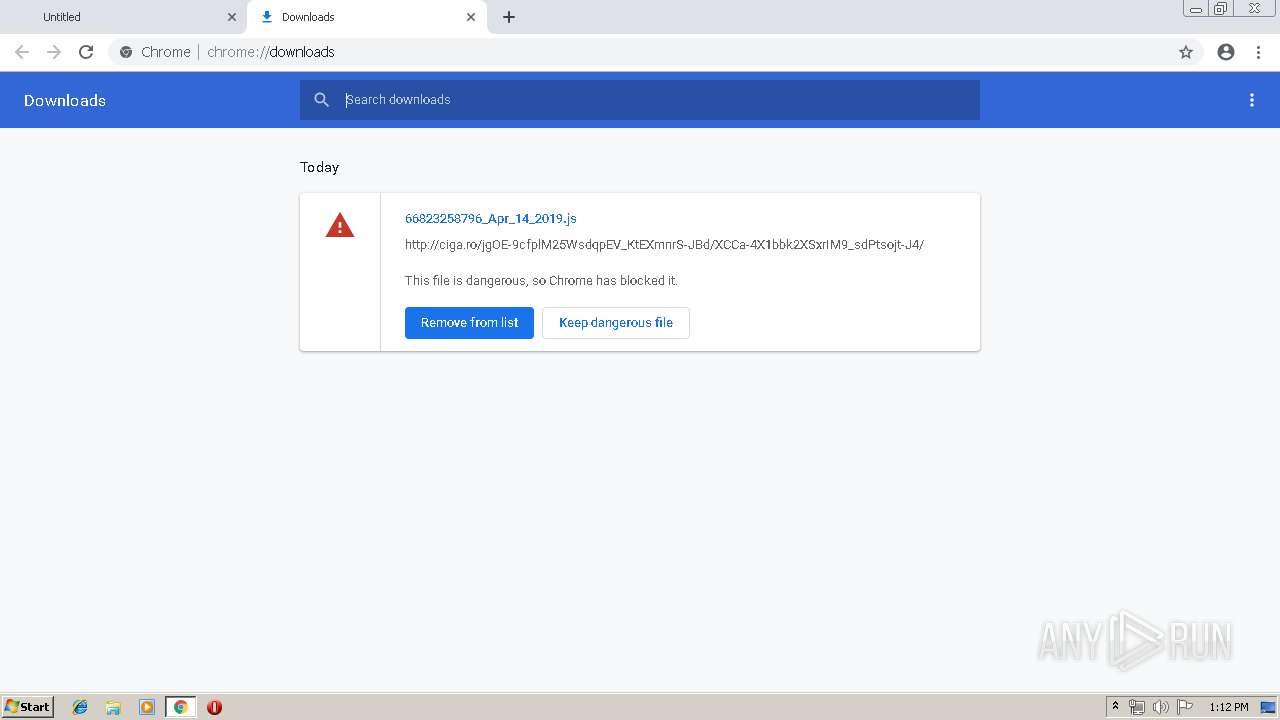
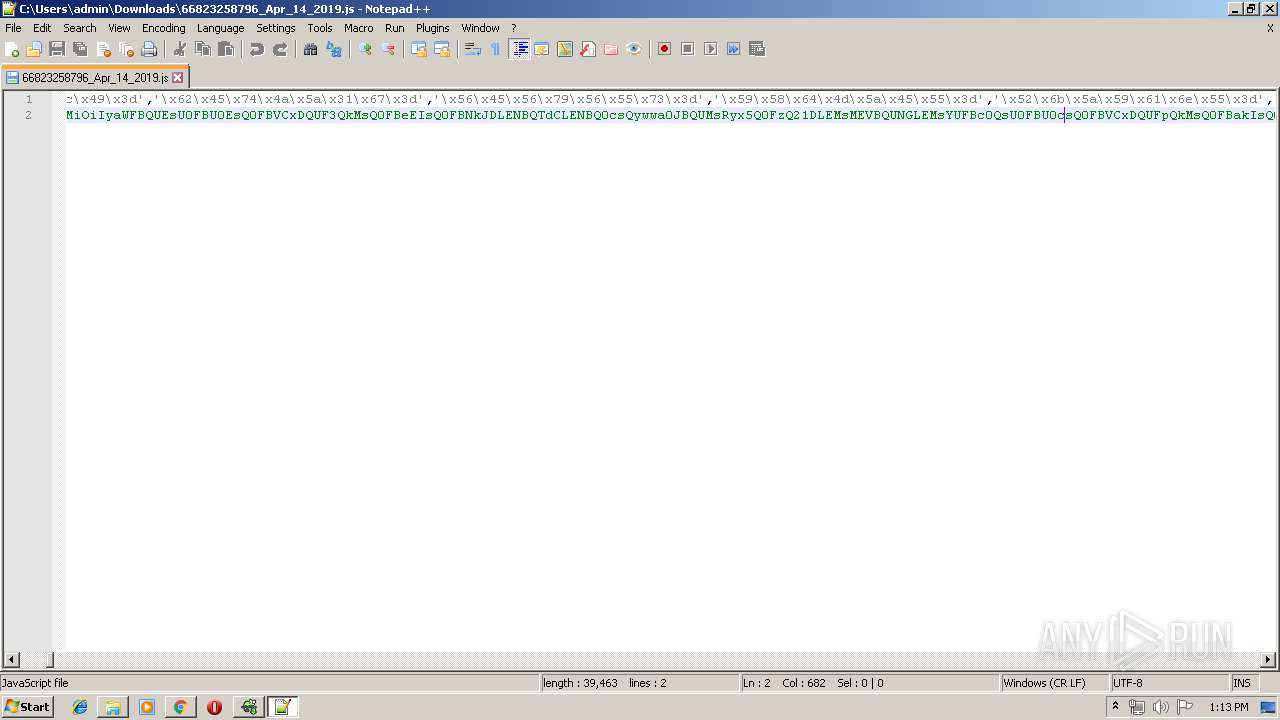
| URL: | http://ciga.ro/jgOE-9cfplM25WsdqpEV_KtEXmnrS-JBd/XCCa-4X1bbk2XSxrIM9_sdPtsojt-J4/ |
| Full analysis: | https://app.any.run/tasks/1f8d21b9-fae7-4850-ae14-4e99966c08c2 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | April 15, 2019, 12:12:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | C6923FCE12B49C9267F9676639AF5EBC |
| SHA1: | A5841256FEEF40E03F71D1935AE5E66BEFE3219D |
| SHA256: | 7BE612B4539BDE7ED069D9C31B203DC038139C92A126791C327ADC39A06D9431 |
| SSDEEP: | 3:N1KdMrabqt92gW/9w29rR9euEVQUK:COraOtId/VEQUK |
MALICIOUS
Application was dropped or rewritten from another process
- npp.7.6.6.Installer.exe (PID: 3232)
- k2fd15j0o.exe (PID: 3308)
- k2fd15j0o.exe (PID: 724)
- npp.7.6.6.Installer.exe (PID: 4076)
- soundser.exe (PID: 2360)
- soundser.exe (PID: 3168)
Loads dropped or rewritten executable
- npp.7.6.6.Installer.exe (PID: 3232)
Downloads executable files from the Internet
- WScript.exe (PID: 3800)
Emotet process was detected
- soundser.exe (PID: 2360)
EMOTET was detected
- soundser.exe (PID: 3168)
Connects to CnC server
- soundser.exe (PID: 3168)
SUSPICIOUS
Executable content was dropped or overwritten
- gup.exe (PID: 388)
- npp.7.6.6.Installer.exe (PID: 3232)
- WScript.exe (PID: 3800)
- k2fd15j0o.exe (PID: 724)
Creates files in the user directory
- WScript.exe (PID: 3800)
- notepad++.exe (PID: 3880)
Starts itself from another location
- k2fd15j0o.exe (PID: 724)
Application launched itself
- k2fd15j0o.exe (PID: 3308)
- soundser.exe (PID: 2360)
Connects to server without host name
- soundser.exe (PID: 3168)
INFO
Application launched itself
- chrome.exe (PID: 3900)
Creates files in the user directory
- chrome.exe (PID: 3900)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
59
Monitored processes
23
