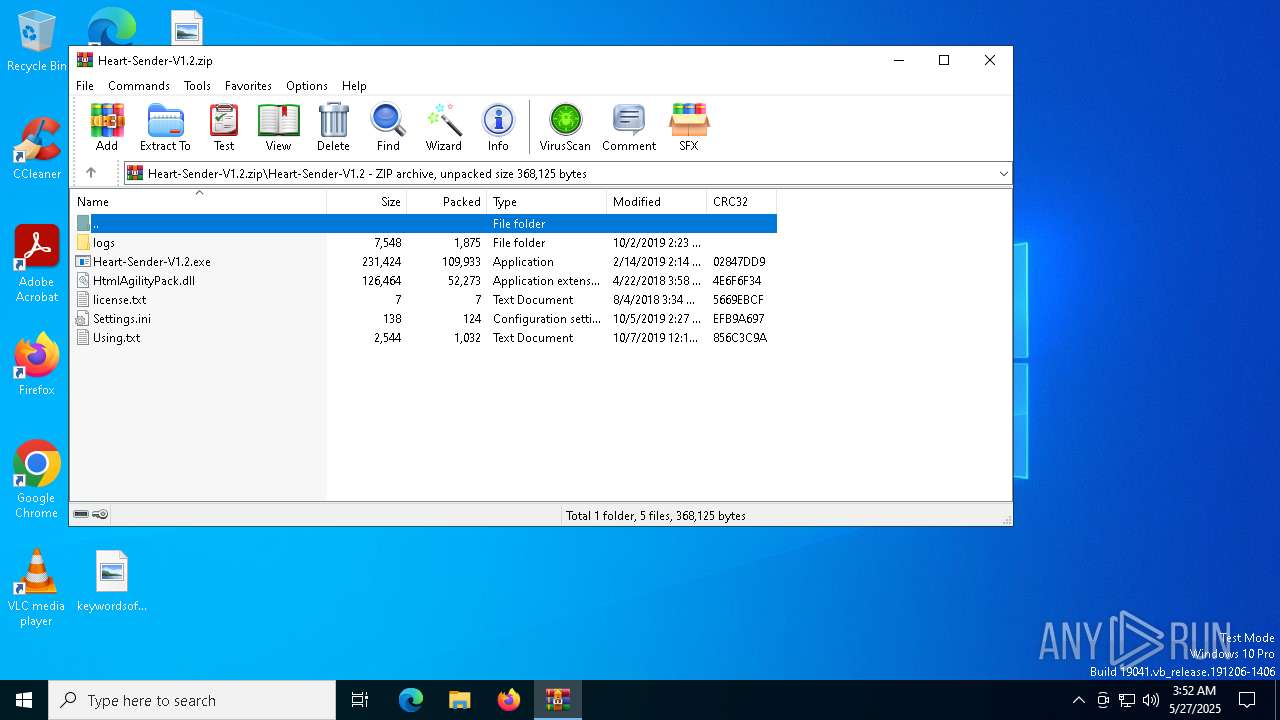
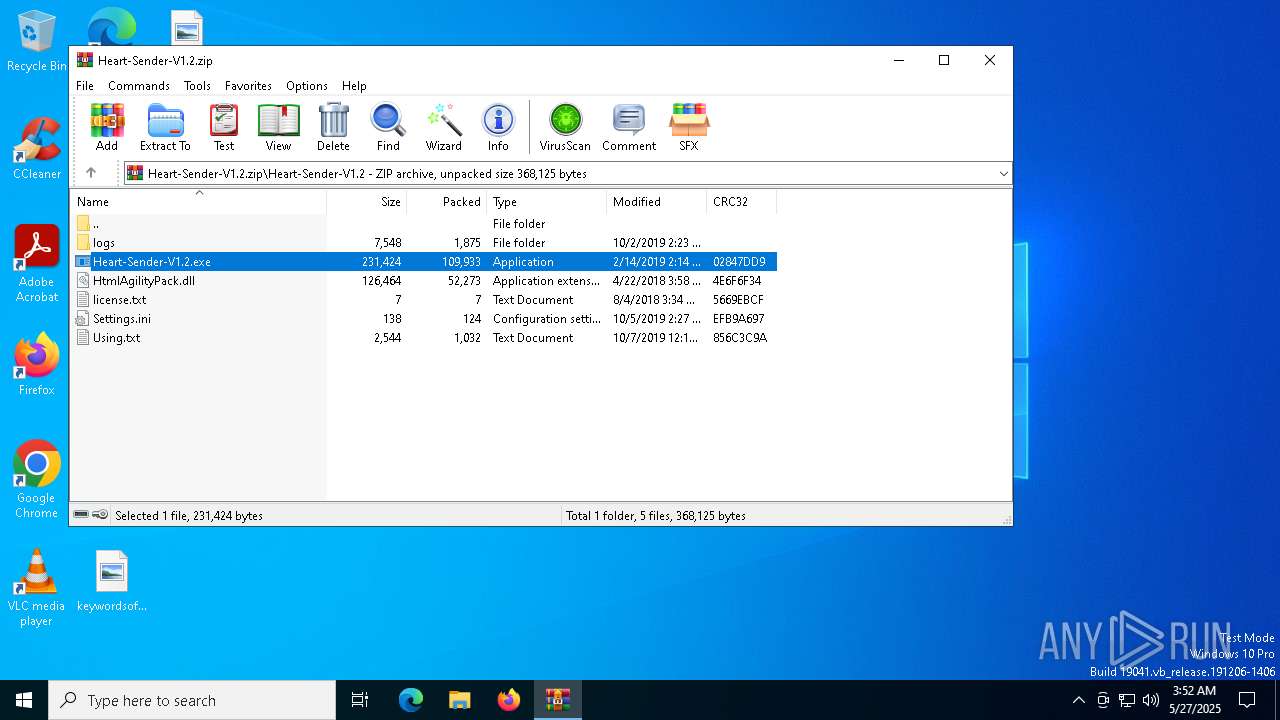
| File name: | Heart-Sender-V1.2.zip |
| Full analysis: | https://app.any.run/tasks/6a2aa10d-2aa7-4a2b-8147-4cf984ce473e |
| Verdict: | Malicious activity |
| Analysis date: | May 27, 2025, 03:52:22 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 61972A819383C70256AC9C7322A91103 |
| SHA1: | 58482C4AB342702BDAB6C2521971092906B9B2FF |
| SHA256: | 7C137B036731EA3A5300CD23E82F093830217D2FAAFEDE5C7CFF0D3A4FFF6900 |
| SSDEEP: | 3072:nl1D5DBvfV6tns3umoQAjYDpJl3WU41+dDxyDpo8OXjCE1lZpD1HMGJEeH:l1VBQtns+DQx9D3WH05xyD+nzrD1sGJR |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5960)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 5960)
INFO
Checks supported languages
- Heart-Sender-V1.2.exe (PID: 5956)
- SearchApp.exe (PID: 2924)
Reads the machine GUID from the registry
- Heart-Sender-V1.2.exe (PID: 5956)
- SearchApp.exe (PID: 2924)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5960)
Reads the computer name
- Heart-Sender-V1.2.exe (PID: 5956)
Reads the software policy settings
- SearchApp.exe (PID: 2924)
Process checks computer location settings
- SearchApp.exe (PID: 2924)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2019:10:07 12:10:06 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Heart-Sender-V1.2/ |
Total processes
134
Monitored processes
6
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2924 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3240 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4756 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
