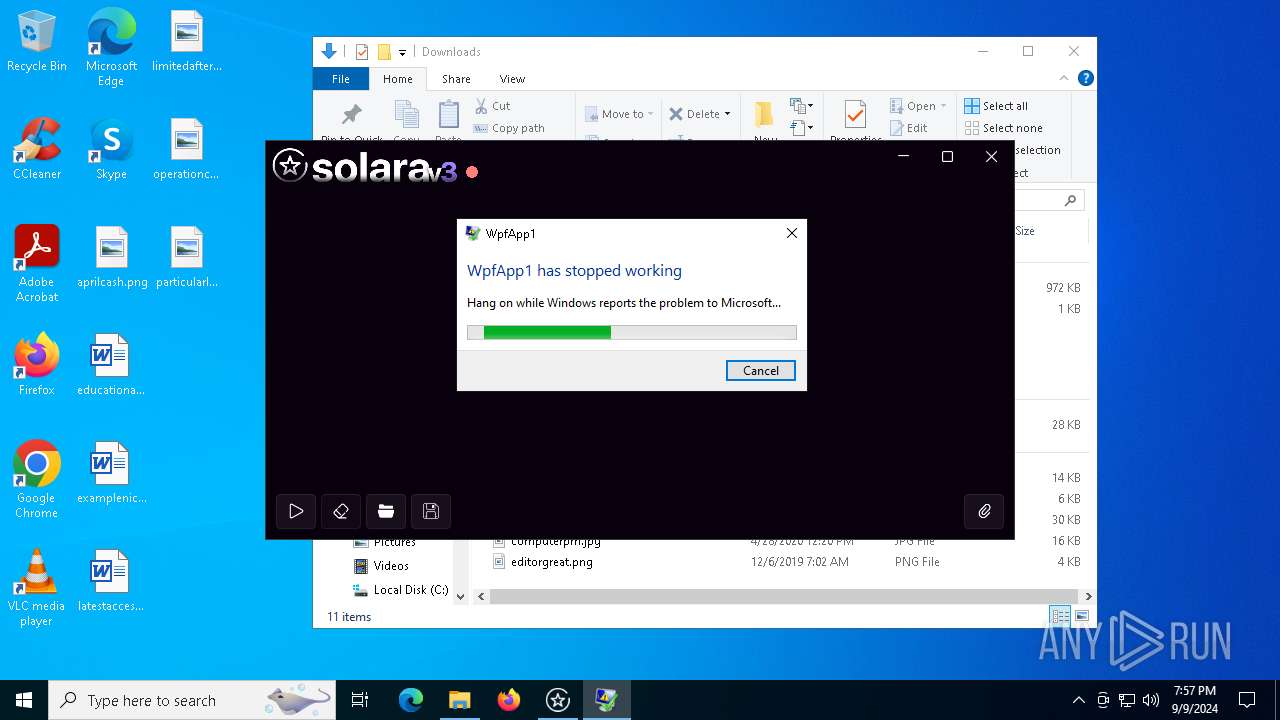
Executes application which crashes
- Solara.exe (PID: 6744)
- Solara.exe (PID: 2628)
Creates file in the systems drive root
- Solara.exe (PID: 2628)
INFO
Reads the machine GUID from the registry
- Bootstrapper.exe (PID: 5516)
- msiexec.exe (PID: 5760)
- BootstrapperV1.18.exe (PID: 6352)
- BootstrapperV1.18.exe (PID: 3272)
- Solara.exe (PID: 6744)
- BootstrapperV1.18.exe (PID: 7036)
- Solara.exe (PID: 2628)
Reads the software policy settings
- Bootstrapper.exe (PID: 5516)
- BootstrapperV1.18.exe (PID: 6352)
- msiexec.exe (PID: 5760)
- BootstrapperV1.18.exe (PID: 3272)
- Solara.exe (PID: 6744)
- WerFault.exe (PID: 6256)
- BootstrapperV1.18.exe (PID: 7036)
- Solara.exe (PID: 2628)
- WerFault.exe (PID: 6904)
Checks supported languages
- Bootstrapper.exe (PID: 5516)
- BootstrapperV1.18.exe (PID: 6352)
- msiexec.exe (PID: 5760)
- msiexec.exe (PID: 6768)
- msiexec.exe (PID: 740)
- msiexec.exe (PID: 4056)
- node.exe (PID: 6604)
- BootstrapperV1.18.exe (PID: 3272)
- node.exe (PID: 6668)
- BootstrapperV1.18.exe (PID: 7036)
- Solara.exe (PID: 6744)
- node.exe (PID: 1164)
- Solara.exe (PID: 2628)
- node.exe (PID: 6916)
Disables trace logs
- Bootstrapper.exe (PID: 5516)
- BootstrapperV1.18.exe (PID: 6352)
- BootstrapperV1.18.exe (PID: 3272)
- Solara.exe (PID: 6744)
- BootstrapperV1.18.exe (PID: 7036)
- Solara.exe (PID: 2628)
Reads Environment values
- Bootstrapper.exe (PID: 5516)
- BootstrapperV1.18.exe (PID: 6352)
- BootstrapperV1.18.exe (PID: 3272)
- Solara.exe (PID: 6744)
- BootstrapperV1.18.exe (PID: 7036)
- Solara.exe (PID: 2628)
Reads the computer name
- Bootstrapper.exe (PID: 5516)
- msiexec.exe (PID: 5760)
- BootstrapperV1.18.exe (PID: 6352)
- msiexec.exe (PID: 4056)
- msiexec.exe (PID: 6768)
- msiexec.exe (PID: 740)
