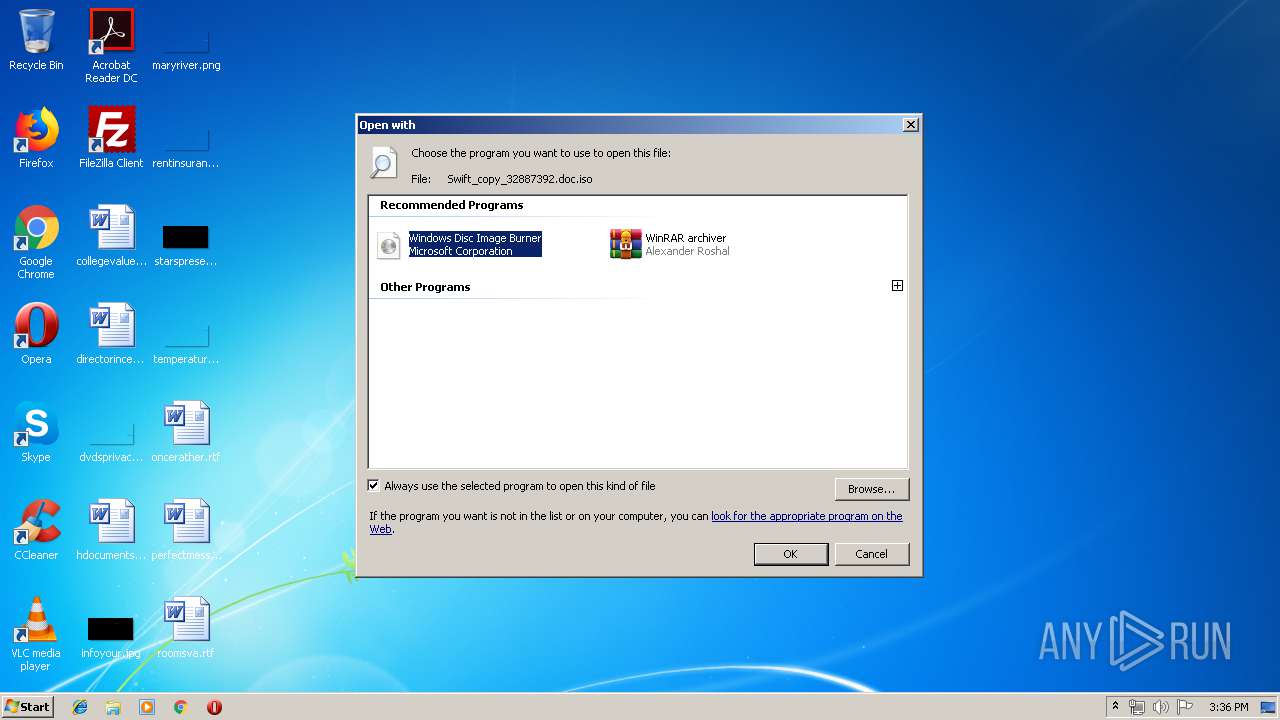
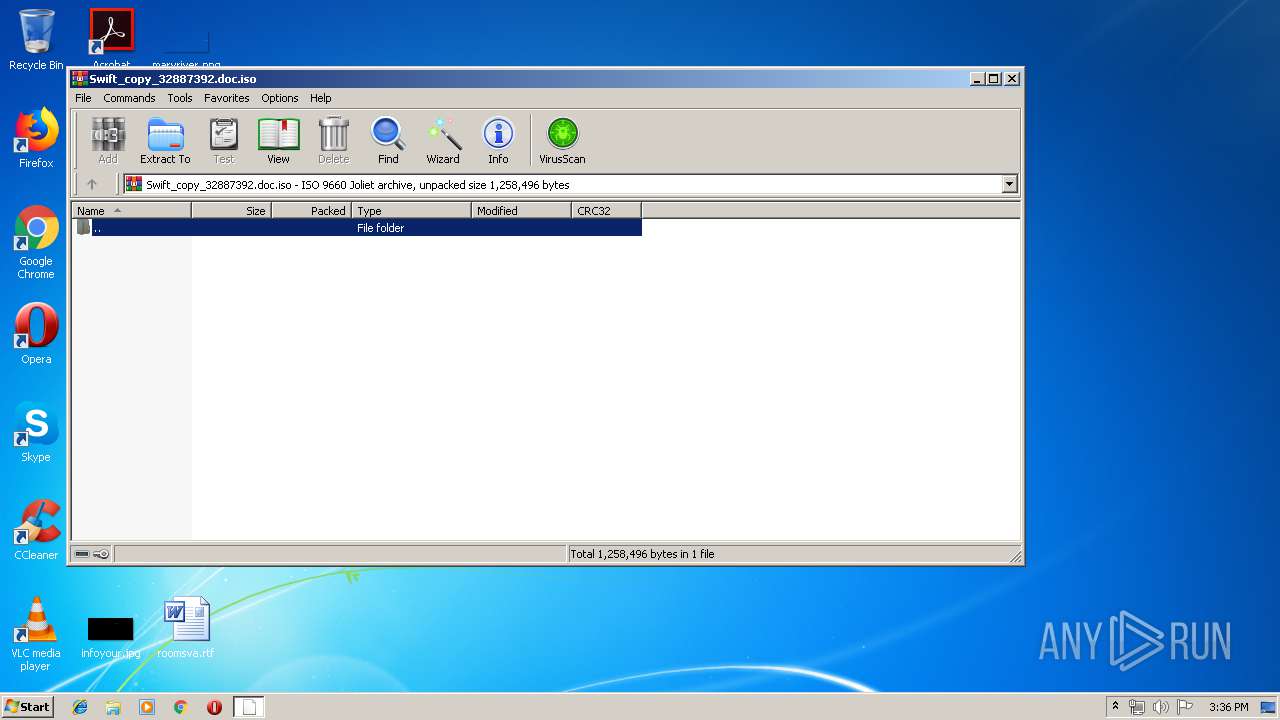
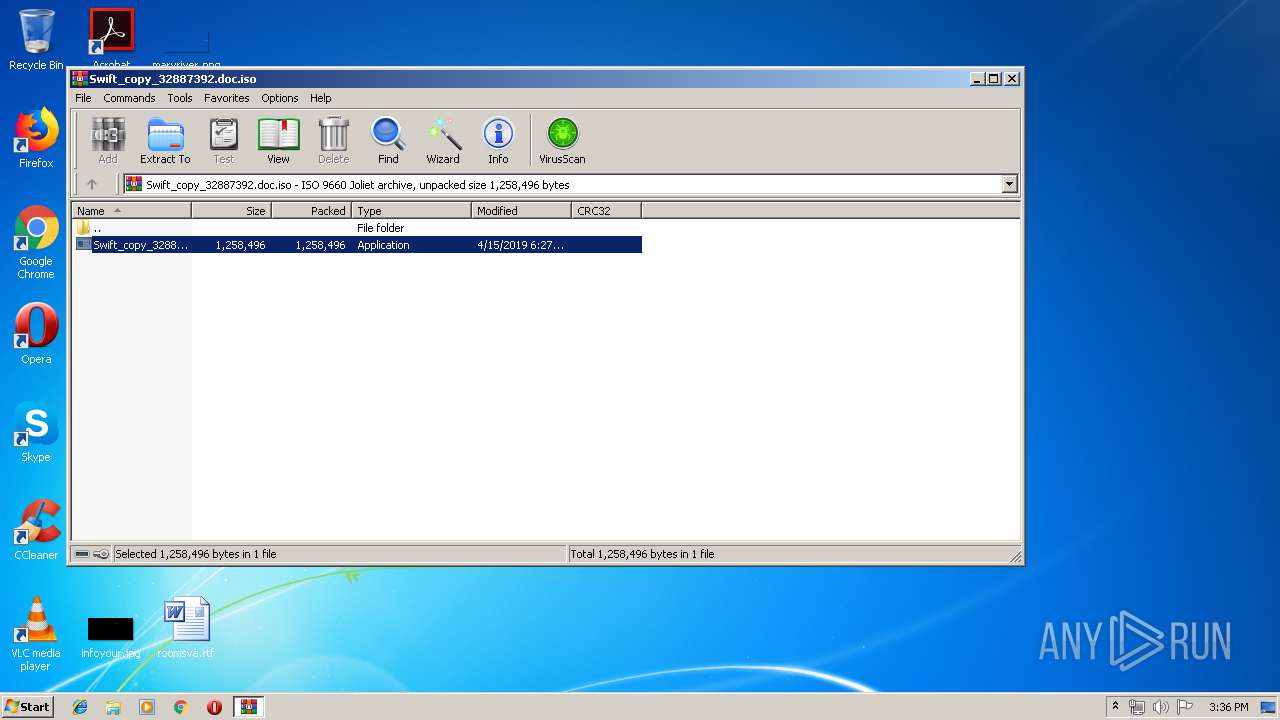
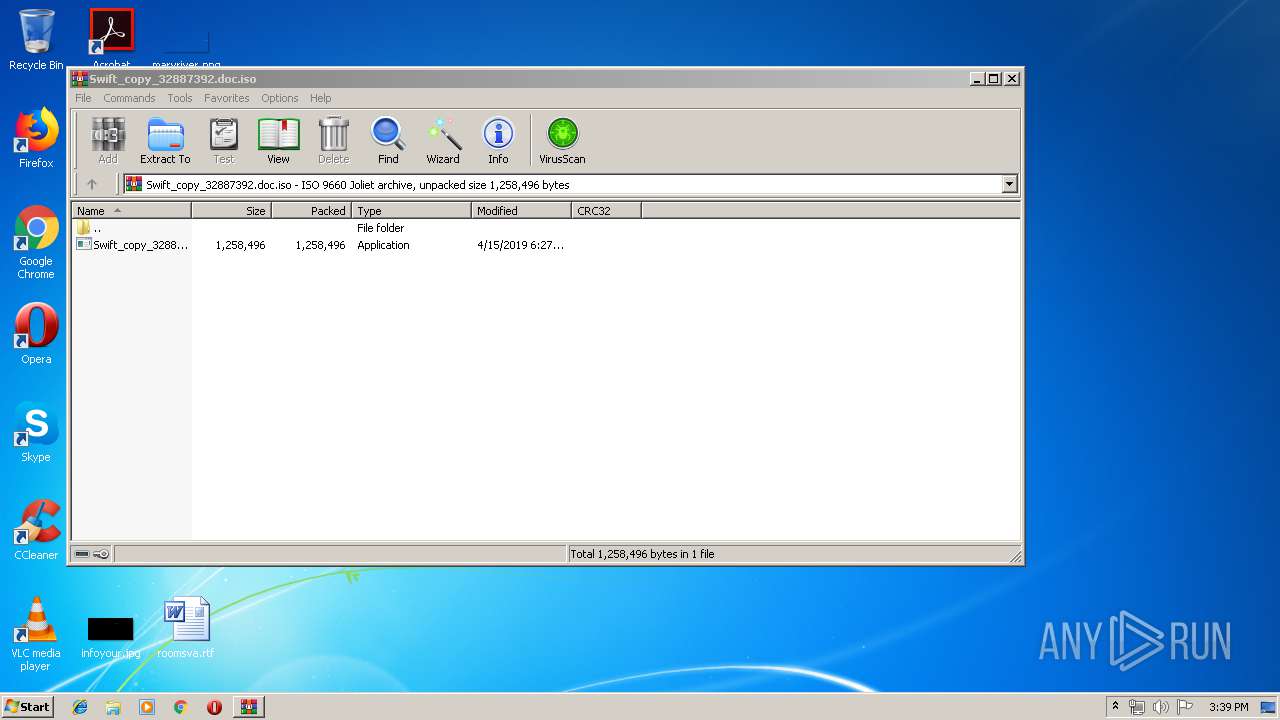
| File name: | Swift_copy_32887392.doc.iso |
| Full analysis: | https://app.any.run/tasks/8184fd04-e198-4c35-8132-55ba968dac32 |
| Verdict: | Malicious activity |
| Analysis date: | April 15, 2019, 14:35:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-iso9660-image |
| File info: | ISO 9660 CD-ROM filesystem data 'Swift_copy_32887392' |
| MD5: | 03C609826F1A74B147F2C3869D052122 |
| SHA1: | 51BAF66173E49F1844C8DCFB087AAF186D32E674 |
| SHA256: | 7BAA3FE37108FF70961A55F5730A056E36B4BBC69018B406E24A6072DA8FA5B9 |
| SSDEEP: | 24576:TAHnh+eWsN3skA4RV1Hom2KXMmHagKkxHZ2ihSsaP5:eh+ZkldoPK8Yag0 |
MALICIOUS
Application was dropped or rewritten from another process
- Swift_copy_32887392.exe (PID: 1256)
- Swift_copy_32887392.exe (PID: 2804)
- Swift_copy_32887392.exe (PID: 2268)
- Swift_copy_32887392.exe (PID: 2792)
- Swift_copy_32887392.exe (PID: 2304)
- Swift_copy_32887392.exe (PID: 2316)
- Swift_copy_32887392.exe (PID: 2820)
- Swift_copy_32887392.exe (PID: 1832)
- Swift_copy_32887392.exe (PID: 2808)
- Swift_copy_32887392.exe (PID: 2728)
- Swift_copy_32887392.exe (PID: 3132)
- Swift_copy_32887392.exe (PID: 1944)
- Swift_copy_32887392.exe (PID: 932)
- Swift_copy_32887392.exe (PID: 3524)
SUSPICIOUS
Application launched itself
- Swift_copy_32887392.exe (PID: 2804)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1388)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .iso | | | ISO 9660 CD image (27.6) |
