| URL: | https://www.slimjet.com/ |
| Full analysis: | https://app.any.run/tasks/1500f9b9-cceb-4441-884c-7be683a972fb |
| Verdict: | Malicious activity |
| Analysis date: | December 09, 2023, 01:18:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 0504ABC95D7AD255C641DC8EAC778858 |
| SHA1: | 119DA4E41817D8B66700A2BFC1BDC37CA152E31F |
| SHA256: | 7C1091DA4AA1AB9BF10F9C0BEFCF7750BD2A7A0FF566B6A63942A38CE7D99749 |
| SSDEEP: | 3:N8DSL0cyK3:2OL0G |
MALICIOUS
Drops the executable file immediately after the start
- sjtwebsetup_x86.exe (PID: 2836)
- sjtsetup_x86.exe (PID: 2364)
- sjt7z_x86_console.exe (PID: 2504)
SUSPICIOUS
Reads the Internet Settings
- sjtwebsetup_x86.exe (PID: 2836)
- webinstaller.exe (PID: 2948)
The process creates files with name similar to system file names
- sjtwebsetup_x86.exe (PID: 2836)
- sjtsetup_x86.exe (PID: 2364)
Malware-specific behavior (creating "System.dll" in Temp)
- sjtwebsetup_x86.exe (PID: 2836)
- sjtsetup_x86.exe (PID: 2364)
Reads settings of System Certificates
- webinstaller.exe (PID: 2948)
Checks Windows Trust Settings
- webinstaller.exe (PID: 2948)
Process requests binary or script from the Internet
- webinstaller.exe (PID: 2948)
Reads security settings of Internet Explorer
- webinstaller.exe (PID: 2948)
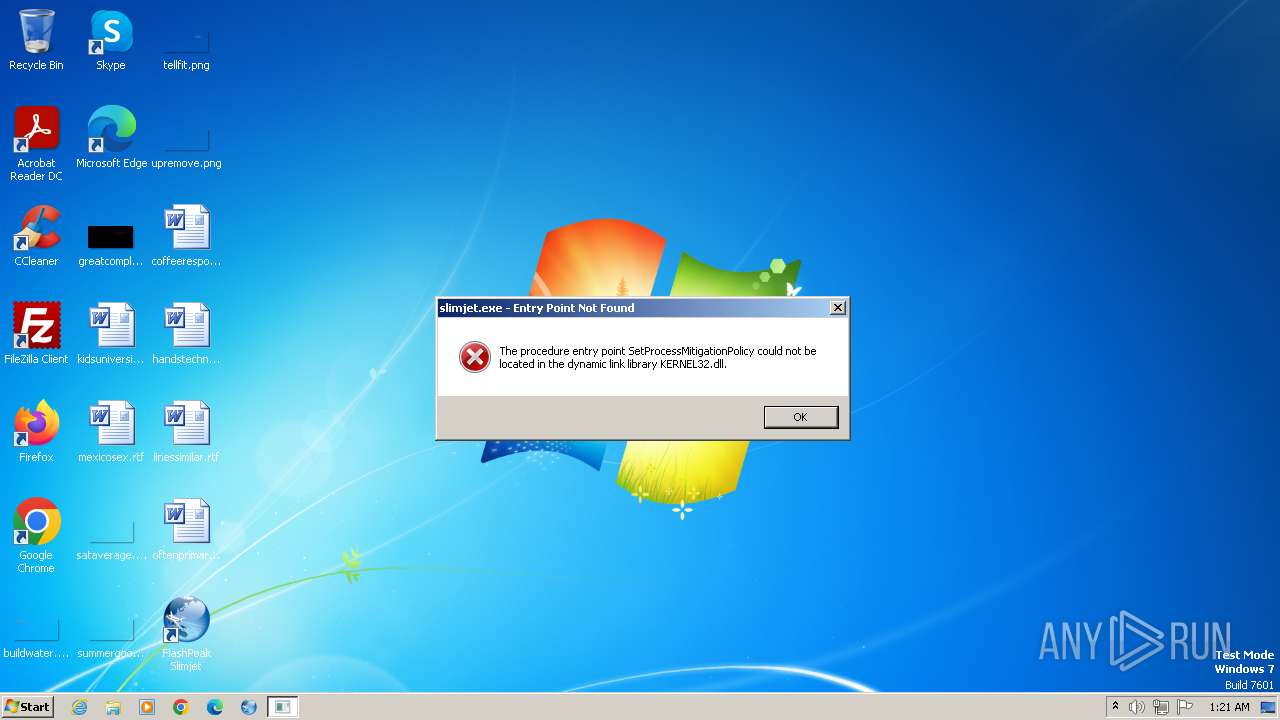
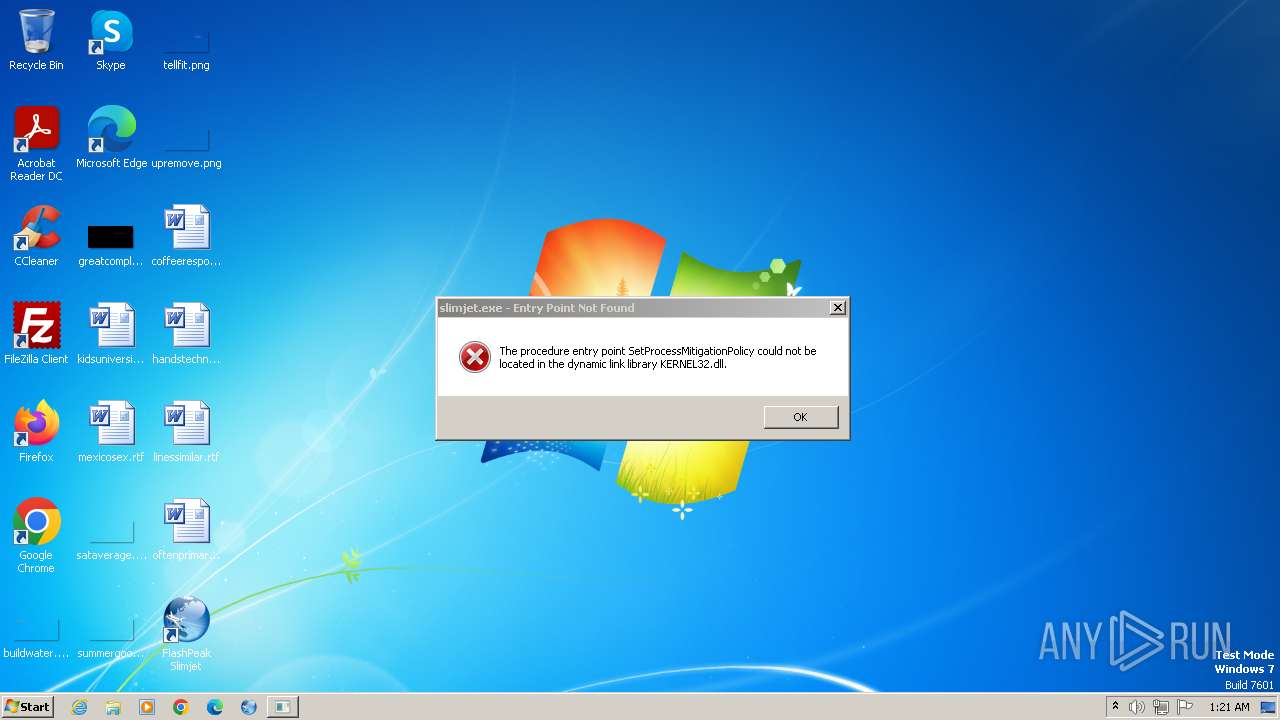
Starts application with an unusual extension
- sjtsetup_x86.exe (PID: 2364)
Process drops legitimate windows executable
- sjt7z_x86_console.exe (PID: 2504)
Adds/modifies Windows certificates
- webinstaller.exe (PID: 2948)
Explorer used for Indirect Command Execution
- explorer.exe (PID: 4016)
Drops 7-zip archiver for unpacking
- sjt7z_x86_console.exe (PID: 2504)
INFO
Application launched itself
- chrome.exe (PID: 1556)
Reads the computer name
- wmpnscfg.exe (PID: 3340)
- sjtwebsetup_x86.exe (PID: 2836)
- webinstaller.exe (PID: 2948)
- sjtsetup_x86.exe (PID: 2364)
Checks supported languages
- wmpnscfg.exe (PID: 3340)
- sjtwebsetup_x86.exe (PID: 2836)
- webinstaller.exe (PID: 2948)
- sjtsetup_x86.exe (PID: 2364)
- ns165F.tmp (PID: 1028)
- sjt7z_x86_console.exe (PID: 2504)
The process uses the downloaded file
- chrome.exe (PID: 2128)
- chrome.exe (PID: 3652)
- chrome.exe (PID: 1556)
- chrome.exe (PID: 2436)
Manual execution by a user
- wmpnscfg.exe (PID: 3340)
- explorer.exe (PID: 1432)
- slimjet.exe (PID: 1936)
Checks proxy server information
- sjtwebsetup_x86.exe (PID: 2836)
- webinstaller.exe (PID: 2948)
Drops the executable file immediately after the start
- chrome.exe (PID: 1556)
Create files in a temporary directory
- sjtwebsetup_x86.exe (PID: 2836)