- BootstrapperV1.18.exe (PID: 3272)
- Solara.exe (PID: 6744)
- BootstrapperV1.18.exe (PID: 7036)
- Solara.exe (PID: 2628)
Checks proxy server information
- Bootstrapper.exe (PID: 5516)
- BootstrapperV1.18.exe (PID: 6352)
- BootstrapperV1.18.exe (PID: 3272)
- Solara.exe (PID: 6744)
- WerFault.exe (PID: 6256)
- BootstrapperV1.18.exe (PID: 7036)
- Solara.exe (PID: 2628)
- WerFault.exe (PID: 6904)
Process checks computer location settings
- Bootstrapper.exe (PID: 5516)
- BootstrapperV1.18.exe (PID: 6352)
- BootstrapperV1.18.exe (PID: 3272)
- BootstrapperV1.18.exe (PID: 7036)
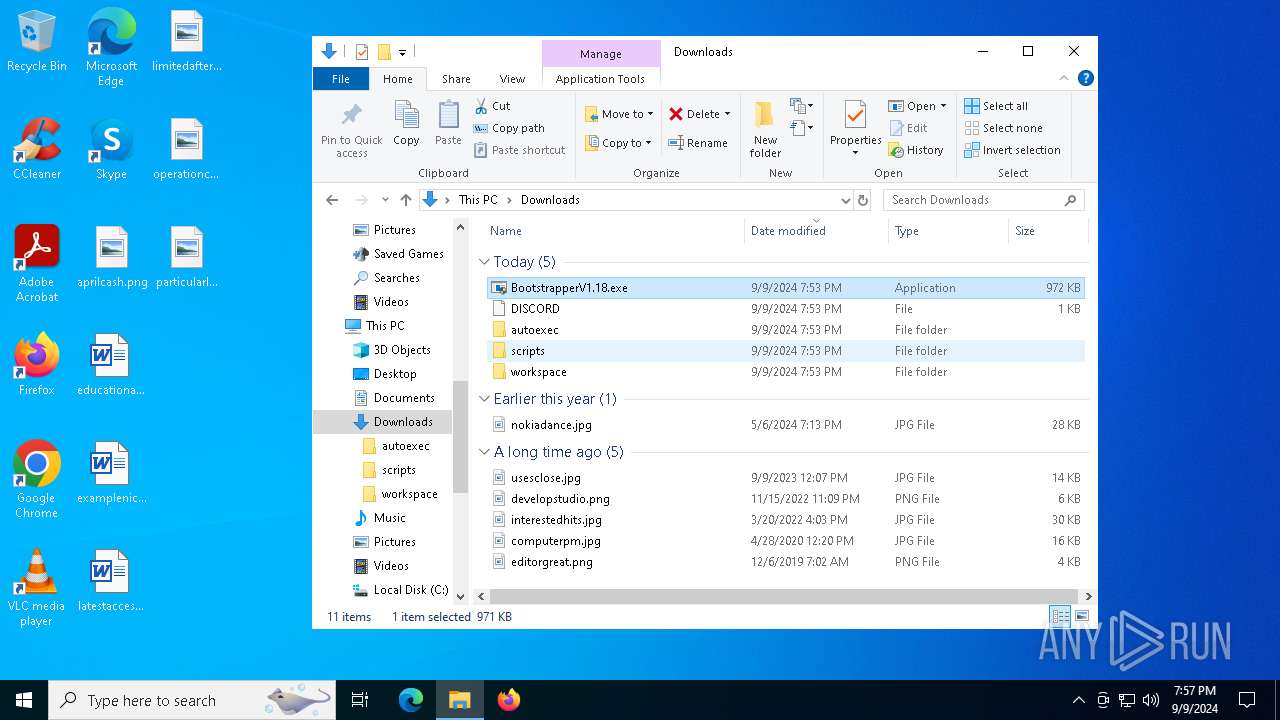
The process uses the downloaded file
- Bootstrapper.exe (PID: 5516)
- BootstrapperV1.18.exe (PID: 6352)
- BootstrapperV1.18.exe (PID: 3272)
- BootstrapperV1.18.exe (PID: 7036)
Create files in a temporary directory
- BootstrapperV1.18.exe (PID: 6352)
Creates files in the program directory
- BootstrapperV1.18.exe (PID: 6352)
Creates files or folders in the user directory
- msiexec.exe (PID: 5760)
- WerFault.exe (PID: 6256)
- WerFault.exe (PID: 6904)
Executable content was dropped or overwritten
- msiexec.exe (PID: 5760)
Application launched itself
- msiexec.exe (PID: 5760)
Manual execution by a user
- BootstrapperV1.18.exe (PID: 3272)
- BootstrapperV1.18.exe (PID: 6284)
- BootstrapperV1.18.exe (PID: 6996)
- BootstrapperV1.18.exe (PID: 7036)
Creates a software uninstall entry
- msiexec.exe (PID: 5760)
Process checks whether UAC notifications are on
- Solara.exe (PID: 6744)
- Solara.exe (PID: 2628)
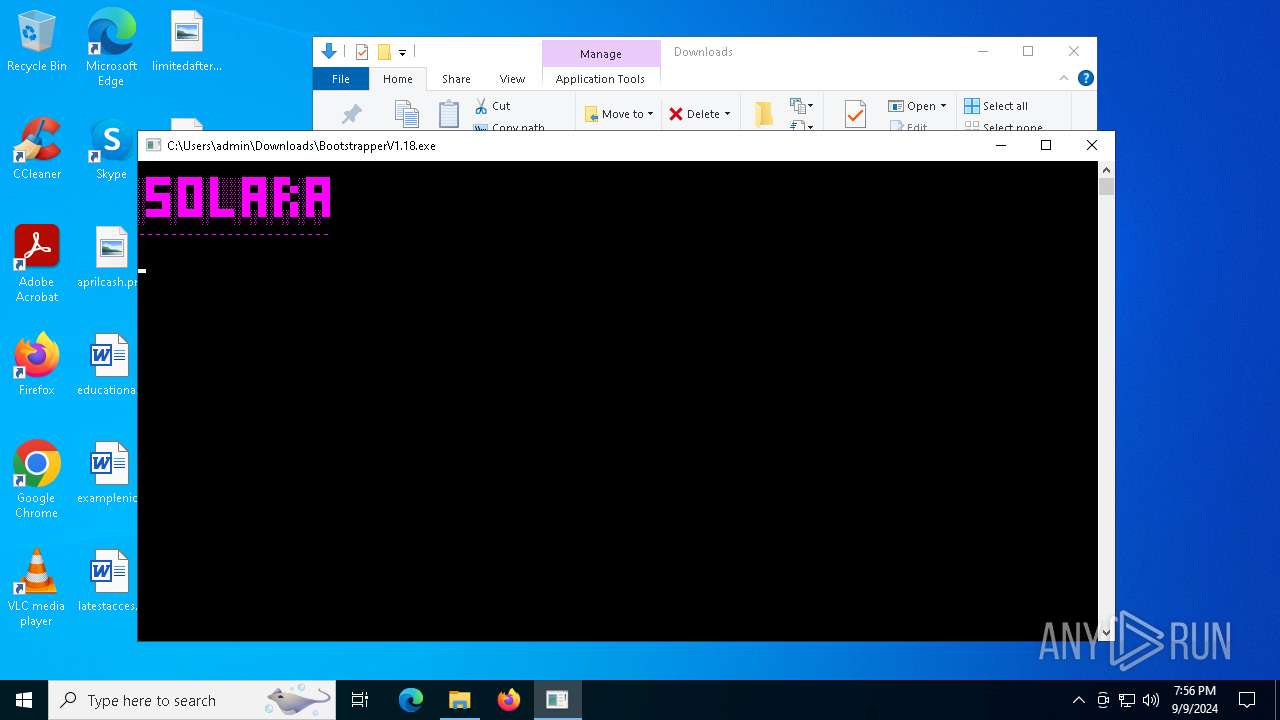
Themida protector has been detected
- Solara.exe (PID: 6744)
- Solara.exe (PID: 2628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:08:22 15:36:30+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 8 |
| CodeSize: | 812544 |