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 296 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=964,25953161142047304,11320173695983223191,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=9843430035421757168 --mojo-platform-channel-handle=3056 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 388 | "C:\Program Files\Notepad++\updater\gup.exe" -v7.51 | C:\Program Files\Notepad++\updater\gup.exe | notepad++.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: GUP : a free (LGPL) Generic Updater Exit code: 0 Version: 4.1 Modules
| |||||||||||||||
| 536 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=964,25953161142047304,11320173695983223191,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --service-request-channel-token=3377113839111158248 --mojo-platform-channel-handle=1504 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 724 | --32f25f04 | C:\Users\admin\AppData\Local\Temp\k2fd15j0o.exe | k2fd15j0o.exe | ||||||||||||
User: admin Company: 360. cn Integrity Level: MEDIUM Description: 360 FirstAid Exit code: 0 Version: 1, 0, 0, 1007 Modules
| |||||||||||||||
| 1000 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=964,25953161142047304,11320173695983223191,131072 --enable-features=PasswordImport --service-pipe-token=4843485197905039858 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4843485197905039858 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2068 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1372 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=964,25953161142047304,11320173695983223191,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=5960995953519928031 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5960995953519928031 --renderer-client-id=8 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3180 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
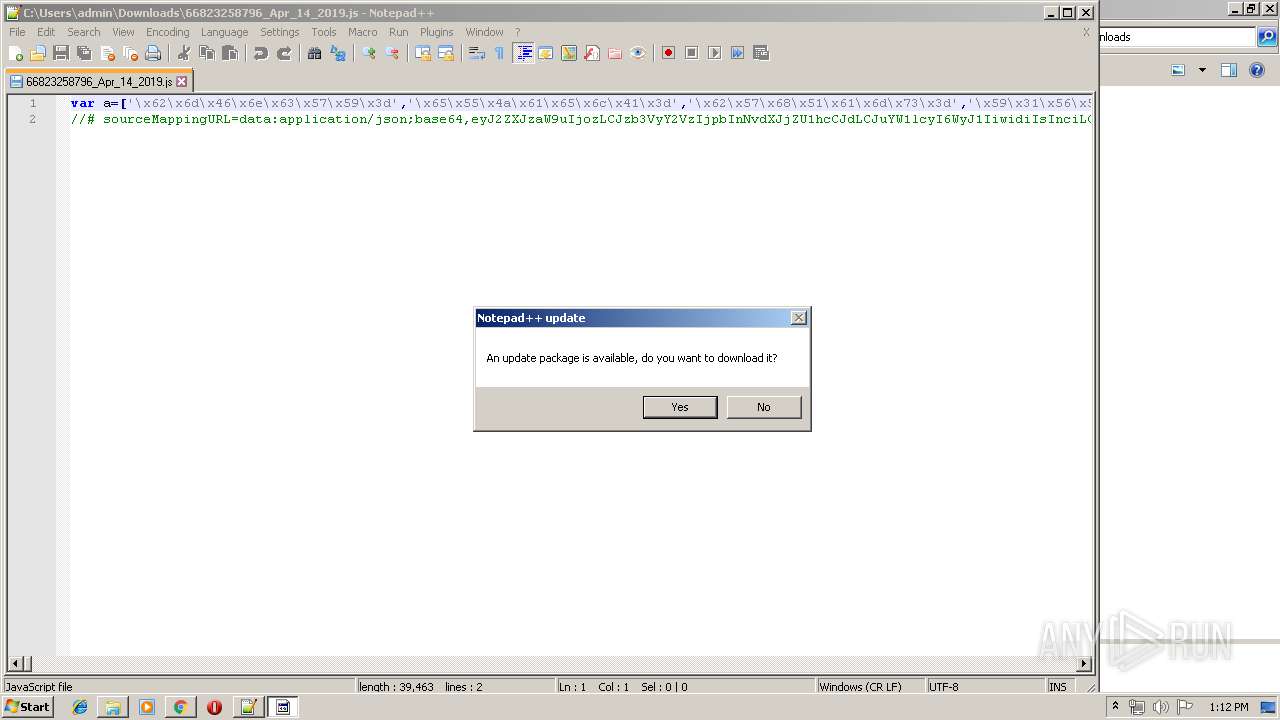
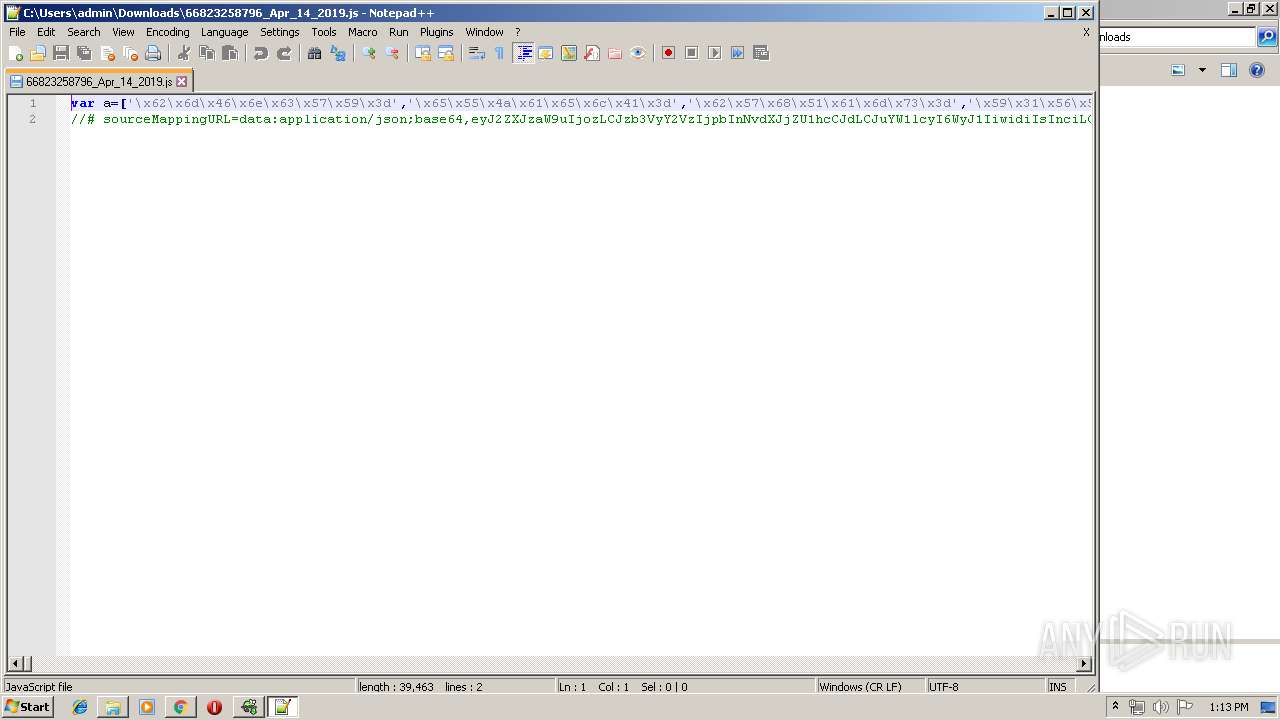
| 1480 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Downloads\66823258796_Apr_14_2019.js" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
| 2132 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=964,25953161142047304,11320173695983223191,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=4706348997586022290 --mojo-platform-channel-handle=1880 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2176 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=3904 --on-initialized-event-handle=308 --parent-handle=312 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2360 | "C:\Users\admin\AppData\Local\soundser\soundser.exe" | C:\Users\admin\AppData\Local\soundser\soundser.exe | k2fd15j0o.exe | ||||||||||||
User: admin Company: 360. cn Integrity Level: MEDIUM Description: 360 FirstAid Exit code: 0 Version: 1, 0, 0, 1007 Modules
| |||||||||||||||
Total events
1 553
Read events
1 432
Write events
118
Delete events
3
Modification events
| (PID) Process: | (3900) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3900) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3900) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3900) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3900) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2176) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 3900-13199803947687750 |
Value: 259 | |||
| (PID) Process: | (3900) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3900) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3900) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3488-13197474229333984 |
Value: 0 | |||
| (PID) Process: | (3900) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3900-13199803947687750 |
Value: 259 | |||
Executable files
4