|---|---|---|
| .atn | | | Photoshop Action (27.1) |
| .gmc | | | Game Music Creator Music (6.1) |
EXIF
ISO
| System: | Win32 |
|---|---|
| VolumeName: | Swift_copy_32887392 |
| VolumeBlockCount: | 645 |
| VolumeBlockSize: | 2048 |
| RootDirectoryCreateDate: | 2019:04:15 08:29:48+03:00 |
| Software: | PowerISO |
| VolumeCreateDate: | 2019:04:15 08:29:48.00+03:00 |
| VolumeModifyDate: | 2019:04:15 08:29:48.00+03:00 |
Composite
| VolumeSize: | 1290 kB |
|---|
Total processes
46
Monitored processes
16
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 932 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.26389\Swift_copy_32887392.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.26389\Swift_copy_32887392.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1256 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.49928\Swift_copy_32887392.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.49928\Swift_copy_32887392.exe | — | Swift_copy_32887392.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1388 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Swift_copy_32887392.doc.iso" | C:\Program Files\WinRAR\WinRAR.exe | rundll32.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1832 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.49928\Swift_copy_32887392.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.49928\Swift_copy_32887392.exe | — | Swift_copy_32887392.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1944 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.49928\Swift_copy_32887392.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.49928\Swift_copy_32887392.exe | — | Swift_copy_32887392.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2268 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.49928\Swift_copy_32887392.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.49928\Swift_copy_32887392.exe | — | Swift_copy_32887392.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2304 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.26389\Swift_copy_32887392.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.26389\Swift_copy_32887392.exe | — | Swift_copy_32887392.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2316 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.26389\Swift_copy_32887392.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.26389\Swift_copy_32887392.exe | — | Swift_copy_32887392.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2728 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.26389\Swift_copy_32887392.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.26389\Swift_copy_32887392.exe | — | Swift_copy_32887392.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2792 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.49928\Swift_copy_32887392.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.49928\Swift_copy_32887392.exe | — | Swift_copy_32887392.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
899
Read events
808
Write events
91
Delete events
0
Modification events
| (PID) Process: | (3040) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3040) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\isoburn.exe,-350 |
Value: Disc Image File | |||
| (PID) Process: | (3040) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.iso\OpenWithProgids |
| Operation: | write | Name: | Windows.IsoFile |
Value: | |||
| (PID) Process: | (3040) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | LangID |
Value: 0904 | |||
| (PID) Process: | (3040) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\System32\isoburn.exe,-352 |
Value: Windows Disc Image Burner | |||
| (PID) Process: | (3040) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\System32\isoburn.exe |
Value: Windows Disc Image Burner | |||
| (PID) Process: | (3040) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\WinRAR\WinRAR.exe |
Value: WinRAR archiver | |||
| (PID) Process: | (3040) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe |
Value: Adobe Acrobat Reader DC | |||
| (PID) Process: | (3040) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\eHome\ehshell.exe |
Value: Windows Media Center | |||
| (PID) Process: | (3040) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Internet Explorer\iexplore.exe |
Value: Internet Explorer | |||
Executable files
2
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.49928\Swift_copy_32887392.exe | executable | |
MD5:— | SHA256:— | |||
| 1388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.26389\Swift_copy_32887392.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report