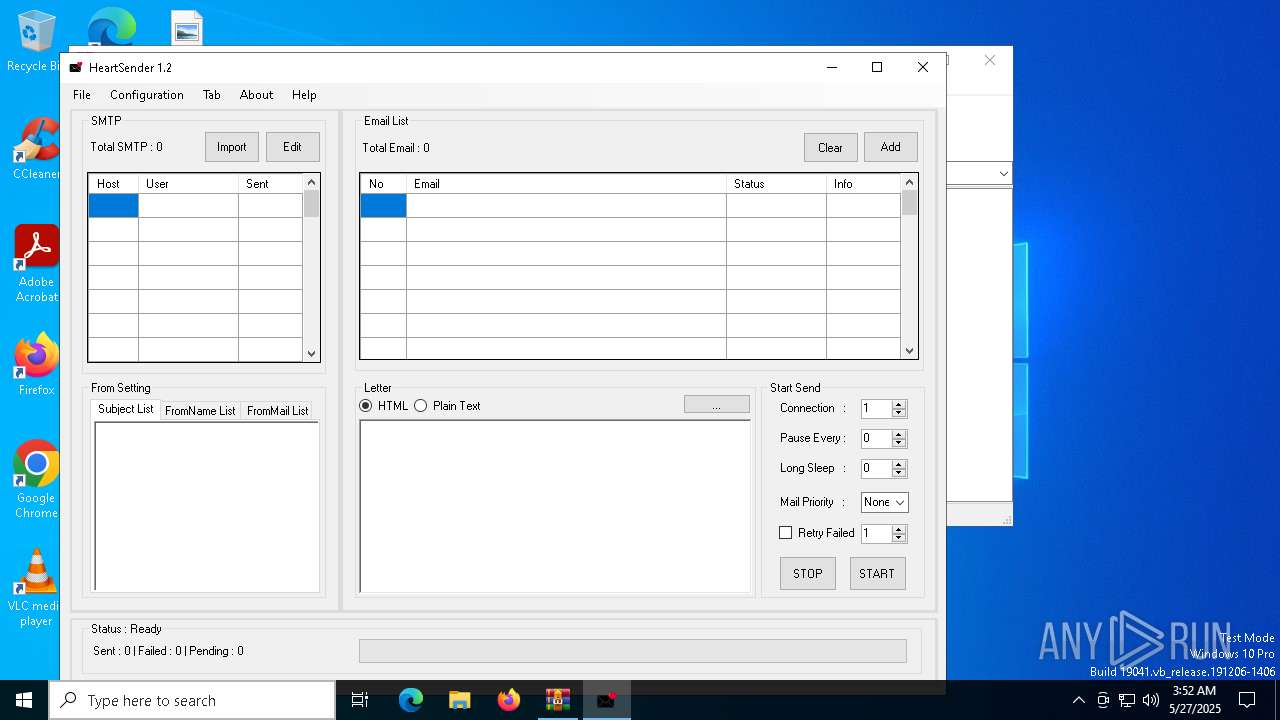
| 5956 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa5960.26552\Heart-Sender-V1.2\Heart-Sender-V1.2.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa5960.26552\Heart-Sender-V1.2\Heart-Sender-V1.2.exe | — | WinRAR.exe | |||||||||||
User: admin Company: HeartFamily Integrity Level: MEDIUM Description: Heart Sender V1 Version: 1.0.0.0 Modules
| |||||||||||||||
| 5960 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Heart-Sender-V1.2.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6876 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 885
Read events
7 796
Write events
87
Delete events
2
Modification events
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Heart-Sender-V1.2.zip | |||
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5960) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2924) SearchApp.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.search_cw5n1h2txyewy\SOFTWARE\Microsoft\Speech_OneCore\Isolated\A1hdl50UVDh2ZbG324Nx-6fZgntcGnHOs5kHLdmaJYE\HKEY_CURRENT_USER\SOFTWARE\Microsoft\Speech_OneCore\Recognizers |
| Operation: | write | Name: | DefaultTokenId |
Value: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Speech_OneCore\Recognizers\Tokens\MS-1033-110-WINMO-DNN | |||
| (PID) Process: | (2924) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | IsMSACloudSearchEnabled |