Suspicious files
7
Text files
68
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3900 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 3900 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 3900 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 3900 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_2 | — | |
MD5:— | SHA256:— | |||
| 3900 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_3 | — | |
MD5:— | SHA256:— | |||
| 3900 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\3ac504bc-9b1f-4506-8aaa-3c6c150f346a.tmp | — | |
MD5:— | SHA256:— | |||
| 3900 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000018.dbtmp | — | |
MD5:— | SHA256:— | |||
| 3900 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 3900 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 3900 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
18
DNS requests
13
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
536 | chrome.exe | GET | 200 | 5.35.209.10:80 | http://ciga.ro/jgOE-9cfplM25WsdqpEV_KtEXmnrS-JBd/XCCa-4X1bbk2XSxrIM9_sdPtsojt-J4/ | RO | text | 13.7 Kb | unknown |
— | — | GET | 200 | 2.16.106.50:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCEBPqKHBb9OztDDZjCYBhQzY%3D | unknown | der | 471 b | whitelisted |
— | — | GET | 200 | 2.16.106.50:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEAXk3DuUOKs7hZfLpqGYUOM%3D | unknown | der | 727 b | whitelisted |
3800 | WScript.exe | GET | 200 | 77.92.74.1:80 | http://1roof.ltd.uk/creationmaintenance.co.uk/FC_W/ | GB | executable | 130 Kb | malicious |
3168 | soundser.exe | POST | — | 117.193.28.115:80 | http://117.193.28.115/add/schema/ | IN | — | — | malicious |
3168 | soundser.exe | POST | — | 202.133.72.136:443 | http://202.133.72.136:443/jit/prov/ringin/ | IN | — | — | malicious |