| InitializedDataSize: | 2048 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc8446 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
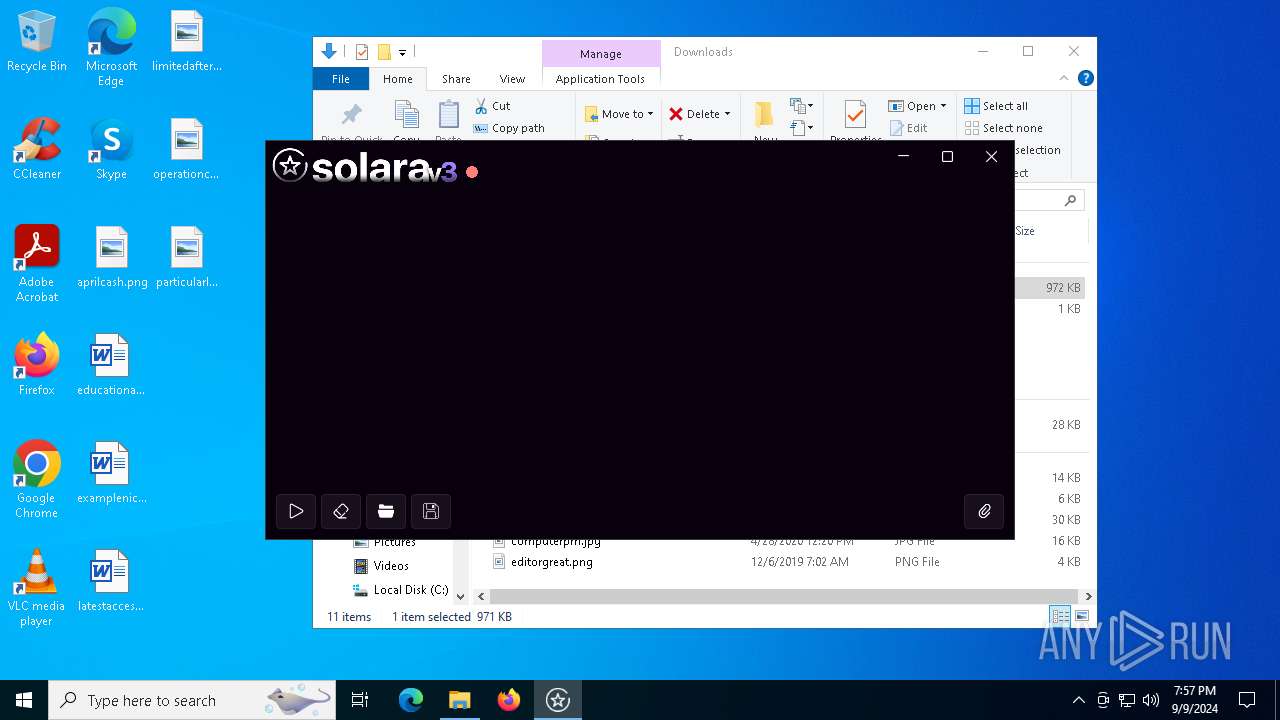
| FileDescription: | SolaraBootstrapper |
| FileVersion: | 1.0.0.0 |
| InternalName: | SolaraBootstrapper.exe |
| LegalCopyright: | Copyright © 2024 |
| LegalTrademarks: | - |
| OriginalFileName: | SolaraBootstrapper.exe |
| ProductName: | SolaraBootstrapper |
| ProductVersion: | 1.0.0.0 |
| AssemblyVersion: | 1.0.0.0 |
Total processes
165
Monitored processes
32
Malicious processes
2
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 252 | "C:\Users\admin\Downloads\Bootstrapper.exe" | C:\Users\admin\Downloads\Bootstrapper.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: SolaraBootstrapper Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 740 | C:\Windows\syswow64\MsiExec.exe -Embedding 279AD4D25CF45E6FAE64FABF25B8030F E Global\MSI0000 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1108 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | node.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | "node" -v | C:\Program Files\nodejs\node.exe | — | BootstrapperV1.18.exe | |||||||||||
User: admin Company: Node.js Integrity Level: HIGH Description: Node.js JavaScript Runtime Exit code: 0 Version: 18.16.0 Modules
| |||||||||||||||
| 1184 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | BootstrapperV1.18.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | node.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2628 | "C:\ProgramData\Solara\Solara.exe" | C:\ProgramData\Solara\Solara.exe | BootstrapperV1.18.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: WpfApp1 Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3272 | "C:\Users\admin\Downloads\BootstrapperV1.18.exe" | C:\Users\admin\Downloads\BootstrapperV1.18.