- sjtsetup_x86.exe (PID: 2364)
- webinstaller.exe (PID: 2948)
Reads the machine GUID from the registry
- webinstaller.exe (PID: 2948)
- sjtsetup_x86.exe (PID: 2364)
Creates files or folders in the user directory
- webinstaller.exe (PID: 2948)
- sjtsetup_x86.exe (PID: 2364)
Reads Environment values
- sjtsetup_x86.exe (PID: 2364)
Creates files in the program directory
- sjtsetup_x86.exe (PID: 2364)
- sjt7z_x86_console.exe (PID: 2504)
Reads the Internet Settings
- explorer.exe (PID: 3528)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
79
Monitored processes
34
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --mojo-platform-channel-handle=3876 --field-trial-handle=1132,i,11269331173937500977,1908815433233384982,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 296 | "C:\Users\admin\Downloads\sjtwebsetup_x86.exe" | C:\Users\admin\Downloads\sjtwebsetup_x86.exe | — | chrome.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 684 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgACAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1148 --field-trial-handle=1132,i,11269331173937500977,1908815433233384982,131072 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 984 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --mojo-platform-channel-handle=2976 --field-trial-handle=1132,i,11269331173937500977,1908815433233384982,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1028 | "C:\Users\admin\AppData\Local\Temp\nsiA47A.tmp\ns165F.tmp" "C:\Users\admin\AppData\Local\Temp\sjt7z_x86_console.exe" -o"C:\Program Files\Slimjet" -y | C:\Users\admin\AppData\Local\Temp\nsiA47A.tmp\ns165F.tmp | — | sjtsetup_x86.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1432 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1556 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --disk-cache-dir=null --disk-cache-size=1 --media-cache-size=1 --disable-gpu-shader-disk-cache --disable-background-networking "https://www.slimjet.com/" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1600 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=3740 --field-trial-handle=1132,i,11269331173937500977,1908815433233384982,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1616 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --disable-quic --mojo-platform-channel-handle=3172 --field-trial-handle=1132,i,11269331173937500977,1908815433233384982,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1936 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2012 --field-trial-handle=1132,i,11269331173937500977,1908815433233384982,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