3168 | soundser.exe | POST | — | 94.11.25.255:80 | http://94.11.25.255/merge/attrib/ringin/merge/ | GB | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 172.217.18.110:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
— | — | 172.217.23.174:443 | safebrowsing.google.com | Google Inc. | US | whitelisted |
388 | gup.exe | 37.59.28.236:443 | notepad-plus-plus.org | OVH SAS | FR | whitelisted |
536 | chrome.exe | 5.35.209.10:80 | ciga.ro | T-Mobile Czech Republic a.s. | RO | unknown |
536 | chrome.exe | 172.217.22.67:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
536 | chrome.exe | 172.217.16.131:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
536 | chrome.exe | 216.58.205.237:443 | accounts.google.com | Google Inc. | US | whitelisted |
— | — | 2.16.106.50:80 | ocsp.usertrust.com | Akamai International B.V. | — | whitelisted |
536 | chrome.exe | 172.217.16.206:443 | clients1.google.com | Google Inc. | US | whitelisted |
3800 | WScript.exe | 77.92.74.1:80 | 1roof.ltd.uk | UK-2 Limited | GB | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ciga.ro |
| unknown |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
sb-ssl.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
safebrowsing.google.com |
| whitelisted |
notepad-plus-plus.org |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
1roof.ltd.uk |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3800 | WScript.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3800 | WScript.exe | A Network Trojan was detected | ET CURRENT_EVENTS Likely Evil EXE download from MSXMLHTTP non-exe extension M2 |
3800 | WScript.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
3168 | soundser.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3168 | soundser.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
2 ETPRO signatures available at the full report
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|