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: SolaraBootstrapper Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3328 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3812 | "wevtutil.exe" im "C:\Program Files\nodejs\node_etw_provider.man" /fromwow64 | C:\Windows\System32\wevtutil.exe | — | wevtutil.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Eventing Command Line Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
30 405
Read events
27 361
Write events
3 027
Delete events
17
Modification events
| (PID) Process: | (5516) Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Bootstrapper_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5516) Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Bootstrapper_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5516) Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Bootstrapper_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (5516) Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Bootstrapper_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (5516) Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Bootstrapper_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (5516) Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Bootstrapper_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (5516) Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Bootstrapper_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (5516) Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Bootstrapper_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5516) Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Bootstrapper_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5516) Bootstrapper.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\Bootstrapper_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
30
Suspicious files
1 065
Text files
1 410
Unknown types
17
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6352 | BootstrapperV1.18.exe | C:\Users\admin\AppData\Local\Temp\node-v18.16.0-x64.msi | — | |
MD5:— | SHA256:— | |||
| 5760 | msiexec.exe | C:\Windows\Installer\13064c.msi | — | |
MD5:— | SHA256:— | |||
| 5760 | msiexec.exe | C:\Windows\Temp\~DF21B8476FB4062655.TMP | gmc | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 5760 | msiexec.exe | C:\Program Files\nodejs\corepack | text | |
MD5:1A27E3E2F449816F5FFCDD57703A3F78 | SHA256:DCEF0A787C4654AC5C085FAFA3A1E12D60D6F42E0D259C38378B61EF64295FA2 | |||
| 5760 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:356DD1FB7A87D3CA25E8DA913AC0019C | SHA256:3EFC97393097AE8723803886E702A88671B8653385E927F43F0223E1D5324F27 | |||
| 5760 | msiexec.exe | C:\Windows\Temp\~DF9EA1BFADB93E6534.TMP | binary | |
MD5:356DD1FB7A87D3CA25E8DA913AC0019C | SHA256:3EFC97393097AE8723803886E702A88671B8653385E927F43F0223E1D5324F27 | |||
| 5760 | msiexec.exe | C:\Windows\Installer\MSI10BF.tmp | binary | |
MD5:ED0C7DF33DE47BFEC666D55FFCA2B7EF | SHA256:08A9E11AC286321F209EB2CBA566D8930E672853170C0A940BA0219F09AD0672 | |||
| 5760 | msiexec.exe | C:\Windows\Installer\MSI1DB4.tmp | executable | |
MD5:7A86CE1A899262DD3C1DF656BFF3FB2C | SHA256:B8F2D0909D7C2934285A8BE010D37C0609C7854A36562CBFCBCE547F4F4C7B0C | |||
| 5760 | msiexec.exe | C:\Windows\Installer\MSI1D94.tmp | executable | |
MD5:A3AE5D86ECF38DB9427359EA37A5F646 | SHA256:C8D190D5BE1EFD2D52F72A72AE9DFA3940AB3FACEB626405959349654FE18B74 | |||
| 5760 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\66AE3BFDF94A732B262342AD2154B86E_CEA48AEE703922244E2530F7A011BBC6 | binary | |