Value: 0 | |||
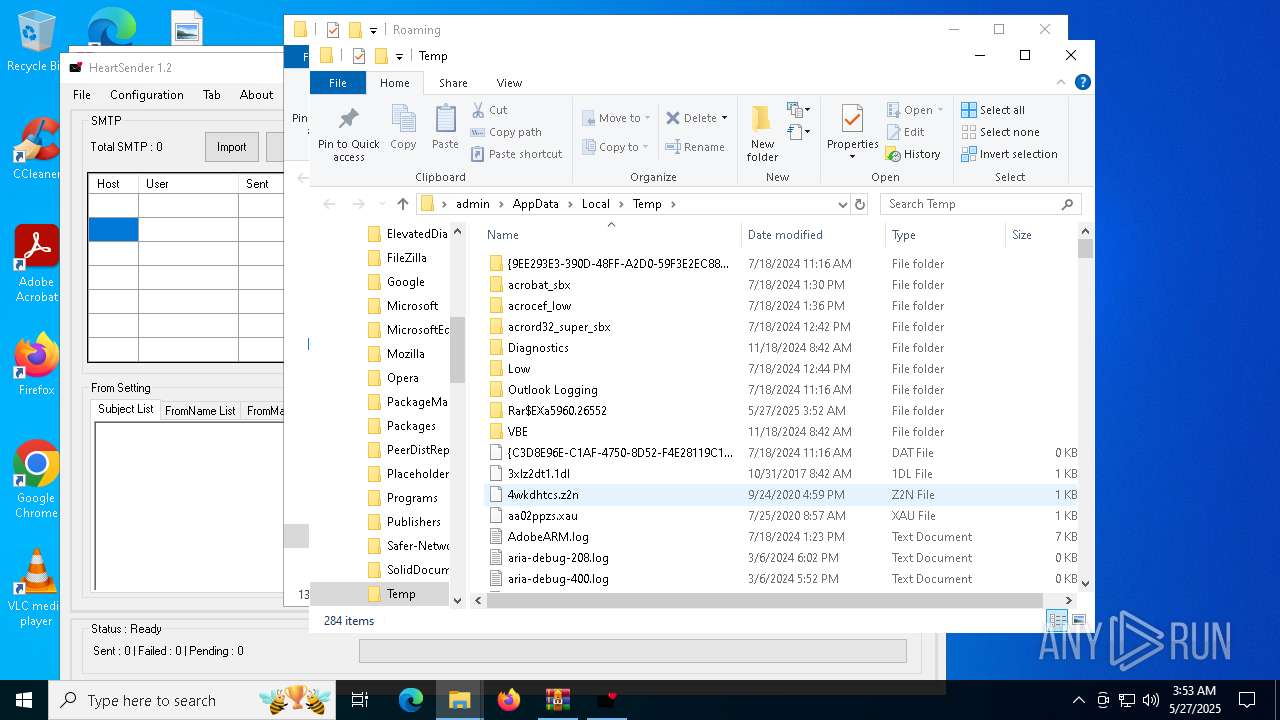
Executable files
2
Suspicious files
49
Text files
205
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5960 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5960.26552\Heart-Sender-V1.2\logs\03-10-2019\failed.txt | text | |
MD5:0B52C82FDFE3628550053A1AB024A7F9 | SHA256:D8A4BF75BDB1A4A61100CA9DB5FFEDA4002D20FA7C9418C8674EDB3135346D2F | |||
| 5960 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5960.26552\Heart-Sender-V1.2\logs\02-10-2019\success.txt | text | |
MD5:DE5420E173F4F5B0043D353FFB27AF27 | SHA256:0B840D73419CC3F33052CC8A9CA07A415CE413630663CF82A9DD42DE43F02F91 | |||
| 5960 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5960.26552\Heart-Sender-V1.2\logs\06-06-2019\logs.txt | text | |
MD5:3FCD971D51E2BC074C57C96C0078A52B | SHA256:00A94A3DC6664DB249AD2F7F5A1FBCF3F9D52F724921F64EA4130F05898C90B7 | |||
| 5960 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5960.26552\Heart-Sender-V1.2\logs\06-10-2019\failed.txt | text | |
MD5:A9E0E908EB7927B02B99BDAB4C882D64 | SHA256:C0F233541B128D2DA2125450A1B244C0694B5E232154D32A7C8B0518D796576C | |||
| 5960 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5960.26552\Heart-Sender-V1.2\logs\06-10-2019\logs.txt | text | |
MD5:A9E0E908EB7927B02B99BDAB4C882D64 | SHA256:C0F233541B128D2DA2125450A1B244C0694B5E232154D32A7C8B0518D796576C | |||
| 5960 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5960.26552\Heart-Sender-V1.2\logs\06-10-2019\success.txt | text | |