15 389
Read events
15 018
Write events
371
Delete events
0
Modification events
| (PID) Process: | (1556) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1556) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1556) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1556) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1556) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1556) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
| (PID) Process: | (1556) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (1556) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (1556) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
| (PID) Process: | (1556) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_enableddate |
Value: 0 | |||
Executable files
31
Suspicious files
201
Text files
420
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF2103b8.TMP | — | |
MD5:— | SHA256:— | |||
| 1556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 1556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Variations | binary | |
MD5:961E3604F228B0D10541EBF921500C86 | SHA256:F7B24F2EB3D5EB0550527490395D2F61C3D2FE74BB9CB345197DAD81B58B5FED | |||
| 1556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\c9e61372-9365-48c1-83e4-60546d4289e8.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 1556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Platform Notifications\LOG.old~RF210493.TMP | text | |
MD5:65635E713D5CFC914717D1CC4CAC6989 | SHA256:4CB3EEB0369758290ABD7868DFD85D663C4AEF6C727FFF43BE693FDDBD0A6C28 | |||
| 1556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF210a02.TMP | — | |
MD5:— | SHA256:— | |||
| 1556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF2103b8.TMP | text | |
MD5:513218482935B0D388C0A990D868387A | SHA256:8E39CBAAF4AACC3A01AFA74EA8C30FB24FE69A22B8B30728AFB1614FD68809D9 | |||
| 1556 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\metadata\LOG.old~RF2104e1.TMP | text | |
MD5:8268A4D53A6A9432A8266584CBD7D624 | SHA256:F785C42945CFE320C52C763837CD41541A8CAAB3E5FD567999EED5343CF0FD7A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
125
TCP/UDP connections
182
DNS requests
55
Threats
179
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | — | 188.114.97.3:80 | http://www.slimjetbrowser.com/release/sjtsetup_x86.exe | unknown | — | — | unknown |
2836 | sjtwebsetup_x86.exe | GET | 301 | 148.72.22.223:80 | http://www.slimjet.com/redir.php?id=startdl_sjt | unknown | html | 256 b | unknown |
2836 | sjtwebsetup_x86.exe | GET | 301 | 148.72.22.223:80 | http://www.slimjet.com/redir.php?id=startdl_sjt | unknown | html | 256 b | unknown |
2836 | sjtwebsetup_x86.exe | GET | 301 | 148.72.22.223:80 | http://www.slimjet.com/redir.php?id=startdl_sjt | unknown | html | 256 b | unknown |
2836 | sjtwebsetup_x86.exe | GET | 301 | 148.72.22.223:80 | http://www.slimjet.com/redir.php?id=startdl_sjt | unknown | html | 256 b | unknown |
2836 | sjtwebsetup_x86.exe | GET | 301 | 148.72.22.223:80 | http://www.slimjet.com/redir.php?id=startdl_sjt | unknown | html | 256 b | unknown |
2836 | sjtwebsetup_x86.exe | GET | 301 | 148.72.22.223:80 | http://www.slimjet.com/redir.php?id=startdl_sjt | unknown | html | 256 b | unknown |
2836 | sjtwebsetup_x86.exe | GET | 301 | 148.72.22.223:80 | http://www.slimjet.com/redir.php?id=startdl_sjt | unknown | html | 256 b | unknown |
2836 | sjtwebsetup_x86.exe | GET | 301 | 148.72.22.223:80 | http://www.slimjet.com/redir.php?id=startdl_sjt | unknown | html | 256 b | unknown |
2836 | sjtwebsetup_x86.exe | GET | 301 | 148.72.22.223:80 | http://www.slimjet.com/redir.php?id=startdl_sjt | unknown | html | 256 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1556 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2868 | chrome.exe | 148.72.22.223:443 | www.slimjet.com | AS-26496-GO-DADDY-COM-LLC | US | unknown |
2868 | chrome.exe | 173.194.76.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2868 | chrome.exe | 142.250.184.228:443 | www.google.com | GOOGLE | US | whitelisted |
2868 | chrome.exe | 157.240.252.13:443 | connect.facebook.net | FACEBOOK | DE | unknown |
2868 | chrome.exe | 142.250.185.110:443 | www.google-analytics.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.slimjet.com |
| unknown |
accounts.google.com |
| shared |
www.google.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
connect.facebook.net |
| whitelisted |
content-autofill.googleapis.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
region1.google-analytics.com |
| whitelisted |
www.facebook.com |
| whitelisted |
optimizationguide-pa.googleapis.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2948 | webinstaller.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
178 ETPRO signatures available at the full report
Process | Message |
|---|---|
webinstaller.exe | |
webinstaller.exe | Starting download... |
webinstaller.exe | |
webinstaller.exe | Redirection succeeded. Opening new URL |
webinstaller.exe | |
webinstaller.exe | Redirecting... - http://www.slimjetbrowser.com/release/sjtsetup_x86.exe |
webinstaller.exe | [Section 1] - Started |
webinstaller.exe | Opening file on the disk... |
webinstaller.exe | |
webinstaller.exe | Succeeded |