MD5:3A69C9E7C65C736293355F88D4040273 | SHA256:38C0EC08692EB0C67BFFABF740EB06D75BCC6A3A5CD9387A38FAB0AC25116045 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
89
DNS requests
30
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2660 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5760 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSnR4FoxLLkI7vkvsUIFlZt%2BlGH3gQUWsS5eyoKo6XqcQPAYPkt9mV1DlgCEAOO2y%2FG5AVzGnYPFRYUTIU%3D | unknown | — | — | whitelisted |
5760 | msiexec.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEAQJGBtf1btmdVNDtW%2BVUAg%3D | unknown | — | — | whitelisted |
3160 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3160 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
768 | lsass.exe | GET | 200 | 142.250.186.67:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
768 | lsass.exe | GET | 200 | 142.250.186.67:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7008 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5516 | Bootstrapper.exe | 172.67.203.125:443 | getsolara.dev | CLOUDFLARENET | US | malicious |
5516 | Bootstrapper.exe | 172.67.19.24:443 | pastebin.com | CLOUDFLARENET | US | shared |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5516 | Bootstrapper.exe | 172.66.47.197:443 | 50157645.solaraweb-alj.pages.dev | CLOUDFLARENET | US | shared |
6352 | BootstrapperV1.18.exe | 172.67.203.125:443 | getsolara.dev | CLOUDFLARENET | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
getsolara.dev |
| malicious |
pastebin.com |
| shared |
client.wns.windows.com |
| whitelisted |
50157645.solaraweb-alj.pages.dev |
| shared |
clientsettings.roblox.com |
| whitelisted |
www.nodejs.org |
| whitelisted |
nodejs.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Pages platform for frontend developers to collaborate and deploy websites (pages .dev) |