MD5:A9E0E908EB7927B02B99BDAB4C882D64 | SHA256:C0F233541B128D2DA2125450A1B244C0694B5E232154D32A7C8B0518D796576C | |||
| 5960 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5960.26552\Heart-Sender-V1.2\logs\05-10-2019\logs.txt | text | |
MD5:1F1B984173D91DF478E4AD744D83827D | SHA256:BDFB06CC2C1BBBCA0E2C25F580E4F8F4FC9A638285D111CDBA6929537FB66F16 | |||
| 5960 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5960.26552\Heart-Sender-V1.2\logs\17-03-2019\failed.txt | text | |
MD5:5BF69041628016D0810F1B1F654A6FF7 | SHA256:3E044122033B8C7F4B6F75144891203924880FED76891BC2198E71944FA1E816 | |||
| 5960 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5960.26552\Heart-Sender-V1.2\logs\06-06-2019\success.txt | text | |
MD5:3FCD971D51E2BC074C57C96C0078A52B | SHA256:00A94A3DC6664DB249AD2F7F5A1FBCF3F9D52F724921F64EA4130F05898C90B7 | |||
| 5960 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa5960.26552\Heart-Sender-V1.2\logs\17-03-2019\logs.txt | text | |
MD5:5BF69041628016D0810F1B1F654A6FF7 | SHA256:3E044122033B8C7F4B6F75144891203924880FED76891BC2198E71944FA1E816 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
37
DNS requests
23
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4068 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
4068 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2112 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2924 | SearchApp.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |